SolarWinds Hackers Target Think Tanks With New 'NativeZone' Backdoor
EPSS
Percentile
61.2%
Microsoft on Thursday disclosed that the threat actor behind the SolarWinds supply chain hack returned to the threat landscape to target government agencies, think tanks, consultants, and non-governmental organizations located across 24 countries, including the U.S.
Some of the entities that were singled out include the U.S. Atlantic Council, the Organization for Security and Co-operation in Europe (OSCE), the Ukrainian Anti-Corruption Action Center (ANTAC), the EU DisinfoLab, and the Government of Ireland’s Department of Foreign Affairs.
“This wave of attacks targeted approximately 3,000 email accounts at more than 150 different organizations,” Tom Burt, Microsoft’s Corporate Vice President for Customer Security and Trust, said. “At least a quarter of the targeted organizations were involved in international development, humanitarian, and human rights work.”
Microsoft attributed the ongoing intrusions to the Russian threat actor it tracks as Nobelium, and by the wider cybersecurity community under the monikers APT29, UNC2452 (FireEye), SolarStorm (Unit 42), StellarParticle (Crowdstrike), Dark Halo (Volexity), and Iron Ritual (Secureworks).
The latest wave in a series of intrusions is said to have begun on Jan. 28, 2021, before reaching a new level of escalation on May 25. The attacks leveraged a legitimate mass-mailing service called Constant Contact to conceal its malicious activity and masquerade as USAID, a U.S.-based development organization, for a wide-scale phishing campaign that distributed phishing emails to a variety of organizations and industry verticals.
“Nobelium launched this week’s attacks by gaining access to the Constant Contact account of USAID,” Burt said.
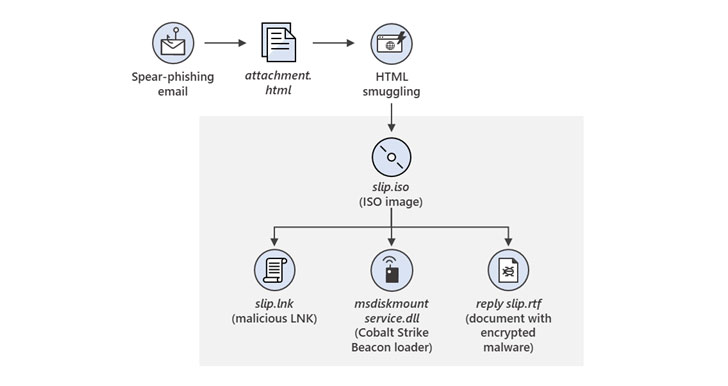
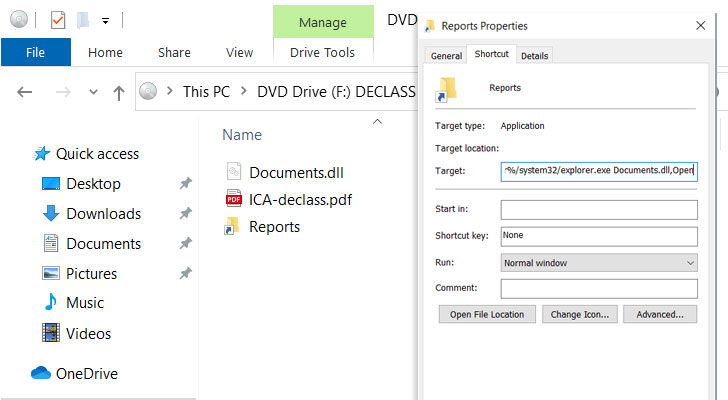
These seemingly authentic emails included a link that, when clicked, delivered a malicious optical disc image file (“ICA-declass.iso”) to inject a custom Cobalt Strike Beacon implant dubbed NativeZone (“Documents.dll”). The backdoor, similar to previous custom malware like Raindrop and Teardrop, comes equipped with capabilities to maintain persistent access, conduct lateral movement, exfiltrate data, and install additional malware.
In another variation of the targeted attacks detected before April, Nobelium experimented with profiling the target machine after the email recipient clicked the link. In the event the underlying operating system turned out to be iOS, the victim was redirected to a second remote server to dispatch an exploit for the then zero-day CVE-2021-1879. Apple addressed the flaw on March 26, acknowledging that “this issue may have been actively exploited.”
Cybersecurity firms Secureworks and Volexity, which corroborated the findings, said the campaign singled out non-governmental organizations, research institutions, government entities, and international agencies situated in the U.S., Ukraine, and the European Union.
“The very narrow and specific set of email identifiers and organizations observed by CTU researchers strongly indicate that the campaign is focused on U.S. and European diplomatic and policy missions that would be of interest to foreign intelligence services,” researchers from Secureworks Counter Threat Unit noted.
The latest attacks add to evidence of the threat actor’s recurring pattern of using unique infrastructure and tooling for each target, thereby giving the attackers a high level of stealth and enabling them to remain undetected for extended periods of time.
The ever-evolving nature of Nobelium’s tradecraft is also likely to be a direct response to the highly publicized SolarWinds incident, suggesting the attackers could further continue to experiment with their methods to meet their objectives.
“When coupled with the attack on SolarWinds, it’s clear that part of Nobelium’s playbook is to gain access to trusted technology providers and infect their customers,” Burt said. “By piggybacking on software updates and now mass email providers, Nobelium increases the chances of collateral damage in espionage operations and undermines trust in the technology ecosystem.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.