
Qualys Top 20 Most Exploited Vulnerabilities
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
0.976 High
EPSS
Percentile
100.0%
The earlier blog posts showcased an overview of the vulnerability threat landscape that is either remotely exploited or most targeted by attackers._ _A quick recap – We focused on high-risk vulnerabilities that can be remotely exploited with or without authentication, and with the view on the time to CISA being down to 8 days, the most vulnerabilities targeted by threat actors, malware & ransomware.
This blog post will focus on **Qualys’ Top Twenty Vulnerabilities,**targeted by threat actors, malware, and ransomware, with recent trending/sightings observed in the last few years and the current year.
Some of these vulnerabilities are part of the recent CISA Joint Cybersecurity Advisory (CSA), published on August 3, 2023; you can access it from 2022 Top Routinely Exploited Vulnerabilities.
Read on-
Stats on the Top 20 Vulnerable Vendors & By-Products
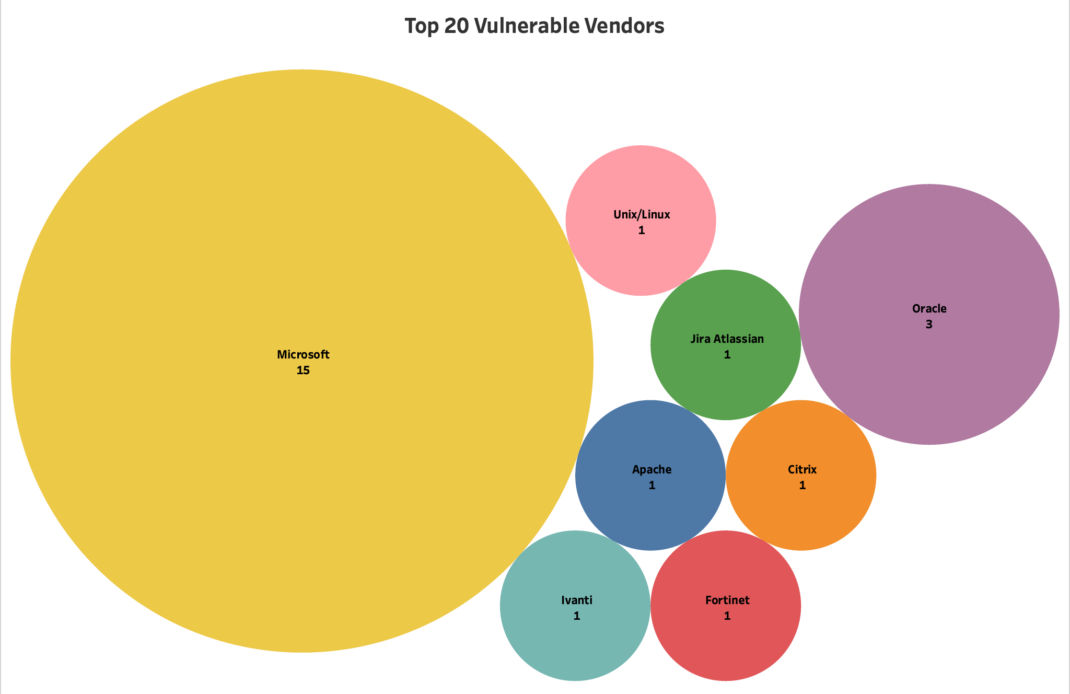 Fig 1. Top Vulnerable Vendor
Fig 1. Top Vulnerable Vendor
 Fig 2. Top Vulnerable Products
Fig 2. Top Vulnerable Products
Top Twenty Most Targeted by Attackers
1. CVE-2017-11882: Microsoft Office Memory Corruption Vulnerability
Vulnerability Trending Over Years: 2018, 2020, 2021, 2022, 2023 (79 times)
It was exploited by 467 Malware, 53 Threat Actors, and 14 Ransomware and was trending in the wild as recently as August 31, 2023.
In the "Additional Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.
Qualys Vulnerability Detection (QID): 110308
Disclosed in 2017, CVE-2017-11882 is a significant memory corruption vulnerability in Microsoft Office's Equation Editor. It could enable an attacker to execute arbitrary code under the current user's permissions.
