
September 2023: VM courses, Bahasa Indonesia, Russian Podcasts, Goodbye Tinkoff, MS Patch Tuesday, Qualys TOP 20, Linux, Forrester, GigaOm, R-Vision VM
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
9.2 High
AI Score
Confidence
High
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
0.976 High
EPSS
Percentile
100.0%
Hello everyone! On the last day of September, I decided to record another retrospective episode on how my Vulnerability Management month went.
Alternative video link (for Russia): <https://vk.com/video-149273431_456239136>
September was quite a busy month for me.
Vulnerability Management courses
I participated in two educational activities. The first one is an on-line cyber security course for my alma mater, Bauman Moscow State Technical University.

Together with Pavel Popov, we recorded three topics: Vulnerability Assessment, Vulnerability Management and Patch Management. About two hours of content.
The second is an online Vulnerability Management course for Positive Technologies, a leading Russian VM-vendor.

I contributed about 30 minutes of content about the importance of Asset Management and the ways of how IT can sabotage the VM-process.
Bahasa Indonesia
Speaking of education, I received my first certificate in Indonesian language after three months of studying at the PermiraMengajar course. Terima kasih banyak atas kesempatan besar ini!

I am very interested in developing vulnerability management in the Republic of Indonesia and the ASEAN region and I hope that my Bahasa Indonesia skills will help me develop more connections there.
Russian Podcasts
This month has also been quite busy with my media activities. Together with Lev Paley and Maxim Kharask, we launched a weekly news talk show Прожектор по ИБ ("Information Security Spotlight").
4 numbered episodes and a pilot are already available. The video edit of the show is currently in my hands and we are releasing it on my YouTube channel.

I also appeared as a guest on the Vulnerability Management podcast КиберДуршлаг ("Cyber Colander") by Positive Technologies. It should be released in October.
Goodbye Tinkoff
On September 18th I left Tinkoff.

I spent a wonderful 6 years and 3 months there. When I got the job, the entire Tinkoff InfoSec team consisted of 5 people, including me and our security director. Now it's a large and powerful department with recognized unique expertise. A real trendsetter for Russian companies in the financial sector (and not only).  I hope I have helped in some way to accomplish this beautiful transformation.
I hope I have helped in some way to accomplish this beautiful transformation.  I really liked Tinkoff for the pleasant atmosphere, without any toxicity, for adequate and professional management, for my dear colleagues who taught me a lot!
I really liked Tinkoff for the pleasant atmosphere, without any toxicity, for adequate and professional management, for my dear colleagues who taught me a lot!  Thank you all very much!
Thank you all very much!
What's next? I'll give an update very soon.  I can only say now, that my Vulnerability Management story is not over, and will receive new impetus and development.
I can only say now, that my Vulnerability Management story is not over, and will receive new impetus and development. 
But enough about me. Let's talk about vulnerabilities.
Microsoft Patch Tuesday
September Microsoft Patch Tuesday. There were 97 CVEs, 35 of them added between Patch Tuesdays.
