
Qualys Tackles 2022’s Top Routinely Exploited Cyber Vulnerabilities
EPSS
Percentile
100.0%
A unified front against malicious cyber actors is climactic in the ever-evolving cybersecurity landscape. The joint Cybersecurity Advisory (CSA), a collaboration between leading cybersecurity agencies from the United States, Canada, United Kingdom, Australia, and New Zealand, is a critical guide to strengthen global cyber resilience. The agencies involved include the U.S.'s CISA, NSA, and FBI; Canada's CCCS; U.K.'s NCSC-UK; Australia's ACSC; and New Zealand's NCSC-NZ and CERT NZ.
This collaboration among key cybersecurity agencies highlights the global nature of cybersecurity threats. Such cooperative efforts signify a unified perspective and highlight the need for shared intelligence and coordinated strategies. The realization that cybersecurity is not limited to national borders but is a shared responsibility is growing more evident.
The CSA sheds light on the Common Vulnerabilities and Exposures (CVEs) routinely and frequently exploited in 2022 and the associated Common Weakness Enumeration(s) (CWE). It outlines crucial technical details and key findings, providing actionable guidance and mitigation strategies. Vendors, designers, developers, and end-user organizations are strongly urged to implement these guidelines to strengthen their defenses against possible threats.
The Cybersecurity Advisory (CSA) has identified the following key findings that outline essential insights into the behaviors and tendencies of malicious cyber actors for 2022:
- Older Vulnerabilities Targeted: Malicious cyber actors exploited older software vulnerabilities more frequently, targeting unpatched, internet-facing systems.
- Proof of Concept (PoC) Code: Public availability of PoC code likely facilitated broader exploitation by malicious actors.
- Success in First Two Years: Known vulnerabilities are most successfully exploited within the first two years of disclosure. Timely patching reduces this effectiveness.
- Prioritization of Severe CVEs: Cyber actors prioritize severe and globally prevalent vulnerabilities, seeking low-cost, high-impact tools and paying attention to vulnerabilities principal in specific targets' networks.
- Detection through Deep Packet Inspection: Deep packet inspection can often detect exploits involving multiple CVE or CVE chains.
In 2022, malicious cyber actors routinely exploited 12 severe vulnerabilities, affecting various products and services. These issues included the long-exploited Fortinet SSL VPNs' CVE-2018-13379 and widespread vulnerabilities such as Apache's Log4Shell (CVE-2021-44228). They impacted multiple systems, from Microsoft Exchange email servers to Atlassian Confluence and software like Zoho ManageEngine and VMware. The exploitation often resulted from organizations' failure to patch software or due to publicly available proofs of concept (PoC), enabling remote execution, privilege escalation, and authentication bypass. The table below shows detailed information on these 12 vulnerabilities, along with Qualys-provided QIDs. A crucial commonality between these vulnerabilities is their potential to compromise system integrity, confidentiality, and availability severely. The Qualys Threat Research Unit (TRU) team has addressed all aforementioned critical vulnerabilities by providing QIDs within 24 hours. These critical vulnerabilities are categorized based on their potential impact if exploited as follows:
| CVE/Vuln Name | Vendor/Product | Type | QID | QDS |
|---|---|---|---|---|
| CVE-2018-13379 | Fortinet - FortiOS and FortiProxy | SSL VPN Credential Exposure | 43702 | 100 |
| CVE-2021-34473 (Proxy Shell) | Microsoft - Exchange Server | RCE | 50114, 50107 | 100 |
| CVE-2021-31207 (Proxy Shell) | Microsoft - Exchange Server | Security Feature Bypass | 50114, 50111 | 95 |
| CVE-2021-34523 (Proxy Shell) | Microsoft - Exchange Server | Elevation of Privilege | 50114, 50112 | 100 |
| CVE-2021-40539 | Zoho ManageEngine - ADSelfService Plus | RCE/Authentication Bypass | 375840 | 100 |
| CVE-2021-26084 | Atlassian - Confluence Server and Data Center | Arbitrary code execution | 375839, 730172 | 100 |
| CVE-2021-44228 (Log4Shell) | Apache - Log4j2 | RCE | 730447, 376521 | 100 |
| CVE-2022-22954 | VMware - Workspace ONE Access and Identity Manager | RCE | 730447, 376521 | 100 |
| CVE-2022-22960 | VMware - Workspace ONE Access, Identity Manager, and vRealize Automation | Improper Privilege Management | 376521 | 95 |
| CVE-2022-1388 | F5 Networks - BIG-IP | Missing Authentication Vulnerability | 730489, 376577 | 96 |
| CVE-2022-30190 (Follina) | Microsoft - Multiple Products | RCE | 91909 | 100 |
| CVE-2022-26134 | Atlassian - Confluence Server and Data Center | RCE | 376657, 730514 | 100 |
Vulnerabilities Paving the Way for Data Theft and More:
The following vulnerabilities that could potentially lead to data theft or lay the groundwork for further attacks:
- CVE-2018-13379, a flaw in the Fortinet FortiOS SSL VPN web portal, could be leveraged by attackers to gain unauthorized access to sensitive SSL VPN session data.
- CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207, collectively known as ProxyShell vulnerabilities affecting Microsoft Exchange Servers, could enable bad actors to deploy web shells and execute arbitrary code on compromised devices.
- CVE-2022-1388, an F5 BIG-IP iControl REST API vulnerability, could offer initial network access to cyber criminals, enabling infamous activities like data theft or ransomware deployment.
Vulnerabilities Leading to System Takeover:
Next, the following vulnerabilities that could potentially compromise an entire system:
- CVE-2021-44228, or Log4Shell, exploits Apache's log4j Java library, possibly leading to a total system compromise.
- CVE-2021-26084 and CVE-2022-26134, vulnerabilities found in Atlassian's Confluence Server and Data Center, can allow an attacker to execute arbitrary code, leading to a potential system takeover.
- CVE-2021-40539, an issue with Zoho ManageEngine ADSelfService Plus, can allow for arbitrary code execution and potential system compromise.
- CVE-2022-30190, found in the Microsoft Support Diagnostic Tool, can be exploited for remote code execution, potentially leading to full system compromise.
- CVE-2022-22954 and CVE-2022-22960, affecting VMware Workspace ONE Access, Identity Manager, and vRealize Automation, can allow for remote code execution and privilege escalation, respectively, potentially leading to full system compromise.
Analyzing Vulnerability Remediation Patterns and the Urgency of Swift Patching
Our data, which sheds light on the patching behavior for 12 significant vulnerabilities, is pulled from the Qualys TruRisk Platform. This data is anonymized to ensure that any data analysis cannot revert to identifying specific organization or asset information.
The data highlights a prominent challenge where some vulnerabilities witness rapid mitigation, highlighting proactive security measures. In contrast, others face prolonged remediation times, raising concerns about potential exposure risks. Such disparities underline the importance of detecting and swiftly addressing vulnerabilities. As cyber threats grow in sophistication, the urgency to patch quickly and efficiently becomes paramount. The following plot contrasting the patch rates and remediation times for 12 frequently exploited vulnerabilities in 2022 further illustrates this point. It shows that while some vulnerabilities are quickly patched, others remain unaddressed for extended periods. This analysis reinforces the importance of timely vulnerability management and the pressing need to do so with speed and diligence, especially for high-risk vulnerabilities.
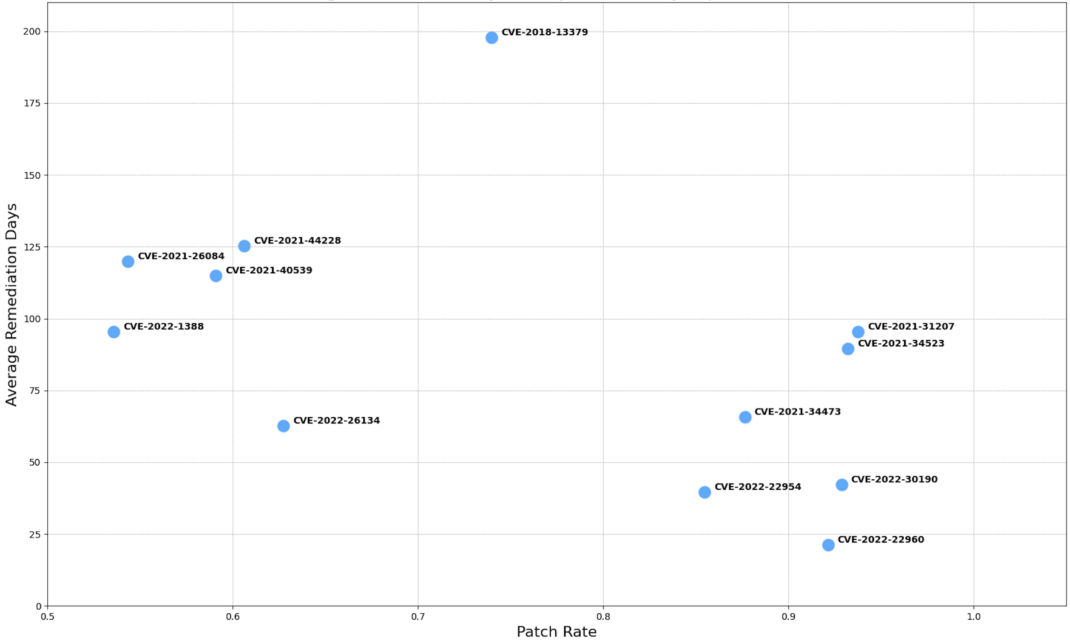
Fig 1. Patch Rate vs. Average Remediation Days for Top 12 Routinely Exploited Vulnerabilities in 2022
The damaging potential of these vulnerabilities highlights the vital importance of cybersecurity alertness. By understanding the risks and possible impacts of these threats, organizations can adopt proactive defense strategies, patching vulnerabilities and updating systems regularly to ensure the integrity of their environments. The advisory also emphasizes the criticality of accurately incorporating the CWE field in published CVEs to highlight vulnerability root causes and support industry-wide software security insights.
