
CISA Alert: Top 15 Routinely Exploited Vulnerabilities
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
The U.S. Cybersecurity & Infrastructure Security Agency has published its report on the top exploited vulnerabilities of 2021. This blog summarizes the report’s findings and how you can use Qualys VMDR to automatically detect and remediate these risks in your enterprise environment.
The Cybersecurity & Infrastructure Security Agency (CISA) releases detailed alerts of critical vulnerabilities and threats when warranted. These alerts cover the most exploited security vulnerabilities and provide critical insights into the type, nature, and vendor product affected, as well as recommended mitigations that enterprise IT/security professionals can take to reduce their risk.
To that end, CISA has released its 2021 Top Routinely Exploited Vulnerabilities Report. It provides in-depth details of each exploited CVE, including which threat actors aggressively targeted both public and private sector organizations worldwide. It also provides mitigation guidance for all the top vulnerabilities.
Of special interest in the report is this key finding by CISA:
Globally, in 2021, malicious cyber actors targeted internet-facing systems, such as email servers and virtual private network (VPN) servers, with exploits of newly disclosed vulnerabilities. For most of the top exploited vulnerabilities, researchers or other actors released proof of concept (POC) code within two weeks of the vulnerability's disclosure, likely facilitating exploitation by a broader range of malicious actors.
CISA’s Top 15 Routinely Exploited Vulnerabilities of 2021
The top 15 routine vulnerability exploits observed by cybersecurity authorities in the U.S., Australia, Canada, New Zealand, and the U.K. are:
| CVE | Vulnerability Name | Vendor and Product | Type |
|---|---|---|---|
| CVE-2021-44228 | Log4Shell | Apache Log4j | Remote code execution (RCE) |
| CVE-2021-40539 | Zoho ManageEngine AD SelfService Plus | RCE | |
| CVE-2021-34523 | ProxyShell | Microsoft Exchange Server | Elevation of privilege |
| CVE-2021-34473 | ProxyShell | Microsoft Exchange Server | RCE |
| CVE-2021-31207 | ProxyShell | Microsoft Exchange Server | Security feature bypass |
| CVE-2021-27065 | ProxyLogon | Microsoft Exchange Server | RCE |
| CVE-2021-26858 | ProxyLogon | Microsoft Exchange Server | RCE |
| CVE-2021-26857 | ProxyLogon | Microsoft Exchange Server | RCE |
| CVE-2021-26855 | ProxyLogon | Microsoft Exchange Server | RCE |
| CVE-2021-26084 | Atlassian Confluence Server and Data Center | Arbitrary code execution | |
| CVE-2021-21972 | VMware vSphere Client | RCE | |
| CVE-2020-1472 | ZeroLogon | Microsoft Netlogon Remote Protocol (MS-NRPC) | Elevation of privilege |
| CVE-2020-0688 | Microsoft Exchange Server | RCE | |
| CVE-2019-11510 | Pulse Secure Pulse Connect Secure | Arbitrary file reading | |
| CVE-2018-13379 | Fortinet FortiOS and FortiProxy | Path traversal |
Highlights of Top Vulnerabilities Cited in CISA 2021 Report
Based on the analysis of this report by the Qualys Research Team, let’s review a few of the top vulnerabilities on the 2021 list and our recommendations for how Qualys enterprise customers can detect and respond to them.
Log4Shell Vulnerability
The Log4Shell vulnerability (CVE-2021-44228) was disclosed in December 2021. It was widely exploited by sending a specially crafted code string, which allowed an attacker to execute arbitrary Java code on the server and take complete control of the system. Thousands of products used Log4Shell and were vulnerable to the Log4Shell exploitation.
Visit the Qualys Log4Shell website for full details on our response to this threat.
ProxyShell: Multiple Vulnerabilities
The multiple vulnerabilities called ProxyShell (CVE-2021-34523, CVE-2021-34473, CVE-2021-31207) affect Microsoft Exchange email servers. Successful exploitation of these vulnerabilities in combination (i.e., via "vulnerability chaining") enables a remote actor to execute arbitrary code and privilege escalation.
