
August 2022 Patch Tuesday | Microsoft Releases 121 Vulnerabilities with 17 Critical, plus 20 Microsoft Edge (Chromium-Based); Adobe Releases 5 Advisories, 25 Vulnerabilities with 15 Critical.
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C
Microsoft Patch Tuesday Summary
Microsoft has fixed 121 vulnerabilities (aka flaws) in the August 2022 update, including 17 vulnerabilities classified as Critical as they allow Elevation of Privilege (EoP) and Remote Code Execution (RCE). This month's Patch Tuesday fixes two (2) zero-day vulnerabilities, with one (1) actively exploited***** in attacks (CVE-2022-34713*****, CVE-2022-30134). Earlier this month, August 5, 2022, Microsoft also released 20 Microsoft Edge (Chromium-Based) updates addressing Elevation of Privilege (EoP), Remote Code Execution (RCE), and Security Feature Bypass with severities of Low, Moderate, and Important respectively.
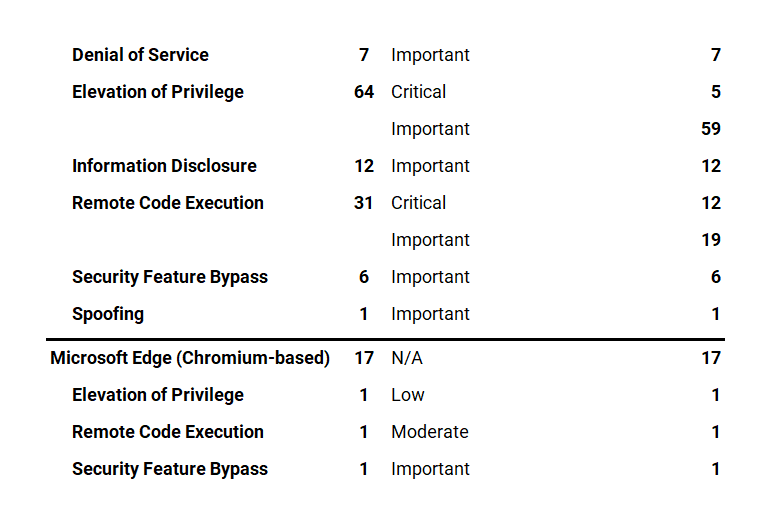
Microsoft has fixed several flaws in its software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Microsoft Edge (Chromium-based), Remote Code Execution (RCE), Security Feature Bypass, and Spoofing.
The August 2022 Microsoft vulnerabilities are classified as follows:
 Related Threat Protection Post
Related Threat Protection Post
Notable Microsoft Vulnerabilities Patched
A vulnerability is classified as a zero-day if it is publicly disclosed or actively exploited with no official fix available.
CVE-2022-34713 | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8/10.
In May, Microsoft released a blog giving guidance for a vulnerability in MSDT and released updates to address it shortly thereafter. Public discussion of a vulnerability can encourage further scrutiny on the component, both by Microsoft security personnel as well as their research partners. This CVE is a variant of the vulnerability publicly known as Dogwalk.
Exploitability Assessment: Exploitation Detected
>  Qualys director of vulnerability and threat research, Bharat Jogi, said DogWalk had actually been reported back in 2019 but at the time was not thought to be dangerous as it required “significant user interaction to exploit,” and there were other mitigations in place.
Qualys director of vulnerability and threat research, Bharat Jogi, said DogWalk had actually been reported back in 2019 but at the time was not thought to be dangerous as it required “significant user interaction to exploit,” and there were other mitigations in place.
>
> - Excerpt from Surge in CVEs as Microsoft Fixes Exploited Zero Day Bug
CVE-2022-30134 | Microsoft Exchange Information Disclosure Vulnerability
This vulnerability has a CVSSv3.1 score of 7.6/10.
This vulnerability requires that a user with an affected version of Exchange Server access a malicious server. An attacker would have to host a specially crafted server share or website. An attacker would have no way to force users to visit this specially crafted server share or website, but would have to convince them to visit the server share or website, typically by way of an enticement in an email or chat message. For more information, see Exchange Server Support for Windows Extended Protection and/or The Exchange Blog.
