ALERT: Critical RCE Bug in VMware vCenter Server Under Active Attack
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
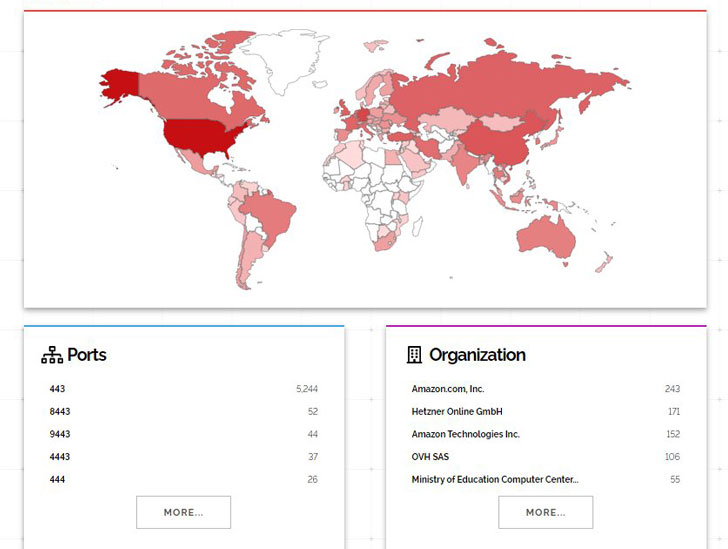
Malicious actors are actively mass scanning the internet for vulnerable VMware vCenter servers that are unpatched against a critical remote code execution flaw, which the company addressed late last month.
The ongoing activity was detected by Bad Packets on June 3 and corroborated yesterday by security researcher Kevin Beaumont. “Mass scanning activity detected from 104.40.252.159 checking for VMware vSphere hosts vulnerable to remote code execution,” tweeted Troy Mursch, chief research officer at Bad Packets.
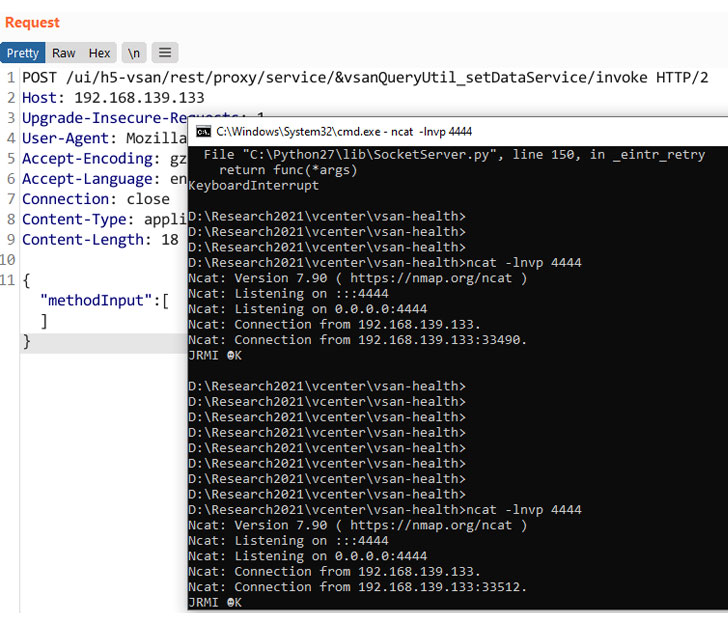
The development follows the publication of a proof-of-concept (PoC) RCE exploit code targeting the VMware vCenter bug.
Tracked as CVE-2021-21985 (CVSS score 9.8), the issue is a consequence of a lack of input validation in the Virtual SAN (vSAN) Health Check plug-in, which could be abused by an attacker to execute commands with unrestricted privileges on the underlying operating system that hosts the vCenter Server.
Although the flaw was rectified by VMware on May 25, the company strongly urged its customers to apply the emergency change immediately. “In this era of ransomware it is safest to assume that an attacker is already inside the network somewhere, on a desktop and perhaps even in control of a user account, which is why we strongly recommend declaring an emergency change and patching as soon as possible,” VMware said.
This is not the first time adversaries have opportunistically mass scanned the internet for vulnerable VMware vCenter servers. A similar remote code execution vulnerability (CVE-2021-21972) that was patched by VMware in February became the target of cyber threat actors attempting to exploit and take control of unpatched systems.
At least 14,858 vCenter servers were found reachable over the internet at the time, according to Bad Packets and Binary Edge.
What’s more, a new research from Cisco Talos earlier this week found that the threat actor behind the Python-based Necro bot wormed its way into exposed VMware vCenter servers by abusing the same security weakness to boost the malware’s infection propagation capabilities.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C