Vulners weekly digest #3

Weekly overview of new vulnerabilities, exploits, tools and other news from the world of information security.

Vulners has officially integrated with EXPLOITPACK on this week. Now customers can get even more information centrally about the required vulnerabilities
All interest in the difference :)
Exploits
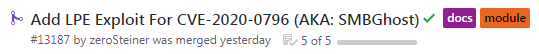
Congratulations, this week there was an exloit for CVE-2020-0796. We wrote about this vulnerability in our previous digest:
- 31 March Local Privilege Escalation exploit released;
- 3 April this module merged in metasploit framework.
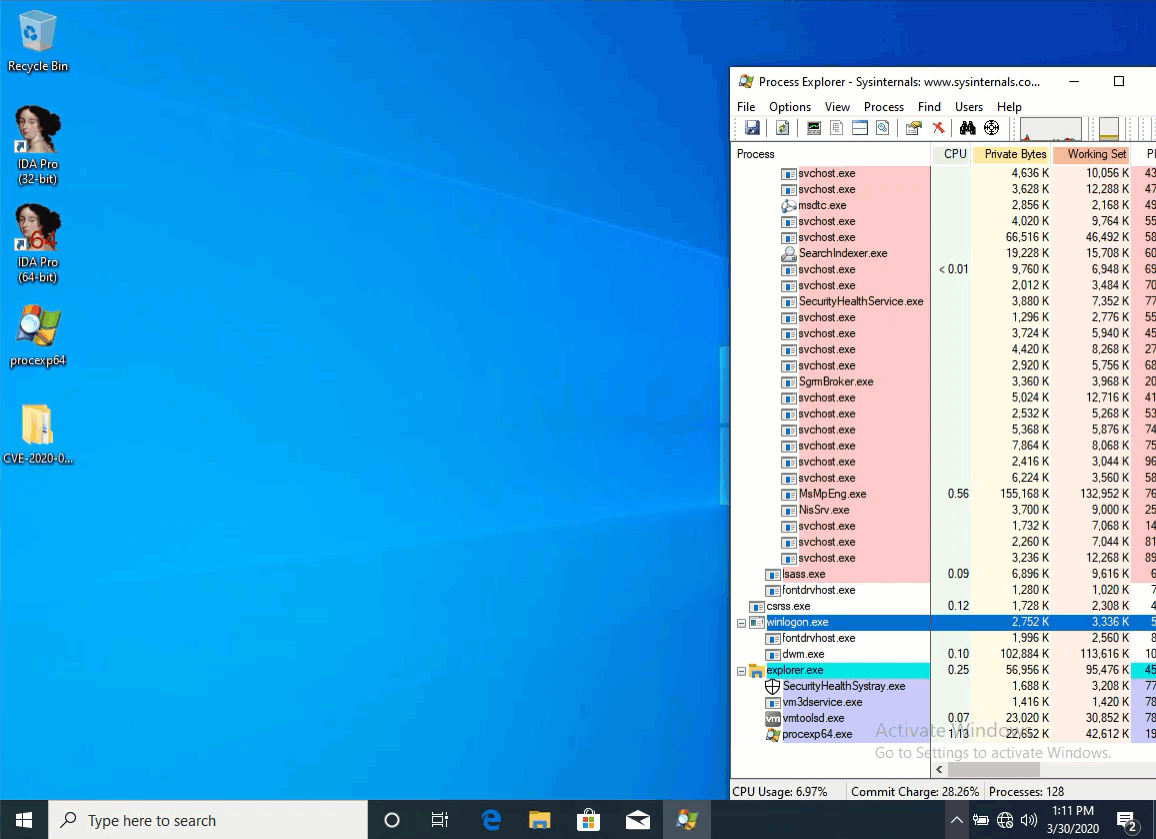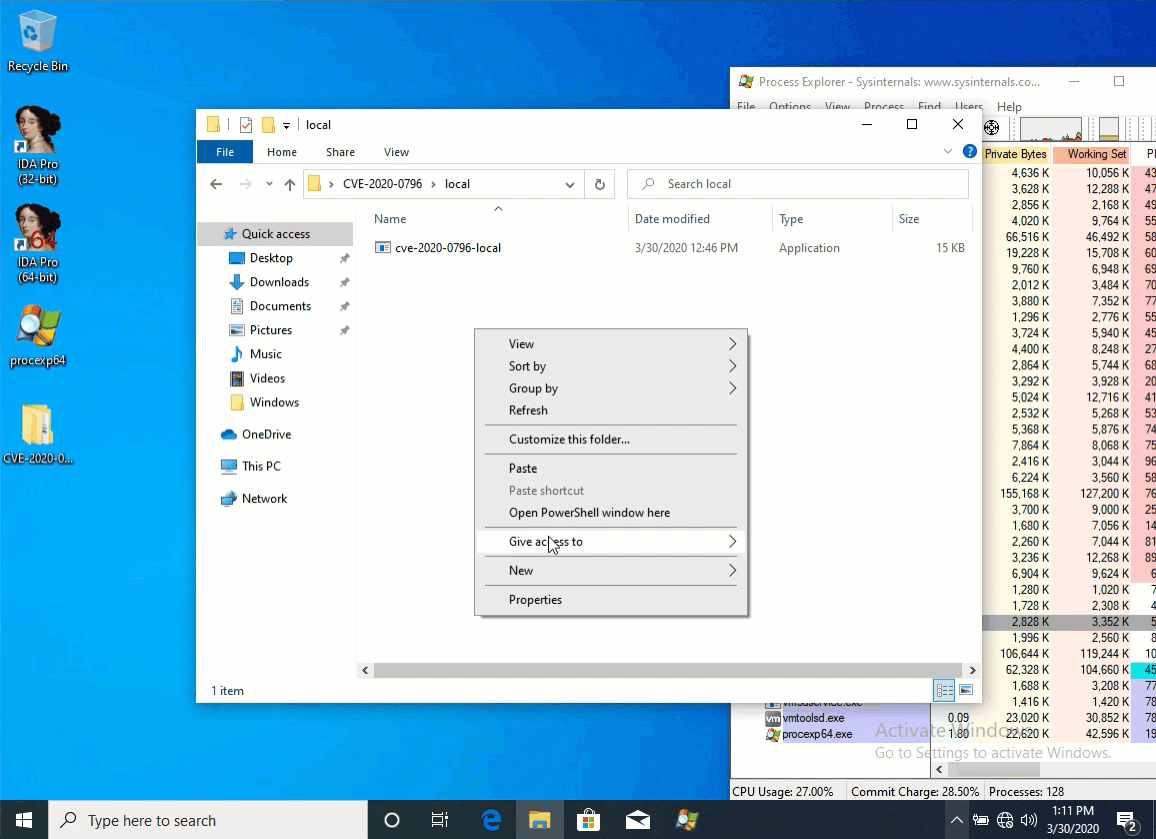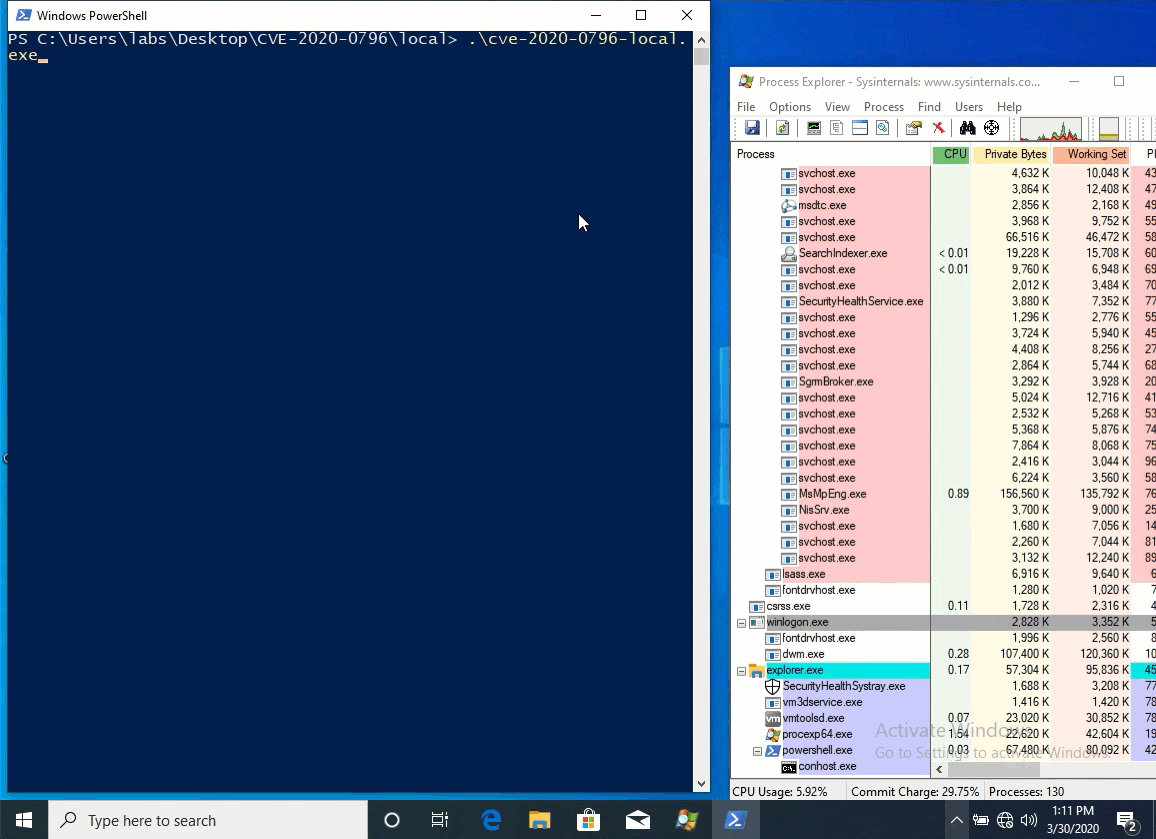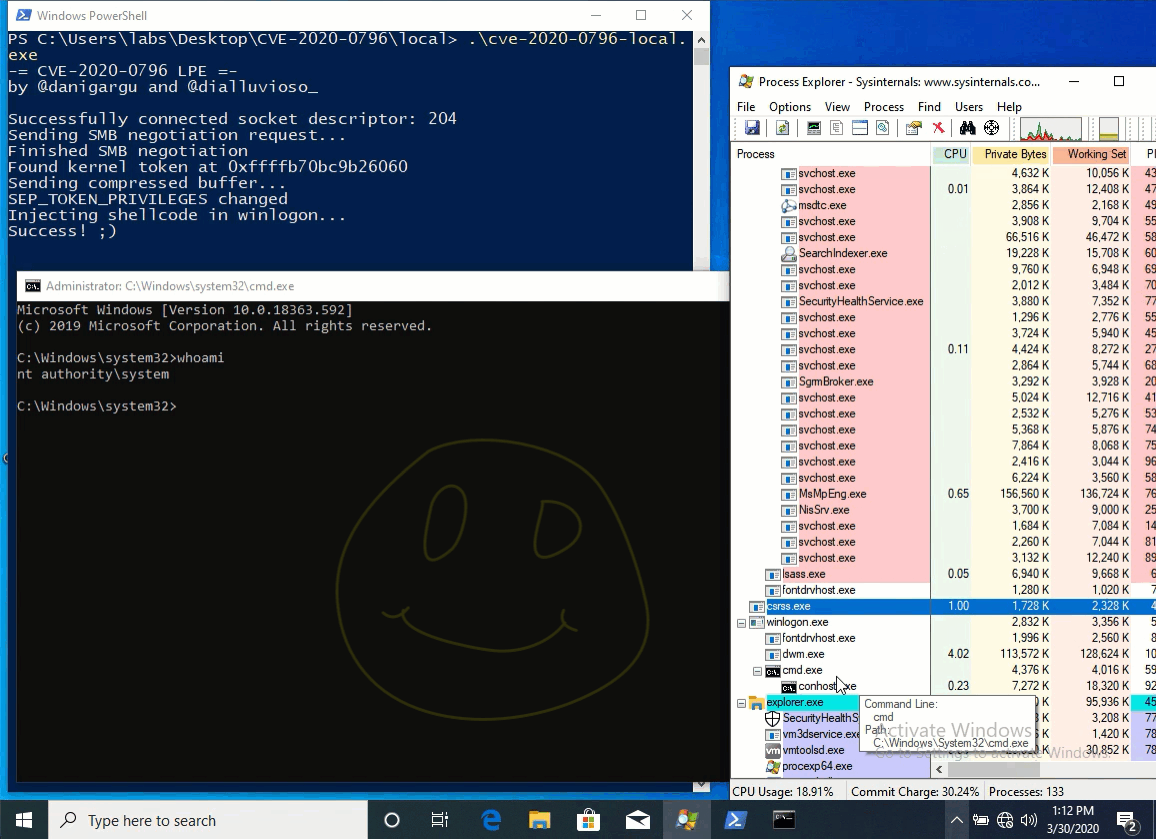
Let's start patching and test exploits (in own labs or for detecting purposes :) )
DotNetNuke
A new module for DotNetNuke (versions 5.0.0 to 9.3.0-RC) was recently added in metasploit. Vulnerable versions store user profile information in the DNNPersonalization cookie in XML format. The expected structure includes the "type" attribute to sprcify the server which type of object to create during deserialization. It happens if the DNN is configured to handle 404 errors with its built-in error page (default configuration). Attacker can use this vulnerability for remote code execution on the target system.