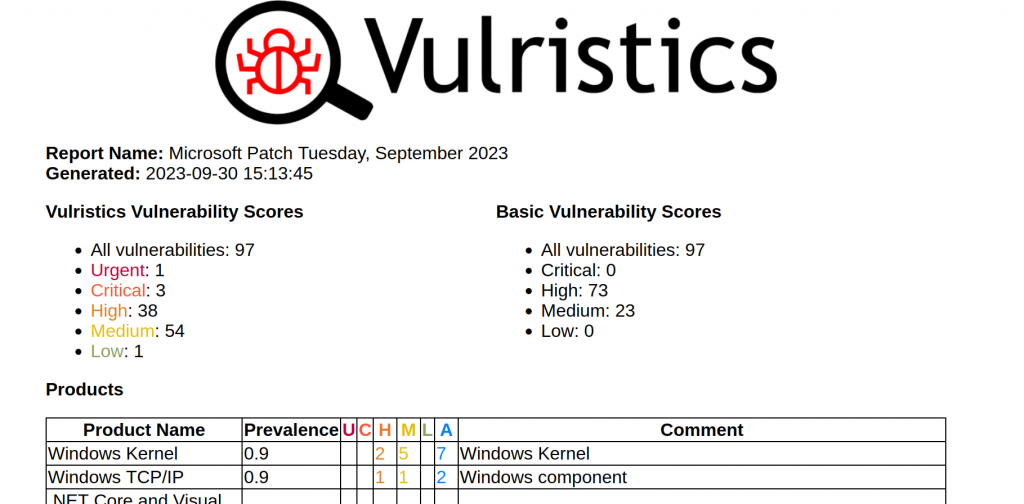
- Urgent: 1
- Critical: 3
- High: 38
- Medium: 54
- Low: 1

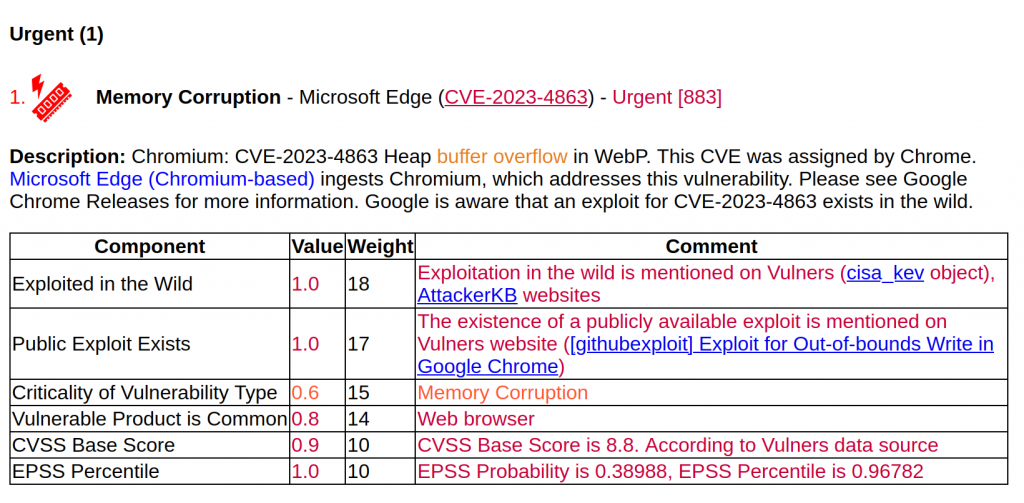
The most critical is Remote Code Execution - Microsoft Edge (CVE-2023-4863). It is quite rare for an RCE vulnerability to be present in both Chrome/Chromium based web browsers (including Edge) and Firefox based web browsers. The CVE-2023-4863 vulnerability was found in libwebp, a library for working with raster images in the WebP format (a replacement for PNG and JPEG). Therefore, any software that can open images in WebP is likely to use libwebp and will therefore be vulnerable. The exploit is available on GitHub and the vulnerability is actively exploited in the wild. Another vulnerability in Edge with a publicly available exploit isMemory Corruption - Microsoft Edge (CVE-2023-4352). Also pay attention to it.
