
Microsoft Patch Tuesday December 2022: SPNEGO RCE, Mark of the Web Bypass, Edge Memory Corruptions
9.6 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P
0.035 Low
EPSS
Percentile
90.2%
Hello everyone! This episode will be about Microsoft Patch Tuesday for December 2022, including vulnerabilities that were added between November and December Patch Tuesdays. As usual, I use my open source Vulristics project to analyse and prioritize vulnerabilities.
Alternative video link (for Russia): <https://vk.com/video-149273431_456239112>
But let's start with an older vulnerability. This will be another example why vulnerability prioritization is a tricky thing and you should patch everything. In the September Microsoft Patch Tuesday there was a vulnerability Information Disclosure - SPNEGO Extended Negotiation (NEGOEX) Security Mechanism (CVE-2022-37958), which was completely unnoticed by everyone. Not a single VM vendor paid attention to it in their reviews. I didn't pay attention either.
SPNEGO**(Simple and Protected GSSAPI Negotiation Mechanism)** is a GSSAPI "pseudo mechanism" used by client-server software to negotiate the choice of security technology. SPNEGO is used when a client application wants to authenticate to a remote server, but neither end is sure what authentication protocols the other supports. Who knows what kind of disclosure there might be. This vulnerability had CVSS 7.5 (High), not even Critical.
And then on December 13th, IBM Security X-Force researcher Valentina Palmiotti posts a video exploiting this vulnerability, which turns out to be Remote Code Execution. In this video, a Python script is executed in a Linux virtual machine, and in a Windows 10 virtual machine, the message "Your PC will automatically restart in one minute" appears, which indicates that some code was executed there. The researcher is famous and it is highly unlikely that the video is fake.
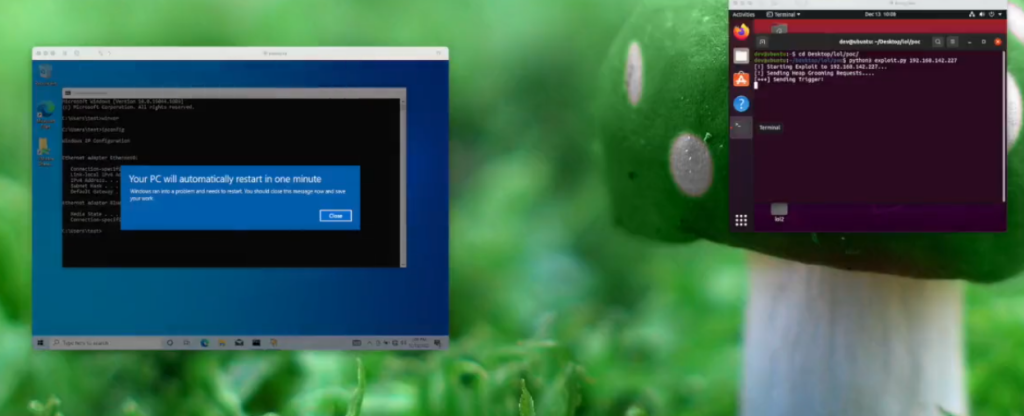
It turned out that the vulnerability can be exploited during the authentication attempts. The vulnerability affects various protocols. Primarily RDP and SMB. It may be relevant for SMTP, HTTP and others with a non-standard configuration. So, this vulnerability could potentially be worse than EternalBlue.
Microsoft has made changes to the description of the vulnerability. Now it is Critical RCE. NVD hasn't made any changes yet. IBM promises not to release details until the second quarter of 2023 to give people time to patch.
Now let's look at the most interesting vulnerabilities of Microsoft Patch Tuesday for December 2022.
$ cat comments_links.txt
Qualys|December 2022 Patch Tuesday|https://blog.qualys.com/vulnerabilities-threat-research/patch-tuesday/2022/12/13/the-december-2022-patch-tuesday-security-update-review
ZDI|THE DECEMBER 2022 SECURITY UPDATE REVIEW|https://www.zerodayinitiative.com/blog/2022/12/13/the-december-2022-security-update-review
$ python3.8 process_classify_ms_products.py # Automated classifier for Microsoft products
$ python3.8 vulristics.py --report-type "ms_patch_tuesday_extended" --mspt-year 2022 --mspt-month "December" --mspt-comments-links-path "comments_links.txt" --rewrite-flag "True"
...
Creating Patch Tuesday profile...
MS PT Year: 2022
MS PT Month: December
MS PT Date: 2022-12-13
MS PT CVEs found: 49
Ext MS PT Date from: 2022-11-09
Ext MS PT Date to: 2022-12-12
Ext MS PT CVEs found: 32
ALL MS PT CVEs: 81
...
- All vulnerabilities: 80
- Urgent: 0
- Critical: 3
- High: 29
- Medium: 48
- Low: 0
There were 2 vulnerabilities with signs of exploitation in the wild:
- Security Feature Bypass - Windows SmartScreen (CVE-2022-44698). It is a bypass of the Windows SmartScreen security feature, and has been seen exploited in the wild. It allows attackers to craft documents that won’t get tagged with Microsoft's "Mark of the Web" despite being downloaded from untrusted sites. Exploitation in the wild is mentioned on Vulners (cisa_kev object), AttackerKB, Microsoft websites. The existence of a public exploit is mentioned in Microsoft CVSS Temporal Score (Functional Exploit). To be honest, I do not consider these warnings from the operating system to be effective. Therefore, this vulnerability does not seem very critical to me. I think an Antivirus or EDR solution should block suspicious files from running in the first place.
- Memory Corruption - Microsoft Edge (CVE-2022-4135, CVE-2022-4262). Exploitation in the wild is mentioned on Vulners (cisa_kev object), AttackerKB websites. CVE-2022-4135: Heap buffer overflow in GPU in Google Chrome prior to 107.0.5304.121 allowed a remote attacker who had compromised the renderer process to potentially perform a sandbox escape via a crafted HTML page. (Chromium security severity: High). CVE-2022-4262: Type confusion in V8 in Google Chrome prior to 108.0.5359.94 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High)
Among other vulnerabilities without public exploits and signs of exploitation in the wild, it makes sense to pay attention to the following:
- Remote Code Execution - Microsoft PowerShell (CVE-2022-41076). This critical vulnerability affects PowerShell where any authenticate user, regardless of its privilege could escape the PowerShell Remoting Session Configuration and run unapproved commands on the target system. It is worth mentioning that, typically after the initial breach, attackers use the tools available on the system to keep the preserve or advance around a network, and PowerShell is one of the more capable tools they can find.
- Remote Code Execution - Windows Secure Socket Tunneling Protocol (SSTP) (CVE-2022-44670, CVE-2022-44676). This critical vulnerability affects Windows Secure Socket Tunneling Protocol (SSTP), and according to Microsoft, an attacker would need to win a race condition to successfully exploit these bugs. An unauthenticated attacker could send a specially crafted connection request to a RAS server, which could lead to remote code execution (RCE) on the RAS server machine. If you do not have this service, disable it.
- Among the Elevation of Privilegevulnerabilities, I would like to highlight a vulnerability in DirectX Graphics Kernel (CVE-2022-44710) and Windows Print Spooler (CVE-2022-44678, CVE-2022-44681).
Full Vulristics report: ms_patch_tuesday_december2022
9.6 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P
0.035 Low
EPSS
Percentile
90.2%