ProxyLogon: Multiple Vulnerabilities
The multiple vulnerabilities named ProxyLogon (CVE-2021-26855, CVE-2021-26858, CVE-2021-26857, CVE-2021-27065) also affect Microsoft Exchange email servers. Successful exploitation of these vulnerabilities in combination allows an unauthenticated threat actor to execute arbitrary code on vulnerable Exchange Servers, which enables the attacker to gain persistent access to files, mailboxes, and credentials stored on the servers.
Read our blog on this threat.
Confluence Server and Data Center Vulnerability
An Object Graph Navigation Library injection vulnerability (CVE-2021-26084) exists in Confluence Server that could allow an authenticated user, and in some instances an unauthenticated user, to execute arbitrary code on a Confluence Server or Data Center instance.
Top Vulnerabilities of 2020 Persist
Three additional vulnerabilities (CVE-2020-1472, CVE-2018-13379, CVE-2019-11510) were part of the routinely exploited top vulnerabilities of 2020 list but continued to be exploited well into 2021.
How Can Qualys Help?
The Qualys Research Team stays on top of CISA’s vulnerability reports by mapping and releasing our QIDs as needed. The goal is to provide our enterprise customers with complete visibility into risk across their organizations.
Detect CISA Top 15 Exploited Vulnerabilities using Qualys VMDR
Qualys VMDR provides coverage for all 15 vulnerabilities described in the CISA report. Qualys Patch Management can automatically patch all Windows-related vulnerabilities which account for 60% of the 15 vulnerabilities. Organizations can quickly reduce the risk from these vulnerabilities. Organizations can quickly reduce the risk from these vulnerabilities.
Using VMDR and Qualys Query Language (QQL) lets you easily detect all your assets that are vulnerable to the top 15.
Use this QQL statement:
vulnerabilities.vulnerability.cveIds:[`CVE-2021-44228`, `CVE-2021-40539`, `CVE-2021-34523`, `CVE-2021-34473`, `CVE-2021-31207`, `CVE-2021-27065`, `CVE-2021-26858`, `CVE-2021-26857`, `CVE-2021-26855`, `CVE-2021-26084`, `CVE-2021-21972`, `CVE-2020-1472`, `CVE-2020-0688`, `CVE-2019-11510`, `CVE-2018-13379`]