Exploitability Assessment: Exploitation Unlikely
Security Feature Bypass Vulnerabilities Addressed
These are standalone security updates. These packages must be installed in addition to the normal security updates to be protected from this vulnerability.
These security updates have a Servicing Stack Update prerequisite for specific KB numbers. The packages have a built-in pre-requisite logic to ensure the ordering.
Microsoft customers should ensure they have installed the latest Servicing Stack Update before installing these standalone security updates. See ADV990001 | Latest Servicing Stack Updates for more information.
An attacker who successfully exploited either of these three (3) vulnerabilities could bypass Secure Boot.
CERT/CC: CVE-2022-34301 Eurosoft Boot Loader Bypass
CERT/CC: CVE-2022-34302 New Horizon Data Systems Inc Boot Loader Bypass
CERT/CC: CVE-2022-34303 Crypto Pro Boot Loader Bypass
At the time of publication, a CVSSv3.1 score has not been assigned.
Exploitability Assessment: **Exploitation More Like**ly
Microsoft Critical and Important Vulnerability Highlights
This month’s advisory covers multiple Microsoft product families, including Azure, Browser, Developer Tools, Extended Security Updates (ESU), Exchange Server, Microsoft Office, System Center, and Windows.
A total of 86 unique Microsoft products/versions are affected, including .NET, Azure, Edge (Chromium-based), Excel, Exchange Server (Cumulative Update), Microsoft 365 Apps for Enterprise, Office, Open Management Infrastructure, Outlook, and System Center Operations Manager (SCOM), Visual Studio, Windows Desktop, and Windows Server.
Downloads include IE Cumulative, Monthly Rollup, Security Only, and Security Updates.
CVE-2022-35766, CVE-2022-35794 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1/10.
Successful exploitation of this vulnerability requires an attacker to win a race condition.
An unauthenticated attacker could send a specially crafted connection request to a RAS server, which could lead to remote code execution (RCE) on the RAS server machine.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-30133, CVE-2022-35744 | Windows Point-to-Point Protocol (PPP) Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
This vulnerability can only be exploited by communicating via Port 1723. As a temporary workaround prior to installing the updates that address this vulnerability, you can block traffic through that port thus rendering the vulnerability unexploitable. Warning: Disabling Port 1723 could affect communications over your network.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-34691 | Active Directory Domain Services Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
This vulnerability can only be exploited by communicating via Port 1723. As a temporary workaround An authenticated user could manipulate attributes on computer accounts they own or manage, and acquire a certificate from Active Directory Certificate Services that would allow elevation of privilege to System.
Please see Certificate-based authentication changes on Windows domain controllers for more information and ways to protect your domain.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-33646 | Azure Batch Node Agent Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.0/10.
Successful exploitation of this vulnerability requires an attacker to prepare the target environment to improve exploit reliability.
Exploitability Assessment: Exploitation More Likely
Microsoft Edge | Last But Not Least
Earlier in August, Microsoft released Microsoft Edge (Chromium-based) vulnerabilities CVE-2022-33636, CVE-2022-33649, and CVE-2022-35796. The vulnerability assigned to each of these CVEs is in the Chromium Open Source Software (OSS) which is consumed by Microsoft Edge. It is being documented in the Security Update Guide to announce that the latest version of Microsoft Edge (Chromium-based) is no longer vulnerable. For more information, please see Security Update Guide Supports CVEs Assigned by Industry Partners.
CVE-2022-33649 | Microsoft Edge (Chromium-based) Security Feature Bypass Vulnerability
This vulnerability has a CVSSv3.1 score of 9.6/10.
An attacker could host a specially crafted website designed to exploit the vulnerability through Microsoft Edge and then convince a user to view the website. However, in all cases an attacker would have no way to force a user to view the attacker-controlled content. Instead, an attacker would have to convince a user to take action, typically by an enticement in an email or instant message, or by getting the user to open an attachment sent through email.
The user would have to click on a specially crafted URL to be compromised by the attacker.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-33636, CVE-2022-35796 | Microsoft Edge (Chromium-based) Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.3/10. Per Microsoft's severity guidelines, the amount of user interaction or preconditions required to allow this sort of exploitation downgraded the severity. The CVSS scoring system doesn't allow for this type of nuance.
