
Qualys Response to CISA Alert: Binding Operational Directive 22-01
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
Start your VMDR 30-day, no-cost trial today
Overview
On November 3, 2021, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released a Binding Operational Directive 22-01, "Reducing the Significant Risk of Known Exploited Vulnerabilities." This directive recommends urgent and prioritized remediation of the vulnerabilities that adversaries are actively exploiting. It establishes a CISA-managed catalog of known exploited vulnerabilities that carry significant risk to the federal government and establishes requirements for agencies to remediate these vulnerabilities.
This directive requires agencies to review and update agency internal vulnerability management procedures within 60 days according to this directive and remediate each vulnerability according to the timelines outlined in 'CISA's vulnerability catalog.
Qualys helps customers to identify and assess risk to organizations' digital infrastructure and automate remediation. Qualys' guidance for rapid response to Operational Directive is below.
Directive Scope
This directive applies to all software and hardware found on federal information systems managed on agency premises or hosted by third parties on an agency's behalf.
However, CISA strongly recommends that private businesses and state, local, tribal, and territorial (SLTT) governments prioritize the mitigation of vulnerabilities listed in CISA's public catalog.
CISA Catalog of Known Exploited Vulnerabilities
In total, CISA posted a list of 291 Common Vulnerabilities and Exposures (CVEs) that pose the highest risk to federal agencies. The Qualys Research team has mapped all these CVEs to applicable QIDs. You can view the complete list of CVEs and the corresponding QIDs here.
Not all vulnerabilities are created equal
Our quick review of the 291 CVEs posted by CISA suggests that not all vulnerabilities hold the same priority. CISA has ordered U.S. federal enterprises to apply patches as soon as possible. The remediation guidance can be grouped into three distinct categories:
Category 1 – Past Due
Remediation of 15 CVEs (~5%) are already past due. These vulnerabilities include some of the most significant exploits in the recent past, including PrintNightmare, SigRed, ZeroLogon, and vulnerabilities in CryptoAPI, Pulse Secure, and more. Qualys Patch Management can help you remediate most of these vulnerabilities.
