
Microsoft and Adobe Patch Tuesday (September 2021) – Microsoft 60 Vulnerabilities with 3 Critical, Adobe 61 Vulnerabilities
Microsoft Patch Tuesday – September 2021
Microsoft patched 60 vulnerabilities in their September 2021 Patch Tuesday release, and an additional 26 CVEs since September 1st. Among the 60 released in the September Patch Tuesday, 3 of them are rated as critical severity, one as moderate, and 56 as important.
Critical Microsoft Vulnerabilities Patched
CVE-2021-40444 - Microsoft MSHTML Remote Code Execution Vulnerability
This vulnerability has been publicly disclosed and is known to be exploited. The vulnerability allows for remote code execution via MSHTML, a component used by Internet Explorer and Office. Microsoft also released a workaround to show how users can disable ActiveX controls in IE. The vendor has assigned a CVSSv3 base score of 8.8. It should be prioritized for patching.
CVE-2021-26435 - Windows Scripting Engine Memory Corruption Vulnerability
Microsoft released patches addressing a critical remote code execution vulnerability in Windows Scripting Engine. The exploitation of this vulnerability requires an attacker to convince users to click a link and then open a specially-crafted file. The vendor has assigned a CVSSv3 base score of 8.8. It should be prioritized for patching.
CVE-2021-36965 - Windows WLAN AutoConfig Service Remote Code Execution Vulnerability
This vulnerability does not allow user interaction and also has a low complexity for attack. The vendor has assigned a CVSSv3 base score of 8.8. It should be prioritized for patching.
CVE-2021-38633, CVE-2021-36963 - Windows Common Log File System Driver Elevation of Privilege Vulnerability
The vulnerabilities allow an attacker to gain elevated privileges to make changes to the victim’s system. These CVEs have a high likelihood of exploitability and is assigned a CVSSv3 base score of 7.8 by the vendor. It should be prioritized for patching.
CVE-2021-38671 - Windows Print Spooler Elevation of Privilege Vulnerability
This CVE has a high likelihood of exploitability and is assigned a CVSSv3 base score of 7.8 by the vendor. It should be prioritized for patching.
Qualys QIDs Providing Coverage
| QID | Title | Severity | CVE ID |
|---|---|---|---|
| 375861 | Microsoft Edge Based On Chromium Prior to 93.0.961.47 Multiple Vulnerabilities | High | CVE-2021-30632 |
| 110390 | Microsoft Office and Microsoft Office Services and Web Apps Security Update September 2021 | High | CVE-2021-38655,CVE-2021-38650,CVE-2021-38654,CVE-2021-38653,CVE-2021-38658,CVE-2021-38646,CVE-2021-38660,CVE-2021-38657,CVE-2021-38656,CVE-2021-38659 |
| 110391 | Microsoft SharePoint Enterprise Server Multiple Vulnerabilities September 2021 | Medium | CVE-2021-38651,CVE-2021-38652 |
| 375860 | Azure Open Management Infrastructure Multiple Vulnerabilities | Medium | CVE-2021-38645 CVE-2021-38647 CVE-2021-38648 CVE-2021-38649 |
91821|
Microsoft Cumulative Security Update for Internet Explorer (KB5005563)
| Medium| _KB5005563 _
375854| Visual Studio Code Spoofing Vulnerability | Medium| _CVE-2021-26437 _
45505| Microsoft MSHTML Remote Code Execution Vulnerability Active X Controls Disabled (Mitigation for CVE-2021-40444 Enabled)| Low|
91815| Microsoft Visual Studio Security Update for September 2021 | Medium | _CVE-2021-26434 CVE-2021-36952 _
91816| Microsoft Windows Security Update for September 2021| High| CVE-2021-38667,CVE-2021-38639,CVE-2021-38638,CVE-2021-38637,CVE-2021-26435,CVE-2021-40447,CVE-2021-38671,CVE-2021-36965,CVE-2021-36967,CVE-2021-36974,CVE-2021-36972,CVE-2021-36966,CVE-2021-36969,CVE-2021-36973,CVE-2021-36962,CVE-2021-36961,CVE-2021-36964,CVE-2021-36963,CVE-2021-36959,CVE-2021-36968,CVE-2021-36975,CVE-2021-38636,CVE-2021-38635,CVE-2021-38633,CVE-2021-38629,CVE-2021-38628,CVE-2021-38634,CVE-2021-38632,CVE-2021-38630,CVE-2021-38624,CVE-2021-36955,CVE-2021-36954,CVE-2021-36960,CVE-2021-36958
91817| Microsoft Dynamics Business Central Cross-Site Scripting (XSS) Vulnerability September 2021| Medium| CVE-2021-40440
91818| Microsoft Windows Kernel Elevation of Privilege Vulnerability September 2021| High| CVE-2021-38625,CVE-2021-38626
91819| Microsoft Windows Codecs Library HEVC Video Extensions Remote Code Execution (RCE) Vulnerability - September 2021| High| _CVE-2021-38661 _
91820| Microsoft MPEG-2 Video Extension Remote Code Execution (RCE) Vulnerability| High| _CVE-2021-38644 _
Adobe Patch Tuesday – September 2021
Adobe addressed 61 CVEs this Patch Tuesday impacting Adobe Acrobat and Reader, ColdFusion, Premiere Pro, Adobe InCopy, Adobe SVG-Native Viewer, InDesign, Framemaker, Creative Cloud Desktop Apps, Photoshop Elements, Premiere Elements, Digital Editions, Genuine Service, Photoshop, XMP Toolit SDK and Experience Manager.