Aligning Qualys Platform with Joint Cybersecurity Advisory Mitigating Guidelines
The recent joint Cybersecurity Advisory (CSA) emphasizes the urgency of identifying exploited vulnerabilities, keeping all network assets updated, and implementing a robust patch management process. Among the recommendations are the timely updating of software, prioritizing patches for known vulnerabilities, performing automated asset discovery, and implementing centralized patch management.
Qualys' suite of products directly aligns with these critical recommendations. Qualys Cybersecurity Asset Management (CSAM) ensures 360-degree visibility of assets, aligning with CSA's call for comprehensive asset discovery. Qualys Patch Management offers an advanced automated solution for timely updates, while Qualys VMDR facilitates the discovery, assessment, and prioritization of vulnerabilities. By leveraging Qualys' unified platform, organizations can efficiently adhere to international best practices outlined in the CSA, enhancing their defense against cyber threats.
In addition, the joint Cybersecurity Advisory (CSA) stresses the need for robust protective controls and architecture. Key recommendations include securing internet-facing network devices, continuously monitoring the attack surface, and prioritizing secure-by-default configurations. There is a strong focus on hardening network protocols, managing access controls, and employing security tools such as EDR and SIEM for enhanced protection.
Qualys Threat Protection aligns seamlessly with these recommendations by providing centralized control and comprehensive visibility of the threat landscape. By continuously correlating external threat information against vulnerabilities and the IT asset inventory, Qualys allows organizations to pinpoint and prioritize the most critical security threats. Whether managing vulnerabilities, controlling the threat prioritization process, or ensuring compliance with regulations, Qualys empowers organizations to align with the CSA's guidelines and achieve a fortified security posture.
Qualys TotalCloud also employs deep learning AI to continuously monitor the attack surface and investigate abnormal activity, aligning with CSA guidelines. It is leveraging an interconnected artificial neural network that detects known and unknown malware with over 99% accuracy in less than a second. Through these capabilities, Qualys TotalCloud delivers an advanced, rapid, and precise solution for malware detection in multi-cloud environments and bypassing the limitations of signature-based systems.
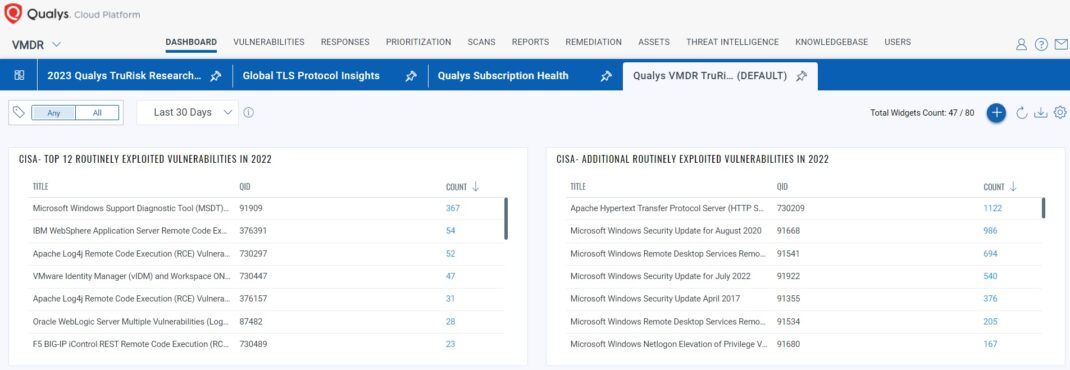
Fig 2. Qualys VMDR TruRisk Dashboard for top 12 routinely exploited vulnerabilities in 2022
The Qualys VMDR TruRisk Dashboard (JSON zipped) helps organizations to have complete visibility into open vulnerabilities that focus on the organization’s global risk score, high-risk vulnerabilities, and Top Exploited Vulnerabilities. Once you identify the vulnerable assets for these top vulnerable CVEs prioritized among your remediation owners, you can instantly use Qualys Patch management to reduce the risk.
In conclusion, this Cybersecurity Advisory (CSA) offers valuable insights and mitigation strategies against routine vulnerabilities. Qualys provides robust solutions that align seamlessly with CSA's recommendations, including asset management, timely updates, vulnerability prioritization, and advanced threat detection capabilities in this growing landscape. Consequently, organizations can strengthen their defenses against cyber threats by sticking to CSA guidelines and leveraging comprehensive cybersecurity solutions like Qualys'.
References
Additional Contributor
- Ramesh Ramachandran, Principal Product Manager, Qualys
- Aubrey Perin, Lead Threat Intelligence Analyst, Qualys