Update Your Chrome Browser ASAP to Patch a Week Old Public Exploit
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P
Google on Tuesday released an update for Chrome web browser for Windows, Mac, and Linux, with a total of seven security fixes, including one flaw for which it says an exploit exists in the wild.
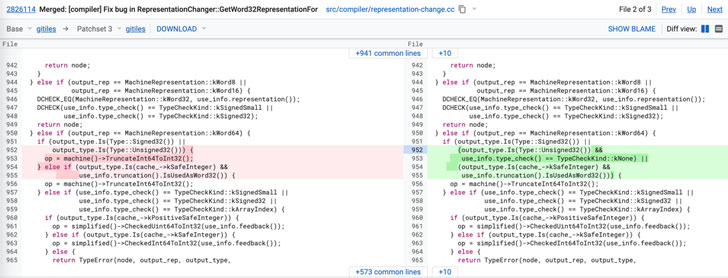
Tracked as CVE-2021-21224, the flaw concerns a type confusion vulnerability in V8 open-source JavaScript engine that was reported to the company by security researcher Jose Martinez on April 5
According to security researcher Lei Cao, the bug [1195777] is triggered when performing integer data type conversion, resulting in an out-of-bounds condition that could be used to achieve arbitrary memory read/write primitive.
“Google is aware of reports that exploits for CVE-2021-21224 exist in the wild,” Chrome’s Technical Program Manager Srinivas Sista said in a blog post.
The update comes after proof-of-concept (PoC) code exploiting the flaw published by a researcher named “frust” emerged on April 14 by taking advantage of the fact that the issue was addressed in the V8 source code, but the patch was not integrated into the Chromium codebase and all the browsers that rely on it, such as Chrome, Microsoft Edge, Brave, Vivaldi, and Opera.
The one-week patch gap meant the browsers were vulnerable to attacks until the patches posted in the open-source code repository were released as a stable update.
It’s worth noting that Google halved the median “patch gap” from 33 days in Chrome 76 to 15 days in Chrome 78, which was released in October 2019, thereby pushing severe security fixes every two weeks.
The latest set of fixes also arrive close on the heels of an update the search giant rolled out last week with patches for two security vulnerabilities CVE-2021-21206 and CVE-2021-21220, the latter of which was demonstrated at the Pwn2Own 2021 hacking contest earlier this month.
Chrome 90.0.4430.85 is expected to roll out in the coming days. Users can update to the latest version by heading to Settings > Help > About Google Chrome to mitigate the risk associated with the flaws.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P