New Chrome 0-day Bug Under Active Attacks – Update Your Browser ASAP!
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P
Exactly a month after patching an actively exploited zero-day flaw in Chrome, Google today rolled out fixes for yet another zero-day vulnerability in the world’s most popular web browser that it says is being abused in the wild.
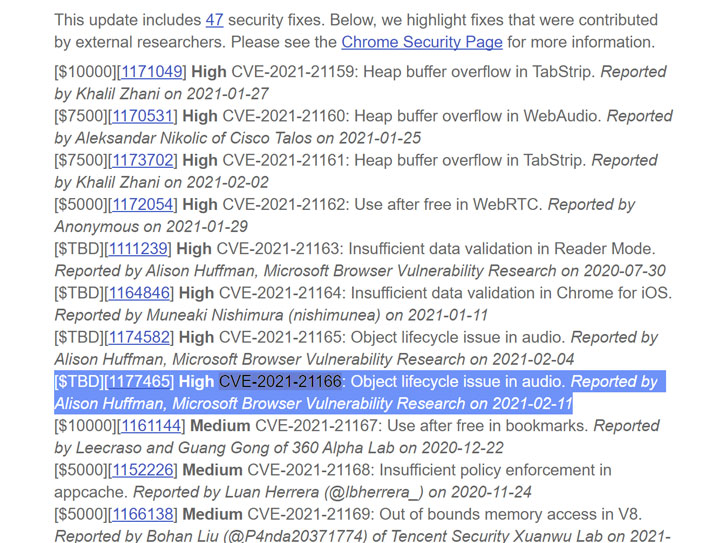
Chrome 89.0.4389.72, released by the search giant for Windows, Mac, and Linux on Tuesday, comes with a total of 47 security fixes, the most severe of which concerns an “object lifecycle issue in audio.”
Tracked as CVE-2021-21166, the security flaw is one of the two bugs reported last month by Alison Huffman of Microsoft Browser Vulnerability Research on February 11. A separate object lifecycle flaw, also identified in the audio component, was reported to Google on February 4, the same day the stable version of Chrome 88 became available.
With no additional details, it’s not immediately clear if the two security shortcomings are related.
Google acknowledged that an exploit for the vulnerability exists in the wild but stopped short of sharing more specifics to allow a majority of users to install the fixes and prevent other threat actors from creating exploits targeting this zero-day.
“Google is aware of reports that an exploit for CVE-2021-21166 exists in the wild,” Chrome Technical Program Manager Prudhvikumar Bommana said.
This is the second zero-day flaw in Chrome that Google has addressed since the start of the year.
On February 4, the company issued a fix for an actively-exploited heap buffer overflow flaw (CVE-2021-21148) in its V8 JavaScript rendering engine. Additionally, Google last year resolved five Chrome zero-days that were actively exploited in the wild in a span of one month between October 20 and November 12.
Chrome users can update to the latest version by heading to Settings > Help > About Google Chrome to mitigate the risk associated with the flaw.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P