The December 2022 Patch Tuesday Security Update Review
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
Welcome to the final second Tuesday of the year. As expected, Microsoft and Adobe have released their latest security updates and fixes. Take a break from your holiday preparations and join us as we review the details of the latest security patches.
Microsoft Patches for December 2022
In this month's Patch Tuesday, Microsoft released 52 new patches addressing CVEs in Microsoft Windows and Windows Components, Azure and Azure Real Time Operating System, Microsoft Dynamics; Exchange Server, Office and Office Components, SysInternals, Visual Studio, SharePoint Server, Network Policy Server (NPS), Windows BitLocker, Microsoft Edge (Chromium-based) and Linux Kernel and Open Source Software. This complements two CVEs appointed earlier this month, bringing the December release total to 54 fixes.
Adobe Patches for December 2022
This month Adobe released three patches that fixed 37 CVEs, all rated as Important. These Adobe products have received updates: Experience Manager (32 bugs), Adobe Illustrator and Adobe Campaign Classic.
The most severe bugs are cross-site scripting (XSS) in Adobe Experience Manager (AEM) and memory leaks in Adobe Illustrator. The Adobe Campaign classic patch fixes a privilege escalation bug. Currently, no bug is listed as publicly known or under attack. Note that Adobe ranks these updates with a deployment priority rating of 3.
Microsoft has fixed several flaws in its software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing.
The December 2022 Microsoft vulnerabilities are classified as follows:
| Vulnerability Type | Quantity | Severities |
|---|---|---|
| Elevation of Privilege Vulnerability | 19 | Important: 19 |
| Remote Code Execution Vulnerability | 24 | Important: 17 |
| Critical: 7 | ||
| Information Disclosure Vulnerability | 3 | Important: 3 |
| Feature Bypass Vulnerability | 2 | Moderate: 1 |
| Important: 1 | ||
| Denial of Service Vulnerability | 3 | Moderate: 1 |
| Important: 2 | ||
| Spoofing Vulnerability | 2 | Moderate: 2 |
| Defense in Depth | 1 | None |
In total, Microsoft addressed 54 vulnerabilities: 2 CVEs on December 5th, 51 new CVEs on December 13th, and one (1) Microsoft Defense in Depth Update ADV220005
Only one new CVE released this month is listed as exploited in the wild and one publicly known by the time this blog was released.
Notable Microsoft Vulnerabilities Patched
CVE-2022-44698 | Windows SmartScreen Security Feature Bypass Vulnerability
This vulnerability has a CVSSv3.1 score of 5.4/10.
This vulnerability is rated as Moderate, and it appears to be related to Windows Mark of the Web Security Feature Bypass Vulnerability (CVE-2022-41091) from last month. Simply, a specially crafted file could be constructed to bypass the Mark of the Web (MOTW) defenses mechanism. It removes the MOTW feature from the file or makes it so that the MOTW isn't recognized by the security features that Microsoft provides and lets you open files without warnings. This will result in a limited loss of integrity and availability of security features such as Protected View in Microsoft Office, which rely on MOTW tagging. With the significant number of phishing attacks every day depending on users opening malicious files/attachments, these types of protection act as essential means to prevent attacks. Patching this vulnerability is highly recommended.
Exploitability Assessment: Exploitation Detected
CVE-2022-44713 | Microsoft Outlook for Mac Spoofing Vulnerability
This vulnerability has a CVSSv3.1 score of 7.5/10.
This security bug is rated as important and a spoofing vulnerability, which we want to emphasize since it relates to email clients. This vulnerability could allow an attacker to appear as a trusted user when they should not be. This could cause a user to mistakenly trust a signed email message as if it came from a legitimate user. If we mix this bug along with above mention Windows SmartScreen Security Feature Bypass (CVE-2022-44698), it will be very destructive. Users could get emails that look like they are coming from trusted users with malicious attachments, and not many users wouldn't open them.
Exploitability Assessment: Exploitation Less Likely
Microsoft Critical Vulnerability Highlights
CVE-2022-41127 | Microsoft Dynamics NAV and Microsoft Dynamics 365 Business Central (On Premises) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.5/10.
This critical vulnerability affects Microsoft Dynamics NAV and Microsoft Dynamics 365 Business Central (On-Premises). This security flaw that could lead to a scope change allows an authenticated attacker to execute code on the host server (underlying operating system) in the context of the service account Dynamics configured to use. Since the Dynamics NAV opened the port, this could be used to connect with the Windows Communication Foundation (WCF) TCP protocol. As an authenticated user, the attacker could try to trigger malicious code in the context of the server's account through a network call. Note that any guest-to-host escape should be taken very seriously.