The patches for Adobe Acrobat and Reader, ColdFusion and Experience Manager are labeled as Priority 2, while the remaining patches are labeled as Priority 3.
| Adobe Security Bulletin | QID | Severity | CVE ID |
|---|---|---|---|
| Adobe Security Update for Adobe Acrobat and Adobe Reader (APSB21-55) | 375845 | Medium | CVE-2021-39841, CVE-2021-39863, CVE-2021-39857, CVE-2021-39856, CVE-2021-39855, CVE-2021-39844, CVE-2021-39861, CVE-2021-39858, CVE-2021-39843, CVE-2021-39846, CVE-2021-39845, CVE-2021-35982, CVE-2021-39859, CVE-2021-39840, CVE-2021-39842, CVE-2021-39839, CVE-2021-39838,CVE-2021-39837,CVE-2021-39836,CVE-2021-39860,CVE-2021-39852,CVE-2021-39854,CVE-2021-39853,CVE-2021-39850,CVE-2021-39849,CVE-2021-39851 |
Discover Patch Tuesday Vulnerabilities in VMDR
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledge Base (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:(qid:375861 OR qid:110390 OR qid:110391 OR qid:375860 OR qid:91821 OR qid:375854 OR qid:45505 OR qid:91815 OR qid:91816 OR qid:91817 OR qid:91818 OR qid:91819 OR qid:91820)
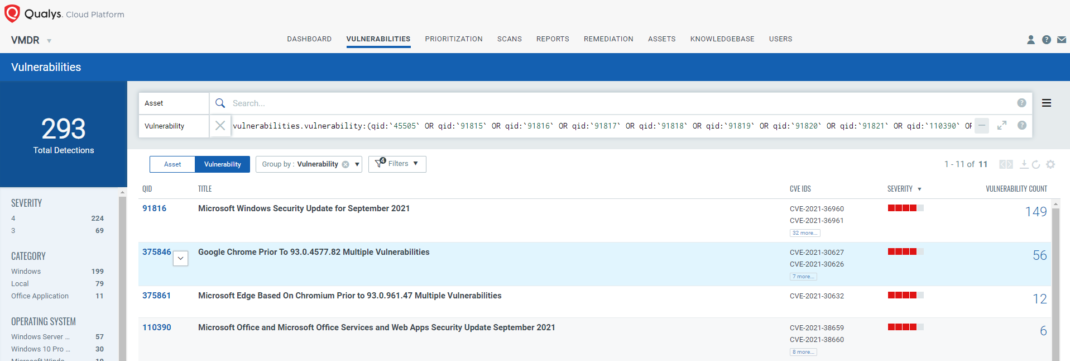
Respond by Patching
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go.
The following QQL will return the missing patches pertaining to this Patch Tuesday.
(qid:375861 OR qid:110390 OR qid:110391 OR qid:375860 OR qid:91821 OR qid:375854 OR qid:45505 OR qid:91815 OR qid:91816 OR qid:91817 OR qid:91818 OR qid:91819 OR qid:91820)
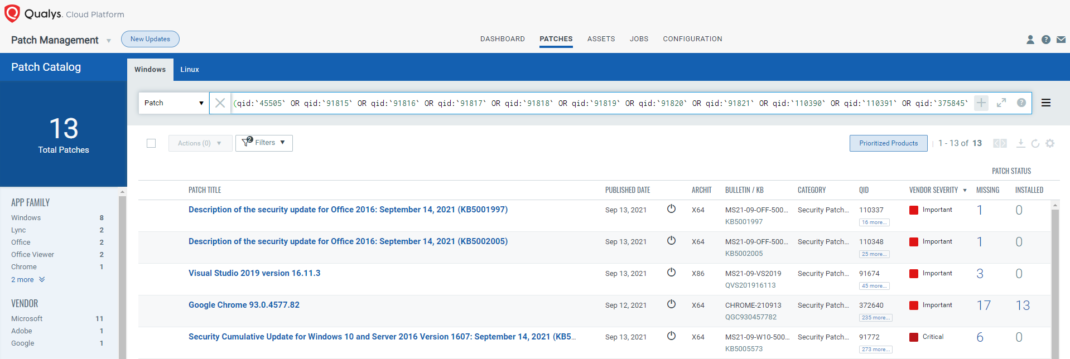
Patch Tuesday Dashboard
The current updated Patch Tuesday dashboards are available in Dashboard Toolbox: 2021 Patch Tuesday Dashboard.
Webinar Series: This Month in Vulnerabilities and Patches
To help customers leverage the seamless integration between Qualys VMDR and Patch Management and reduce the median time to remediate critical vulnerabilities, the Qualys Research team is hosting a monthly webinar series This Month in Vulnerabilities and Patches.
We discuss some of the key vulnerabilities disclosed in the past month and how to patch them:
- Microsoft Patch Tuesday, September 2021
- Adobe Patch Tuesday, September 2021
Join us live or watch on demand!
 Thursday, September 16, 2021 or later on demand
Thursday, September 16, 2021 or later on demand
About Patch Tuesday
Patch Tuesday QIDs are published at Security Alerts, typically late in the evening of Patch Tuesday, followed shortly after by PT dashboards.