Category 2 – Patch in less than two weeks
100 (34%) Vulnerabilities need to be patched in the next two weeks, or by November 17, 2022.
Category 3 – Patch within six months
The remaining 176 vulnerabilities (60%) must be patched within the next six months or by May 3, 2022.
Detect CISA's Vulnerabilities Using Qualys VMDR
The Qualys Research team has released several remote and authenticated detections (QIDs) for the vulnerabilities. Since the directive includes 291 CVEs, we recommend executing your search based on vulnerability criticality, release date, or other categories.
For example, to detect critical CVEs released in 2021:
vulnerabilities.vulnerability.criticality:CRITICAL and vulnerabilities.vulnerability.cveIds:[ CVE-2021-1497,CVE-2021-1498,CVE-2021-1647,CVE-2021-1675,CVE-2021-1732,CVE-2021-1782,CVE-2021-1870,CVE-2021-1871,CVE-2021-1879,CVE-2021-1905,CVE-2021-1906,CVE-2021-20016,CVE-2021-21017,CVE-2021-21148,CVE-2021-21166,CVE-2021-21193,CVE-2021-21206,CVE-2021-21220,CVE-2021-21224,CVE-2021-21972,CVE-2021-21985,CVE-2021-22005,CVE-2021-22205,CVE-2021-22502,CVE-2021-22893,CVE-2021-22894,CVE-2021-22899,CVE-2021-22900,CVE-2021-22986,CVE-2021-26084,CVE-2021-26411,CVE-2021-26855,CVE-2021-26857,CVE-2021-26858,CVE-2021-27059,CVE-2021-27065,CVE-2021-27085,CVE-2021-27101,CVE-2021-27102,CVE-2021-27103,CVE-2021-27104,CVE-2021-28310,CVE-2021-28550,CVE-2021-28663,CVE-2021-28664,CVE-2021-30116,CVE-2021-30551,CVE-2021-30554,CVE-2021-30563,CVE-2021-30632,CVE-2021-30633,CVE-2021-30657,CVE-2021-30661,CVE-2021-30663,CVE-2021-30665,CVE-2021-30666,CVE-2021-30713,CVE-2021-30761,CVE-2021-30762,CVE-2021-30807,CVE-2021-30858,CVE-2021-30860,CVE-2021-30860,CVE-2021-30869,CVE-2021-31199,CVE-2021-31201,CVE-2021-31207,CVE-2021-31955,CVE-2021-31956,CVE-2021-31979,CVE-2021-33739,CVE-2021-33742,CVE-2021-33771,CVE-2021-34448,CVE-2021-34473,CVE-2021-34523,CVE-2021-34527,CVE-2021-35211,CVE-2021-36741,CVE-2021-36742,CVE-2021-36942,CVE-2021-36948,CVE-2021-36955,CVE-2021-37973,CVE-2021-37975,CVE-2021-37976,CVE-2021-38000,CVE-2021-38003,CVE-2021-38645,CVE-2021-38647,CVE-2021-38647,CVE-2021-38648,CVE-2021-38649,CVE-2021-40444,CVE-2021-40539,CVE-2021-41773,CVE-2021-42013,CVE-2021-42258 ]
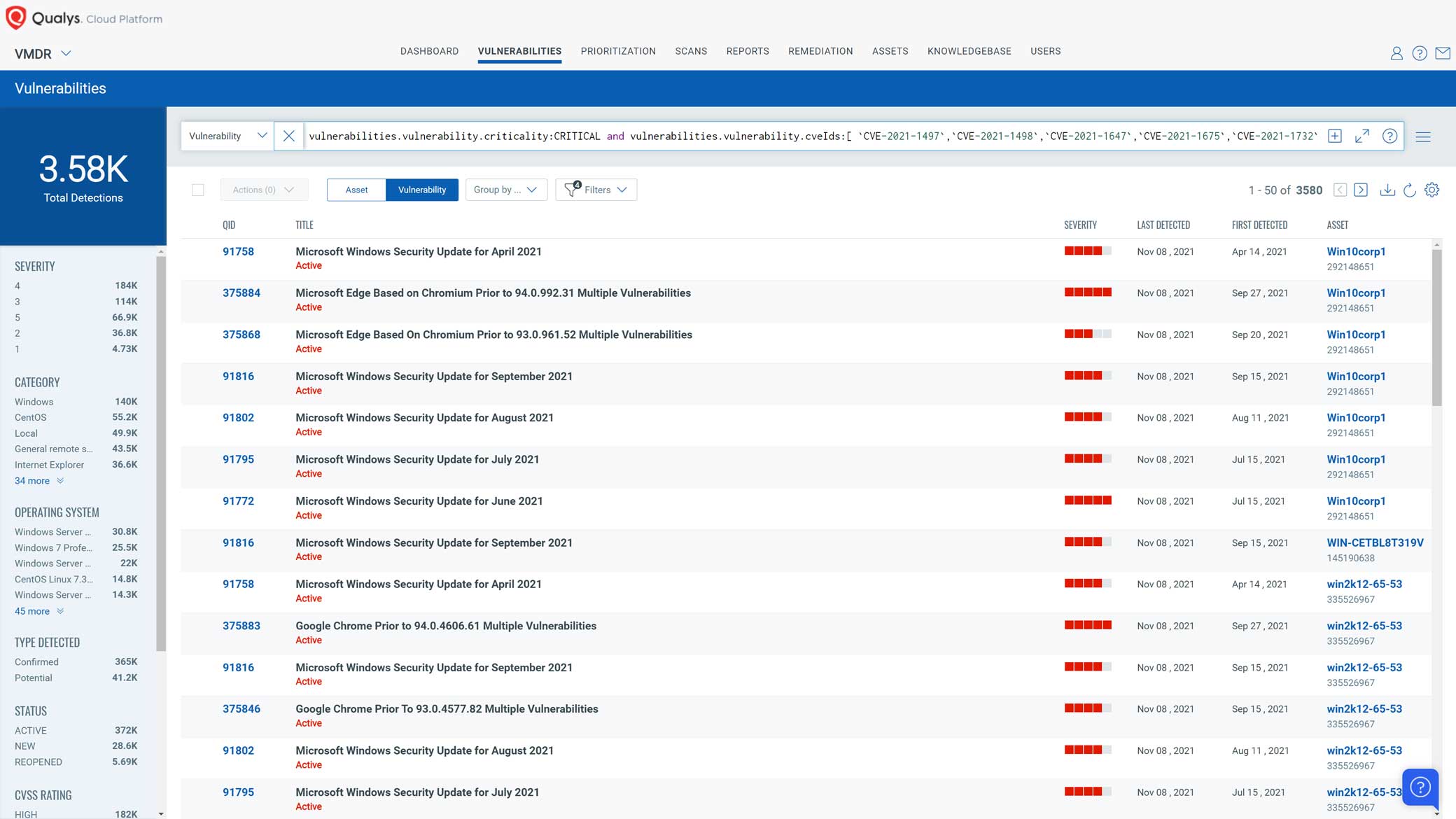
Using Qualys VMDR, you can effectively prioritize those vulnerabilities using the VMDR Prioritization report.