Potential Impact is HIGH for Confidentiality, Integrity, and Availability.
A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-44690 and CVE-2022-44693 | Microsoft SharePoint Server Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
This critical vulnerability affects Microsoft SharePoint Server, an authenticated attacker with Manage List permissions could execute code remotely on the SharePoint Server. These two vulnerabilities affect the following version of Microsoft SharePoint:
Microsoft SharePoint Enterprise Server 2013 Service Pack 1 and 2016, Microsoft SharePoint Foundation 2013 Service Pack 1, Microsoft SharePoint Server 2019, Microsoft SharePoint Server Subscription Edition Note: The customers running SharePoint Server 2013 Service Pack 1 can install the cumulative update or the security update, which is the same update as for Foundation Server 2013.
Potential Impact is HIGH for Confidentiality, Integrity, and Availability.
A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-41076 | PowerShell Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.5/10.
This critical vulnerability affects PowerShell where any authenticate user, regardless of its privilege could escape the PowerShell Remoting Session Configuration and run unapproved commands on the target system. It is worth mentioning that, typically after the initial breach, attackers use the tools available on the system to keep the preserve or advance around a network, and PowerShell is one of the more capable tools they can find. We highly recommend testing and patching this bug.
Potential Impact is HIGH for Confidentiality, Integrity, and Availability.
A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
Exploitability Assessment: Exploitation More Likely
CVE-2022-44670 and CVE-2022-44676 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1/10.
This critical vulnerability affects Windows Secure Socket Tunneling Protocol (SSTP), and according to Microsoft, an attacker would need to win a race condition to successfully exploit these bugs. An unauthenticated attacker could send a specially crafted connection request to a RAS server, which could lead to remote code execution (RCE) on the RAS server machine. If you do not have this service, we recommend disabling it. Otherwise, test and deploy these patches immediately.
Potential Impact is HIGH for Confidentiality, Integrity, and Availability.
A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
Exploitability Assessment: Exploitation Unlikely
CVE-2022-41089 | .NET Framework Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
This security update handles a security flaw where restricted mode is triggered for the parsing of XPS files. The XPS documents utilize structural or semantic elements like table structure, storyboards, or hyperlinks. This vulnerability may cause it to not display correctly in WPF-based readers, preventing gadget chains which could allow remote code execution on an affected system.
There is also a workaround regarding this issue.
Potential Impact is HIGH for Confidentiality, Integrity, and Availability.
A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
Exploitability Assessment: Exploitation less likely
There are three Denial-of-Service (DOS) vulnerabilities that is patched this month. The Windows Hyper-V Denial of Service Vulnerability (CVE-2022-44682) affects the Hyper-V host's functionality. Microsoft did not provide many details. Moreover, it is never good when a guest operating system can adversely influence the host OS.
There are 18 patches addressing Elevation of Privilege (EoP) vulnerabilities, which mostly require an authenticated user to execute specifically crafted code to escalate privileges. There are a few bugs in the Print Spooler service, which is an appendage of PrintNightmare. The DirectX Graphics Kernel Elevation of Privilege Vulnerability(CVE-2022-44710) is listed as public in this month's release.
The Azure Network Watcher Agent Security Feature Bypass Vulnerability (CVE-2022-44699) is another important one this month since it could allow an attacker to end the packet capture from the Network Watcher agent, which could result in logs being missed. Any organization that uses VM extension for log collection should treat this as a critical bug.
The Microsoft Edge (Chromium-based) spoofing bug is receiving a patch that allows an attacker to change the content of the autofill box.
