
Trellix Global Defenders: Defending against Cyber Espionage Campaigns – Operation Graphite
8.4 High
AI Score
Confidence
Low

Trellix Global Defenders: Defending against Cyber Espionage Campaigns – Operation Graphite
By Ben Marandel, Arnab Roy · June 20, 2022
Cyber Espionage campaigns by nature are targeted attacks that can go undetected for prolonged periods of time. Cyber Espionage campaigns often involve adversaries with clear objectives with capabilities to avoid defenses and leverage trusted enterprise IT systems or operational weaknesses within organisations. Some of the key targets for espionage campaigns are as follows:
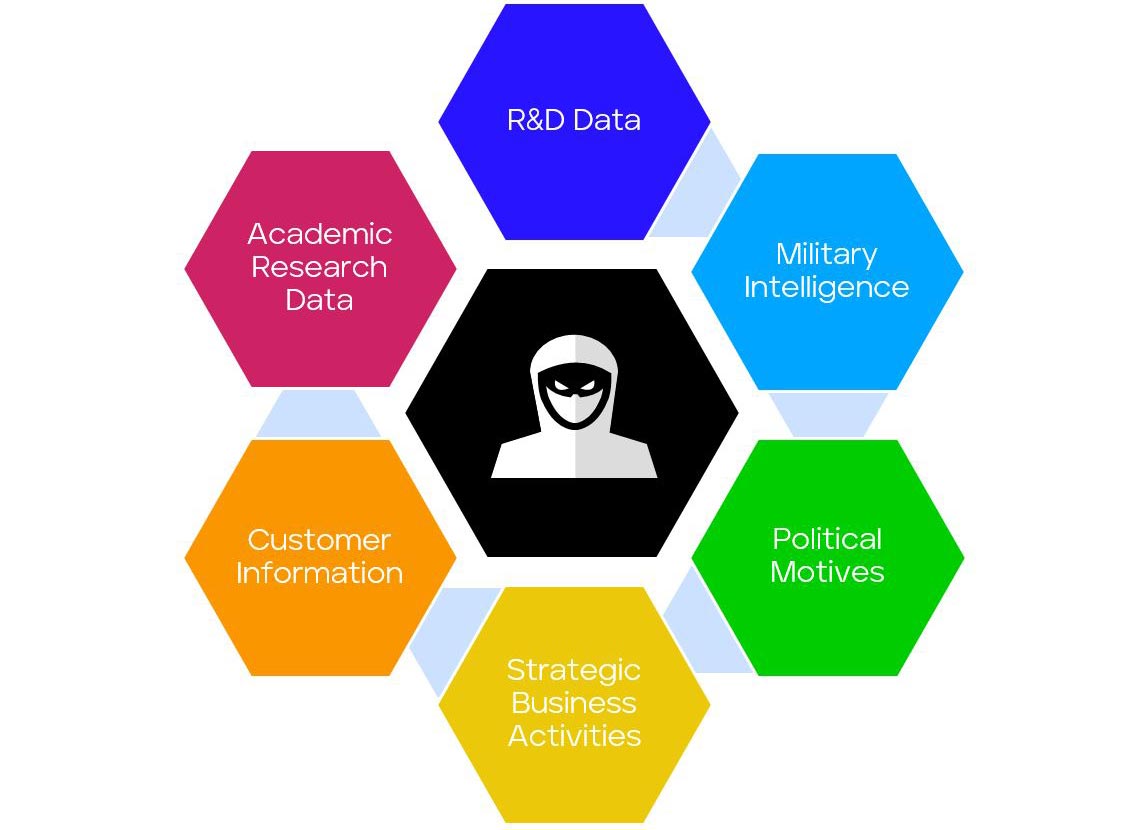 Figure 1: Cyber Espionage Key Targets
Figure 1: Cyber Espionage Key Targets
The ultimate goal of most cyber espionage campaigns are data exfiltration and wide spread reconasaince.
