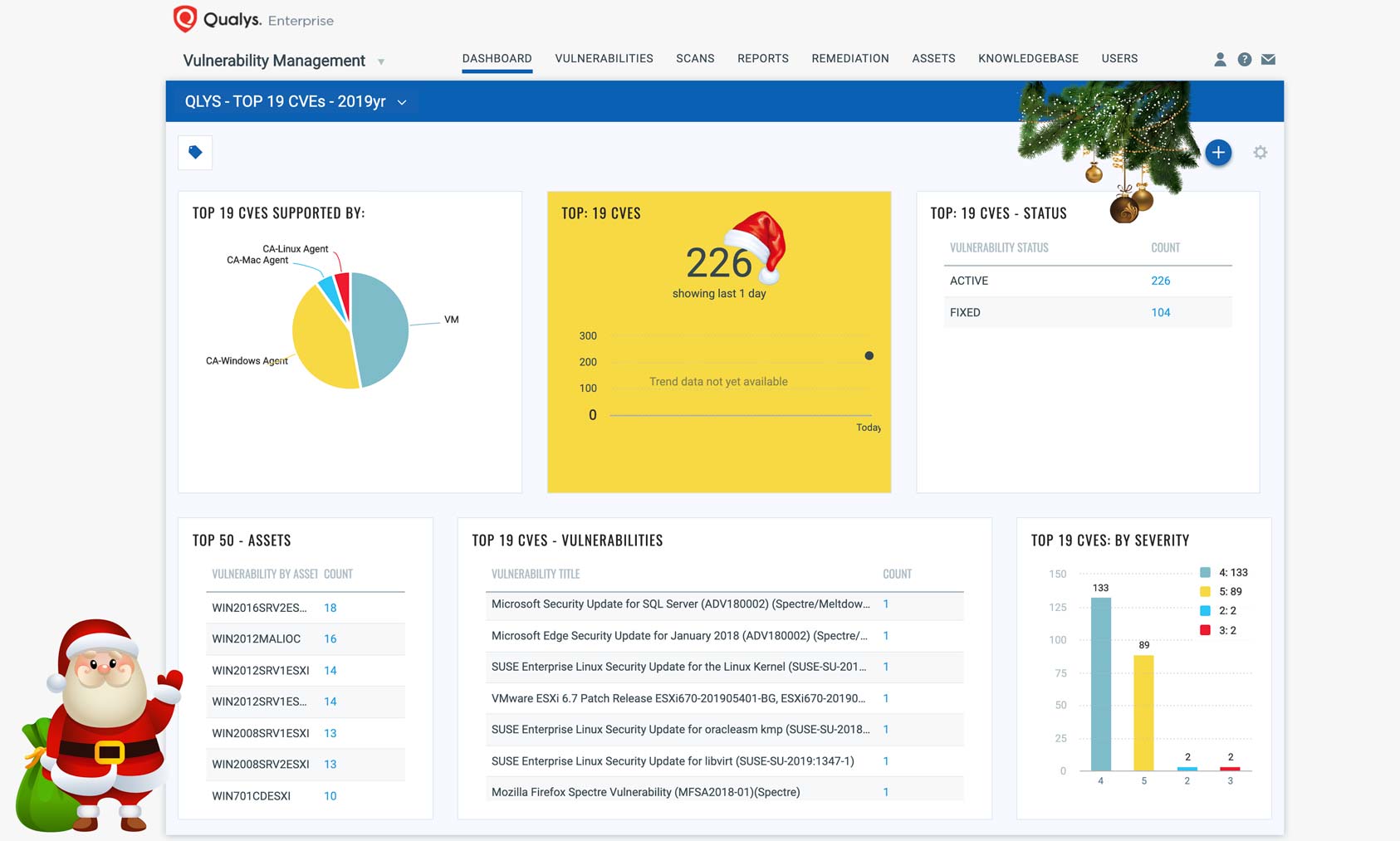
Top 19+ Vulnerability CVEs in Santa’s Dashboard Tracking
A recent report identified 19+ vulnerabilities that should be mitigated by end of year 2019. These are a range of top vulnerabilities attacked and leveraged by Advance Persistent Threat (APT) actors from all parts of the world.
