Vulners weekly digest #5

+1 integration for Vulners
Review fresh vulnerabilities without Microsoft
Tools
News without COVID-19 and ZOOM

This week the Vullners integrated with a new great project: https://attackerkb.com
It is already available: https://vulners.com/search?query=type:attackerkb
Vulnerabilities, exploits or PoCs
Is it possible to make a digest without vulnerabilities in microsoft products? Let's try to do it!
Multiple vulnerabilities in the IQrouter

Information security researchers often like to deal with noname network devices and find all sorts of vulnerabilities in them. This week's target was the IQrouter and its firmware version 3.3.1:
The researcher also made an example of exploiting all these vulnerabilities:
RCE PoC for Sysaid v20.1.11
Sysaid is a free Help Desk software for IT support. CVE-2020-10569 allows unauthenticated access to upload any files, which can be used to execute commands on the system by chaining it with a GhostCat attack. Attackers could read app configuration files and steal passwords or API tokens, or they could write files to a server, such as backdoors or web shells:
Oracle Solaris
CVE-2020-2944 in this UNIX OS for versions 10 and 11. Vulnerability allows low privileged attacker with logon to the infrastructure where Oracle Solaris executes to compromise it. Oracle has released a fix for all affected and supported versions of Solaris in the Critical Patch Update of April.
Multiple vulnerabilities in the QRadar Community Edition 7.3.1.6
QRadar one of the most famous SIEM system. Community edition is limited to 50 events per second and 5,000 network flows a minute, supports apps, but is based on a smaller footprint for non-enterprise use. Too many vulnerabilities were found in one of the latest releases of this version:
At the time of publication of this digest, the latest version of the QRadar is V7. 3. 3
Tools
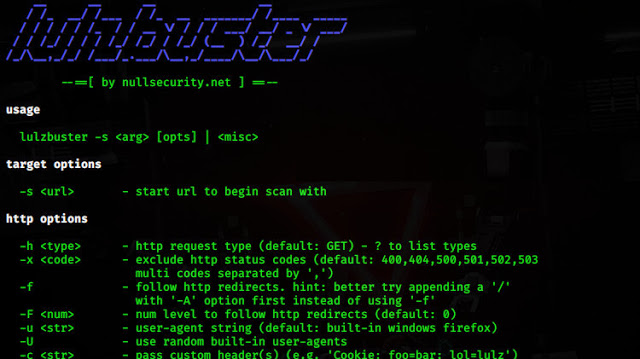
Lulzbuster
Lulzbuster is a very fast and smart web directory and file enumeration tool written in C.
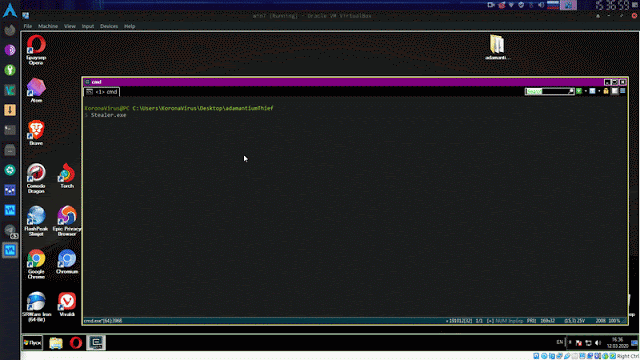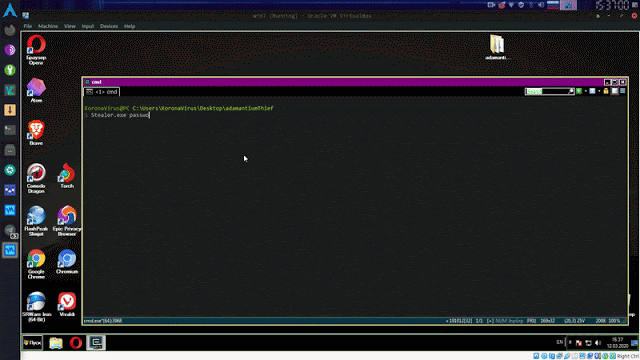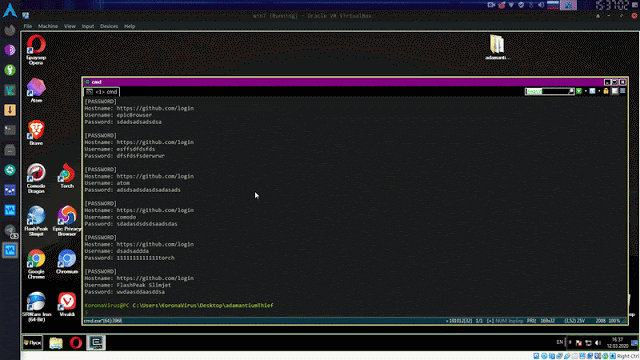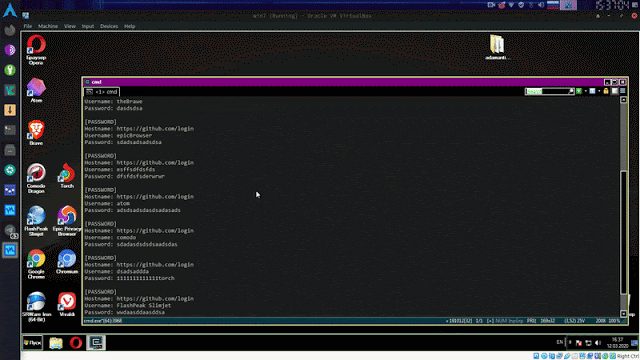
Adamantium-Thief
Get chromium browsers: passwords, credit cards, history, cookies, bookmarks.
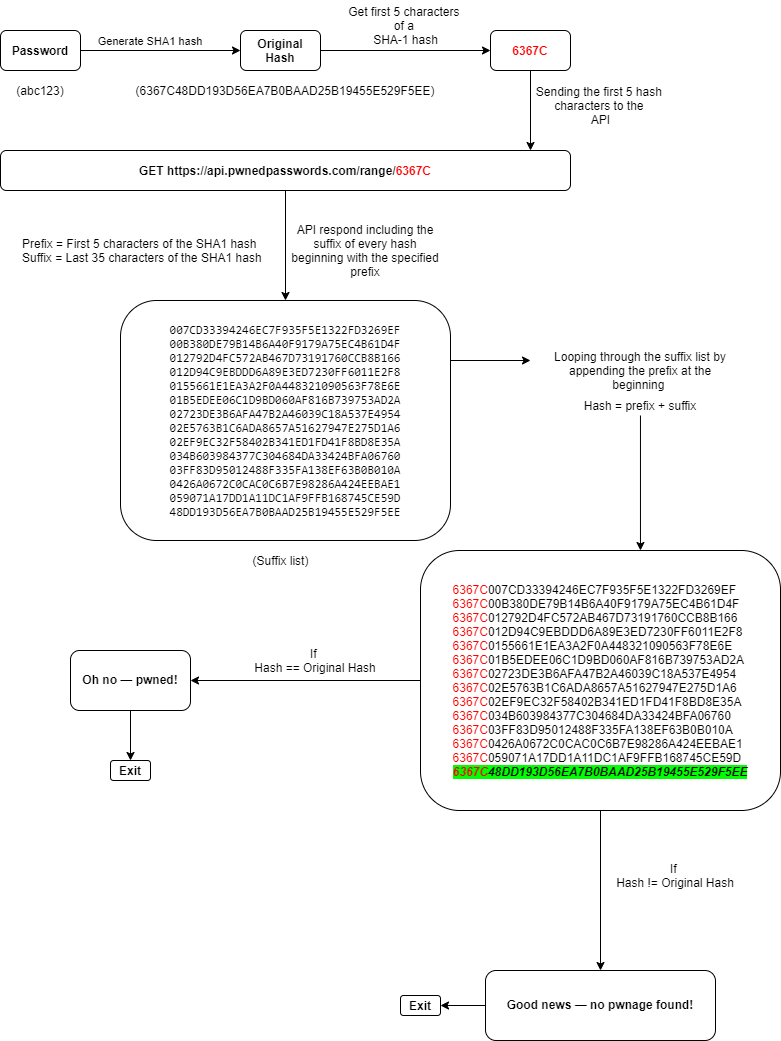
Pwned
Pwned is a simple command-line python script to check if you have a password that has been compromised in a data breach. The full scheme of the script:
News
MITRE releasing the results of evaluations
Apple zero-days in Mail app
The Incident Response Challenge 2020 - $$$
MITRE ATT&CK Evaluations

