
Introducing Periscope: Out-of-Band Vulnerability Detection Mechanism in Qualys WAS
Web applications and REST APIs can be susceptible to a certain class of vulnerabilities that can’t be detected by a traditional HTTP request-response interaction. These vulnerabilities are challenging to find but provide a way for attackers to target otherwise inaccessible, internal systems. An attacker can potentially use this to their advantage. Essentially, a vulnerable application (or API) can be used as a proxy for an attack against a separate internal application, a cloud service, or other protected system.
An example from 2019 was a much-publicized data breach against a large U.S. bank, where a key component to the attack was exploitation of a server-side request forgery (SSRF) vulnerability. With SSRF, a vulnerable application incorporates user-supplied data in a request or message sent to an internal, protected system. The request or message is assumed to be safe since it comes from a trusted source.
An external sensor is a useful technique for vulnerability scanners to identify these types of “blind” vulnerabilities. External sensors can be used to capture information sent by a vulnerable application upon successful execution of the scanner’s payload.
What is Qualys Periscope?
Qualys Web Application Scanning (WAS) is Qualys’ leading dynamic application security testing (DAST) product. Periscope is a new out-of-band vulnerability detection mechanism within Qualys WAS. With Periscope, an external sensor enhances WAS’ detection capabilities to identify blind vulnerabilities in web applications and APIs. The sensor captures and processes DNS lookup requests generated by a vulnerable application or API.
The current list of vulnerabilities detected with Periscope are:
- SMTP Header Injection, reported as QID 150255 in WAS
- Server-Side Request Forgery (SSRF), reported as QID 150258
- Blind XXE, reported as QID 150179
- Oracle WebLogic Remote Code Execution (CVE-2019-2725), reported as QID 150267
These new QIDs are enabled by default as part of the core detection scope in WAS. In the future, we expect to add more vulnerability detections that leverage this external sensor approach.
How does Qualys Periscope work?
Periscope includes an external sensor that captures DNS lookup requests generated from a vulnerable application. A scanned web application that has a blind vulnerability will execute the payload sent by the scanner for a specific vulnerability type. The payload execution triggers an external DNS lookup request, where the source of the request is the application itself. Qualys Periscope comes into play by capturing and analyzing this external DNS request. Its job is to decompose the data embedded in the request to understand which type of vulnerability was identified, which scan triggered the request, and the specific URL and parameter that served as the injection point. Furthermore, it sends the relevant information about the vulnerability to WAS which will subsequently report the appropriate QID.
The detection mechanism consists of the following steps:
-
When Qualys WAS scans a web application for out-of-band vulnerabilities, it fuzzes/injects the fields with specially-crafted payloads. Different payloads are used for different vulnerability types. In this example, WAS is scanning the web app at “www.example.com”. Imagine this web app includes functionality to display an image that is retrieved from a certain URL. To test for SSRF, a request similar to the one below would be sent by the scanner. Here we see the field being fuzzed is the “url” query string parameter and the specific payload is for SSRF.
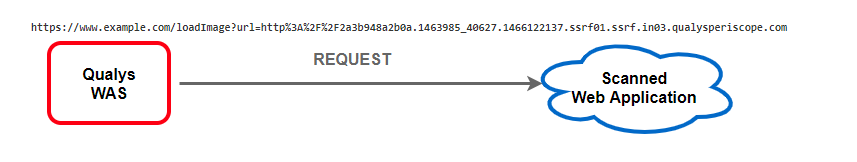
2. If the scanned web application is vulnerable, it tries to make the following HTTP request but first must resolve the FQDN having domain of qualysperiscope.com mentioned in the payload.
http://2a3b948a2b0a.1463985_40627.1466122137.ssrf01.ssrf.in03.qualysperiscope.com
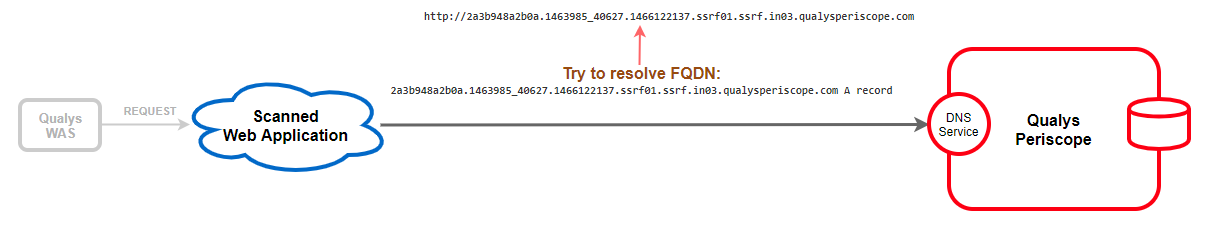
3. Now as a part of DNS resolution process, the request will hit Qualys Periscope’s DNS service. The DNS service initially processes the request to verify the hash embedded in the request is valid. This ensures the lookup request is genuine and was generated from a WAS scan. Once everything is verified, Periscope logs the request internally. If verification fails, the request is simply dropped.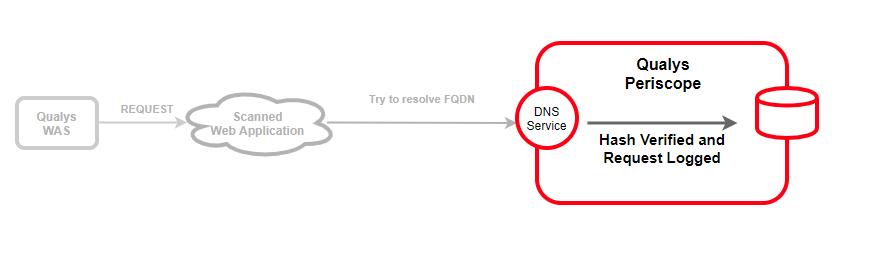
4. Subsequently, Qualys WAS will ask for the lookup request data from Periscope along with the scan ID and a hash. Periscope again verifies the hash and serves the external request data corresponding to that scan ID (if present).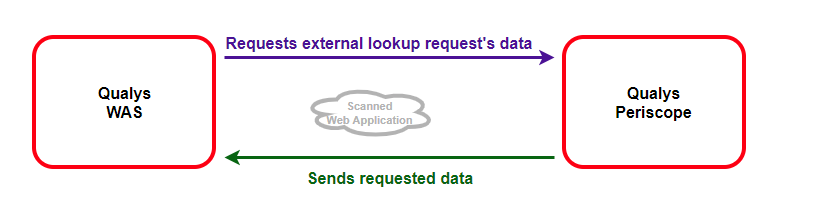
The data received from Periscope is in JSON as below:
{
"lookup": "A-record"
"request": "2a3b948a2b0a.1463985_40627.1466122137.ssrf01.ssrf.in03.qualysperiscope.com",
}
- WAS processes the data received from Qualys Periscope, and reports the vulnerabilities corresponding to the payload which were successfully executed.
New Insight to Reduce Risk
With the new Periscope detection mechanism in Qualys WAS, organizations gain deeper insight into their web application vulnerabilities. This new information can then be used to drive remediation efforts to decrease attack surface and reduce risk.
Availability
At this time, Periscope-based vulnerability detections are available on the following Qualys platforms:
- EU1
- EU2
- US1
- US2
- US3
- IN1 (India)
If you have a Qualys login, but aren’t sure which platform your organization is using, please refer to Identify your Qualys platform.