
The Bug Report - February 2022 Edition
The Bug Report - February 2022
By Jesse Chick · March 2, 2022
Your Cybersecurity Comic Relief
 Image courtesy of https://toggl.com/
Image courtesy of https://toggl.com/
Why am I here?
Welcome back to the Bug Report, stubby-month edition! For those in the audience unfamiliar with our shtick, every month we compile a shortlist of the top vulnerabilities of the month, so that they might whittle away at your last few hours of peaceful sleep.
It’s a testament to the excitement of the last few months that February came as something of a reprieve for many of us who follow the ebbs and flows of the vulnerability landscape. But as we all slow down and catch our breath, someone, somewhere is having their personal information leaked, their intellectual property held by ransomware, or their privacy otherwise abused by a 0-day…and you’re probably here for the grisly details. So, we at Trellix dutifully present to you our four high-impact vulns released during the month of February:
- CVE-2022-22620: Apple WebKit
- CVE-2022-0609: Google Chrome
- CVE-2022-24086: Magento/ Adobe Commerce
- CVE-2022-22536: SAP Internet Communications Manager
CVE-2022-22620: Apple finally gave something away for free!
What is it?
WebKit is Apple’s browser engine. If you are browsing the internet using an Apple product, I’d bet with next month’s rent money that WebKit is churning behind the scenes. Versions of WebKit prior to iOS 15.3.1 contain a use-after-free vulnerability (which occurs due to shoddy memory management) that can allow full remote code execution on a victim’s device. The avenue of attack most likely to be used by attackers is a malicious URL (remember phishing from those pesky compliance trainings?) or via embedding the payload in a cross-site scripting attack on a vulnerable webpage. In the same terse fashion we curious souls have come to expect, Apple has withheld further detail on this vulnerability and the nature of the exploit.
Who cares?
I care. I have an iPhone. And so do 6 million of you on Twitter, apparently, who likely rely on Apple products for either professional or personal tasks. To make this threat even less abstract for us Apple used-to-be-elite-now-commoners, there have been reports of CVE-2022-22620 being exploited in conjunction with privilege escalation to gain access to users’ cameras and microphones.
What can I do?
Update. Gotta update, always. To make sure your iPhone is running the patched version of iOS, go to Settings > General > About. If the “Software Version” shows something older than 15.3.1, that device is vulnerable, and it would be best to update immediately.
The Gold Standard
At this point, patching via software update is your best option. If you would like to have security and other updates installed automatically overnight upon release by Apple, this can be configured on all relevant devices to ensure you are free of exposure as quickly as possible.
CVE-2022-0609: Should you switch to Firefox?
What is it?
Appearing like roaches, use-after-free browser bugs travel in groups. This one was discovered in-house at Google, by the Threat Analysis Group, inside of Chrome’s animation component. Although some interaction from the user is required to carry out a successful exploit, this vulnerability can be leveraged to send and execute commands on a victim’s machine over a local network.
Who cares?
The hundreds of millions of Chrome users (backed by Chrome’s nearly two-thirds market share among today’s browsers) may want to pay it some mind. This especially holds true for those who often browse from a public network, e.g. students and those who frequently travel, since public networks are a common reservoir of targets for malicious actors. Sure enough, according to Google, this vulnerability is reported to have been exploited numerous times in the wild. But we all work from home now so no big deal, right? (I’m hoping this comment does NOT age well).
What can I do?
Update Chrome to version 98.0.4758.102 or later, if you have not done so already. Checking the current version of Chrome is as simple as pasting “chrome://version” into the search bar.
The Gold Standard
As with iOS, etc., turning on automatic updates for Chrome is a good practice. Set it and forget.
CVE-2022-24086: All your e-commerce belongs to….?
What is it?
You can be forgiven for having never heard of Magento; avoiding PHP back ends like Ebola seems like decent practice. It turns out Magento is an open-source e-commerce platform which was bought by Adobe in 2018 and now forms the backbone of Adobe Commerce. Due to a lack of proper input validation (CWE-20, if you care) during the checkout stage of a transaction, an attacker can use Adobe Commerce—or the open-source release of Magento that parallels it—to achieve unauthenticated RCE with the same privileges as the corresponding server process. So, if Magento is running as root, this is about as bad as it gets.
Who cares?
Well, if your platform relies on Adobe Commerce or open-source Magento, consider yourself vulnerable—all unpatched versions of each are affected. Not to mention, CVE-2022-24086 has been actively exploited in the wild.
As of this writing, there is no complete publicly-available proof of concept, although a redacted version of a working POC (seen below) created by researchers with Positive Technologies Offensive Team has been released on Twitter and distributed widely, which illustrates the leaking of “/etc/passwd” on a vulnerable host.
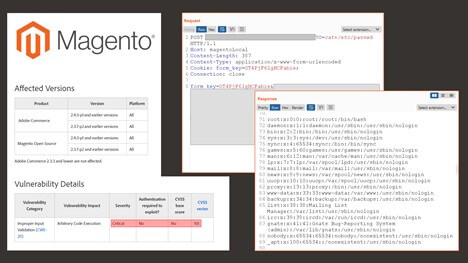
What can I do?
Patch, and patch quickly. Time is of the essence! But be sure to follow the instructions from Adobe with care: there are two patches which must be applied in sequence, one to address CVE-2022-24086 and another to fix the near-identical follow-on issue tracked as CVE-2022-24087. Both patches are required to make sure that your platform is safe from exploitation of this vulnerability.
The Gold Standard
Stay abreast on the latest impactful vulnerabilities throughout the industry; or you just might see a piece of your own infrastructure featured in the latest CVE. Our security bulletins are a great place to start.
CVE-2022-22536: A Perfect 10!
What is it?
Does anyone have a clue what SAP stands for? I’ve always wondered but never been able to demystify the potential acronym. This month it could be confused with a Strikingly Attackable Platform thanks to CVE-2022-22536. The bug exists in the SAP Internet Communication Manager (ICM) when the webserver hosting the ICM is sitting behind a proxy. An attacker can use a technique called HTTP Response Smuggling to poison the proxy’s web cache and ICM response queue. Upon an unexpecting user visiting the website and making a GET request for the page, they will download the attacker’s malicious JavaScript instead of the intended webpage. A more detailed (and colorful!) explanation of the attack mechanics is available on the Onapsis website, for the price of your email, of course.
Who cares?
SAP in January of 2022 proudly reported that 99 of 100 of the largest companies in the world were SAP customers with over 230 million cloud users. Couple that statistic with the fact that every SAP application sitting behind any kind of proxy with standard configuration will be vulnerable to this bug, there is a good chance you might need to cancel your weekend plans. Although we don’t put much stock in CVSS score for this publication, it’s worth noting this scored the magical unicorn rating of a perfect 10 and was able to garner special attention from our friends at CISA.
What can I do?
If in doubt as to whether or not your SAP server is vulnerable, the good people at Onapsis, who discovered the vulnerability, released a Python-based scanning tool with a complete CLI. Or, if you have the version number of your NetWeaver, Web Dispatcher, etc., you can simply cross-reference it with SAP’s official list of vulnerable versions. Don’t want a call at 2 a.m. about a breach? Take the time to download and install the patches for your SAP products today!
The Gold Standard
Unfortunately, not every vulnerability can be adequately addressed by network security products, and this vulnerability happens to be one of those cases. Your best bet is to follow the mitigations mentioned above and keep your servers up to date.