
Atlassian Confluence: Questions for Confluence App Hardcoded Credentials Vulnerability (CVE-2022-26138)
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
Over the last few months, Atlassian Confluence has increasingly become a target for attackers. In June 2022, a critical severity OGNL Remote Code Execution vulnerability was disclosed (CVE-2022-26134). More recently, CVE-2022-26138 was disclosed on social media platforms in July 2022.
In CVE-2022-26138, a Confluence user account is created by the Questions for Confluence app with hardcoded credentials stored inside the plugin jar file available on Atlassian packages. An attacker with knowledge of these credentials could log into the Confluence application and access all contents within the confluence-users group. Atlassian has rated the vulnerability "critical" and highlighted that the vulnerability is being exploited in the wild.
Due to the nature of this vulnerability, it can only be verified remotely by logging into the Confluence application with the hardcoded credentials. Traditional open source scanners and scripts are checking for the Location HTTP response header and 302 status code to verify the credentials, which could result in false positives. Qualys Web Application Scanning has released QID 150556 that confirms the vulnerability detection in two steps. The detection takes an additional step to verify the valid credentials by navigating to the user profile page and verifying that the correct page is returned. This check is much more efficient in comparison to open source scanners and eliminates any possibility of false positives.
About CVE-2022-26138
According to Confluence's Questions for Confluence Security Advisory, both Confluence Server and Confluence Data Center products using affected versions of the Questions for Confluence app are impacted by CVE-2022-26138.
Affected versions :
Questions for Confluence 2.7.x| 2.7.34
2.7.35
—|—
Questions for Confluence 3.0.x| 3.0.2
Hardcoded Credentials Vulnerability
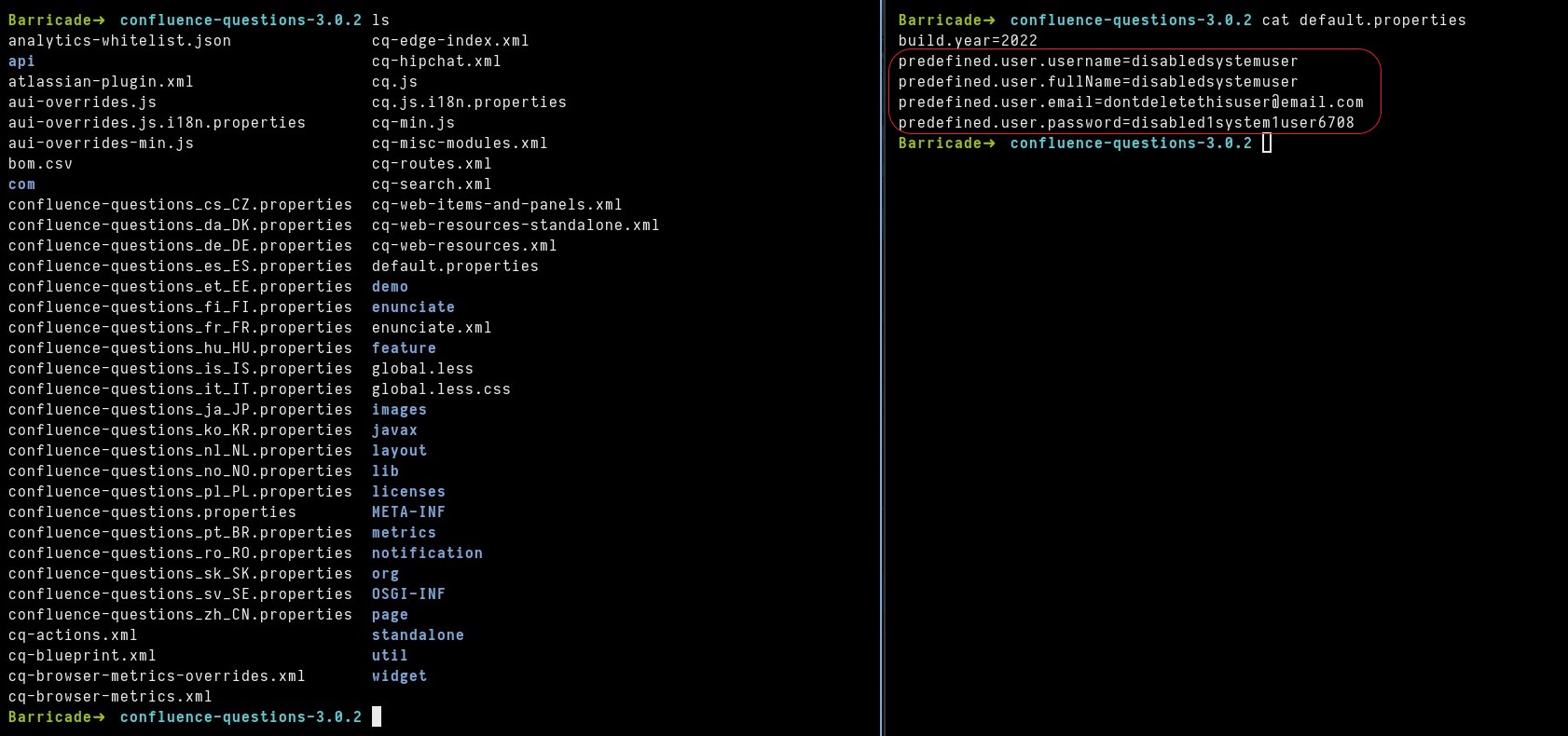
Affected versions of the Questions for Confluence app, when installed on a Confluence application, create a user account with username disabledsystemuser and password disabled1system1user6708 and the account is added to confluence-users group, which allows viewing and editing all non-restricted pages within Confluence by default. A remote attacker can easily leverage these credentials to browse sensitive contents within the Confluence application.
These hardcoded credentials are stored in default.properties file inside a confluence-questions-X.X.X.jar file, as shown below.
Detecting the Vulnerability with Qualys Web Application Scanning
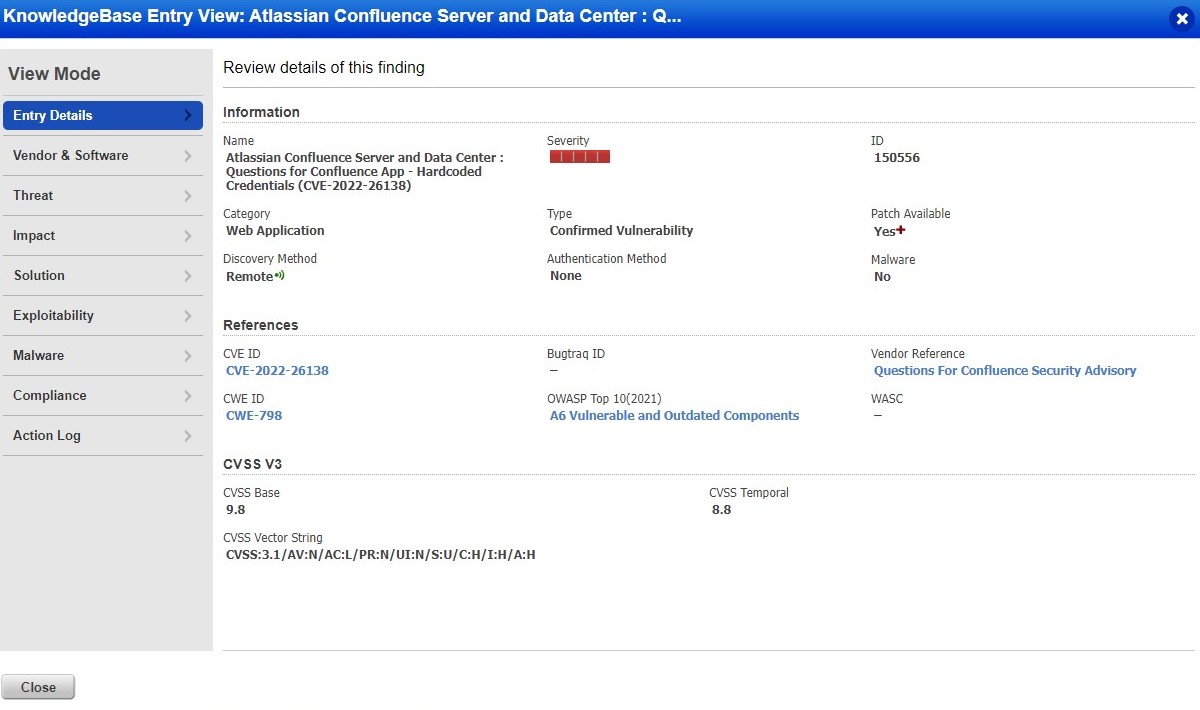
Existing Qualys customers can detect CVE-2022-26138 on their target Confluence instance with Qualys Web Application Scanning (WAS) using the following Qualys ID (QID):
- 150556 : Atlassian Confluence Server and Data Center : Questions for Confluence App - Hardcoded Credentials (CVE-2022-26138)
The QID is part of the core category. A vulnerability scan with a core or custom search list including the QID in the options profile will flag all vulnerable applications, as shown below.