Operation graphite introduction
Trellix Advanced Threat Research team released threat research on the 25th of January 2022 which highlighted discovery of a new espionage campaign targeting high-ranking government officials Western Asia and Eastern Europe. The attack is believed to have been triggered via targeted phishing with malicious macro enabled word document used to establish the initial access. Once executed the malicious document leveraged a vulnerability in Excel (CVE2021-40444) which allows remote code execution on the impacted endpoint. Similar to other espionage campaigns their was hands on recon of the targeted organization, specifically looking for documents with specific keywords of interest. This was followed by multi-stage attack which included lateral movement to other systems of interest such as domain controllers and file servers. The following figure shows the attack progression:
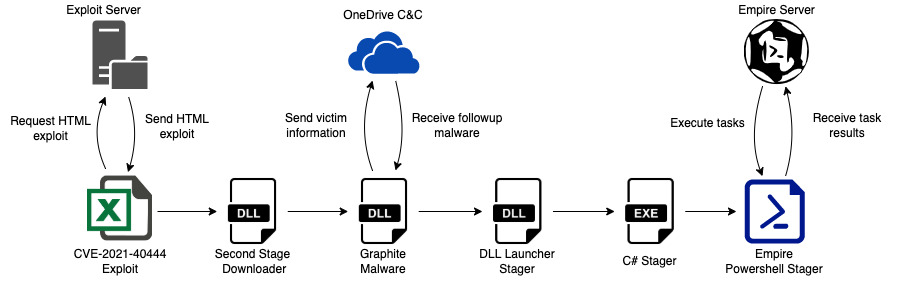 Figure 2: Attack Chain
Figure 2: Attack Chain
Like most multi-stage attacks a combination of exploitation techniques are observed such as use of LolBas/LolBins like Powershell and exploitation of enterprise architecture and system vulnerabilities.
During our analysis of the overall flow of the attack and the related payloads the following attributes of the attack stood out that could be critical at detecting/preventing this threat:
- Use of OneDrive as a command a control server as well as for storing payload configuration and staging. Their is evidence that the OneDrive Implant module of the empire framework was used by the threat actor which has been documented by the empire framework maintainers. This was used specifically to subvert network security controls and hide traffic inside legitimate applications.
