
Part 1: An In-Depth Look at the Latest Vulnerability Threat Landscape
EPSS
Percentile
95.1%
The number of vulnerabilities is steadily increasing over the years, as evidenced by the 206,000 vulnerabilities reported and still counting in the National Vulnerability Database (NVD). With each subsequent year, this trend has persisted since 2016, surpassing the previous vulnerability count.
In 2023 alone, over 14K (14,205 to be precise) vulnerabilities have already been reported.
While organizations employ huge efforts to recognize vulnerabilities similar in nature, it's not always the case. There may be several vulnerabilities that are different and are more critical than others, even when CVSS considers a vulnerability to be critical.
This 3 part blog series will help you uncover some valuable insights involved in the vulnerability threat landscape, the top-most malware and ransomware vulnerabilities that are exploited, and how
Qualys VMDR TruRisk Dashboard can equip you with the right measures.
When we consider the vulnerability and threat landscape, here’s what every organization is concerned
about — What do we know about the 5,000-odd CVEs? Can we discern any patterns? Is one type of vulnerability more prevalent or favored by threat actors and ransomware groups over others?
As mentioned above, some vulnerabilities are more critical than others; even when the CVSS considers it to be of similar effect.
- Compromise susceptible systems
- Establish a presence within organizations
- Propagate laterally.
Vulnerabilities that have weaponized exploits available, and become part of the arsenal used by malware, threat actors, and ransomware groups for system infiltration. As evidence of exploitation in the wild becomes an available subset, they are also tracked as part of the CyberSecurity & Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities (KEV) catalog.