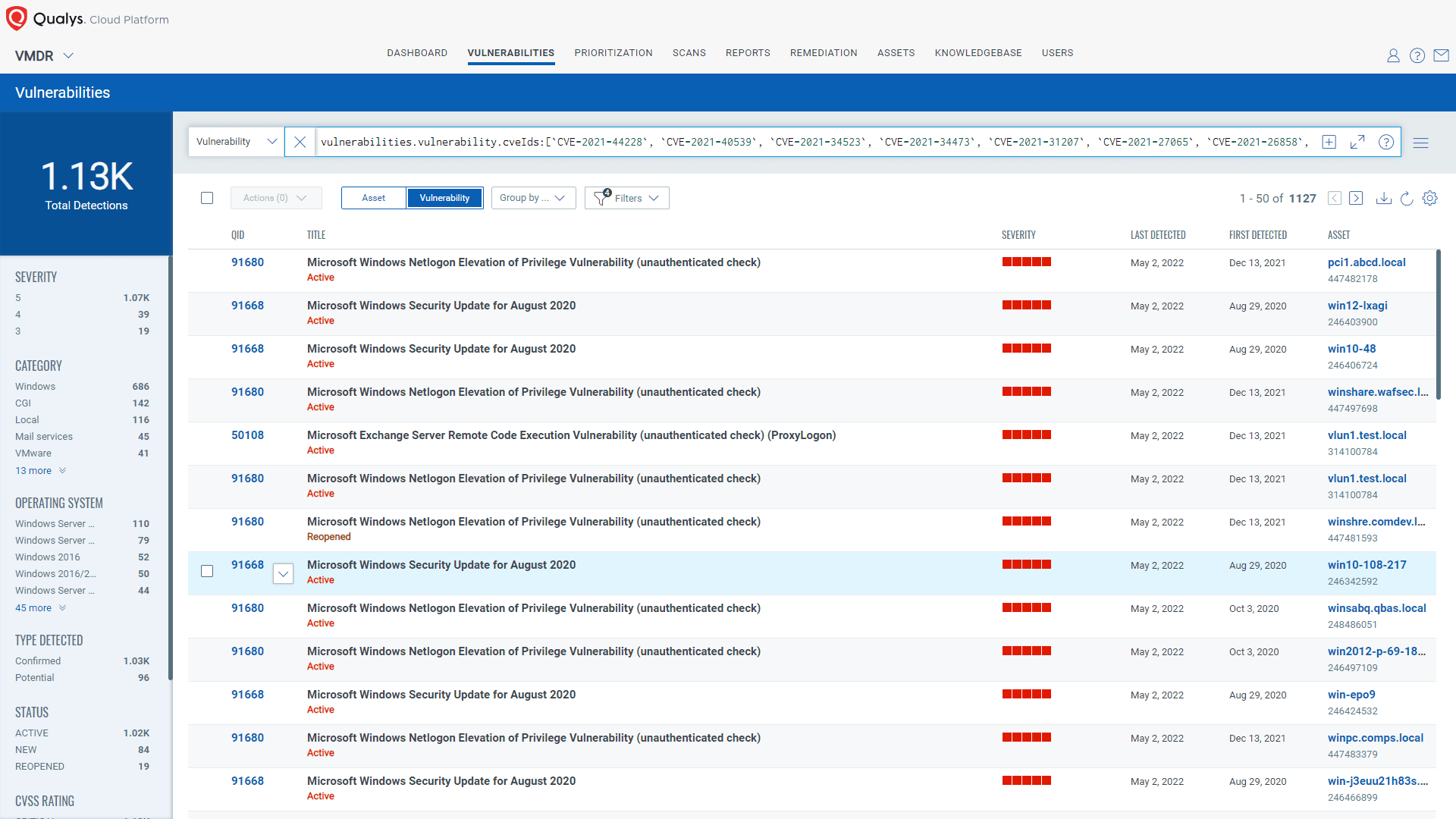 View vulnerabilities be severity in Qualys VMDR
View vulnerabilities be severity in Qualys VMDR
Qualys Unified Dashboard provides a comprehensive view of the top 15 exploited vulnerabilities as they affect your entire enterprise environment. The dashboard allows the security team to keep track of each vulnerability as they may propagate across multiple assets in your infrastructure.
Dashboard CISA: Alert (AA22-117A) | Top 15 Routinely Exploited
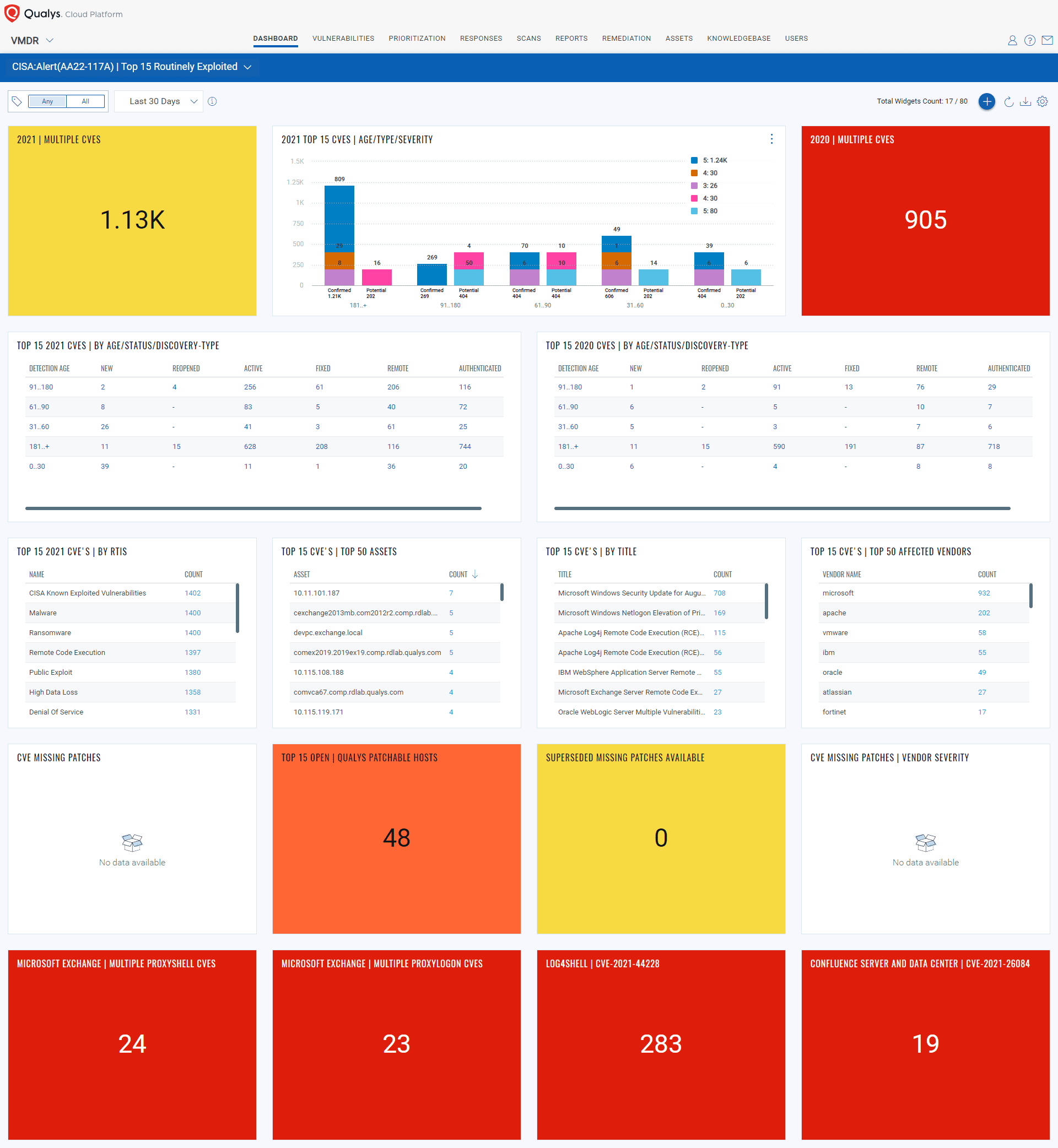 Qualys Unified Dashboard
Qualys Unified Dashboard
Prioritize CISA Top 15 Exploited Vulnerabilities using Qualys VMDR
Qualys VMDR makes it easy to prioritize the top 15 exploited vulnerabilities affecting your company’s internet-facing assets. To do so, apply the tag “Internet Facing Assets” in the Prioritization tab. You can add tags like "Cloud Environments", "Type: Servers", "Web Servers", and "VMDR-Web Servers" to increase your scope of assets.