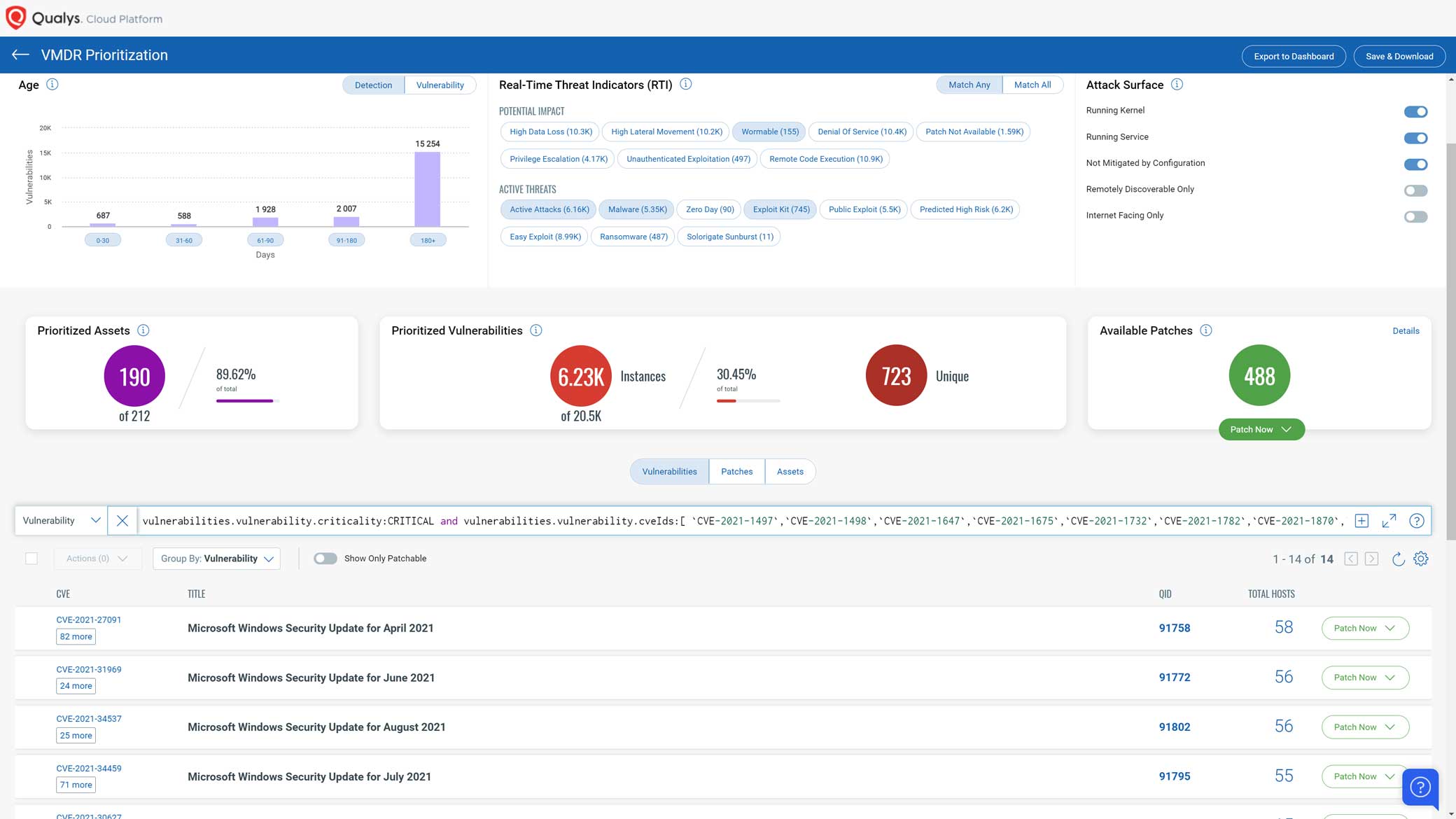
In addition, you can locate a vulnerable host through Qualys Threat Protection by simply clicking on the impacted hosts to effectively identify and track this vulnerability.
