Non-hype vulnerabilities and news in Vulners monthly review

Microsoft in our weekly digests of this month. Traditionally, it was collected underestimated and unmentioned vulnerabilities with the news of the past month. There will be vulnerabilities in Kindle and Trend Micro, and news about hackers in white hat and new trends in attacking guys.
*All information was harvested by the author's hands via Vulners DB :)
- Vulnerabilities: DNS-as-a-service, Kindle, Pulse Secure, Confluensce (again), F5 BIG-IP, Azure, Apex One's (Trend Micro);
- Tools: sgCheckup (nmap ext), HTTP Request Smuggling Detection Tool, LiquidSnake, go-shellcode generator;
- News: Dropper as a Service website network, traffic abusers, ransomware starts to use PrintNightmare, White Hat guy upgraded his own brand;
- Research: not monthly, but weekly article from author.
Feedback and Vulners docs
Vulnerabilities

DNS-as-a-service
- As a result of domain registration, experts were able to listen to a dynamic stream of DNS traffic from the networks of Route 53 clients.
- The data collected included the names of employees, the names of computers and their locations, as well as sensitive information about the organization's infrastructure, including network devices available on the Web.
- This information can greatly simplify the work of intruders to penetrate the organization's network and further espionage.
The researchers found no evidence that the DNS vulnerability they discovered was previously used in actual attacks. However, any hacker who knew about these problems could collect data and go unnoticed for more than ten years, experts said. In addition, while the two major DNS providers (Google and Amazon) have already patched these vulnerabilities, others are likely still vulnerable, putting millions of devices at risk.

Amazon Kindle Vulnerable to Malicious EBooks
Check Point researchers reported that Amazon fixed critical vulnerabilities in the Kindle in April this year. The problems could be used to gain full control over the device, allowing them to steal the Amazon device token and other confidential data stored on it. For a successful attack on a Kindle, just one book with malicious code is enough.

CVE-2021-22937: Remote Code Execution Patch Bypass in Pulse Connect Secure
The vulnerability could be exploited to execute arbitrary code with root privileges.
Ivanti developers have released fixes for several vulnerabilities in Pulse Connect Secure VPN devices, including a critical issue that could be exploited to execute arbitrary code with superuser privileges.
Issue CVE-2021-22937 is actually a workaround for a patch released last October for another remote code execution vulnerability in the Pulse Connect Secure web admin interface CVE-2020-8260.
CVE-2021-22937 issue has been fixed in Pulse Connect Secure version 9.1R12. Users are advised to apply the available patch as soon as possible.

There has been an increase in the number of scans and attempts to exploit the recently disclosed vulnerability CVE-2021-26084 in Atlassian's Conflunce Data Center and Confluence Server software. This vulnerability allows you to bypass authentication and execute arbitrary code on the system.
We wrote about this critical vulnerability this week. The specified vulnerability is one of the most dangerous this month.

Critical vulnerability has been identified in F5 BIG-IP devices
13 dangerous vulnerabilities have been fixed in F5 BIG-IP network devices, one of which CVE-2021-23031 may become critical under certain conditions. The issue affects the BIG-IP Advanced Web Application Firewall (WAF) and Application Security Manager (ASM) modules.
F5 Vulnerability Notice CVE-2021-23031 does not detail why there are two severity levels. According to experts, there are a limited number of clients that are affected by the critical issue unless they update to the latest version or apply mitigation measures (restrict access to the configuration utility to only fully trusted users).
The rest of the vulnerabilities were rated medium according to the CVSS scale. Issues include vulnerabilities in authenticated remote command execution, cross-site scripting (XSS), request forgery, and DoS.

The vulnerability was discovered by the research group of the cloud security company Wiz. Experts named the vulnerability ChaosDB and reported it to Microsoft on August 12, 2021. At the same time, according to the researchers, the vulnerability was hidden in the code "for at least several months, and possibly years." Microsoft paid Wiz a $ 40,000 fee for this bug.
The bug allowed attackers to exploit a chain of bugs associated with the work of the open source Jupyter Notebook functionality, which is enabled by default and is designed to help clients visualize data.
According to Microsoft - there is no evidence that attackers discovered and exploited the Chaos DB vulnerability before the Wiz experts.