 Fig 1. High-Risk Vulnerabilities
Fig 1. High-Risk Vulnerabilities
Access Vector: Network vs Local
After analyzing the access vector associated with the high-risk vulnerabilities, (as shown in Fig.1), the most significant observation that emerges is over 80% of the CVEs (Fig. 2), have an access vector of Network according to data from NVD. Therefore, 80% of vulnerabilities can be exploited remotely over the network. This finding aligns with the perspective of attackers, who generally lack physical access to the devices they aim to exploit.
It is crucial to note that this percentage also includes vulnerabilities in client-side applications such as Google Chrome (e.g., CVE-2023-3079), which can be remotely exploited; simply by tricking unsuspecting users into clicking on a malicious URL and compromising their systems. Therefore, to accurately detect vulnerabilities and evaluate their actual risk, it is imperative that organizations enable the use of different sensors, from agent and authenticated scans to network scanners for a comprehensive risk assessment.
 Fig 2: Percentage of CVEs with Access Vector Types
Fig 2: Percentage of CVEs with Access Vector Types
Authentication/Privilege Required to Exploiting the Vulnerability
It is also worth noting that over 80% of the high-risk vulnerabilities (Fig. 3) do not require authentication for exploitation. Oftentimes, attackers have limited or no knowledge about them, and establish initial access to move laterally within the organization.
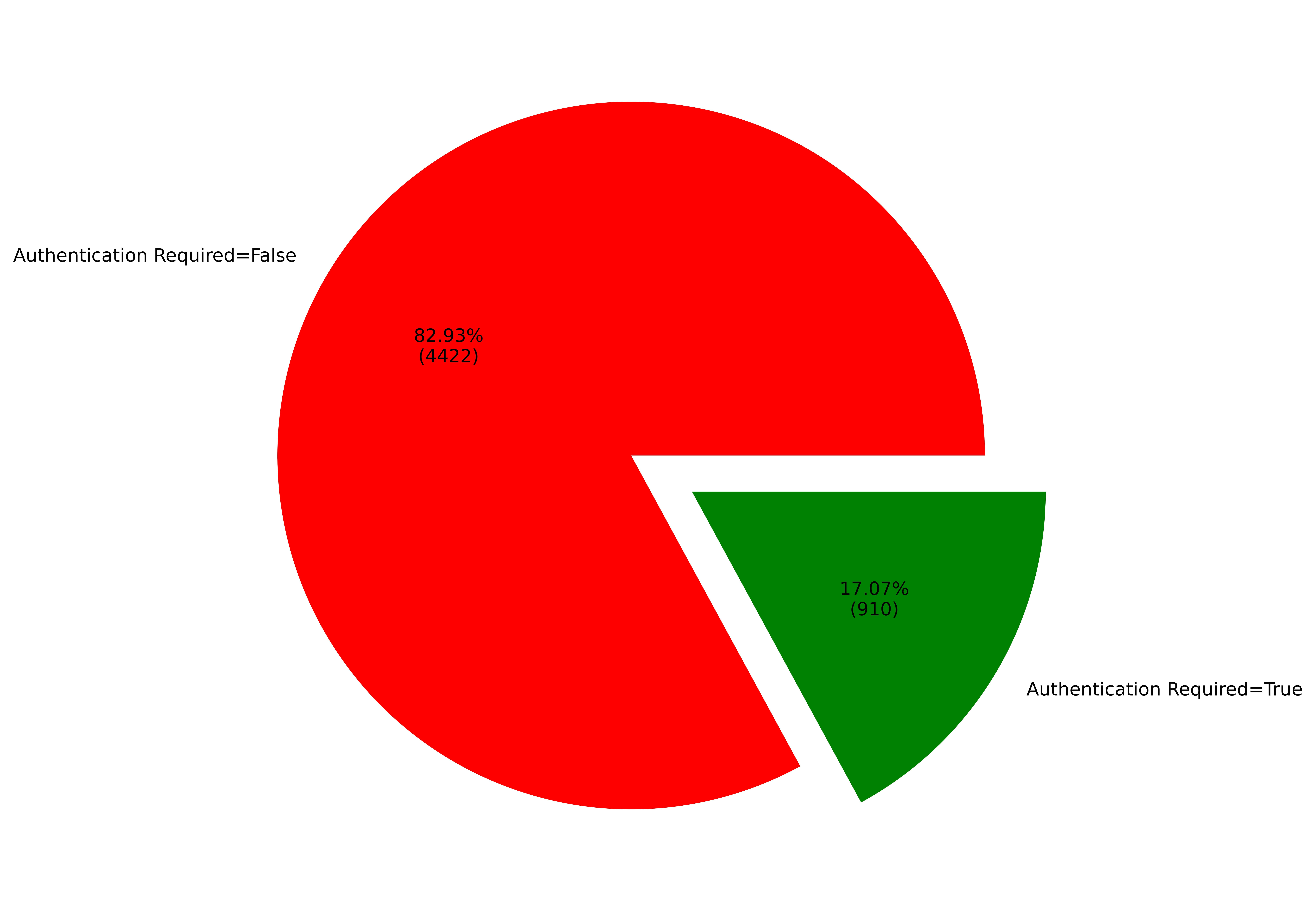 Fig. 3: Percentage of CVEs with Authentication/Privilege
Fig. 3: Percentage of CVEs with Authentication/Privilege
Required to Exploit
Common Weakness Exploited by High-Risk Vulnerabilities