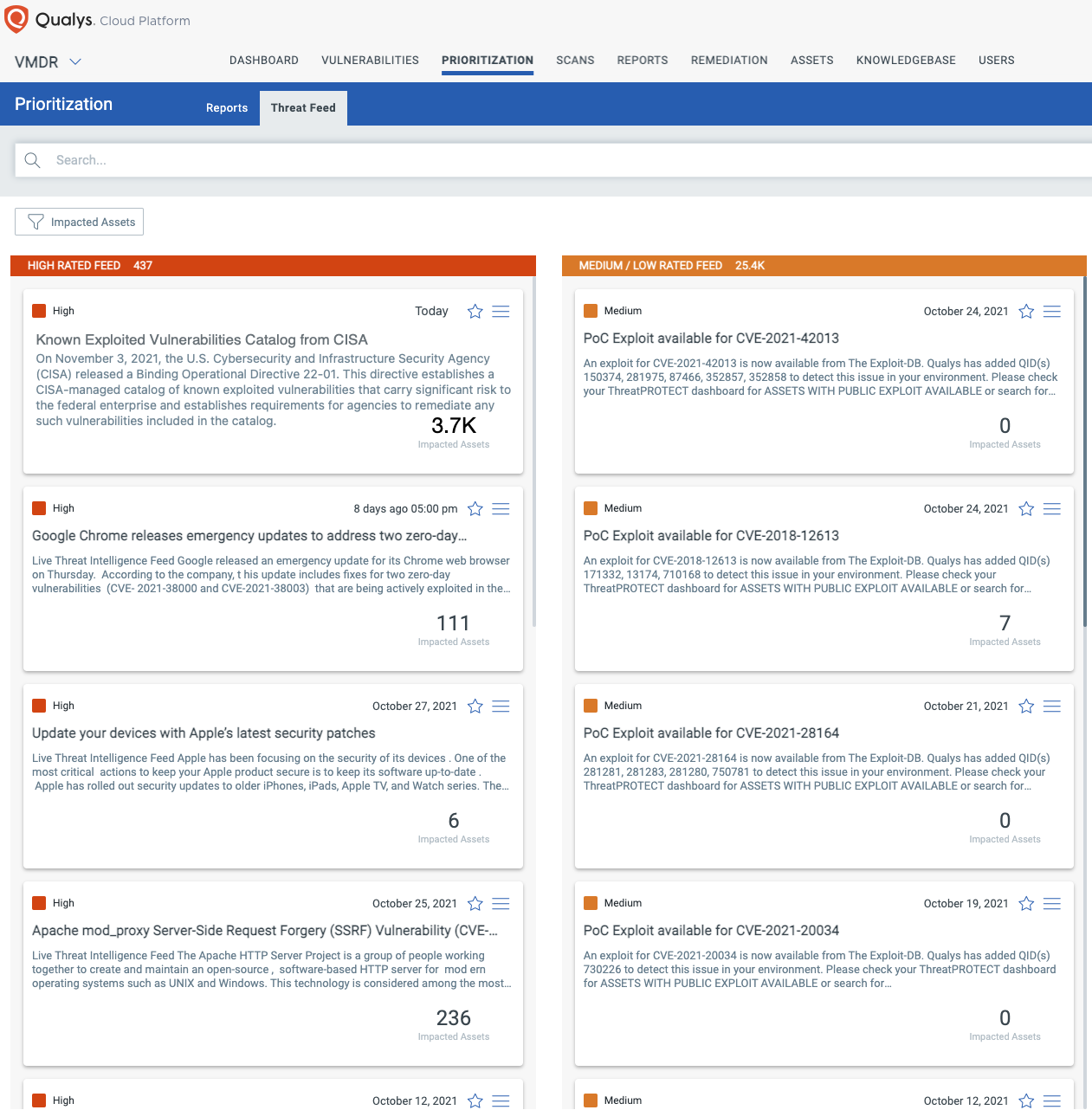
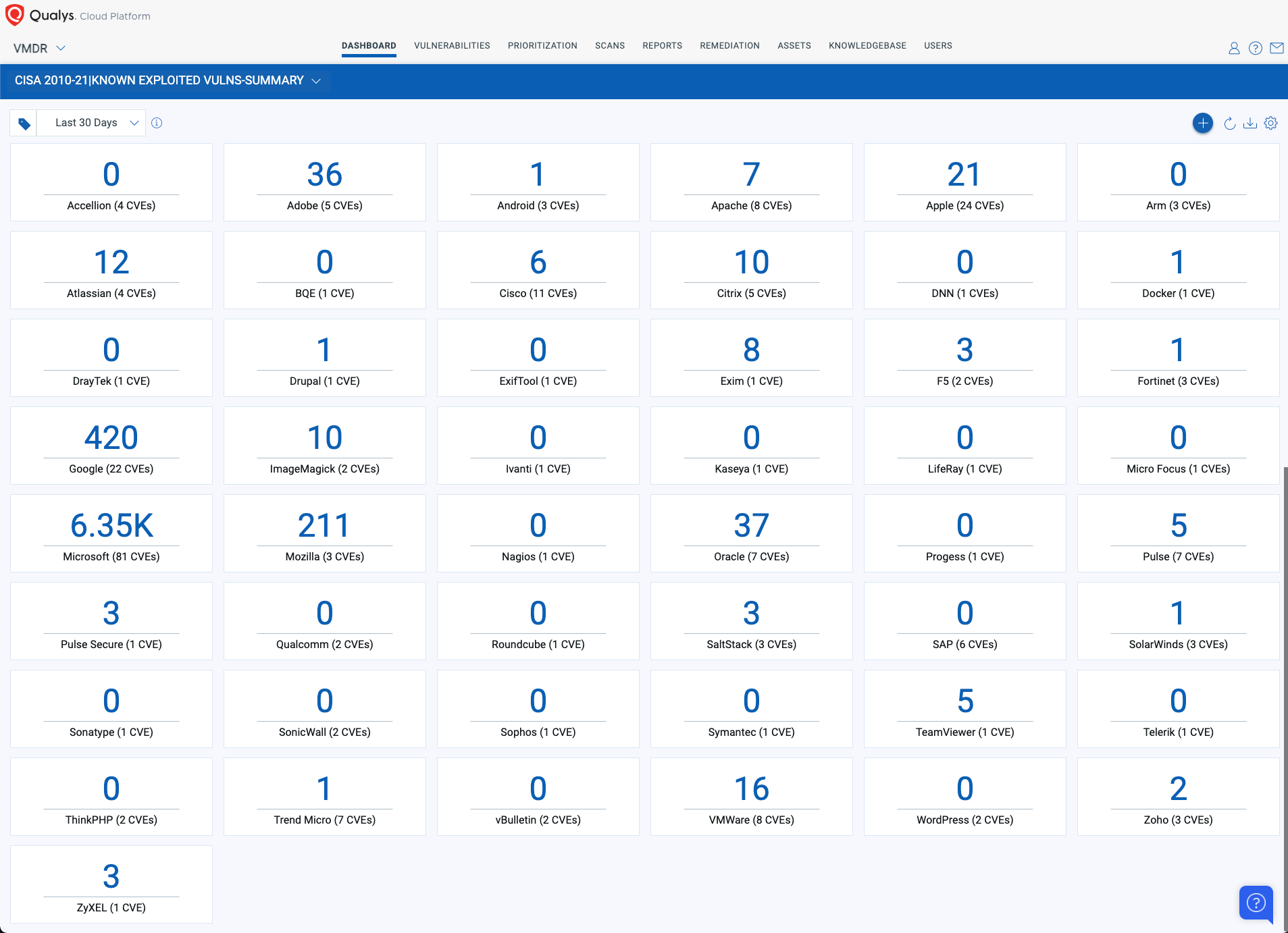
With Qualys Unified Dashboard, you can track your exposure to the CISA Known Exploited Vulnerabilities and gather your status and overall management in real-time. With trending enabled for dashboard widgets, you can keep track of the status of the vulnerabilities in your environment using the "CISA 2010-21| KNOWN EXPLOITED VULNERABILITIES" Dashboard.
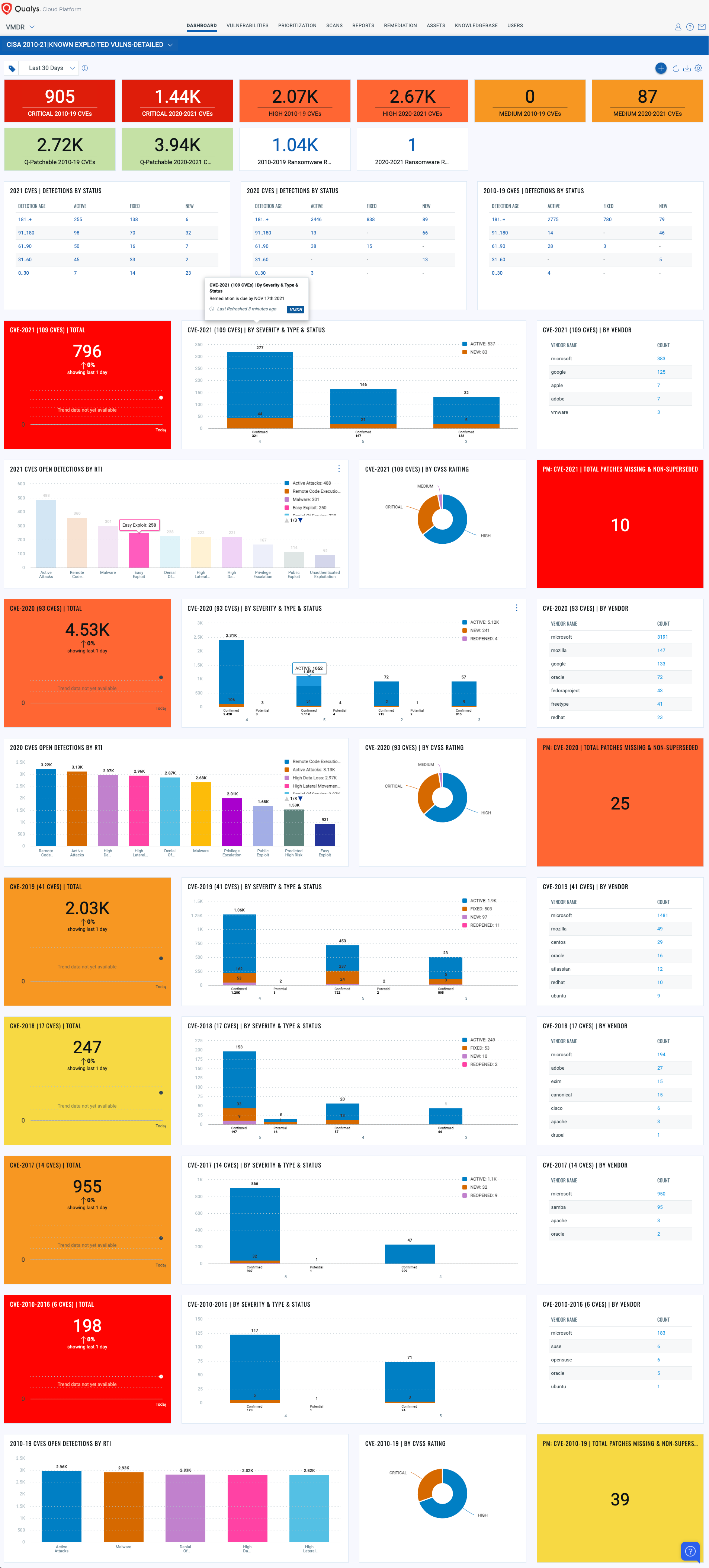
Detailed Operational Dashboard:
Summary Dashboard High Level Structured by Vendor:
Remediation
To comply with this directive, federal agencies must remediate most "Category 2" vulnerabilities by November 17, 2021, and "Category 3" by May 3, 2021. Qualys Patch Management can help streamline the remediation of many of these vulnerabilities.