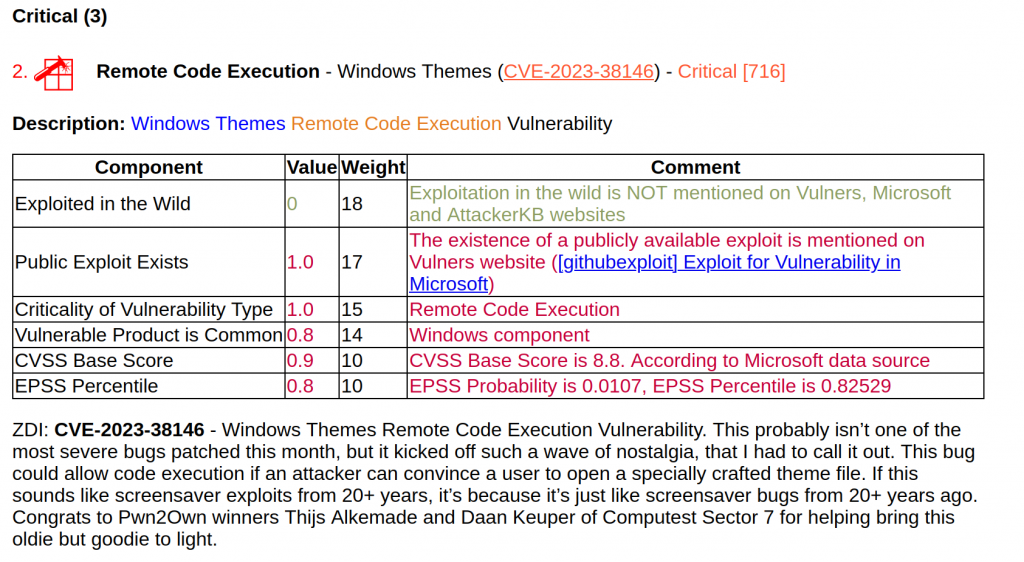
Remote Code Execution - Windows Themes (CVE-2023-38146) "ThemeBleed". This is a good example of how the criticality of a vulnerability can change overnight. It was ranked 8th in terms of criticality, only due to the RCE type. And a few days after the Path Tuesday, when a write-up and POC were published, the vulnerability became the second most critical. So you never know how things will change and what vulnerability will become truly exploitable and dangerous. Try to fix everything!
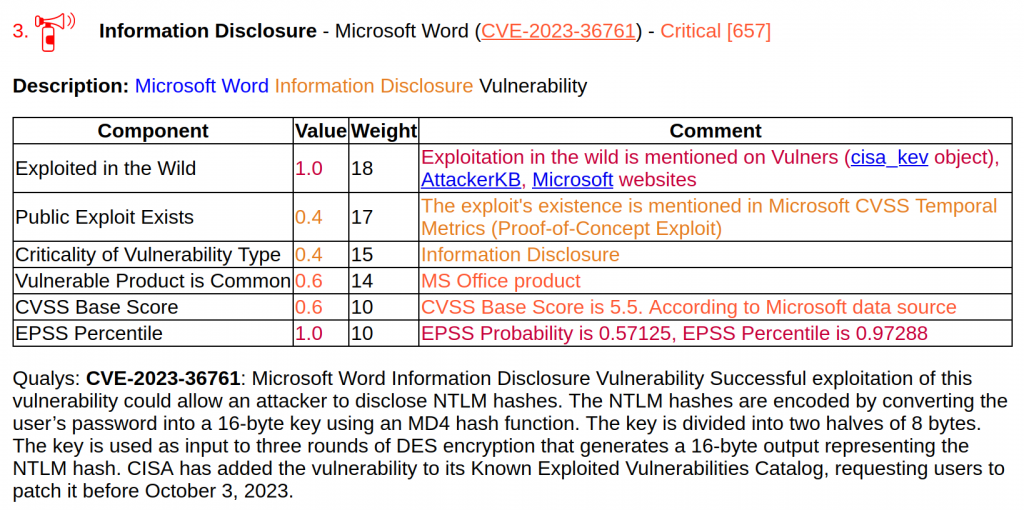
The other critical vulnerability is the exploitable in the wild Information Disclosure - Microsoft Word (CVE-2023-36761), which, according to ZDI, actually allows attackers to perform an NTLM Relay attack. NTLM relay attacks allow attackers to sit between clients and servers and relay validated authentication requests in order to access network services.