Now, let's examine the most prevalent weakness such high-risk vulnerabilities exploit. Despite more robust memory management and safety features, buffer overflow vulnerabilities are the most significant of them.
Even with automatic memory management (garbage collection) and array bounds checking in higher-level languages such as Java, Python, and others, these vulnerabilities still account for the top-most position (as shown in Fig 4), with nearly a thousand vulnerabilities susceptible to this type of issue compared to others, and one might have expected frequent buffer overflow vulnerabilities to decrease.
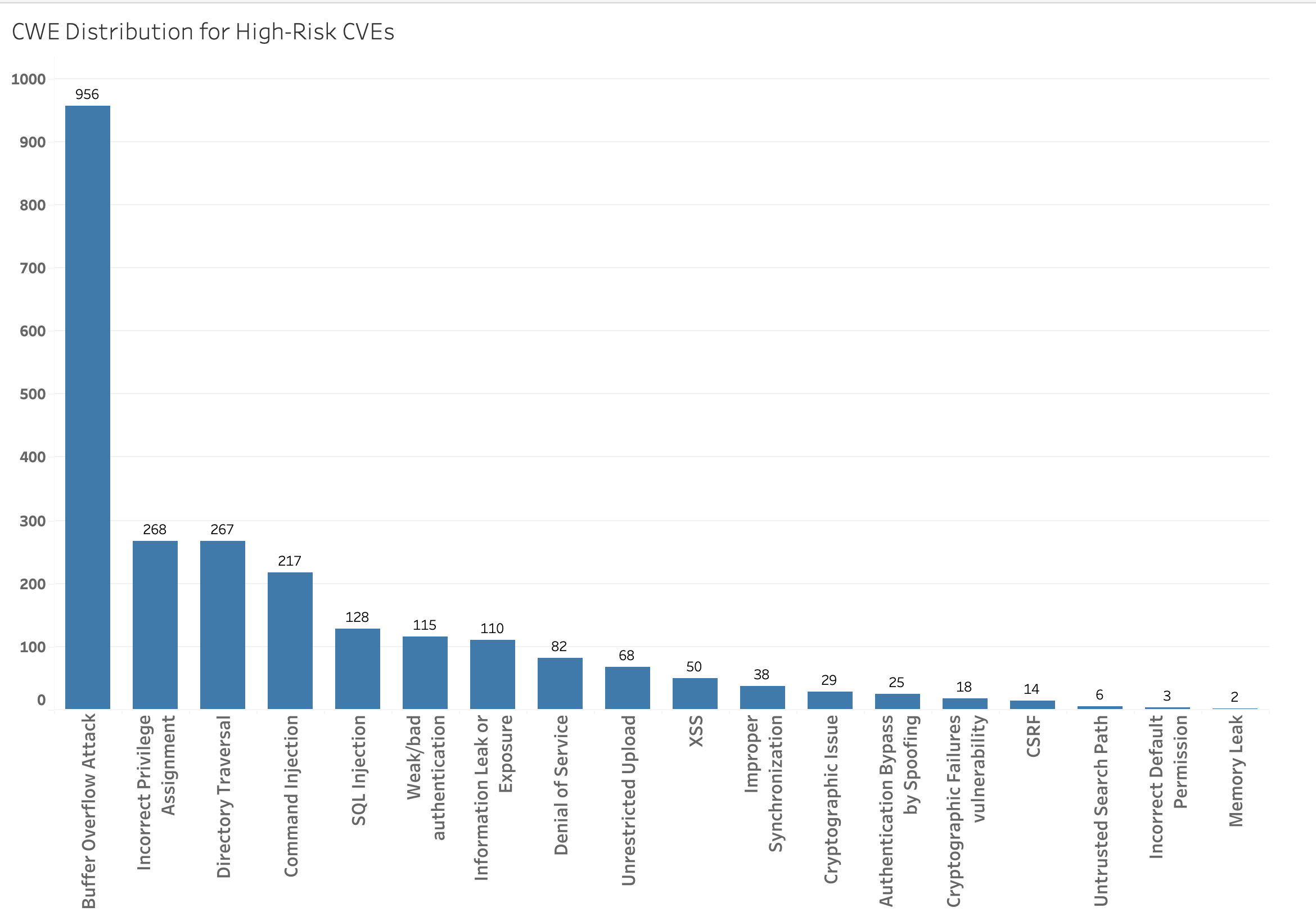 Fig. 4: CWE distribution for High-Risk CVEs
Fig. 4: CWE distribution for High-Risk CVEs
High-Risk Vulnerabilities Vs MITRE ATT&CK Framework
In recent months, the Qualys research team has dedicated significant efforts to mapping vulnerabilities to the MITRE ATT&CK Framework tactics and techniques.
The MITRE ATT&CK Framework serves as a comprehensive knowledge base that categorizes and describes adversary tactics, techniques, and procedures (TTPs) utilized in cyber-attacks. For defenders to effectively safeguard against them, it is crucial to contextualize this information within the specific environment. From identifying potential attack paths to promptly addressing vulnerabilities before adversaries exploit them.
Here are some of the most-known Tactics & Techniques leveraged by high-risk vulnerabilities.
A. High-Risk Vulnerabilities vs MITRE ATT&CK Tactic
The top three tactics leveraged by high-risk vulnerabilities are Initial Access, Lateral Movement, and Privilege Escalation (Fig. 5). This kind of tactic is most executed when the attackers employ are infiltrating an organization. Initially, they seek a foothold by exploiting vulnerabilities that grant them initial access.