Customers can copy the following query into the Patch Management app to help customers comply with the directive's aggressive remediation date of November 17, 2021. Running this query will find all required patches and allow quick and efficient deployment of those missing patches to all assets directly from within the Qualys Cloud Platform.
cve:[CVE-2021-1497,CVE-2021-1498,CVE-2021-1647,CVE-2021-1675,CVE-2021-1732,CVE-2021-1782,CVE-2021-1870,CVE-2021-1871,CVE-2021-1879,CVE-2021-1905,CVE-2021-1906,CVE-2021-20016,CVE-2021-21017,CVE-2021-21148,CVE-2021-21166,CVE-2021-21193,CVE-2021-21206,CVE-2021-21220,CVE-2021-21224,CVE-2021-21972,CVE-2021-21985,CVE-2021-22005,CVE-2021-22205,CVE-2021-22502,CVE-2021-22893,CVE-2021-22894,CVE-2021-22899,CVE-2021-22900,CVE-2021-22986,CVE-2021-26084,CVE-2021-26411,CVE-2021-26855,CVE-2021-26857,CVE-2021-26858,CVE-2021-27059,CVE-2021-27065,CVE-2021-27085,CVE-2021-27101,CVE-2021-27102,CVE-2021-27103,CVE-2021-27104,CVE-2021-28310,CVE-2021-28550,CVE-2021-28663,CVE-2021-28664,CVE-2021-30116,CVE-2021-30551,CVE-2021-30554,CVE-2021-30563,CVE-2021-30632,CVE-2021-30633,CVE-2021-30657,CVE-2021-30661,CVE-2021-30663,CVE-2021-30665,CVE-2021-30666,CVE-2021-30713,CVE-2021-30761,CVE-2021-30762,CVE-2021-30807,CVE-2021-30858,CVE-2021-30860,CVE-2021-30860,CVE-2021-30869,CVE-2021-31199,CVE-2021-31201,CVE-2021-31207,CVE-2021-31955,CVE-2021-31956,CVE-2021-31979,CVE-2021-33739,CVE-2021-33742,CVE-2021-33771,CVE-2021-34448,CVE-2021-34473,CVE-2021-34