Hackers Exploit Accellion Zero-Days in Recent Data Theft and Extortion Attacks
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
Cybersecurity researchers on Monday tied a string of attacks targeting Accellion File Transfer Appliance (FTA) servers over the past two months to data theft and extortion campaign orchestrated by a cybercrime group called UNC2546.
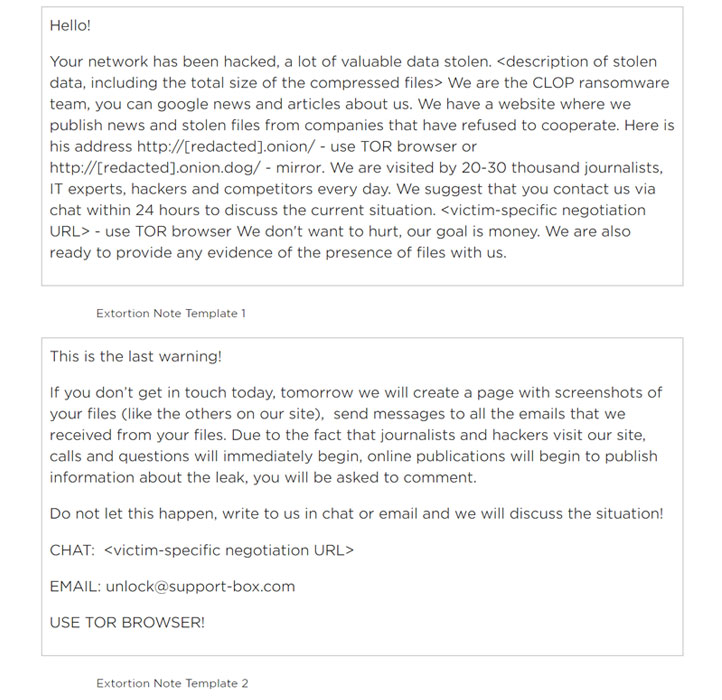
The attacks, which began in mid-December 2020, involved exploiting multiple zero-day vulnerabilities in the legacy FTA software to install a new web shell named DEWMODE on victim networks and exfiltrating sensitive data, which was then published on a data leak website operated by the CLOP ransomware gang.
But in a twist, no ransomware was actually deployed in any of the recent incidents that hit organizations in the U.S., Singapore, Canada, and the Netherlands, with the actors instead resorting to extortion emails to threaten victims into paying bitcoin ransoms.
According to Risky Business, some of the companies that have had their data listed on the site include Singapore’s telecom provider SingTel, the American Bureau of Shipping, law firm Jones Day, the Netherlands-based Fugro, and life sciences company Danaher.
Following the slew of attacks, Accellion has patched four FTA vulnerabilities that were known to be exploited by the threat actors, in addition to incorporating new monitoring and alerting capabilities to flag any suspicious behavior. The flaws are as follows -
- CVE-2021-27101 - SQL injection via a crafted Host header
- CVE-2021-27102 - OS command execution via a local web service call
- CVE-2021-27103 - SSRF via a crafted POST request
- CVE-2021-27104 - OS command execution via a crafted POST request
FireEye’s Mandiant threat intelligence team, which is leading the incident response efforts, is tracking the follow-on extortion scheme under a separate threat cluster it calls UNC2582 despite “compelling” overlaps identified between the two sets of malicious activities and previous attacks carried out by a financially motivated hacking group dubbed FIN11.
“Many of the organizations compromised by UNC2546 were previously targeted by FIN11,” FireEye said. “Some UNC2582 extortion emails observed in January 2021 were sent from IP addresses and/or email accounts used by FIN11 in multiple phishing campaigns between August and December 2020.”
Once installed, the DEWMODE web shell was leveraged to download files from compromised FTA instances, leading to the victims receiving extortion emails claiming to be from the “CLOP ransomware team” several weeks later.
Lack of reply in a timely manner would result in additional emails sent to a wider group of recipients in the victim organization as well as its partners containing links to the stolen data, the researchers detailed.
Besides urging its FTA customers to migrate to kiteworks, Accellion said fewer than 100 out of 300 total FTA clients were victims of the attack and that less than 25 appear to have suffered “significant” data theft.
The development comes after grocery chain Kroger disclosed last week that HR data, pharmacy records, and money services records belonging to some customers might have been compromised as a result of the Accellion incident.
Then earlier today, Transport for New South Wales (TfNSW) became the latest entity to confirm that it had been impacted by the worldwide Accellion data breach.
“The Accellion system was widely used to share and store files by organisations around the world, including Transport for NSW,” the Australian agency said. “Before the attack on Accellion servers was interrupted, some Transport for NSW information was taken.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C