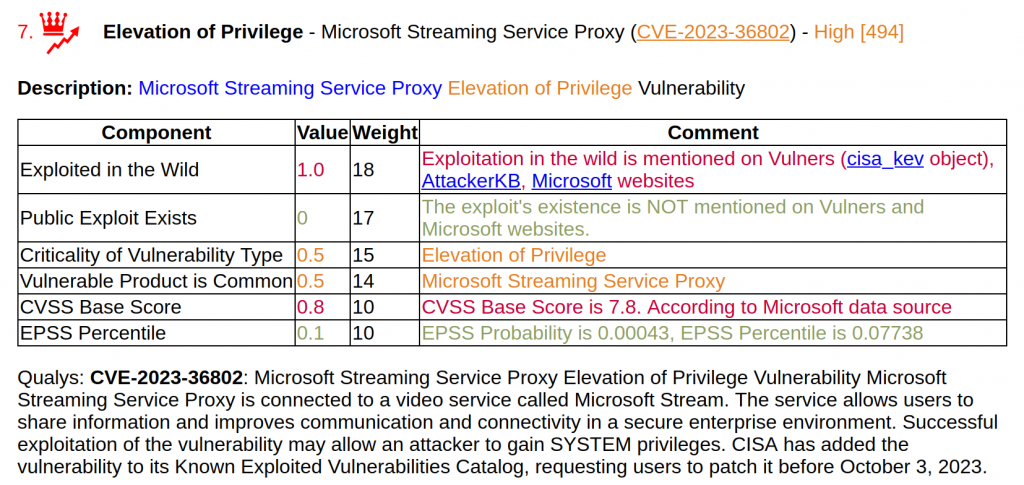
Among the Elevation of Privilege vulnerabilities, the most interesting is Elevation of Privilege - Microsoft Streaming Service Proxy (CVE-2023-36802).
The remaining CVEs show no signs of exploitation in the wild.
There were 3 Remote Code Executions in Microsoft Exchange (CVE-2023-36744, CVE-2023-36745, CVE-2023-36756). But these vulnerabilities are unlikely to be exploited. Exploitation requires an attacker to authenticate with LAN-access and have valid Exchange user credentials.
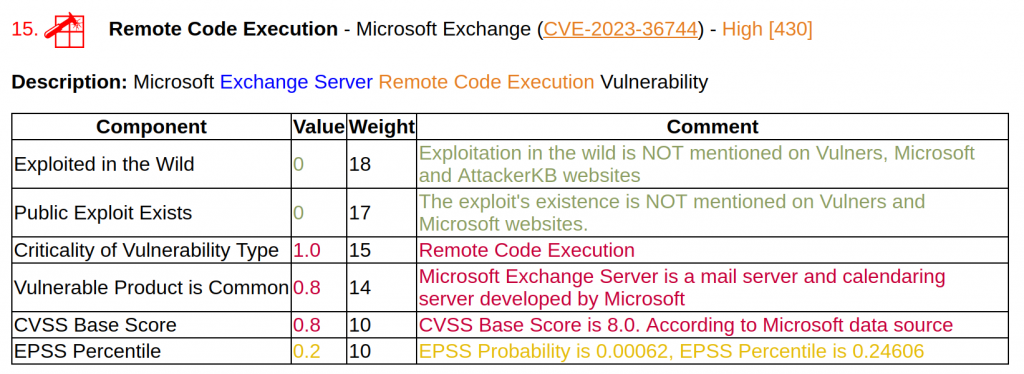
What's interesting about these MS Exchange CVEs is that Microsoft quietly patched them in August. Therefore, users who installed updates as soon as they became available were not affected by these vulnerabilities for a month. And those who usually make decisions about updating systems based on analysis of CVE IDs did not have all the information, so they could make the wrong decision and remain vulnerable for a month. Regular updates without paying much attention to CVEs seem to be the best strategy when you can't fully trust your vendor's data.
The full Vulristics report updated at September 30:
 ms_patch_tuesday_september2023
ms_patch_tuesday_september2023
Bitrix CMS RCE
This month I also drew attention to the critical RCE vulnerability BDU:2023-05857 in Bitrix CMS, which is very popular in Russia.