523,CVE-2021-34527,CVE-2021-35211,CVE-2021-36741,CVE-2021-36742,CVE-2021-36942,CVE-2021-36948,CVE-2021-36955,CVE-2021-37973,CVE-2021-37975,CVE-2021-37976,CVE-2021-38000,CVE-2021-38003,CVE-2021-38645,CVE-2021-38647,CVE-2021-38647,CVE-2021-38648,CVE-2021-38649,CVE-2021-40444,CVE-2021-40539,CVE-2021-41773,CVE-2021-42013,CVE-2021-42258 ]
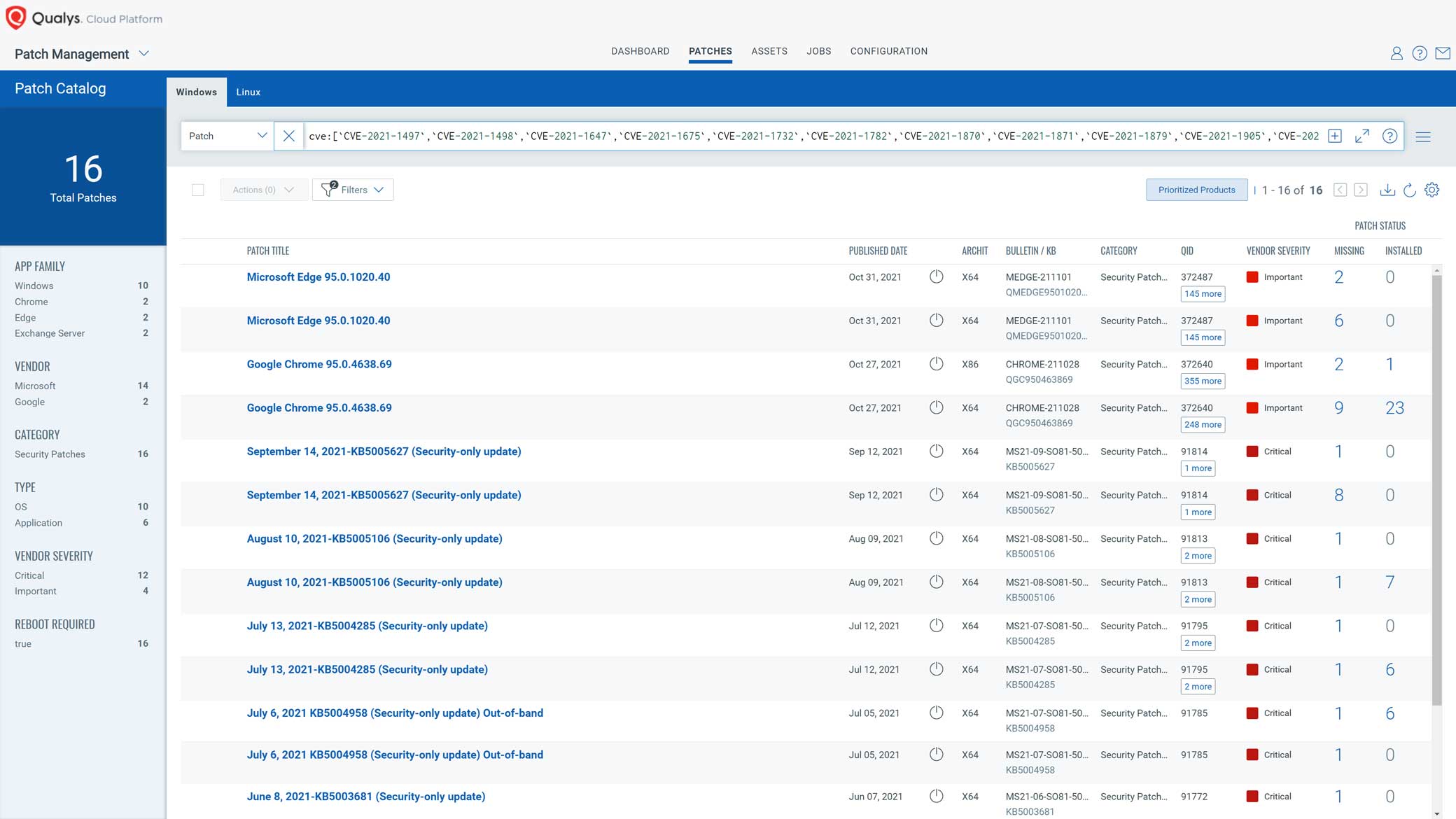
Qualys patch content covers many Microsoft, Linux, and third-party applications; however, some of the vulnerabilities introduced by CISA are not currently supported out-of-the-box by Qualys. To remediate those vulnerabilities, Qualys provides the ability to deploy custom patches. The flexibility to customize patch deployment allows customers to patch the remaining CVEs in this list.
