
CISA Alert: Top Routinely Exploited Vulnerabilities
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
On July 28, 2021, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released a cybersecurity advisory detailing the top 30 publicly known vulnerabilities that have been routinely exploited by cyber threat actors in 2020 and 2021. Organizations are advised to prioritize and apply patches or workarounds for these vulnerabilities as soon as possible.
The advisory states, “If an organization is unable to update all software shortly after a patch is released, prioritize implementing patches for CVEs that are already known to be exploited or that would be accessible to the largest number of potential attackers (such as internet-facing systems).”
CISA released the advisory in conjunction with the Australian Cyber Security Centre (ACSC), the United Kingdom’s National Cyber Security Centre (NCSC), and the U.S. Federal Bureau of Investigation (FBI).
The CISA advisory is similar in scope to the October 2020 United States National Security Agency (NSA) cybersecurity advisory listing the top 25 known vulnerabilities being actively used by Chinese state-sponsored cyber actors that security teams can detect and mitigate or remediate in their infrastructure using Qualys VMDR.
Top Routinely Exploited Vulnerabilities
Here is the list of top routinely exploited vulnerabilities in 2020 and 2021 along with affected products and associated Qualys VMDR QID(s) for each vulnerability.
| CVE-IDs | Affected Products | Qualys Detections (QIDs) |
|---|---|---|
| CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065 | Microsoft Exchange | 50107, 50108 |
| CVE-2021-22893, CVE-2021-22894, CVE-2021-22899, CVE-2021-22900 | Pulse Secure | 38838 |
| CVE-2021-27101, CVE-2021-27102, CVE-2021-27103, CVE-2021-27104 | Accellion | 38830 |