- Use of embedded XLS into XLSX to bypass macro execution protection added in Office Excel. The XLS file is used as a secondary payload which is exploiting the CVE-2021-40444, this is not the first file to be open by the victim. To maximize the chances of execution of the exploitable XLS document the attacker uses dynamic loading of the office ribbon and custom options in the office toolbar by using a XLSM file, this XLSM file then dynamically loads the XLS file which triggers the execution of CVE-2021-40444.
Based on the observed TTP’s and operational similarity Trellix Threat research team was moderately confident that this attack could be attributed to APT 28.
Defensive architecture guidance
The question is how do we protect ourselves from such attacks? At the heart of the answer is building an effective threat model for cyber espionage campaigns and then driving your defensive strategy based on “think red - act blue mindset” where the threat informed layered defensive strategy drives how the security controls are configured to provide a resilient defensive architecture. Below is how the Trellix XDR solution architecture protects and detects this attack.
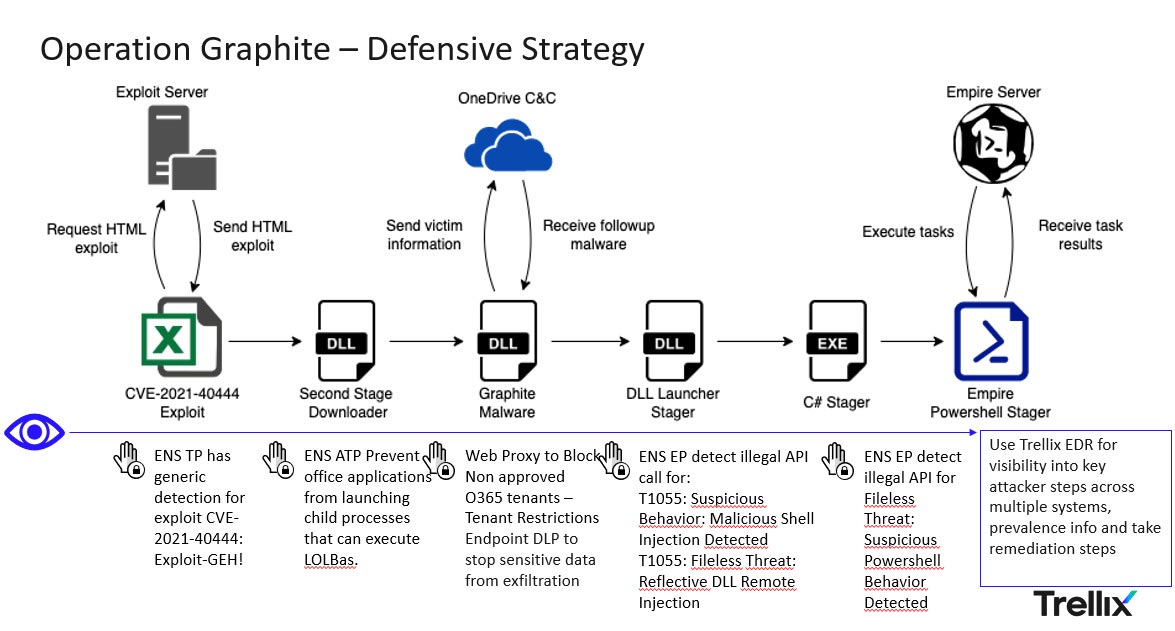 Figure 3: Trellix Solution Architecture
Figure 3: Trellix Solution Architecture
Organizations can build an effective threat model based on adversary characteristics some of which is very well documented within the MITRE ATT&CK framework. Leveraging tools like MITRE ATT&CK navigator is one of the methods where you can combine multiple threat actor TTP’s and create an effective threat model for your SOC, an example below for TTP’s used by APT 28:
Common techniques used for Cyber Espionage - using ATT&CK
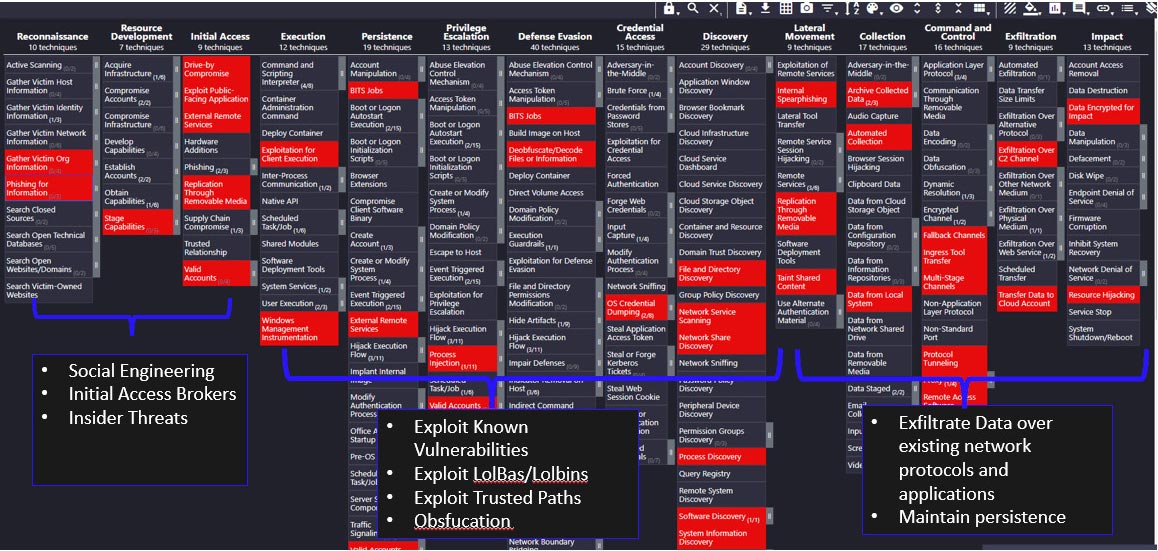 Figure 4: MITRE ATT&CK Navigator for APT28
Figure 4: MITRE ATT&CK Navigator for APT28
However, for customers who have Trellix Insights this process is even simpler: By filtering the Profiles to APT28, you will get a complete overview of the APT28 Group activities. As an introduction the tool will give you a short description of the group and their current targeted countries / sectors.