If the user has administrative rights, the attacker could gain complete control of the system, install programs, alter data, or create new user accounts with full privileges. This vulnerability will be exploited if the user opens a specially crafted file, potentially sent via email or hosted on a compromised website.
It’s been primarily exploited in various cyber-attacks and espionage campaigns.
2. CVE-2017-0199: Microsoft Wordpad Remote Code Execution Vulnerability
Vulnerability Trending Over Years: 2017, 2020, 2021, 2023 (59 times)
It was exploited by 93 Malware, 53 Threat Actors, and 5 Ransomware and was trending in the wild as recently as September 4, 2023.
Qualys Vulnerability Detection (QID): 110297
In the "Additional Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.
CVE-2017-0199 is a notable remote code execution vulnerability that affects specific Microsoft Office and WordPad versions precisely when they parse specially crafted files. This vulnerability is the most favored vulnerability by malware, threat actors, and ransomware.
If successfully exploited, an attacker could execute arbitrary code in the current user's security context, potentially taking control of the system. Exploitation involves a user opening or previewing a maliciously crafted file, often sent via email. Microsoft has addressed this vulnerability by correcting how Office and WordPad parse these files and by enabling certain API functionality in Windows for further resolution.
3. CVE-2012-0158: Vulnerability in Windows Common Controls Could Allow RCE
Vulnerability Trending Over Years: 2013, 2020, 2021, 2023 (33 times)
It was exploited by 63 Malware, 45 Threat Actors, 2 Ransomware and was trending in the wild as recently as August 31, 2023.
Qualys Vulnerability Detection (QID): 90793
CVE-2012-0158 is a substantial remote code execution vulnerability in Windows standard controls. An attacker can exploit the flaw by constructing a specially crafted webpage. Upon viewing this webpage, the vulnerability can allow remote code execution, potentially granting the attacker the same rights as the logged-on user.
If the user has administrative privileges, this could mean total control of the affected system. Disclosed in 2012, this vulnerability has been notably exploited in various cyber-attacks, enabling attackers to install programs, manipulate data, or create new accounts with full user rights.
4. CVE-2017-8570: Microsoft Office Remote Code Execution Vulnerability
Vulnerability Trending Over Years: 2018, 2020, 2023 (25 times)
It was exploited by 52 Malware 11 Threat Actors and was trending in the wild as recently as September 2, 2023
Qualys Vulnerability Detection (QID): 110300
CVE-2017-8570 is a significant remote code execution vulnerability in Microsoft Office and WordPad. It involves the way these applications handle specially crafted files. It can be exploited by an attacker who convinces a user to open a specially designed file, potentially allowing the attacker to run arbitrary code on the victim's machine with the same privileges as the logged-in user and serving as a downloader to other high-profile malware.
5. CVE-2020-1472: Zerologon - An Unauthenticated Privilege Escalation to Full Domain Privileges
Vulnerability Trending Over Years: 2020, 2021, 2022, 2023 (56 times)
It was exploited by 18 Malware, 16 Threat Actors, 11 Ransomware and was trending in the wild as recently as September 4, 2023.
**Qualys Vulnerability Detection (QID):**91680
In the "Additional Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.
CVE-2020-1472, or Zerologon, is a severe vulnerability in Microsoft's Netlogon Remote Protocol due to a flawed implementation of AES-CFB8 encryption.
Using a fixed initialization vector and accepting unencrypted sessions allows an attacker to impersonate a server and compromise the entire Windows domain. The attacker takes control over all the Active Directory identity services.
6. CVE-2017-0144, CVE-2017-0145, CVE-2017-0143: Windows SMBv1 Remote Code Execution Vulnerability WannaCry, Petya
Vulnerability Trending Over Years: 2017, 2020, 2021, 2023 (50 times)
It was exploited by 12 Malware, 10 Threat Actors, and 12 Ransomware and was trending in the wild as recently as September 1, 2023.
Qualys Vulnerability Detection (QID): 91361, 91360, 91359, 91345
Commonly known as Shadow Broker or MS17-010, or "ETERNALBLUE," or "ETERNALSYNERGY" or "ETERNAL ROMANCE" is a remote code execution vulnerability in Microsoft's Server Message Block 1.0 (SMBv1) protocol.
