Vulners weekly digest #6

This review is more about exploiting vulnerabilities in attacks on various areas. We also gave examples of why security updates should not be ignored.
The most interesting vulnerabilities
If you use any tools / systems that are mentioned in this section, it is recommended to install security updates.
Gitlab multiple vulnerabilities

Many companies use such enterprise tools like Jira, Gitlab, Bitbucket and etc. Therefore, these tools are often a sweet target for attackers.This week a security patch was released to fix 13 vulnerabilities in Gitlab:
- Path Traversal in NuGet Package Registry CVE-2020-12448. It allows to use a malicious NuGet package to read any *.nupkg file on the system.
- OAuth Application Client Secrets Revealed CVE-2020-10187. It allows for any user to retrieve OAuth application client secrets after authorizing
- Update Nokogiri dependency. Security fix for CVE-2020-7595
- Update git. Security fix for CVE-2020-11008
The official description of remaining vulnerabilities: https://about.gitlab.com/releases/2020/04/30/security-release-12-10-2-released/
These issues have been fixed in the latest release, and for many of them, the CVEs is pending status.
For one of the critical vulnerabilities software developer William Bowling (@vakkz) resieved 1k$ (Path Traversal) + 19k$ (RCE) = 20k$ with detailed info in his report.
Great work!
Docker

New metasploit module based on CVE-2019-15752 with local privilege escalation via Docker-Credential-Wincred.exe. This exploit leverages a vulnerability in docker desktop community editions prior to 2.1.0.1. You can write a payload to a lower-privileged session to be executed automatically by the docker user at login.
Salt Bugs story

Timeline:
- In mid-March this year, F-secure identified 2 vulnerabilities - CVE-2020-11651 (authentication bypass) and CVE-2020-11652 (directory-traversal) in the open-source Salt management framework. Vulnerabilities allow full remote code execution as root on servers in data centers and cloud environments
- On April 29, Saltstack released a version of Salt V. 3000. 2, in which the vulnerabilities were fixed.
- April 30, F-secure published write-up about vulnerabilities with the following note: “We expect that any competent hacker will be able to create 100 percent reliable exploits for these issues in under 24 hours.” It looks like a challenge for any security enthusiast, isn't it? :)
- A day after this publication, attacks began on the servers of the mobile operating system LineageOS. The developers said that the attackers used vulnerabilities in Salt.
- A few days later, a popular blogging platform was also attacked, using vulnerabilities in Salt. The platform with 2 million installations, including organizations such as Nasa, Mozilla and DuckDuckGo.
F-Secure formally survived the time after the publication of the security updates, but it was clearly not enough for the vendors to update their systems and products.
p.s. the vulnerability is really easy to exploit ;)
https://vulners.com/threatpost/THREATPOST:5CB5F29FA05D52DEEC4D54AA46EB9235
https://vulners.com/thn/THN:8E401822CBD35E8E7CCE9E5DD922A70E
Tools
Sysmon update v11.0 including features like file delete monitoring, reducing Reverse DNS lookup noise and more: https://docs.microsoft.com/en-us/sysinternals
Print-My-Shell
Shell code generator for the tiny ones. A useful tool to quickly generate shell code during CTF or other testing activity.