This month we have a new advisory (ADV220005) providing further recommendations on third-party drivers certified by the Microsoft Windows Hardware Developer Program. Microsoft stated that drivers that appear to be approved/certified by this program had been seen in the wild.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions that are affected, including, but not limited to, .NET Framework, Azure, Client Server Run-time Subsystem (CSRSS), Microsoft Bluetooth Driver, Microsoft Dynamics, Microsoft Edge (Chromium-based), Microsoft Graphics Component, Microsoft Office, Microsoft Office OneNote, Microsoft Office SharePoint, Microsoft Office Visio, Microsoft Windows Codecs Library, Windows Hyper-V, SysInternals, Windows Certificates, Windows Contacts, Windows DirectX, Windows Error Reporting, Windows Fax Compose Form, Windows HTTP Print Provider, Windows Kernel, Windows PowerShell, Windows Print Spooler Components, Windows Projected File System, Windows Secure Socket Tunneling Protocol (SSTP), Windows SmartScreen, Windows Subsystem for Linux, Windows Terminal
Downloads include Cumulative Updates, Monthly Rollups, Security Only, and Security Update
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
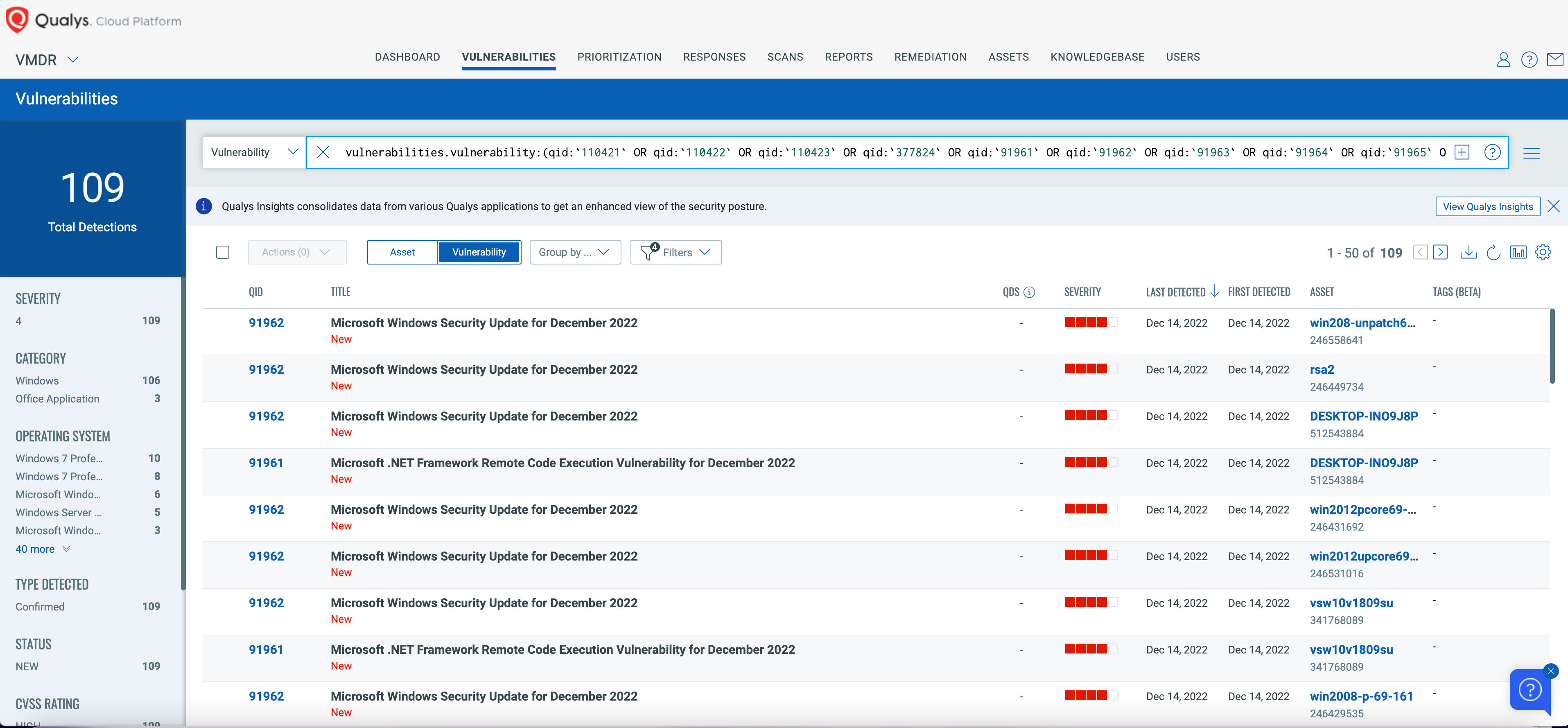
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:(qid:`110421` OR qid:`110422` OR qid:`110423` OR qid:`377824` OR qid:`91961` OR qid:`91962` OR qid:`91963` OR qid:`91964` OR qid:`91965` OR qid:`91966` OR qid:`91967`)
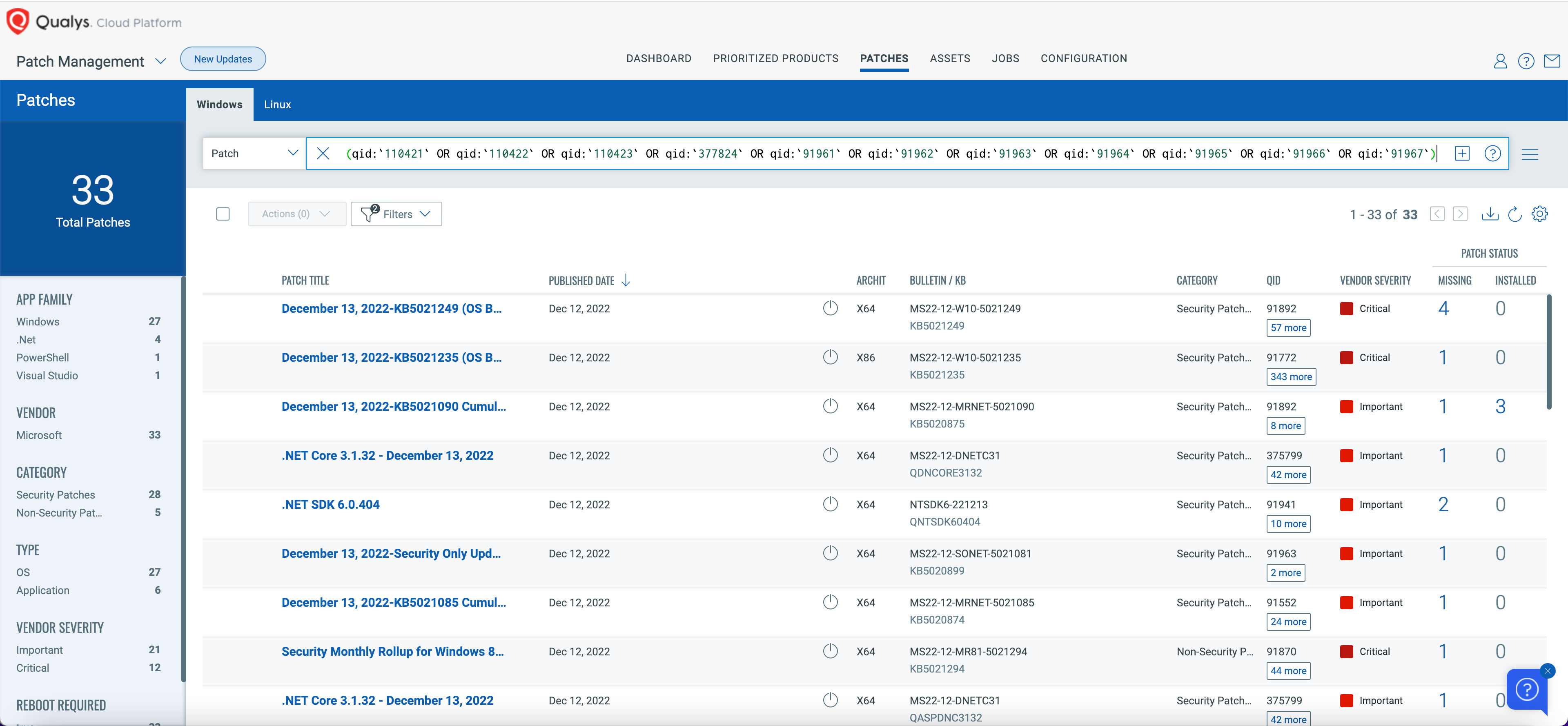
Rapid Response withPatch Management** (PM)**
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
(qid:`110421` OR qid:`110422` OR qid:`110423` OR qid:`377824` OR qid:`91961` OR qid:`91962` OR qid:`91963` OR qid:`91964` OR qid:`91965` OR qid:`91966` OR qid:`91967`)
EXECUTE Mitigation Using Qualys Custom Assessment and Remediation (CAR)
Qualys Custom Assessment and Remediation empowers a system administrator to quickly and easily perform configuration updates on your technology infrastructure when the current situation requires the implementation of a vendor-suggested mitigation or workaround.