The main event of the week for many information security vendors - results of MITRE evaluation methodology based on APT29: https://ela.st/mitre-eval-rd2
In late 2019, the ATT&CK Evaluations team evaluated 21 endpoint security vendors with their endpoint detection and response (EDR) products, using its now industry-standard open methodology, the ATT&CK framework.
For complete evaluation results, you can review the data published on the MITRE website.
VMware Carbon Black results: https://vulners.com/carbonblack/CARBONBLACK:8DEE9836AF3A9C5A0954C0941127CFC9
Microsoft ATP results: https://vulners.com/mssecure/MSSECURE:7C2EBC78AA9ED84F61D237B3E3AE3C1D
Apple

On April 22, ZecOps announced the use of two 0-day vulnerabilities in the Mail application in the wild, allowing full control of the correspondence of the attacked user on the entire line of iPad and iPhone devices.
Secops reported that it recorded the use of exploits in relation to:
- employees of us companies from the Fortune 500 list;
- Director of a carrier company from Japan;
- German VIP;
- MSSP (Managed Security Service Provider) from Saudi Arabia and Israel;
- European journalist;
- as well as suspicion of hacking the head of one of the Swiss companies.
To this Apple responds as expected "We have studied the zecops report and concluded that the identified errors do not pose a threat to users. We will close them in the next updates."
ZecOps also promises to post more technical information about errors and the facts of their use after the patch is released.
https://vulners.com/thn/THN:7749C9AD2429E9716C12DEB1307ABB29
https://vulners.com/threatpost/THREATPOST:D091476FC2E5A0AFECA0813539BECDF9
The Incident Response Challenge 2020

Cybersecurity firm Cynet 21-st April announced the launch of a first of its kind challenge to enable Incident Response professionals to test their skills with 25 forensic challenges that were built by top researchers and analysts.
The challenge is available on https://incident-response-challenge.com/ and is open to anyone willing to test his or her investigation skills, between April 21st and May 15th.
Are you a hands-on forensic researcher, SOC analyst, or malware analyzer? Go to https://incident-response-challenge.com/, get your hands dirty, and beat your peers to get the first prize!