Redis Replication Code Execution
Vulners sets own AI score for many exploits and vulnerabilities. Thus, exploit for Redis has gained a fairly high rating and becomes more popular due to a new bug fix. Extended functionality added after Redis 4.0.0 for executing arbitrary code has become vulnerable. To transmit the given extension it makes use of the feature of Redis which called replication between master and slave.
https://vulners.com/zdt/1337DAY-ID-34165
More research about Vulners AI score: http://vulners.blog/2020/04/02/hidden-threat-vulnerability-analysis-using-the-news-graph
INFOSEC TOOLS

JACKDAW
This tool help you help to collect information about domain, store it in a SQL database and show graph. It gain a better understanding of Active Directory objects interact with each-other . Main features:
- Data acquisition;
- Graph building;
- Anomlaies detection
Webkiller v2.0
Simple tool for gathering infomation. If you don’t like to understand large and intricate OSINT frameworks, you will like this tool .
Pulsar
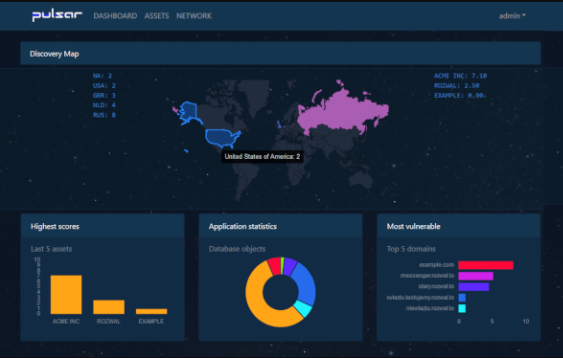
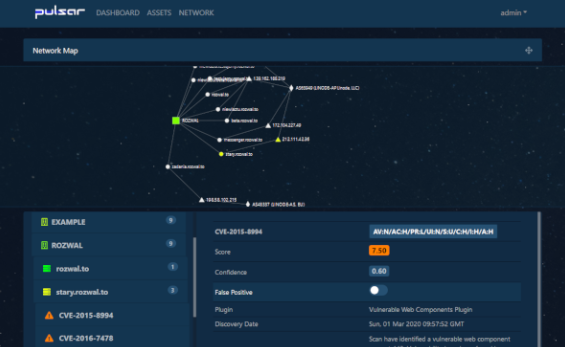
Pulsar is an automated framework with GUI for Red teams, pentesters and Bounty Hunters. If you like to know about full-scale and holistic tools, it will fascinate you for a long time and can become a permanent tool. This framework integrated several projects:
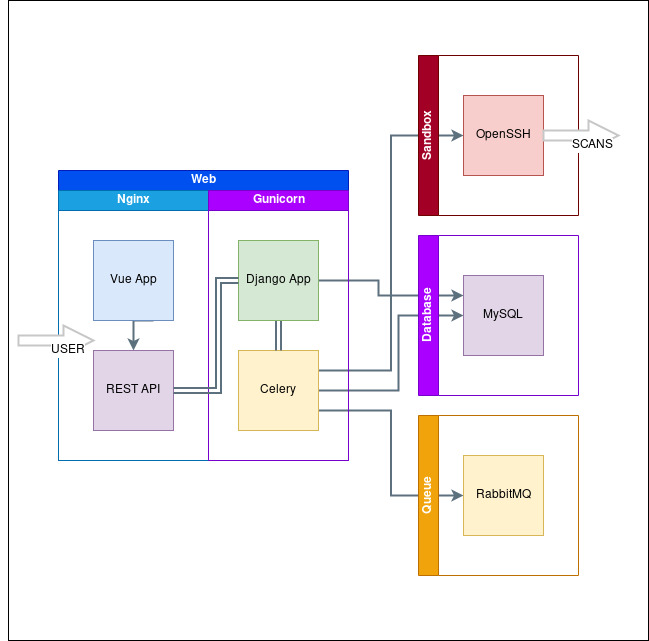
The full structure of the project:
SauronEye
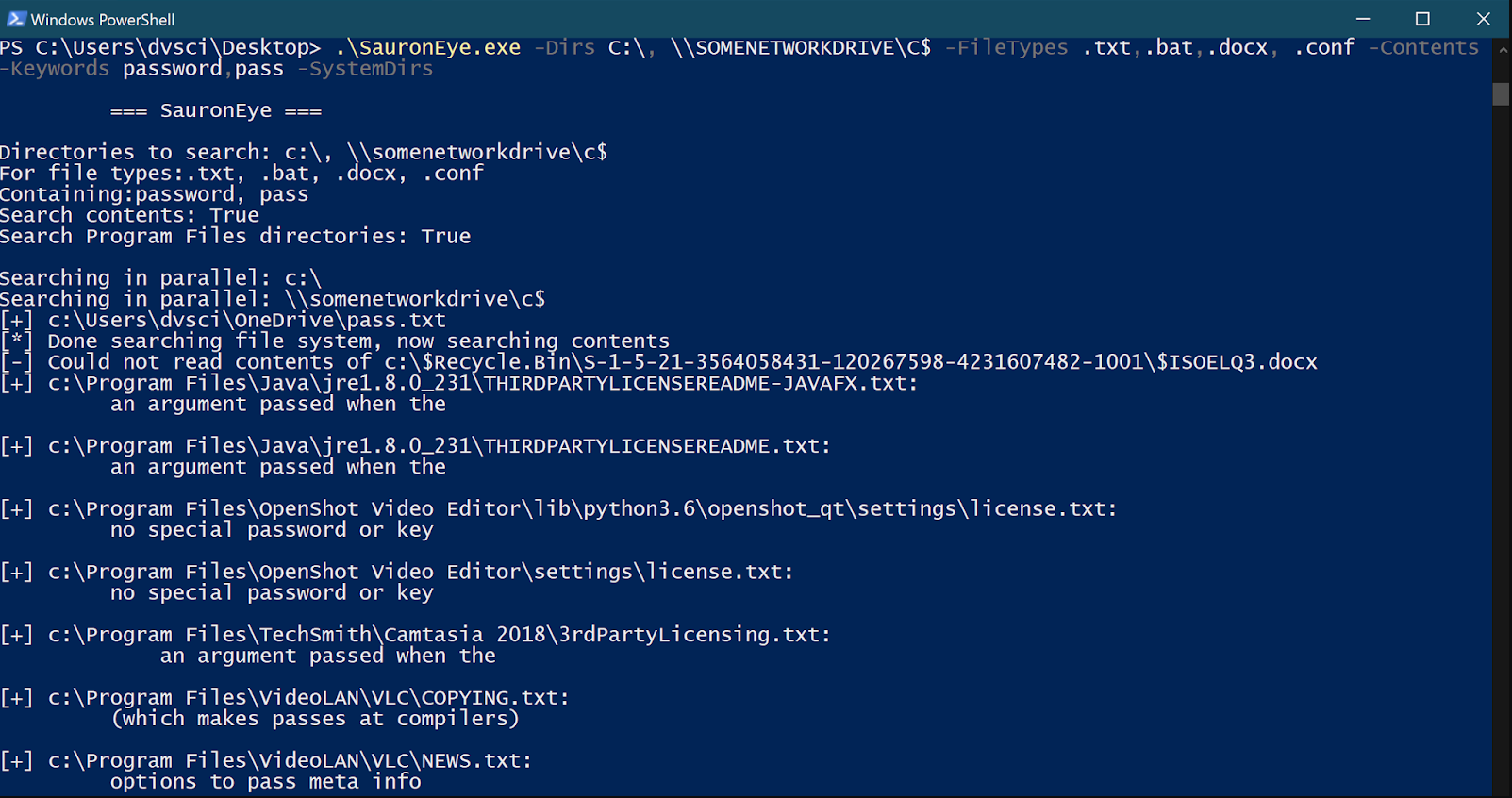
Simple search tool to find files containing specific keywords. Main features:
- Search multiple (network) drives;
- Search contents of files;
- Search contents of Microsoft Office files;
- Supports regular expressions in search keywords.
