Weekly/daily zero-days and ransomware news

This week Apple and Google fixed zero-day vulnerabilities. More information about APTs and ransomware. All this proves once again that vulnerability management process in information security is just as important as the others.
- Vulnerabilities: Few zero-days from Chrome and Apple, cool Instagram bug and do you use paint?
- Tools: Event killer, aim to shellcoders, Rustcat (like netcat) and PPLdump;
- News: Ransomware and no more ransomware
- Research: Mostly awesome for defenders or useful how to detect sth.
Vulnerabilities

Chrome update for Windows, Mac and Linux, which fixed the seventh 0-day vulnerability in 2021
CVE-2021-30544 - UAF (User-After-Free, incorrect dynamic memory handling when released) vulnerability in JavaScript WebGL API, used for rendering interactive 2D and 3D graphics.
The vulnerability leads to remote code execution (RCE) on the attacked system. Google does not disclose any technical details, but they do report that they are aware of CVE-2021-30544 being used in the wild.

Vulnerability was fixed in the Instagram app that allowed third parties to view the posts and stories of users with a closed profile. Facebook paid $30,000 to cybersecurity specialist Mayur Farhad to find the problem.

Zero Day Initiative (ZDI) identified a vulnerability in Microsoft Paint 3D modeling application. Attackers could use the flaw to execute arbitrary code.
The vulnerability was identified as CVE-2021-31946. Its exploitation involves the victim visiting a malicious web page. The bug can also be exploited using a malicious file.

Apple released iOS 12.5.4 update fixing two zero-day vulnerabilities in mobile OS.
The update fixes three vulnerabilities in iOS - a memory corruption vulnerability in the ASN.1 decoder CVE-2021-30737 and two vulnerabilities in the WebKit browser engine CVE-2021-30761 and CVE-2021-30762. The first is a memory corruption vulnerability that can be exploited to remotely execute code with malicious web content.
CVE-2021-30762 is a post-release exploit vulnerability that also allows remote code execution using malicious web content.
The problems affect iPhone 5s, iPhone 6, iPhone 6 Plus, iPad Air, iPad mini 2, iPad mini 3, iPod touch (6th). All owners of iOS devices are advised to update as soon as possible.
Tools

