Multiple Code Execution Flaws Found In PHP Programming Language
EPSS
Percentile
86.6%
Maintainers of the PHP programming language recently released the latest versions of PHP to patch multiple high-severity vulnerabilities in its core and bundled libraries, the most severe of which could allow remote attackers to execute arbitrary code and compromise targeted servers.
Hypertext Preprocessor, commonly known as PHP, is the most popular server-side web programming language that powers over 78 percent of the Internet today.
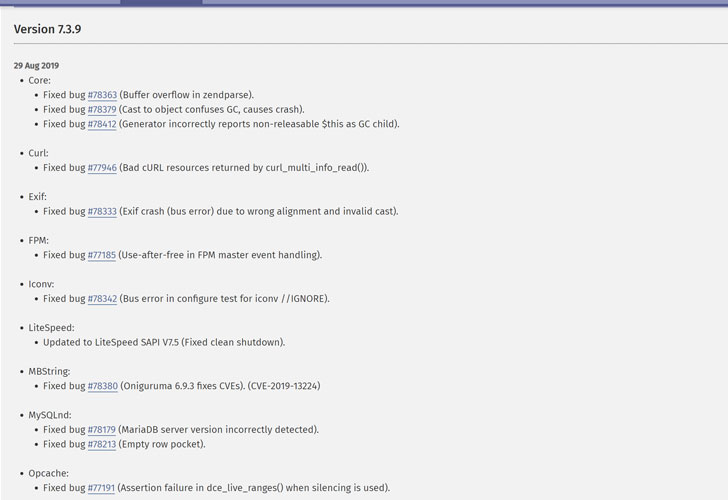
The latest releases under several maintained branches include PHP version 7.3.9, 7.2.22 and 7.1.32, addressing multiple security vulnerabilities.
Depending on the type, occurrence, and usage of the affected codebase in a PHP application, successful exploitation of some of the most severe vulnerabilities could allow an attacker to execute arbitrary code in the context of the affected application with associated privileges.
On the other hand, failed attempts at exploitation will likely result in a denial of service (DoS) condition on the affected systems.
The vulnerabilities could leave hundreds of thousands of web applications that rely on PHP open to code execution attacks, including websites powered by some popular content management systems like WordPress, Drupal and Typo3.
Out of these, a ‘use-after-free’ code execution vulnerability, assigned as CVE-2019-13224, resides in Oniguruma, a popular regular expression library that comes bundled with PHP, as well as many other programming languages.
A remote attacker can exploit this flaw by inserting a specially crafted regular expression in an affected web application, potentially leading to code execution or causing information disclosure.
“The attacker provides a pair of a regex pattern and a string, with a multi-byte encoding that gets handled by onig_new_deluxe(),” Red Hat says in its security advisory describing the vulnerability.
Other patched flaws affect curl extension, Exif function, FastCGI Process Manager (FPM), Opcache feature, and more.
Good news is that so far there is no report of any of these security vulnerabilities being exploited in the wild by attackers.
The PHP security team has addressed the vulnerabilities in the latest versions. So users and hosting providers are strongly recommended to upgrade their servers to the latest PHP version 7.3.9, 7.2.22, or 7.1.32.