Another Google Chrome 0-Day Bug Found Actively Exploited In-the-Wild
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P
Google has addressed yet another actively exploited zero-day in Chrome browser, marking the second such fix released by the company within a month.
The browser maker on Friday shipped 89.0.4389.90 for Windows, Mac, and Linux, which is expected to be rolling out over the coming days/weeks to all users.
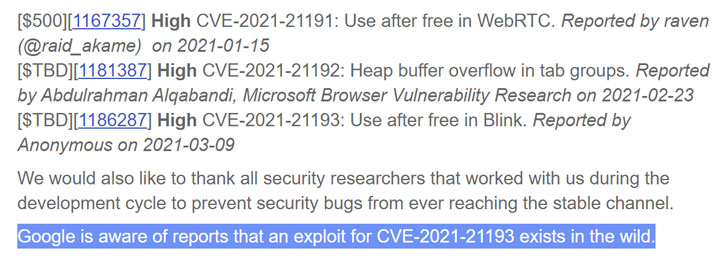
While the update contains a total of five security fixes, the most important flaw rectified by Google concerns a use after free vulnerability in its Blink rendering engine. The bug is tracked as CVE-2021-21193.
Details about the flaw are scarce except that it was reported to Google by an anonymous researcher on March 9.
According to IBM, the vulnerability is rated 8.8 out of 10 on the CVSS scale, and could allow a remote attacker to execute arbitrary code on the target system. “By persuading a victim to visit a specially crafted Web site, a remote attacker could exploit this vulnerability to execute arbitrary code or cause a denial of service condition on the system,” the report stated.
As is usually the case with actively exploited flaws, Google issued a terse statement acknowledging that an exploit for CVE-2021-21193 existed but refrained from sharing additional information until a majority of users are updated with the fixes and prevent other threat actors from creating exploits targeting this zero-day.
“Google is aware of reports that an exploit for CVE-2021-21193 exists in the wild,” Chrome Technical Program Manager Prudhvikumar Bommana noted in a blog post.
With this update, Google has fixed three zero-day flaws in Chrome since the start of the year.
Earlier this month, the company issued a fix for an “object lifecycle issue in audio” (CVE-2021-21166) which it said was being actively exploited. Then on February 4, the company resolved another actively-exploited heap buffer overflow flaw (CVE-2021-21148) in its V8 JavaScript rendering engine.
Chrome users can update to the latest version by heading to Settings > Help > About Google Chrome to mitigate the risk associated with the flaw.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P