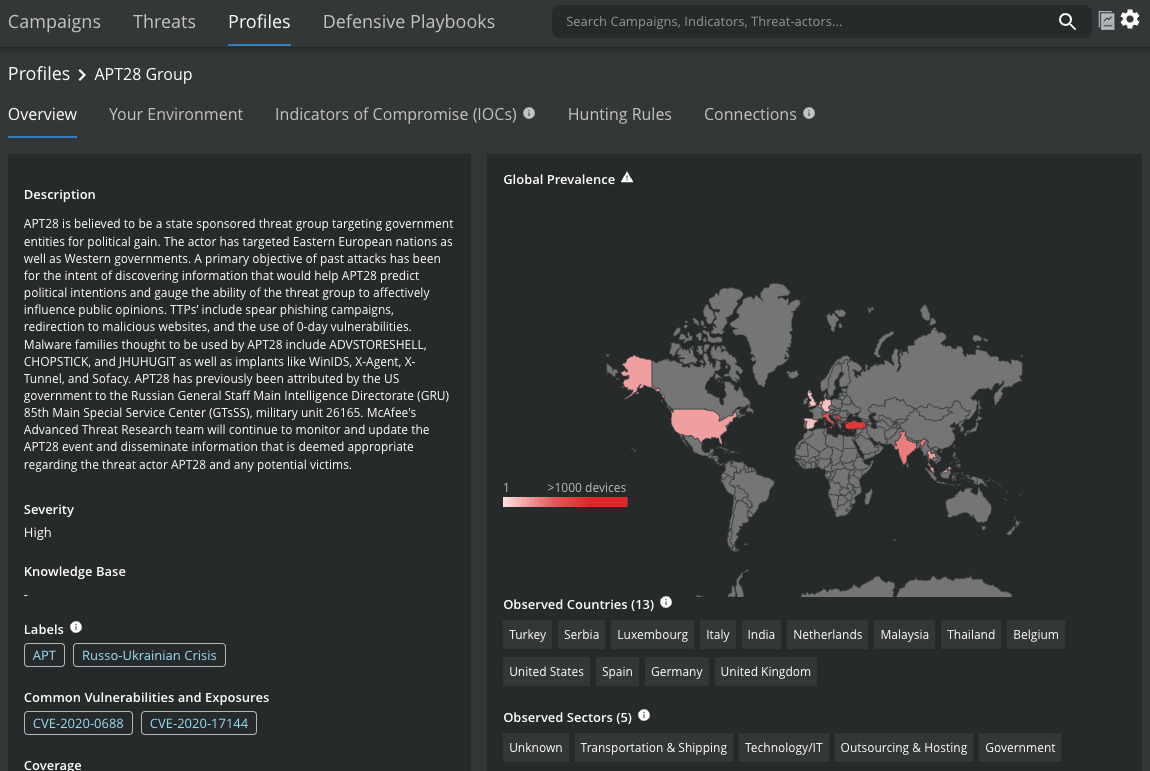 Figure 5: APT28 Group Overview from MVISION Insights
Figure 5: APT28 Group Overview from MVISION Insights
Just after this introduction, you will get overview of the 42+ campaign currently observed by the Trellix Labs. This view also indicates which endpoints within your organization may have insufficient coverage to protect themselves. By clicking on the name of the campaign, you will pivot to the full details of the selected campaign.
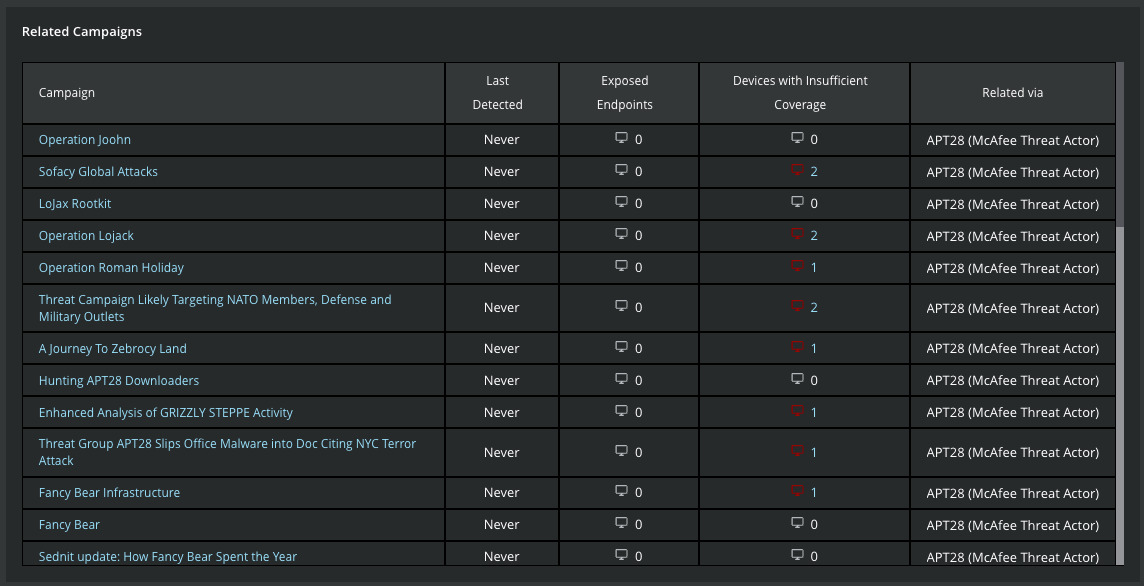 Figure 6: Examples of APT28 related campaigns from MVISION Insights
Figure 6: Examples of APT28 related campaigns from MVISION Insights
The third section of the interface, describes the MITRE Techniques of Tools used by APT28 group. Once C2 communications is established, researchers established the use of “Files and Directory Discovery – T1083” technique for Discovery and “Data Transfer Size Limits – T1030” technique for Exfiltration.
