
CVE-2018-13379 Path Traversal in Fortinet FortiOS
EPSS
Percentile
99.7%
An Improper Limitation of a Pathname to a Restricted Directory (“Path Traversal”) in Fortinet FortiOS 6.0.0 to 6.0.4, 5.6.3 to 5.6.7 under SSL VPN web portal allows an unauthenticated attacker to download system files via special crafted HTTP resource requests.
Recent assessments:
bulw4rk at March 25, 2020 8:04pm UTC reported:
Description
Due to a pre-authenticated Path Trasversal vulnerability under the SSL VPN portal on FortiOS, an attacker is able to pull arbitrary system files from the file system. One of the most critical files which an attacker may pull is “sslvpn_websessions” which contains session information including usernames and password.
Once the attacker has obtained the credentials from this file, he can authenticated with those credentials, compromising the corporate perimeter.
Mitigation
-
Upgrade to FortiOS 5.4.13, 5.6.8, 6.0.5 or 6.2.0 and above.
-
Enable 2FA. Note the attacker will not be able to log in to the VPN, but the obtained credentials are still valid (potencial domain creds) to access corporate mail, etc.
Affected Systems
-
FortiOS 6.0: 6.0.0 to 6.0.4
-
FortiOS 5.6: 5.6.3 to 5.6.7
-
FortiOS 5.4: 5.4.6 to 5.4.12
NOTE: Only if the SSL VPN service (web-mode or tunnel-mode) is enabled.
PoC
There are some public working exploits for this vulnerability, targeting the “sslvpn_websessions” system file.
An attacker would access the following URL:
- https://`<IP_ADDRESS>`/remote/fgt_lang?lang=/…/…/…/…//////////dev/cmdb/sslvpn_websession
And after some parsing to the binary file, something like the following output would be obtained:
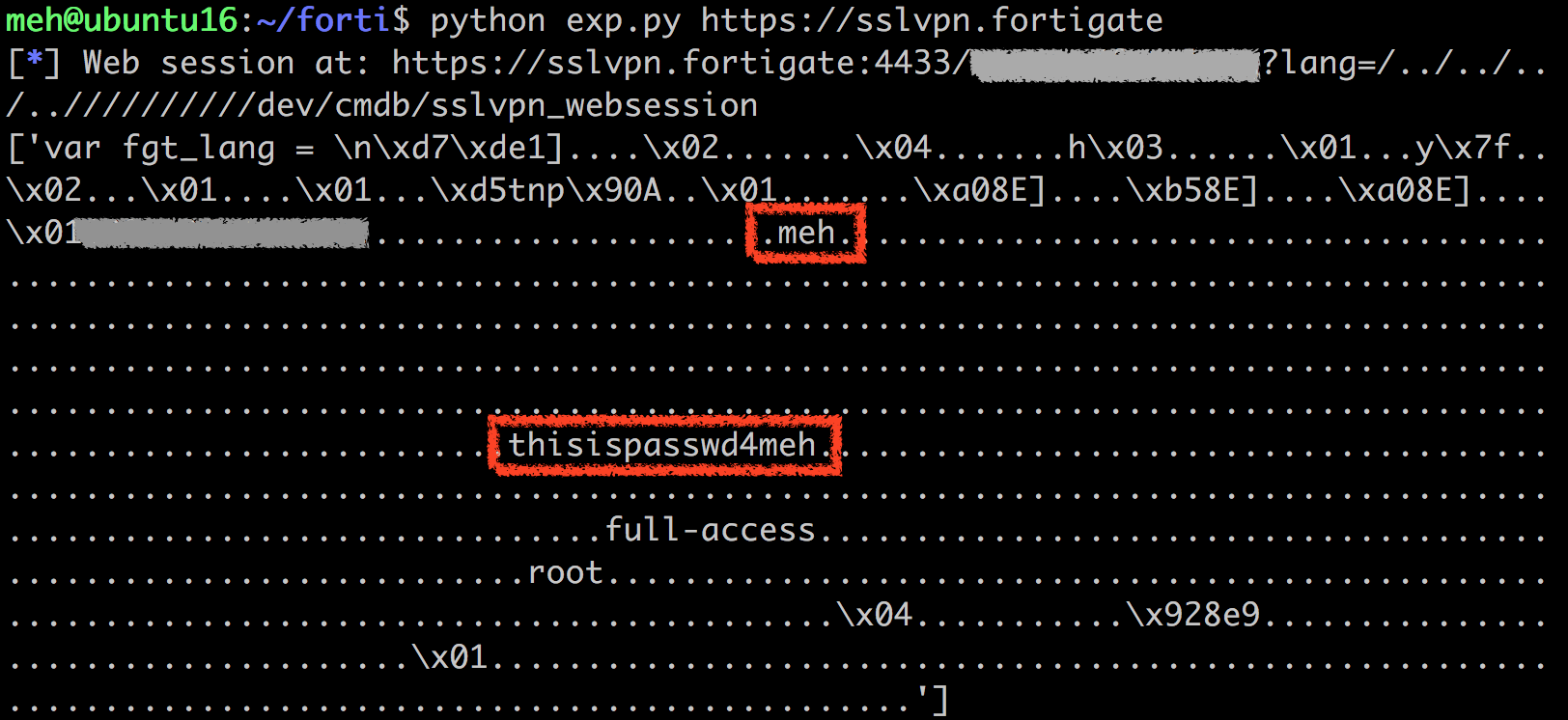
NOTE: Example image obtained from <https://devco.re/blog/2019/08/09/attacking-ssl-vpn-part-2-breaking-the-Fortigate-ssl-vpn/>
gwillcox-r7 at November 04, 2020 4:04pm UTC reported:
Description
Due to a pre-authenticated Path Trasversal vulnerability under the SSL VPN portal on FortiOS, an attacker is able to pull arbitrary system files from the file system. One of the most critical files which an attacker may pull is “sslvpn_websessions” which contains session information including usernames and password.
