Experts Warn of Browser Extensions Spying On Users via Cloud9 Chrome Botnet Network
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
The Keksec threat actor has been linked to a previously undocumented malware strain, which has been observed in the wild masquerading as an extension for Chromium-based web browsers to enslave compromised machines into a botnet.
Called Cloud9 by security firm Zimperium, the malicious browser add-on comes with a wide range of features that enables it to siphon cookies, log keystrokes, inject arbitrary JavaScript code, mine crypto, and even enlist the host to carry out DDoS attacks.
The extension “not only steals the information available during the browser session but can also install malware on a user’s device and subsequently assume control of the entire device,” Zimperium researcher Nipun Gupta said in a new report.
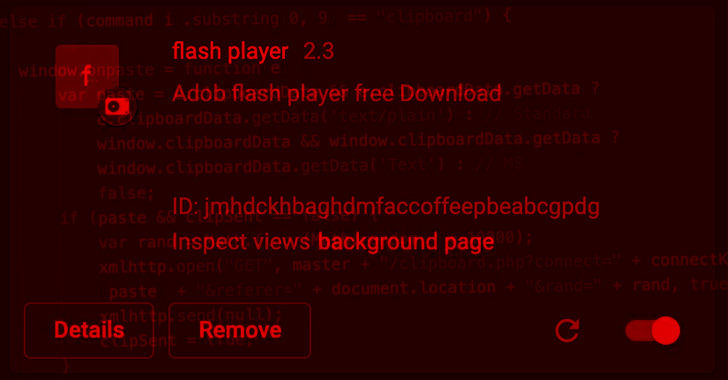
The JavaScript botnet isn’t distributed via Chrome Web Store or Microsoft Edge Add-ons, but rather through fake executables and rogue websites disguised as Adobe Flash Player updates.
Once installed, the extension is designed to inject a JavaScript file called “campaign.js” on all pages, meaning the malware could also operate as a standalone piece of code on any website, legitimate or otherwise, potentially leading to watering hole attacks.
The JavaScript code takes responsibility for cryptojacking operations, abusing the victim’s computing resources to illicitly mine cryptocurrencies, as well as inject a second script named “cthulhu.js.”
This attack chain, in turn, exploits flaws in web browsers such as Mozilla Firefox (CVE-2019-11708, CVE-2019-9810), Internet Explorer (CVE-2014-6332, CVE-2016-0189), and Edge (CVE-2016-7200) to escape the browser sandbox and deploy malware on the system.
The script further acts as a keylogger and a conduit for launching additional commands received from a remote server, allowing it to steal clipboard data, browser cookies, and mount layer 7 DDoS attacks against any domain.
Zimperium attributed the malware to a threat actor tracked as Keksec (aka Kek Security, Necro, and FreakOut), which has a history of developing a wide range of botnet malware, including EnemyBot, for crypto mining and DDoS operations.
The connection to Keksec comes from overlaps in the domains that were previously identified as used by the malware group.
The fact that Cloud9 is JavaScript-based and is offered either for free or a small fee on hacker forums makes it possible for less-skilled cybercriminals to get easy access to low-cost options for launching attacks targeting different browsers and operating systems.
The disclosure comes over three months after Zimperium discovered a malicious browser add-on dubbed ABCsoup that posed as a Google Translate tool to strike Russian users of Google Chrome, Opera, and Mozilla Firefox browsers.
“Users should be trained on the risks associated with browser extensions outside of official repositories, and enterprises should consider what security controls they have in place for such risks,” Gupta said.
Update: Following the publication of the story, a Google spokesperson shared the below statement with The Hacker News -
“We always recommend users update to the latest version of Google Chrome to ensure they have the most up-to-date security protections. Users can also stay better protected from malicious executables and websites by enabling Enhanced Protection in the privacy and security settings in Chrome. Enhanced Protection automatically warns you about potentially risky sites and downloads and inspects the safety of your downloads and warns you when a file may be dangerous.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C