This group also uses tools such as Mimikatz to simplify Credential Access via LSASS Memory – T1003.001, Certutil to download third-party tools or X-Tunnel for Exfiltration over Asymmetric Encrypted Non-C2 Protocols – T1048.002.
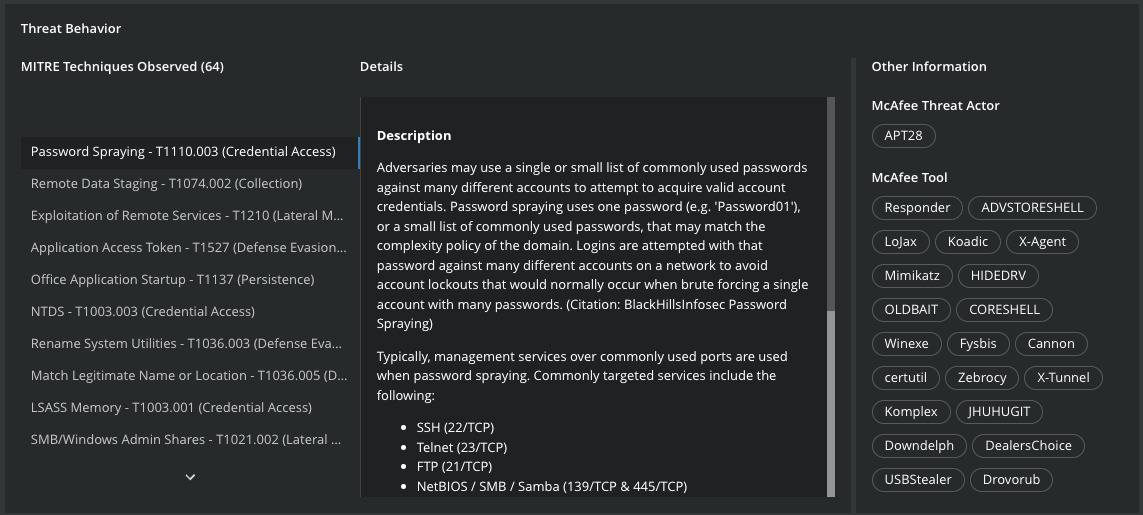 Figure 7: MITRE Techniques used by the APT28 Group from MVISION Insights
Figure 7: MITRE Techniques used by the APT28 Group from MVISION Insights
And finally, based on all those information, the interface builds for you the powerful ATT&CK Matrix with a clear representation of the observed techniques.
