New DNS Vulnerability Lets Attackers Launch Large-Scale DDoS Attacks
7.5 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
5 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:N/I:N/A:P
Israeli cybersecurity researchers have disclosed details about a new flaw impacting DNS protocol that can be exploited to launch amplified, large-scale distributed denial-of-service (DDoS) attacks to takedown targeted websites.
Called NXNSAttack, the flaw hinges on the DNS delegation mechanism to force DNS resolvers to generate more DNS queries to authoritative servers of attacker’s choice, potentially causing a botnet-scale disruption to online services.
“We show that the number of DNS messages exchanged in a typical resolution process might be much higher in practice than what is expected in theory, mainly due to a proactive resolution of name-servers’ IP addresses,” the researchers said in the paper.
“We show how this inefficiency becomes a bottleneck and might be used to mount a devastating attack against either or both, recursive resolvers and authoritative servers.”
Following responsible disclosure of NXNSAttack, several of the companies in charge of the internet infrastructure, including PowerDNS (CVE-2020-10995), CZ.NIC (CVE-2020-12667), Cloudflare, Google, Amazon, Microsoft, Oracle-owned Dyn, Verisign, and IBM Quad9, have patched their software to address the problem.
The DNS infrastructure has been previously at the receiving end of a rash of DDoS attacks through the infamous Mirai botnet, including those against Dyn DNS service in 2016, crippling some of the world’s biggest sites, including Twitter, Netflix, Amazon, and Spotify.
The NXNSAttack Method
A recursive DNS lookup happens when a DNS server communicates with multiple authoritative DNS servers in a hierarchical sequence to locate an IP address associated with a domain (e.g., www.google.com) and return it to the client.
This resolution typically starts with the DNS resolver controlled by your ISPs or public DNS servers, like Cloudflare (1.1.1.1) or Google (8.8.8.8), whichever is configured with your system.
The resolver passes the request to an authoritative DNS name server if it’s unable to locate the IP address for a given domain name.
But if the first authoritative DNS name server also doesn’t hold the desired records, it returns the delegation message with addresses to the next authoritative servers to which DNS resolver can query.
In other words, an authoritative server tells the recursive resolver: “I do not know the answer, go and query these and these name servers, e.g., ns1, ns2, etc., instead”.
This hierarchical process goes on until the DNS resolver reaches the correct authoritative server that provides the domain’s IP address, allowing the user to access the desired website.
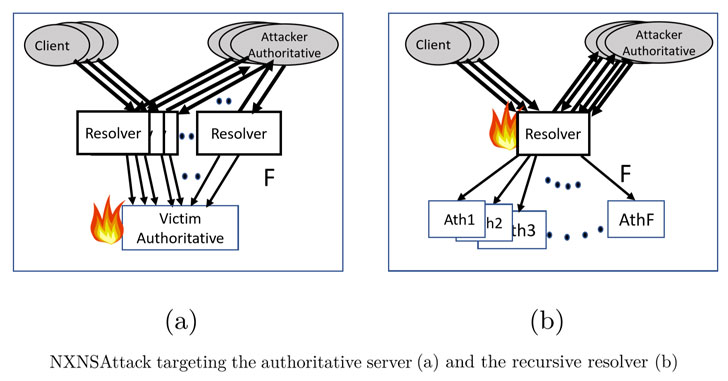
Researchers found that these large undesired overheads can be exploited to trick recursive resolvers into forcefully continuously sending a large number of packets to a targeted domain instead of legitimate authoritative servers.
In order to mount the attack through a recursive resolver, the attacker must be in possession of an authoritative server, the researchers said.
“This can be easily achieved by buying a domain name. An adversary who acts as an authoritative server can craft any NS referral response as an answer to different DNS queries,” the researchers said.
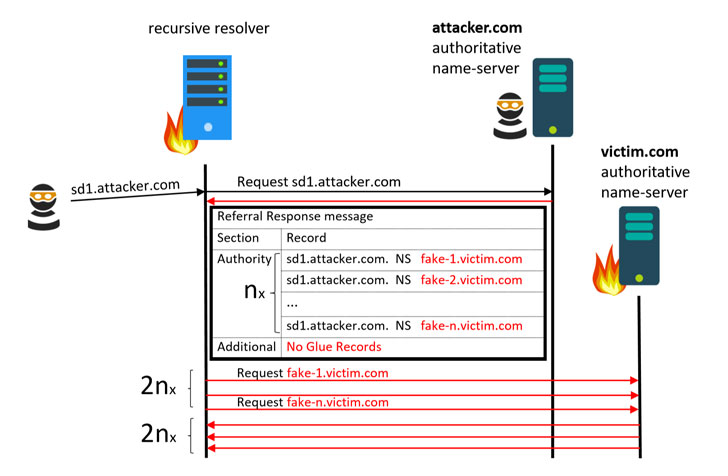
The NXNSAttack works by sending a request for an attacker-controlled domain (e.g., “attacker.com”) to a vulnerable DNS resolving server, which would forward the DNS query to the attacker-controlled authoritative server.
Instead of returning addresses to the actual authoritative servers, the attacker-controlled authoritative server responds to the DNS query with a list of fake server names or subdomains controlled by the threat actor that points to a victim DNS domain.
The DNS server, then, forwards the query to all the nonexistent subdomains, creating a massive surge in traffic to the victim site.
The researchers said the attack can amplify the number of packets exchanged by the recursive resolver by as much as a factor of more than 1,620, thereby overwhelming not only the DNS resolvers with more requests they can handle, but also flood the target domain with superfluous requests and take it down.
What’s more, using a botnet such as the Mirai as a DNS client can further augment the scale of the attack.
“Controlling and acquiring a huge number of clients and a large number of authoritative NSs by an attacker is easy and cheap in practice,” the researchers said.
“Our initial goal was to investigate the efficiency of recursive resolvers and their behavior under different attacks, and we ended up finding a new seriously looking vulnerability, the NXNSAttack,” the researchers concluded.
“The key ingredients of the new attack are (i) the ease with which one can own or control an authoritative name server, and (ii) the usage of nonexistent domain names for name servers and (iii) the extra redundancy placed in the DNS structure to achieve fault tolerance and fast response time,” they added.
It’s highly recommended that network administrators who run their own DNS servers update their DNS resolver software to the latest version.
7.5 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
5 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:N/I:N/A:P