Splunk plugin¶
The Vulners Splunk Plugin converts Splunk into a potent platform for vulnerability assessment and security scanning by utilizing the comprehensive Vulners.com vulnerability database.
Note
- The current distribution package is optimized for a single-machine environment but is fully compatible with setups that include one indexer and one search head on a single machine. It includes components for the forwarder, indexer, and search head.
- Despite Splunk's AppInspect guidance against custom indexes, this package includes one for convenience in single-machine setups. Multi-machine users should adjust accordingly (details below).
- For simple installations without separate indexers, use the package as is. For more complex deployments, refer to the slim partitioning section below.
Installation Steps¶
Dashboard app¶
Install¶
In Splunk dashboard search head go to
Apps -> Install app from file -> choose [vulners-lookup-*.tar.gz](https://github.com/vulnersCom/splunk-vulners/blob/master/result/vulners-lookup-0.0.3.tar.gz)
Then restart Splunk
Add Vulners API key¶
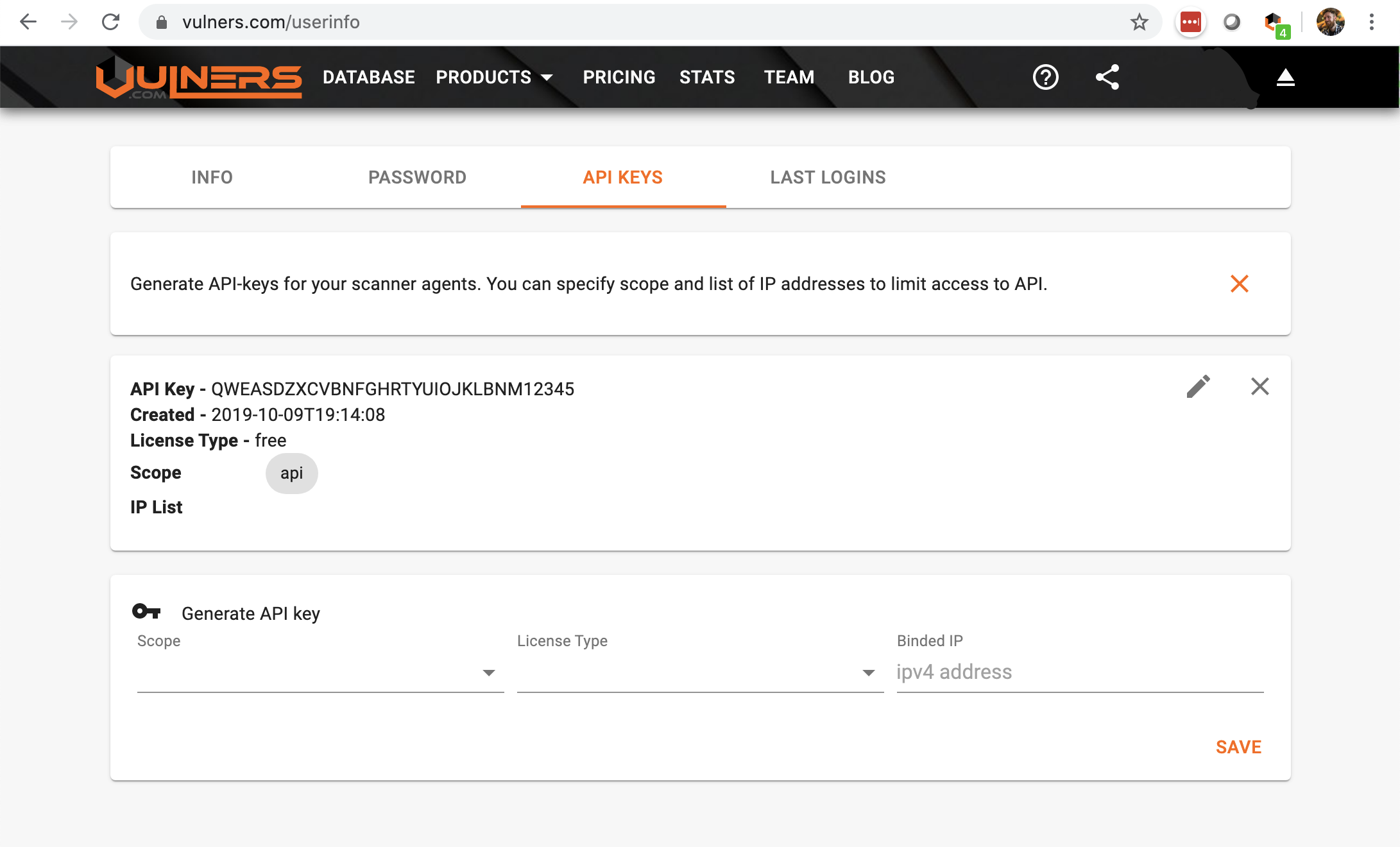
-
get API key from vulners.com
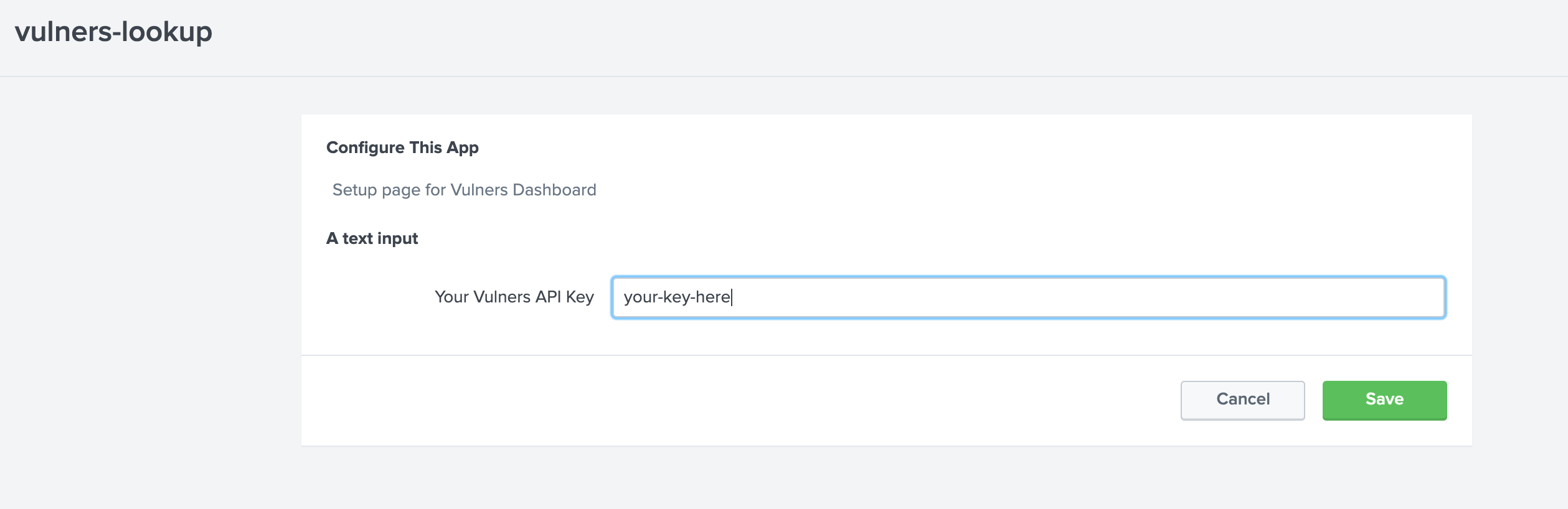
-
add API key to Vulners Splunk dashboard
Create vulners index¶
Since the forwarder app forwards data to the index named vulners, it has to be present in the system.