Next, they escalate privileges and move laterally to compromise other systems. It is important to note that not all vulnerabilities neatly align with a specific tactic or technique. Nonetheless, this data provides valuable insights into the playbook attackers follow to breach an organization's defenses.
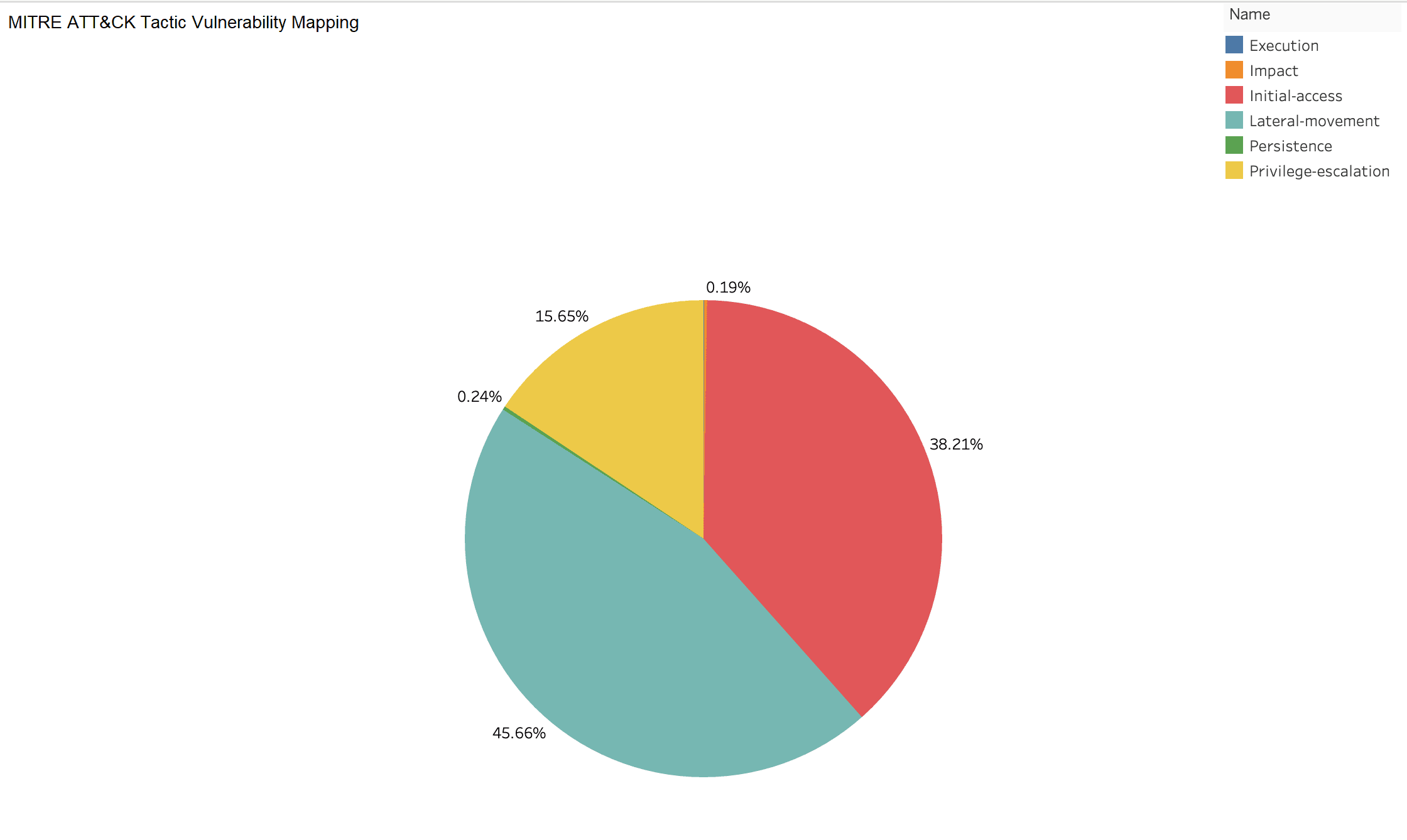 Fig. 5. High-Risk Vulns Vs MITRE ATT&CK Tactic
Fig. 5. High-Risk Vulns Vs MITRE ATT&CK Tactic
B. High-Risk Vulnerabilities Vs MITRE ATT&CK Technique
A similar pattern emerges when we delve into the techniques associated with such vulnerabilities. The top techniques observed are the exploitation of remote services, public-facing applications, and even for privilege escalation.
Fig. 6. Attackers often initiate their intrusion by exploiting a public-facing application, subsequently utilizing either remote service exploits or privilege escalation to facilitate lateral movement within the network.
 Fig. 6. High-Risk Vulns vs MITRE ATT&CK Technique
Fig. 6. High-Risk Vulns vs MITRE ATT&CK Technique
High-Risk Vulns Vs CISA Known Exploited Vulns (CISA KEV)
One of the most valuable contributions made by the team at CISA is the publication of a list of known exploited vulnerabilities, which is rapidly approaching a thousand entries. This effort has dramatically assisted defenders in prioritizing the appropriate vulnerabilities for remediation.
However, defenders should not solely rely on ONLY prioritizing and addressing the vulnerabilities listed in the CISA KEV catalog, as it does not necessarily encompass all vulnerabilities exploited in the wild. For instance, CVE-2021-42298, a vulnerability in Microsoft Defender, is reportedly exploited by the Varison group but is not part of the CISA KEV catalog.Qualys VMDR leverages over 25+ threat intelligence sources to accurately assess the vulnerabilities/CVEs that can give better visibility within QualysTrurisk.