ROADtools
ROADtools is a framework to interact with Azure AD. It currently consists of a library (roadlib) and the ROADrecon Azure AD exploration tool. Meet one of the first versions of the BloodHound for AzureAD!
News
Ruthless ransomware, APT groups and Teams instead of ZOOM
Ransomware groups continue to target critical services
Microsoft Detection and Response Team (DART) has published an interesting post about ransomware and tips on how to deal with them. So far, attacks have affected aid organizations, medical billing companies, manufacturing, transportation, and government agencies. Ransomware attacks, however, are not limited to critical services, so organizations should be vigilant for signs of compromise.
To get access to target networks, recent extortion campaigns have used systems with Internet access with the following weaknesses:
- Remote Desktop Protocol (RDP) or Virtual Desktop endpoints without multi-factor authentication
- Old platforms like Windows Server 2003 or Windows Server 200 without actually security updates
- Misconfigured web servers, including IIS, electronic health record (EHR) software, backup servers, or systems management servers
- Citrix Application Delivery Controller (ADC) with CVE-2019-19781
- Pulse Secure VPN systems affected by CVE-2019-11510
All ransomwares deployed in the same way and used mostly the same attack techniques. Ultimately, the specific ransom payload at the end of each attack chain was almost exclusively a stylistic choice made by the attackers.
List of active ransomware:
- RobbinHood
- Vatet loader
- NetWalker
- PonyFinal
- Maze
- REvil (aka Sodinokibi)
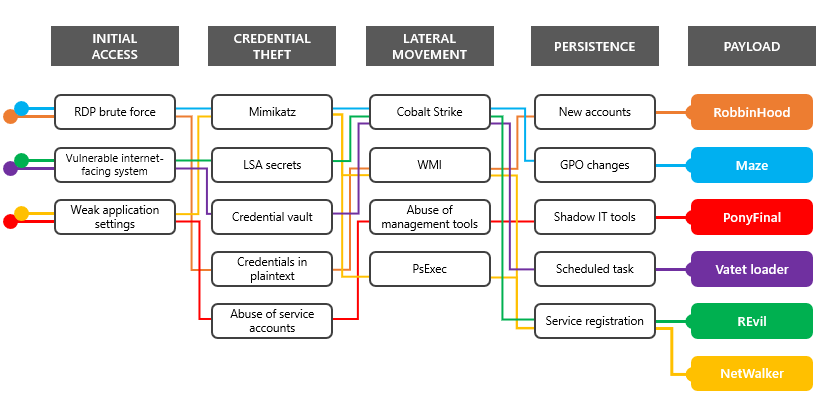
A motley crew of ransomware payloads
Few of these groups have gained fame for selling data, almost all of them have been seen viewing and filtering data during these attacks, even if they have not yet been advertised or sold. Currently, situations more often occur when, after the publication of vulnerabilities for a system/tool, a very short period of time elapses before an exploit/PoC appears.
Full report with technical datails:
https://vulners.com/mssecure/MSSECURE:E3C8B97294453D962741782EC959E79C
Maze Ransomware - this week's winner
Operators of the Maze ransomware were able to become famous a little more than others and compromised the network of the state Bank of Costa Rica (Banco BCR), as a result of which, among other things, they stole the data of 11 million Bank cards.
On their press release, hackers claim that they first gained access to the Bank's network back in August 2019, but did not encrypt the data, because "the probable damage could have been too much for the bank"