An attacker could host a specially crafted website designed to exploit the vulnerability through Microsoft Edge and then convince a user to view the website. However, in all cases, an attacker would have no way to force a user to view the attacker-controlled content. Instead, an attacker would have to convince a user to take action, typically by an enticement in an email or instant message, or by getting the user to open an attachment sent through email.
Successful exploitation of this vulnerability requires an attacker to win a race condition.
Exploitability Assessment: Exploitation Less Likely
Adobe Security Bulletins and Advisories
Adobe released five (5) advisories with updates to fix 25 vulnerabilities affecting Adobe Acrobat and Reader, Commerce, FrameMaker, Illustrator, and Premiere Elements applications. Of these 25 vulnerabilities, 15 are rated as Critical; ranging in severity from a CVSS score of 7.8/10 to 9.1/10, as summarized below.

APSB22-38 | Security update available for Adobe Commerce
This update resolves seven (7) vulnerabilities:
Adobe has released a security update for Adobe Commerce and Magento Open Source. This update resolves critical, important, and moderate vulnerabilities. Successful exploitation could lead to arbitrary code execution, privilege escalation, and security feature bypass.
APSB22-39 | Security update available for Adobe Acrobat and Reader
This update resolves seven (7) vulnerabilities:
Adobe has released security updates for Adobe Acrobat and Reader for Windows and macOS. These updates address multiple critical and important vulnerabilities. Successful exploitation could lead to arbitrary code execution and memory leak.
APSB22-41 | Security Updates Available for Adobe Illustrator
This update resolves four (4) vulnerabilities:
Adobe has released an update for Adobe Illustrator 2022. This update resolves critical and important vulnerabilities that could lead to arbitrary code execution and memory leak.
APSB22-42 | Security update available for Adobe FrameMaker
This update resolves six (6) vulnerabilities:
Adobe has released a security update for Adobe FrameMaker. This update addresses multiple critical and important vulnerabilities. Successful exploitation could lead to arbitrary code execution
and memory leak.
APSB22-43 | Security update available for Adobe Premiere Elements
This update resolves one (1) Critical vulnerability.