Use this QQL statement:
vulnerabilities.vulnerability.cveIds:[`CVE-2021-44228`, `CVE-2021-40539`, `CVE-2021-34523`, `CVE-2021-34473`, `CVE-2021-31207`, `CVE-2021-27065`, `CVE-2021-26858`, `CVE-2021-26857`, `CVE-2021-26855`, `CVE-2021-26084`, `CVE-2021-21972`, `CVE-2020-1472`, `CVE-2020-0688`, `CVE-2019-11510`, `CVE-2018-13379`]
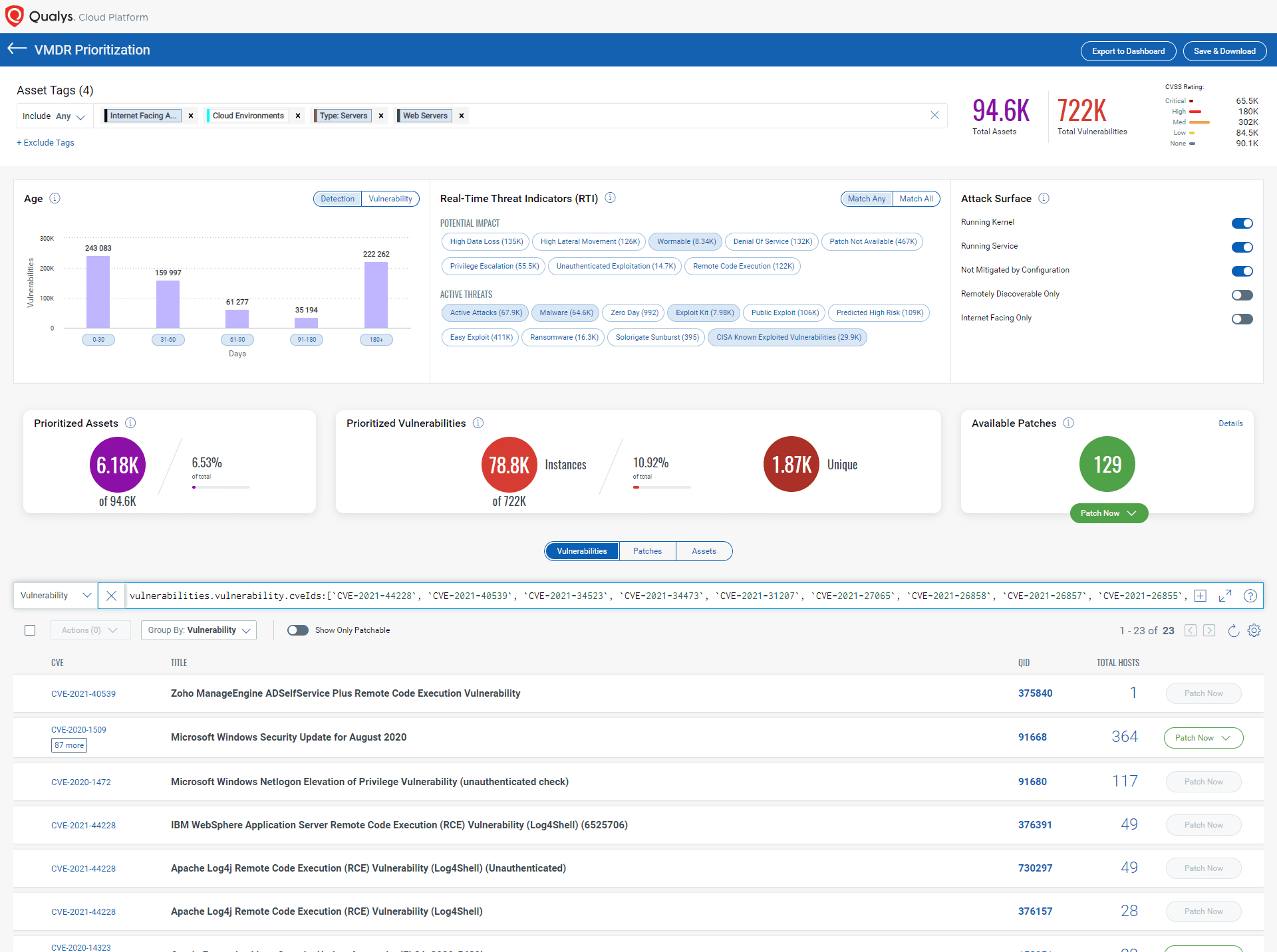 Prioritizing vulnerabilities for remediation in Qualys VMDR
Prioritizing vulnerabilities for remediation in Qualys VMDR
Remediate CISA Top 15 Exploited Vulnerabilities using Qualys VMDR
Qualys Patch Management offers out-of-the-box support for patching multiple CISA vulnerabilities. Patch Management also provides patches for many Microsoft, Linux, and third-party application vulnerabilities.
To view the patchable QIDs, enable the "Show only Patchable" toggle button. After that, you can configure the patch job to patch the relevant QIDs and their respective associated CVEs.