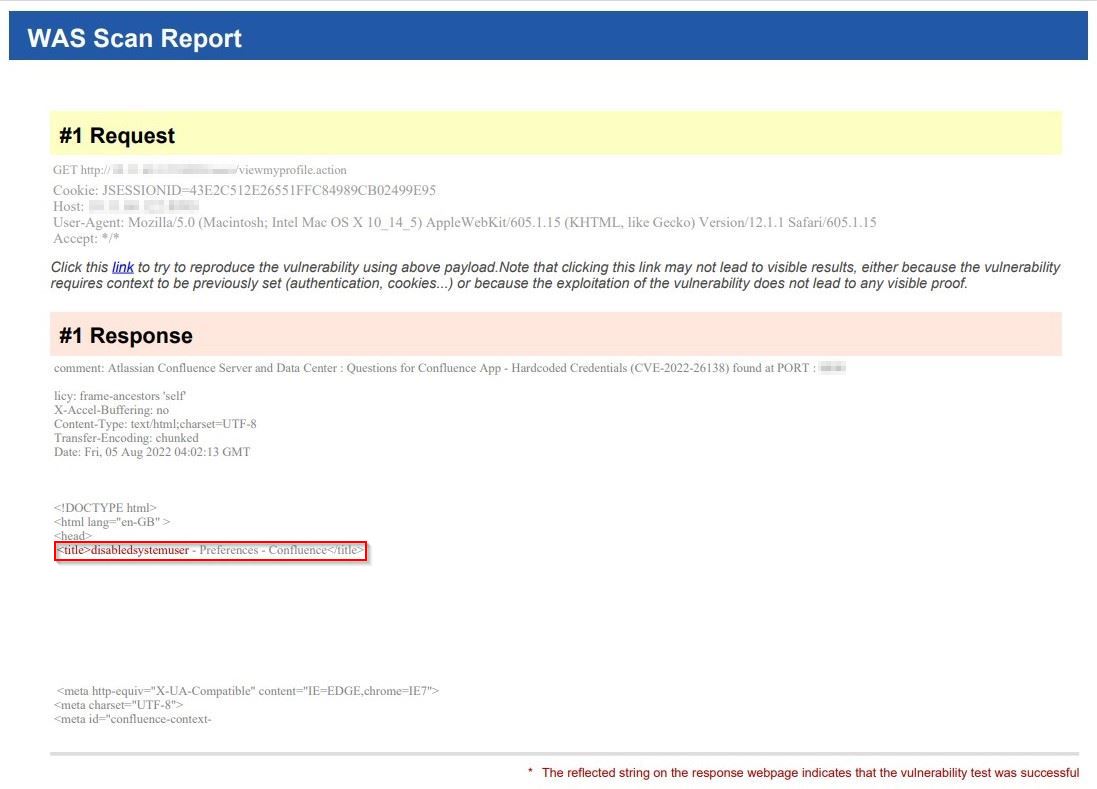
Qualys WAS Report
Once the vulnerability is successfully detected by Qualys WAS, the user will see similar results in the vulnerability scan report, as shown here:
Solution & Mitigation
To remediate this vulnerability, any organization using the Questions for Confluence app is advised to ensure the following:
- Upgrade to Version 2.7.x >= 2.7.38 (compatible with Confluence 6.13.18 through 7.16.2) and Versions >= 3.0.5 (compatible with Confluence 7.16.3 and later)
- Disable or delete the disabledsystemuser account
Please note that uninstalling the Questions for Confluence app does not remediate this vulnerability. The disabledsystemuser account does not automatically get removed after the app has been uninstalled. It is possible for this account to be present if the Questions for Confluence app was previously installed. It is advised to check the list of active users to ensure the Confluence instance is not affected.
Credit
Confluence Security Advisory: <https://confluence.atlassian.com/doc/questions-for-confluence-security-advisory-2022-07-20-1142446709.html>
CVE Details:
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P