Adobe has released a security update for Adobe FrameMaker. This update addresses multiple critical and important vulnerabilities. Successful exploitation could lead to arbitrary code execution
and memory leak.
About Qualys Patch Tuesday
Qualys Patch Tuesday QIDs are published as Security Alerts typically late in the evening on the day of Patch Tuesday, followed later by the publication of the monthly queries for the Unified Dashboard: 2022 Patch Tuesday (QID Based) Dashboard by Noon on Wednesday.
Qualys Threat Protection High-Rated Advisories for August 1-9, 2022 New Content
- Microsoft Patches 121 Vulnerabilities with Two Zero-days and 17 Critical; Plus 20 Microsoft Edge (Chromium-Based) in August 2022 Patch Tuesday
- VMware vRealize Operations Multiple Vulnerabilities Patched in the Latest Security update (CVE-2022-31672, CVE-2022-31673, CVE-2022-31674, & CVE-2022-31675)
- Cisco Patched Small Business RV Series Routers Multiple Vulnerabilities (CVE-2022-20827, CVE-2022-20841, and CVE-2022-20842)
- VMware Patched Multiple Vulnerabilities in VMware Products including Identity Manager (vIDM) and Workspace ONE Access
- Atlassian Confluence Server and Confluence Data Center – Questions for Confluence App – Hardcoded Password Vulnerability (CVE-2022-26138)
Discover and Prioritize Vulnerabilities in Vulnerability Management Detection Response (VMDR)
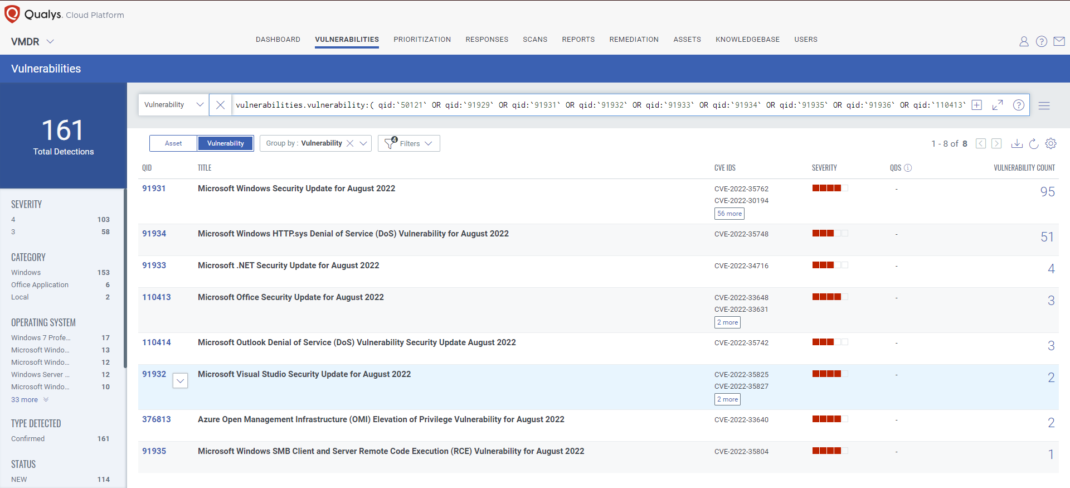
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its KnowledgeBase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:( qid:`50121` OR qid:`91929` OR qid:`91931` OR qid:`91932` OR qid:`91933` OR qid:`91934` OR qid:`91935` OR qid:`91936` OR qid:`110413` OR qid:`110414` OR qid:`376813` )
 A Deep Dive into VMDR 2.0 with Qualys TruRisk™ The old way of ranking vulnerabilities doesn’t work anymore. Instead, enterprise security teams need to rate the true risks to their business. In this blog, we examine each of the risk scores delivered by Qualys TruRisk, the criteria used to compute them, and how they can be used to prioritize remediation.
A Deep Dive into VMDR 2.0 with Qualys TruRisk™ The old way of ranking vulnerabilities doesn’t work anymore. Instead, enterprise security teams need to rate the true risks to their business. In this blog, we examine each of the risk scores delivered by Qualys TruRisk, the criteria used to compute them, and how they can be used to prioritize remediation.
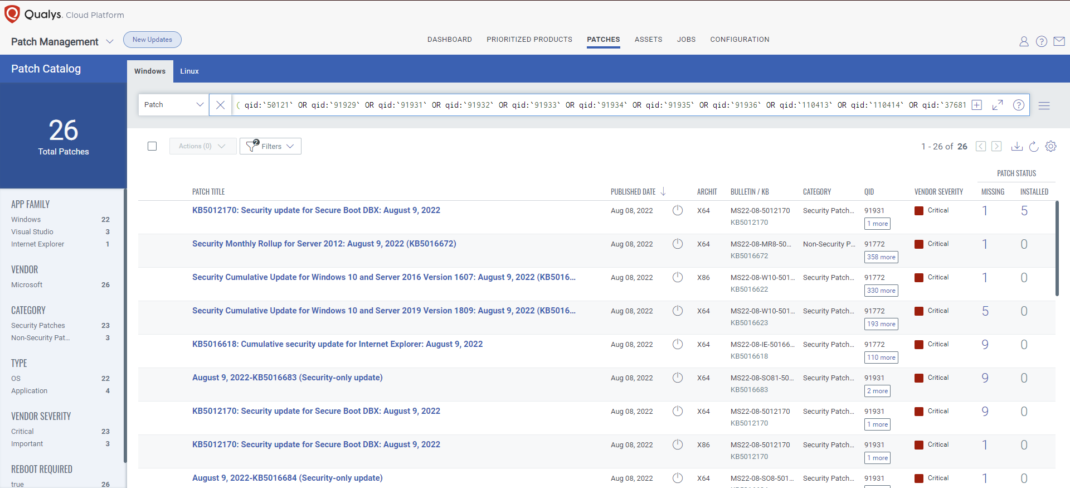
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go.