Phant0m | Windows Event Log Killer

Redpill project aims to assist reverse tcp shells in post-exploration tasks. Often in redteam engagements we
need to use unconventional ways to access target system, such as reverse tcp shells (not metasploit ) in order
to bypass the defenses implemented by the system administrator.
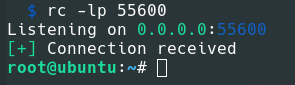
Rustcat is a port listener that can be used for different purposes.
It is basically like netcat but with fewer options:
- Serves it purpose of listening to ports;
- Has command history;
- It is easy to use;
- Supports udp;
- Uses colors.
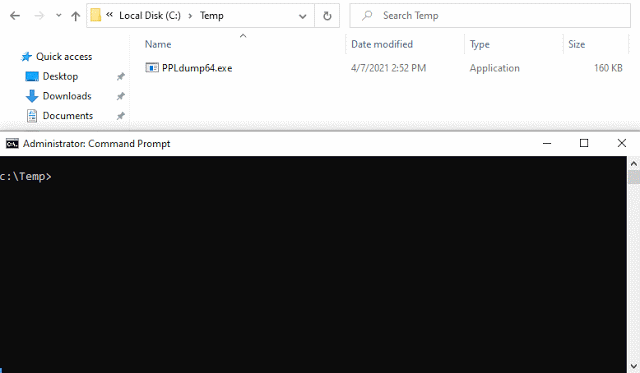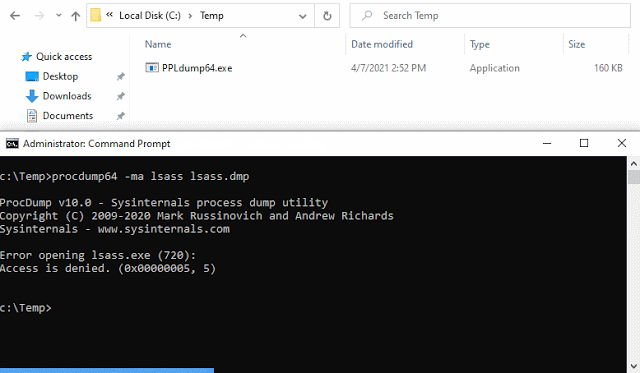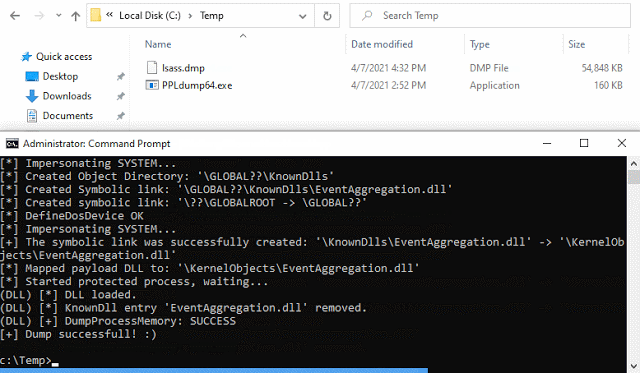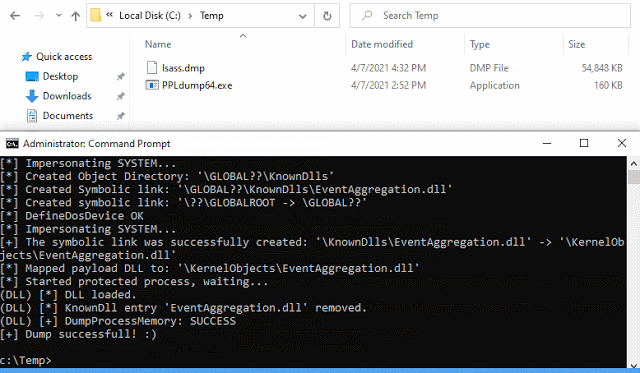
PPLdump is a tool which implements a userland exploit for dumping the memory of any PPL as an administrator.
News

Journalists received an anonymous message with a link to an archive containing a file with 2,934 decryption keys for the Avaddon ransomware. Emsisoft specialists used the data to develop a decryption tool. At the moment all Avaddon sites on the darknet are down. No one knows yet for what reason the group decided to go out of business. According to one version, it was caused by the fact that after a series of high-profile attacks law enforcement agencies began to take active measures to combat ransomware.
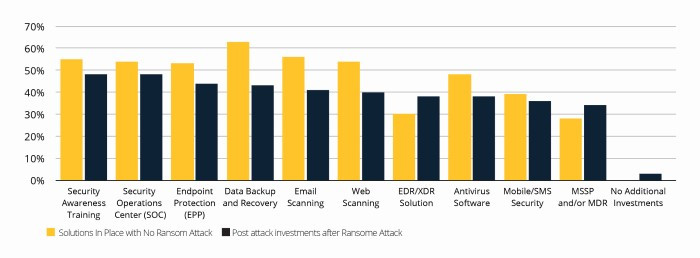
According to the Cybereason report, about 80 percent of the organizations that paid ransom to ransomware owners were attacked again, with almost half of them suspecting the same ransomware. If a company has fallen victim to ransomware, it means there are holes in its information security system, and likely many more than one.

Sol Oriens was attacked by ransomware
APT REvil was able to gain access to the systems of the organization Sol Oriens, which is a consultant to the Pentagon on nuclear safety issues. According to a representative of Sol Oriens, the attackers managed to steal payment documents for contracts, project descriptions, payroll. At the same time, there is no evidence that the attackers managed to gain access to classified information.
Research
Click your shortcut and… you got pwnd: https://redteamer.tips/click-your-shortcut-and-you-got-pwned
Bypassing Image Load Kernel Callbacks: https://www.mdsec.co.uk/2021/06/bypassing-image-load-kernel-callbacks
Certified Pre-Owned: https://posts.specterops.io/certified-pre-owned-d95910965cd2
[THE DFIR REPORT] From Word to Lateral Movement in 1 Hour
Feedback
pecterops.io/certified-pre-owned-d95910965cd2)
[THE DFIR REPORT] From Word to Lateral Movement in 1 Hour
