
BlackByte ransomware exploits Microsoft Servers ProxyShell Vulnerabilities
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
THREAT LEVEL: Red.
For a detailed advisory, download the pdf file here.
BlackByte ransomware is targeting organizations with unpatched ProxyShell vulnerabilities. Proxy Shell was addressed by hive pro threat researcher in the previous advisory released on August 24.
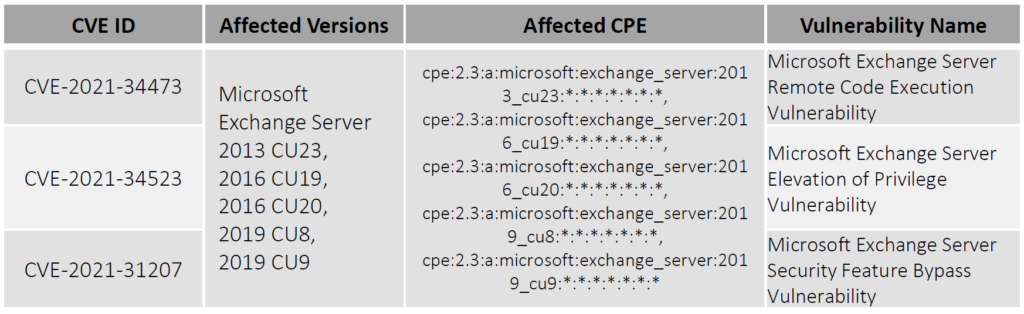
ProxyShell is a combination of three flaws in Microsoft Exchange:
CVE-2021-34473 Pre-auth path confusion vulnerability to bypass access control.
CVE-2021-34523 Privilege escalation vulnerability in the Exchange PowerShell backend.
CVE-2021-31207 Post-auth remote code execution via arbitrary file write.
These security flaws are used together by threat actors to perform unauthenticated, remote code execution on vulnerable servers. After exploiting these vulnerabilities, the threat actors then install web shells, coin miners, ransomwares or backdoors on the servers. Attackers then use this web shell to deploy cobalt strike beacon into Windows Update Agent and get the credentials for a service account on compromised servers. The actor then installs Anydesk to gain control of the system and do lateral movement in the organization network. Post exploitation, attackers carry on with using Cobalt Strike to execute the Blackbyte ransomware and encrypt the data.
Affected organizations can decrypt their files using a free decryption tool written by Trustwave. Users can patch their server for ProxyShell vulnerabilities using the link down below.
Techniques used by Blackbyte ransomware are :
T1505.003 Server Software Component: Web Shell
T1055 Process Injection
T1059.001 Command and Scripting Interpreter: PowerShell
T1595.002 Active Scanning: Vulnerability Scanning
T1027 Obfuscated Files of Information
T1490 Inhibit System Recovery
T1112 Modify Registry
T1562.001 Impair Defenses: Disable or Modify Tools
T1562.004 Impair Defenses: Disable or Modify System Firewall
T1018 Remote System Discovery
T1016 System Network Configuration Discovery
T1070.004 Indicator Removal on Host: File Deletion
T1560.001 Archive Collected Data: Archive via Utility
Vulnerability Details
Actor Detail

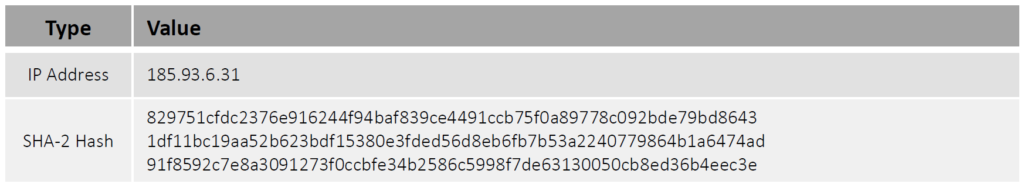
Indicators of Compromise(IoCs)
Patch Link
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-34473>
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-34523>
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-31207>
References
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C