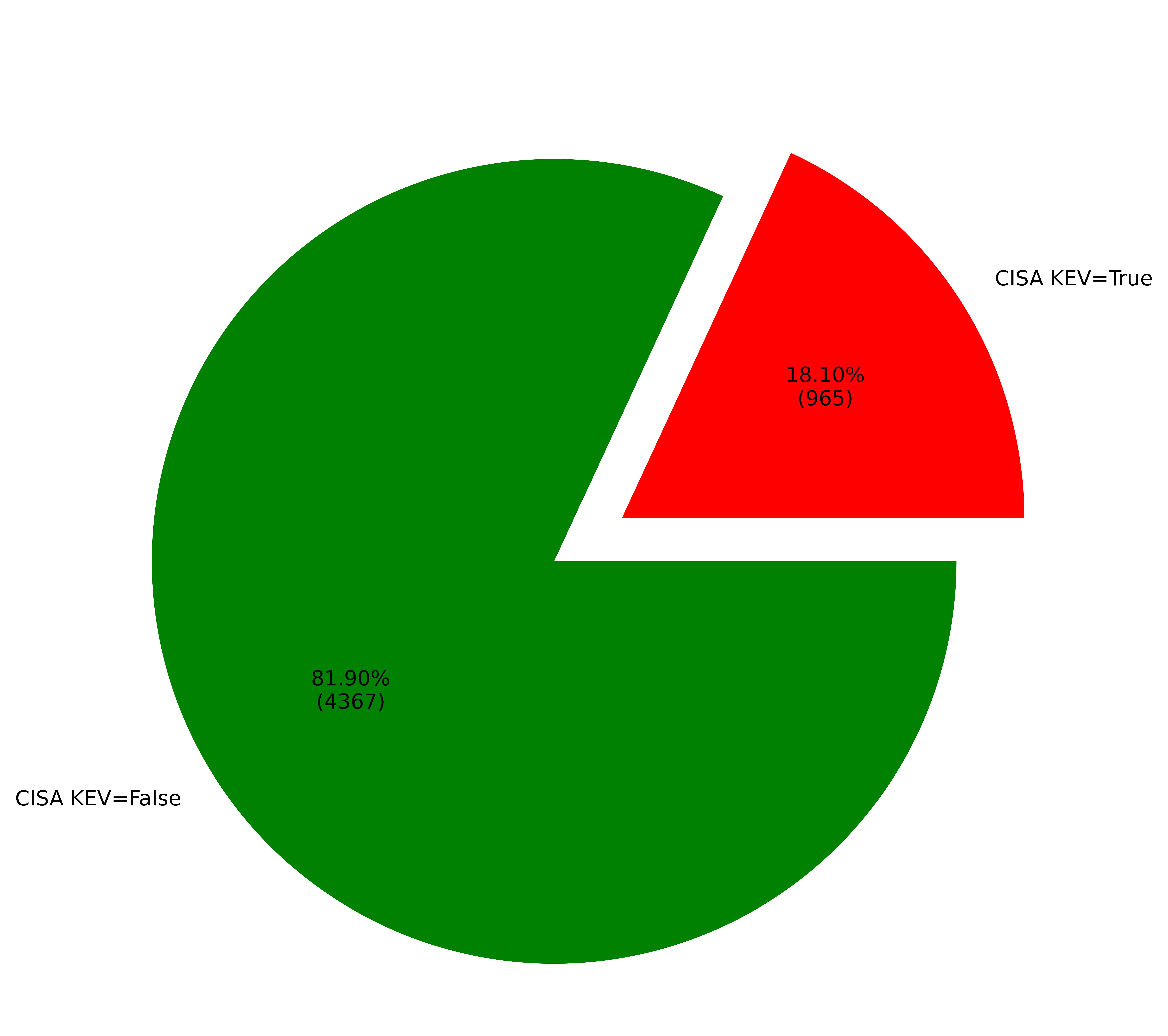 Fig. 7: CISA KEV Vulns Vs High-Risk Vulns
Fig. 7: CISA KEV Vulns Vs High-Risk Vulns
Qualys VMDR with TruRisk takes a more cautious approach when identifying high-risk vulnerabilities. Even if a vulnerability has a weaponized exploit available, it is assigned a High level of criticality. The underlying assumption being attackers could use it at any point in time. As more evidence of exploitation becomes available, the score is further increased.
The following chart illustrates the distribution of CISA's known exploited vulnerabilities over the course of years, compared to the vulnerabilities identified as high risk by Qualys TruRisk with a score of 70 or higher.