Settings -> Indexes -> New Index
Add receiving port¶
If you are using Splunk for the first time, don't forget to set data receiver
Settings -> Forwarding and receiving -> Configure receiving -> New Receiving port

Forwarder app¶
Install¶
Unpack vulners_lookup.tar.gz into $SPLUNK_FORWARDER_HOME/etc/apps/
Python libs¶
Install the following Python libs on forwarder machines
pip3 install distro getmac ifaddr futures
Add forward server¶
If you are installing forwarder for the first time, you have to add forward-server
Usage¶
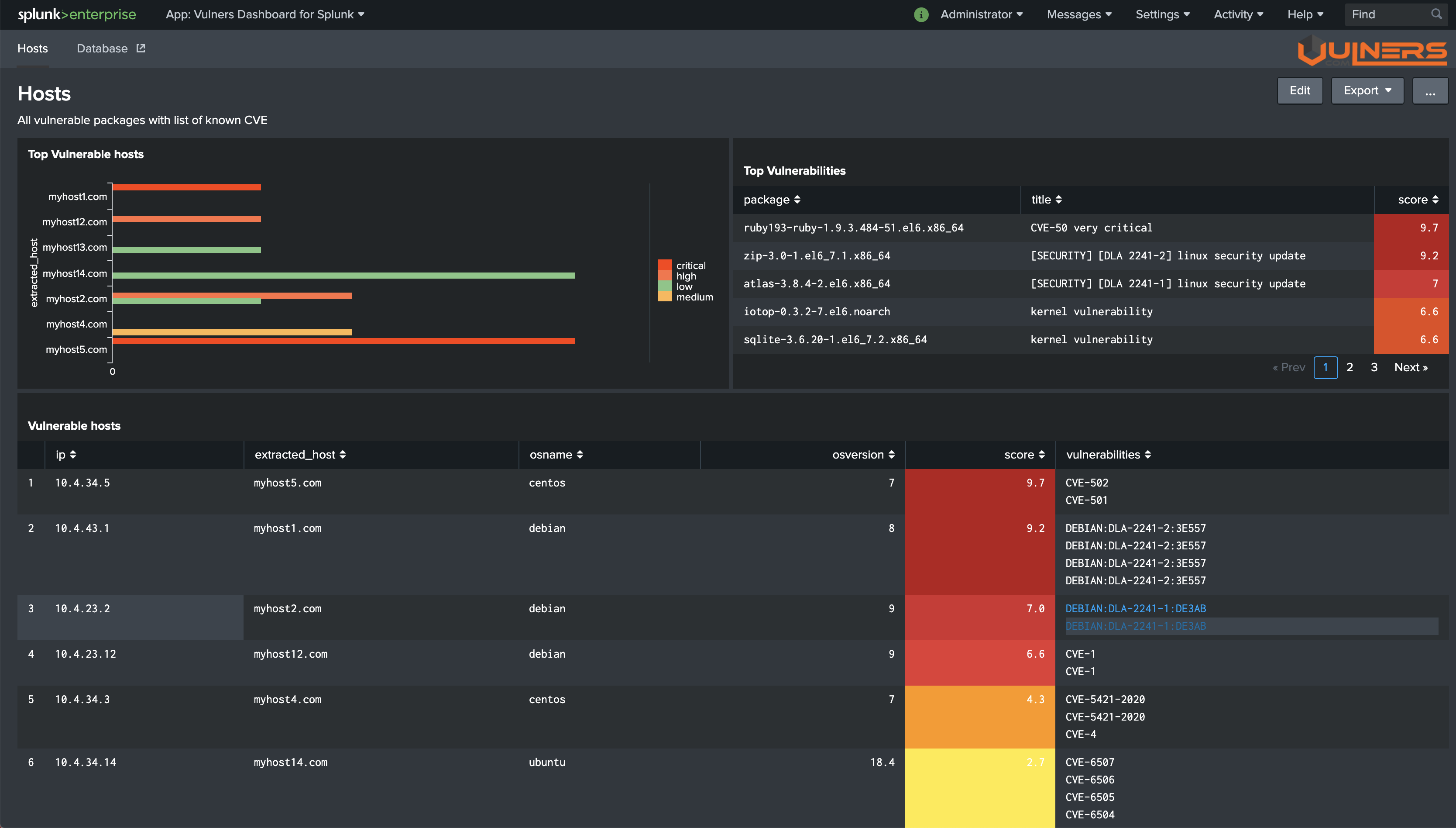
Seach for packages collected by forwarder¶
By default, the forwarder sends information about packages hourly or right after restart. To see collected packages run search
index=vulners
Run Vulners audit¶
Vulners application runs audit script automatically at 9 o'clock in the morning. Alternatively, you can select saved search
| savedsearch vulners_report
Using slim¶
NB: The process of DU creation has been tested and should work without issues. However no tests have been conducted regarding the use of the deployment server. Any feedback on that would be appreciated.
- Install slim as in the instructions (take note of this bug though)
- Create a package
slim package -o result/ ./vulners-lookup/ - Partition the package into deployment units
slim partition -o deployment-units/ vulners-lookup-0.0.3.tar.gz - Use your deployment server for installation