
Vulnerability Databases: Classification and Registry
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.976 High
EPSS
Percentile
100.0%
What publicly available Vulnerability Databases do we have? Well, I can only say that there are a lot of them and they are pretty different. Here I make an attempt to classify them.
It’s quite an ungrateful task. No matter how hard you try, the final result will be rather inaccurate and incomplete. I am sure someone will be complaining. But this is how I see it.  If you want to add or change something feel free to make a comment bellow or email [email protected].
If you want to add or change something feel free to make a comment bellow or email [email protected].
The main classifier, which I came up with:
- There are individual vulnerability databases in which one identifier means one vulnerability. They try to cover all existing vulnerabilities.
- And others are security bulletins. They cover vulnerabilities in a particular product or products. And they usually based on on patches. One patch may cover multiple vulnerabilities.
I made this diagram with some Vulnerability Databases. Note that I wanted to stay focused, so there are no exploit DBs, CERTs, lists of vulnerabilities detected by some researchers (CISCO Talos, PT Research, etc.), Media and Bug Bounty sites.
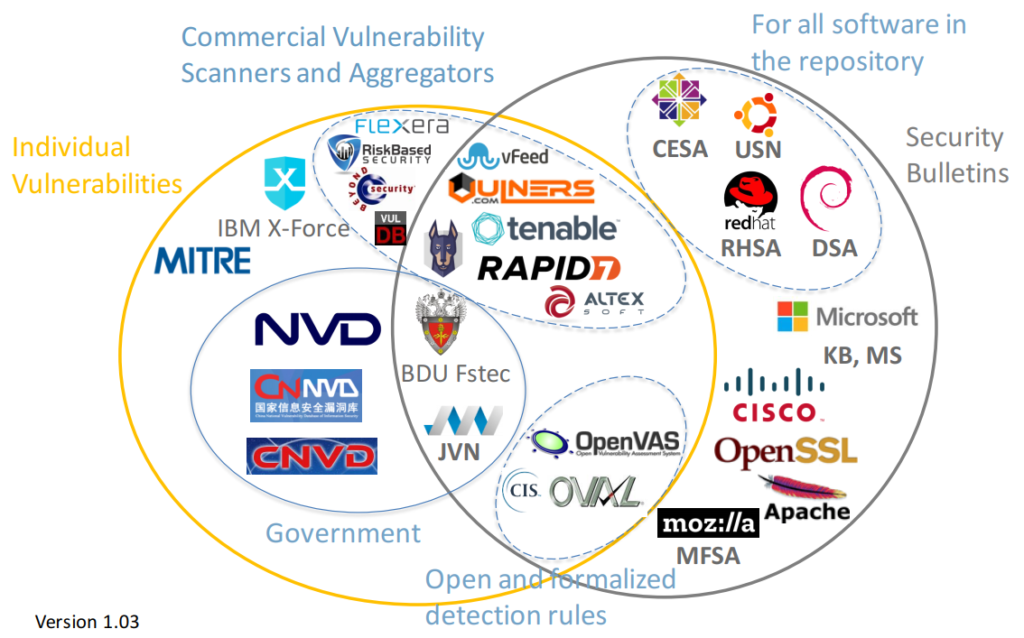
For these databases the descriptions of vulnerabilities are publicly available on the site (in html interface or downloadable data feed), or exist in a form of paid Vulnerability Intelligence service (for example, Flexera).
On one side there are databases of individual vulnerabilities, the most important is National Vulnerability Database. There are also Chinese, Japanese bases that can be derived from NVD or not.
On the other side we have security bulletins, for example RedHat Security Advisories.
And in the middle we have a Vulnerability Databases, for which it is not critical whether they have duplicated vulnerability IDs or not.
These are the Vulnerability Databases of aggregators, vulnerability scanners, security content databases. We can say that CIS OVAL or OpenVAS NVTs are the forms of public security content. Russian FSTEC BDU Vulnerability Database also has individual vulnerabilities and security bulletins.
Classification
I have the following groups:
- Individual Vulnerabilities
- Individual Vulnerabilities -> Government
- Individual Vulnerabilities -> Commercial Vulnerability Scanners and Aggregators
- Mixed Individual Vulnerabilities and Security Bulletins -> Commercial Vulnerability Scanners and Aggregators
- Mixed Individual Vulnerabilities and Security Bulletins -> Government
- Mixed Individual Vulnerabilities and Security Bulletins -> Open and formalized detection rules
- Security Bulletins
- Security Bulletins -> All software in repository
Registry
I was trying to give a link on the same “Drupalgedon2” CVE-2018-7600 vulnerability in examples, where it was possible. I mentioned the ways to grab all the entries from particular Vulnerability Database in the Aggregation column. Most of this methods are provided by the owner of the Database (“official”) or in a form of Vulners collections.