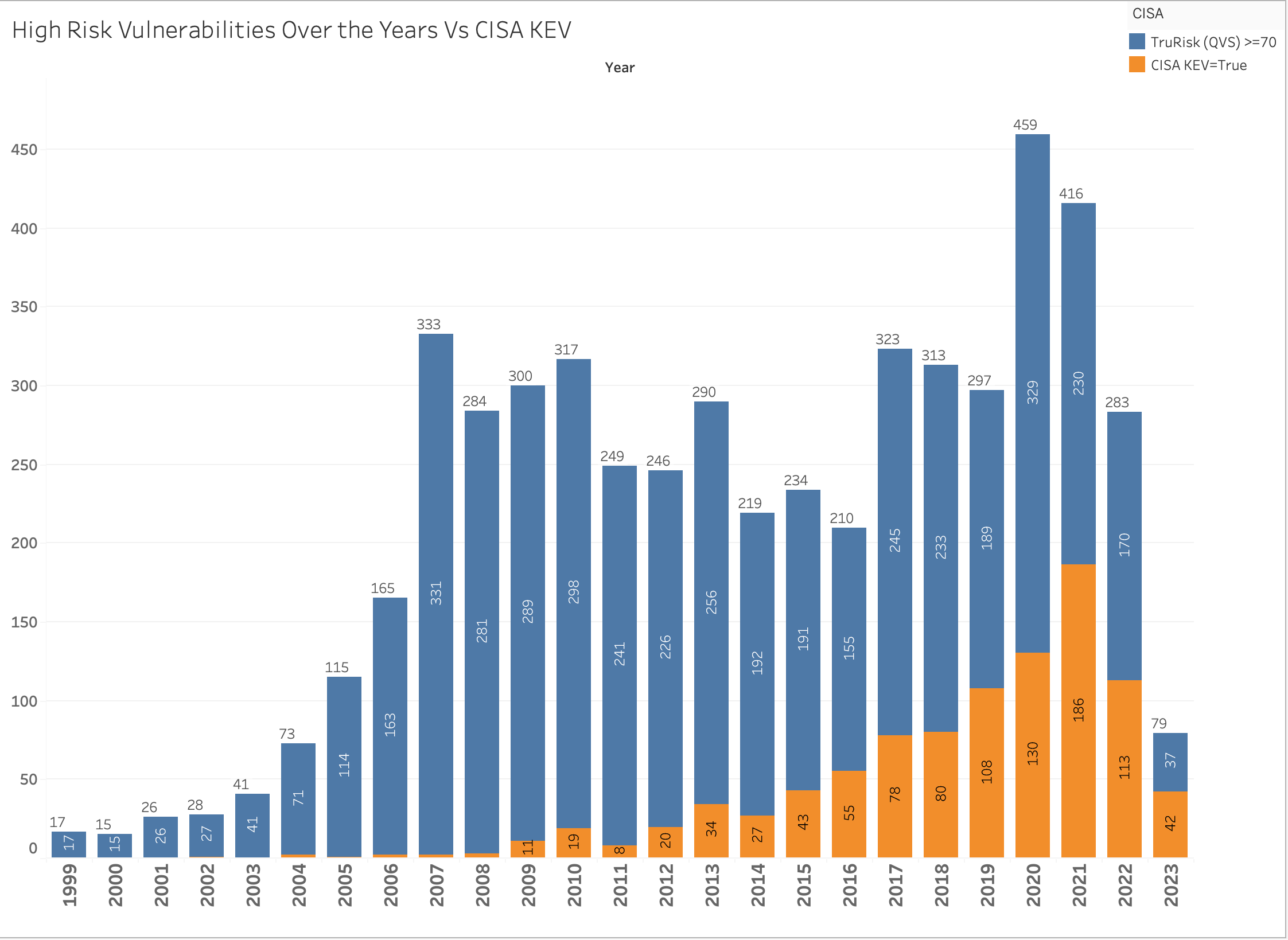 Fig. 8: CISA KEV Vulns Vs High-Risk Vulns Year Wise
Fig. 8: CISA KEV Vulns Vs High-Risk Vulns Year Wise
Exploit Prediction Scoring System (EPSS) for Vulnerabilities with Weaponized Exploits
With the Exploit Prediction Scoring System (EPSS), the defenders now have one more data insight for vulnerability prioritization. This scoring system estimated the likeliness of vulnerability being exploited, with the probability score between 0 and 1 (0-100%). Higher the score, the greater the likelihood of exploitation of the vulnerability within the next 30 days. A score that is computed daily for all the CVEs, provides the organizations with real-time insights daily.
To elaborate further, here's a quick chart of the EPSS score distribution for all the CVEs.
Approximately, 2.5% of the vulnerabilities have an EPSS score of 0.7 or higher, thus indicating a higher likelihood of exploitation.