ZOOM and MITRE

If coronavirus is the number one topic in IT news, then ZOOM has definitely taken the second place in recent days.
The ZOOM client, when sending a URL to an internal chat, converts it into a hyperlink. However, along with this, it also converts the UNC paths that Windows uses to access network resources to hyperlinks.
When you click on such a hyperlink, Windows uses the SMB protocol and transfers the username and NTLM hash of the user's password to the other side. The latter can be easily opened taking into account modern computing power.
Thus, an attacker, having sent a specially formed link to the application’s internal chat, can subsequently obtain a user login and password. In addition, a command to start a local application can be sent in UNC format. True, in this case, Windows will ask permission to run.
More detailed: https://vulners.com/thn/THN:679E49F88578E2E63101319B5AB7DAAC
Based on low AI score of news about ZOOM vulnerabilities, we can conclude that most of them are hype and do not make much sense:

One of the most important events for all who try to detect APT attacks and analyse endpoint logs - MITRE Sub-Techniques (beta). The current one is still the October 2019 version.

The version of ATT&CK with sub-techniques is only in beta right now to allow enough time for feedback and for organizations to determine how to transition. We are expecting to make we make it the official version sometime in July 2020.
One good example of demonstrating the benefits of sub-techniques is T1003. The name was changed slightly to OS Credential Dumping and the technique kept:

Technique T1003
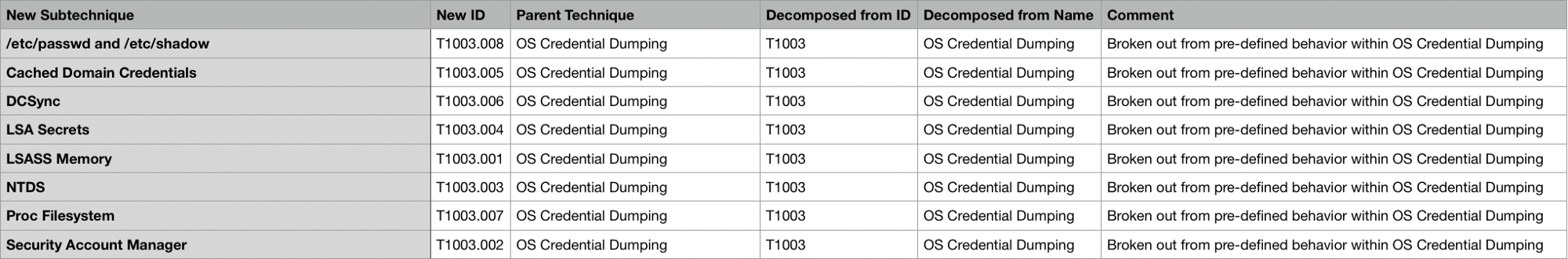
Sub-techniques of this techniques
The added granularity will allow you to represent different types of credential dumping that can happen at a more detailed level than just mapping to the broader OS Credential Dumping. MITRE're asking for feedback on technique and sub-technique pairings as well as any additional techniques or sub-technique ideas that help organize remaining techniques without sub-techniques.