Trend Micro warns of the introduction of Zero-Day in Apex One's network monitoring and threat intelligence product. Both on-premises and cloud versions of Apex One are vulnerable. CVE-2021-36741 and CVE-2021-36742 (loading arbitrary files and local privilege escalation) have already been used in a chain of exploits to upload malware to the Apex One platform in order to escalate privileges and further seize control over the system.
It is worth remembering the incident when attackers steal vulnerabilities in the Trend Micro OfficeScan product from the electronics manufacturer Mitsubishi Electric and stole personal and corporate information.
Tools
sgCheckup: Generate nmap output based on scanning your AWS Security Groups for unexpected open ports
HTTP Request Smuggling Detection Tool
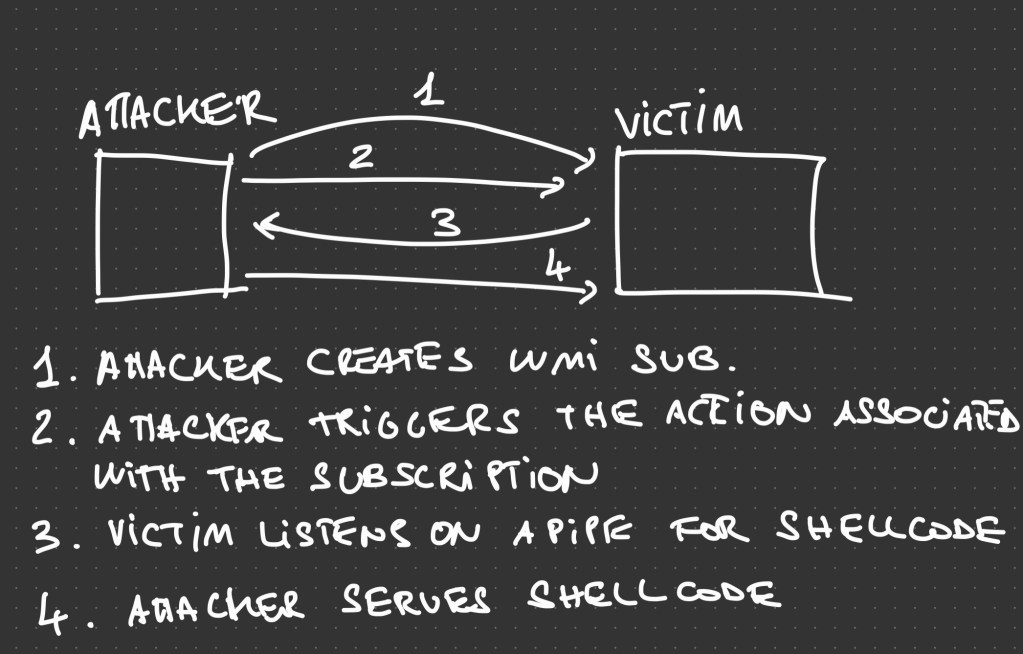
LiquidSnake is a tool that allows operators to perform fileless lateral movement using WMI Event Subscriptions and GadgetToJScript

go-shellcode is a repository of Windows Shellcode runners and supporting utilities. The applications load and execute Shellcode using various API calls or techniques.
News

Sophos has published a report on the Dropper as a Service website network
Experts found several networks of sites with pirated software, the owners of which offer malware distribution services to malware operators. To attract victims, these sites use search engine optimization for queries related to pirated software.

Researchers have noted a significant increase in attacks when an attacker illegally installs software designed to allow users to “distribute” part of their Internet channel traffic for monetary rewards. With the help of such attacks, fraudsters seek to obtain hidden passive income from the resources of the victim's system. Among the software seen in such attacks are Honeygain, PacketStream, Nanowire.

Ransomware groups have adopted exploits for PrintNightmare
Crowdstrike noticed that ransomware operators have added exploits to their arsenal for PrintNightmare vulnerabilities and are using them to deploy Magniber ransomware payloads.
Magniber has been active since October 2017, originally distributed through malicious ads using the Magnitude Exploit Kit (EK) as the successor to Cerber ransomware, now delivered via Magnitude EK to devices running Internet Explorer running unpatched CVE-2020-0968. The grouping is focused on South Korea, China, Taiwan, Hong Kong, Singapore, Malaysia and others. And in the last 30 days it has become especially active, now it is clear why.

Poly Network White Hat
This month ended the amazed Polu Network incident with the world-famous Mr. White Hat, who first gracefully withdrew crypto assets worth more than half a billion dollars, and then returned them no less spectacularly.
It is worth paying tribute to the Poly Network company, which listened to the alliance of BinomialPool developers and, instead of criminal, offered the hacker a reward of 500 thousand dollars.

SFA is officially recognized by the US Cyber and Infrastructure Security Agency (CISA) as an ineffective cybersecurity method and is included in the relevant registry along with such risky practices as: the use of software with an expired (or no support) and default credentials.
The above measures, according to the standards of the regulator, can no longer be applied at critical infrastructure facilities (NCF) that ensure national security and economic stability.
In the future, the list of BAD PRACTICES may also include: the use of weak cryptography, the intersection of IT and OT networks, weak network segmentation, lack of allocation of rights, transmission of unencrypted traffic, reuse of compromised systems without proper response to incidents.
Research
Fileless Malware: https://dmcxblue.net/2021/08/30/fileless-malware
Writting Better Pentest Reports w/ Examples! https://lockboxx.blogspot.com/2021/08/cptc-better-pentest-reports-w-examples.html
Blinding EDR On Windows: https://synzack.github.io/Blinding-EDR-On-Windows
Backdoor Office 365 and Active Directory - Golden SAML: https://www.inversecos.com/2021/09/backdooring-office-365-and-active.html
15-Year-Old Malware Proxy Network VIP72 Goes Dark: https://krebsonsecurity.com/2021/09/15-year-old-malware-proxy-network-vip72-goes-dark
Backdoor Office 365 and Active Directory - Golden SAML: https://www.inversecos.com/2021/09/backdooring-office-365-and-active.html
The Art of the Device Code Phish - walkthrough the Azure Device Code Phishing attack, from creating a malicious Azure phishing infrastructure, to achieving Azure Account Take-Over (ATO). https://0xboku.com/2021/07/12/ArtOfDeviceCodePhish.html
Cobalt Strike PowerShell Payload Analysis: https://michaelkoczwara.medium.com/cobalt-strike-powershell-payload-analysis-eecf74b3c2f7
Feedback and Vulners docs
oczwara.medium.com/cobalt-strike-powershell-payload-analysis-eecf74b3c2f7](https://michaelkoczwara.medium.com/cobalt-strike-powershell-payload-analysis-eecf74b3c2f7)
Feedback and Vulners docs