The vulnerability arises from how SMBv1 handles specific requests, allowing an attacker(usually authenticated) to send a specially crafted packet to an SMBv1 server, enabling them to execute code on the target server.
It was infamously exploited in the widespread WannaCry ransomware attack in 2017, leading to global data encryption and ransom demands.
7. CVE-2012-1723: Java Applet Field Bytecode Verifier Cache Remote Code Execution
Vulnerability Trending Over Years: 2023 (6 times)
It was exploited by 91 Malware, 8 Threat Actors, 41 Ransomware and was trending in the wild as recently as August 17, 2023.
Qualys Vulnerability Detection (QID): 120274
CVE-2012-1723 is a substantial vulnerability found in the Java Runtime Environment. It can be exploited through a malicious web page, hosting a rogue Java applet can be exploited through a malicious web page hosting rogue Java applet.
The issue, originating from a type-confusion error in the "HotSpot" component, allows untrusted Java applets or applications to bypass the Java sandbox security restrictions and execute arbitrary code on a user's system
8. CVE-2021-34473, CVE-2021-34523, CVE-2021-31207: Microsoft Exchange Server RCE (ProxyShell)
Vulnerability Trending Over Years: 2021, 2022, 2023 (39 times)
It was exploited by 12 Malware, 20 Threat Actors, and 12 Ransomware and was trending in the wild as recently as September 2, 2023.
Qualys Vulnerability Detection (QID): 50114, 50111, 50112
In the "Top 12 Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.
ProxyShell, a chain of vulnerabilities that impacts on-premises Microsoft Exchange Servers, is widely used for email and associated services globally.
These vulnerabilities exist in the Microsoft Client Access Service (CAS), typically running on port 443 in IIS, often exposed to the internet to allow users to access their email remotely. This exposure has led to widespread exploitation by threat actors deploying web shells to execute arbitrary code on compromised devices. They allow an actor to bypass authentication and execute code as a privileged user.
9. CVE-2019-11510: Pulse Secure Pulse Connect Secure SSL VPN Unauthenticated Path
Vulnerability Trending Over Years: 2019, 2020, 2023 (53 times)
It was exploited by 13 Malware, 18 Threat Actors, and 12 Ransomware and was trending in the wild as recently as September 4, 2023.
Qualys Vulnerability Detection (QID): 38771
In the "Additional Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.
CVE-2019-11510 is a critical vulnerability found in Pulse Connect Secure, a widely used VPN solution by Pulse Secure. The flaw enables an unauthenticated, remote attacker to exploit a specific endpoint and read arbitrary files on the system, including sensitive information such as private keys and user credentials.
Due to its severity, It can provide an attacker with similar access to the corporate network as a legitimate user.
10. CVE-2021-44228: Apache Log4j Remote Code Execution Vulnerability
Vulnerability Trending Over Years: 2021, 2022, 2023 (77 times)
It was exploited by 10 Malware, 26 Threat Actors, and 5 Ransomware and was trending in the wild as recently as September 4, 2023.
Qualys Vulnerability Detection (QID): 376157, 730297
In the "Top 12 Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.
CVE-2021-44228, or "Log4Shell," is a severe vulnerability in Apache's log4j Java library. The flaw exploits the 'lookups' feature of log4j, enabling an attacker to use a specially crafted input to trigger the execution of a remote Java class on an LDAP server, leading to Remote Code Execution.
This issue is highly dangerous if the user input containing specific characters is logged by log4j. It can trigger Java method lookup, resulting in the execution of a user-defined remote Java class on an LDAP server, leading to Remote Code Execution (RCE) on the server running the vulnerable log4j instance.
11. CVE-2014-6271: Shellshock – Linux Bash Vulnerability
Vulnerability Trending Over Years: 2014, 2016, 2017, 2020, 2021, 2022, 2023 (70 times)
It was exploited by 18 Malware, 1 Threat Actors, and was trending in the wild as recently as September 2, 2023.