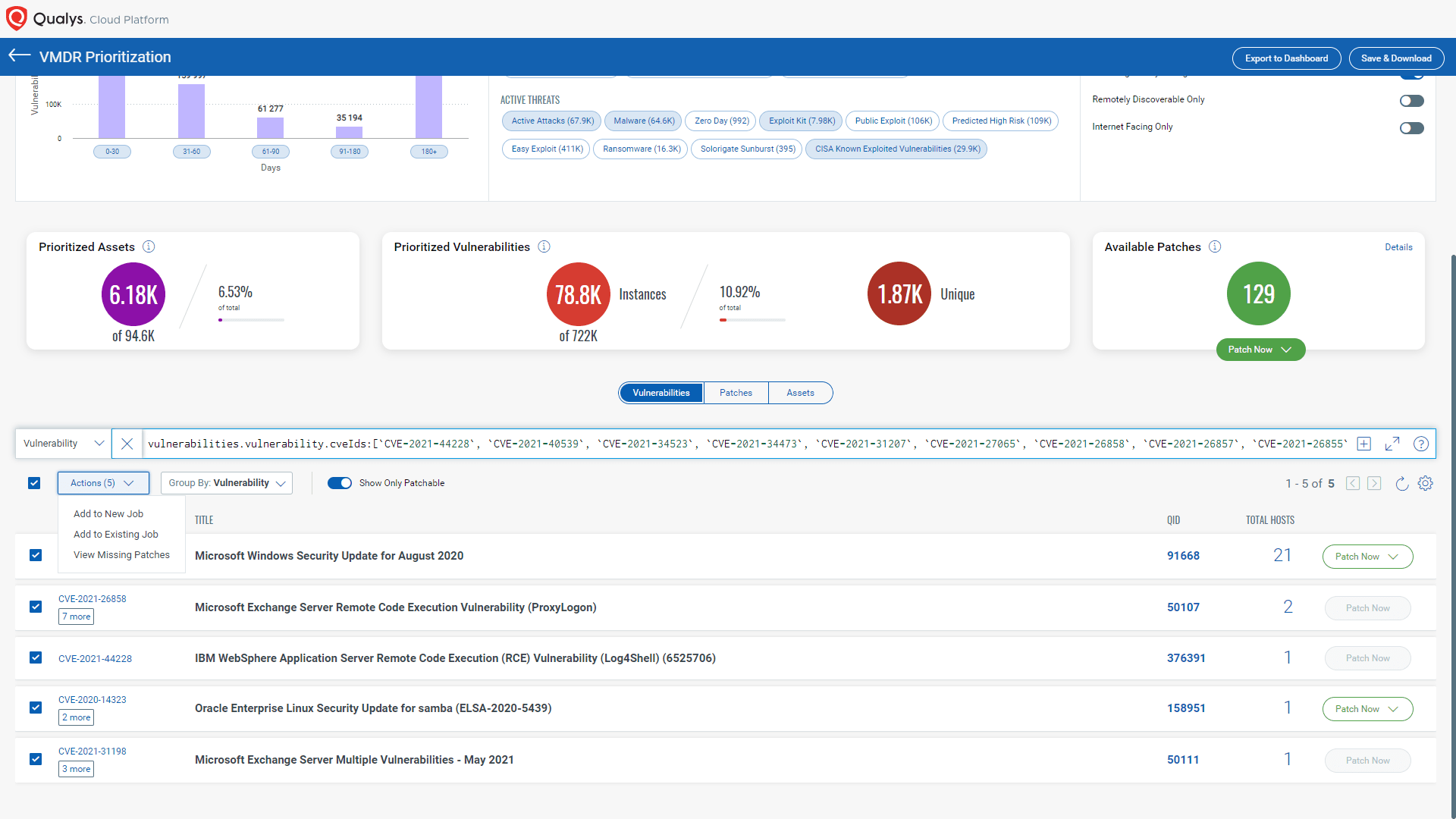 Using Qualys Patch Management to apply patches
Using Qualys Patch Management to apply patches
Qualys Patch Management also provides the ability to deploy custom patches. The flexibility to customize patch deployment allows you to patch all the remaining CVEs in your patching to-do list.
