Microsoft’s Patch Tuesday Security Updates for November
EPSS
Percentile
99.6%
THREAT LEVEL: Red.
For a detailed advisory, download the pdf file here.
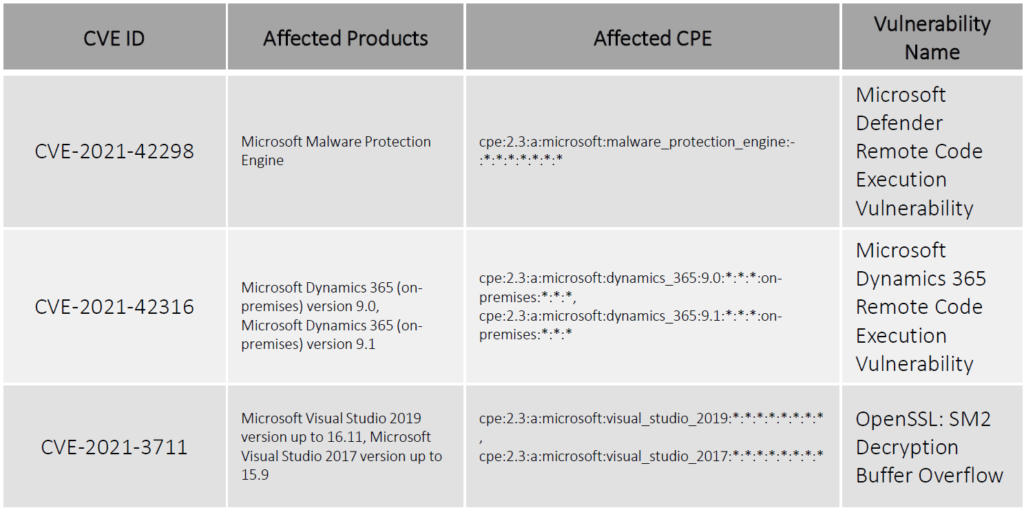
For the month of November, Microsoft has reported a total of 55 vulnerabilities, 6(CVE-2021-38666, CVE-2021-26443, CVE-2021-42279, CVE-2021-42298, CVE-2021-42316, CVE-2021-3711) of which have been rated critical. Four (CVE-2021-43208, CVE-2021-43209) of these vulnerabilities have been publicly known and two (CVE-2021-42292, CVE-2021-42321) of them have been exploited in the wild. Patches of all these vulnerabilities have been published by Microsoft. This Advisory only focuses on the important 12 vulnerabilities.
Vulnerability Details
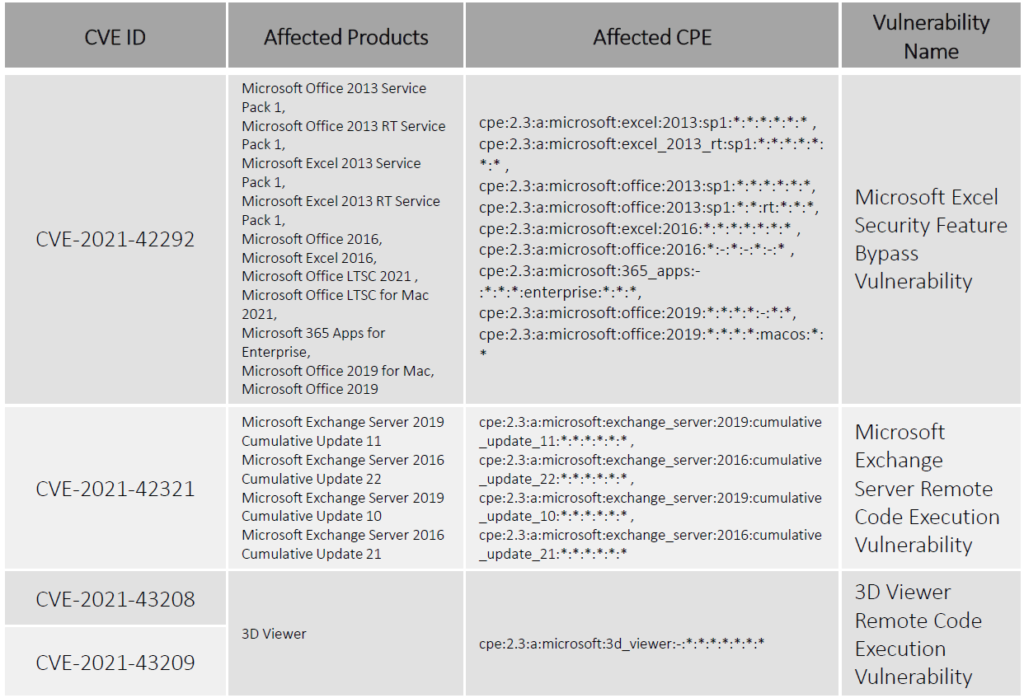
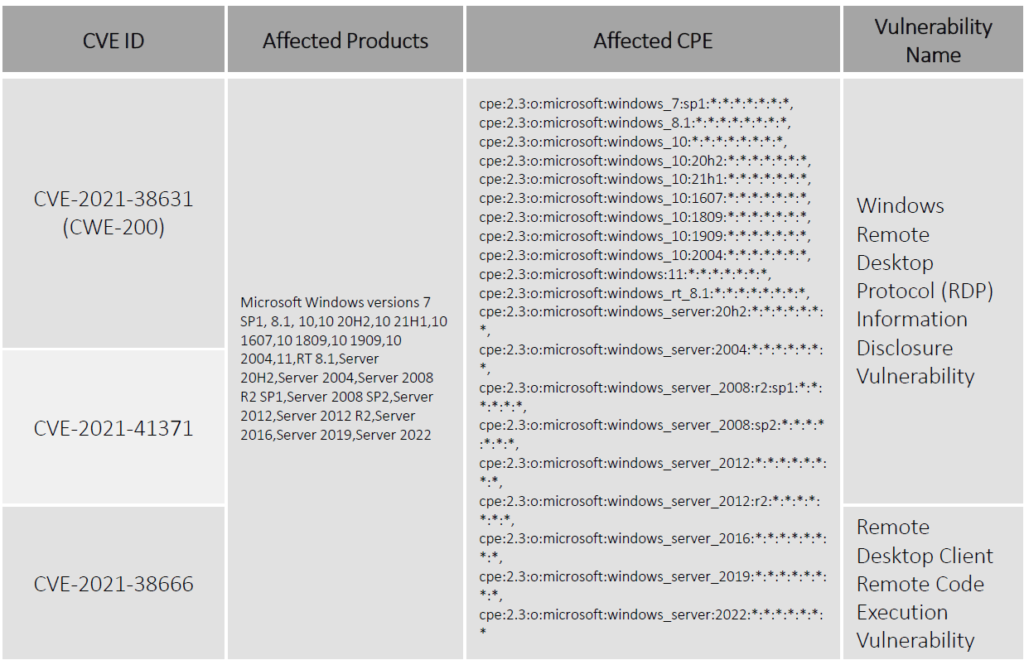
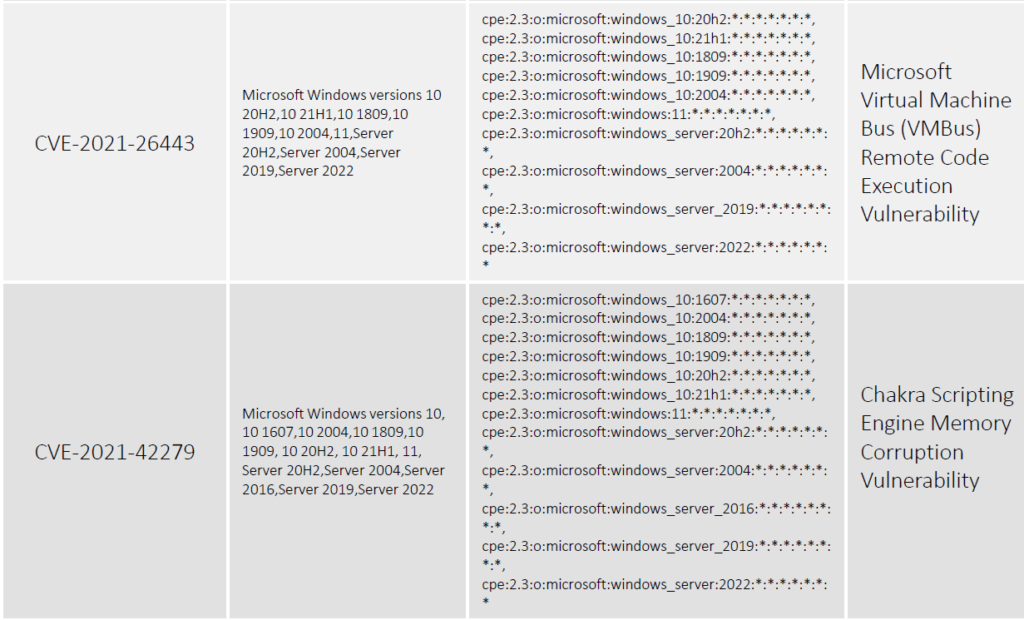
Patch Link
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-42292>
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-42321>
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-43208>
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-43209>
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-38631>
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-41371>
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-38666>
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-26443>
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-42279>
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-42298>
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-42316>
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-3711>
References
<https://threatpost.com/microsoft-nov-patch-tuesday-fixes-six-zero-days-55-bugs/176143/>
<https://www.zerodayinitiative.com/blog/2021/11/9/the-november-2021-security-update-review>