Qualys Vulnerability Detection (QID): 122693, 13038, 150134
Shellshock (CVE-2014-6271) is a critical vulnerability affecting the Unix Bash shell in many Linux, Unix, and Mac OS systems. It allows remote code execution by misusing Bash's processing of environment variables, enabling attackers to append and execute malicious commands. It has a high severity score since it can impact multiple devices and applications, risking unauthorized data access or service disruption,
12. CVE-2018-8174: Windows VBScript Engine Remote Code Execution Vulnerability
Vulnerability Trending Over Years: 2018, 2020, 2023 (30 times)
It was exploited by 21 Malware, 10 Threat Actors, and 7 Ransomware and was trending in the wild as recently as September 4, 2023.
Qualys Vulnerability Detection (QID): 91447
CVE-2018-8174 is a critical vulnerability in Microsoft Windows' VBScript Engine, enabling remote code execution. Triggered by viewing a malicious website with Internet Explorer or opening a rigged Microsoft Office document, this flaw allows an attacker to manipulate memory objects and execute code.
The attacker can fully control the system if the user has administrative rights.** **
13. CVE-2013-0074: Microsoft Silverlight Could Allow Remote Code Execution
Vulnerability Trending Over Years:2023 (8 times)
It was exploited by 62 Malware 50 Ransomware and was trending in the wild as recently as August 20, 2023.
Qualys Vulnerability Detection (QID): 90870
CVE-2013-0074 is a remote code execution vulnerability in Microsoft Silverlight, which permits a crafted Silverlight application to access memory unsafely, thereby leading to the execution of arbitrary code under the current user’s security context.
If the user has admin rights, the attacker installs programs, alters or deletes data, or generates new accounts with full privileges. The user can be deceived into visiting a malicious website or clicking on a link, commonly through an email or instant message.
14. CVE-2012-0507: Oracle Java SE Remote Java Runtime Environment Vulnerability
Vulnerability Trending Over Years: 2023 (10 times)
It was exploited by 66 Malware, 3 Threat Actors, and 42 Ransomware and was trending in the wild as recently as July 26, 2023.
Qualys Vulnerability Detection (QID): 119956
CVE-2012-0507 is a critical vulnerability in the Java Runtime Environment (JRE) allowing untrusted Java applets to execute arbitrary code outside the Java sandbox. Originating from a flaw in the AtomicReferenceArray class implementation, this vulnerability was exploited by Flashback Trojan in 2012. It was observed to have led to one of the most significant known malware attacks on Apple devices. Attackers can exploit this vulnerability by tricking users into visiting a malicious website hosting a Java applet.
15. CVE-2019-19781: Citrix ADC and Citrix Gateway - Remote Code Execution (RCE) Vulnerability
Vulnerability Trending Over Years: 2020, 2022, 2023 (60 times)
It was exploited by 11 Malware, 12 Threat Actors, and 10 Ransomware and was trending in the wild as recently as September 4, 2023.
Qualys Vulnerability Detection (QID): 372305, 150273
In the "Additional Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.
CVE-2019-19781, or "Shitrix," is a significant vulnerability associated with Citrix Application Delivery Controller (ADC) and Citrix Gateway, allowing unauthenticated attackers to perform arbitrary code execution, granting them access to internal network resources.
The flaw resides in the VPN component of the affected products, enabling directory traversal and giving attackers both read and write access to the underlying file system.
16. CVE-2018-0802: Microsoft Office Memory Corruption Vulnerability
Vulnerability Trending Over Years: 2021, 2022, 2023 (19 times)
Exploited by 29 Malware 24 Threat Actors, and was trending in the wild as recently as September 2, 2023.
Qualys Vulnerability Detection (QID): 110310
CVE-2018-0802 is a critical vulnerability within Microsoft Office and WordPad, which, if exploited, allows remote code execution via specially crafted files.
Attackers can run arbitrary code in the current user's context, potentially taking over the system if the user holds administrative rights. This vulnerability was notably used in targeted attacks and was being actively exploited before Microsoft released a security update in January 2018 that correctly handles objects in memory, resolving the issue.
17. CVE-2021-26855: Microsoft Exchange Server Authentication Bypass (RCE)
**Vulnerability Trending Over Years:**2021, 2023 (46 times)
It was exploited by 19 Malware, 22 Threat Actors, and 9 Ransomware and was trending in the wild as recently as September 2, 2023.
Qualys Vulnerability Detection (QID): 50107, 50108
In the "Additional Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.