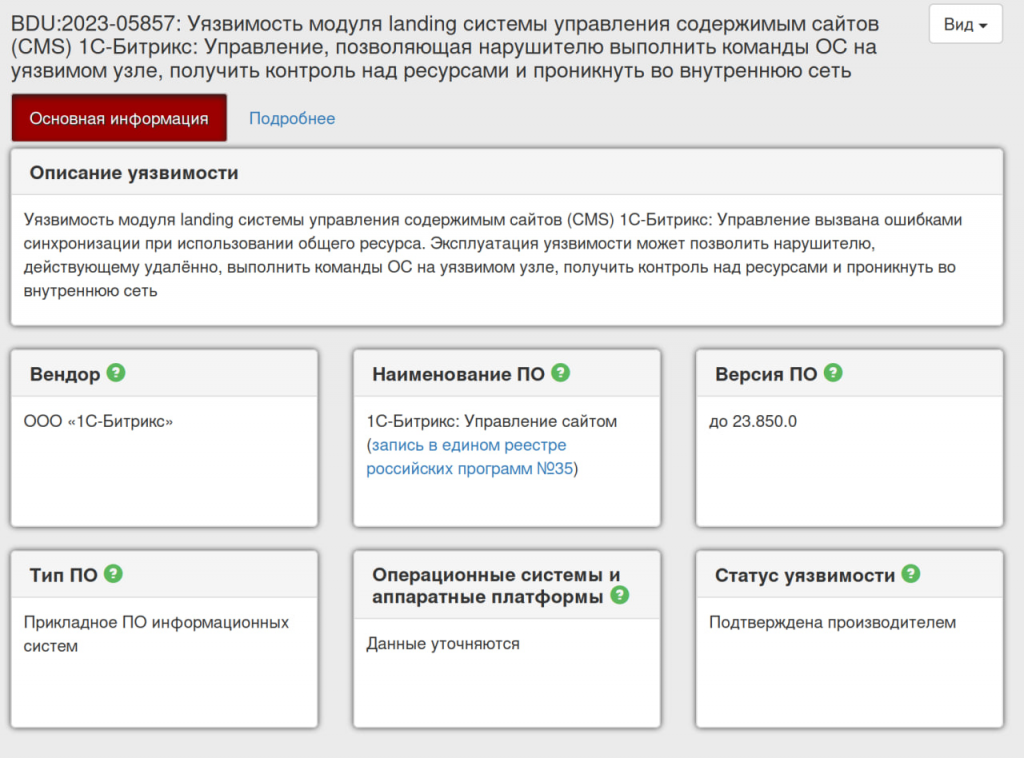
This vulnerability only has an ID in the Russian BDU FSTEC vulnerability database. It's a good example of how the world of Security and Vulnerabilities is dividing on clusters. In such clusters people use their own software products, that have their own vulnerabilities, which only their own vulnerability scanners can detect.
RHEL/CentOS 7 can't be detected, can't be fixed vulnerability
Speaking of vulnerabilities that cannot be detected, I noted an interesting vulnerability in the Linux kernel CVE-2022-1012.

Interestingly, this is not fixed in RHEL/Centos 7, and these OS versions are not yet in EOL. This means that if you use a vulnerability detection tool that makes detection based on security bulletins or OVAL content, it will not be able to detect such a vulnerability.  You can show this case to your VM vendor, specifically to Linux vulnerability detection specialists.
You can show this case to your VM vendor, specifically to Linux vulnerability detection specialists.
Qualys TOP 20 vulnerabilities
On September 4th Qualys released their own Top 20 Most Exploited Vulnerabilities list (24 CVE). I collected them in Vulristics comment format.

And I wondered if there were vulnerabilities that were not included in the recent Anglo-Saxon lists. It turned out that 12 CVEs are not included, i.e. exactly one half:
- CVE-2012-0158
- CVE-2012-0507
- CVE-2012-1723
- CVE-2013-0074
- CVE-2014-6271
- CVE-2017-0143
- CVE-2017-0144
- CVE-2017-0145
- CVE-2017-8570
- CVE-2018-0802
- CVE-2018-8174
- CVE-2019-2725
These are Shellshock, MS17-010, 3 RCEs for Office, 2 RCEs for VBScript and Silverlight, 3 vulnerabilities for Oracle Java and WebLogic. Apparently the Anglo-Saxons decided that in 2022 this was no longer relevant. 