Once the attacker has obtained the credentials from this file, he can authenticated with those credentials, compromising the corporate perimeter.
Mitigation
-
Upgrade to FortiOS 5.4.13, 5.6.8, 6.0.5 or 6.2.0 and above.
-
Enable 2FA. Note the attacker will not be able to log in to the VPN, but the obtained credentials are still valid (potencial domain creds) to access corporate mail, etc.
Affected Systems
-
FortiOS 6.0: 6.0.0 to 6.0.4
-
FortiOS 5.6: 5.6.3 to 5.6.7
-
FortiOS 5.4: 5.4.6 to 5.4.12
NOTE: Only if the SSL VPN service (web-mode or tunnel-mode) is enabled.
PoC
There are some public working exploits for this vulnerability, targeting the “sslvpn_websessions” system file.
An attacker would access the following URL:
- https://`<IP_ADDRESS>`/remote/fgt_lang?lang=/…/…/…/…//////////dev/cmdb/sslvpn_websession
And after some parsing to the binary file, something like the following output would be obtained:

NOTE: Example image obtained from <https://devco.re/blog/2019/08/09/attacking-ssl-vpn-part-2-breaking-the-Fortigate-ssl-vpn/>
ccondon-r7 at November 22, 2020 6:52pm UTC reported:
Description
Due to a pre-authenticated Path Trasversal vulnerability under the SSL VPN portal on FortiOS, an attacker is able to pull arbitrary system files from the file system. One of the most critical files which an attacker may pull is “sslvpn_websessions” which contains session information including usernames and password.
Once the attacker has obtained the credentials from this file, he can authenticated with those credentials, compromising the corporate perimeter.
Mitigation
-
Upgrade to FortiOS 5.4.13, 5.6.8, 6.0.5 or 6.2.0 and above.
-
Enable 2FA. Note the attacker will not be able to log in to the VPN, but the obtained credentials are still valid (potencial domain creds) to access corporate mail, etc.
Affected Systems
-
FortiOS 6.0: 6.0.0 to 6.0.4
-
FortiOS 5.6: 5.6.3 to 5.6.7
-
FortiOS 5.4: 5.4.6 to 5.4.12
NOTE: Only if the SSL VPN service (web-mode or tunnel-mode) is enabled.
PoC
There are some public working exploits for this vulnerability, targeting the “sslvpn_websessions” system file.
An attacker would access the following URL:
- https://`<IP_ADDRESS>`/remote/fgt_lang?lang=/…/…/…/…//////////dev/cmdb/sslvpn_websession
And after some parsing to the binary file, something like the following output would be obtained:

NOTE: Example image obtained from <https://devco.re/blog/2019/08/09/attacking-ssl-vpn-part-2-breaking-the-Fortigate-ssl-vpn/>
Assessed Attacker Value: 5
Assessed Attacker Value: 5Assessed Attacker Value: 5
References
packetstormsecurity.com/files/154146/FortiOS-5.6.7-6.0.4-Credential-Disclosure.html
packetstormsecurity.com/files/154147/FortiOS-5.6.7-6.0.4-Credential-Disclosure.html
www.securityfocus.com/bid/108693
cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-13379
devco.re/blog/2019/08/09/attacking-ssl-vpn-part-2-breaking-the-Fortigate-ssl-vpn
devco.re/blog/2019/08/09/attacking-ssl-vpn-part-2-breaking-the-Fortigate-ssl-vpn/
fortiguard.com/advisory/FG-IR-18-384
github.com/blacklotuslabs/Development/blob/master/Mitigations/CVE/CVE-2018-13379/CVE-2018-13379%20-%20Summary%20%26%20Emergency%20Mitigations.pdf
i.blackhat.com/USA-19/Wednesday/us-19-Tsai-Infiltrating-Corporate-Intranet-Like-NSA.pdf
www.fortiguard.com/psirt/FG-IR-20-233