CVE-2021-26855, a part of the ProxyLogon exploit chain, is a server-side request forgery (SSRF) vulnerability in Microsoft Exchange Server that enables attackers to bypass authentication mechanisms and impersonate users.
The flaw allows arbitrary HTTP requests, granting access to users' mailboxes and enabling information theft. It has been widely exploited by various threat actors, leading to emergency patches by Microsoft.
18. CVE-2019-2725: Oracle WebLogic Affected by Unauthenticated RCE Vulnerability
Vulnerability Trending Over Years: 2019, 2020, 2022, 2023 (53 times)
It was exploited by 10 Malware, 4 Threat Actors, 9 Ransomware and was trending in the wild as recently as September 4, 2023.
Qualys Vulnerability Detection (QID): 150267, 87386
CVE-2019-2725 is a severe remote code execution vulnerability in Oracle WebLogic Server that allows unauthenticated attackers to execute arbitrary code over a network without user interaction. It was quickly weaponized to install cryptocurrency miners.
19. CVE-2018-13379: Fortinet FortiGate (FortiOS) System File Leak through Secure Sockets Layer (SSL)
Vulnerability Trending Over Years: 2020, 2021, 2023 (41 times)
It was exploited by 6 Malware, 13 Threat Actors, 6 Ransomware and was trending in the wild as recently as August 30, 2023.
Qualys Vulnerability Detection (QID): 43702
In the "Top 12 Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.
CVE-2018-13379 is a path traversal vulnerability found in the Fortinet FortiOS SSL VPN web portal. An unauthenticated attacker can read sensitive system files via specially crafted HTTP requests. The exploit could expose SSL VPN session data, leading to more severe attacks.
20. CVE-2021-26084: Atlassian Confluence Server Webwork OGNL Injection RCE Vulnerability
Vulnerability Trending Over Years: 2021, 2022, 2023 (35 times)
It was exploited by 8 Malware, 6 Threat Actors, and 8 Ransomware and was trending in the wild as recently as September 2, 2023.
Qualys Vulnerability Detection (QID): 730172, 150368, 375839
In the "Top 12 Routinely Exploited Vulnerabilities in 2022" list, published by CISA earlier.
CVE-2021-26084 is a critical vulnerability in Atlassian's Confluence Server and Data Center, specifically within the Webwork OGNL component. This vulnerability can enable an unauthenticated attacker to execute arbitrary code on a Confluence Server or Data Center instance, potentially compromising system integrity.
TruRisk Dashboard
The Qualys VMDR helps organizations get instant visibility into high-risk and top twenty vulnerabilities.
 Fig 3. Qualys VMDR TruRisk Dashboard for Top 20 Vulnerabilities
Fig 3. Qualys VMDR TruRisk Dashboard for Top 20 Vulnerabilities
The Qualys VMDR TruRisk Dashboard helps organizations to have complete visibility into open vulnerabilities that focus on the organization’s global risk score and high-risk vulnerabilities with your organization’s global risk score and high-risk vulnerabilities. Once you identify the vulnerable assets for these top twenty CVEs prioritized among your remediation owners, you can use Qualys Patch management to instantly reduce the risk.
The TruRisk VMDR Dashboard is available – Download the Dashboard Here
Key Insights & Takeaways
- In the current Vulnerability Threat Landscape, identifying open vulnerabilities and effective remediation is the highest priority for every defender.
- Among the vast scale of the CVEs available, you need to know the weaponized high-risk vulnerabilities that are actively targeted by Threat Actors, Malware, and ransomware families.
- Use multi-dimensional Threat Intelligence to prioritize vulnerabilities rather than implementing multiple siloed threat approaches.
- The Qualys VMDR with TruRisk automatically prioritizes vulnerabilities exploited in the wild with a TruRisk score of 90 or higher, greatly simplifying the prioritization process.
References
- Part 1: An In-Depth Look at the Latest Vulnerability Threat Landscape
- Part 2: An In-Depth Look at the Latest Vulnerability Threat Landscape (Attackers’ Edition)
Additional Contributors
- Shreya Salvi, Data Scientist, Qualys *Saeed Abbasi, Product Manager, Vulnerability Research
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
0.976 High
EPSS
Percentile
100.0%