
Cerber targeting organizations with publicly available exploits
EPSS
Percentile
99.9%
THREAT LEVEL: Red.
For a detailed advisory, download the pdf file here.
Cerber, ransomware that mysteriously vanished in 2019, has reappeared with a new encryption. The new cerber includes fresh source code and makes use of the new library Crypto+++, whereas the previous form made use of Windows CryptoAPI libraries.
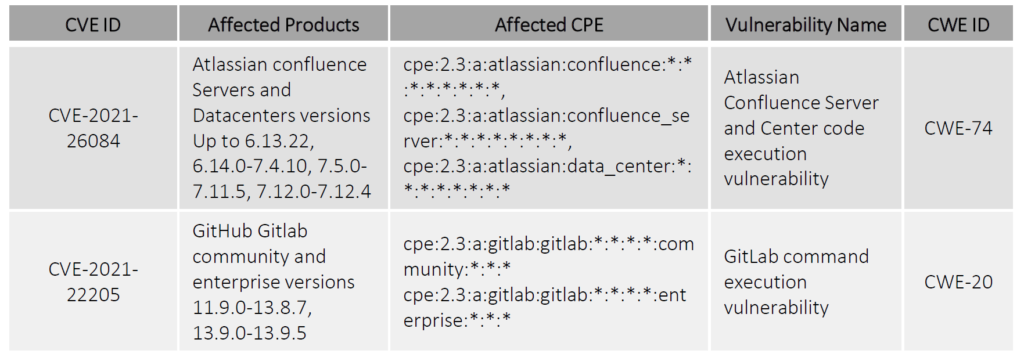
Cerber is utilizing the following two vulnerabilities: -CVE-2021-26084: a remote code execution vulnerability that allows an attacker to execute arbitrary code in Atlassian Confluence Servers and Datacenters versions 6.13.22, 6.14.0-7.4.10, 7.5.0-7.11.5, 7.12.0-7.12.4. It has been fixed in versions 6.13.23, 7.4.11, 7.11.6, and 7.12.5. -CVE-2021-22205: GitHub Gitlab community and enterprise versions 11.9.0-13.8 are affected by a command execution vulnerability that can be exploited by uploading an image that runs via the ExifTool of GitLab Workhorse and achieving remote code execution via a specially designed file. It has been fixed in version 13.9.
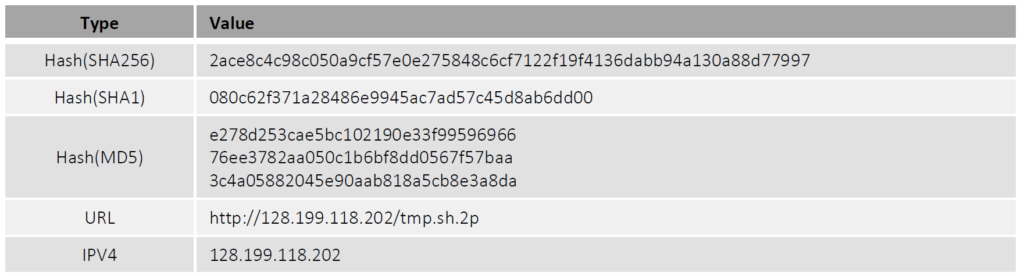
The new Cerber ransomware uses either of the two vulnerabilities mentioned above and then enters victims' systems and encrypts their files. Cerber ransomware places the ransom note in the file $$RECOVERY_README$$.html, and all the encrypted files have an extension of .locked.
Organizations can patch both vulnerabilities by upgrading their systems to fixed versions.
The TTP's used by Cerber includes:
TA0002 - Execution
T1059 - Command and Scripting Interpreter
T1059.003 - Command and Scripting Interpreter: Windows Command Shell
TA0007 - Discovery
T1012 - Query Registry
T1082 - System Information Discovery
Vulnerability Details
Indicators of Compromise(IoCs)
Patch Links
<https://jira.atlassian.com/browse/CONFSERVER-67940>
References
<https://gitlab.com/gitlab-org/gitlab/-/issues/327121>
<https://otx.alienvault.com/pulse/61af78ee529faac40b2de15e/related>
<https://app.any.run/tasks/c59f562e-4a61-459c-b0a3-9890c412b0ea/>