Monthly Vulners Review #2

Vulners events
The most interesting vulnerabilities of the month
Very few tools
News with almost no attacks
Vulners events
There have been several events for Vulners this month:
- Intergated with project: https://attackerkb.com which we mentioned at Vulners weekly digest #5;
- Vullners integrated with data about Apple vulnerabilities. Mentioned at Vulners weekly digest #7;
- Update our contacts :) Anyone can contact us through any way;
- Made a survey for feedback: https://forms.gle/D17BaFwD5hJnKkUUA.
We are constantly experimenting with the format of our posts. At this time, we decided to show the maximum number of the most interesting vulnerabilities this month and not to divide by platforms as in the previous monthly post.
Microsoft
Microsoft wouldn't be themselves if their next monthly update didn't break something. So it broke…

Released on may 12, the monthly update of Windows 10 KB4556799 may cause LTE modems (internal or external) to stop working. In this case, Windows will show that there is a network. And it's not really there.
Microsoft promises to solve the problem in the nearest fix.
Ambiguous vulnerabilities
According to vulners AI score, there are some ambiguous vulnerabilities (low CVSS with high AI score or without CVSS).
(bulletinFamily:exploit OR bulletinFamily:NVD) AND enchantments.score.value:[6 TO 10] AND cvss.score:[0 TO 6] AND order:viewCount last month
A few examples from this month are below:
Few PoCs for few vulnerabilities in the ManageEngine
ManageEngine is one of the most popular software solutions for managing IT infrastructure (typical Help Desk)
| CVE | Component | Type | PoC |
| CVE-2020-11531 | Data Security <v6.0.1 | Path Traversal | PoC for CVE-2020-11531 |
| CVE-2020-11532 | Data Security <v6.0.1 | Authentication Bypass | Poc for CVE-2020-11532 |
| CVE-2020-8838 | Windows agent <v6.5 | Remote Code Execution | Poc for CVE-2020-8838 |
All these vulnerabilities were disclosed on may 5.
Kill-chain with IBM Data Risk Manager
IDRM is a special software platform designed to collect threat data from various security systems. Thanks to this principle IDRM is well suited for evaluating an organization's cyber risks.
If attackers compromise this component, it is highly likely that they will be able to completely compromise the organization. Please note that IDRM stores the credentials used to access other security products. Moreover, the platform contains information about the company's critical vulnerabilities.
The three vulnerabilities can be linked in a kill-chain, which will allow the attacker to remotely code execution with high privileges.
The metasploit module includes CVE-2020-4427, CVE-2020-4428, CVE-2020-4429: https://vulners.com/metasploit/MSF:EXPLOIT/LINUX/HTTP/IBM_DRM_RCE
Pi-hole <= 4.4 RCE
Pi-hole is a Linux-based assembly that allows you to block ads and save sensitive data while on the network. Blocking takes place at the DNS level and allows you to flexibly configure lists of banned resources.
CVE-2020-11108: Pi-hole through 4.4 allows an authenticated adversary to upload arbitrary files. This opportunity can be abuse for arbitaru code execution by writing to a PHP file in the web directory. Exploit: https://vulners.com/exploitdb/EDB-ID:48442
Metsploit module: https://vulners.com/metasploit/MSF:EXPLOIT/UNIX/HTTP/PIHOLE_BLOCKLIST_EXEC
Top 10 Routinely Exploited Vulnerabilities