The list below shows those top 19 vulnerabilities, and it should be no surprise that you can easily track and remediate them via a dashboard within Qualys. Import the dashboard into your subscription for easy insight into what assets and vulnerabilities in your organization are at risk.
| No. | CVE | Products Affected by CVE | CVSS Score (NVD) | Examples of Threat Actors |
|---|---|---|---|---|
| 1 | CVE-2017-11882 | Microsoft Office | 7.8 | APT32 (Vietnam), APT34 (Iran), APT40 (China), APT-C-35 (India), Cobalt Group (Spain, Ukraine), Silent Group (Russia), Lotus Blossom (China), FIN7 (Russia) 2 |
- according to cvedetails.com
Detecting the Top 19 CVEs
Qualys has detections (QIDs) for Qualys Vulnerability Management that cover authenticated and remotely detected vulnerabilities supported by Qualys scanners and Qualys Cloud Agent.
To return a list of all impacted hosts, use the following QQL query within the VM Dashboard:
vulnerabilities.vulnerability.cveIds:[CVE-2017-11882, CVE-2018-8174, CVE-2017-0199, CVE-2018-4878, CVE-2017-10271, CVE-2019-0708, CVE-2017-5638, CVE-2017-5715, CVE-2017-8759, CVE-2018-20250, CVE-2018-7600, CVE-2018-10561, CVE-2012-0158, CVE-2017-8570, CVE-2018-0802, CVE-2017-0143, CVE-2018-12130, CVE-2019-2725, CVE-2019-3396]
You can import the following dashboard to track all 19 CVEs as shown in the template below:
Alerts
The Qualys Cloud Platform enables you to continuously monitor for vulnerabilities and misconfigurations and get alerted for your most critical assets.
See how to set up notifications for new and updated QIDs.
Tracking Per-Year Environment Impact and Remediation
The Qualys visualization team has included a Per-Year Environment Insight View Dashboard for easy tracking and remediation. This dashboard has been included in release 2.42 and can be found within the dashboard templates library. It will automatically show your systems whether scanned internally, externally or on remote mobile computers with the groundbreaking Qualys Cloud Agent.
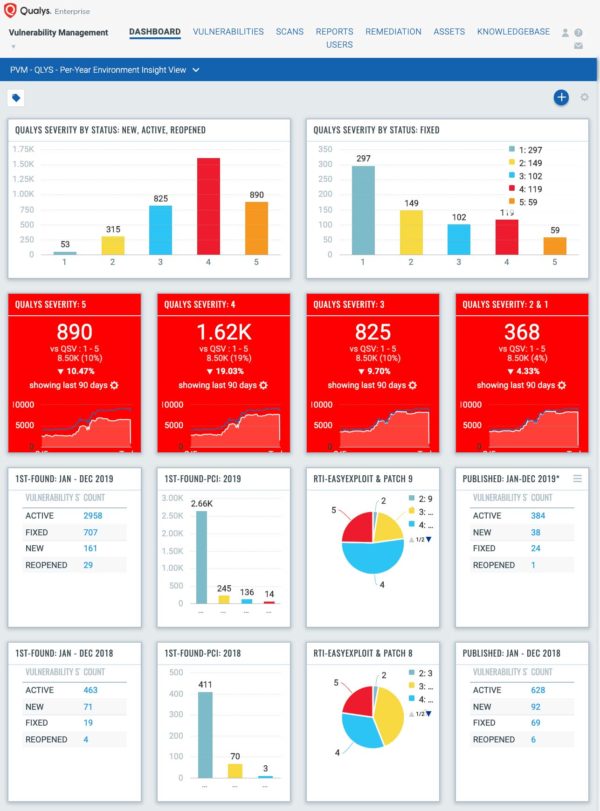
This Per-Year Environment Insight View Dashboard will display data per year based on First Found date, followed by Vulnerability Status, Severity, Compliance, Real-Time Threat Intelligence (RTI)s from Qualys Threat Protection, and Vulnerability Published Dates, allowing for an easy glance across your environment.
Get Started Now
To start detecting and remediating these vulnerabilities now, get a Qualys Suite trial.
Visit the Qualys Community to download other dashboards created by your SMEs and Product Management team and import them into your subscription for further data insights.