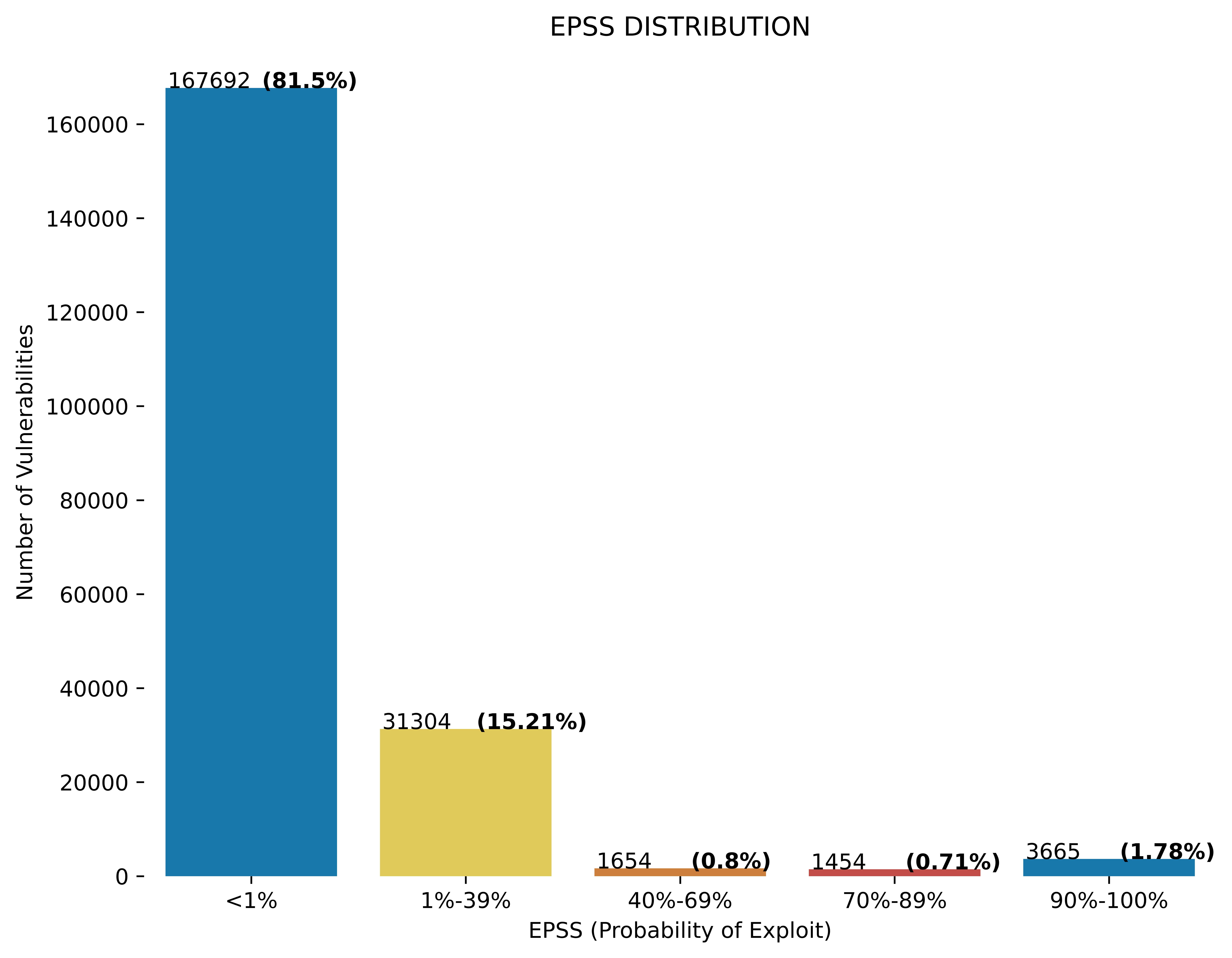 Fig. 9: EPSS Score distribution for Vulnerabilities
Fig. 9: EPSS Score distribution for Vulnerabilities
Organizations considering the implementation of risk-based vulnerability management should incorporate EPSS as one of the criteria for prioritization. However, similar to CISA KEV, it would be imprudent to rely solely on EPSS for prioritization as it may overlook high-risk vulnerabilities or those being exploited in the wild.
The chart below displays all vulnerabilities with a TruRisk score above 70 in comparison to an EPSS score exceeding 0.7.
Not all high-risk vulnerabilities have a high EPSS score, which is expected as EPSS predicts the likelihood of exploitation within the next 30 days.
Qualys VMDR, in tandem with TruRisk, utilizes EPSS scores as part of the scoring algorithm to consistently rank CVEs with a high likelihood of exploitation within the critical range.
 Fig. 10: EPSS Vulns Vs High-Risk Vulns Year Wise
Fig. 10: EPSS Vulns Vs High-Risk Vulns Year Wise
Risk-Based Prioritization with Qualys VMDR with TruRisk
Keeping track of the various vulnerability attributes and their exploit contexts can seem daunting, but, it doesn't need to be. Qualys VMDR with TruRisk greatly simplifies the prioritization criteria by translating the risk associated with vulnerabilities, assets, and asset groups into easy-to-understand TruRisk scores.
This scoring system is designed to be comprehensible for technical and non-technical teams. For instance, vulnerabilities are scored on a scale from 1-100, with 90-100 earmarked for critical vulnerabilities. This category includes vulnerabilities actively exploited in the wild, those with weaponized exploits available, and those exploited by ransomware groups or different types of malware.
High-Risk Vulnerabilities (as defined by Fig.1) are consistently ranked 70 or higher TruRisk scores.
Leverage Qualys Query Language (QQLs)
From a prioritization perspective, TruRisk scores can be further combined with additional attributes
using QQL to refine the prioritization process.