The following QQL will return the missing patches for this Patch Tuesday:
( qid:`50121` OR qid:`91929` OR qid:`91931` OR qid:`91932` OR qid:`91933` OR qid:`91934` OR qid:`91935` OR qid:`91936` OR qid:`110413` OR qid:`110414` OR qid:`376813` )
 Risk-based Remediation Powered by Patch Management in Qualys VMDR 2.0
Risk-based Remediation Powered by Patch Management in Qualys VMDR 2.0
Evaluate Vendor-Suggested Workarounds with Policy Compliance New Content
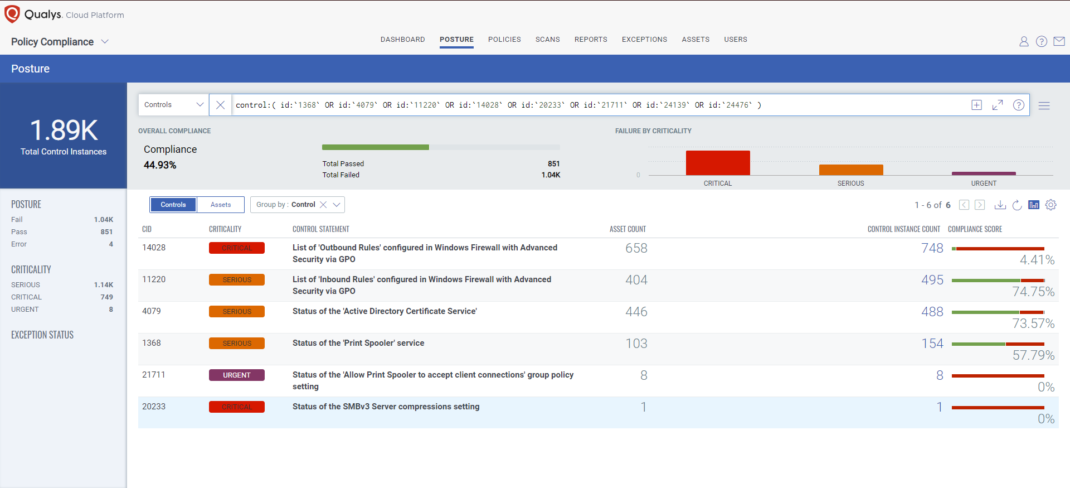
Qualys’ Policy Compliance Control Library makes it easy to evaluate your technology infrastructure when the current situation requires the implementation of a vendor-suggested workaround. A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn't working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned. _ Source_
The following Qualys Policy Compliance Control IDs (CIDs), and System Defined Controls (SDC) have been updated to support Microsoft recommended workaround for this Patch Tuesday:
CVE-2022-35793 | Windows Print Spooler Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.3/10.
Policy Compliance Control IDs (CIDs):
- 1368: Status of the ‘Print Spooler’ service
- 21711: Status of the ‘Allow Print Spooler to accept client connections’ group policy setting
Exploitability Assessment: Exploitation More Likely
CVE-2022-35804 |SMB Client and Server Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
Policy Compliance Control IDs (CIDs):
- 24476: Status of the SMBv3 Client compressions setting
- 20233: Status of the SMBv3 Server compressions setting
Exploitability Assessment: Exploitation More Likely
CVE-2022-35755 |Windows Print Spooler Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.3/10.
Policy Compliance Control IDs (CIDs):
- 1368: Status of the ‘Print Spooler’ service
Exploitability Assessment: Exploitation More Likely
CVE-2022-30133,CVE-2022-35744|Windows Point-to-Point Protocol (PPP) Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
Policy Compliance Control IDs (CIDs):
- 11220: List of ‘Inbound Rules’ configured in Windows Firewall with Advanced Security via GPO
- 14028: List of ‘Outbound Rules’ configured in Windows Firewall with Advanced Security via GPO
Exploitability Assessment: Exploitation Less Likely
CVE-2022-34715: Windows Network File System Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
Policy Compliance Control IDs (CIDs):
- 24139: Status of the Windows Network File System (NFSV4) service
Exploitability Assessment: Exploitation Less Likely
CVE-2022-34691: Active Directory Domain Services Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
Policy Compliance Control IDs (CIDs):
- 4079: Status of the ‘Active Directory Certificate Service’
Exploitability Assessment: Exploitation Less Likely
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control:( id:`1368` OR id:`4079` OR id:`11220` OR id:`14028` OR id:`20233` OR id:`21711` OR id:`24139` OR id:`24476` )
 Mitigating the Risk of Zero-Day Vulnerabilities by using Compensating Controls
Mitigating the Risk of Zero-Day Vulnerabilities by using Compensating Controls
 Policy Compliance (PC) | Policy Library Update Blogs
Policy Compliance (PC) | Policy Library Update Blogs
Patch Tuesday is Complete.
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are part of this month's Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C