Vulristics reports:
 Qualys TOP 20 2023
Qualys TOP 20 2023
 Qualys TOP 20 2023 NOT in Joint report
Qualys TOP 20 2023 NOT in Joint report
Forrester and GigaOm VM Market reports
Now let's talk about Vulnerability Management market news. In September approximately at the same time two marketing reports were released.
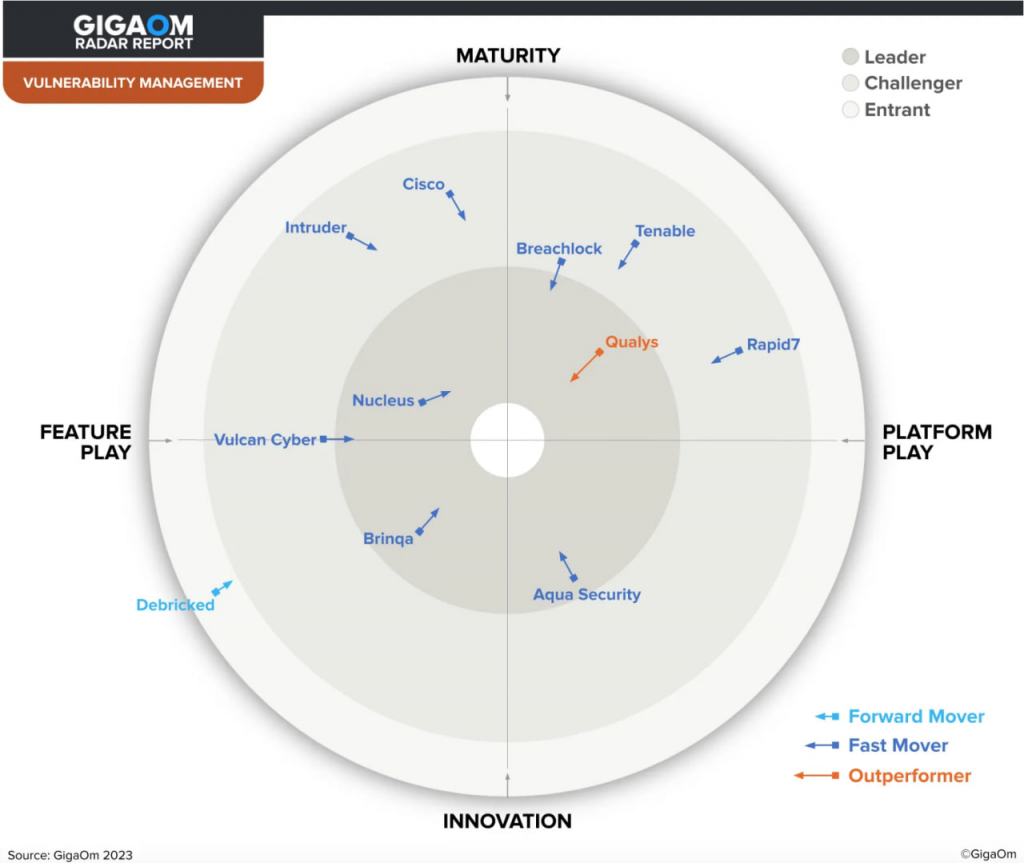
 GigaOm Radar Report for Continuous Vulnerability Management v3.01. You you can get it from Qualys.
GigaOm Radar Report for Continuous Vulnerability Management v3.01. You you can get it from Qualys.
 The Forrester Wave
The Forrester Wave : Vulnerability Risk Management, Q3 2023. You you can get it from Tenable.
: Vulnerability Risk Management, Q3 2023. You you can get it from Tenable.