| CVE-2021-21985 | VMware | 730102, 216261, 216260, 216259 |
| CVE-2018-13379, CVE-2020-12812, CVE-2019-5591 | Fortinet | 43702, 43769, 43825 |
| CVE-2019-19781 | Citrix | 150273, 372305, 372685 |
| CVE-2019-11510 | Pulse | 38771 |
| CVE-2018-13379 | Fortinet | 43702 |
| CVE-2020-5902 | F5- Big IP | 38791, 373106 |
| CVE-2020-15505 | MobileIron | 13998 |
| CVE-2017-11882 | Microsoft | 110308 |
| CVE-2019-11580 | Atlassian | 13525 |
| CVE-2018-7600 | Drupal | 371954, 150218, 277288, 176337, 11942 |
| CVE-2019-18935 | Telerik | 150299, 372327 |
| CVE-2019-0604 | Microsoft | 110330 |
| CVE-2020-0787 | Microsoft | 91609 |
| CVE-2020-1472 | Netlogon | 91688 |
Detect CISA’s Top Routinely Exploited Vulnerabilities using Qualys VMDR
Qualys released several remote and authenticated detections (QIDs) for the vulnerabilities. You can search for these QIDs in VMDR Dashboard using the following QQL query:
vulnerabilities.vulnerability.cveIds: [__CVE-2021-26855,CVE-2021-26857,CVE-2021-26858,CVE-2021-27065,CVE-2021-22893,CVE-2021-22894,CVE-2021-22899,CVE-2021-22900,CVE-2021-27101,CVE-2021-27102,CVE-2021-27103,CVE-2021-27104,CVE-2021-21985, CVE-2018-13379,CVE-2020-12812,CVE-2019-5591,CVE-2019-19781,CVE-2019-11510,CVE-2018-13379,CVE-2020-5902,CVE-2020-15505,CVE-2017-11882,CVE-2019-11580,CVE-2019-18935,CVE-2019-0604,CVE-2020-0787,CVE-2020-1472]
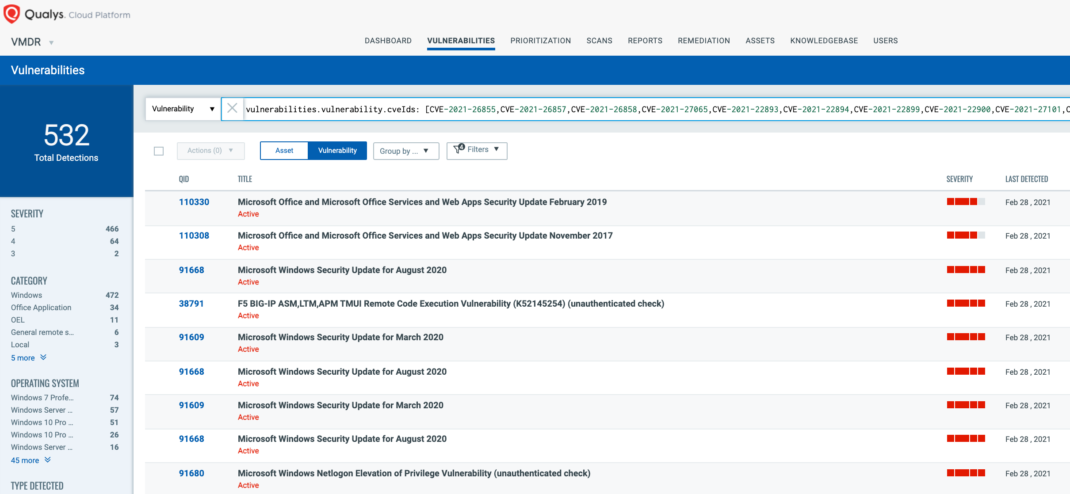
Using Qualys VMDR, customers can effectively prioritize this vulnerability for “Active Attack” RTI:
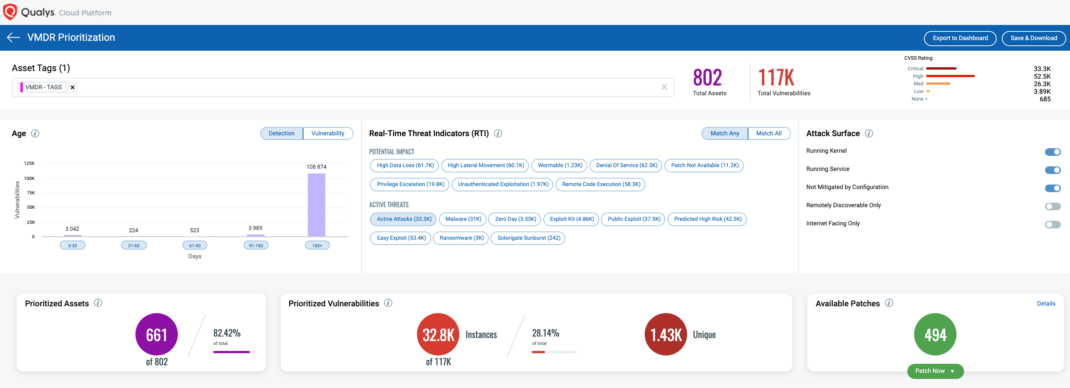
With VMDR Dashboard, you can track top 30 publicly known exploited vulnerabilities, their impacted hosts, their status and overall management in real time. With trending enabled for dashboard widgets, you can keep track of these vulnerabilities trends in your environment using the “CISA: Alert (AA21-209A) | Top Exploited” dashboard.