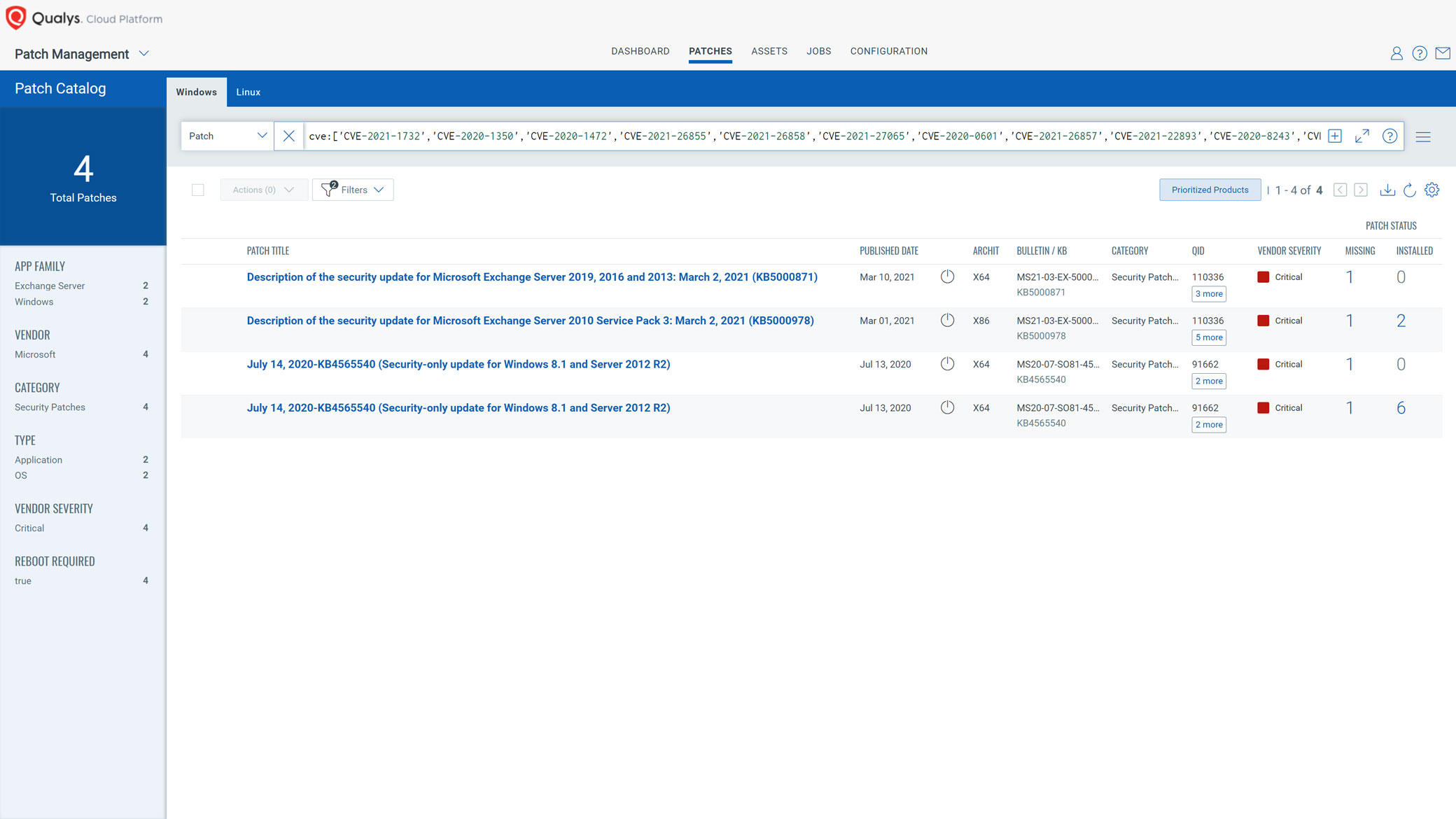
Note that the due date for “Category 1” patches has already passed. To find missing patches in your environment for “Category 1” past due CVEs, copy the following query into the Patch Management app:
cve:['CVE-2021-1732′,'CVE-2020-1350′,'CVE-2020-1472′,'CVE-2021-26855′,'CVE-2021-26858′,'CVE-2021-27065′,'CVE-2020-0601′,'CVE-2021-26857′,'CVE-2021-22893′,'CVE-2020-8243′,'CVE-2021-22900′,'CVE-2021-22894′,'CVE-2020-8260′,'CVE-2021-22899′,'CVE-2019-11510']
Federal Enterprises and Agencies Can Act Now
For federal enterprises and agencies, it's a race against time to remediate these vulnerabilities across their respective environments and achieve compliance with this binding directive. Qualys solutions can help achieve compliance with this binding directive. Qualys Cloud Platform is FedRAMP authorized, with 107 FedRAMP authorizations.
Here are a few steps Federal enterprises can take immediately:
- Run vulnerability assessments against all your assets by leveraging various sensors such as Qualys agent, scanners, and more
- Prioritize remediation by due dates
- Identify all vulnerable assets automatically mapped into the threat feed
- Use Patch Management to apply patches and other configurations changes
- Track remediation progress through Unified Dashboards
Summary
Understanding vulnerabilities is a critical but partial part of threat mitigation. Qualys VMDR helps customers discover, assess threats, assign risk, and remediate threats in one solution. Qualys customers rely on the accuracy of Qualys' threat intelligence to protect their digital environments and stay current with patch guidance. Using Qualys VMDR can help any organization efficiently respond to the CISA directive.
Getting Started
Learn how Qualys VMDR provides actionable vulnerability guidance and automates remediation in one solution. Ready to get started? Sign up for a 30-day, no-cost VMDR trial.
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C