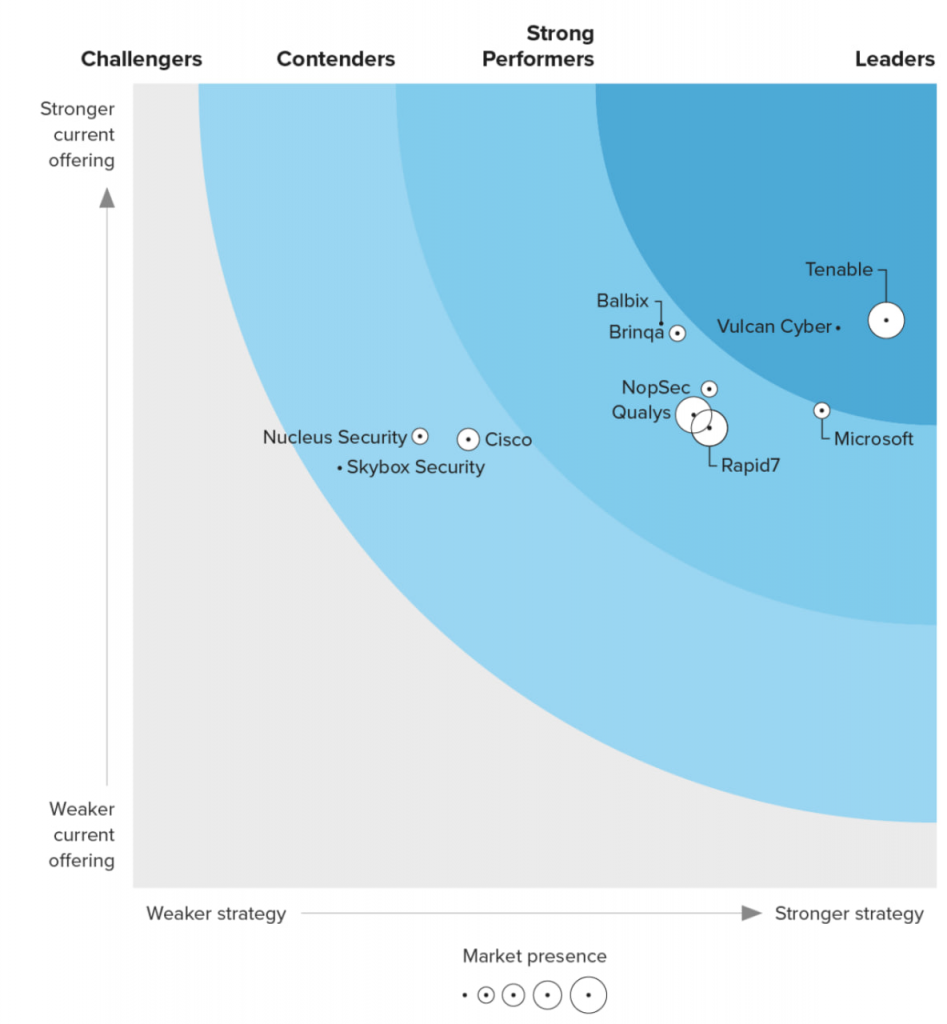
It's not surprising that the companies that provide us the reprints of the reports are named the leaders in those reports.  As usual such reports try to compare incomparable companies and solutions, but IMHO still it's better than nothing.
As usual such reports try to compare incomparable companies and solutions, but IMHO still it's better than nothing.
R-Vision VM
The biggest news on the Russian VM market in September was the R-Vision conference and the presentation of the R-Vision VM product.

From a vulnerability detection perspective, R-Vision VM is an OVAL/SCAP scanner. For now, MVP only supports Linux distributions.
Western:
 Debian v. 7-11
Debian v. 7-11
 RHEL v. 6-9
RHEL v. 6-9
 Ubuntu v. 14.04-23.04
Ubuntu v. 14.04-23.04
 Suse SLED/SLES 11, 12, 15
Suse SLED/SLES 11, 12, 15
Russian:
 RedOS v. 7.3
RedOS v. 7.3
 AstraLinux v. 17
AstraLinux v. 17
And the very fact that a VM-vendor can present an MVP solution that supports only Linux systems shows how important the role, that Linux now plays in Russia. Russian distributions especially.
R-Vision also published an article in which they presented their ideas for building an ideal vulnerability management process in organizations. Actually, it looks quite nice.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
9.2 High
AI Score
Confidence
High
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
0.976 High
EPSS
Percentile
100.0%