
The 9th Google Chrome Zero-Day Threat this Year – Again Just Before the Weekend
9.6 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P
Google has released yet another security update for the Chrome desktop web browser to address a high-severity vulnerability that is being exploited in the wild. This is the ninth Chrome zero-day fixed this year by Google. This security bug (CVE-2022-4262; QID 377804) is a Type Confusion vulnerability in Chrome’s V8 JavaScript Engine.
Google has withheld details about the vulnerability to prevent expanding its malicious exploitation and to allow users time to apply the security updates necessary on their Chrome installations.
Google’s previous zero-days were also released right before a weekend (see Don’t spend another weekend patching Chrome and Don’t Spend Your Holiday Season Patching Chrome).

Organizations respond, but slowly
Analyzing anonymized data from the Qualys data lake, the Qualys Threat Research Unit found for Chrome zero-day vulnerabilities introduced between February and August, more than 90% of these instances were remediated. However, it took 11-21 days to remediate via the Chrome patch. With the frequency of vulnerabilities released in this widely used browser and the fact that browsers, by their nature, are more exposed to external attacks, reducing the MTTR for those Chrome vulnerabilities is critical.
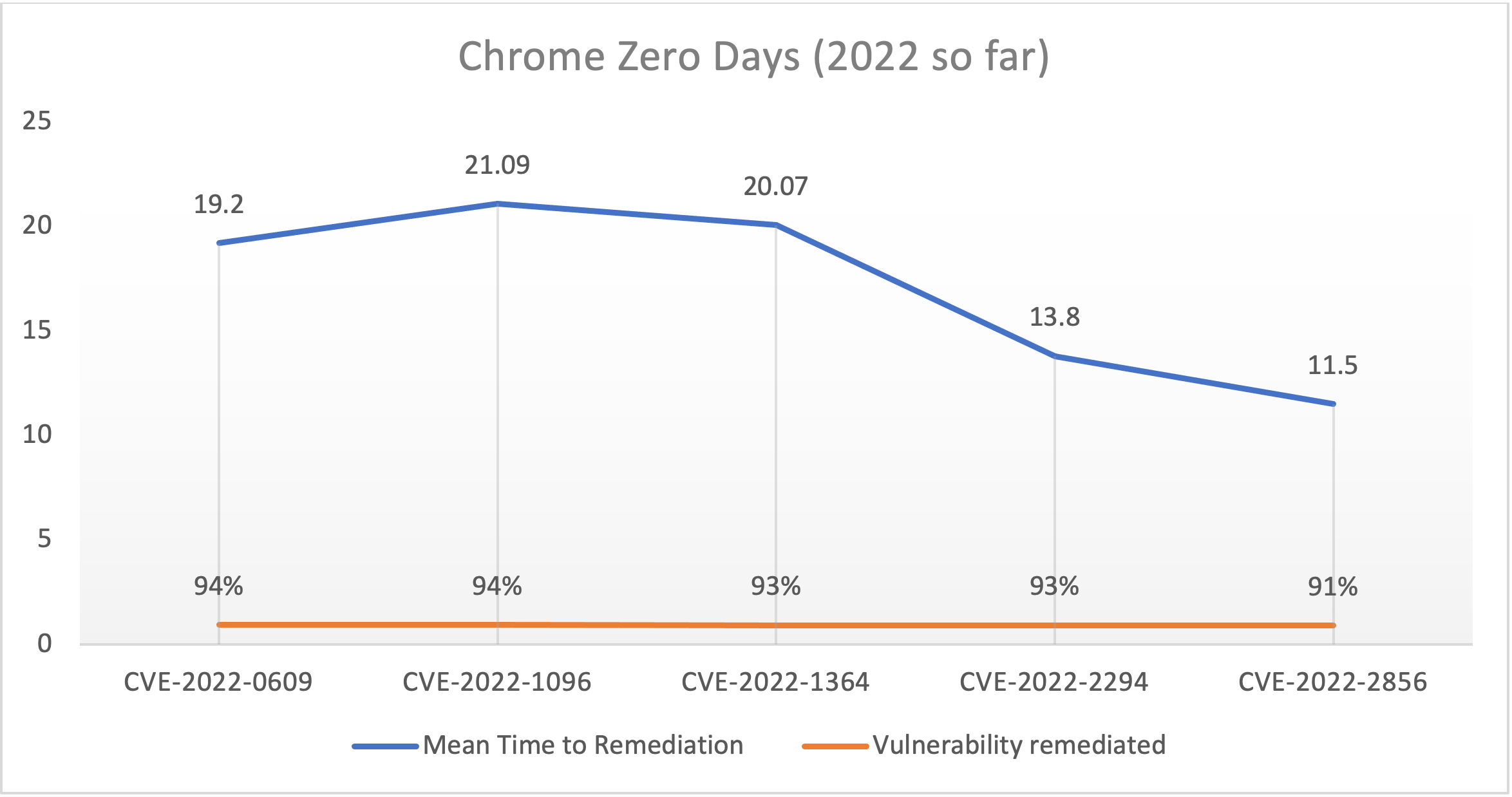 2022 Chrome Zero-Day Vulnerabilities, MTTR
2022 Chrome Zero-Day Vulnerabilities, MTTR
Of the nine Chrome zero-day threats this year, five were introduced just before the weekend on a Thursday or Friday. Organizations that don't leverage automated patching must spend the weekend or holiday working on the manual, lengthy process of detecting vulnerable devices, preparing the Chrome patch, testing it, and deploying it to affected assets.
| CVE | Release Date | Day of the Week | Vulnerability Remediation Rate |
|---|---|---|---|
| CVE-2022-0609 | 2/14/2022 | Monday | 94% |
| CVE-2022-1096 | 3/25/2022 | Friday | 94% |
| CVE-2022-1364 | 4/14/2022 | Thursday | 93% |
| CVE-2022-2294 | 7/4/2022 | Monday | 93% |
| CVE-2022-2856 | 8/16/2022 | Tuesday | 91% |
| CVE-2022-3075 | 9/2/2022 | Friday | 85% |
| CVE-2022-3723 | 10/27/2022 | Thursday | 65% |
| CVE-2022-4135 | 11/24/2022 | Thursday (Thanksgiving) | 52% |
| CVE-2022-4262 | 12/2/2022 | Friday | NA |
| 2022 Chrome Zero-Day vulnerability release dates and percentage of remediation |
Qualys Patch Management speeds remediation
The Qualys Threat Research Unit has found on average critical vulnerabilities are weaponized in 15.9 days. Significantly reducing MTTR shortens the exposure window and improves an organization's risk posture.
Qualys Patch Management with Zero-Touch Patching allows organizations to use their Qualys Cloud Agent for vulnerability management and to deploy third-party application patches, including Chrome. If the Qualys Cloud Agent is installed on an asset, customers can patch it, regardless of any other deployed patch solution. By defining a simple zero-touch policy, assets can automatically deploy patches when the vendor releases a new one. If testing patches like Chrome is required before production deployment, automatically setup a zero-touch policy to deploy to a set of test devices before deploying the same tested patches to production devices.
If you are a Qualys customer without Patch Management, a trial can be enabled quickly, leveraging the same agent used with VMDR. This allows you to immediately deploy the Chrome patch to your environment and create those automation jobs to ensure that the next time Google or any other vendor releases a patch, your assets are automatically updated.
9.6 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P