This month, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the broader U.S. Government are providing this technical guidance to advise IT security professionals.
For each of the mentioned vulnerabilities it is specified which malware it was found in, when it was fixed, IOCs and etc. The list of vulnerabilities includes vulnerabilities from 2012 to 2019:
- CVE-2017-11882
- CVE-2017-0199
- CVE-2017-5638
- CVE-2012-0158
- CVE-2019-0604
- CVE-2017-0143
- CVE-2018-4878
- CVE-2017-8759
- CVE-2015-1641
- CVE-2018-7600
And vulnerabilities in 2020, which managed to be remembered in various events:
You may notice that there are links at the bottom of each Vulners page with a vulnerability. These links include all news and events that will be associated with the vulnerability. Example for CVE-2017-11882:
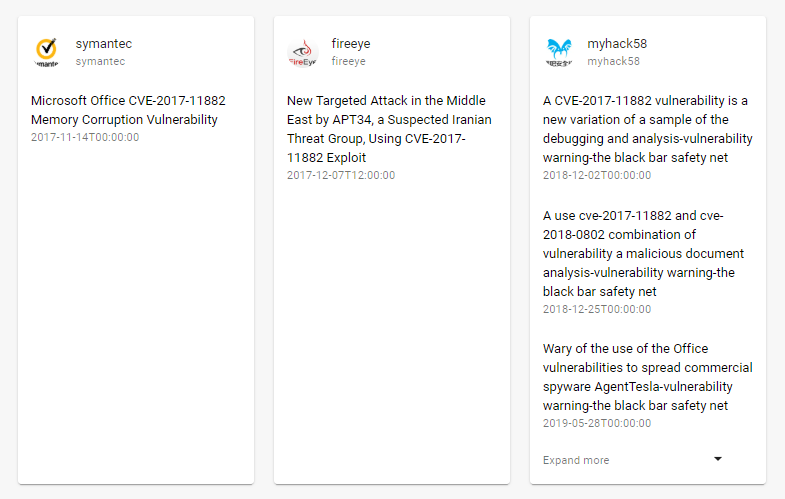
This feature allows you to perform your own analysis of these vulnerabilities and prioritize them for your own purposes.
High-profile vulnerabilities of the month
A new type of DoS attack using the DNS protocol is called NXNSAttack.
Briefly: An attacker sends a request to the Openresolver server, redirecting it to his controlled authoritative server, which responds with a long list of NS victims' servers (most often spoofed names).
Openresolver takes this list and begins to query the victim's DNS for information about these addresses, which causes a large number of NXDomain messages, which leads to an increase in server load. In fact, the attack is directed only at the target DNS server.
At the moment, the only salvation is to install patches on your DNS servers and configure polling limits.
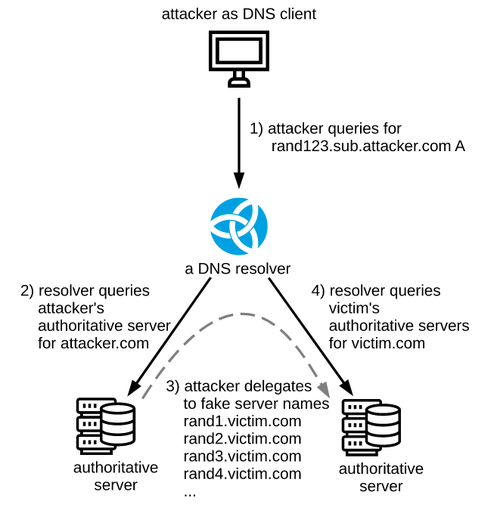
According to research, the gain when attacking the BIND server (9.12.3) can increase the attack by 1000 times (Packet Amplification Factor, PAF).
Vulnerable:
BIND (CVE-2020-8616)
Knot (CVE-2020-12667)
PowerDNS (CVE-2020-10995)
Windows DNS Server
Unbound (CVE-2020-12662)
as well as public DNS services of Google, Cloudflare, Amazon, Quad 9, ICANN and other companies.
- http://www.nxnsattack.com
- https://vulners.com/thn/THN:B16A54F3A6063EA035782D8584261F00
- https://en.blog.nic.cz/2020/05/19/nxnsattack-upgrade-resolvers-to-stop-new-kind-of-random-subdomain-attack
Symantec endpoint privilege escalation
The exploitation of CVE-2020-5837 allow for low privileged user to create a file anywhere in the system. The attacker partially controls the content of the file. There are many ways to abuse this issue. Vulnerable version prior to 14.3
Video PoC Step By Step:
CVE-2020-5837 PoC
Tools
Most of the most interesting and fresh tools that appear we publish in our weekly reviews.
Powershell script obfuscator meant for red teamers. Takes the original command name and displays the obfuscated command name to be used in Powershell.
Malicious Android apk generator (Reverse Shell)

RAT for Discord written in Python3. You can generate binart fle, deploy bot on your own server and after that get access. We don't know the practical meaning of this tool, but it's a cool idea.

Thomas Brewster, a Forbes journalist who raised the fuss, said that Xiaomi will make an option that allows the user to disable data collection in incognito mode. The new privacy setting now allows Mi Browser users to disable aggregated data collection feature while in Incognito Mode, but it bears noting that it’s not enabled by default.
If Xiaomi was serious about its “commitment to user privacy,” it would have sought users for their explicit consent. In its present state, it’s just an illusion of control.
https://vulners.com/thn/THN:D12A519EAC085DA9915F1B1370B970B5

In Ukraine, the data broker Sanix was arrested, which is accused of involvement in trading stolen user data. Hacker has been engaged in its malicious activities since at least 2018. The Ukrainian did not break anything, but collected and resold data obtained in the course of other hacks.
Sanix was reportedly involved in data collections Collection #1, #2, etc., which appeared in January 2019 and contained a total of more than 3.5 billion. email addresses, passwords, and phone numbers.
https://vulners.com/thn/THN:32403D554849523AAB204629304EDE77
https://vulners.com/thn/THN:78C014B66408C3D4219EC395F9F108C0
EasyJet Suffers Data Breach

British low-cost airline EasyJet reported a leak of information about 9 million customers and data of 2208 Bank cards. The airline claims that the data was obtained by hackers during a technically sophisticated cyberattack.
The leaked data included the email addresses and information about the flights. The company claims to have found no evidence that this data was used maliciously. EasyJect will contact customers affected by the leak in the coming days, with a deadline of may 26. The company has already contacted those customers whose Bank card details were stolen, the report said. Passengers ' passport details were not leaked.

The publication Motherboard, whose journalists are closely following the lawsuits between Facebook and the Israeli NSO Group, has unearthed yet another detail of Semites' not entirely legal activities.
NSO produces Pegasus software designed to hack WhatsApp, and sells it all over the world to law enforcement agencies, intelligence agencies and private security companies. WhatsApp is being sued by Facebook.
Motherboard was able to obtain information from a former NSO employee who anonymously transmitted data regarding the Israeli company's infrastructure, in particular the IP address used to infect the Pegasus victim. It turned out that between 2015 and 2016, several domains were tied to that IP. These included domains impersonating the resource of the Facebook security team and the FedEx parcel tracking service.
It was suspected that this IP address belonged to Amazon. That is, the Israeli NSO used a phishing page Facebook to infect smartphones from the American server. Nice :)

The RagnarLocker operator first installs Oracle VirtualBox on the compromised system and configures its full access to all local and shared disks. Then MicroXP v0.82 (stripped-down Windows XP SP3) is installed on the virtual machine and RagnarLocker is placed on it.
In this way, ransomware hides from antiviruses, as all the actions taken to encrypt the infected system files are performed by the VirtualBox process. This trick was revealed by the British antivirus Sophos, which says that it is the first time it has encountered such a trick.
VirtualBox is signed and antiviruses are treated less suspiciously by the signed processes. But as soon as this technique becomes mass, a detective will appear. It is possible to generate many ways of changing the file system with the help of white software, but such ways will not work very long.
Please leave your feedback. It takes less than one minute and helps us get better: https://forms.gle/D17BaFwD5hJnKkUUA
