Hackers Exploit Unpatched VPNs to Install Ransomware on Industrial Targets
EPSS
Percentile
99.7%
Unpatched Fortinet VPN devices are being targeted in a series of attacks against industrial enterprises in Europe to deploy a new strain of ransomware called “Cring” inside corporate networks.
At least one of the hacking incidents led to the temporary shutdown of a production site, said cybersecurity firm Kaspersky in a report published on Wednesday, without publicly naming the victim.
The attacks happened in the first quarter of 2021, between January and March.
“Various details of the attack indicate that the attackers had carefully analyzed the infrastructure of the targeted organization and prepared their own infrastructure and toolset based on the information collected at the reconnaissance stage,” said Vyacheslav Kopeytsev, a security researcher at Kaspersky ICS CERT.
The disclosure comes days after the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) warned of advanced persistent threat (APT) actors actively scanning for Fortinet SSL VPN appliances vulnerable to CVE-2018-13379, among others.
“APT actors may use these vulnerabilities or other common exploitation techniques to gain initial access to multiple government, commercial, and technology services. Gaining initial access pre-positions the APT actors to conduct future attacks,” the agency said.
CVE-2018-13379 concerns a path traversal vulnerability in the FortiOS SSL VPN web portal, which allows unauthenticated attackers to read arbitrary system files, including the session file, which contains usernames and passwords stored in plaintext.
Although patches for the vulnerability were released in May 2019, Fortinet said last November that it identified a “large number” of VPN appliances that remained unpatched, while also cautioning that IP addresses of those internet-facing vulnerable devices were being sold on the dark web.
In a statement shared with The Hacker News, Fortinet said it had urged customers to upgrade their appliances “on multiple occasions in August 2019, July 2020, and again in April 2021” following the May 2019 fix. “If customers have not done so, we urge them to immediately implement the upgrade and mitigations,” the company said.
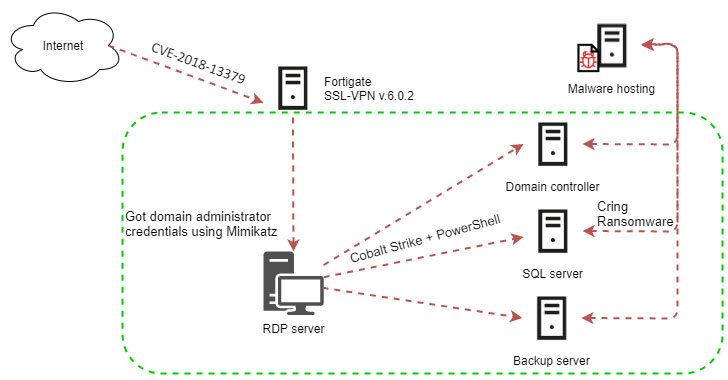
The attacks aimed at European businesses were no different, according to Kaspersky’s incident response, which found that the deployment of Cring ransomware involved the exploitation of CVE-2018-13379 to gain access to the target networks.
“Some time prior to the main phase of the operation, the attackers performed test connections to the VPN Gateway, apparently in order to make sure that the stolen user credentials for the VPN were still valid,” Kaspersky researchers said.
Upon gaining access, the adversaries are said to have used the Mimikatz utility to siphon account credentials of Windows users who had previously logged in to the compromised system, then utilizing them to break into the domain administrator account, move laterally across the network, and eventually deploy the Cring ransomware on each machine remotely using the Cobalt Strike framework.
Cring, a nascent strain that was first observed in January 2021 by telecom provider Swisscom, encrypts specific files on the devices using strong encryption algorithms after removing traces of all backup files and terminating Microsoft Office and Oracle Database processes. Following successful encryption, it drops a ransom note demanding payment of two bitcoins.
What’s more, the threat actor was careful to hide their activity by disguising the malicious PowerShell scripts under the name “kaspersky” to evade detection and ensured that the server hosting the ransomware payload only responded to requests coming in from European countries.
“An analysis of the attackers’ activity demonstrates that, based on the results of the reconnaissance performed on the attacked organization’s network, they chose to encrypt those servers which the attackers believed would cause the greatest damage to the enterprise’s operations if lost,” Kopeytsev said.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.