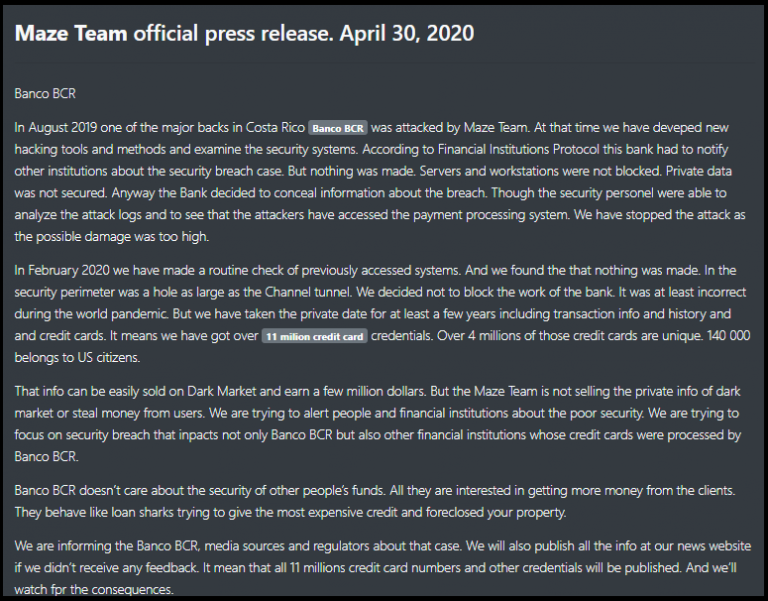
Press release from Maze operators
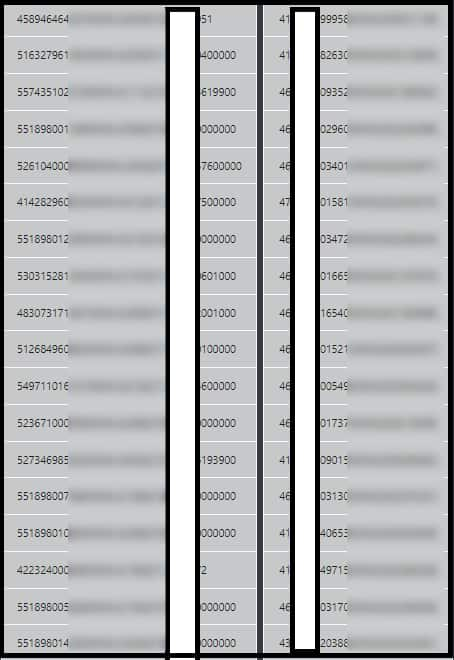
As proof of theft, Maze published the numbers of 240 credit cards without the last 4 digits, as well as their expiration dates and CVC codes:
Recently, the American IT giant Cognizant, a company from NASDAQ-100, confirmed that it was hit by the Maze ransomware . Considering 30 billion dollars of capitalization of the company the sum of the repayment for data should make not one million, and even not one tenth of millions dollars.
PerSwaysion attacks
Group IB has released a report on the investigation of a series of phishing attacks under the symbol PerSwaysion.
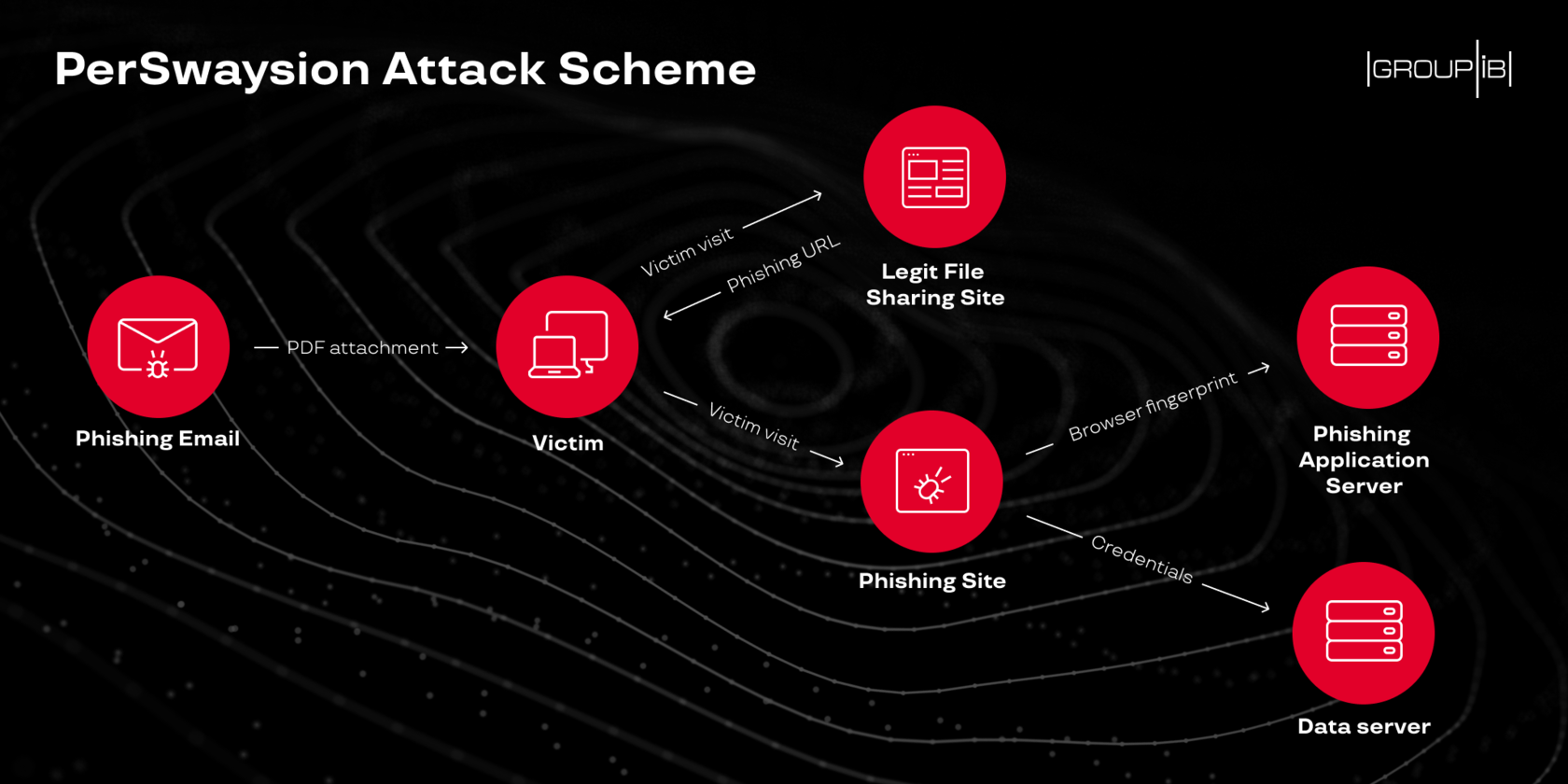
PerSwaysion operation also lured victims with a non-malicious PDF, and later Microsoft file sharing services, including Sway, are used-hence the name of the phishing campaign. The hackers target high-level employees in the financial, legal, and real estate industries. Geographical preferences - USA, Canada, Singapore, Germany, UK, Netherlands, Hong Kong.
According to researchers, behind a series of attacks there are several hacker groups using the same infrastructure. Most of the PerSwaysion operations were orchestrated by scammers from Nigeria and South Africa who used a Vue.js JavaScript framework-based phishing kit, evidently, developed by and rented from Vietnamese speaking hackers.

Group-IB has also set-up an online web-page where anyone can check if their email address was compromised as part of PerSwaysion attacks—however, you should only use it and enter your email if you’re highly expecting to be attacked.
Microsoft Teams

Recently there has been a lot of news about holes in the ZOOM video conferencing service. But, as it turns out, their competitors are also not far behind.
The researchers found that in the process of delivering images, Microsoft Teams uses two authentication tokens "authtoken" and "skypetoken", the second is generated using the first and with it you can intercept the Microsoft Teams account. The "authtoken" token can be obtained by attacking the "teams .microsoft .com" subdomains. And two such CyberArk subdomains were found - this is "aadsync-test .teams .microsoft .com" and "data-dev .teams .microsoft .com".
According to CyberArk, they transferred all the data to Microsoft and they eliminated the vulnerability, including the incorrect configuration of the domain "teams .microsoft .com".