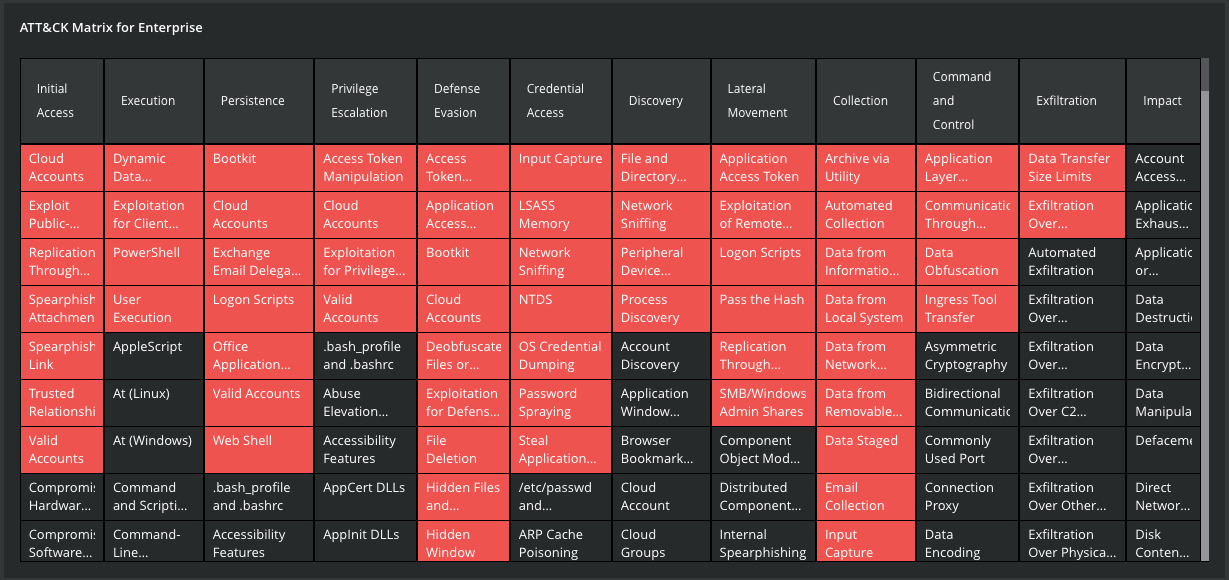 Figure 8: APT28 Group MITRE ATT&CK matrix from MVISION Insights
Figure 8: APT28 Group MITRE ATT&CK matrix from MVISION Insights
Endpoint Protection Actions: Trellix Endpoint uses exploit prevention to block execution of CVE-2021-40444 as well as use behavioral threat protection via Adaptive Threat Prevention module. Specifically, Advanced Behavior Blocking (ABB) rules stop the execution of child processes from office processes thus breaking the kill chain early in the attack lifecycle. The following rules in Trellix ENS Exploit Prevention and Adaptive Threat Protection (ATP) are recommended to observe or block behavioral activity associated with exploitation techniques.
ENS Exploit Prevention Signature 6163: T1055: Suspicious Behavior: Malicious Shell Injection Detected
ENS Exploit Prevention Signature 6115: T1055: Fileless Threat: Reflective DLL Remote Injection
ENS ATP Rule 300: T1566: Prevent office applications from launching child processes that can execute script commands
To complement protection capabilities, Trellix EDR solution detects and visualizes the attack chain, as illustrated bellow at the “Initial Access” when the victim is opening for the first time the specifically crafted XLSX file.
In this screenshot of a demo sample illustrating Office Excel, you can observe the download of the XLS file natively through an HTTPS connection, after it has opened the XLSX file.
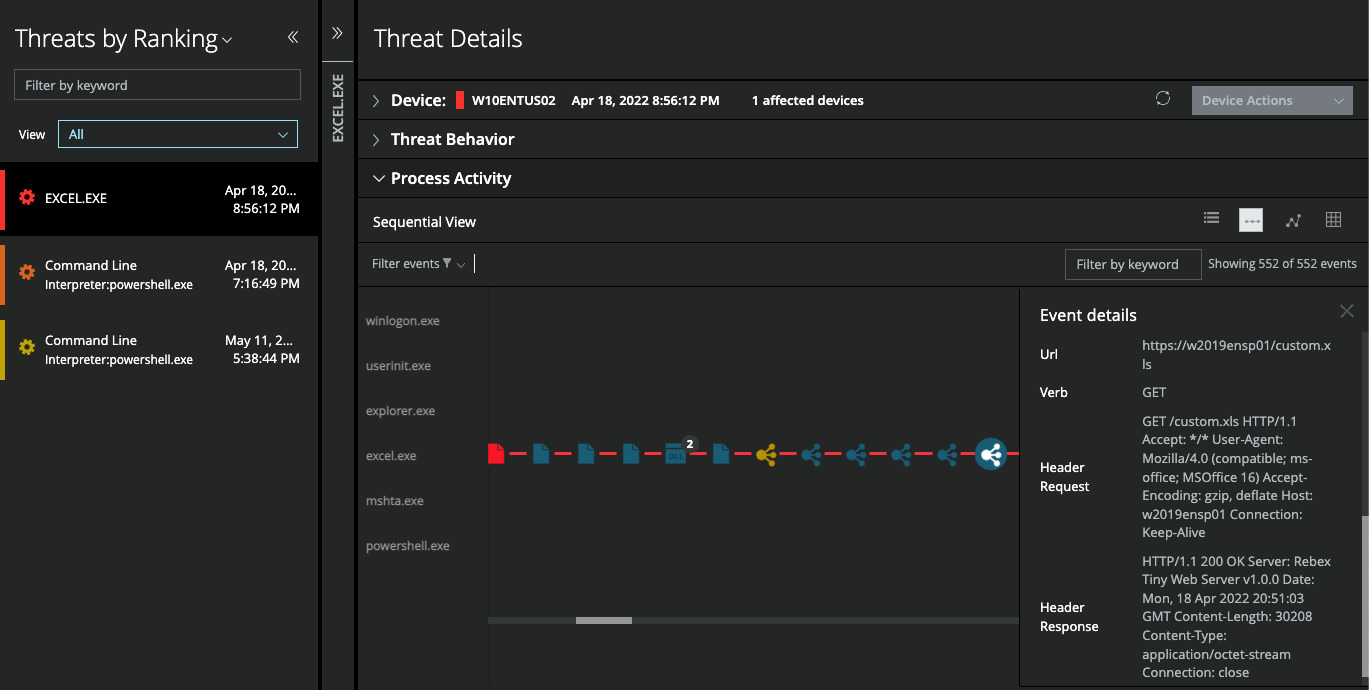 Figure 9: Excel.exe opening an XLSX file and then downloading an XLS file, captured by MVISION EDR
Figure 9: Excel.exe opening an XLSX file and then downloading an XLS file, captured by MVISION EDR