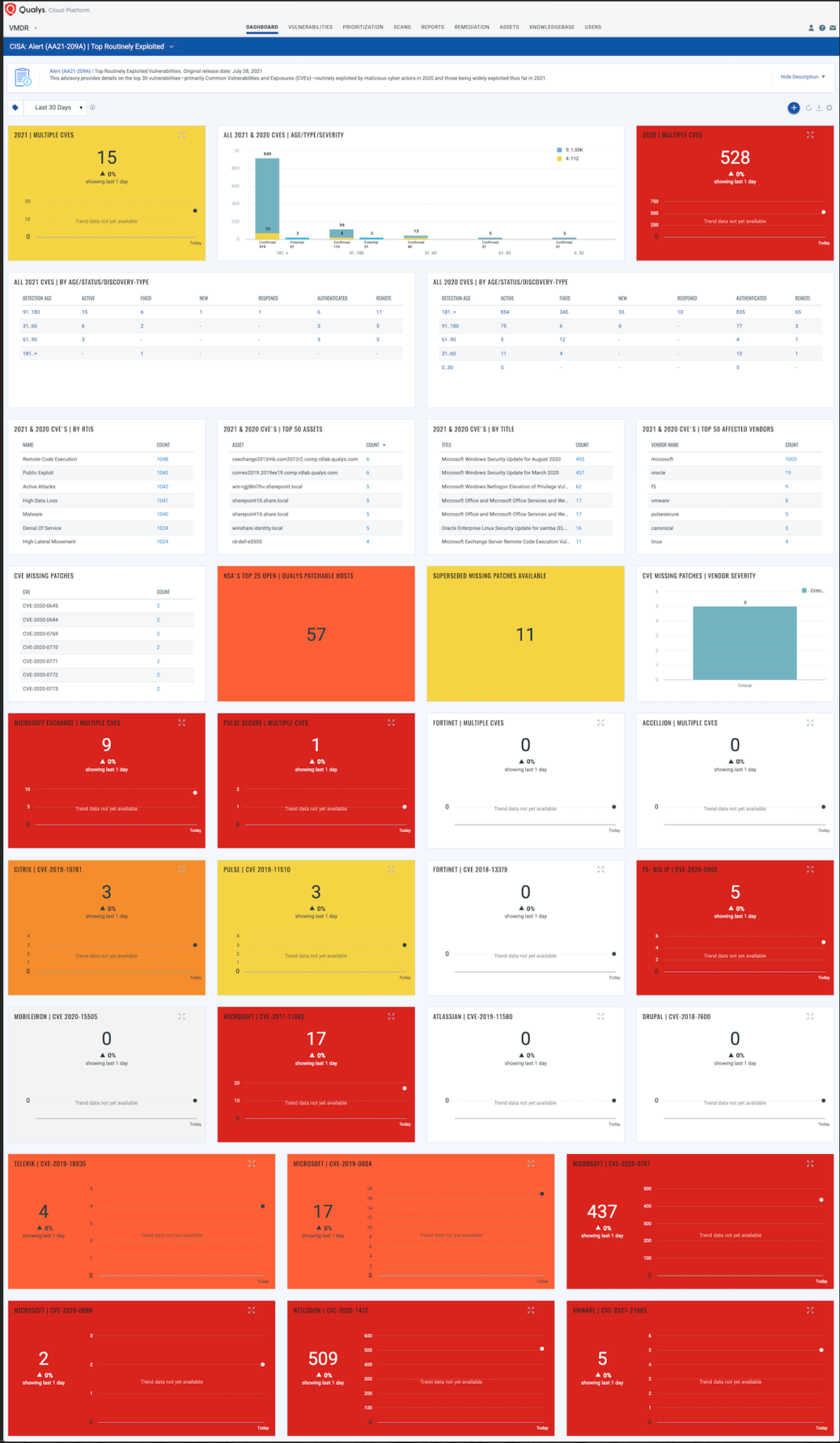
Recommendations
As guided by CISA, one must do the following to protect assets from being exploited:
- Minimize gaps in personnel availability and consistently consume relevant threat intelligence.
- Organizations’ vigilance team should keep a close eye on indications of compromise (IOCs) as well as strict reporting processes.
- Regular incident response exercises at the organizational level are always recommended as a proactive approach.
- Organizations should require multi-factor authentication to remotely access networks from external sources, especially for administrator or privileged accounts.
- Focus cyber defense resources on patching those vulnerabilities that cyber actors most often use.
Remediation and Mitigation
- Patch systems and equipment promptly and diligently.
- Implement rigorous configuration management programs.
- Disable unnecessary ports, protocols, and services.
- Enhance monitoring of network and email traffic.
- Use protection capabilities to stop malicious activity.
Get Started Now
Start your Qualys VMDR trial to automatically detect and mitigate or remediate the CISA top 30 publicly known vulnerabilities that have been routinely exploited by cyber threat actors in 2020 and 2021.
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C