More detailed info in MITRE blog: https://medium.com/mitre-attack/attack-subs-what-you-need-to-know-99bce414ae0b
Attack matrix for Kubernetes
On this week, Microsoft crafted an ATT&CK-like matrix comprising the major techniques that are relevant to container orchestration security, with focus on Kubernetes:
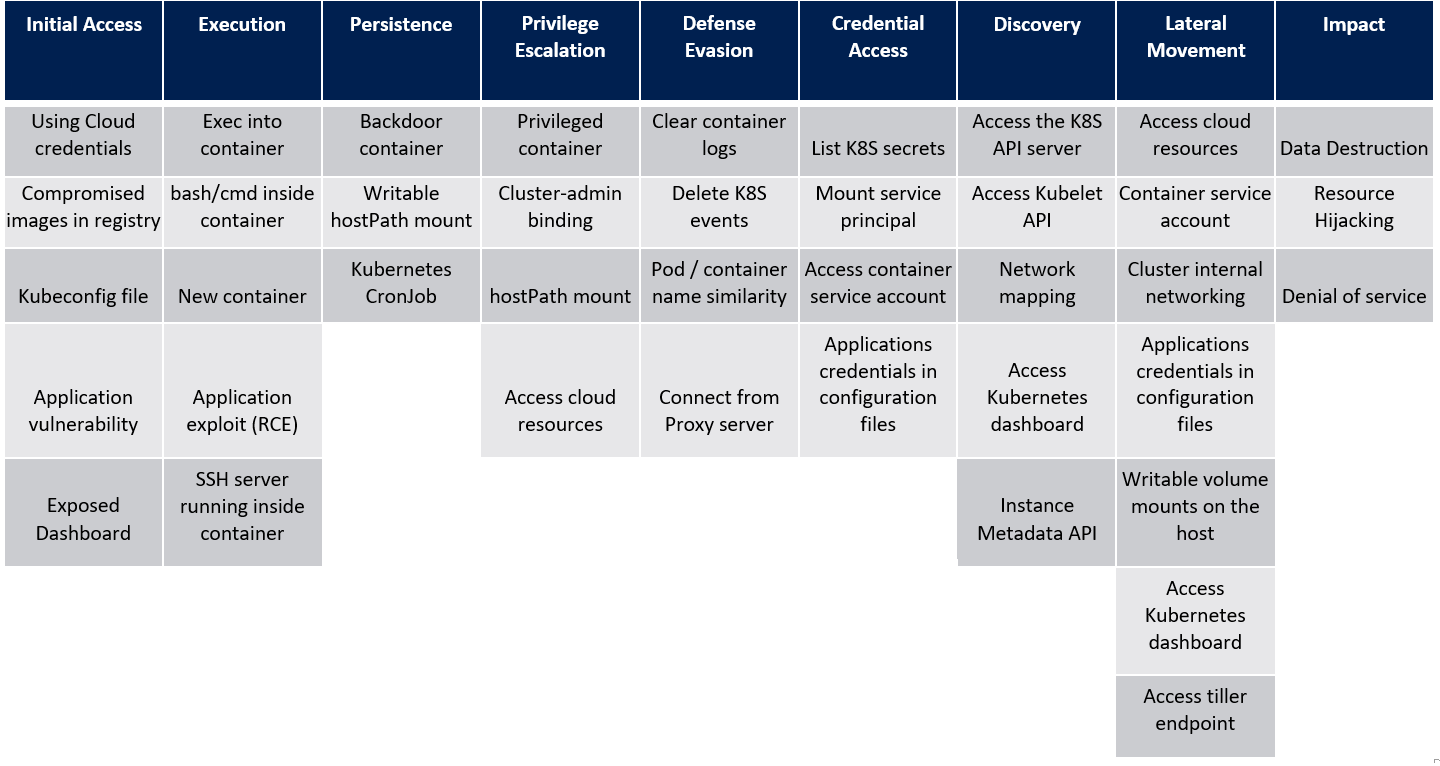
Understanding the attack surface of containerized environments is the first step of building security solutions for these environments. This matrix can help organizations identify the current gaps in their defenses coverage against the different threats that target Kubernetes.
https://vulners.com/mssecure/MSSECURE:B88202FB5B97F91B4C2853079E60CFF1