Preventing Data Exfiltration: Preventing the attempts to exfiltrate data can defeat this type of attack at an early stage. The threat actor uses two key techniques for data exfiltration: exfiltration over existing network protocols and endpoint data reconnaissance techniques. The exfiltration over the existing network protocol leverages the Microsoft Graph API utilized by O365 suite of apps to communicate between various O365 services. The graph API has been a target of previous APT campaigns as it provides a unique insight into existing enterprise data sitting inside O365. One of the key ways this attack can be completely defeated is by ensuring users cannot login to non-sanctioned O365 tenants. This is possible by leveraging a URL content proxy that inspects the O365 instance id in the login URL of the tenant and subsequent communication. The proxy can be configured to only allow the organizational tenant id of the enterprise O365 instance and not that of other O365 tenants. This will prevent the threat actor from succeeding in establishing the initial command and control connection as well as data exfiltration. Deploying endpoint DLP is the second critical factor in preventing the data exfiltration of sensitive information leaving organizational perimeter. This includes getting visibility into endpoint processes accessing sensitive/tagged data.
Bringing Visibility into the SOC with XDR: Detecting multi-vector telemetry requires context and correlation across multiple data sources so that the right alerts and telemetry is presented to the SOC analyst for effective triage, scoping of the threat and effective incident response.
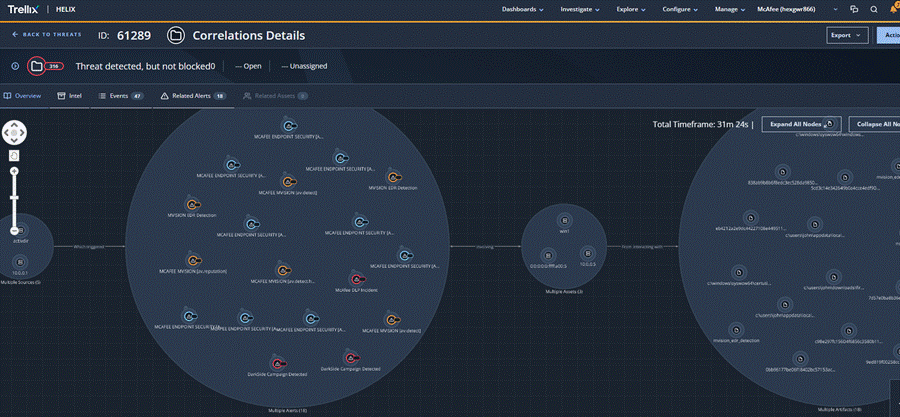 Figure 10: Example XDR Correlation with multi-vector sensor telemetry from Threat Intelligence, Endpoint, DLP
Figure 10: Example XDR Correlation with multi-vector sensor telemetry from Threat Intelligence, Endpoint, DLP
Integrated sandbox for malware analysis: As part of the Trellix solution architecture, the endpoints are capable of sending files dynamically or through integrated SOAR workflows to the Trellix Detection on Demand Cloud Sandbox. A quick analysis of the XLSX document reveals that pseudo data was used entice the end user into opening the document.
