Critical Firefox 0-Day Under Active Attacks – Update Your Browser Now!
EPSS
Percentile
97.6%
Attention! Are you using Firefox as your web browsing software on your Windows, Linux, or Mac systems?
If yes, you should immediately update your free and open-source Firefox web browser to the latest version available on Mozilla’s website.
Why the urgency? Mozilla earlier today released Firefox 72.0.1 andFirefox ESR 68.4.1 versions to patch a critical zero-day vulnerability in its browsing software that an undisclosed group of hackers is actively exploiting in the wild.
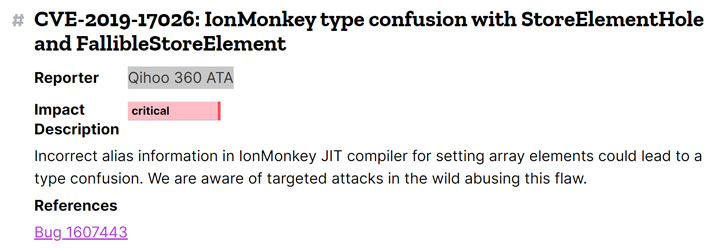
Tracked as ‘CVE-2019-17026,’ the bug is a critical ‘type confusion vulnerability’ that resides in the IonMonkey just-in-time (JIT) compiler of the Mozilla’s JavaScript engine SpiderMonkey.
In general, a type confusion vulnerability occurs when the code doesn’t verify what objects it is passed to and blindly uses it without checking its type, allowing attackers to crash the application or achieve code execution.
Without revealing details about the security flaw and any details on the ongoing potential cyberattacks, Mozilla said, “incorrect alias information in IonMonkey JIT compiler for setting array elements could lead to type confusion.”
That means, the issue in the vulnerable JavaScript engine component can be exploited by a remote attacker just by tricking an unsuspecting user into visiting a maliciously crafted web page to execute arbitrary code on the system within the context of the application.
The vulnerability was reported to Mozilla by cybersecurity researchers at Qihoo 360 ATA, who has also not yet released any information about their investigation, findings, and exploit.
Though Firefox, by default, automatically installs updates when they are available and activate a new version after a restart, you can always do a manual update using the built-in functionality by navigating to Menu > Help > About Mozilla Firefox.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.