To get a view of all available patches for CISA’s top 15 exploitable vulnerabilities of 2021, go to the Patch Management application and run this QQL statement in the Patches tab:
cve:[`CVE-2021-44228`, `CVE-2021-40539`, `CVE-2021-34523`, `CVE-2021-34473`, `CVE-2021-31207`, `CVE-2021-27065`, `CVE-2021-26858`, `CVE-2021-26857`, `CVE-2021-26855`, `CVE-2021-26084`, `CVE-2021-21972`, `CVE-2020-1472`, `CVE-2020-0688`, `CVE-2019-11510`, `CVE-2018-13379`]
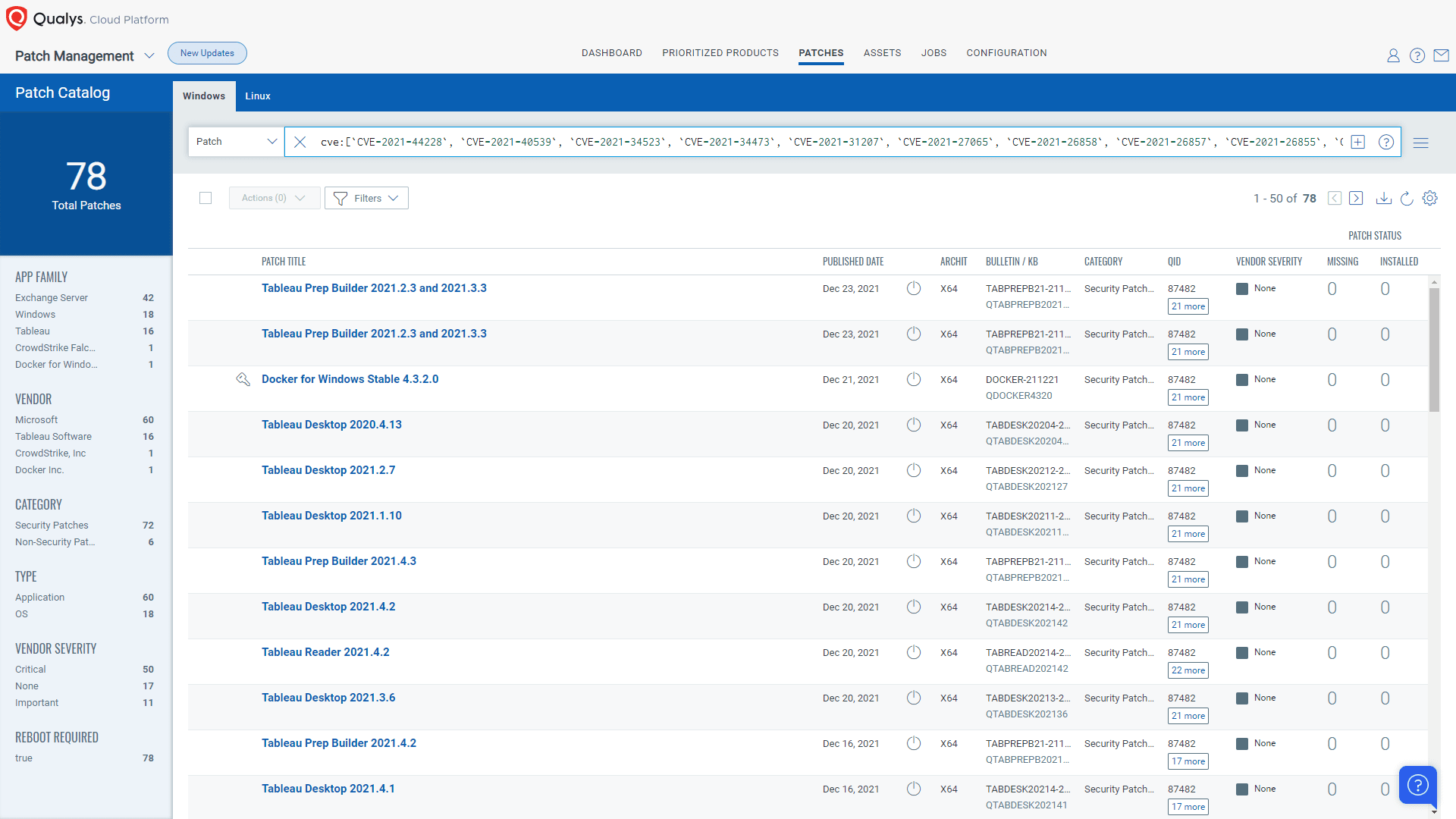 Viewing available patches in Qualys Patch Management
Viewing available patches in Qualys Patch Management
For additional patch details about vulnerabilities reported by CISA, please see the Appendix of the CISA report.
Getting Started
Ready to get started? Learn how Qualys VMDR provides actionable vulnerability guidance and automates remediation in one solution.
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C