Try it for free! Sign up now for a no-cost trial of Qualys Custom Assessment and Remediation
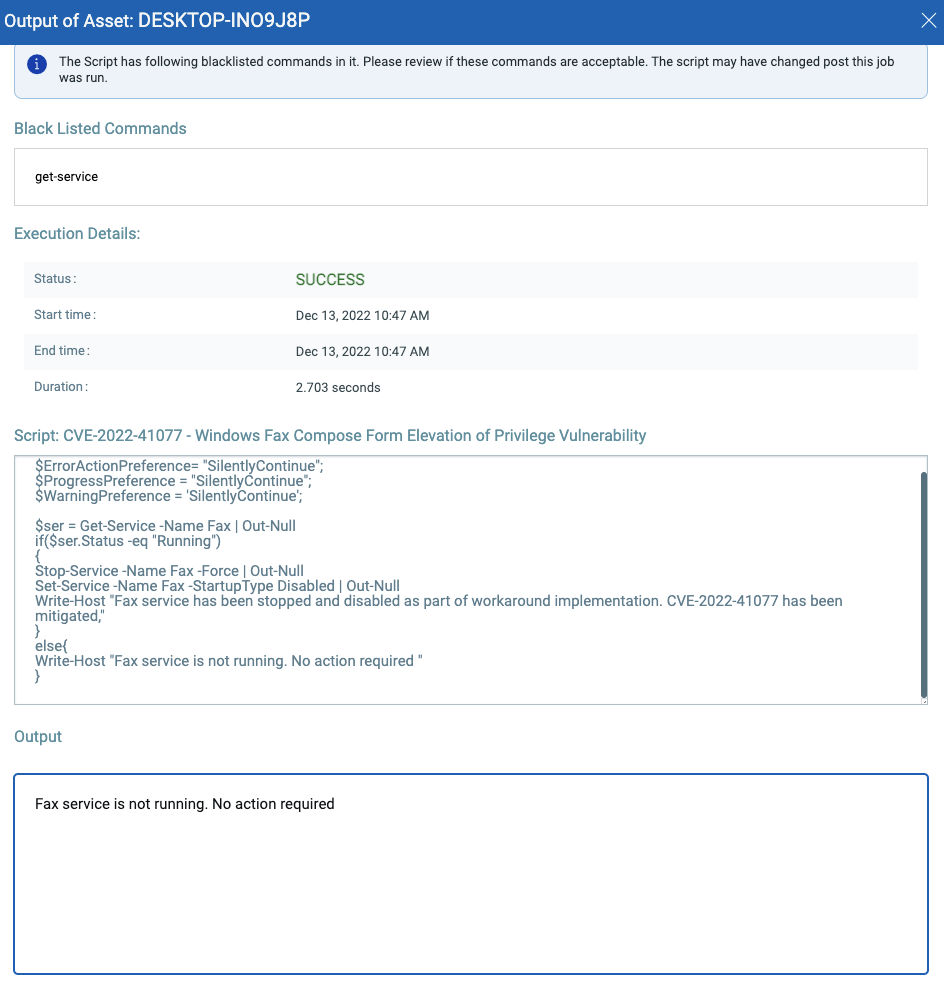
Customers can perform the provided mitigation steps by creating a PowerShell script and executing it on vulnerable assets.
Please refer to the Qualys GitHub link to ensure the most current version of a Qualys script is being applied.
CVE-2022-41077 | Windows Fax Compose Form Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8/10.
Script
$ErrorActionPreference= "SilentlyContinue";
$ProgressPreference = "SilentlyContinue";
$WarningPreference = 'SilentlyContinue';
$ser = Get-Service -Name Fax | Out-Null
if($ser.Status -eq "Running")
{
Stop-Service -Name Fax -Force | Out-Null Set-Service -Name Fax -StartupType Disabled | Out-Null Write-Host "Fax service has been stopped and disabled as part of workaround implementation. CVE-2022-41077 has been mitigated,"
}
else{
Write-Host "Fax service is not running. No action required "
}
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
Qualys Policy Compliance Control Library makes it easy to evaluate your technology infrastructure when the current situation requires implementation validation of a vendor-suggested mitigation or workaround.
Mitigation refers to a setting, common configuration, or general best practice, existing in a default state, that could reduce the severity of exploitation of a vulnerability.
A workaround is sometimes used temporarily for accomplishing a task or purpose while the standard or planned procedure isn’t functioning. Once a problem is resolved, a workaround is typically abandoned.
The following Qualys Policy Compliance Control IDs (CIDs), and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2022-41077 | Windows Fax Compose Form Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8/10.
Policy Compliance Control IDs (CIDs):
- 1161 Status of the 'Fax' service
- 14916 Status of Windows Services
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control:( id:`1161` OR id:`14916`)

The next Patch Tuesday falls on January 10th, and we’ll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to the This Month in Vulnerabilities and Patches webinar.
Happy Holidays!
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are part of this month's Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H