Here are a few examples:
Vulnerabilities.vulnerability.cvss2Info.accessVector:NETWORK and vulnerabilities.detectionScore>90Vulnerabilities.detectionScore>70 and vulnerabilities.vulnerability.threatIntel.ransomware:trueVulnerabilities.vulnerability.threatIntel.cisaKnownExploitedVulns:true and vulnerabilities.typeDetected:Confirmed and vulnerabilities.detectionScore>90
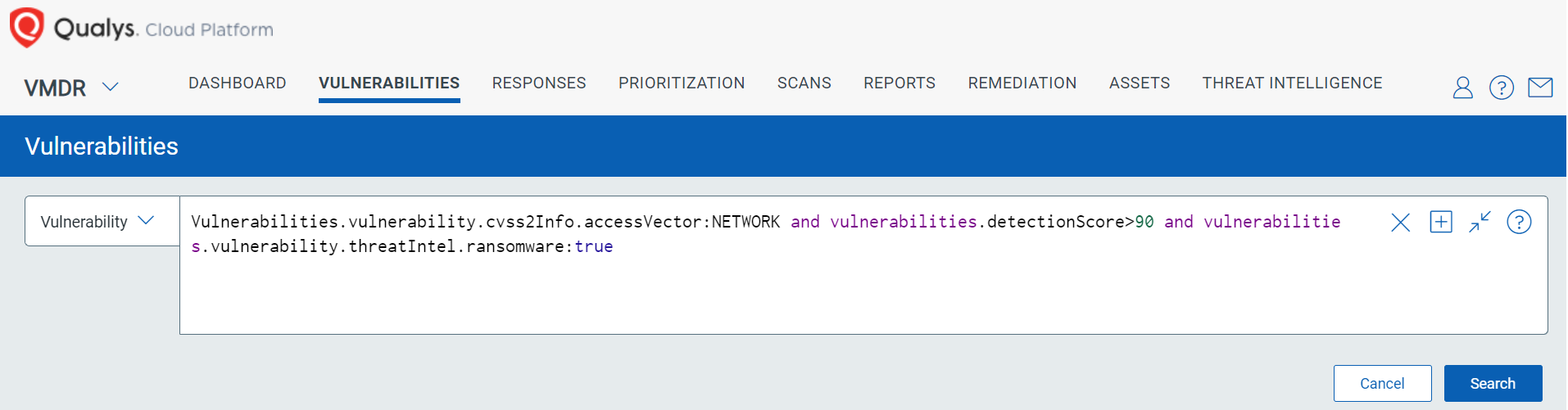 Fig. 11: Vulnerability QQL Search in VMDR
Fig. 11: Vulnerability QQL Search in VMDR
TruRisk Dashboard
The fastest method to gain insights into your TruRisk is by downloading and importing the TruRisk Dashboard into your VMDR subscription.
The TruRisk VMDR Dashboard is available - Download the Dashboard Here
This dashboard enables a quick assessment of your organization's global risk score and high-risk vulnerabilities. It allows for swift prioritization of assets and asset groups, significantly accelerating the process and focusing on the most urgent items to rapidly mitigate risks.
Key Insights & Takeaways:
- To accurately assess the genuine risk presented by open vulnerabilities within their organization, it's essential that businesses employ a comprehensive set of sensors, ranging from agent to network scanners to external scanners.
- The prioritization of vulnerabilities should be a multifaceted approach. The focus should be given to those known to be exploited in the wild (CISA KEV), those with a high likelihood of exploitation (indicated by a high EPSS score), and those with weaponized exploit code available.
- Generally, any vulnerability carrying a TruRisk score (QVS/QDS > 70) warrants immediate attention and prioritization for remediation.
- Thoroughly inventory all public-facing applications and remote services to ensure they are not vulnerable to high-risk vulnerabilities.
- To streamline the vulnerability prioritization process, make use of the Qualys TruRisk Dashboard. This tool facilitates swift and accurate prioritization, empowering you toprotect your organization effectively.
- Leverage MITRE ATT&CK Framework to better understand and counter the tactics and techniques that threat actors often employ. Utilizing this knowledge can aid in contextualizing the threats in relation to your specific environment.
In the next blog from this series, we will discuss some of the top vulnerabilities leveraged by threat actors and ransomware groups, so stay tuned.
References
- <https://blog.qualys.com/qualys-insights/2022/10/10/in-depth-look-into-data-driven-science-behind-qualys-trurisk>
- <https://blog.qualys.com/vulnerabilities-threat-research/2022/12/16/implement-risk-based-vulnerability-management-with-qualys-trurisk-part-2>
- <https://blog.qualys.com/qualys-insights/2022/08/08/a-deep-dive-into-vmdr-2-0-with-qualys-trurisk>
Additional Contributor
- Shreya Salvi, Data Scientist, Qualys