| Name | Classification Group | Description | Example of content | Aggregation |
|---|---|---|---|---|
| Mitre CVE | Individual Vulnerabilities | Coordinate the release of CVE identifiers | CVE-2018-7600 | Official |
| IBM X force | Individual Vulnerabilities | Threat and Vulnerability Intelligence service | CVE-2018-7600 | n/a |
| NIST NVD | Individual Vulnerabilities -> Government | The NVD is the U.S. government repository of standards based vulnerability management data | CVE-2018-7600 | Official, Vulners |
| CNNVD | Individual Vulnerabilities -> Government | China National Vulnerability Database of Information Security | CNNVD-201803-1136 | Official |
| CNVD | Individual Vulnerabilities -> Government | China National Vulnerability Database | CNTA-2018-0012 | n/a |
| JVN | Mixed Individual Vulnerabilities and Security Bulletins -> Government | Japan Vulnerability Notes | JVN#65268217 | n/a |
| BDU Fstec | Mixed Individual Vulnerabilities and Security Bulletins -> Government | Russian Data Security Threats Database | BDU:2018-00749 | Official |
| Risk Based Security VulnDB | Individual Vulnerabilities -> Commercial Vulnerability Scanners and Aggregators | Vulnerability Intelligence vendor | n/a | n/a |
| Flexera | Individual Vulnerabilities -> Commercial Vulnerability Scanners and Aggregators | Vulnerability Intelligence vendor | n/a | n/a |
| Beyond Security SecuriTeam | Individual Vulnerabilities -> Commercial Vulnerability Scanners and Aggregators | Vulnerability Management vendor | CVE-2016-9939 | n/a |
| VulDB | Individual Vulnerabilities -> Commercial Vulnerability Scanners and Aggregators | “Number 1 vulnerability database worldwide with more than 117000 entries available.” | CVE-2018-7600 | n/a |
| vFeed | Mixed Individual Vulnerabilities and Security Bulletins -> Commercial Vulnerability Scanners and Aggregators | “Trusted Vulnerability & Threat Intelligence Database” | n/a | Official |
| Vulners | Mixed Individual Vulnerabilities and Security Bulletins -> Commercial Vulnerability Scanners and Aggregators | “Complete Vulnerability DataBase & Security Scanne” | CVE-2018-7600 | Official |
| Tenable | Mixed Individual Vulnerabilities and Security Bulletins -> Commercial Vulnerability Scanners and Aggregators | Tenable Nessus Attack Scripting Language (NASL) plugins | CVE-2018-7600 | Vulners |
| Snyk | Mixed Individual Vulnerabilities and Security Bulletins -> Commercial Vulnerability Scanners and Aggregators | “Snyk helps you use open source and stay secure.” | CVE-2018-7600 | n/a |
| Rapid7 | Mixed Individual Vulnerabilities and Security Bulletins -> Commercial Vulnerability Scanners and Aggregators | “Vulnerability & Exploit Database” | CVE-2018-7600 | n/a |
| Altx-Soft OVAL Repository | Mixed Individual Vulnerabilities and Security Bulletins -> Commercial Vulnerability Scanners and Aggregators | ALTEX-SOFT-owned OVAL repository | CVE-2018-7600 | n/a |
| SecPod SCAP Repo | Mixed Individual Vulnerabilities and Security Bulletins -> Commercial Vulnerability Scanners and Aggregators | SecPod-owned OVAL repository | CVE-2018-7600 | n/a |
| OpenVAS NVT | Mixed Individual Vulnerabilities and Security Bulletins -> Open and formalized detection rules | “Public feed of Network Vulnerability Tests (NVTs) for the OpenVAS project” | n/a | Vulners |
| CIS OVAL | Mixed Individual Vulnerabilities and Security Bulletins -> Open and formalized detection rules | Main database of OVAL content sponsored by Center for Internet Security | n/a | Official |
| CentOS CESA | Security Bulletins -> All software in repository | The CentOS-announce Archives | CESA-2014:0376 | Vulners |
| Ubuntu USN | Security Bulletins -> All software in repository | Ubuntu security notices | USN-2165-1 | Vulners |
| RedHat RHSA | Security Bulletins -> All software in repository | The RedHat-announce Archives | RHSA-2014:0376 | Vulners |
| Debian DSA | Security Bulletins -> All software in repository | Debian Security Advisories | DSA-4156-1 | Vulners |
| Microsoft KB | Security Bulletins | Microsoft Knowledge Base | KB4013389 | n/a |
| Microsoft MS | Security Bulletins | Microsoft Security Bulletin | MS17-10 | n/a |
| CISCO SA | Security Bulletins | Cisco Security Advisories | cisco-sa-20180521 | Vulners |
| OpenSSL Vulnerabilities | Security Bulletins | OpenSSL Vulnerabilities | CVE-2018-0737 | Vulners |
| Apache | Security Bulletins | Security Problems with the Apache HTTP Server | CVE-2017-9798 | Vulners |
| Mozilla MFSA | Security Bulletins | Mozilla Foundation Security Advisories | mfsa2018-13 | Vulners |
Other Vulnerability Databases
Of course this table is far from being complete. It’s a basic structure, just to give an overall picture.
You can find more:
- Different Vulnerability Databases in Vulnerability Database Catalog by FIRST.org.
- Security Bulletins for different Operating Systems and Software at Vulners.com stats page (blocks “Unix” and “Software”).
- Bases of OVAL content listed at MITRE OVAL Product List (it is in archive state; see the type “Definition Repository”)
Do you know any other interesting sources about known software vulnerabilities? Feel free to mention them in the comments bellow.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.976 High
EPSS
Percentile
100.0%