CISA Warns of Atlassian Confluence Hard-Coded Credential Bug Exploited in Attacks
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added the recently disclosed Atlassian security flaw to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation.
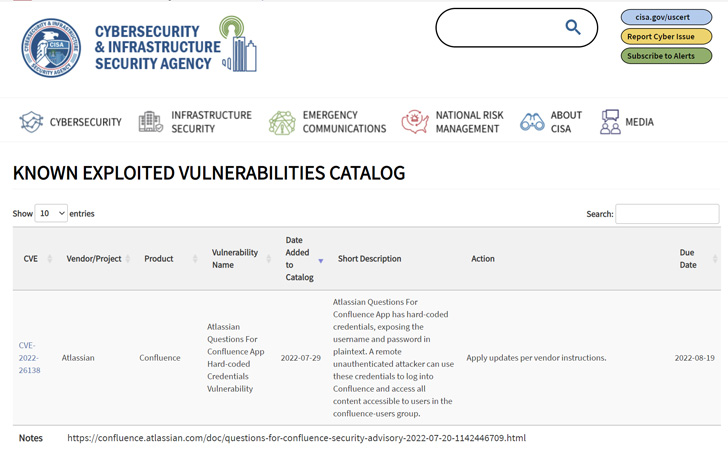
The vulnerability, tracked as CVE-2022-26138, concerns the use of hard-coded credentials when the Questions For Confluence app is enabled in Confluence Server and Data Center instances.
“A remote unauthenticated attacker can use these credentials to log into Confluence and access all content accessible to users in the confluence-users group,” CISA notes in its advisory.
Depending on the page restrictions and the information a company has in Confluence, successful exploitation of the shortcoming could lead to the disclosure of sensitive information.
Although the bug was addressed by the Australian software company last week in versions 2.7.38 and 3.0.5, it has since come under active exploitation, cybersecurity firm Rapid7 disclosed this week.
“Exploitation efforts at this point do not seem to be very widespread, though we expect that to change,” Erick Galinkin, principal AI researcher at Rapid7, told The Hacker News.
“The good news is that the vulnerability is in the Questions for Confluence app and not in Confluence itself, which reduces the attack surface significantly.”
With the flaw now added to the catalog, Federal Civilian Executive Branch (FCEB) in the U.S. are mandated to apply patches by August 19, 2022, to reduce their exposure to cyberattacks.
“At this point, the vulnerability has been public for a relatively short amount of time,” Galinkin noted. “Coupled with the absence of meaningful post-exploitation activity, we don’t yet have any threat actors attributed to the attacks.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.