Researchers Uncover UEFI Secure Boot Bypass in 3 Microsoft Signed Boot Loaders
A security feature bypass vulnerability has been uncovered in three signed third-party Unified Extensible Firmware Interface (UEFI) boot loaders that allow bypass of the UEFI Secure Boot feature.
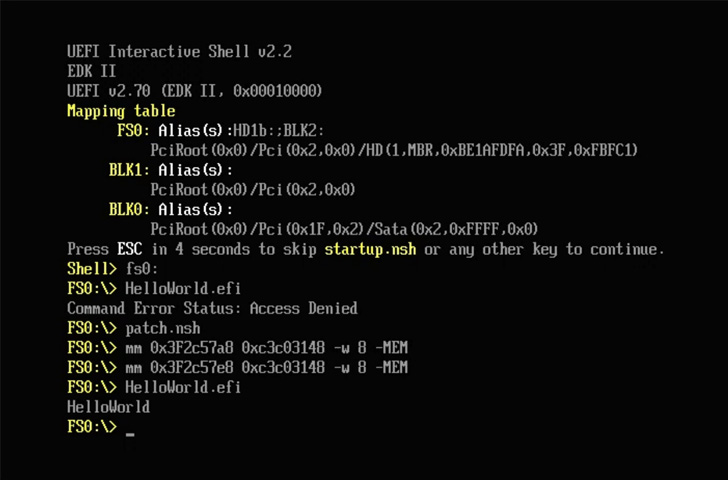
“These vulnerabilities can be exploited by mounting the EFI System Partition and replacing the existing bootloader with the vulnerable one, or modifying a UEFI variable to load the vulnerable loader instead of the existing one,” hardware security firm Eclypsium said in a report shared with The Hacker News.
The following vendor-specific boot loaders, which were signed and authenticated by Microsoft, have been found vulnerable to the bypass and have been patched as part of the tech giant’s Patch Tuesday update released this week -
- Eurosoft Boot Loader (CVE-2022-34301)
- New Horizon Data Systems Inc Boot Loader (CVE-2022-34302), and
- Crypto Pro Boot Loader (CVE-20220-34303)
Secure Boot is a security standard designed to thwart malicious programs from loading when a computer starts up (boots) and ensure only the software that is trusted by the Original Equipment Manufacturer (OEM) is launched.
“The firmware boot loaders boot the UEFI environment and hands over control to UEFI applications written by the SoC vendor, Microsoft, and OEMs,” Microsoft notes in its documentation. “The UEFI environment launches the Windows Boot Manager, which determines whether to boot to Full Flash Update (FFU) image flashing or device reset mode, to the update OS, or to the main OS.”
In a nutshell, successful exploitation of the flaws identified by Eclypsium could permit an adversary to circumvent security guardrails at startup and execute arbitrary unsigned code during the boot process.
This can have further knock-on effects, enabling a bad actor to gain entrenched access and establish persistence on a host through in a manner that can survive operating system reinstalls and hard drive replacements, not to mention completely bypassing detection by security software.
Calling CVE-2022-34302 “far more stealthy,” Eclypsium noted the New Horizon Datasys vulnerability is not only trivial to exploit in the wild, but can also “enable even more complex evasions such as disabling security handlers.”
Security handlers, for instance, can include Trusted Platform Module (TPM) measurements and signature checks, Eclypsium researchers Mickey Shkatov and Jesse Michael said.
It’s worth noting that exploiting these vulnerabilities requires an attacker to have administrator privileges, although gaining local privilege escalation is not considered insurmountable owing to the fact that Microsoft doesn’t treat User Account Control (UAC) bypass as a security risk.
“Much like BootHole, these vulnerabilities highlight the challenges of ensuring the boot integrity of devices that rely on a complex supply chain of vendors and code working together,” the researchers concluded, adding “these issues highlight how simple vulnerabilities in third-party code can undermine the entire process.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.