Nmap plugin and http-vulners-regex¶
This guide explains how to use the Nmap plugin and the http-vulners-regex script to improve your vulnerability scanning capabilities by leveraging the power of Nmap with the Vulners database.
Nmap plugin¶
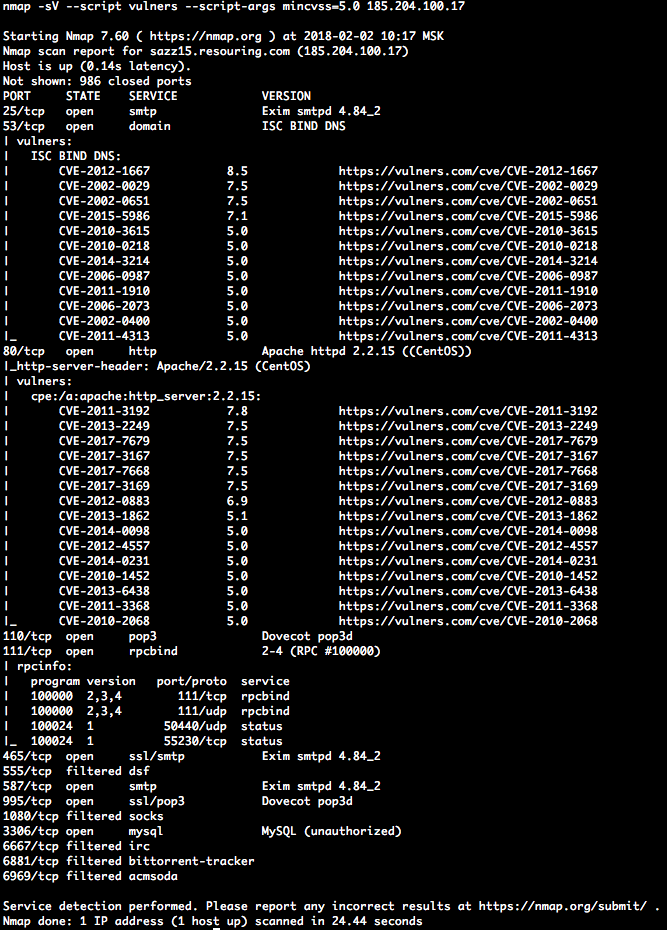
The Nmap Scripting Engine (NSE) script uses known service information to identify potential vulnerabilities. It is part of the standard Nmap NSE library.
Dependencies¶
- Nmap Libraries Required:
- http
- json
-
string
-
Additional Dependency:
- http-vulners-regex
Note
The script primarily operates with the -sV flag to detect software versions. However, it can run without the -sV flag if used alongside the http-vulners-regex script.
Installation¶
-
Locate Nmap Script Directory:
-
Unix/Linux:
~/.nmap/scripts/or$NMAPDIR - Mac:
/usr/local/Cellar/nmap/<version>/share/nmap/scripts/ -
Windows:
C:\Program Files (x86)\nmap\scripts -
Copy Script: Place
vulners.nseinto the directory. - Update Script Database: Execute
nmap --script-updatedb.
Usage¶
To conduct a scan, execute the following command, adjusting parameters as needed:
nmap -sV --script vulners [--script-args mincvss=<arg_val>] <target>
http-vulners-regex¶
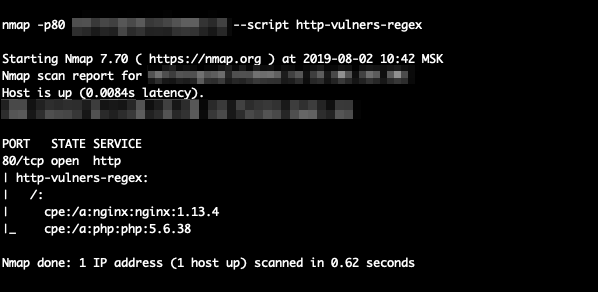
This script improves the efficiency of the main vulners script by scanning HTTP responses and identifying CPEs of the mentioned software, which enhances the performance of the Nmap plugin.
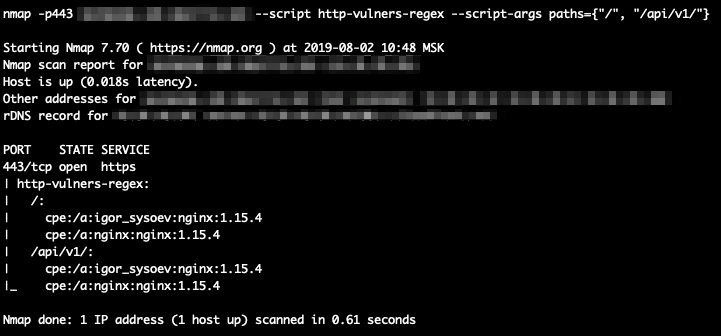
With paths:
Dependencies¶
- Nmap Libraries Required:
- http
- json
- string
- stdnse
- shortport
- table
Installation¶
-
Locate Nmap Script Directory:
-
Unix/Linux:
~/.nmap/or$NMAPDIR - Mac:
/usr/local/Cellar/nmap/<version>/share/nmap/ -
Windows:
C:\Program Files (x86)\nmap\ -
Copy Script and Data:
Place
http-vulners-regex.nsein<nmap_dir>/scripts/. Move the provided JSON with regexes to<nmap_dir>/nselib/data/. Transfer the default paths txt file to<nmap_dir>/nselib/data/, or specify your file via command-line arguments. -
Update Script Database: Run
nmap --script-updatedb.
Usage¶
Execute as a standard NSE script, adjusting the paths argument as necessary:
nmap --script http-vulners-regex.nse [--script-args paths={"/"}] <target>