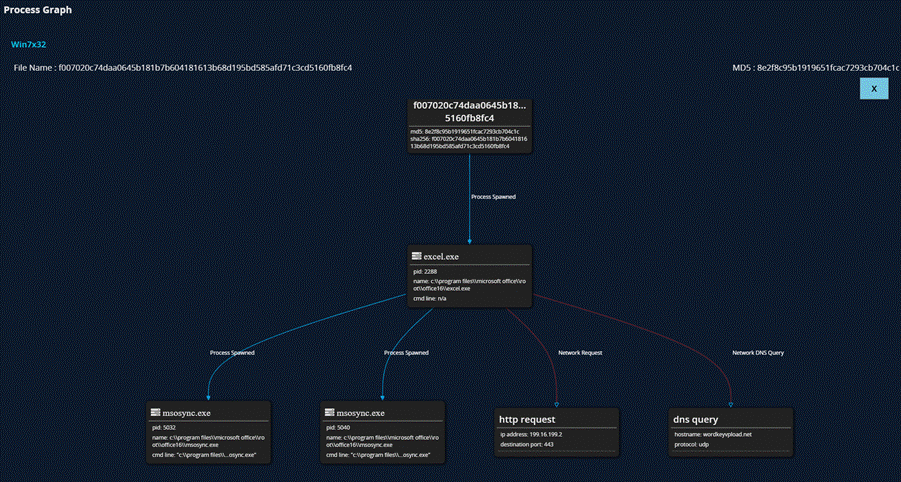 Figure 11: Trellix DOD Analysis
Figure 11: Trellix DOD Analysis
Summary
Defeating a multi-stage cyberespionage campaign requires a multipronged defensive strategy that starts by building an effective threat model leading to prioritization and deployment of highest impact preventive controls which leads to a security model that stalls the attackers progress and delivering enterprise resilience to cyberespionage campaigns. Some of the key steps in building such resilience is as follows:
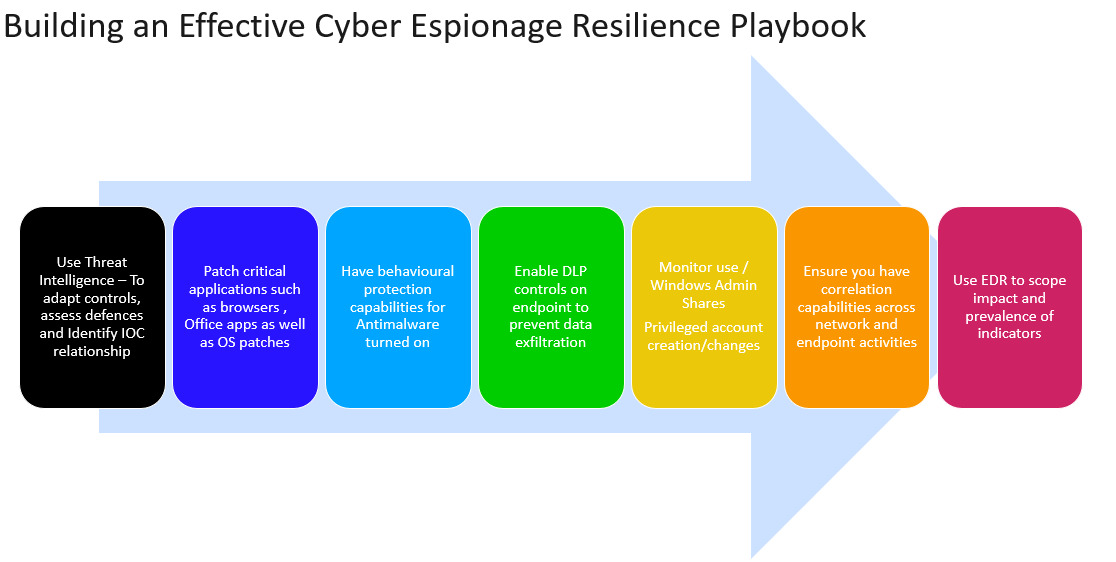 Figure 12: Cyber Espionage Playbook
Figure 12: Cyber Espionage Playbook
For additional details and understanding, you can view our Threat Center webinar with Trellix Solution Architects explaining how we defend against this attack here.